SELWAK: A Secure and Efficient Lightweight and Anonymous Authentication and Key Establishment Scheme for IoT Based Vehicular Ad hoc Networks
Abstract
:1. Introduction
- In this paper, a novel lightweight anonymous authentication and key establishment scheme for VANETs is proposed that uses one-way cryptographic hash functions and simple XOR operations.
- We ensure the privacy of vehicles so that an adversary cannot trace the real identity and travel routes of vehicles.
- SELWAK is secure against replay attacks, impersonation attacks, man-in-the-middle attacks, stolen verifier attacks, stolen OBU attacks, untraceability, and anonymity.
- Formal security proof of establishing a secure session key is provided using the RoR model.
2. Related Work
Motivations
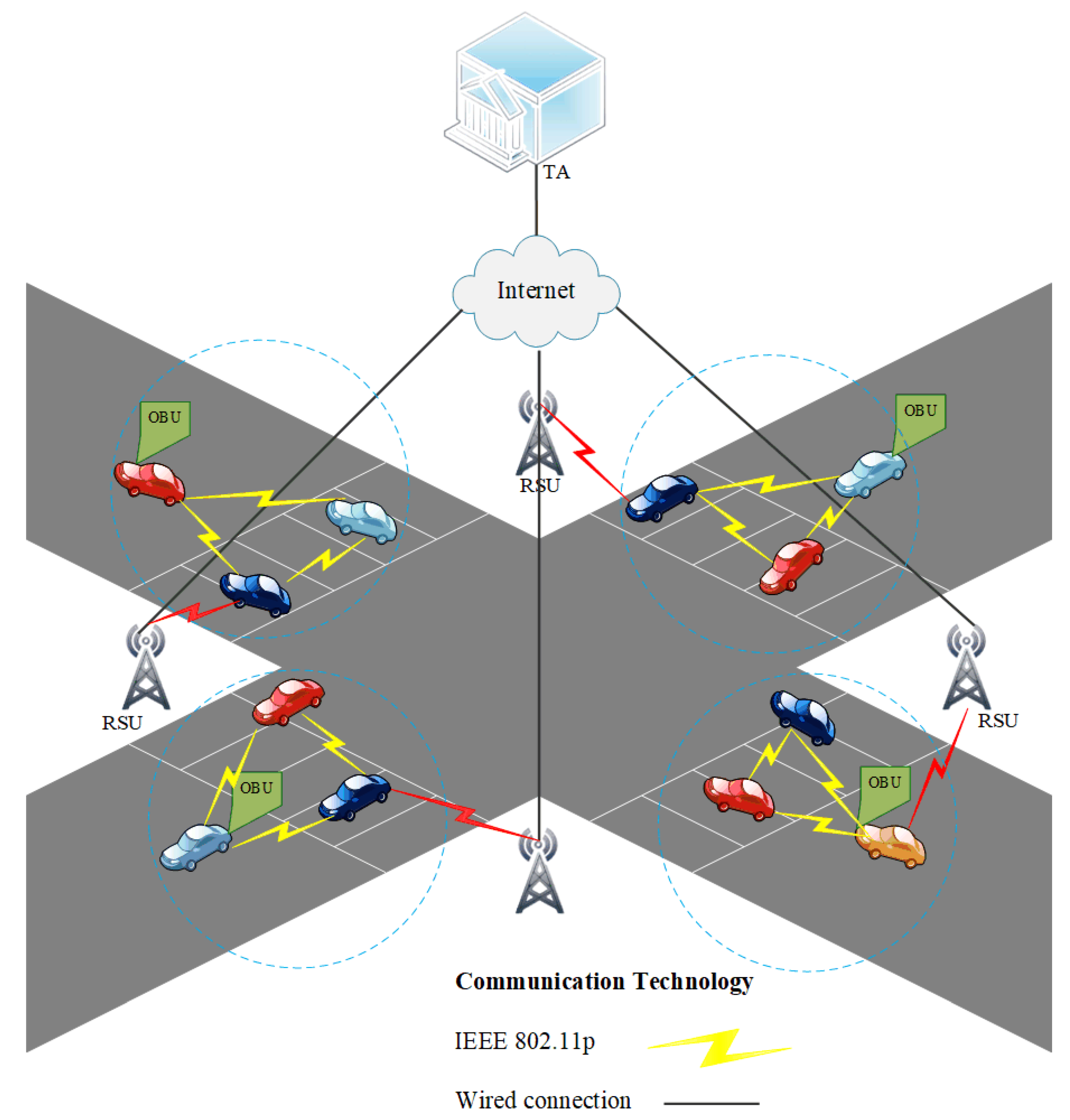
3. System Model
3.1. Network Model
3.2. Threat Model
4. Proposed Scheme
4.1. Registration Phase
4.1.1. Vehicle Registration Phase
- The driver Drvi of vehicle Vi, on his own choice, chooses a password PWDi and unique identity Drvid and two 160-bit random numbers si and k. OBUi computes a masked password , transmit to the TA through a secure channel.
- After receiving the registration request TA calculated using a pre-generated 160-bit secret key α. It further calculate Furthermore, for every registered vehicle Vi, a unique secret key is also generated by TA and computes time based credential on the basis of timestamp generated duringregistration time Then, TA transmit to through a secure channel.
- After receiving information compute
4.1.2. Roadside Unit Registration Phase
4.2. Authentication and Key Establishment Phase
4.2.1. V-To-V Authentication and Key Establishment Phase
- Onboard Unit OBUi generates current timestamp T1 and chooses random nonce and computes secret key Two neighbor vehicles used r and for authentication in VANETs. An OBUj further compute and and sends authentication requests {L1, L2, T1} to its neighboring vehicle through a public channel.
- “After receiving {L1, L2, T1}, OBUj validates the timeliness of T1 by checking condition where is the time when the message is received and ΔT is the maximum transmission delay. If the condition holds, OBUj calculates the time-dependent secret key on the basis of T1 and previously computed r. It then computes To proceed, it then calculates The OBUi further checks the condition L3 = L3, if condition holds then Vj authenticate Vi and reject otherwise.
- The OBUj selects a random nonce and current timestamp T2, and computes time-dependent secret key Then, the session key is computed and sends {L4, L5, T2} to Vi via a public channel.
- On the reception of {L4, L5, T2}, OBUi also checks the validity of T2 by where I message arrival time. If the condition is fulfilled, by using received T2 and earlier computer r and , OBUi computes . The OBUi further computes the session key It then checks the condition L6 = L5. If the condition is satisfied, Vi successfully authenticates. Using the current timestamp T3, the OBU computes and finally sends a response message {L7, T3} to Vj via a public channel.
- On the reception of {L7, T3}, OBUj checks the correctness of T3 by checking condition is reaching time. Then, it computes and checks whether If the condition is satisfied, the session key computed by OBUi is correct, and it guarantees that both Vi and the session key are established by Vj in this way start mutual communication. The pictorial representation of algorithm is given in Figure 4.
4.2.2. V-to-RSU Authentication and Key Establishment Phase
- An OBUi chooses a timestamp T1 and random nonce and calculates the time-dependent key on the basis of previously calculated r. It further computes and sends {L1, L2, T1} as an authentication message to its nearby RSUj through a public channel.
- After receiving {L1, L2, T1} RSUj validate T1. If it validates the timestamp, then RSUj calculates the time-dependent key If L3 = L2 holds the RSUj authenticate Vi and reject otherwise.
- The RSUj then chooses the current timestamp T2 and random nonce NRSU to calculate another time-dependent key It further calculates the session key and and sends message {L4, L5, T2} to Vi through an open channel. The pictorial representation of algorithm is given in Figure 5.
4.3. Key Establishment Phase between RSUs
- The random nonce is generated by RSUu and sends to RSUv.
- Upon receiving “RSUu calculates symmetric key shared with RSUu as by pre-loaded polynomial share þ (TRSv, y) and The RSUv then sends the message
- Finally, on reception of RSUu calculate the symmetric key and share with RSUuby pre-loaded polynomial share þ (TRSUu, y) and on the basis of its own already generated random nonce In addition to this, RSUu proves if it showed that both RSUu and RSUv used valid symmetric keys for their onward communication.
- After receiving {L4, L5, T2}, OBUi also validates T2. If it is valid, then OBUi calculate time-dependent key the basis of T2 and It further calculates a session key and is satisfied then Vi successfully authenticate RSUj. The OBUi again generates the current timestamp T3 to calculates and sends {L7, T3} to RSUj through an open channel.
- Upon receiving a message {L7, T3}, RSUj Validates T3. If it is valid, then RSUj calculates and checks whether L8 = L7. If the condition is satisfied, then the session key computed by OBUi is correct.
4.4. Password Update Phase
- Drvi provides provides an identity drvid and an old passwordIf the condition is not satisfied, the password updating process is stopped. Else, user and allowed the OBUi to update the password.
- The driver Drvi is requested to give a new password Then, it computes
- Finally, OBUi replaces with in its memory. Therefore, OBUi contains the message after the password update. The pictorial representation of algorithm is given in Figure 6.
5. Security Analysis
5.1. Formal Security Analysis
5.1.1. Participants
5.1.2. Accepted State
5.1.3. Partnering
- Both of and are in valid accepted states.
- Both of and mutual authenticate and share identical session identification.
- Both of and are mutual partners [36].
5.1.4. Freshness
5.1.5. Adversary
- EX (, ): An adversary executes this query to obtain a message that is exchanged between two original partners. This is called an eavesdropping attack.
- RL (): An adversary using this query gets the current session key generated by .
- SN (, message): By executing this query, an adversary sends a message to the participant and receives the message. This is called an active attack.
- OBU (): An adversary executes this query to extract stored information in OBU. This is called a stolen attack.
- Test ():It models the semantic security ofa session key. After starting the experiment, coin c is flipped, and only the adversary can know the output. This is helpful for determining the output of a test query.
5.1.6. Session Key’s Semantic Security
5.1.7. Random Oracle
5.2. Informal Security Analysis
- Replay Attack: In the V2V and V2RSU authentication processes, the corresponding messages MSG1 = (L1, L2, T1) and MSG2 = (L7, T3) have timestamps T1 and T3. If an attacker wants to reply to the message with delay, then the timestamp attached to the message will fail. Therefore, our scheme is robust against reply attacks.
- Impersonation Attack: During the V2V authentication an attacker can impersonate the vehicle; to do so, an attacker must create an authentic message MSG1 = (L1, L2, T1). For creating MSG1 an attacker requires secret r. An attacker cannot calculate message MSG1 even if he/she generates his/her own timestamp and random none as secret r, Mdrvid, TVi and TAid.
- Man-in-the-middle Attack: In the proposed scheme, two messages, namely MSG1 = (L1, L2, T1) and MSG2 = (L7, T3) are required for V2V authentication. If an attacker wants to modify the message, then he/she first generates a current timestamp and random nonce. An attacker cannot calculate KSr1A = h(r||T1A as he/she did not have a secret key. Thus, an attacker cannot modify messages.
- Stolen Verifier Attack: The information (, , , , fi, Y, , E4, h(·)) is stored in OBUi of the vehicle. We assume that an attacker can steal stored information from OBUi. However, the one-way hash function protects the secrets PWDi, r, r’, TAid, drvid. An attacker cannot guess the secrets PWDi, r, r′, TAid, drvid correctly due to the collision resistance property of a one-way hash function.
- Stolen OBU Attack: Suppose that an attacker has stolen the OBUi of the vehicle. An attacker can extract the stored information (, , , , fi, Y, , E4, h(·)) from OBUi. It is difficult for an attacker to drive drvid from Mdrvid without having the secret α.
- Untraceability: In the V2V and V2RSU authentication phases of the proposed scheme, two messages are followed: MSG1 = (L1, L2, T1) and MSG2 = (L7, T3). All messages are distinct in each session, and the attacker cannot trace the RSU or vehicle.
- Anonymity: In the proposed scheme, the messages for V2V and V2RSU authentication do not involve the identities of the RSU and the user. Therefore, it is infeasible for an attacker to drive the real identities of the RSU and the user. Hence, the proposed scheme satisfies the anonymity property.
- Insider Attack: SELWAk is robust against insider attacks. The neighboring vehicles cannot get unauthorized access to the sensitive information of a particular vehicle by stealing its credentials.
6. Performance Analysis
6.1. Computation Overhead
6.2. Communication Overhead
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zafar, F.; Khattak, H.A.; Aloqaily, M.; Hussain, R. Carpooling in Connected and Autonomous Vehicles: Current Solutions and Future Directions. ACM Comput. Surv. 2022, 1–33. [Google Scholar] [CrossRef]
- King, J.; Awad, A.I. A distributed security mechanism for resource-constrained IoT devices. Informatica 2016, 40, 133–143. [Google Scholar]
- Zahra, S.; Gong, W.; Khattak, H.A.; Shah, M.A.; Song, H. Cross-Domain Security and Interoperability in Internet of Things. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Chaubey, N.K. Security analysis of vehicular ad hoc networks (VANETs): A comprehensive study. Int. J. Secur. Its Appl. 2016, 10, 261–274. [Google Scholar] [CrossRef]
- Cui, J.; Tao, X.; Zhang, J.; Xu, Y.; Zhong, H. HCPA-GKA: A hash function-based conditional privacy-preserving authentication and group-key agreement scheme for VANETs. Veh. Commun. 2018, 14, 15–25. [Google Scholar] [CrossRef]
- Kouicem, D.E.; Bouabdallah, A.; Lakhlef, H. Internet of things security: A top-down survey. Comput. Netw. 2018, 141, 199–221. [Google Scholar] [CrossRef] [Green Version]
- Sicari, S.; Rizzardi, A.; Miorandi, D.; Coen-Porisini, A. Internet of Things: Security in the keys. In Proceedings of the 12th ACM Symposium on QoS and Security for Wireless and Mobile Networks, Malta, Malta, 13–17 November 2016; pp. 129–133. [Google Scholar]
- Wang, Y.; Zhong, H.; Xu, Y.; Cui, J. ECPB: Efficient conditional privacy-preserving authentication scheme supporting batch verification for VANETs. Int. J. Netw. Secur. 2016, 18, 374–382. [Google Scholar]
- Islam, S.H.; Obaidat, M.S.; Vijayakumar, P.; Abdulhay, E.; Li, F.; Reddy, M.K.C. A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs. Futur. Gener. Comput. Syst. 2018, 84, 216–227. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Deboarh, L.J. EAAP: Efficient Anonymous Authentication With Conditional Privacy-Preserving Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2467–2476. [Google Scholar] [CrossRef]
- Islam, S.H.; Biswas, G.P. A pairing-free identity-based authenticated group key agreement protocol for imbalanced mobile networks. Ann. Telecommun. 2012, 67, 547–558. [Google Scholar] [CrossRef]
- Malik, A.; Pandey, B. Security Analysis of Discrete Event Based Threat Driven Authentication Approach in VANET Using Petri Nets. Int. J. Netw. Secur. 2018, 20, 601–608. [Google Scholar]
- Zhang, L.; Men, X.; Choo, K.-K.R.; Zhang, Y.; Dai, F. Privacy-Preserving Cloud Establishment and Data Dissemination Scheme for Vehicular Cloud. IEEE Trans. Dependable Secur. Comput. 2018, 17, 634–647. [Google Scholar] [CrossRef]
- Liu, J.; Li, J.; Zhang, L.; Dai, F.; Zhang, Y.; Meng, X.; Shen, J. Secure intelligent traffic light control using fog computing. Future Gener. Comput. Syst. 2018, 78, 817–824. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Odelu, V.; Reddy, A.G.; Park, K.S.; Park, Y. Design of Lightweight Authentication and Key Agreement Protocol for Vehicular Ad Hoc Networks. IEEE Access 2017, 5, 14966–14980. [Google Scholar] [CrossRef]
- Ibrahim, S.; Hamdy, M.; Shaaban, E. Towards an optimum authentication service allocation and availability in VANETs. Int. J. Netw. Secur. 2017, 19, 955–965. [Google Scholar]
- Zhong, H.; Huang, B.; Cui, J.; Xu, Y.; Liu, L. Conditional Privacy-Preserving Authentication Using Registration List in Vehicular Ad Hoc Networks. IEEE Access 2017, 6, 2241–2250. [Google Scholar] [CrossRef]
- Gope, P.; Amin, R.; Islam, S.H.; Kumar, N.; Bhalla, V.K. Lightweight and privacy-preserving RFID authentication scheme for distributed IoT infrastructure with secure localization services for smart city environment. Future Gener. Comput. Syst. 2018, 83, 629–637. [Google Scholar] [CrossRef]
- Ali, I.; Lawrence, T.; Li, F. An efficient identity-based signature scheme without bilinear pairing for vehicle-to-vehicle communication in VANETs. J. Syst. Arch. 2019, 103, 101692. [Google Scholar] [CrossRef]
- Cui, J.; Zhang, J.; Zhong, H.; Xu, Y. SPACF: A Secure Privacy-Preserving Authentication Scheme for VANET With Cuckoo Filter. IEEE Trans. Veh. Technol. 2017, 66, 10283–10295. [Google Scholar] [CrossRef]
- Xie, L.; Ding, Y.; Yang, H.; Wang, X. Blockchain-Based Secure and Trustworthy Internet of Things in SDN-Enabled 5G-VANETs. IEEE Access 2019, 7, 56656–56666. [Google Scholar] [CrossRef]
- Alshudukhi, J.S.; Mohammed, B.A.; Al-Mekhlafi, Z.G. An Efficient Conditional Privacy-Preserving Authentication Scheme for the Prevention of Side-Channel Attacks in Vehicular Ad Hoc Networks. IEEE Access 2020, 8, 226624–226636. [Google Scholar] [CrossRef]
- Bayat, M.; Barmshoory, M.; Rahimi, M.; Aref, M.R. A secure authentication scheme for VANETs with batch verification. Wirel. Netw. 2014, 21, 1733–1743. [Google Scholar] [CrossRef]
- Al-shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H.; Abdullah, N.; Hamdi, M.M.; Al-Hiti, A.S. NE-CPPA: A new and efficient conditional privacy-preserving authentication scheme for vehicular ad hoc networks (VANETs). Appl. Math. 2020, 14, 1–10. [Google Scholar]
- Al-Shareeda, M.A.; Anbar, M.; Alazzawi, M.A.; Manickam, S.; Al-Hiti, A.S. LSWBVM: A Lightweight Security Without Using Batch Verification Method Scheme for a Vehicle Ad Hoc Network. IEEE Access 2020, 8, 170507–170518. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An Efficient Identity-Based Conditional Privacy-Preserving Authentication Scheme for Vehicular Ad Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Alshudukhi, J.S.; Al-Mekhlafi, Z.G.; Mohammed, B.A. A Lightweight Authentication With Privacy-Preserving Scheme for Vehicular Ad Hoc Networks Based on Elliptic Curve Cryptography. IEEE Access 2021, 9, 15633–15642. [Google Scholar] [CrossRef]
- Cui, J.; Wang, Y.; Zhang, J.; Xu, Y.; Zhong, H. Full Session Key Agreement Scheme Based on Chaotic Map in Vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2020, 69, 8914–8924. [Google Scholar] [CrossRef]
- Vijayakumar, P.; Azees, M.; Chang, V.; Deborah, J.; Balusamy, B. Computationally efficient privacy preserving authentication and key distribution techniques for vehicular ad hoc networks. Clust. Comput. 2017, 20, 2439–2450. [Google Scholar] [CrossRef]
- Vijayakumar, P.; Azees, M.; Kozlov, S.A.; Rodrigues, J.J.P.C. An Anonymous Batch Authentication and Key Exchange Protocols for 6G Enabled VANETs. IEEE Trans. Intell. Transp. Syst. 2021, 23, 1630–1638. [Google Scholar] [CrossRef]
- Pulagara, S.B.; Alphonse, P. An intelligent and robust conditional privacy preserving authentication and group-key management scheme for vehicular ad hoc networks using elliptic curve cryptosystem. Concurr. Comput. Pract. Exp. 2019, 33, e5153. [Google Scholar] [CrossRef]
- Theodore, S.K.A.; Gandhi, K.R.; Palanisamy, V. A novel lightweight authentication and privacy-preserving protocol for vehicular ad hoc networks. Complex Intell. Syst. 2021, 1–11. [Google Scholar] [CrossRef]
- Ren, Y.; Li, X.; Sun, S.-F.; Yuan, X.; Zhang, X. Privacy-preserving batch verification signature scheme based on blockchain for Vehicular Ad-Hoc Networks. J. Inf. Secur. Appl. 2021, 58, 102698. [Google Scholar] [CrossRef]
- Srinivas, J.; Mishra, D.; Mukhopadhyay, S.; Kumari, S.; Guleria, V. An Authentication Framework for Roaming Service in Global Mobility Networks. Inf. Technol. Control 2019, 48, 129–145. [Google Scholar] [CrossRef] [Green Version]
- Abdalla, M.; Fouque, P.-A.; Pointcheval, D. Password-based authenticated key exchange in the three-party setting. In Proceedings of the International Workshop on Public Key Cryptography, Edinburgh, UK, 4–7 May 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 65–84. [Google Scholar]
- Chatterjee, S.; Roy, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Vasilakos, A.V. Secure Biometric-Based Authentication Scheme Using Chebyshev Chaotic Map for Multi-Server Environment. IEEE Trans. Dependable Secur. Comput. 2016, 15, 824–839. [Google Scholar] [CrossRef]
- Chang, C.-C.; Le, H.-D. A Provably Secure, Efficient, and Flexible Authentication Scheme for Ad hoc Wireless Sensor Networks. IEEE Trans. Wirel. Commun. 2015, 15, 357–366. [Google Scholar] [CrossRef]
- Li, J.; Choo, K.-K.R.; Zhang, W.; Kumari, S.; Rodrigues, J.J.; Khan, M.K.; Hogrefe, D. EPA-CPPA: An efficient, provably-secure and anonymous conditional privacy-preserving authentication scheme for vehicular ad hoc networks. Veh. Commun. 2018, 13, 104–113. [Google Scholar] [CrossRef]







| Notation | Description |
|---|---|
| jth Roadside Units | |
| ith Vehicle | |
| Identity of the driver | |
| Masked Identity of drivers | |
| ith Onboard Unit | |
| Identity of TA | |
| α, β | 160 bits secret keys of TA |
| Password chosen by drivers | |
| T | Current time stamp |
| N | Random Nonce |
| ΔT | Max transmission delay |
| h(.) | One way hash function |
| || | Concatenation |
| ⊕ | Bitwise XOR operation |
| Scheme | Total Computational Overhead | Total Execution Time (ms) |
|---|---|---|
| [17] | 500Th | ≈0.5 |
| [19] | 1Tpm − ECC + 1Tpa − ECC | ≈0.6749 |
| [20] | 2Tpm − ECC + 1Tpa − ECC | ≈1.3467 |
| [21] | 2Tpm − ECC + 1Tpa − ECC + Th | ≈1.3477 |
| [32] | 6 Tpm − ECC + 1 Tpa − ECC + 4 Th | ≈4.0348 |
| [24] | 7 Tpm − ECC + 2 Tpa − ECC + 4 Th | ≈4.7128 |
| [27] | 5 Tpm − ECC + 1 Tpa − ECC + 4 Th | ≈3.3661 |
| [38] | 4Tpm − ECC + 12Th | ≈2.6992 |
| SELWAK | 16 Th + 11 TXOR | ≈0.016 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jan, S.A.; Amin, N.U.; Shuja, J.; Abbas, A.; Maray, M.; Ali, M. SELWAK: A Secure and Efficient Lightweight and Anonymous Authentication and Key Establishment Scheme for IoT Based Vehicular Ad hoc Networks. Sensors 2022, 22, 4019. https://doi.org/10.3390/s22114019
Jan SA, Amin NU, Shuja J, Abbas A, Maray M, Ali M. SELWAK: A Secure and Efficient Lightweight and Anonymous Authentication and Key Establishment Scheme for IoT Based Vehicular Ad hoc Networks. Sensors. 2022; 22(11):4019. https://doi.org/10.3390/s22114019
Chicago/Turabian StyleJan, Sagheer Ahmed, Noor Ul Amin, Junaid Shuja, Assad Abbas, Mohammed Maray, and Mazhar Ali. 2022. "SELWAK: A Secure and Efficient Lightweight and Anonymous Authentication and Key Establishment Scheme for IoT Based Vehicular Ad hoc Networks" Sensors 22, no. 11: 4019. https://doi.org/10.3390/s22114019
APA StyleJan, S. A., Amin, N. U., Shuja, J., Abbas, A., Maray, M., & Ali, M. (2022). SELWAK: A Secure and Efficient Lightweight and Anonymous Authentication and Key Establishment Scheme for IoT Based Vehicular Ad hoc Networks. Sensors, 22(11), 4019. https://doi.org/10.3390/s22114019






