Memory Offloading for Remote Attestation of Multi-Service IoT Devices †
Abstract
:1. Introduction
1.1. Motivation
1.2. Contribution
- The paper proposes a novel RA protocol (ERAMO—Effective Remote Attestation through Memory Offloading) that takes into account both static and dynamic memory regions of an IoT device and checks the integrity of all memory-mapped peripherals.
- This paper successfully implements and evaluates secure memory offloading as a means for enhancing remote attestation. ERAMO has been implemented and evaluated on an ARM Cortex-M33 based microcontroller, leveraging the security features provided by ARM TrustZone.
- The paper expands the remote attestation procedure to attest multi-service devices by using offloading. We provide comprehensive memory analysis details, demonstrating that the flash memory, RAM, boot ROM and peripheral device registers adhere to some patterns.
- The paper evaluates the protocol on various metrics, e.g., transmission time, data authentication time, energy consumption. The conducted experiments confirm the feasibility of ERAMO and demonstrate that offloading technique increases the RA effectiveness in attesting dynamic memory regions.
- The proof-of-concept implementation is significantly enhanced by considering a multi-service device with two sensor nodes. We present comprehensive details about the implementation setting, including the memory layout of the sensor nodes. In addition, we provide extensive analysis of the memory patterns of multi-service devices.
- The evaluation is extended to include additional results for energy consumption measurement which are important and were absent in the previous work.
- Section 3.3 has been added to include the most recent RA protocols for attesting IoT services. These state-of-the-art IoT service RA protocols are particularly relevant to the current paper.
- A detailed background related to ARM TrustZone functioning and working methodologies has been added in Section 4.
- Section 9 provides exhaustive implementation details for multi-sensor devices. In addition, we include the detailed memory analysis of the new approach.
- Section 10.1 provides with energy consumption evaluation. The evaluations prove the lightweight nature of the proposed scheme.
- Section 12 is extended to provide a comprehensive discussion about the memory locking, as a promising mechanism in improving the security and performance of memory offloading approach.
- New figures have been added throughout the manuscript to enhanse the representation of our proposed mechanisms.
1.3. Organization
2. Problem Statement
3. Related Works
3.1. Remote Attestation Overview
3.2. Dynamic Remote Attestation
3.3. Service Attestation in IoT Swarms
3.4. Memory Offloading
3.5. Discussion
4. Background
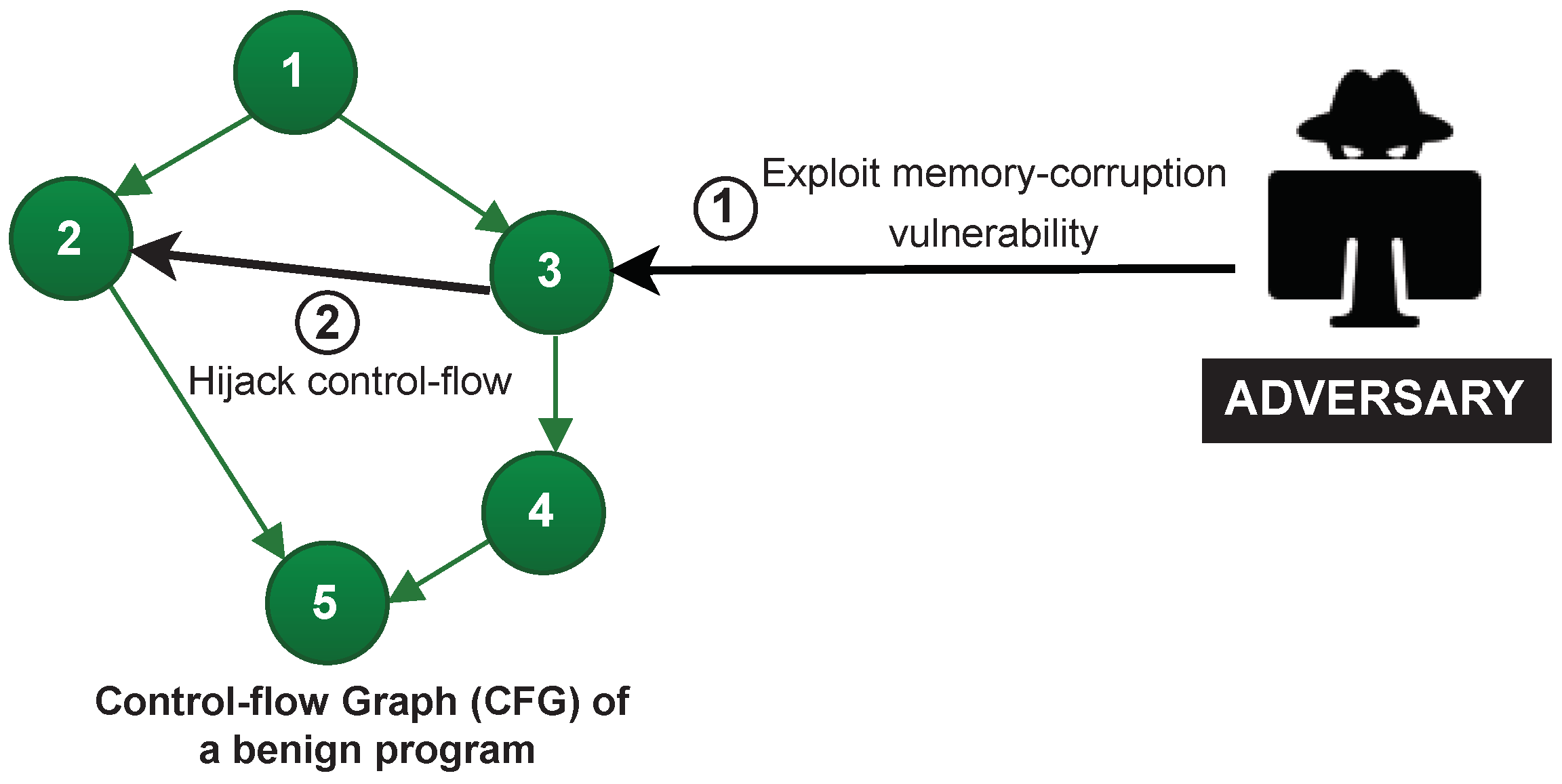
4.1. Runtime Attacks
4.2. Fog Computing
- Sensors and actuators: Sensors and actuator devices are the physical things that produce data. These IoT devices are heterogeneous with different processing capabilities, ranging from very simple devices with minimal resources to more powerful devices that can support wired or wireless protocols, such as BTLE, ZigBee, USB, Ethernet, etc. Many IoT devices can be associated with a single fog node.
- Fog nodes: Fog nodes at the edge are often used for sensor data collection, data standardization, and command/control of sensors and actuators. Fog nodes in the higher layer typically focus on data filtering, compression, aggregation, and turning the data into knowledge.
- Cloud: The traditional backend cloud remains an important part of a fog computing paradigm, performing tasks that are not completed by the fog devices.
4.3. Arm Trustzone
5. System Model
- The Prover (Prv) is an untrusted IoT device. We assume the Prover to be a multi-service device, e.g., a multi-sensor IoT device that provides a set of sensing capabilities using external peripheral. This device can be infected by malware or can be misconfigured as a result of previous attacks. Prover’s memory consists of a set of memory regions as shown in Figure 7. Each memory region can be seen as a set of smaller units called memory blocks.
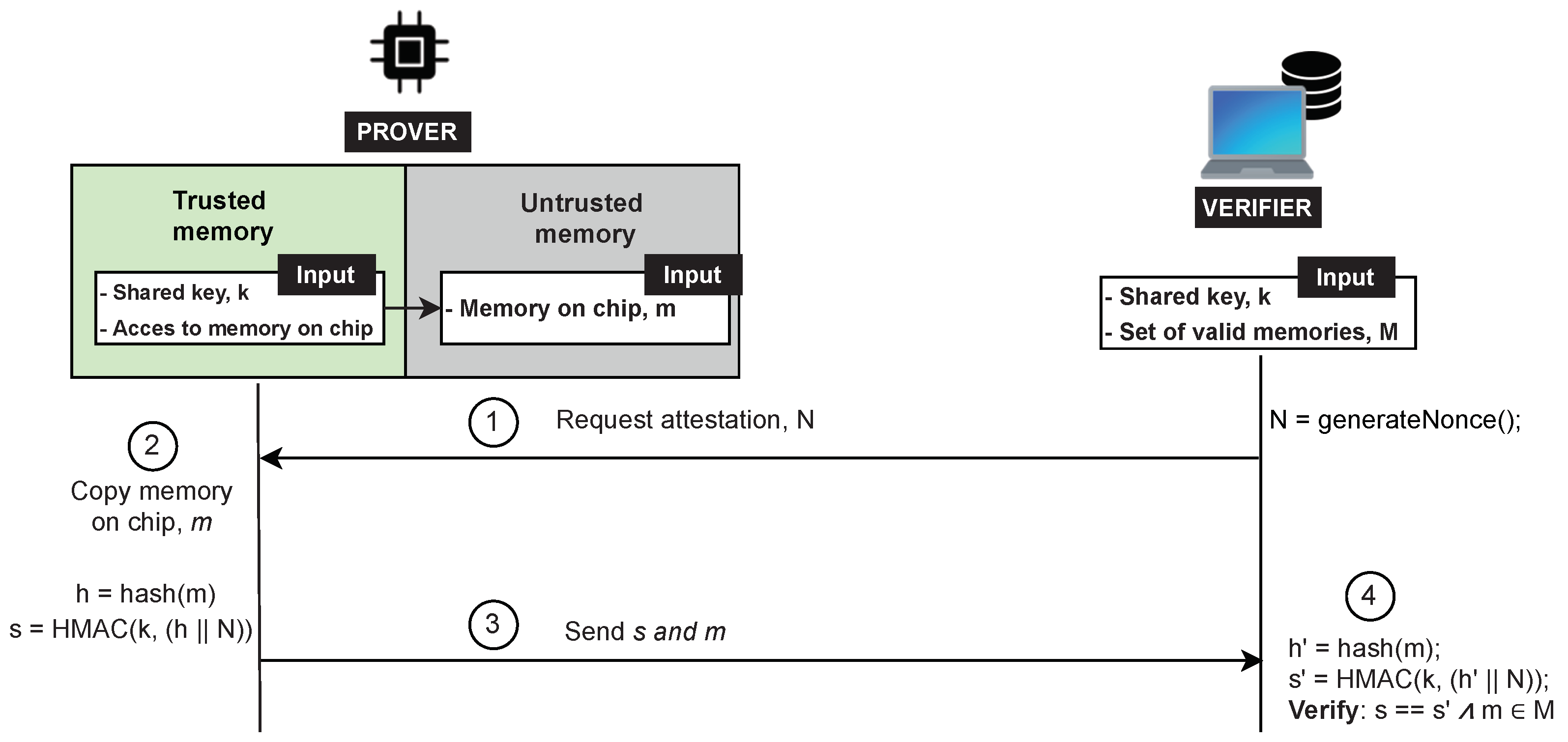
- The Verifier (Vrf) is responsible for checking the integrity of the Prover. In our system model, the Verifier is a fog node resided next to the IoT device. For simplicity, we consider a system with only one layer with fog devices, assuming that a fog node is a powerful device that has all the required resources and computational capabilities to perform complex operations. Alternatively, the Verifier’s task can be distributed in a set of hierarchical fog nodes where some degree of analysis is done by the fog node next to the IoT devices, while the other part of the task is performed by the nodes at the higher layers (as depicted in Figure 3). Besides, the Verifier has the required resources to adopt advanced security and trust techniques (e.g., it is equipped with a Trusted Platform Module (TPM) [51]); thus, it is assumed to be trusted. Additionally, aligned with other RA schemes in the literature, we assume that the Verifier knows in advance the legitimate program binaries and has the ability to detect irregularities in dynamic memory or peripherals of the Prover. The Verifier randomly initiates the attestation on the Prover, after which it can perform memory forensics techniques to determine the Prover’s integrity.
6. Threat Model
6.1. Adversarial Actions
- Software attack: A software adversary compromises the Prover’s program memory by injecting and executing malicious code. Additionally, this adversary can exploit a software vulnerability to compromise data memory, for instance, by modifying variable’s value, corrupting control-flow pointers, data pointers. This can also be exploited to misconfigure internal or external peripheral to cause unintended device behaviour.
- Communication attack: The communication adversary can fully control communications between the Prover and the Verifier by forging, dropping, delaying, eavesdropping the exchanged messages.
- Mobile attack: A mobile adversary is a smart adversary that tries to avoid detection by deleting itself during the attestation time or relocating itself to different memory blocks or memory regions which have already been transmitted to the Verifier.
- Replay attack: An adversary precomputes a valid attestation response and sends this old legitimate response to hide an ongoing attack.
6.2. Attack Capabilities and Limitations
6.3. Defense Capabilities
- Read-Only Memory (ROM). A ROM memory region contains the code of ERAMO protocol. The protocol code resided in this memory region cannot be tampered with by a software adversary.
- Secure key storage. A secure memory region stores the Prover’s keys. Only ERAMO protocol has read permissions in this memory region.
7. Security Requirements
- Integrity. The protocol should provide reliable evidence guaranteeing that the transmitted memory contents correspond to the Prover’s memory at the time of the attestation request.
- Authenticity. The protocol should provide verifiable evidence for the origin of the memory contents transmitted.
- Integrity of communication data. The protocol should ensure that any memory contents transmitted cannot be altered without it being detectable.
- Freshness. The protocol should ensure that any given response to an attestation request can be reliably linked to that request.
8. Eramo: Protocol Proposal
8.1. Setup Phase
8.2. Attestation Phase
8.3. Verification Phase
8.4. Attested Device Memory
Attestation of Multi-Service Devices
9. Proof-of-Concept Implementation
9.1. Sensors
9.1.1. Water Level Sensor
9.1.2. Temperature Sensor—Bosch BME280
9.2. Eramo Protocol
- The trusted component includes the RA procedure and the LPC55S69 hash engine. Additionally, a section of the RAM and flash is allocated to the secure world. The attestation code and key are located in the secure flash, and the key is handled exclusively in secure RAM.
- The non-trusted component includes FreeRTOS, the IoT sensor application tasks, and associated interrupts and peripherals. The remaining RAM, flash, and any unused peripheral are also allocated to the non-secure world.
9.3. Memory Analysis of Sensor Nodes
Attested Memory and Device Integrity
10. Evaluation
10.1. Energy Consumption
10.2. Verification Process: Fog Node’S Perspective
| Listing 1. The Verifier receiving and attesting the offloaded memory. |
 |
| Listing 2. Register white-list for digital temperature sensor. |
 |
11. Eramo Limitations
12. Discussion
- No-Lock: A naive solution to this issue is to let the attestation procedure run concurrently with the devices normal operation without locking. This does not ensure any temporal consistency, leaving the system vulnerable to mobile adversaries.
- All-Lock: All-Lock is the contrary to the No-Lock and avoids the mobile malware. It instead keeps the system temporally consistent throughout the entire process. This method is equivalent to having an uninterruptible attestation procedure.
- Decreasing Lock (Dec-Lock): Like All-Lock, this method detects mobile adversary, while having the benefit of the memory being gradually unlocked.
- Increasing Lock (Inc-Lock): Inc-Lock does provide temporal consistency at the time which the attestation. This will be enough to detect migratory malware, however it does not protect against mobile malware. Malware not located in the first region to be attested could delete itself before the memory is locked and could thereby avoid detection.
- Copy Lock (Cpy-Lock): Cpy-Lock protects against mobile malware but is only viable if the time required to copy is less than time required for the attestation.
- Extended locking: Extended variants All-Lock-Ext and Inc-Lock-Ext can be used instead of their normal counterparts if consistency is needed until the memory has been attested by the verifier. This is done by locking the memory until the attestation is finished, which is useful to prevent TOCTOU vulnerabilities.
- 1.
- The memory area of the main stack is offloaded and unlocked.
- 2.
- The memory area of the main heap (before the allocated task) is offloaded and unlocked.
- 3.
- The memory area of the Idle task and software timers are offloaded and unlocked.
- 4.
- The memory area of the scheduler is offloaded and unlocked.
- 5.
- Start allowing interrupts from the application.
- 6.
- The memory area of the queue for the transmissions task is unlocked (e.g., UART Transmit Queue).
- 7.
- The memory area of the communication transmission task is offloaded and unlocked (e.g., UART Transmit Task).
- 8.
- The communications task is resumed.
- 9.
- The memory area of the temperature sensor task is offloaded and unlocked.
- 10.
- The temperature sensor task is resumed.
13. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
Abbreviations
| CFA | Control Flow Attestation |
| CFI | Control Flow integrity |
| DDoS | Distributed Denial of Service |
| DDS | Data Distribution Service |
| DOP | Data Oriented Programming |
| HMAC | Hash Message Authentication Code |
| IoT | Internet of Things |
| IRQ | Interrupt Request |
| MAC | Message authentication code |
| MITM | Man in the middle |
| NS | Non-Secure |
| NSC | Non-secure callable |
| RA | Remote attestation |
| RAM | Random Access Memory |
| ROM | Read-Only Memory |
| ROP | Return Oriented Programming |
| PoC | Proof of Concept |
| SCR | Secure Configuration Register |
| TEE | Trusted Execution Environment |
| TOCTOU | Time-Of-Check Time-Of-Use |
| TPM | Trusted Platform Module |
References
- STMicroelectronics. 2019. Available online: https://www.st.com/content/st_com/en.html (accessed on 30 April 2022).
- Arduino. 2019. Available online: https://www.arduino.cc/ (accessed on 30 April 2022).
- Dragoni, N.; Giaretta, A.; Mazzara, M. The Internet of Hackable Things. In Proceedings of the 5th the International Conference in Software Engineering for Defence Applications, Rome, Italy, 7–8 June 2018; Ciancarini, P., Litvinov, S., Messina, A., Sillitti, A., Succi, G., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 129–140. [Google Scholar]
- Shacham, H. The Geometry of Innocent Flesh on the Bone: Return-into-Libc without Function Calls (on the X86). In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 2 November–31 October 2007. [Google Scholar]
- Abera, T.; Asokan, N.; Davi, L.; Ekberg, J.; Nyman, T.; Paverd, A.; Sadeghi, A.; Tsudik, G. C-FLAT: Control-FLow ATtestation for Embedded Systems Software. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security (CCS), Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Dessouky, G.; Zeitouni, S.; Nyman, T.; Paverd, A.; Davi, L.; Koeberl, P.; Asokan, N.; Sadeghi, A. LO-FAT: Low-Overhead Control Flow ATtestation in Hardware. In Proceedings of the 54th Annual Design Automation Conference (DAC), Austin, TX, USA, 18–22 June 2017. [Google Scholar]
- Zeitouni, S.; Dessouky, G.; Arias, O.; Sullivan, D.; Ibrahim, A.; Jin, Y.; Sadeghi, A.R. ATRIUM: Runtime attestation resilient under memory attacks. In Proceedings of the 2017 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Irvine, CA, USA, 13–16 November 2017; pp. 384–391. [Google Scholar] [CrossRef]
- Hu, H.; Shinde, S.; Adrian, S.; Chua, Z.L.; Saxena, P.; Liang, Z. Data-Oriented Programming: On the Expressiveness of Non-control Data Attacks. In Proceedings of the IEEE Symposium on Security and Privacy, San Jose, CA, USA, 22–26 May 2016. [Google Scholar]
- Carpent, X.; Rattanavipanon, N.; Tsudik, G. Remote attestation of IoT devices via SMARM: Shuffled measurements against roving malware. In Proceedings of the 2018 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Washington, DC, USA, 30 April–4 May 2018; pp. 9–16. [Google Scholar]
- Carpent, X.; Tsudik, G.; Rattanavipanon, N. ERASMUS: Efficient remote attestation via self-measurement for unattended settings. In Proceedings of the 2018 Design, Automation Test in Europe Conference Exhibition (DATE), Dresden, Germany, 19–23 March 2018. [Google Scholar]
- De Donno, M.; Tange, K.; Dragoni, N. Foundations and Evolution of Modern Computing Paradigms: Cloud, IoT, Edge, and Fog. IEEE Access 2019, 7, 150936–150948. [Google Scholar] [CrossRef]
- Østergaard, J.H.; Dushku, E.; Dragoni, N. ERAMO: Effective Remote Attestation through Memory Offloading. In Proceedings of the 2021 IEEE International Conference on Cyber Security and Resilience (CSR), Rhodes, Greece, 26–28 July 2021; pp. 73–80. [Google Scholar]
- Seshadri, A.; Perrig, A.; van Doorn, L.; Khosla, P. SWATT: SoftWare-based attestation for embedded devices. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 12 May 2004. [Google Scholar]
- Seshadri, A.; Perrig, A.; Luk, M.; Van Doom, L.; Shi, E.; Khosla, P. Pioneer: Verifying code integrity and enforcing untampered code execution on legacy systems. Oper. Syst. Rev. 2005, 39, 1–16. [Google Scholar] [CrossRef]
- Castelluccia, C.; Francillon, A.; Perito, D.; Soriente, C. On the Difficulty of Software-Based Attestation of Embedded Devices. In Proceedings of the 16th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009. [Google Scholar]
- Ankergård, S.F.J.J.; Dushku, E.; Dragoni, N. State-of-the-Art Software-Based Remote Attestation: Opportunities and Open Issues for Internet of Things. Sensors 2021, 21, 1598. [Google Scholar] [CrossRef] [PubMed]
- Kil, C.; Sezer, E.C.; Azab, A.M.; Ning, P.; Zhang, X. Remote attestation to dynamic system properties: Towards providing complete system integrity evidence. In Proceedings of the 2009 IEEE/IFIP International Conference on Dependable Systems Networks, Lisbon, Portugal, 29 June–2 July 2009; pp. 115–124. [Google Scholar]
- Sailer, R.; Zhang, X.; Jaeger, T.; van Doorn, L. Design and Implementation of a TCG-based Integrity Measurement Architecture. In Proceedings of the 13th USENIX Security Symposium, San Diego, CA, USA, 9–13 August 2004. [Google Scholar]
- Eldefrawy, K.; Perito, D.; Tsudik, G. SMART: Secure and Minimal Architecture for (Establishing a Dynamic) Root of Trust. In Proceedings of the Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 5–8 February 2012. [Google Scholar]
- Koeberl, P.; Schulz, S.; Varadharajan, V.; Sadeghi, A. TrustLite: A Security Architecture for Tiny Embedded Devices. In Proceedings of the Ninth European Conference on Computer Systems (EuroSys), Amsterdam, The Netherlands, 14–16 April 2014. [Google Scholar]
- Brasser, F.; El Mahjoub, B.; Sadeghi, A.; Wachsmann, C.; Koeberl, P. TyTAN: Tiny trust anchor for tiny devices. In Proceedings of the 2015 52nd ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 7–11 June 2015. [Google Scholar]
- Asokan, N.; Brasser, F.; Ibrahim, A.; Sadeghi, A.; Schunter, M.; Tsudik, G.; Wachsmann, C. SEDA: Scalable Embedded Device Attestation. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security (CCS), Denver, CO, USA, 12–16 October 2015. [Google Scholar]
- Ambrosin, M.; Conti, M.; Ibrahim, A.; Neven, G.; Sadeghi, A.R.; Schunter, M. SANA: Secure and Scalable Aggregate Network Attestation. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security CCS ’16, Vienna, Austria, 24–28 October 2016. [Google Scholar]
- Rabbani, M.M.; Vliegen, J.; Winderickx, J.; Conti, M.; Mentens, N. SHeLA: Scalable Heterogeneous Layered Attestation. IEEE Internet Things J. 2019, 6, 10240–10250. [Google Scholar] [CrossRef]
- Ambrosin, M.; Conti, M.; Lazzeretti, R.; Rabbani, M.M.; Ranise, S. Toward Secure and Efficient Attestation for Highly Dynamic Swarms: Poster. In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks, Boston, MA, USA, 18–20 July 2017; Association for Computing Machinery: New York, NY, USA, 2017; pp. 281–282. [Google Scholar] [CrossRef]
- Ambrosin, M.; Conti, M.; Lazzeretti, R.; Rabbani, M.M.; Ranise, S. PADS: Practical Attestation for Highly Dynamic Swarm Topologies. In Proceedings of the 2018 International Workshop on Secure Internet of Things (SIoT), Barcelona, Spain, 6 September 2018; pp. 18–27. [Google Scholar]
- Ankergård, S.F.J.J.; Dragoni, N. PERMANENT: Publicly Verifiable Remote Attestation for Internet of Things through Blockchain. In Proceedings of the 14th International Symposium on Foundations & Practice of Security, Paris, France, 7–10 December 2021; Association for Computing Machinery: Paris, France, 2021. [Google Scholar]
- Dessouky, G.; Abera, T.; Ibrahim, A.; Sadeghi, A.R. LiteHAX: Lightweight Hardware-Assisted Attestation of Program Execution. In Proceedings of the International Conference on Computer-Aided Design, San Diego, CA, USA, 5–8 November 2018. [Google Scholar]
- Conti, M.; Dushku, E.; Mancini, L.V. Distributed Services Attestation in IoT. In From Database to Cyber Security; Samarati, P., Ray, I., Ray, I., Eds.; Lecture Notes in Computer Science; Springer International Publishing: Cham, Switzerland, 2018; pp. 261–273. [Google Scholar]
- Abera, T.; Bahmani, R.; Brasser, F.; Ibrahim, A.; Sadeghi, A.; Schunter, M. DIAT: Data Integrity Attestation for Resilient Collaboration of Autonomous System. In Proceedings of the 26th Annual Network & Distributed System Security Symposium (NDSS), San Diego, CA, USA, 24–27 February 2019. [Google Scholar]
- Conti, M.; Dushku, E.; Mancini, L.V. RADIS: Remote Attestation of Distributed IoT Services. In Proceedings of the 6th IEEE International Conference on Software Defined Systems (SDS 2019), Rome, Italy, 10–13 June 2019; pp. 25–32. [Google Scholar]
- Rabbani, M.M.; Dushku, E.; Vliegen, J.; Braeken, A.; Dragoni, N.; Mentens, N. RESERVE: Remote Attestation of Intermittent IoT Devices. In Proceedings of the 19th ACM Conference on Embedded Networked Sensor Systems, Coimbra, Portugal, 15–17 November 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 578–580. [Google Scholar]
- Dushku, E.; Rabbani, M.M.; Conti, M.; Mancini, L.V.; Ranise, S. SARA: Secure Asynchronous Remote Attestation for IoT Systems. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3123–3136. [Google Scholar] [CrossRef]
- Halldórsson, R.M.; Dushku, E.; Dragoni, N. ARCADIS: Asynchronous Remote Control-Flow Attestation of Distributed IoT Services. IEEE Access 2021, 9, 144880–144894. [Google Scholar] [CrossRef]
- Chun, B.; Ihm, S.; Maniatis, P.; Naik, M.; Patti, A. CloneCloud: Elastic Execution between Mobile Device and Cloud. European Conference on Computer Systems. In Proceedings of the Sixth European conference on Computer systems (EuroSys ’11), Salzburg, Austria, 10–13 April 2011. [Google Scholar]
- Conti, M.; Dushku, E.; Mancini, L.V.; Rabbani, M.; Ranise, S. Remote Attestation as a Service for IoT. In Proceedings of the 2019 Sixth International Conference on Internet of Things: Systems, Management and Security, Granada, Spain, 22–25 October 2019. [Google Scholar]
- The Volatility Foundation. 2021. Available online: https://www.volatilityfoundation.org/ (accessed on 30 April 2022).
- Pinto, S.; Santos, N. Demystifying Arm TrustZone: A Comprehensive Survey. ACM Comput. Surv. 2019, 51, 1–36. [Google Scholar] [CrossRef]
- Checkoway, S.; Davi, L.; Dmitrienko, A.; Sadeghi, A.R.; Shacham, H.; Winandy, M. Return-oriented programming without returns. In Proceedings of the 17th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 4–8 October 2010; pp. 559–572. [Google Scholar]
- Bletsch, T.; Jiang, X.; Freeh, V.W.; Liang, Z. Jump-oriented programming: A new class of code-reuse attack. In Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security, Hong Kong, China, 22–24 March 2011; pp. 30–40. [Google Scholar]
- Vaquero, L.M.; Rodero-Merino, L. Finding Your Way in the Fog: Towards a Comprehensive Definition of Fog Computing. SIGCOMM Comput. Commun. Rev. 2014, 44, 27–32. [Google Scholar] [CrossRef]
- OpenFog Consortium Architecture Working Group. OpenFog Reference Architecture for Fog Computing. 2017. Available online: https://www.iiconsortium.org/pdf/OpenFog_Reference_Architecture_2_09_17.pdf (accessed on 24 May 2022).
- Chiang, M.; Zhang, T. Fog and IoT: An Overview of Research Opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Azure IoT Edge Documentation. 2019. Available online: https://docs.microsoft.com/en-us/azure/iot-edge/ (accessed on 24 May 2022).
- AWS IoT Greengrass. 2019. Available online: https://aws.amazon.com/greengrass/ (accessed on 24 May 2022).
- EdgeX. 2019. Available online: https://www.edgexfoundry.org/ (accessed on 24 May 2022).
- Arm TrustZone Technology. 2019. Available online: https://developer.arm.com/ip-products/security-ip/trustzone/trustzone-for-cortex-m (accessed on 30 April 2022).
- Ngabonziza, B.; Martin, D.; Bailey, A.; Cho, H.; Martin, S. TrustZone Explained: Architectural Features and Use Cases. In Proceedings of the 2016 IEEE 2nd International Conference on Collaboration and Internet Computing (CIC), Pittsburgh, PA, USA, 1–3 November 2016; pp. 445–451. [Google Scholar]
- Cerdeira, D.; Santos, N.; Fonseca, P.; Pinto, S. SoK: Understanding the Prevailing Security Vulnerabilities in TrustZone-assisted TEE Systems. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020. [Google Scholar]
- Roth, T. TrustZone-M(eh): Breaking ARMv8-M’s Security. Available online: https://media.ccc.de/v/36c3-10859-trustzone-m_eh_breaking_armv8-m_s_security (accessed on 24 May 2022).
- Arthur, W.; Challener, D. A Practical Guide to TPM 2.0: Using the Trusted Platform Module in the New Age of Security; Springer: Cham, Switzerland, 2015. [Google Scholar]
- Abera, T.; Asokan, N.; Davi, L.; Koushanfar, F.; Paverd, A.; Sadeghi, A.R.; Tsudik, G. Invited—Things, Trouble, Trust: On Building Trust in IoT Systems. In Proceedings of the 53rd Annual Design Automation Conference, Austin, TX, USA, 5–9 June 2016; p. 121. [Google Scholar]
- Ambrosin, M.; Conti, M.; Lazzeretti, R.; Rabbani, M.; Ranise, S. Collective Remote Attestation at the Internet of Things Scale: State-of-the-art and Future Challenges. IEEE Commun. Surv. Tutor. 2020, 22, 2447–2461. [Google Scholar] [CrossRef]
- BME280—Data Sheet, Bosch Sensortec. 2018. Available online: https://ae-bst.resource.bosch.com/media/_tech/media/datasheets/BST-BME280-DS002.pdf (accessed on 30 April 2022).
- Stevens, M.; Bursztein, E.; Karpman, P.; Albertini, A.; Markov, Y. The First Collision for Full SHA-1. In Advances in Cryptology; Springer International Publishing: Cham, Switzerland, 2017; pp. 570–596. [Google Scholar]
- Leurent, G.; Peyrin, T. SHA-1 is a Shambles: First Chosen-Prefix Collision on SHA-1 and Application to the PGP Web of Trust. In Proceedings of the 29th USENIX Security Symposium (USENIX Security 20), Boston, MA, USA, 12–14 August 2020. [Google Scholar]
- UM11158, LPCXpresso55S69/55S28 User Manual. 2019. Available online: https://www.nxp.com/webapp/Download?colCode=UM10914 (accessed on 29 April 2022).
- Ibrahim, A.; Sadeghi, A.; Zeitouni, S. SeED: SeCure Non-Interactive Attestation for EMbedded DEvices. In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), Boston, MA, USA, 18–20 July 2017; pp. 64–74. [Google Scholar]
- OP-TEE. About OP-TEE. 2020. Available online: https://optee.readthedocs.io/en/latest/general/about.html (accessed on 24 May 2022).
- Eldefrawy, K.; Carpent, X.; Tsudik, G.; Rattanavipanon, N. Temporal Consistency of Integrity-Ensuring Computations and Applications to Embedded Systems Security. In Proceedings of the 2018 on Asia Conference on Computer and Communications Security (ASIACCS), Incheon, Korea, 4 June 2018. [Google Scholar]














| Scheme | Static Memory | RAM | Peripheral | Verification | Type | Attestation |
|---|---|---|---|---|---|---|
| SWATT [13], Pioneer [14] | ● | ○ | ○ | Program checksum | One-to-one | On-demand |
| SMART [19], TrustLite [20], TyTan [21] | ● | ○ | ○ | Program checksum | One-to-one | On-demand |
| C-FLAT [5], LO-FAT [6] | ○ | ◐ | ○ | Control flow integrity (CFI) | One-to-one | On-demand |
| ATRIUM [7], LiteHAX [28] | ● | ◐ | ○ | Program checksum & CFI | One-to-one | On-demand |
| SMARM [9] | ● | ○ | ○ | Program checksum & Shuffled Measurements | One-to-one | On-demand |
| ERASMUS [10] | ● | ○ | ○ | Program checksum | One-to-one | Self-initiated |
| SEDA [22], SANA [23], SARA [33] | ● | ○ | ○ | Program checksum | One-to-many | On-demand |
| DIAT [30] | ● | ◐ | ○ | Program checksum & CFI | Many-to-many | On-demand |
| RADIS [31], ARCADIS [34] | ○ | ◐ | ○ | Program checksum & CFI | One-to-many | On-demand |
| CloneCloud [35] | ○ | ● | ○ | ○ | One-to-one | ○ |
| ERAMO | ● | ● | ◐ | Memory offloading | One-to-one | On-demand |
| Communication Rate [bytes/second] | Voltage over Shunt Resistor [mV] | Power [mW] | Excess Power [mW] | Duration of ERAMO Offloading [s] | Excess Energy [mJ] | |
|---|---|---|---|---|---|---|
| Normal operation (no offloading) | NAN | 679 | 190 | NAN | NAN | NAN |
| Offloading using ERAMO | 460,800 | 711 | 208 | 18 | 23.3 | 419 |
| Offloading using ERAMO | 115,200 | 708 | 206 | 16 | 89.0 | 1424 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dushku, E.; Østergaard, J.H.; Dragoni, N. Memory Offloading for Remote Attestation of Multi-Service IoT Devices. Sensors 2022, 22, 4340. https://doi.org/10.3390/s22124340
Dushku E, Østergaard JH, Dragoni N. Memory Offloading for Remote Attestation of Multi-Service IoT Devices. Sensors. 2022; 22(12):4340. https://doi.org/10.3390/s22124340
Chicago/Turabian StyleDushku, Edlira, Jeppe Hagelskjær Østergaard, and Nicola Dragoni. 2022. "Memory Offloading for Remote Attestation of Multi-Service IoT Devices" Sensors 22, no. 12: 4340. https://doi.org/10.3390/s22124340






