1. Introduction
Many industries are adopting Internet of Things (IoT) technology to automate different processes, to avoid manual labour, to perform predictive maintenance, or to speed up development. Recent trends show no sign of slowing down the process of utilizing IoT technology. The goal of IoT is to connect billions of constrained devices to the Internet. As the number of devices participating in the network increases, their competition to access the communication channel and consequently the channel contention increases as well. This may result in data loss.
One of the latest WiFi protocols published by the WiFi Alliance primarily for IoT networks is IEEE 802.11ah, which is also known as WiFi HaLow. It has multiple novel features compared to the legacy IEEE 802.11 protocol. WiFi Certified 6 provides improved power saving to support IoT capabilities in some applications; however, it lacks range and penetration. WiFi 4 offers high data rates for applications such as video streaming and internet surfing at the cost of high battery consumption. Therefore, the WiFi Alliance has introduced the IEEE 802.11ah for the IoT market [
1].
IEEE 802.11ah operates in the sub-1 GHz frequency spectrum band, which allows a communication range of up to 1 km with high obstacle penetration [
2]. The association identifier feature allows a single access point (AP) to be associated with 8192 stations, which aims at high scalability [
3].
1.1. Restricted Access Window in IEEE802.11ah
Contention between stations in IEEE 802.11ah can be reduced using Restricted Access Windows (RAW), which provides a deterministic and stochastic medium access control mechanism as stated in [
3]. As the name suggests, RAW provides a time window, during which channel access is restricted to certain stations only. During RAW, stations use an Enhanced Distributed Channel Access/Distributed Coordination Function (EDCA/DCF) to access the channel [
3]. DCF uses Carrier-Sense Multiple Access with Collision Avoidance (CSMA/CA) with Binary Exponential Backoff (BEB) algorithm. With EDCA, traffic is prioritized depending on the traffic in four different access categories [
4]. Information about the RAW organization is forwarded by AP using the RAW Parameter Set (RPS). The RPS is communicated during each beacon transmission by the AP and can be dynamically adjusted. Each RAW group is split into RAW slots and stations of a RAW group are evenly distributed over the RAW slots using Round Robin [
5]. The duration of a slot is determined using Equation (
1) [
5]. The minimal duration of a slot is 500 μs when
is equal to 0; the maximal duration is 246.14 ms when slot format is set to 1 and 31.1 ms when slot format is set to 0. All slots within a group have the same duration. A visual representation of the RAW assignment can be found in
Figure 1. Stations can compete for medium access only during their RAW slot duration. Cross-Slot Boundary (CSB) is a setting that allows stations to continue an ongoing transmissions even if the RAW slot duration is exceeded if enabled. RAW can be restricted to paged traffic indication map stations only. In this case, only the paged stations will compete for the medium access in each RAW slot. Otherwise, all stations can compete.
1.2. The Problem of Selfish Behavior in IEEE802.11ah
The selfish behavior of stations is a serious threat to the network’s quality of service in any wireless network, especially if there is no mitigation mechanism to deal with it. This is a problem that can occur in any type of network and has been greatly researched in IEEE 802.11 networks. The selfish behavior of a station can occur in different ways, which according to [
6] are as follows:
Scramble Clear To Send (CTS)—upon hearing Request To Send (RTS) from one station to the access point, the selfish station sends a message that will collide with the CTS response, causing the sender to backoff;
Scramble Acknowledge (ACK) and DATA frames—same as above but for ACK or DATA frames;
Reduced backoff time—stations draw the random backoff value from a set with smaller minimal value;
Transmit before DCF InterFrame Spacing (DIFS)—stations begin transmission before the minimum time to transmit after the channel is idle has passed;
Increase Network Allocation Vector (NAV) value in RTS or DATA frames to prevent stations in range from competing during this time.
Reducing the backoff time is a widely used scheme by selfish stations. This type of selfish behavior is achieved in the form of modifying the set from which the random backoff value is drawn after the channel is sensed to be busy. In IEEE 802.11ah and IEEE 802.11, the Contention Window (CW) is determined using the BEB algorithm. When a station using CSMA senses that the channel is busy for the first time, it draws a random CW value from the set [0, CWmin]. After CW idle time slots are detected, a transmission is attempted. If it fails, the upper bound of the set is doubled and the procedure is repeated. The upper bound can reach CWmax, which is usually 1023 time slots. Upon a successful transmission, the upper bound is reset to CWmin. However, selfish stations have their lower bound set to any value, which can even be lower than the default CWmin. This means that selfish stations in the network wait less before accessing the channel again and therefore have a higher chance of accessing the channel.
The fact that selfish stations have a higher chance of accessing the channel and therefore higher throughput comes at the cost of degrading the overall network quality. Therefore, it is essential to understand how and to what extent selfish stations will affect network performance in IEEE802.11ah, how selfish nodes can be detected and how their behavior can be combated to optimize overall network quality of service. To this end, our contribution can be summarized as follows:
A thorough analysis of the inherent fairness of the IEEE 802.11ah protocol;
Investigating applicability of two existing selfish behavior detection algorithms, i.e., Principle-agent method [
7] and Deviation detection [
8] mechanism designed for IEEE 802.11, to the IEEE 802.11ah protocol;
Proposing a new definition of ’selfish behavior’ specifically for IEEE 802.11ah as well as an algorithm to detect stations exhibiting selfish behavior;
Proposing a mitigation algorithm called Selfish Stations Quarantine Punishment Algorithm (SSQPA) to combat selfish behavior by utilizing an award and punishment concept.
3. Simulation Set Up
The simulator used for this paper is NS-3 [
33] with the IEEE 8022.11ah extension developed in [
34]. The parameters used in the simulation can be found in
Table 1. We consider a network of
N stations ∈ {30, 50, 100}, divided into
k RAW slots ∈ {1, 2, 4}. The stations are competing for the channel access to a single AP. We consider three different network traffic scenarios, i.e., UDP, TCP and TCP IP camera, each of which having different traffic intensity. In all scenarios, the stations constantly have data packets to send to the AP. The three scenarios we consider are as follows:
A UDP communication, in which stations generate UDP packets every 0.1 s and send a packet to the AP when they obtain access to the channel.
A TCP communication, in which the stations have TCP packets every 0.2 s. Stations send packets to the AP to check whether there is a firmware update. Note that the down-link communication of the TCP firmware from the AP to the stations is disabled so that only the up-link communication is monitored.
A TCP communication, in which the stations are IP cameras and compete for channel access to stream a video footage for a short period of time.
The stations of the network are either honest or selfish. Honest stations obey the MAC layer and use the default CWmin of 15 units of slot time. Selfish stations are modified and their CWmin value is set to two units of slot time.
4. Inherent Fairness of IEEE 802.11ah and Effect of Selfish Behavior
In this section, we analyze fairness of IEEE 802.11ah without introducing any selfish stations. To calculate fairness, we use the Jain’s fairness function [
35], which can be found in Equation (
2), where
xi is the number of data transmission of station
i and
N is the number of stations. The fairness is a value between 0 and 1, where a higher value indicates a better fairness. Value 1 equals to 100% fairness, which means all stations have the same channel access and transmit the same number of packets.
As it can be seen in
Figure 2 (left), the fairness of the network decreases with the increase in stations and increases with the increase in RAW slots. The fluctuations in the fairness are due to the fact that the larger the number of stations, the higher the contention. On the other hand, the higher the number of RAW slots, the lower the number of stations per slot; hence, contention decreases. However, if the network has more than 500 stations, it becomes very unfair and the difference between the three slot variations is not significant. Therefore, for the rest of our analysis, we only consider a maximum of 50 stations in the network. For the cases of 30 and 50 stations, the difference between the fairness of the three slot variations is not as noticeable for the TCP scenarios as for UDP. This is due to the different nature of the protocols. TCP is slower and, therefore, in general, there is less contention in the network between the stations than UDP and, hence, lower fairness variations.
The throughput for the different scenarios can be found in
Figure 2 (right). It can be seen that throughput decreases with the increase in the number of stations, following a similar pattern to the one of the fairness. However, the number of RAW slots does not improve the throughput and only improves fairness. The different numbers of RAW slots result in almost the same throughput values; therefore, the lines of the graph are overlapping.
Finally, we analyze packet loss of the network. The source of packet loss in the network is only one and it is the limited transmission queue at the stations. Because the network always has packets to send, which are generated in every 0.1 s for UDP and 0.2 s for TCP, if a new packet is generated while the queue of the station is full, the packet will be dropped. Both TCP scenarios have 0 packet loss due to TCP’s higher reliability, lower data rate and lower packet generation interval; therefore, we do not illustrate them. As it can be seen in
Figure 3, the packet loss for UDP is increasing with a higher number of stations. Furthermore, because packet loss is directly related to throughput,
Figure 3 is almost the reverse of the graph for UDP throughput (
Figure 2). Since packet loss is due to queue limitations, a higher data rate leads to a lower packet loss and a lower data rate leads to a higher packet loss.
The next step of our analysis is to introduce different numbers of selfish stations to study their effects on the network fairness.
Figure 4 shows the network fairness for different percentages of selfish stations. As it can be seen, the fairness with any percentage of selfish stations is always lower than the fairness with no selfish stations. Furthermore, in UDP, the number of RAW slots does not play a significant role. Another interesting observation is that, for UDP and TCP IP camera with 30% selfish stations, the fairness is the lowest compared to the cases with higher percentages of selfish stations. The reason behind this is that when the selfish stations are not dominating, they only compete with the honest stations for the channel access, but when the share of the selfish stations increases, they begin to compete with each other. A conclusion that can be drawn here is that compared to TCP, UDP suffers more from the presence of selfish stations in the network. This can be explained by the different nature of the protocols and the lower speed and contention in TCP.
To better illustrate why fairness of the network decreases when more selfish stations are added to the network, the share of the channel access is visualized in
Figure 5, which shows the share of packets received at the AP from 50 stations. In a perfect scenario (i.e., 100% fair network) the share of each station must be 2%. As it can be seen, when no selfish stations are introduced, the share is relatively similar, although it is still not the expected 2%. The smallest value is 1.2% and the largest value is 6.6%. This shows that even without introducing selfish stations, the IEEE 802.11ah network is not entirely fair. However, in the case of having 40% selfish stations, the network share changes noticeably. The network share of some stations drops to only 0.1%, whereas others increase to 7.9%. It can be clearly seen that some stations are more dominant than others.
So far, we have seen how fairness and network share change with the introduction of selfish stations. Next, it is important to analyze the network quality of service in terms of throughput and packet loss of the honest and selfish stations in the presence of selfish station. As it can be seen in
Figure 6, when the selfish stations are fewer than 20% of the network, the throughput of the selfish stations is lower than the throughput of the honest stations. This means that selfish stations do not gain any advantage if they are not more than 20% of network’s stations. The reason behind this is the inherent unfairness of IEEE 802.11ah, which we have shown in
Figure 2. For the selfish stations to gain advantages, they must not be selfish individually but as a group (i.e., together with other selfish stations). Looking at
Figure 6, 30% of the stations should be selfish to gain significant advantage. In all three scenarios, when selfish stations are 30%, they have the highest throughput, but the advantage is reduced as their number increases further. Finally, the overall network throughput is slightly decreasing for all scenarios, due to the lowered throughput of honest stations.
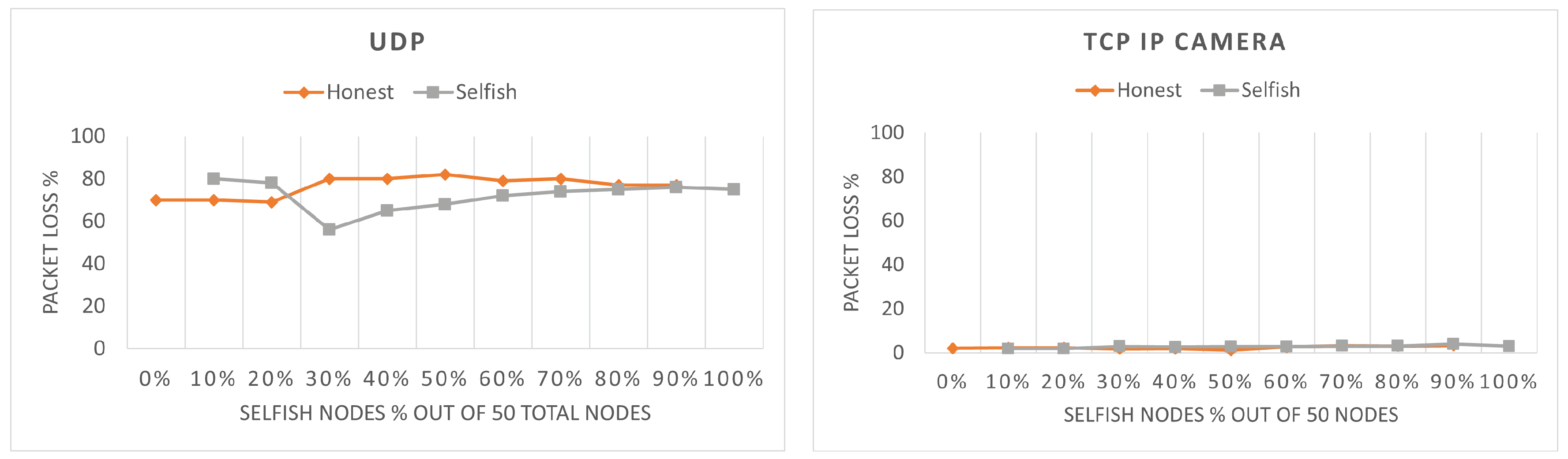
The packets loss can be found in
Figure 7. Note that for the TCP firmware scenario, no packet loss was observed; therefore, it is not visualized. As it can be seen, the packet loss is higher for UDP than TCP IP camera, because the packet generation period of UDP is lower than TCP IP camera due to the higher data rate of UDP. Moreover, the honest stations have higher packet loss, because they have a smaller possibility to transmit their packets and, hence, their queue fills faster and empties slower. For TCP IP camera, selfish stations have higher packet loss; however, both selfish and honest stations have relatively low packet loss and the difference between the two is not significant (i.e., 1–2%). The values of the packet loss are dependent on the throughput. A higher throughput will result in a lower packet loss and vice versa. Therefore, packet loss figures are the reverse of throughput figures. This is most clearly noticed for UDP with 30% selfish stations. As it can be seen, the throughput of the selfish stations is lower than the honest stations up to 30% and they also have higher packet loss. At the point of 30%, selfish stations gain higher throughput and their packet loss drops below the packet loss of honest stations.
5. Detection of Selfish Behavior
In this section, we analyze two selfish behavior detection algorithms from the literature. After analyzing their applicability to IEEE 802.11ah, we propose a new detection algorithm tailored to IEEE 802.11ah. Through our extensive evaluations with these three algorithms, we determine which one fits the IEEE 802.11ah best.
5.1. Principal-Agent Method
The principal-agent method [
7] was proposed for IEEE 802.11 wireless ad hoc networks. Due to lack of a central station such as an AP in ad hoc networks, the authors introduced a so called principal station to the network to identify whether a stations is selfish. All other non-principal stations in the network are referred to as agents. The communication in the network works as follows: (i) a transmitting agent sends a RTS to the receiving agent; (ii) the receiving agent sends a query to the Principal to ask whether the sender is selfish; (iii) the Principal computes the utility function (described later) and sends the outcome to the receiving agent; (iv) if the Principal determines that the sender is selfish, the receiver does not respond to the sender; (v) if the Principal determines that the sender is honest, the receiver replies with CTS.
One should note that there are differences between ad hoc networks and star based networks such as IEEE 802.11ah. Firstly, in IEEE 802.11ah, RTS and CTS are disabled to reduce the communication overhead. Secondly, in IEEE 802.11ah there already exists a station that can monitor the entire network and that is the AP. Therefore, some modifications need to be made to apply the algorithm to IEEE 802.11ah. The first and the most obvious one is combining the receiving station and the principal station because in case of IEEE 802.11ah, they both are AP. The second required change is that all packets are received from a station, even if it is detected as selfish, due to the lack of RTS and CTS packets. Modified communication appears as follows: (i) a transmitting agent sends a packet to the AP, (ii) the AP computes the utility function, and (iii) if the AP determines that the sender is selfish, AP marks the sender as such.
The utility function of the principal-agent method is a function that determines whether a station is selfish. If the outcome of the utilization function is less than zero, then the station is selfish and it will spend less time being idle, which results in higher utilization. For the fairness function, the authors used Jain’s fairness function [
35].
5.2. Deviation Detection Mechanism
The second detection algorithm studied in this paper is the distributed deviation detection mechanism [
8], which again is originally proposed for adhoc networks and we need to modify it to work for IEEE 802.11ah. In the original version, every station in the network calculates the mean and standard deviation of the number of packets sent by all stations. Then, whenever a station sends a RTS to a receiver, all stations check the number of total packets sent by the sender. If the total packets sent are greater than the sum of the mean and standard deviation, then the station is considered to be selfish and the receiving station will not respond with CTS.
Our modification of deviation detection from adhoc networks to be applicable to IEEE 802.11ah is straightforward. Instead of all stations computing the statistics of all other stations, only the AP performs this. Furthermore, again because RTS and CTS are disabled in IEEE 802.11ah, the station will only be marked as selfish so that the mitigation algorithm described later in
Section 6 can handle it. The drawback of this mechanism is that in cases where selfish stations are dominating the network, the values of the mean and standard deviation are going to be primarily based on the selfish stations and only extreme cases of selfish behavior can be detected.
5.3. Inherent Selfish Stations Detector (ISSD)
In this section, we present our new selfish behavior detection algorithm, called Inherent selfish stations detector (ISSD), tailored specifically towards IEEE 802.11ah. We have designed this algorithm considering the fact that IEEE 802.11ah is unfair by design, as we have illustrated in
Figure 2. Therefore, we believe that a selfish behavior detection algorithm for IEEE 802.11ah should not only be able to detect the introduced selfish stations but also the inherent selfish stations. This can be achieved by studying the distribution of the network share without the presence of selfish stations.
As it can be seen from
Figure 8, even without the presence of selfish stations, most of the stations fall in the lower end of the network share and a small number of stations is having a greater share. Based on this distribution, a threshold value can be introduced for each of the three applications that will detect stations that are behaving as selfish, even though they are not modified to be so. The thresholds have such values that only a few stations that have the greater share of the network will have a greater value. We set for UDP the threshold as 3.1, TCP firmware as 3.34 and TCP IP camera as 3.5. The formal definition of an inherent selfish station, which is also the function used for detection of selfish stations by the algorithm, is station_share > threshold.
The threshold is selected based on the application of the network. Looking at the distributions, UDP has 12 selfish stations, TCP firmware has 15 and TCP IP camera has 7. Therefore, a selfish stations is now a station that has been introduced as selfish or is inherently selfish. Note that the distributions are the average of 10 simulation rounds. When applying the algorithm in the simulations, the number of inherent selfish stations may vary based on the random seed used in the simulation.
5.4. Performance Evaluation
To evaluate and compare the previous three detection algorithms, we perform the simulations to be described in this section. The simulation parameters are the same as those described in
Section 3. The three detection algorithms described were evaluated for a network of 50 stations and 2 RAW slots. Furthermore, they were also tested for the three different applications: UDP, TCP firmware and TCP IP camera.
5.4.1. Principal-Agent Method
The results of the experiments with the principal-agent method can be found in
Table 2,
Table 3 and
Table 4. As it can be seen, even though all selfish stations are detected successfully, the method detects almost all of the honest stations in the network as selfish as well. This is a very high false-positive rate, which makes the method unusable for IEEE 802.11ah. One of our observations that explains the results is that the average network fairness used in fairness function of this method (reader is referred to [
7] for more details about the function) is almost always greater than the network fairness. Furthermore, the current idle time and the average idle time have very small difference and compared to the total transmission time they are insignificant. Therefore the outcome of their utility function is very small and does not play a role in the final outcome because it is always smaller than the difference between the fairness functions. However, the simulated traffic in our study is very intense; hence, the network has very high utilization. The high utilization causes the utilization function to have a very small value compared to the fairness function.
5.4.2. Deviation Detection Mechanism
The results of the experiment with the Deviation detection mechanism can be found in
Table 5,
Table 6 and
Table 7. As it can be seen, the results are better than the ones from the principal-agent method; however, the false-positive and false-negative results are still high. Especially for the case of 20% selfish stations, for UDP and TCP IP camera, only 10% of the selfish stations were detected. However, these results do not mean that the detection algorithm is not working well but rather that the network itself is unfair. As we have illustrated earlier in
Figure 5, even without the presence of selfish stations, some stations have as much as five times higher channel share than others. Therefore, it is expected that a good selfish behavior detection algorithm can detect the stations that are inherently selfish. Furthermore, the rate of false negative detected stations increases as the number of selfish stations increases. This behavior is expected, because the selfish stations are dominating the network and being selfish becomes the new norm.
5.4.3. Inherent Selfish Stations Detector
The results of the experiments with our ISSD algorithm can be found in
Table 8,
Table 9 and
Table 10. As it can be seen, the algorithm performs well. When there are no selfish stations, it detects all of the inherent selfish station successfully. Furthermore, because we consider both inherent selfish stations and added selfish stations in detection, the algorithm achieves lower false positive and false negative rates. With the introduction of selfish station, some of the inherent selfish stations may be dominated by the introduced selfish stations. In that case, the inherent selfish stations will no longer be detected as selfish, because they will obtain a low network share; thus, the false negative percentage will increase as it happens in the cases with 10% and 20% selfish stations. Furthermore, because the introduced selfish stations are random, some may overlap with the inherent selfish stations. In the tables with the results, the inherent selfish stations are written in parenthesis on the seconds row of the tables. Overlapping selfish stations are extracted from the number of introduced selfish stations. For example, for UDP with 10% selfish stations, there are ten inherent selfish stations, and five introduced ones. However, one of the introduced stations overlaps with inherent stations, so in the column under 10%, we only see a four on the second row.
5.5. Discussion and Comparison
Due to the high false positive and false negative rates of the principle-agent method, we will not continue with the algorithm. Due to different definitions of selfish behavior considered by the deviation detection and ISSD algorithms, we perform a new set of experiments in which not only the introduced selfish stations but also the inherent selfish stations are considered for the results of the deviation detection algorithm. This will allow us to perform a fair comparison between the two detection algorithms. Results of this comparison in terms of true positives can be found in
Figure 9 (left). The true positives are calculated by taking the percentage of correct selfish stations detected from both inherent and introduced selfish stations. As it can be seen, ISSD performs significantly better when no additional selfish stations are introduced and it is slightly better for the remaining cases.
A comparison of the false positive rates can be found in
Figure 9 (right). As it can be seen, both algorithms follow a similar pattern for the false positive; however, in most cases ISSD has a lower false positive.
The last metric considered in the comparison is the false negative rate, illustrated in
Figure 10. A lower false negative rate means that fewer stations were not detected as selfish although they were. Therefore, the better algorithm is the one with lower value. As it can be seen, ISSD performs better in this respect.
Thus far, we have seen based on the graphs that ISSD performs better compared to the deviation detection algorithm. The last comparison is related to the F1 score, which is calculated using Equation (
3). The outcome of the equation varies between 0 and 1 and a higher value means a better score.
The F1 scores for both algorithm for the three applications are shown in
Table 11. As it can be seen, ISSD has the highest score in all applications. This confirms that indeed, the inherent selfish station detector outperforms deviation detections for the case of IEEE 802.11ah.
The advantages of ISSD combined with the introduction of our “inherent selfish behavior in IEEE 802.11ah” concept allows the following for ISSD: (i) be able to detect selfish stations with higher accuracy, especially when the selfish stations are lower percentages, and (ii) have lower numbers of false positive and false negative outcomes expected due to the refined definition of selfish stations. The drawback of the algorithms is that it is harder to apply it in real scenarios. The traffic of the network is assumed to have similar deterministic pattern, which may not always be the case. Furthermore, the distribution of the network must be obtained first before the threshold can be determined, because the same threshold cannot be used for different applications.
7. Conclusions
In this paper, we studied the IEEE 802.11ah protocol, also known as WiFi HaLow, introduced by the WiFi Alliance as the WiFi solution for IoT networks.
We first investigated normal behavior of a simulated IEEE 802.11ah network with honest stations only to investigate the default fairness of the network and then gradually introduced different percentages of selfish stations. The simulations included different combinations of RAW slots and various number of stations for UDP, TCP firmware and TCP IP camera. The quality of service parameters in terms of fairness, throughput, and packet loss were analyzed. From our simulation results, it became clear that the IEEE802.11ah network has some inherent unfairness by default. The more stations in the network, the less fair the network became. The highest fairness was achieved when there were 30 stations in the network split into four slots. Therefore, when number of stations increases, fairness can be maintained by increasing the number of slots, because more slots means less stations per slot. After introducing selfish stations, the results showed that the selfish stations need to be selfish together (collaboratively) in order to actually gain advantages. Our results showed that if the selfish stations are less than 30% of the network, they are actually suffering because of the inherent selfish behavior of the network. The selfish stations had the highest advantage when they were 30% to 40% of the network. When they became more than 40%, they began to compete with each other and suffered again. Furthermore, the network’s fairness gradually decreased when selfish stations were introduced. The throughput of selfish stations was higher than the throughput of honest stations when there were more than 30% selfish stations. The reduced throughput of honest stations also led to increased packet loss due to the limited packet buffer size of the stations. Finally, UDP showed to be less influenced by the selfish stations, because it has higher data rates that TCP. Both TCP firmware and TCP IP camera were less fair compared to UDP by default, but the introduction of selfish stations did not affect fairness as significantly as in UDP.
Consequently, we studied applicability of the Principle-agent [
7] and Deviation detection [
8] for detecting selfish behavior in IEEE802.11ah. Our simulation results showed that the Principle-agent method resulted in extremely high false positive. We expect that it performed poorly because it is designed to work for less traffic-intensive networks. The seconds technique showed better results; however, it still did not perform as expected due to the inherent selfish behavior of IEEE 802.11ah. Therefore, we proposed a new detection algorithm called Inherent Selfish Stations Detector (ISSD) designed to detect not only the introduced selfish stations but also the inherent ones. The proposed technique uses the baseline distribution of the network share to identify a threshold for detection of selfish stations. The comparison with the deviation detection mechanism showed that ISSD performed better for UDP, TCP firmware and TCP IP camera and, thus, may be considered a suitable detection mechanism for IEEE 802.11ah.
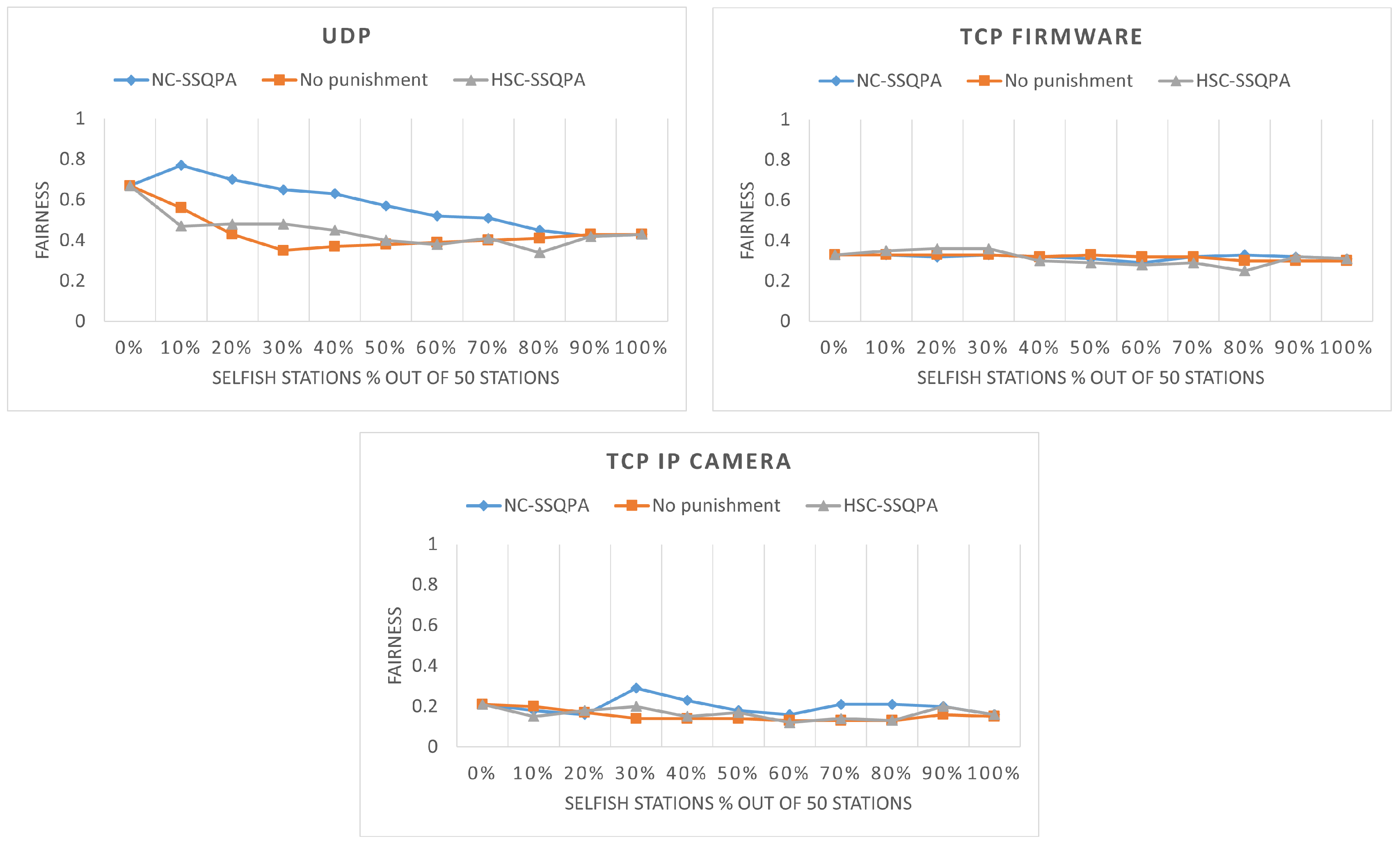
Finally, we presented a new selfish behavior mitigation algorithm, called Selfish Stations Quarantine Punishment Algorithm (SSQPA). The algorithm relies on the successful detection of the selfish stations by a selfish stations detection technique. Then, it allocates the identified selfish stations in a separate RAW group dedicated to selfish stations only. By doing so, the honest stations are completely isolated from the selfish ones and no longer suffer from decreased throughput and packet loss. The punishment strategy for the selfish stations is based on reducing their slot duration and increasing the contention. Honest stations were awarded for being honest through increased slot duration and decreased contention. Two different variants of SSQPA were presented: network-centric SSQPA and honest station-centric SSQPA. The goal of NC-SSQPA is to create a fair network, in which the award of honest stations is limited to prevent honest stations from gaining significant advantages. On the other hand, HSC-SSQPA awards the honest stations without any limits in order to create a network that highly favors honest stations but decreases fairness. Our performance evaluation showed that both variants of SSQPA successfully mitigate the negative effect of selfish behavior on the network and can be used for UDP, TCP firmware and TCP IP camera scenarios.
We also studied the breaking point of the algorithm, which is the percentage of correctly detected selfish station required for the SSQPA to be beneficial. The results showed that, for NC-SSQPA, at least 70% of the selfish stations need to be detected, while for HSC-SSQPA, at least 80% need to be detected. Failing to detect that many stations would provide higher gain to the honest stations compared to the case where they are not being punished, because they will be awarded for obeying the protocol, even though they are not obeying the protocol. Therefore, the detection algorithm used for SSQPA must detect at least 70% of the stations for NC-SSQPA and at least 90% for HSC-SSQPA.
The current version of ISSD relies on the manual analysis of network distribution to determine the threshold for detection of selfish stations. This can be improved, in future studies, by implementing an algorithm that calculates the shares and selects a threshold based on the distribution such that the most dominant stations with the highest network share are detected as selfish only. Additionally, the evolution of the population of the network can be studied when all stations can choose their own behavior and the goal of the stations are to maximize their own throughput.
Additionally, in the current version of SSQPA, it is not possible to determine whether a selfish station has changed its behavior. As part of future studies, it would be good to study how introduction of new RAW groups in which selfish stations will be allocated after they have spent some time in the selfish stations group can influence mitigation.