CM-CPPA: Chaotic Map-Based Conditional Privacy-Preserving Authentication Scheme in 5G-Enabled Vehicular Networks
Abstract
:1. Introduction
- A chaotic map-based CPPA scheme is proposed for vehicular networks relying on 5G technology to achieve security goals in terms of piracy (Identity-Anonymity and Unlinkability) and security (Message Integrity and Authentication and Traceability) requirements. Moreover, our proposal has the ability to resist security attacks, such as modification, impersonation, replay, and man-in-the-middle.
- A scheme that applies chaotic polynomial map to generate/sign message (e.g., signer side) and verify the validity and authenticity of signature (e.g., checker side).
- A scheme that uses the well-known accepted simulator called AVISPA tool under OFMC and CL-AtSe back ends and shows that the scheme is perfectly secure against active and passive attacks.
- A scheme that outperforms most recent related schemes based on EC and BP operations with regard to overhead of computation and communication.
2. Related Work
3. Background
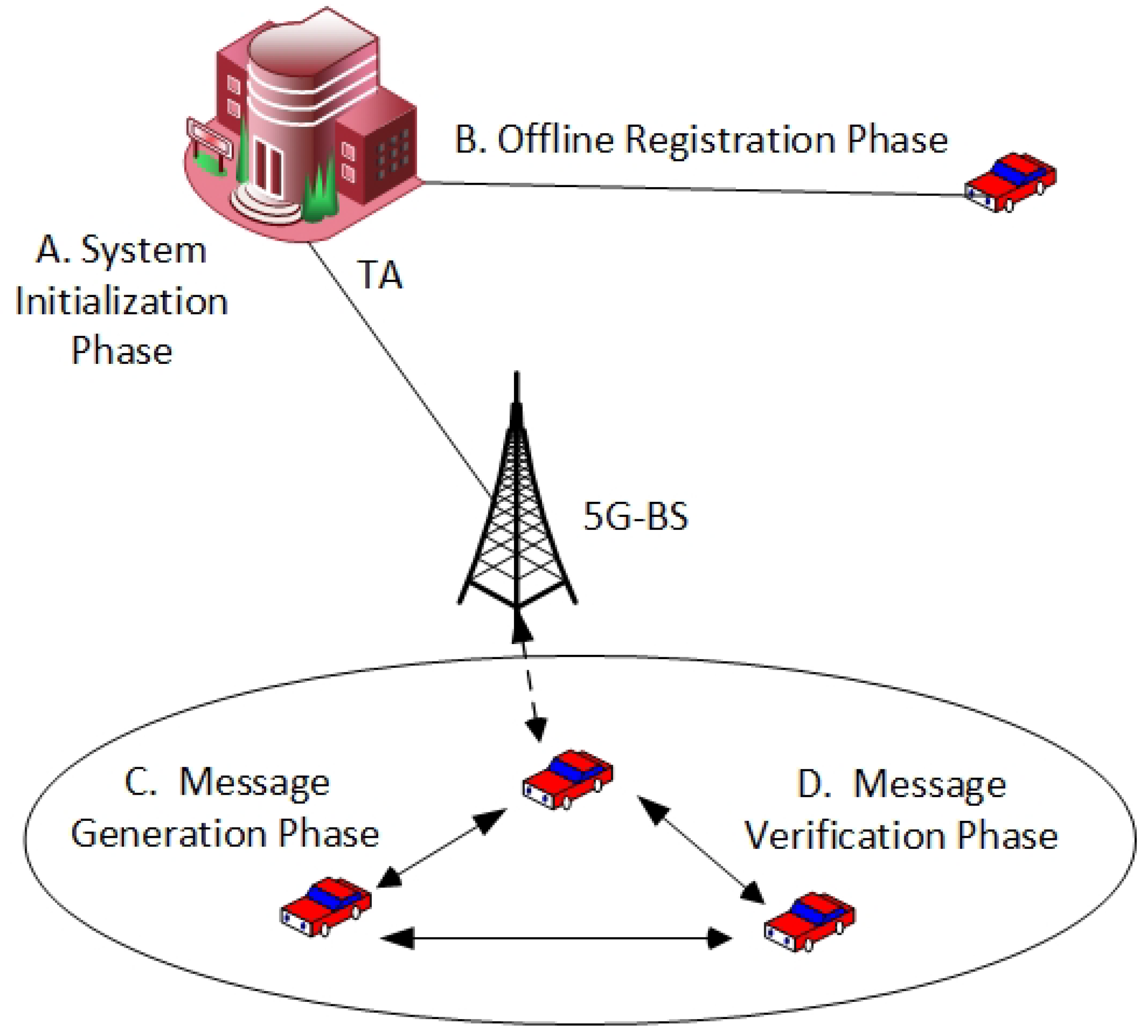
3.1. Network Structure
- TA: Suppose that TA is full trust and has high resources with regard to computation capacity, sufficient storage, and high credibility. In the proposed CM-CPPA scheme, TA is in charge of generating security parameters (chaotic map) and preloading them to participating registered vehicles during the registration process. Furthermore, the TA saves its private key to the vehicle security. If the attacker compromises the TA, the entire system will be insecure. Additionally, the TA has the ability to update the parameters and then preload them into the vehicle to avoid any attack occurring.
- 5G-BS: The 5G-BS is a wireless infrastructure mounted along the sides of roads. Suppose that 5G-BS is hard to be compromised. In the proposed CM-CPPA scheme, 5G-BS only acts as an intermediary transmission medium between the nodes and the TA without any storage or verification.
- Vehicle: Each vehicle has OBU for communicating with each other and sharing traffic information. A tamper-proof device (TPD) is fitted in each OBU to save critical data received from TA.
3.2. Security Goals
- Privacy (Identity-Anonymity): A true identification of the node must become fully anonymous to all participating registered vehicles.
- Message Integrity and Authentication: The recipient of a message has the ability to validate that the received message has not been changed by an adversary. Furthermore, the recipient of the message can check that it was issued by a participating registered vehicle.
- Traceability: In vehicular communication relying on 5G technology, the TA has the capability to track down the true identity of the sender in case of a dispute.
- Unlinkability: A third party should not be capable of relating several messages or predicting that these were issued by the same sender.
- Resistance to Security Attacks includes: modification, replay, impersonation, and man-in-the-middle attacks.
3.3. Attackers Model
- Modification Attack: The message shared by the vehicle can be modified/altered by the attacker to disturb the system.
- Impersonation Attack: The true identification of the node can be impersonated by an attacker to broadcast a forged message in the system.
- Replay Attack: The message shared by vehicles can be replied to at different times to send it again to other vehicles.
- Man-In-The-Middle Attack: The data shared between the recipient and sender can be interrupted by a third party to make damage to the entire system.
4. Proposed Scheme
- Consider P be a large prime number and n be an integer.
- Consider x be an inconstant tacking value in the interval .
- Consider be a chaotic map (e.g., Chebyshev polynomial) of class n, which it is determined according to Equation (1).
- Chaotic feature: If degree 1 < n, it can determine the chaotic map with a fixed thickness function.
- Semi-group feature:where l and w are positive integers and .
- Discrete Logarithm (DL) problem: The major function of DL is to detect the unknown number w such that for two taking items y and x.
- Diffie–Hellman (DH) problem: The major function of DH is to evaluate the for three taking items x, , and .
- h: The chaotic map-based hash function, where .
- : The identity of the vehicle.
- : The operation of message concatenation.
- ⊕: The operation of exclusive-OR.
- : The information-related message.
- : The pseudonym-identification of the vehicle.
- : The signature of the safety-related message .
- : The current timestamp.
4.1. System Initialization Phase
- TA randomly picks values and the large prime P based on the chaotic map in the whole system.
- TA randomly picks a value s as its private key.
- TA chooses a chaotic map-based hash function h, where .
- TA sets {x, , P, h} as the public parameters.
4.2. Offline Registration Phase
- The driver submits the true identity of vehicle to the local TA.
- Once receiving , the TA saves it to the list of vehicle registration.
- TA preloads the public parameters {x, , P, h} to the vehicle .
- Finally, TA saves its private key s to the TPD of vehicle .
4.3. Message Generation Phase
- issues safety-related message and the current timestamp .
- generates pseudonym-ID .
- computes the parameter .
- signs the message
- computes the signature of safety-related message .
- Finally, broadcasts the message-tuple {, , , } to the participating vehicles nearby in 5G-enabled vehicular networks.
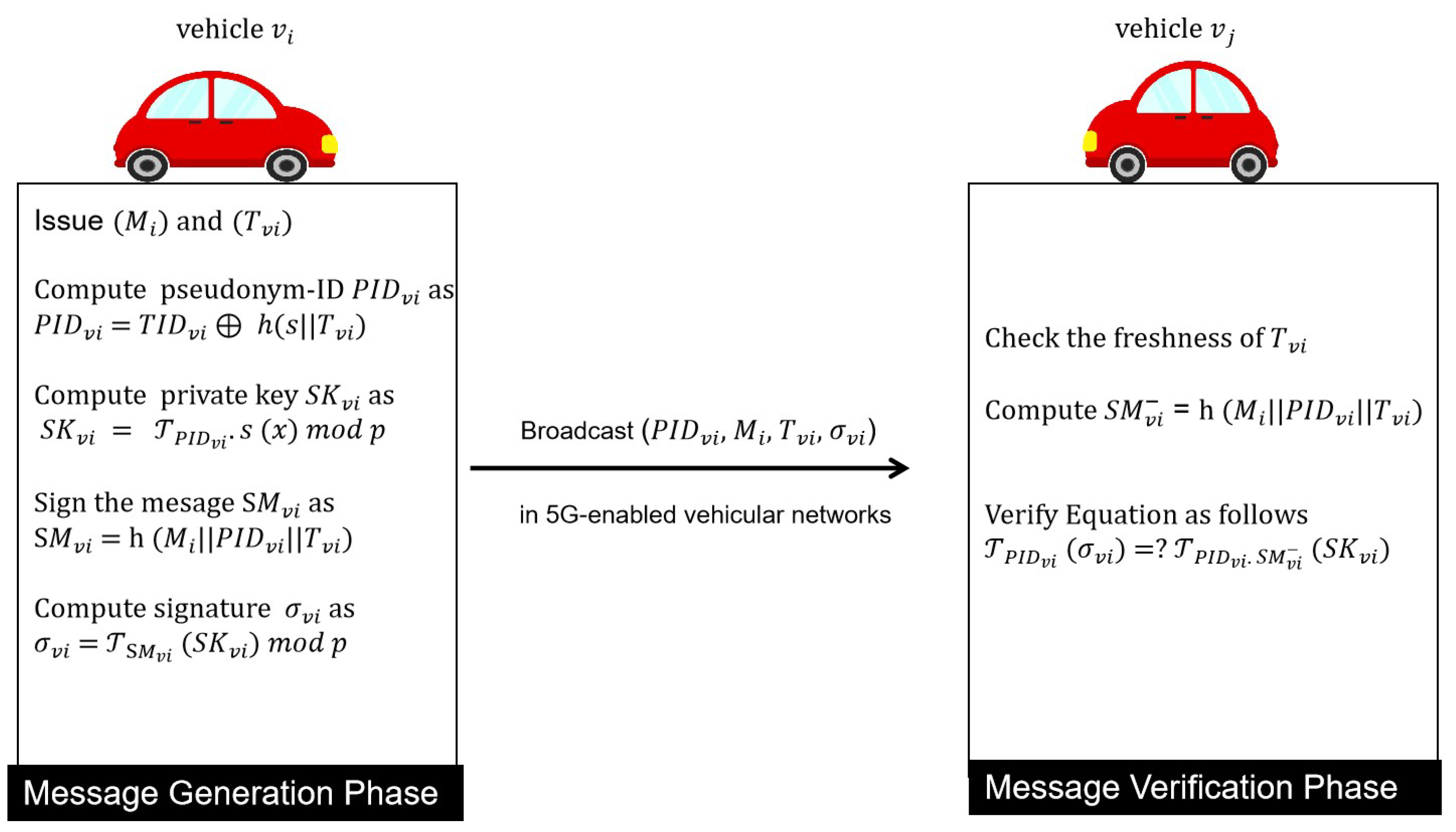
4.4. Message Verification Phase
- When receiving the message-tuple {, , , }, the verifier initially checks the freshness of timestamp .
- Then, the verifier computes .
- Finally, the verifier uses the message signature of the message-tuple {, , , } to check the safety-related message , where . The verifier accepts the message if Equation (4) holds. Otherwise, the message is discarded.
5. Security Analysis
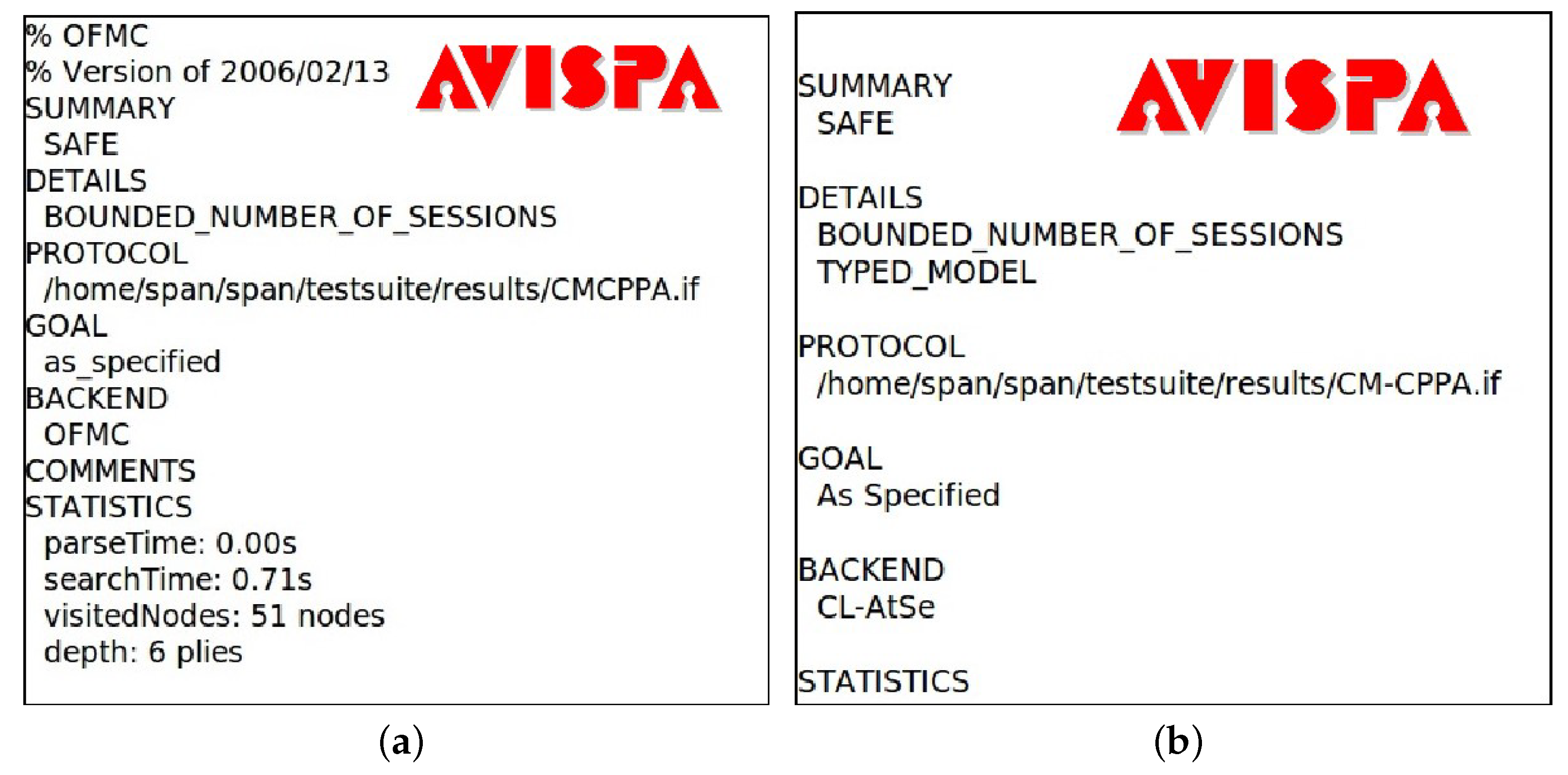
5.1. AVISPA
5.2. Security Proof
5.3. Informal Security
- Privacy (identity-anonymity): In this work, the participating registered vehicle transmits the message-tuple {, , , } to nearby others. The true identity of vehicle is hidden to the message-tuple by =, where s is the private key of the system and is the current timestamp. During the offline registration phase (Section 4.2), once the true identity of the vehicle is submitted by the driver, the TA saves it to the vehicle registration list. Moreover, when the message-tuple {, , , } is captured by a third party, there is no information about the identity of vehicle . Therefore, the identity of the vehicle is the only known by the participating registered vehicle and the TA. So, this work achieves the privacy (identity-anonymity) requirement in 5G-enabled vehicular networks.
- Message Authentication and Integrity: In the proposed CM-CPPA scheme, the message-tuple {, , , } is included as a sophisticated signature , where , and = (Section 4.3). Based on the complexity of DLP associated with the chaotic map, the malicious vehicle () cannot find/retrieve the private key of the system s such that for two given parts x and y. Therefore, the verifier can confirm the authenticity and integrity of message-tuple {, , , } sent from vehicle by checking whether equation holds (Section 4.4). For instance, after capturing the message-tuple {, , , } sent from , a malicious vehicle () modifies/changes the safety-related message to a bogus message and then sends the altered false message-tuple {, , , } into 5G-enabled vehicular networks. The verifier confirms the authenticity and integrity of the altered false message-tuple {, , , } by checking whether Equation (4) holds. If it holds, then the proposed CM-CPPA scheme achieves the message authenticity and integrity requirements.
- Traceability: In the proposed CM-CPPA scheme, the TA is responsible to register the vehicle based on an unique true identity of vehicle in the offline registration phase (Section 4.2). Furthermore, there is no publicly available information with respect to the true identity of vehicle on the message-tuple {, , , }, where =. Therefore, the TA has the capability to retrieve the true identity of vehicle from a pseudonym-ID = included on the message-tuple {, , , } by executing since TA has its private key s and obtained timestamp . Thus, this work achieves the traceability requirement.
- Unlinkability: In the proposed CM-CPPA scheme, the vehicle generates a new pseudonym-ID = to each message generation process, where is the new current timestamp. According to the chaotic map-based hash function , the result will change from the various initial input. Therefore, the adversary cannot link two or more message-tuples {, , , }, {, , , } sent from the same sender (vehicle ). Thus, the proposed CM-CPPA scheme achieves the unlinkability requirement.
- Resistance to modification attack: The main malicious task of the modification attack is to launch a modified safety-related message to falsify the message and then broadcast the altered false message-tuple {, , , } in 5G-enabled vehicular networks. As a result, the entire the system will be insecure. To resist the modification attack, the verifier in the proposed CM-CPPA scheme can distinguish any alteration in {, , , } by checking whether equation holds. If it holds, then the receiver accepts the message ; otherwise, it will be discarded. Hence, the proposed CM-CPPA scheme successfully withstands the modification attack.
- Resistance to impersonation attack: The main malicious task of an impersonation attack is to impersonate a forged message signature as participating registered vehicle and then broadcast the forged message-tuple {, , , } in vehicular communication relying on 5G technology. Furthermore, the attacker must initially obtain/retrieve the identity of vehicle and the private key of the system s to impersonate a legitimate vehicle. Thus, in this work, vehicle hides its into a pseudonym-ID = and the private key of the system s is stored in the TPD of the participating registered vehicle . According to DLP of the chaotic map, the adversary cannot find the private key of the system. Thus, the proposed CM-CPPA scheme successfully withstands the impersonation attack.
- Resistance to replay attack: The main malicious task of replay attack is to replay the previously generated message-tuple {, , , } sent from a participating registered vehicle to disturb the 5G-enabled vehicular networks. However, in this work, a timestamp is contained in the message-tuple {, , , }, where and . The freshness timestamp is issued by the vehicle during the message generation process. Once receiving the message-tuple {, , , }, the verifier initially checks the freshness of the timestamp to continue the verification process. Otherwise, the message will be discarded immediately. Thus, the proposed CM-CPPA scheme successfully withstands the replay attack.
- Resistance to Man-In-The-Middle (MITM) Attack: The main malicious task of MITM attack is to intercept the participating registered sender and receiver . However, in the proposed CM-CPPA scheme, mutual authentication among nodes is executed. Furthermore, by using the AVISPA tool (Section 5.1), this work is secure against high control attackers (Dolev–Yao model) over the system. Thus, the proposed CM-CPPA scheme successfully resists the MITM attack in 5G-enabled vehicular networks.
6. Performance Evaluation
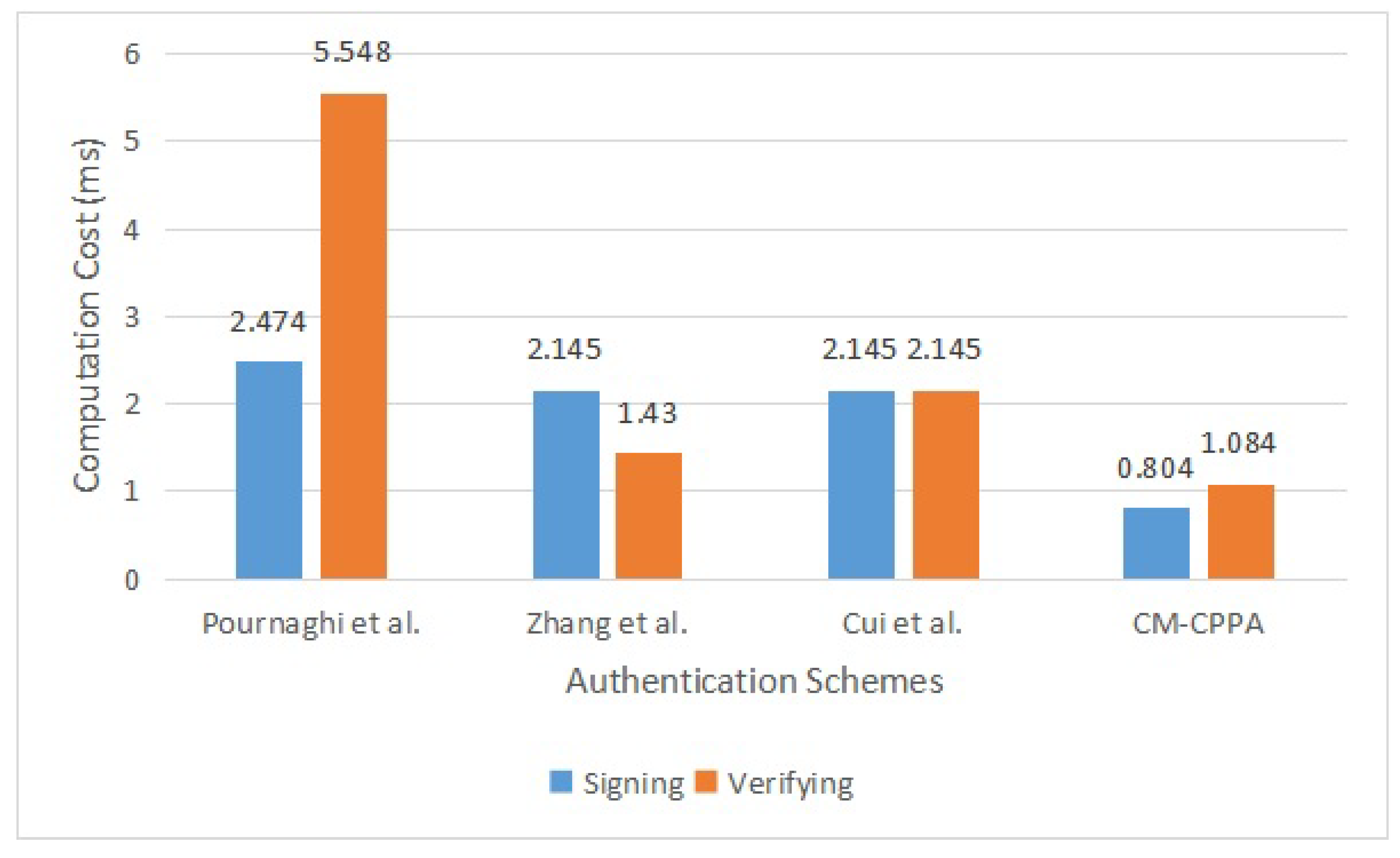
6.1. Computation Overhead Analysis and Comparison
- : the running cost of the BP operation (S, T), where , ∈.
- : the running cost of a Point-to-Map hashing operation for the BP in .
- : the running cost of operation with regards to a scale multiplication for the EC, where and .
- : the running cost of Chebyshev’s polynomial mapping operation.
- : the running cost of the chaotic map hashing operations.
6.2. Communication Overhead Analysis and Comparison
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Lai, C.; Lu, R.; Zheng, D.; Shen, X. Security and privacy challenges in 5G-enabled vehicular networks. IEEE Netw. 2020, 34, 37–45. [Google Scholar] [CrossRef]
- Cheng, X.; Zhang, R.; Yang, L. Wireless toward the era of intelligent vehicles. IEEE Internet Things J. 2018, 6, 188–202. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. A Secure Pseudonym-Based Conditional Privacy-Preservation Authentication Scheme in Vehicular Ad Hoc Networks. Sensors 2022, 22, 1696. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Khalil, A.; Hasbullah, I.H. Security and Privacy Schemes in Vehicular Ad-Hoc Network with Identity-Based Cryptography Approach: A Survey. IEEE Access 2021, 9, 121522–121531. [Google Scholar] [CrossRef]
- Alazzawi, M.A.; Al-behadili, H.A.; Srayyih Almalki, M.N.; Challoob, A.L.; Al-shareeda, M.A. ID-PPA: Robust identity-based privacy-preserving authentication scheme for a vehicular ad-hoc network. In Proceedings of the International Conference on Advances in Cyber Security, Penang, Malaysia, 8–9 December 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 80–94. [Google Scholar]
- Cheng, X.; Zhang, R.; Chen, S.; Li, J.; Yang, L.; Zhang, H. 5G enabled vehicular communications and networking. China Commun. 2018, 15, 3–6. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Al-Mekhlafi, Z.G.; Qtaish, A.; Alzahrani, A.J.; Alshammari, G.; Sallam, A.A.; Almekhlafi, K. Chebyshev Polynomial-Based Scheme for Resisting Side-Channel Attacks in 5G-Enabled Vehicular Networks. Appl. Sci. 2022, 12, 5939. [Google Scholar] [CrossRef]
- Prasad, K.S.V.; Hossain, E.; Bhargava, V.K. Energy efficiency in massive MIMO-based 5G networks: Opportunities and challenges. IEEE Wirel. Commun. 2017, 24, 86–94. [Google Scholar] [CrossRef] [Green Version]
- Al-Shareeda, M.A.; Anbar, M.; Hasbullah, I.H.; Manickam, S. Survey of authentication and privacy schemes in vehicular ad hoc networks. IEEE Sens. J. 2020, 21, 2422–2433. [Google Scholar] [CrossRef]
- Cui, J.; Wei, L.; Zhang, J.; Xu, Y.; Zhong, H. An efficient message-authentication scheme based on edge computing for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2018, 20, 1621–1632. [Google Scholar] [CrossRef]
- Hamdi, M.M.; Mustafa, A.S.; Mahd, H.F.; Abood, M.S.; Kumar, C.; Al-shareeda, M.A. Performance analysis of QoS in MANET based on IEEE 802.11 b. In Proceedings of the 2020 IEEE International Conference for Innovation in Technology (INOCON), Bangluru, India, 6–8 November 2020; pp. 1–5. [Google Scholar]
- Raya, M.; Hubaux, J.P. Securing vehicular ad hoc networks. J. Comput. Secur. 2007, 15, 39–68. [Google Scholar] [CrossRef] [Green Version]
- Cincilla, P.; Hicham, O.; Charles, B. Vehicular PKI scalability-consistency trade-offs in large scale distributed scenarios. In Proceedings of the 2016 IEEE Vehicular Networking Conference (VNC), Columbus, OH, USA, 8–10 December 2016; pp. 1–8. [Google Scholar]
- Huang, D.; Misra, S.; Verma, M.; Xue, G. PACP: An efficient pseudonymous authentication-based conditional privacy protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2011, 12, 736–746. [Google Scholar] [CrossRef]
- Joshi, A.; Gaonkar, P.; Bapat, J. A reliable and secure approach for efficient car-to-car communication in intelligent transportation systems. In Proceedings of the 2017 International Conference on Wireless Communications, Signal Processing and Networking (WiSPNET), Chennai, India, 22–24 March 2017; pp. 1617–1620. [Google Scholar]
- Lu, R.; Lin, X.; Luan, T.H.; Liang, X.; Shen, X. Pseudonym changing at social spots: An effective strategy for location privacy in vanets. IEEE Trans. Veh. Technol. 2011, 61, 86–96. [Google Scholar] [CrossRef] [Green Version]
- Thenmozhi, T.; Somasundaram, R. Pseudonyms based blind signature approach for an improved secured communication at social spots in VANETs. Wirel. Pers. Commun. 2015, 82, 643–658. [Google Scholar] [CrossRef]
- Rajput, U.; Abbas, F.; Oh, H. A hierarchical privacy preserving pseudonymous authentication protocol for VANET. IEEE Access 2016, 4, 7770–7784. [Google Scholar] [CrossRef]
- Asghar, M.; Doss, R.R.M.; Pan, L. A scalable and efficient PKI based authentication protocol for VANETs. In Proceedings of the 2018 28th International Telecommunication Networks and Applications Conference (ITNAC), Sydney, Australia, 21–23 November 2018; pp. 1–3. [Google Scholar]
- Förster, D.; Kargl, F.; Löhr, H. PUCA: A pseudonym scheme with user-controlled anonymity for vehicular ad-hoc networks (VANET). In Proceedings of the 2014 IEEE Vehicular Networking Conference (VNC), Paderborn, Germany, 3–5 December 2014; pp. 25–32. [Google Scholar]
- Sun, Y.; Zhang, B.; Zhao, B.; Su, X.; Su, J. Mix-zones optimal deployment for protecting location privacy in VANET. Peer Peer Netw. Appl. 2015, 8, 1108–1121. [Google Scholar] [CrossRef]
- Zhang, C.; Ho, P.H.; Tapolcai, J. On batch verification with group testing for vehicular communications. Wirel. Netw. 2011, 17, 1851–1865. [Google Scholar] [CrossRef]
- Lee, C.C.; Lai, Y.M. Toward a secure batch verification with group testing for VANET. Wirel. Netw. 2013, 19, 1441–1449. [Google Scholar] [CrossRef]
- Jianhong, Z.; Min, X.; Liying, L. On the security of a secure batch verification with group testing for VANET. Int. J. Netw. Secur. 2014, 16, 351–358. [Google Scholar]
- Zhong, H.; Han, S.; Cui, J.; Zhang, J.; Xu, Y. Privacy-preserving authentication scheme with full aggregation in VANET. Inf. Sci. 2019, 476, 211–221. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Deboarh, L.J. EAAP: Efficient anonymous authentication with conditional privacy-preserving scheme for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2467–2476. [Google Scholar] [CrossRef]
- Zhang, L.; Wu, Q.; Domingo-Ferrer, J.; Qin, B.; Hu, C. Distributed aggregate privacy-preserving authentication in VANETs. IEEE Trans. Intell. Transp. Syst. 2016, 18, 516–526. [Google Scholar] [CrossRef]
- Bayat, M.; Barmshoory, M.; Pournaghi, S.M.; Rahimi, M.; Farjami, Y.; Aref, M.R. A new and efficient authentication scheme for vehicular ad hoc networks. J. Intell. Transp. Syst. 2020, 24, 171–183. [Google Scholar] [CrossRef]
- Bayat, M.; Pournaghi, M.; Rahimi, M.; Barmshoory, M. NERA: A New and Efficient RSU based Authentication Scheme for VANETs. Wirel. Netw. 2020, 26, 3083–3098. [Google Scholar] [CrossRef]
- Pournaghi, S.M.; Zahednejad, B.; Bayat, M.; Farjami, Y. NECPPA: A novel and efficient conditional privacy-preserving authentication scheme for VANET. Comput. Netw. 2018, 134, 78–92. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. SE-CPPA: A Secure and Efficient Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-Hoc Networks. Sensors 2021, 21, 8206. [Google Scholar] [CrossRef] [PubMed]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An efficient identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Asaar, M.R.; Salmasizadeh, M.; Susilo, W.; Majidi, A. A secure and efficient authentication technique for vehicular ad-hoc networks. IEEE Trans. Veh. Technol. 2018, 67, 5409–5423. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. Towards identity-based conditional privacy-preserving authentication scheme for vehicular ad hoc networks. IEEE Access 2021, 9, 113226–113238. [Google Scholar] [CrossRef]
- Li, J.; Choo, K.K.R.; Zhang, W.; Kumari, S.; Rodrigues, J.J.; Khan, M.K.; Hogrefe, D. EPA-CPPA: An efficient, provably-secure and anonymous conditional privacy-preserving authentication scheme for vehicular ad hoc networks. Veh. Commun. 2018, 13, 104–113. [Google Scholar] [CrossRef]
- Alshudukhi, J.S.; Mohammed, B.A.; Al-Mekhlafi, Z.G. Conditional Privacy-Preserving Authentication Scheme Without Using Point Multiplication Operations Based on Elliptic Curve Cryptography (ECC). IEEE Access 2020, 8, 222032–222040. [Google Scholar] [CrossRef]
- Alazzawi, M.; Lu, H.; Yassin, A.; Chen, K. Efficient Conditional Anonymity with Message Integrity and Authentication in a Vehicular Ad hoc Network. IEEE Access 2019, 7, 71424–71435. [Google Scholar] [CrossRef]
- Zhang, J.; Cui, J.; Zhong, H.; Chen, Z.; Liu, L. PA-CRT: Chinese remainder theorem based conditional privacy-preserving authentication scheme in vehicular ad-hoc networks. IEEE Trans. Depend. Secur. Comput. 2019, 18, 722–735. [Google Scholar] [CrossRef] [Green Version]
- Alshudukhi, J.S.; Al-Mekhlafi, Z.G.; Mohammed, B.A. A Lightweight Authentication with Privacy-Preserving Scheme for Vehicular Ad Hoc Networks Based on Elliptic Curve Cryptography. IEEE Access 2021, 9, 15633–15642. [Google Scholar] [CrossRef]
- Cui, J.; Wang, Y.; Zhang, J.; Xu, Y.; Zhong, H. Full Session Key Agreement Scheme Based on Chaotic Map in Vehicular Ad hoc Networks. IEEE Trans. Veh. Technol. 2020, 69, 8914–8924. [Google Scholar] [CrossRef]
- Zhang, J.; Zhong, H.; Cui, J.; Tian, M.; Xu, Y.; Liu, L. Edge computing-based privacy-preserving authentication framework and protocol for 5G-enabled vehicular networks. IEEE Trans. Veh. Technol. 2020, 69, 7940–7954. [Google Scholar] [CrossRef]
- Cui, J.; Chen, J.; Zhong, H.; Zhang, J.; Liu, L. Reliable and Efficient Content Sharing for 5G-Enabled Vehicular Networks. IEEE Trans. Intell. Transp. Syst. 2020, 23, 1247–1259. [Google Scholar] [CrossRef]
- Cui, J.; Zhang, X.; Zhong, H.; Ying, Z.; Liu, L. RSMA: Reputation system-based lightweight message authentication framework and protocol for 5G-enabled vehicular networks. IEEE Internet Things J. 2019, 6, 6417–6428. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. Password-Guessing Attack-Aware Authentication Scheme Based on Chinese Remainder Theorem for 5G-Enabled Vehicular Networks. Appl. Sci. 2022, 12, 1383. [Google Scholar] [CrossRef]


| Cryptography Operation | Running Cost (ms) |
|---|---|
| 1.537 | |
| 0.937 | |
| 0.715 | |
| 0.341 | |
| 0.061 |
| Schemes | Message Signing | Message Verification | Operations Based |
|---|---|---|---|
| Pournaghi et al. [30] | ms | ms | Bilnear Pair |
| Zhang et al. [41] | ms | ms | Elliptic Curve |
| Cui et al. [42] | m | m | Elliptic Curve |
| CM-CPPA | ms | ms | Chaotic Map |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Al-Mekhlafi, Z.G.; Qtaish, A.; Alzahrani, A.J.; Alshammari, G.; Sallam, A.A.; Almekhlafi, K. CM-CPPA: Chaotic Map-Based Conditional Privacy-Preserving Authentication Scheme in 5G-Enabled Vehicular Networks. Sensors 2022, 22, 5026. https://doi.org/10.3390/s22135026
Al-Shareeda MA, Manickam S, Mohammed BA, Al-Mekhlafi ZG, Qtaish A, Alzahrani AJ, Alshammari G, Sallam AA, Almekhlafi K. CM-CPPA: Chaotic Map-Based Conditional Privacy-Preserving Authentication Scheme in 5G-Enabled Vehicular Networks. Sensors. 2022; 22(13):5026. https://doi.org/10.3390/s22135026
Chicago/Turabian StyleAl-Shareeda, Mahmood A., Selvakumar Manickam, Badiea Abdulkarem Mohammed, Zeyad Ghaleb Al-Mekhlafi, Amjad Qtaish, Abdullah J. Alzahrani, Gharbi Alshammari, Amer A. Sallam, and Khalil Almekhlafi. 2022. "CM-CPPA: Chaotic Map-Based Conditional Privacy-Preserving Authentication Scheme in 5G-Enabled Vehicular Networks" Sensors 22, no. 13: 5026. https://doi.org/10.3390/s22135026
APA StyleAl-Shareeda, M. A., Manickam, S., Mohammed, B. A., Al-Mekhlafi, Z. G., Qtaish, A., Alzahrani, A. J., Alshammari, G., Sallam, A. A., & Almekhlafi, K. (2022). CM-CPPA: Chaotic Map-Based Conditional Privacy-Preserving Authentication Scheme in 5G-Enabled Vehicular Networks. Sensors, 22(13), 5026. https://doi.org/10.3390/s22135026











