Security and Privacy Analysis of Smartphone-Based Driver Monitoring Systems from the Developer’s Point of View
Abstract
1. Introduction
2. Related Work
- Integration with vehicle infotainment systems for the data storage, transfer, analysis and interpretation [85].
- Most of the solutions are focused on the analysis of one aspect of the security or privacy of such systems, while the task of combining them into a single automated approach has not been studied enough;
- Work of security and privacy analysis approaches in conditions of lack or inaccessibility of data has not been fully explored;
- Most of the approaches do not include the evaluation of the quality of the performed analysis into their reports;
- Most of the available solutions do not take into account specific features of the smartphone-based driver monitoring systems.
3. Data Models
3.1. Input Data
- —set of attacker models, protection against which is considered during the analysis (for example, can be a simple attacker on mobile applications for casual use, —advanced attacker on mobile applications for business use, —powerful attacker on mobile applications for specific use, etc.);
- —functionality of the analyzed driver monitoring system (for example, can be a road situation tracking, —context situation interpretation, —driver behavior tracking, etc.);
- —agreement between the user of the analyzed smartphone-based driver monitoring system and its owner that defines permissions on the user’s data extraction, storage and transferring;
- —access rights that are requested from the user of the system when the related application is installed on the user’s smartphone (usually, it is access to the smartphone’s camera (), microphone () and storage (); note that such access rights might be given to the application even when it is not used, which defines additional security and privacy concerns [86]);
- —source code of the analyzed driver monitoring system;
- —logs of the analyzed driver monitoring system;
- —traffic of the analyzed driver monitoring system;
- —requirements of the mobile application that represents the analyzed smartphone-based driver monitoring system;
- —requirements under the law that define the work with the private data of the user of the analyzed driver monitoring system (usually depending on the country of the user).
- —hardware components of the smartphone that are involved in the implementation of the functionality (for example, can be a rear camera, —front-facing camera, —gyroscope, etc.);
- —software algorithms of the application that are involved in the implementation of the functionality (for example, can be a noise detection algorithm, —heavy rain detection algorithm, —driver drinking detection algorithm, etc.);
- —data storage processes that are involved in the implementation of the functionality (for example, can be a smartphone local storage, —storage of the vehicle infotainment system, —cloud storage, etc.);
- —data extraction processes that are involved in the implementation of the functionality (for example, can be the extraction of the data from the application memory, —user contacts, —user media data, etc.);
- —data transfer processes that are involved in the implementation of the functionality (for example, can be USB, —Bluetooth, —cellular (4G, 5G, etc.), etc.).
- Hardware components (): front-facing camera ();
- Software algorithms (): computer vision algorithms for the detection of the inappropriate behavior detection—drowsiness (), distraction (), unfastened belt (), eating () and drinking (); note that the list of the algorithms for the driver behavior tracking depends on the product and may vary from one solution to another;
- Data storage processes (): smartphone local storage () and cloud storage (), assuming that machine learning models are too heavy to be used on a smartphone directly, so a remote server is required;
- Data transfer processes (): cellular ().
- —files that contain the source code of the application, including their extensions (for example, in Android Studio with Flutter project, can be the main.dart file, —project.yaml, —AppManifest.xml, etc.);
- —packages that are used in the application (for example, can be the google_fonts package, —animations, —crypto, etc.);
- —objects that are used in the source code (object-oriented programming);
- —variables that are used in the source code;
- —functions that are used in the source code;
- —IDEs (Integrated Development Environment) that were used during the development of the source code (for example, can be the Android Studio IDE, —DataGrip, —PyCharm, etc.).
- —required amount of memory for the installation of the application;
- —set of smartphone models that are supported by the application (for example, can be the iPhone 13 Pro smartphone, —Google Pixel 4a, —Xiaomi Redmi 10C, etc.);
- —set of vehicle models that are supported by the application (for example, can be the Tesla Model Y vehicle, —Ford Mustang Mach-E, —Chevrolet Bolt EV, etc.);
- —set of operating systems with their versions that are supported by the application (for example, can be the Android 12 operating system, —iOS 15.4.1, —HarmonyOS 2.0.1.195 SP5, etc.);
- —set of infotainment systems with their versions that are supported by the application (for example, can be the Windows Embedded Automotive 7 infotainment system, —Audi MMI 3G (Multi Media Interface), —BMW iDrive 7, etc.).
- —data object, work with which is covered by the requirement under the law (for example, date of birth, name and surname, salary, etc.);
- —data subject, whose work with the data object is covered by the requirement under the law (for example, owner of the application, infotainment system, cloud, etc.);
- —method that is required to be used on the data object to be processed by the subject in accordance with the requirement under the law (for example, encryption, anonymization, etc.);
- —data storage process of the data object that is allowed to the data subject in accordance with the requirement under the law ;
- —data extraction process of the data object that is allowed to the data subject in accordance with the requirement under the law ;
- —data transfer process of the data object that is allowed to the data subject in accordance with the requirement under the law ;
- —Boolean indicator that provides the information about the necessity of the permission from the application user for data subject to work (, , , ) with data object .
3.2. Output Data
- —Boolean indicator that shows if the information about the functionality of the product was provided;
- —Boolean indicator that shows if the information about the user agreement of the product was provided;
- —Boolean indicator that shows if the information about the access rights on the user’s smartphone, which are required for the correct work of the product, was provided;
- —Boolean indicator that shows if the information about the source code of the product was provided;
- —Boolean indicator that shows if the information about the logs of the product was provided;
- —Boolean indicator that shows if the information about the traffic of the product was provided;
- —Boolean indicator that shows if the information about the system requirements of the product was provided;
- —Boolean indicator that shows if the information about the requirements under the law to work with user’s data was provided.
4. Proposed Approach
- , where the possibility of detection of and depends on the availability of the information about concrete implementations of the hardware components/software algorithms, while for the , abstract descriptions are enough;
- , where any process that works with sensitive data is connected with the corresponding and defines an additional check of the product source code () to identify specific and ;
- , where potentially dangerous user permissions to the application on the smartphone are connected with the corresponding ;
- , where any part of the source code that works with the product user’s data is analyzed in terms of security to detect specific and ;
- , where the availability of the information about a concrete model of the smartphone () and vehicle (), as well as concrete version of the smartphone’s operating system () and vehicle’s infotainment system () provides a possibility to extract information about the corresponding and .
- To compare and to identify which requirements under the law must be considered in detail by the approach (), because private data that are covered by them are processed in the application;
- To compare and to identify situations when private data are processed by the application without permission from the user, while such a permission is required according to the law ().
5. Experimental Evaluation
- Stage 1: , , ;
- Stage 2: , ;
- Stage 3: , , , ;
- Stage 4: ;
- Stage 5: , .
- Stage 1: , 35%;
- Stage 2: , 20%;
- Stage 3: , 10%;
- Stage 4: , 0%;
- Stage 5: , 30%.
- , 17.5%;
- , 2%;
- , 2%;
- , 0%;
- , 3%.
- , 32.5%;
- , 12.5%;
- , 24.5%.
- Hardware components (): microphone (), accelerometer ();
- Software algorithms (): dangerous noise (), driver’s talking () and dangerous maneuvers () detection;
- Data storage processes (): smartphone () and cloud ();
- Data extraction processes (): none;
- Data transfer processes (): cellular ().
- Context situation interpretation (): driver’s talking ();
- Driver behavior tracking (): driver’s eating () and drinking ().
- : Front-facing camera (), microphone (), accelerometer ();
- : Detection of the dangerous noise () and vehicle maneuvers (), driver’s drowsiness (), distraction () and unfastened belt ();
- : Smartphone local () and cloud () storage;
- : Cellular () network.
- Sensors (): generation of false events (), bypass of the detection (), physical harm (), replacement ();
- Algorithm (): generation of false data (), interception or modification of input data (), interception or modification of output data (), partial modification of the functionality ();
- Application (): insertion of the malicious code (), insertion of additional destinations for collected data (), insertion of malicious ads ();
- Operating system (): termination of security measures (), spoofing of applications data (), extraction of user credentials (), failure of update system ();
- External connections (): violation of the authentication system (), traffic sniffing (), man-in-the-middle (), interfaces jamming ();
- External systems (): violation of the access control (), malfunction of API (), cloud storage malfunction (), external sharing of data ().
- Possibility of users’ credentials extraction, failure of the update system, violation of the authentication system, traffic sniffing, man-in-the-middle, interfaces jamming, violation of the access control, malfunction of API, cloud storage malfunction;
- 653 CVEs for Android 8, 211 CVEs for Samsung devices and related CWEs, the relevance of which must be checked due to no information about already installed security updates.
- Functionality () for the third stage; and
- Required access rights on the user’s smartphone () for the fifth stage.
- Presence of the user’s sensitive data in the smartphone local storage;
- Presence of the user’s sensitive data in the cloud storage;
- Transfer of the user’s sensitive data through the cellular network;
- Audio recording of the user;
- Photographing and video recording of the user;
- Recording of the user’s driving habits.
6. Discussion
- Combination of the security and privacy analysis;
- Required protection level is set through the attacker model;
- Detected issues are reported together with appropriate measures;
- Approach can work in conditions of lack or inaccessibility of data;
- Specific features of driver monitoring systems are taken into account;
- Results of the analysis can be stored and used multiple times;
- Quality of the analysis is measured based on the missed input data;
- Approach is modular and extensible.
- Correctness of the issues detection and measures suggestion highly depends on the completeness of the approach’s database;
- Fulfillment of such a database cannot be fully automated (manual work required);
- Quality of the security and privacy analysis directly depends on the input data that are provided by the developers;
- Security and privacy issues are only detected, not fixed.
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| CPE | Common Platform Enumeration |
| NVD | National Vulnerability Database |
| CVE | Common Vulnerabilities and Exposures |
| CWE | Common Weakness Enumeration |
| CVSS | Common Vulnerability Scoring System |
| URI | Uniform Resource Identifier |
| GPS | Global Positioning System |
| GLONASS | Global Navigation Satellite System |
| IDE | Integrated Development Environment |
| MMI | Multi Media Interface |
| GDPR | General Data Protection Regulation |
| TPM | Trusted Platform Module |
| OWASP | Open Web Application Security Project |
| API | Application Programming Interface |
| SSL | Secure Sockets Layer |
| VPN | Virtual Private Network |
References
- Mallozzi, P.; Pelliccione, P.; Knauss, A.; Berger, C.; Mohammadiha, N. Autonomous vehicles: State of the art, future trends, and challenges. Automot. Syst. Softw. Eng. 2019, 347–367. [Google Scholar] [CrossRef]
- Thakur, D.; Biswas, S. Smartphone based human activity monitoring and recognition using ML and DL: A comprehensive survey. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 5433–5444. [Google Scholar] [CrossRef]
- Kashevnik, A.; Ponomarev, A.; Shilov, N.; Chechulin, A. In-vehicle situation monitoring for potential threats detection based on smartphone sensors. Sensors 2020, 20, 5049. [Google Scholar] [CrossRef] [PubMed]
- Talal, M.; Zaidan, A.; Zaidan, B.; Albahri, O.S.; Alsalem, M.; Albahri, A.S.; Alamoodi, A.; Kiah, M.L.M.; Jumaah, F.; Alaa, M. Comprehensive review and analysis of anti-malware apps for smartphones. Telecommun. Syst. 2019, 72, 285–337. [Google Scholar] [CrossRef]
- Kumar, R.; Goyal, R. On cloud security requirements, threats, vulnerabilities and countermeasures: A survey. Comput. Sci. Rev. 2019, 33, 1–48. [Google Scholar] [CrossRef]
- Point, C. Mobile Security Report 2021: Insights on Emerging Mobile Threats. Available online: https://pages.checkpoint.com/mobile-security-report-2021.html (accessed on 13 May 2022).
- Services, A.W. 2021 AWS Cloud Security Report. 2022. Available online: https://fidelissecurity.com/resource/report/aws-cloud-security-report/ (accessed on 13 May 2022).
- Zelle, D.; Rieke, R.; Plappert, C.; Krauß, C.; Levshun, D.; Chechulin, A. Sepad–security evaluation platform for autonomous driving. In Proceedings of the 28th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP), Västerås, Sweden, 11–13 March 2020; pp. 413–420. [Google Scholar]
- Swiftic. Official Website of the Swiftic Framework for Mobile Applications. Available online: https://www.swiftic.com/ (accessed on 28 June 2022).
- React. Official Website of the React Native Framework for Mobile Applications. Available online: https://reactnative.dev/ (accessed on 28 June 2022).
- Flutter. Official Website of the Flutter Framework for Mobile Applications. 2022. Available online: https://flutter.dev/ (accessed on 28 June 2022).
- Kulenovic, M.; Donko, D. A survey of static code analysis methods for security vulnerabilities detection. In Proceedings of the 37th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 26–30 May 2014; pp. 1381–1386. [Google Scholar]
- Tabrizi, F.M.; Pattabiraman, K. Design-level and code-level security analysis of IoT devices. ACM Trans. Embed. Comput. Syst.) 2019, 18, 1–25. [Google Scholar] [CrossRef]
- Mathas, C.M.; Vassilakis, C.; Kolokotronis, N.; Zarakovitis, C.C.; Kourtis, M.A. On the Design of IoT Security: Analysis of Software Vulnerabilities for Smart Grids. Energies 2021, 14, 2818. [Google Scholar] [CrossRef]
- Gerking, C.; Schubert, D. Component-based refinement and verification of information-flow security policies for cyber-physical microservice architectures. In Proceedings of the IEEE International Conference on Software Architecture (ICSA), Hamburg, Germany, 25–29 March 2019; pp. 61–70. [Google Scholar]
- Peng, H.; Liu, C.; Zhao, D.; Ye, H.; Fang, Z.; Wang, W. Security analysis of CPS systems under different swapping strategies in IoT environments. IEEE Access 2020, 8, 63567–63576. [Google Scholar] [CrossRef]
- Beaulaton, D.; Said, N.B.; Cristescu, I.; Fleurquin, R.; Legay, A.; Quilbeuf, J.; Sadou, S. A language for analyzing security of IoT systems. In Proceedings of the 13th Annual Conference on System of Systems Engineering (SoSE), Paris, France, 19–22 June 2018; pp. 37–44. [Google Scholar]
- Desnitsky, V.; Kotenko, I.; Chechulin, A. Configuration-based approach to embedded device security. In Proceedings of the 6th International Conference on Mathematical Methods, Models and Architectures for Computer Network Security (MMM-ACNS), St. Petersburg, Russia, 17–19 October 2012; pp. 270–285. [Google Scholar]
- Geldenhuys, M.K.; Thamsen, L.; Gontarskay, K.K.; Lorenz, F.; Kao, O. Effectively testing system configurations of critical iot analytics pipelines. In Proceedings of the IEEE International Conference on Big Data (Big Data), Los Angeles, CA, USA, 9–12 December 2019; pp. 4157–4162. [Google Scholar]
- Meng, Y.; Li, J. Research on intelligent configuration method of mine IoT communication resources based on data flow behavior. IEEE Access 2020, 8, 172065–172075. [Google Scholar] [CrossRef]
- Alberca, C.; Pastrana, S.; Suarez-Tangil, G.; Palmieri, P. Security analysis and exploitation of arduino devices in the internet of things. In Proceedings of the ACM International Conference on Computing Frontiers, Como, Italy, 16–19 May 2016; pp. 437–442. [Google Scholar]
- Al-Hadadi, M.; AlShidhani, A. Smartphone forensics analysis: A case study. Int. J. Comput. Electr. Eng. 2013, 5, 576. [Google Scholar] [CrossRef]
- Jeong, Y.; Jung, H.; Lee, J. Cyberslacking or smart work: Smartphone usage log-analysis focused on app-switching behavior in work and leisure conditions. Int. J.-Hum.-Comput. Interact. 2020, 36, 15–30. [Google Scholar] [CrossRef]
- Hasegawa, T.; Koshino, M.; Kimura, H. Analysis of Actual Smartphone Logs for Predicting the User’s Routine Settings of Application Volume. In Proceedings of the IEEE International Conference on Systems, Man, and Cybernetics, Hong Kong, China, 9–12 October 2015; pp. 2654–2659. [Google Scholar]
- Li, Y.; Yang, J.; Ansari, N. Cellular smartphone traffic and user behavior analysis. In Proceedings of the IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 1326–1331. [Google Scholar]
- Taylor, V.F.; Spolaor, R.; Conti, M.; Martinovic, I. Robust smartphone app identification via encrypted network traffic analysis. IEEE Trans. Inf. Forensics Secur. 2017, 13, 63–78. [Google Scholar] [CrossRef]
- Wang, Q.; Yahyavi, A.; Kemme, B.; He, W. I know what you did on your smartphone: Inferring app usage over encrypted data traffic. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), Florence, Italy, 28–30 September 2015; pp. 433–441. [Google Scholar]
- Martin, K.; Shilton, K. Putting mobile application privacy in context: An empirical study of user privacy expectations for mobile devices. Inf. Soc. 2016, 32, 200–216. [Google Scholar] [CrossRef]
- Li, Y.; Guo, Y.; Chen, X. Peruim: Understanding mobile application privacy with permission-ui mapping. In Proceedings of the 2016 ACM International Joint Conference on Pervasive and Ubiquitous Computing, Heidelberg, Germany, 12–16 September 2016; pp. 682–693. [Google Scholar]
- Balapour, A.; Nikkhah, H.R.; Sabherwal, R. Mobile application security: Role of perceived privacy as the predictor of security perceptions. Int. J. Inf. Manag. 2020, 52, 102063. [Google Scholar] [CrossRef]
- Adomnicai, A.; Fournier, J.J.; Masson, L. Hardware security threats against Bluetooth mesh networks. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), Beijing, China, 30 May–1 June 2018; pp. 1–9. [Google Scholar]
- Karimi, K.; Krit, S. Smart home-smartphone systems: Threats, security requirements and open research challenges. In Proceedings of the International Conference of Computer Science and Renewable Energies (ICCSRE), Agadir, Morocco, 22–24 July 2019; pp. 1–5. [Google Scholar]
- Muchagata, J.; Ferreira, A. How can visualization affect security. In ICEIS (2); SciTePress: Funchal, Portugal, 2018; pp. 503–510. [Google Scholar]
- Hussain, S.R.; Echeverria, M.; Karim, I.; Chowdhury, O.; Bertino, E. 5GReasoner: A property-directed security and privacy analysis framework for 5G cellular network protocol. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 669–684. [Google Scholar]
- Altuwaijri, H.; Ghouzali, S. Android data storage security: A review. J. King Saud-Univ.-Comput. Inf. Sci. 2020, 32, 543–552. [Google Scholar] [CrossRef]
- Qamar, A.; Karim, A.; Chang, V. Mobile malware attacks: Review, taxonomy & future directions. Future Gener. Comput. Syst. 2019, 97, 887–909. [Google Scholar]
- Xu, T.; Wendt, J.B.; Potkonjak, M. Security of IoT systems: Design challenges and opportunities. In Proceedings of the IEEE/ACM International Conference on Computer-Aided Design (ICCAD), San Jose, CA, USA, 2–6 November 2014; pp. 417–423. [Google Scholar]
- Choi, S.K.; Yang, C.H.; Kwak, J. System hardening and security monitoring for IoT devices to mitigate IoT security vulnerabilities and threats. KSII Trans. Internet Inf. Syst. 2018, 12, 906–918. [Google Scholar]
- Riahi, A.; Challal, Y.; Natalizio, E.; Chtourou, Z.; Bouabdallah, A. A systemic approach for IoT security. In Proceedings of the IEEE iNternational Conference on Distributed Computing in Sensor Systems, Cambridge, MA, USA, 20–23 May 2013; pp. 351–355. [Google Scholar]
- O’Neill, M. Insecurity by design: Today’s IoT device security problem. Engineering 2016, 2, 48–49. [Google Scholar] [CrossRef]
- Lam, K.Y.; Mitra, S.; Gondesen, F.; Yi, X. Ant-centric iot security reference architecture–security-by-design for satellite-enabled smart cities. IEEE Internet Things J. 2021, 9, 5895–5908. [Google Scholar] [CrossRef]
- Masood, A.; Java, J. Static analysis for web service security-Tools & techniques for a secure development life cycle. In Proceedings of the IEEE International Symposium on Technologies for Homeland Security (HST), Waltham, MA, USA, 14–16 April 2015; pp. 1–6. [Google Scholar]
- Qian, B.; Su, J.; Wen, Z.; Jha, D.N.; Li, Y.; Guan, Y.; Puthal, D.; James, P.; Yang, R.; Zomaya, A.Y.; et al. Orchestrating the development lifecycle of machine learning-based IoT applications: A taxonomy and survey. ACM Comput. Surv. 2020, 53, 1–47. [Google Scholar] [CrossRef]
- Dias, J.P.; Ferreira, H.S. State of the software development life-cycle for the internet-of-things. arXiv 2018, arXiv:1811.04159. [Google Scholar]
- Rahman, L.F.; Ozcelebi, T.; Lukkien, J. Understanding IoT systems: A life cycle approach. Procedia Comput. Sci. 2018, 130, 1057–1062. [Google Scholar] [CrossRef]
- Yousefnezhad, N.; Malhi, A.; Främling, K. Security in product lifecycle of IoT devices: A survey. J. Netw. Comput. Appl. 2020, 171, 102779. [Google Scholar] [CrossRef]
- Kandasamy, K.; Srinivas, S.; Achuthan, K.; Rangan, V.P. IoT cyber risk: A holistic analysis of cyber risk assessment frameworks, risk vectors, and risk ranking process. EURASIP J. Inf. Secur. 2020, 2020, 1–18. [Google Scholar] [CrossRef]
- Zahra, B.F.; Abdelhamid, B. Risk analysis in Internet of Things using EBIOS. In Proceedings of the IEEE 7th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 9–11 January 2017; pp. 1–7. [Google Scholar]
- Nurse, J.R.; Creese, S.; De Roure, D. Security risk assessment in Internet of Things systems. IT Prof. 2017, 19, 20–26. [Google Scholar] [CrossRef]
- Casola, V.; De Benedictis, A.; Rak, M.; Villano, U. Toward the automation of threat modeling and risk assessment in IoT systems. Internet Things 2019, 7, 100056. [Google Scholar] [CrossRef]
- Radanliev, P.; De Roure, D.C.; Nicolescu, R.; Huth, M.; Montalvo, R.M.; Cannady, S.; Burnap, P. Future developments in cyber risk assessment for the internet of things. Comput. Ind. 2018, 102, 14–22. [Google Scholar] [CrossRef]
- Kim, H.; Cho, T.; Ahn, G.J.; Hyun Yi, J. Risk assessment of mobile applications based on machine learned malware dataset. Multimed. Tools Appl. 2018, 77, 5027–5042. [Google Scholar] [CrossRef]
- Kim, K.; Kim, J.; Ko, E.; Yi, J.H. Risk assessment scheme for mobile applications based on tree boosting. IEEE Access 2020, 8, 48503–48514. [Google Scholar] [CrossRef]
- Cheikes, B.A.; Cheikes, B.A.; Kent, K.A.; Waltermire, D. Common Platform Enumeration: Naming Specification Version 2.3; US Department of Commerce, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2011. [Google Scholar]
- Zhang, S.; Caragea, D.; Ou, X. An empirical study on using the national vulnerability database to predict software vulnerabilities. In Proceedings of the International Conference on Database and Expert Systems Applications, Linz, Austria, 31 August–4 September 2011; pp. 217–231. [Google Scholar]
- Pham, V.; Dang, T. Cvexplorer: Multidimensional visualization for common vulnerabilities and exposures. In Proceedings of the IEEE International Conference on Big Data (Big Data), Seattle, WA, USA, 10–13 December 2018; pp. 1296–1301. [Google Scholar]
- Christey, S.; Kenderdine, J.; Mazella, J.; Miles, B. Common Weakness Enumeration. Mitre Corp. 2013. Version 1.0. Available online: https://cwe.mitre.org/documents/views/view-evolution.html (accessed on 2 June 2022).
- Mell, P.; Scarfone, K.; Romanosky, S. Common vulnerability scoring system. IEEE Secur. Priv. 2006, 4, 85–89. [Google Scholar] [CrossRef]
- Feng, Q.; Kazman, R.; Cai, Y.; Mo, R.; Xiao, L. Towards an architecture-centric approach to security analysis. In Proceedings of the 13th Working IEEE/IFIP Conference on Software Architecture (WICSA), Venice, Italy, 5–8 April 2016; pp. 221–230. [Google Scholar]
- Eldefrawy, M.; Butun, I.; Pereira, N.; Gidlund, M. Formal security analysis of LoRaWAN. Comput. Netw. 2019, 148, 328–339. [Google Scholar] [CrossRef]
- Ying, H.; Zhang, Y.; Han, L.; Cheng, Y.; Li, J.; Ji, X.; Xu, W. Detecting buffer-overflow vulnerabilities in smart grid devices via automatic static analysis. In Proceedings of the IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019; pp. 813–817. [Google Scholar]
- Ghanavati, M.; Costa, D.; Andrzejak, A.; Seboek, J. Memory and resource leak defects in java projects: An empirical study. In Proceedings of the 40th International Conference on Software Engineering: Companion Proceeedings, Gothenburg, Sweden, 27 May–3 June 2018; pp. 410–411. [Google Scholar]
- He, X.; Xu, L.; Cha, C. Malicious javascript code detection based on hybrid analysis. In Proceedings of the 25th Asia-Pacific Software Engineering Conference (APSEC), Nara, Japan, 4–7 December 2018; pp. 365–374. [Google Scholar]
- Liu, C.; Chusap, K.; Li, Z.; Chen, Z.; Rogers, D.; Song, F. Continuous collateral privacy risk auditing of evolving autonomous driving software. In Proceedings of the IEEE International Conference on Software Maintenance and Evolution (ICSME), Cleveland, OH, USA, 29 September–4 October 2019; p. 363. [Google Scholar]
- Ali, A.; Al-Perumal, S. Source Code Analysis for Mobile Applications for Privacy Leaks. In Proceedings of the IEEE Madras Section Conference (MASCON), Chennai, India, 27–28 August 2021; pp. 1–6. [Google Scholar]
- Celik, Z.B.; McDaniel, P.; Tan, G. Soteria: Automated {IoT} Safety and Security Analysis. In Proceedings of the USENIX Annual Technical Conference (USENIX ATC 18), Boston, MA, USA, 11–13 July 2018; pp. 147–158. [Google Scholar]
- Hosseinzadeh, S.; Rauti, S.; Hyrynsalmi, S.; Leppänen, V. Security in the internet of things through obfuscation and diversification. In Proceedings of the International Conference on Computing, Communication and Security (ICCCS), Pointe aux Piments, Mauritius, 4–5 December 2015; pp. 1–5. [Google Scholar]
- Shwartz, O.; Mathov, Y.; Bohadana, M.; Elovici, Y.; Oren, Y. Reverse engineering IoT devices: Effective techniques and methods. IEEE Internet Things J. 2018, 5, 4965–4976. [Google Scholar] [CrossRef]
- Feremans, L.; Vercruyssen, V.; Cule, B.; Meert, W.; Goethals, B. Pattern-Based Anomaly Detection in Mixed-Type Time Series. In Proceedings of the Joint European Conference on Machine Learning and Knowledge Discovery in Databases, Würzburg, Germany, 16–20 September 2019; pp. 240–256. [Google Scholar]
- Liu, L.; Zhang, X.; Qiao, M.; Shi, W. SafeShareRide: Edge-based attack detection in ridesharing services. In Proceedings of the IEEE/ACM Symposium on Edge Computing (SEC), Seattle, WA, USA, 25–27 October 2018; pp. 17–29. [Google Scholar]
- Angelini, M.; Bonomi, S.; Borzi, E.; Pozzo, A.D.; Lenti, S.; Santucci, G. An attack graph-based on-line multi-step attack detector. In Proceedings of the 19th International Conference on Distributed Computing and Networking, Varanasi, India, 4–7 January 2018; pp. 1–10. [Google Scholar]
- Fahrenkrog-Petersen, S.A.; Van Der Aa, H.; Weidlich, M. PRETSA: Event log sanitization for privacy-aware process discovery. In Proceedings of the International Conference on Process Mining (ICPM), Aachen, Germany, 24–26 June 2019; pp. 1–8. [Google Scholar]
- Liu, Y.; James, J.; Kang, J.; Niyato, D.; Zhang, S. Privacy-preserving traffic flow prediction: A federated learning approach. IEEE Internet Things J. 2020, 7, 7751–7763. [Google Scholar] [CrossRef]
- Mangset, P.L. Analysis of Mobile Application’s Compliance with the General Data Protection Regulation (GDPR). Master’s Thesis, Norwegian University of Science and Technology (NTNU), Trondheim, Norway, 2018. [Google Scholar]
- Ferrara, P.; Spoto, F. Static Analysis for GDPR Compliance. In Proceedings of the 2nd Italian Conference on Cybersecurity (ITASEC 2018), Milan, Italy, 6–9 February 2018. [Google Scholar]
- Gil González, E.; De Hert, P. Understanding the Legal Provisions That Allow Processing And Profiling of Personal Data—An Analysis of GDPR Provisions and Principles; Era Forum; Springer: Berlin/Heidelberg, Germany, 2019; Volume 19, pp. 597–621. [Google Scholar]
- Galarza, E.E.; Egas, F.D.; Silva, F.M.; Velasco, P.M.; Galarza, E.D. Real time driver drowsiness detection based on driver’s face image behavior using a system of human computer interaction implemented in a smartphone. In Proceedings of the International Conference on Information Technology & Systems, Libertad City, Ecuador, 10–12 January 2018; pp. 563–572. [Google Scholar]
- Kashevnik, A.; Shchedrin, R.; Kaiser, C.; Stocker, A. Driver distraction detection methods: A literature review and framework. IEEE Access 2021, 9, 60063–60076. [Google Scholar] [CrossRef]
- Othman, W.; Kashevnik, A.; Ali, A.; Shilov, N. DriverMVT: In-cabin dataset for driver monitoring including video and vehicle telemetry information. Data 2022, 7, 62. [Google Scholar] [CrossRef]
- Chaudhary, U.; Patel, A.; Patel, A.; Soni, M. Survey paper on automatic vehicle accident detection and rescue system. In Data Science and Intelligent Applications; Springer: Berlin/Heidelberg, Germany, 2021; pp. 319–324. [Google Scholar]
- Lee, T.; Chun, C.; Ryu, S.K. Detection of road-surface anomalies using a smartphone camera and accelerometer. Sensors 2021, 21, 561. [Google Scholar] [CrossRef]
- Guo, H.; Huang, H.; Sun, Y.E.; Zhang, Y.; Chen, S.; Huang, L. Chaac: Real-time and fine-grained rain detection and measurement using smartphones. IEEE Internet Things J. 2018, 6, 997–1009. [Google Scholar] [CrossRef]
- Kashevnik, A.; Lashkov, I.; Ponomarev, A.; Teslya, N.; Gurtov, A. Cloud-based driver monitoring system using a smartphone. IEEE Sens. J. 2020, 20, 6701–6715. [Google Scholar] [CrossRef]
- Dai, J.; Teng, J.; Bai, X.; Shen, Z.; Xuan, D. Mobile phone based drunk driving detection. In Proceedings of the 4th International Conference on Pervasive Computing Technologies for Healthcare, Munich, Germany, 22–25 March 2010; pp. 1–8. [Google Scholar]
- Ramnath, R.; Kinnear, N.; Chowdhury, S.; Hyatt, T. Interacting with Android Auto and Apple CarPlay when driving: The effect on driver performance. In IAM RoadSmart Published Project Report PPR948; IAM RoadSmart: London, UK, 2020. [Google Scholar]
- Wottrich, V.M.; van Reijmersdal, E.A.; Smit, E.G. The privacy trade-off for mobile app downloads: The roles of app value, intrusiveness, and privacy concerns. Decis. Support Syst. 2018, 106, 44–52. [Google Scholar] [CrossRef]
- Levshun, D.; Chevalier, Y.; Kotenko, I.; Chechulin, A. Design and verification of a mobile robot based on the integrated model of cyber-Physical systems. Simul. Model. Pract. Theory 2020, 105, 102151. [Google Scholar] [CrossRef]
- Sun, W.; Cai, Z.; Li, Y.; Liu, F.; Fang, S.; Wang, G. Data processing and text mining technologies on electronic medical records: A review. J. Healthc. Eng. 2018, 2018, 4302425. [Google Scholar] [CrossRef]
- Diba, K.; Batoulis, K.; Weidlich, M.; Weske, M. Extraction, correlation, and abstraction of event data for process mining. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2020, 10, e1346. [Google Scholar] [CrossRef]
- Aßmuth, A.; Duncan, R.; Liebl, S.; Söllner, M. A secure and privacy-friendly logging scheme. In Proceedings of the Cloud Computing 2021: 2th International Conference on Cloud Computing, GRIDs, and Virtualization. International Academy, Research, and Industry Association (IARIA), Porto, Portugal, 18–22 April 2021; pp. 8–12. [Google Scholar]
- Houser, K.A.; Voss, W.G. GDPR: The end of Google and Facebook or a new paradigm in data privacy. Rich. Tech. 2018, 25, 1. [Google Scholar] [CrossRef]
- Levshun, D.; Chechulin, A.; Kotenko, I. Design of Secure Microcontroller-Based Systems: Application to Mobile Robots for Perimeter Monitoring. Sensors 2021, 21, 8451. [Google Scholar] [CrossRef]
- Chakraborty, D.; Hanzlik, L.; Bugiel, S. {simTPM}: User-centric {TPM} for Mobile Devices. In Proceedings of the 28th USENIX Security Symposium (USENIX Security 19), Santa Clara, CA, USA, 14–16 August 2019; pp. 533–550. [Google Scholar]
- Levshun, D.; Kotenko, I.; Chechulin, A. The application of the methodology for secure cyber–physical systems design to improve the semi-natural model of the railway infrastructure. Microprocess. Microsyst. 2021, 87, 103482. [Google Scholar] [CrossRef]
- Levshun, D.; Chechulin, A.; Kotenko, I.; Chevalier, Y. Design and verification methodology for secure and distributed cyber-physical systems. In Proceedings of the 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Canary Islands, Spain, 24–26 June 2019; pp. 1–5. [Google Scholar]



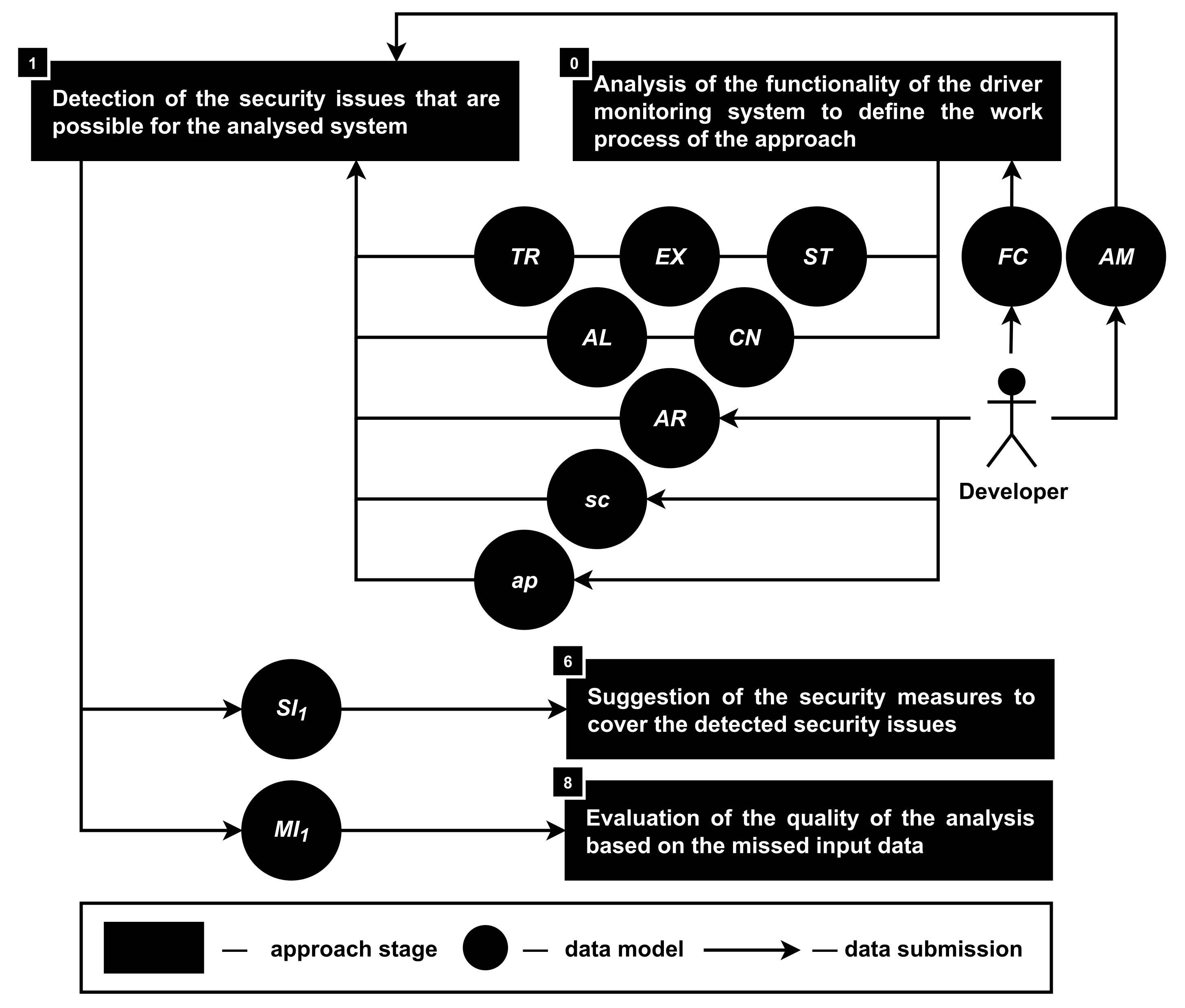

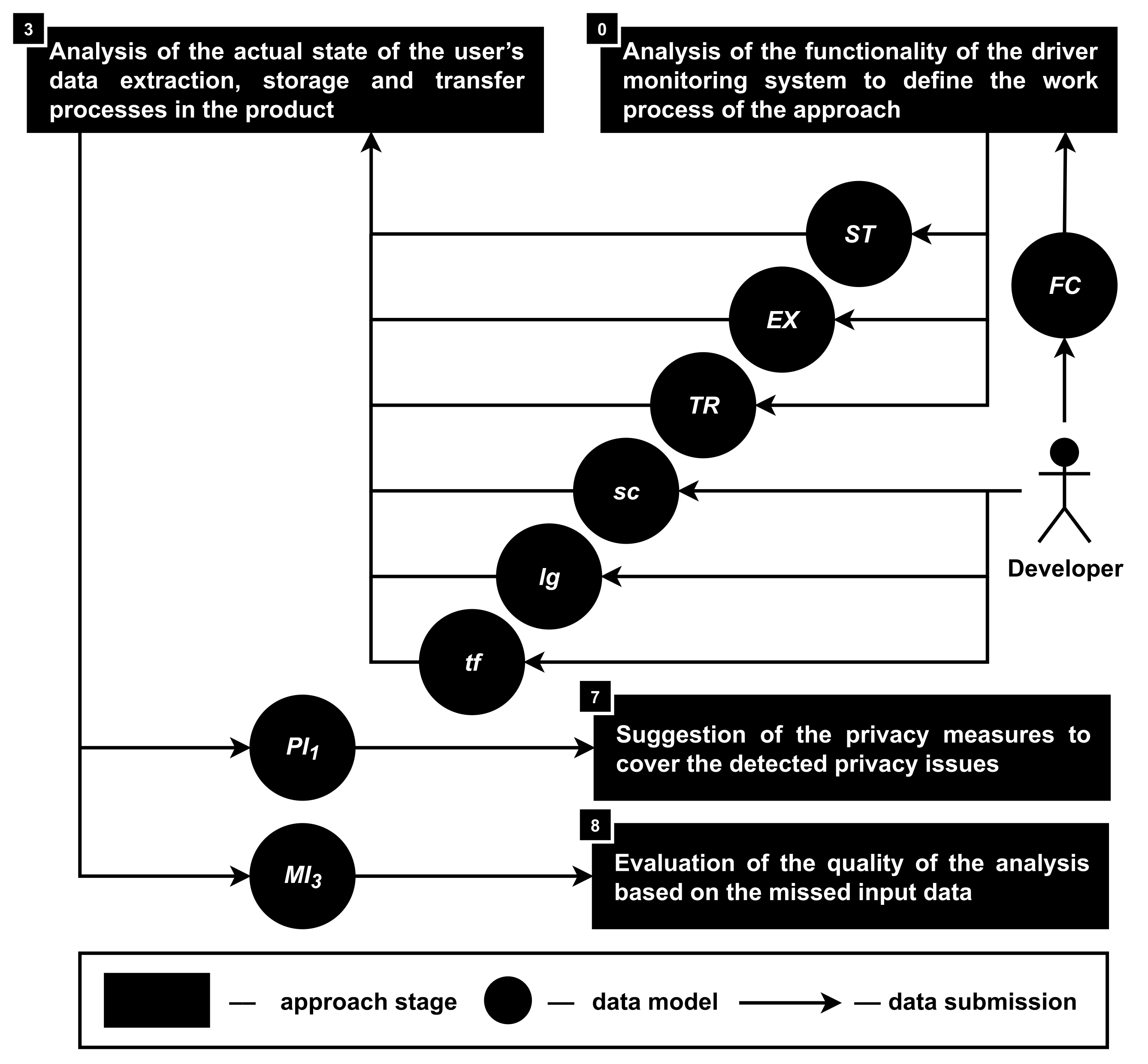





| Object of Analysis | References | Analyzed Data | Provided Data |
|---|---|---|---|
| Functionality | [31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46] | hardware and software elements, interfaces, data transfer protocols, data extraction, storage and transfer processes | security threats, classes of attacks |
| Configuration | [18,47,48,49,50,51,52,53] | platforms and versions of their hardware components, firmware and operating systems, as well as software applications used by them | vulnerabilities, weaknesses, risks |
| Source code | [59,60,61,62,63,64,65,66] | code’s architecture and logic of operation, extraction, storage or transfer of data processes, interactions between elements | detected buffer overflows, memory leaks and code inserts, compliance with privacy policy |
| Logs | [69,70,71,72,73] | events | anomalies, attacks, leakage of user’s sensitive data |
| Traffic | packets | ||
| Documents | [74,75,76] | agreements, legal documents | current state of work with user’s private data and its compliance with legal requirements |
| Issue | Stage | Input | Stage Value | Approach Value |
|---|---|---|---|---|
| 1 | 0.50 | 0.50 | ||
| 0.30 | ||||
| 0.20 | ||||
| 2 | 0.20 | 0.10 | ||
| 0.80 | ||||
| 3 | 0.10 | 0.20 | ||
| 0.50 | ||||
| 0.20 | ||||
| 0.20 | ||||
| 4 | 1.00 | 0.10 | ||
| 5 | 0.70 | 0.10 | ||
| 0.30 |
| 2017 | 2018 | 2019 | 2020 | 2021 | Total | |
|---|---|---|---|---|---|---|
| Denial of service | 9 | 21 | 2 | 7 | 1 | 40 |
| Code execution | 20 | 43 | 38 | 43 | 3 | 147 |
| Overflow | 14 | 12 | 9 | 32 | 2 | 69 |
| Memory corruption | 0 | 1 | 11 | 4 | 1 | 17 |
| SQL injection | 0 | 1 | 3 | 5 | 0 | 9 |
| Cross site scripting | 0 | 1 | 0 | 0 | 0 | 1 |
| Directory traversal | 0 | 2 | 0 | 3 | 0 | 5 |
| Bypass | 0 | 11 | 12 | 35 | 4 | 62 |
| Gain information | 21 | 27 | 7 | 32 | 0 | 87 |
| Gain privileges | 0 | 0 | 1 | 3 | 1 | 5 |
| 2017 | 2018 | 2019 | 2020 | 2021 | Total | |
|---|---|---|---|---|---|---|
| Denial of service | 5 | 0 | 0 | 1 | 3 | 9 |
| Code execution | 3 | 13 | 1 | 1 | 6 | 24 |
| Overflow | 1 | 4 | 1 | 1 | 7 | 14 |
| Memory corruption | 0 | 1 | 0 | 0 | 0 | 1 |
| Cross site scripting | 1 | 3 | 4 | 0 | 1 | 9 |
| Directory traversal | 2 | 1 | 0 | 0 | 1 | 4 |
| Bypass | 2 | 0 | 0 | 0 | 2 | 4 |
| Gain information | 11 | 2 | 0 | 0 | 4 | 17 |
| Gain privileges | 2 | 0 | 0 | 1 | 0 | 3 |
| Cross site request forgery | 0 | 1 | 0 | 0 | 0 | 1 |
| Approach | Input Data | Output Data | |||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Functionality [31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46] | + | + | – | – | – | – | – | – | – | + | – | + | – | – | – |
| Configuration [47,48,49,50,51,52,53] | – | + | – | – | + | – | – | + | – | + | – | + | – | – | – |
| Source code [59,60,61,62,63,64,65,66] | – | – | – | + | + | – | – | – | – | + | + | + | + | – | – |
| Logs, traffic [69,70,71,72,73] | – | – | – | – | – | + | – | – | – | + | + | – | – | – | + |
| – | – | – | – | – | – | + | – | – | + | + | – | – | – | + | |
| Documents [74,75,76] | – | – | + | + | – | – | – | – | + | – | + | – | + | – | + |
| Developed | + | + | + | + | + | + | + | + | + | + | + | + | + | + | + |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Levshun, D.; Chechulin, A.; Kotenko, I. Security and Privacy Analysis of Smartphone-Based Driver Monitoring Systems from the Developer’s Point of View. Sensors 2022, 22, 5063. https://doi.org/10.3390/s22135063
Levshun D, Chechulin A, Kotenko I. Security and Privacy Analysis of Smartphone-Based Driver Monitoring Systems from the Developer’s Point of View. Sensors. 2022; 22(13):5063. https://doi.org/10.3390/s22135063
Chicago/Turabian StyleLevshun, Dmitry, Andrey Chechulin, and Igor Kotenko. 2022. "Security and Privacy Analysis of Smartphone-Based Driver Monitoring Systems from the Developer’s Point of View" Sensors 22, no. 13: 5063. https://doi.org/10.3390/s22135063
APA StyleLevshun, D., Chechulin, A., & Kotenko, I. (2022). Security and Privacy Analysis of Smartphone-Based Driver Monitoring Systems from the Developer’s Point of View. Sensors, 22(13), 5063. https://doi.org/10.3390/s22135063








