Robust Zero-Watermarking of Color Medical Images Using Multi-Channel Gaussian-Hermite Moments and 1D Chebyshev Chaotic Map
Abstract
:1. Introduction
- (1)
- Most of the abovementioned moment-based zero-watermarking techniques fail to achieve an acceptable trade-off between imperceptibility and robustness performance.
- (2)
- Most of them utilized the inaccurate zeroth-approximation method to compute the continuous orthogonal moments of integer orders, which results in a group of inaccurate features.
- (3)
- Most of them show low robustness against geometric and noise attacks.
- (4)
- Most of them are limited to the standard gray and color images and are not used in the medical field.
- (5)
- Due to the inaccurate direct computation method used in these algorithms, zero-watermarking algorithms are time-consuming and unsuitable for telemedicine applications.
- We present a new image descriptor called multi-channel Gaussian–Hermite moments of fractional orders (MFrGHMs).
- We utilize a fast and highly accurate kernel-based method to compute (MFrGHMs).
- We propose a zero-watermarking scheme via accurate features of MFrGHMs, then apply it to protect the color medical image.
- We apply a new 1D Chebyshev chaotic map to enhance the security levels of the proposed algorithm.
- The utilization of multi-channel moments significantly reduces the computational complexity.
- Results from numerous experiments indicate that the proposed algorithm has superiority in robustness, security, and time computation.
2. Gaussian–Hermite Moments
2.1. Traditional Gaussian-Hermite Moments of Gray Images
2.2. Fractional-Order Gaussian–Hermite Moments of Gray Images
2.3. Accurate Computation of New Multi-Channel Gaussian-Hermite Moments of Color Images
3. Proposed Zero-Watermarking Algorithm
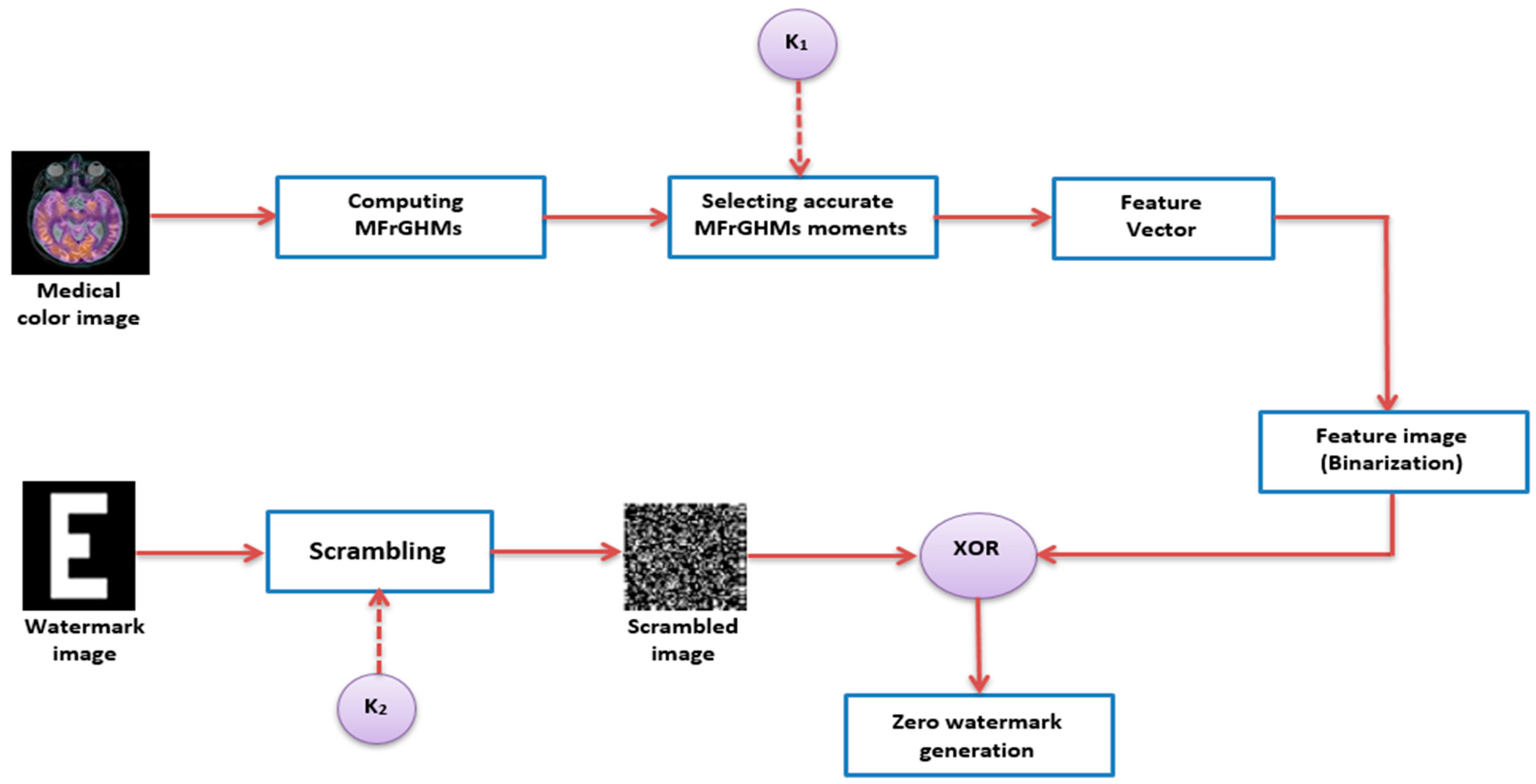
3.1. Watermark Generation
- Step 1: Computing the coefficients of MFrGHMs.
- Step2: Selected Features
- Step 3: Construction of feature vector
- Step 4: Binary Feature Vector
- Step 5: Watermark Scrambling
- Step 6: Generation of the Watermark Image
3.2. Detection of the Watermark
- Step 1: Computation of the coefficients of MFrGHMs
- Step 2: Selection of the precise coefficients
- Step 3: Construction of feature vector
- Step 4: Binary Feature Vector
- Step 5: Generation of the scrambled watermark image
- Step 6: Extraction of watermark image.
4. Experimental Results
4.1. Evaluation Metrics
4.2. Robustness
4.2.1. Common Signal Processing Attacks
4.2.2. Geometric Attacks
4.3. Robustness Comparison with Similar Algorithms
4.4. Computational Time
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| GOFMMs | Generalized Orthogonal Fourier–Mellin Moments |
| QGOFMMs | Quaternion Generalized Orthogonal Fourier–Mellin Moments |
| QPHTs | Quaternion Polar Harmonic Transforms |
| QPHFTs | Quaternion Polar Harmonic Fourier Transforms |
| QPHFMs | Quaternion Polar Harmonic Fourier Moments |
| TPCET | Ternary Polar Cosine Exponent Transform |
| MFrGMs | Fractional Genenbauer Moments of Fractional Orders |
| FoRHFMs | Radial Harmonic Fourier Moment of Fractional Orders |
| QFPJFMs | Quaternion Orthogonal Pseudo-Jacobi–Fourier Moments of Fractional Order |
| MFrGHMs | Multi-channel Gaussian–Hermite Moments of Fractional Orders |
| QLPRHFMs | Quaternion Log-polar Radial Harmonic Fourier Moments |
| FrGHPs | Fractional-order Gaussian–Hermite Polynomials |
| 2D | Two Dimensional |
| 1D | One Dimensional |
| PSNR | Peak Signal-to-noise Ratio |
References
- Aparna, P.; Kishore, P.V.V. A blind medical image watermarking for secure E-healthcare application using crypto-watermarking system. J. Intell. Syst. 2020, 29, 1558–1575. [Google Scholar] [CrossRef]
- Magdy, M.; Ghali, N.I.; Ghoniemy, S.; Hosny, K.M. Multiple Zero-Watermarking of Medical Images for Internet of Medical Things. IEEE Access 2022, 10, 38821–38831. [Google Scholar] [CrossRef]
- Castiglione, A.; Pizzolante, R.; Palmieri, F.; Masucci, B.; Carpentieri, B.; Santis, A.D.; Castiglione, A. On-board format-independent security of functional magnetic resonance images. ACM Trans. Embedded Comput. Syst. 2017, 16, 1–15. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M.; Li, K.; Salah, A. Parallel Multi-core CPU and GPU for Fast and Robust Medical Image Watermarking. IEEE Access 2018, 6, 77212–77225. [Google Scholar] [CrossRef]
- Haddad, S.; Coatrieux, G.; Moreau-Gaudry, A.; Cozic, M. Joint Watermarking-Encryption-JPEG-LS for Medical Image Reliability Control in Encrypted and Compressed Domains. IEEE Trans. Inf. Forensic Secur. 2020, 15, 2556–2569. [Google Scholar] [CrossRef]
- Abdel-Aziz, M.M.; Hosny, K.M.; Lashin, N.A.; Fouda, M.M. Blind Watermarking of Color Medical Images Using Hadamard Transform and Fractional-Order Moments. Sensors 2021, 21, 7845. [Google Scholar] [CrossRef]
- Zhou, X.; Ma, Y.; Zhang, Q.; Mohammed, M.A.; Damaševičius, R. A Reversible Watermarking System for Medical Color Images: Balancing Capacity, Imperceptibility, and Robustness. Electronics 2021, 10, 1024. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M. Invariant image watermarking using accurate polar harmonic transforms. Comput. Electr. Eng. 2017, 62, 429–447. [Google Scholar] [CrossRef]
- Cedillo-Hernandez, M.; Cedillo-Hernandez, A.; Nakano-Miyatake, M.; Perez-Meana, H. Improving the management of medical imaging by using robust and secure dual watermarking. Biomed. Signal Process. Control 2020, 56, 101695. [Google Scholar] [CrossRef]
- Kumar, M.; Aggarwal, J.; Rani, A.; Stephan, T.; Shankar, A.; Mirjalili, S. Secure video communication using firefly optimization and visual cryptography. Artif. Intell. Rev. 2021, 55, 2997–3017. [Google Scholar] [CrossRef]
- Juarez-Sandoval, O.U.; Garcia-Ugalde, F.J.; Cedillo-Hernandez, M.; Ramirez-Hernandez, J.; Hernandez-Gonzalez, L. Imperceptible–Visible Watermarking to Information Security Tasks in Color Imaging. Mathematics 2021, 9, 2374. [Google Scholar] [CrossRef]
- Magdy, M.; Hosny, K.M.; Ghali, N.I.; Ghoniemy, S. Security of medical images for telemedicine: A systematic review. Multimed. Tools Appl. 2022, 81, 25101–25145. [Google Scholar] [CrossRef]
- Wen, Q.T.; Sun, F.; Wang, S.X. Concept and application of zero-watermark. Acta Electron. Sin. 2003, 31, 214–216. [Google Scholar]
- Ren, N.; Zhao, Y.; Zhu, C.; Zhou, Q.; Xu, D. Copyright Protection Based on Zero Watermarking and Blockchain for Vector Maps. ISPRS Int. J. Geo-Inf. 2021, 10, 294. [Google Scholar] [CrossRef]
- Zhou, Q.; Zhu, C.; Ren, N.; Chen, W.; Gong, W. Zero Watermarking Algorithm for Vector Geographic Data Based on the Number of Neighboring Features. Symmetry 2021, 13, 208. [Google Scholar] [CrossRef]
- Chang, C.C.; Lin, P.Y. Adaptive watermark mechanism for rightful ownership protection. J. Syst. Softw. 2008, 81, 1118–1129. [Google Scholar] [CrossRef]
- Zou, B.; Du, J.; Liu, X.; Wang, Y. Distinguishable zero-watermarking scheme with similarity-based retrieval for digital rights Management of Fundus Image. Multimed. Tools Appl. 2018, 77, 28685–28708. [Google Scholar] [CrossRef]
- Liu, J.; Li, J.; Zhang, K.; Bhatti, U.A.; Ai, Y. Zero-watermarking algorithm for medical images based on dual-tree complex wavelet transform and discrete cosine transform. J. Med. Imaging Health Inform. 2019, 9, 188–194. [Google Scholar] [CrossRef]
- Wu, X.; Li, J.; Tu, R.; Cheng, J.; Bhatti, U.A.; Ma, J. Contourlet-DCT based multiple robust watermarking for medical images. Multimed. Tools Appl. 2019, 78, 8463–8480. [Google Scholar] [CrossRef]
- Wang, X.Y.; Wang, L.; Tian, J.L.; Niu, P.P.; Yang, H.Y. Color image zero-watermarking using accurate quaternion generalized orthogonal Fourier–Mellin moments. J. Math. Imaging Vis. 2021, 63, 708–734. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Zhou, W.; Li, R.; Wang, C.; Zhang, C. Color medical image lossless watermarking using chaotic system and accurate quaternion polar harmonic transforms. Signal Process. 2019, 157, 108–118. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Li, X.; Wang, C.; Unar, S.; Wang, M.; Zhao, T. Efficient copyright protection for three CT images based on quaternion polar harmonic Fourier moments. Signal Process. 2019, 164, 368–379. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Wang, M.; Unar, S.; Wang, C.; Liu, Y.; Li, X. Geometrically invariant color medical image null-watermarking based on precise quaternion polar harmonic Fourier moments. IEEE Access 2019, 7, 122544–122560. [Google Scholar] [CrossRef]
- Ma, B.; Chang, L.; Wang, C.; Li, J.; Li, G.; Xia, Z.; Wang, X. Double medical images zero-watermarking algorithm based on the chaotic system and ternary accurate polar complex exponential transform. J. Math. Imaging Vis. 2021, 63, 1160–1178. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Wang, C.; Ma, B.; Wang, M.; Shi, Y.Q. Local quaternion polar harmonic Fourier moments-based multiple zero-watermarking scheme for color medical images. Knowl.-Based Syst. 2021, 216, 106568. [Google Scholar] [CrossRef]
- Niu, P.P.; Wang, L.; Wang, F.; Yang, H.Y.; Wang, X.Y. Fast Quaternion Log-Polar Radial Harmonic Fourier Moments for Color Image Zero-Watermarking. J. Math. Imaging Vis. 2022, 64, 537–568. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M.; Aboelenen, T. New Fractional-order Legendre-Fourier Moments for Pattern Recognition Applications. Pattern Recognit. 2020, 103, 107324. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M.; Aboelenen, T. Novel Fractional-Order Generic Jacobi-Fourier Moments for Image Analysis. Signal Process. 2020, 172, 107545. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M.; Aboelenen, T. Novel Fractional-Order Polar Harmonic Transforms for Gray-scale and Color Image Analysis. J. Frankl. Inst. 2020, 357, 2533–2560. [Google Scholar] [CrossRef]
- Hosny, K.M.; Darwish, M.M. New geometrically invariant multiple zero-watermarking algorithm for color medical images. Biomed. Signal Process. Control 2021, 70, 103007. [Google Scholar] [CrossRef]
- Xia, Z.; Wang, X.; Wang, C.; Wang, C.; Ma, B.; Li, Q.; Wang, M.; Zhao, T. A robust zero-watermarking algorithm for lossless copyright protection of medical images. Appl. Intell. 2021, 52, 607–621. [Google Scholar] [CrossRef]
- Wang, X.; Zhang, Y.; Tian, J.; Niu, P.; Yang, H. Accurate quaternion fractional-order pseudo-Jacobi–Fourier moments. Pattern Anal. Appl. 2022, 1–25. [Google Scholar] [CrossRef]
- Abramowitz, M.; Stegun, I.A. (Eds.) Handbook of Mathematical Functions with Formulas, Graphs, and Mathematical Tables; Applied Mathematics Series; National Bureau of Standards: Washington, DC, USA, 1964; Reprinted by Dover Publications: New York, NY, USA, 1965.
- Yang, B.; Dai, M. Image analysis by Gaussian–Hermite moments. Signal Process. 2011, 91, 2290–2303. [Google Scholar] [CrossRef]
- Yang, B.; Shi, X.; Chen, X. Image Analysis by Fractional-Order Gaussian-Hermite Moments. IEEE Trans. Image Process. 2022, 31, 2488–2502. [Google Scholar] [CrossRef]
- Chandan, S.; Jaspreet, S. Multi-channel versus quaternion orthogonal rotation invariant moments for color image representation. Digit. Signal Prog. 2018, 78, 376–392. [Google Scholar]
- Hosny, K.M.; Darwish, M.M. New set of multi-channel orthogonal moments for color image representation and recognition. Pattern Recognit. 2019, 88, 153–173. [Google Scholar] [CrossRef]
- Faires, J.D.; Burden, R.L. Numerical Methods, 3rd ed.; Brooks Cole Publication: Boston, MA, USA, 2002. [Google Scholar]
- Xin, Y.; Liao, S.; Pawlak, M. Circularly orthogonal moments for geometrically robust image watermarking. Pattern Recognit. 2007, 40, 3740–3752. [Google Scholar] [CrossRef]
- Johnson, K.A.; Becker, J.A. The Whole Brain Atlas. Available online: http://www.med.harvard.edu/AANLIB/home.html (accessed on 19 April 2022).
- Erkan, U.; Toktas, A.; Toktas, F.; Alenezi, F. 2D eπ-map for image encryption. Inf. Sci. 2022, 589, 770–789. [Google Scholar] [CrossRef]










| Attack | Parameter |
|---|---|
| JPEG-Compression | Compression-Ratio: 30%, 50%, 70%, 90% |
| Gaussian-noise | Noise-variance: 0.005, 0.02 |
| “Salt and pepper”-noise | Noise-density: 0.005, 0.02 |
| Median-filtering | Window-size: 3 × 3 |
| Gaussian-filtering | Window-size: 3 × 3 |
| Average-filtering | Window-size: 3 × 3 |
| Applied-Attack | JPEG-(10) | JPEG-(30) | JPEG-(10) | JPEG-(70) |
| Extracted watermark |  |  |  |  |
| BER | 0.0068 | 0.0039 | 0.0029 | 0 |
| NC | 0.9849 | 0.9914 | 0.9936 | 1.0000 |
| Applied-Attack | JPEG-(90) | “Gaussian- Noise” (0.005) | “Gaussian- Noise” (0.02) | “Salt and pepper” noise (0.005) |
| Extracted watermark |  |  |  |  |
| BER | 0 | 0 | 0.0039 | 0 |
| NC | 1.0000 | 1.0000 | 0.9914 | 1.0000 |
| Applied-Attack | “Salt and pepper” noise (0.02) | “Median-Filtering” (3 × 3) | “Gaussian-filtering” (3 × 3) | “Average-Filtering” (3 × 3) |
| Extracted watermark |  |  |  |  |
| BER | 0.0020 | 0.0029 | 0.0029 | 0.0039 |
| NC | 0.9957 | 0.9936 | 0.9936 | 0.9914 |
| Attack | Parameter |
|---|---|
| Image rotation | Rotation angles: 50, 150, 250, 450 |
| Image scaling | Scaling factors: 0.5, 0.75, 1.25, 1.5 |
| Length–width ratio changing | Factor (1.0, 0.75) and (0.5, 1.0). Note: The parameters refer to vertically and horizontally scaling. |
| Image flipping | Vertical and horizontal |
| Applied Attack | Rotation# 5° | Rotation# 15° | Rotation# 25° | Rotation# 45° |
| Extracted watermark |  |  |  |  |
| BER | 0 | 0 | 0.0039 | 0.0010 |
| NC | 1.0000 | 1.0000 | 0.9914 | 0.9979 |
| Applied Attack | Scaling# 0.5 | Scaling# 0.75 | Scaling# 1.5 | Scaling# 2.0 |
| Extracted watermark |  |  |  |  |
| BER | 0.0029 | 0.0020 | 0.0010 | 0 |
| NC | 0.9936 | 0.9957 | 0.9979 | 1.0000 |
| Applied Attack | LWR (1.0, 0.75) | LWR (0.5, 1.0) | Horizontal-flipping | Vertical- Flipping |
| Extracted watermark |  |  |  |  |
| BER | 0.0049 | 0.0068 | 0.0010 | 0.0010 |
| NC | 0.9892 | 0.9849 | 0.9979 | 0.9979 |
| Attacks | Scheme [20] | Scheme [22] | Scheme [23] | Scheme [26] | Scheme [30] | Scheme [32] | Proposed | |
|---|---|---|---|---|---|---|---|---|
| Rotation | 5 | 0.0000 | 0.0037 | 0.0015 | 0.0000 | 0.0011 | 0.0000 | 0.0000 |
| 45 | 0.0000 | 0.0042 | 0.0044 | 0.0000 | 0.0015 | 0.0000 | 0.0000 | |
| Scaling | 0.25 | 0.0002 | 0.0274 | 0.0410 | 0.0048 | 0.0054 | 0.0000 | 0.0001 |
| 4.0 | 0.0001 | 0.0020 | 0.0001 | 0.0000 | 0.0000 | 0.0000 | 0.0000 | |
| Flipping | H | 0.0000 | 0.0035 | 0.0027 | 0.0000 | 0.0001 | 0.0000 | 0.0000 |
| V | 0.0000 | 0.0048 | 0.0036 | 0.0000 | 0.0002 | 0.0000 | 0.0000 | |
| Upper left corner cropping | 1/16 | 0.0002 | 0.0000 | 0.0000 | 0.0000 | 0.0000 | 0.0000 | 0.0000 |
| 1/8 | 0.0050 | 0.0000 | 0.0000 | 0.0000 | 0.0000 | 0.0000 | 0.0000 | |
| JPEG compression | 30 | 0.0007 | 0.0054 | 0.0079 | 0.0000 | 0.0034 | 0.0000 | 0.0002 |
| 70 | 0.0009 | 0.0037 | 0.0030 | 0.0000 | 0.0020 | 0.0011 | 0.0000 | |
| Median filtering | 3 × 3 | 0.0039 | 0.0098 | 0.0342 | 0.0048 | 0.0035 | 0.0038 | 0.0013 |
| Gaussian filtering | 3 × 3 | 0.0001 | 0.0024 | 0.0015 | 0.0000 | 0.0015 | 0.0000 | 0.0000 |
| Salt and pepper noise | 0.01 | 0.0009 | 0.0260 | 0.0249 | 0.0048 | 0.0027 | 0.0011 | 0.0005 |
| Gaussian-noise | 0.01 | 0.0077 | 0.0200 | 0.0273 | 0.0048 | 0.0039 | 0.0106 | 0.0029 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khafaga, D.S.; Karim, F.K.; Darwish, M.M.; Hosny, K.M. Robust Zero-Watermarking of Color Medical Images Using Multi-Channel Gaussian-Hermite Moments and 1D Chebyshev Chaotic Map. Sensors 2022, 22, 5612. https://doi.org/10.3390/s22155612
Khafaga DS, Karim FK, Darwish MM, Hosny KM. Robust Zero-Watermarking of Color Medical Images Using Multi-Channel Gaussian-Hermite Moments and 1D Chebyshev Chaotic Map. Sensors. 2022; 22(15):5612. https://doi.org/10.3390/s22155612
Chicago/Turabian StyleKhafaga, Doaa Sami, Faten Khalid Karim, Mohamed M. Darwish, and Khalid M. Hosny. 2022. "Robust Zero-Watermarking of Color Medical Images Using Multi-Channel Gaussian-Hermite Moments and 1D Chebyshev Chaotic Map" Sensors 22, no. 15: 5612. https://doi.org/10.3390/s22155612







