Drone Detection and Classification Using Physical-Layer Protocol Statistical Fingerprint
Abstract
:1. Introduction
2. State of the Art
2.1. Video-Based
2.2. Sound-Based
2.3. Radar-Based
2.4. RF-Based
2.5. WiFi-Based
2.6. Fusion-Based
3. Methodology
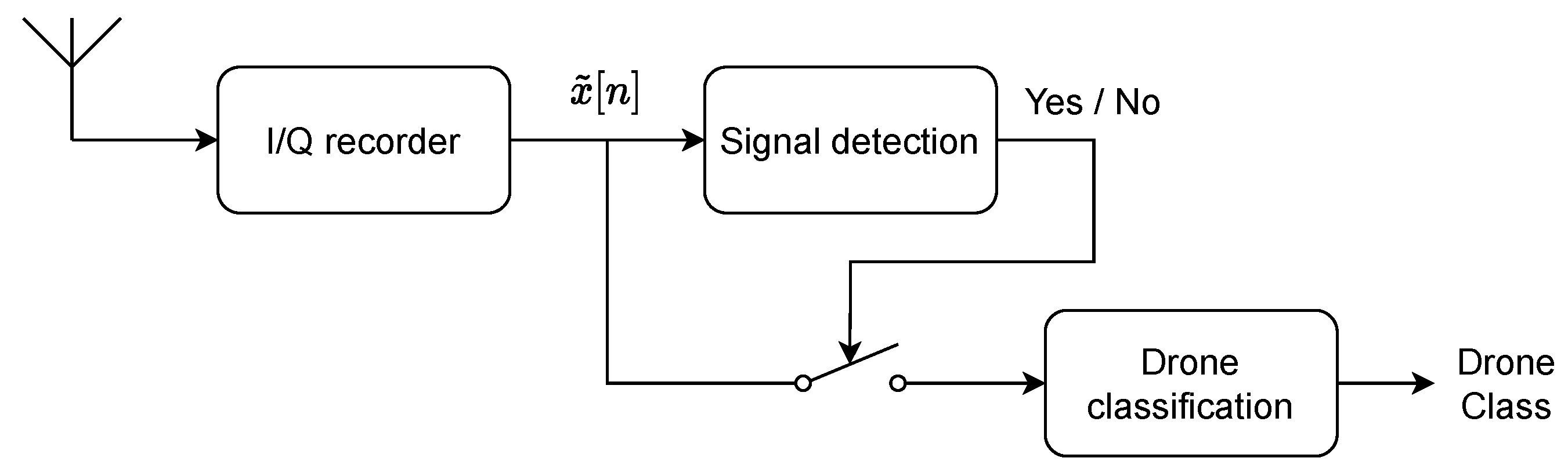
3.1. Global Architecture
3.2. Dataset
3.3. Noise Injection
3.4. Signal Detection: Power Spectral Entropy (PSE)
- 1.
- The first step estimate PSD with , we choose Bartlett estimator [21] (N = 2048, ) instead of periodogram due to its consistency properties.
- 2.
- Then normalize the PSD to obtain the so-called frequency probability density function (FPDF) .
- 3.
- After estimating the FPDF, we compute the entropy to obtain the PSE.
- 4.
- Finally, we compare the PSE to a specific threshold (computed for a specific false alarm rate) to determine if it correspond to a noise or a signal.
3.5. Drone Classification: Physical-Layer Protocol Statistical Fingerprint (PLPSF)
- Mean of packets duration ()
- Standard deviation of packets duration ()
- Mean of inter-packets duration ()
- Standard of inter-packets duration ()
- Number of packets ()
| Algorithm 1: Hysteresis thresholding |
 |
3.6. Invariances to Environmental Conditions
- Scale invariance : The algorithm is not sensitive to the complex coefficient and so makes the result invariant to homothety and phase rotation due to propagation and amplification. This can be performed thanks to the absolute value function allowing to remove any phase effect including phase rotation. Furthermore, covariant properties of filtering, minimum , maximum and mean computation allow homothety invariance.
- Frequency invariance : The algorithm is not sensitive to the frequency offset due to frequency difference in oscillators (even in same make devices) and/or Doppler shifting. This is handled by absolute value allowing to remove any phase effect including frequency offset.
4. Experimentations
4.1. Detection
4.2. Statistical Robustness of Packets Extraction Method
4.3. Classification
4.4. Parametric Analysis
- Window size: The window size correspond to the segment size and is equal to 100 ms.
- Processing: The first step of packet extraction extract packet using signal envelope ().
- Threshold: The hysteresis thresholding depend of two thresholds: and ().
4.4.1. Window Size
4.4.2. Processing
4.4.3. Threshold
5. Discussion and Perspectives
5.1. Discussion
5.2. Perspectives
- Dataset: Currently, our dataset is limited in terms of classes and recordings. Adding more drones classes and more recordings per drone and thus showing that performances are stable is paramount to prove scalability and generalization of our approach.
- Robust statistics: The features we used for classification algorithm are mean and standard deviation. However, use of robust statistics such as median and interquartile can be interesting because they are less sensitive to outliers.
- Power spectral entropy: We presented a detection approach using PSE, a measure of energy distribution uniformity in the frequency-domain. PSE in time domain could also be used to detect presence of signal to extract packets instead of using hysteresis thresholding and allow better robustness against variable RSSI.
- Clustering: Packets clustering could be used using packet RSSI, frequency aspects or goniometry. Thus, it could be beneficial to separate control link, video link and telemetry link.
- Real-world implementation: In this study, the central frequencies of communication signals were defined manually. For future implementation, it is necessary to study the use of band scanning techniques compatible with our approach but also to study its hardware implementability.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Classification Invariance
Appendix A.1. Scale Invariance
Appendix A.2. Frequency Invariance
Appendix A.3. Variable RSSI

Appendix A.3.1. Processing: Envelope
- : 10.2 m
- : 2.5 m
- : 0.6 m
Appendix A.3.2. Processing: Energy
- : 23.7 m
- : 5.9 m
- : 1.5 m
Appendix B. Detection Invariance
Appendix B.1. Scale Invariance
Appendix B.2. Frequency Invariance
References
- Nguyen, P.; Truong, H.; Ravindranathan, M.; Nguyen, A.; Han, R.; Vu, T. Matthan Drone Presence Detection by Identifying Physical Signatures in the Drone’s RF Communication. In Proceedings of the 15th ACM International Conference on Mobile Systems, Applications, and Services, MobiSys 2017, Niagara Falls, NY, USA, 19–23 June 2017. [Google Scholar]
- Florez, J.; Ortega, J.; Betancourt, A.; García, A.; Bedoya, M.; Botero, J.S. A review of algorithms, methods and techniques for detection UAV and UAS using audio, radiofrequency and video applications. TecnoLógicas 2020, 23, 262–278. [Google Scholar] [CrossRef]
- Taha, B.; Shoufan, A. Machine Learning Based Drone Detection and Classification: State of the art in research. IEEE Access 2019, 7, 138669–138682. [Google Scholar] [CrossRef]
- Robin Radar Systems. 10 Counter-Drone Technologies to Detect and Stop Drones Today. 2021. Available online: https://www.robinradar.com/ (accessed on 25 August 2022).
- Bisio, I.; Garibotto, C.; Lavagetto, F.; Sciarrone, A.; Zappatore, S. Unauthorized Amateur UAV Detection Base of Wifi Statistical Fingerprint Analysis. IEEE Commun. Mag. 2018, 56, 106–111. [Google Scholar] [CrossRef]
- De Wit, J.J.M.; Harmanny, R.I.A.; Premel-Cabic, G. Micro-Doppler analysis of small UAVs. In Proceedings of the 2012 9th European Radar Conference, Amsterdam, The Netherlands, 31 October–2 November 2012. [Google Scholar]
- Pallotta, L.; Clemente, C.; Raddi, A.; Giunta, G. A feature Based Approach for Loaded/Unloaded Drone Classification Exploiting micro-Doppler Signatures. In Proceedings of the 2020 IEEE Radar Conference (RadarConf20), Florence, Italy, 21–25 September 2020. [Google Scholar]
- Bello, A. Radio-Frequency Toolbox for Drone Detection and Classification. Master’s Thesis, Old Dominion University, Norfolk, VA, USA, 2019. [Google Scholar]
- Alaboudi, M.M.; Abu Talib, M.; Nasir, Q. Radio-Frequency-based Techniques of Drone Detection and Classification using Machine Learning. In Proceedings of the 2020 6th International Conference on Robotics and Artificial Intelligence, Singapore, 20–22 November 2020. [Google Scholar]
- Yang, S.; Qin, H.; Liang, X.; Gulliver, T.A. An Improved Unauthorized Unmanned Aerial Vehicle Detection Algorithm Using Radiofrequency-Based Statistical Fingerprint Analysis. Sensors 2019, 19, 274. [Google Scholar] [CrossRef] [PubMed]
- Mototolea, D.; Stolk, C. Detection and Localization of Small Drones Using Commercial Off-the-Sheld FPGA Based Software Defined Radio systems. In Proceedings of the 2018 International Conference on Communications, Bucharest, Romania, 14–16 June 2018. [Google Scholar]
- Nguyen, P.; Ravindranatha, M.; Nguyen, A.; Han, R.; Vu, T. Investigating Cost-Effective RF-based Detection of Drones. In Proceedings of the 2nd Workshop on Micro Aerial Vehicle Networks, Systems, and Applications for Civilian Use, DroNet 2016, Singapore, 26 June 2016. [Google Scholar]
- Fu, H.; Abeywickrama, S.; Zhang, L.; Yuen, C. Low Complexity Portable Passive Drone Signature via SDR-Based Signal Classification. IEEE Commun. Mag. 2018, 56, 112–118. [Google Scholar] [CrossRef]
- Digulescu, A.; Despina-Stoian, C.; Stănescu, D.; Popescu, F.; Enache, F.; Ioana, C.; Rădoi, E.; Rîncu, I.; Șerbănescu, A. New Approach of UAV Movement detection and characterization using Advanced Signal Processing Methods Based on UWB Sensing. Sensors 2020, 20, 5904. [Google Scholar] [CrossRef] [PubMed]
- Alipour-Fanid, A.; Dabaghchian, M.; Wang, N.; Wang, P.; Zhao, L.; Zeng, K. Machine Learning-Based Delay-Aware UAV Detection and Operation Mode Identification over Encrypted Wifi Traffic. IEEE Trans. Inf. Forensics Secur. 2019, 15, 2346–2360. [Google Scholar] [CrossRef]
- Sciancalepore, S.; Ibrahim, O.A.; Oligeri, G.; Di Pietro, R. PiNcH: An effective, efficient, and robust solution to drone detection via network traffic analysis. Comput. Netw. 2020, 168, 107044. [Google Scholar] [CrossRef]
- Thales EagleSHIELD Counter—UAS Solution for Sensitive Sites. Available online: https://www.youtube.com/ (accessed on 25 August 2022).
- Soltani, N.; Sankhe, K.; Dy, J.; Ioannidis, S.; Chowdhury, K. More is Better: Data Augmentation for Channel-Resilient RF Fingerprinting. IEEE Commun. Mag. 2020, 58, 66–72. [Google Scholar] [CrossRef]
- Ozturk, E.; Erden, F.; Guvenc, I. RF-Based Low-SNR Classification of UAV using Convolutional Neural Networks. arXiv 2020, arXiv:2009.05519. [Google Scholar]
- Ezuma, M.; Erden, F.; Anjinappa, C.K.; Ozdemir, O.; Guvenc, I. Detection and Classification of UAV Using RF Fingerprints in the Presence of Interference. IEEE Open J. Commun. Soc. 2019, 1, 60–67. [Google Scholar] [CrossRef]
- Stoica, P.; Moses, R.L. Spectral Analysis of Signals, Petre Stoica and Randolph Moses; Pearson Prentice Hall: Upper Saddle River, NJ, USA, 2004. [Google Scholar]
- Canny, J. A Computational Approach to Edge Detection. IEEE Trans. Pattern Anal. Mach. Intell. 1968, PAMI-8, 679–698. [Google Scholar] [CrossRef]
- Géron, A. Hands-On Machine Learning with Scikit-Learn, Keras, and Tensorflow: Concepts, Tools, and Techniques to Build Intelligent Systems; O’Reilly: Sebastopol, CA, USA, 2019. [Google Scholar]
- Zeng, K.; Govindan, K.; Mohapatra, P. Non-Cryptographic Authentification and Identification in Wireless Network. IEEE Wirel. Commun. 2010, 17, 56–62. [Google Scholar] [CrossRef]
- Dalai, A.K.; Jena, S.K. WDTF: A Techique for Wireless Device Type Fingerprinting. Wirel. Pers. Commun. 2017, 97, 1911–1928. [Google Scholar] [CrossRef]
- Soltanieh, N.; Norouzi, Y.; Yang, Y.; Karmakar, N.C. Review of Radio Frequency Fingerprinting Techniques. IEEE J. Radio Freq. Identif. 2020, 4, 222–233. [Google Scholar] [CrossRef]
- Guo, X.; Zhang, Z.; Chang, J. Survey of Mobile Device Authentication Methods Based on RF fingerprint. In Proceedings of the EEE INFOCOM 2019—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April–2 May 2019. [Google Scholar]
- Brik, V.; Banerjee, S.; Gruteser, M.; Oh, S. Wireless device identification with radiometric signatures. In Proceedings of the 14th ACM International Conference on Mobile Computing and Networking, San Francisco, CA, USA, 14–19 September 2008. [Google Scholar]









| Drone Model | Protocol |
|---|---|
| (a) Parrot Bebop | Wifi |
| (b) Phantom 4 Pro | LightBridge |
| (c) Mavic 2 Pro | Ocusync 2 |
| (d) Parrot Anafi | Wifi |
| (e) Syma X5C | Enhanced Shock Burst |
| (f) Smartphone and AP | Wifi |
| Conditions | (1) | (2) | (3) | (4) |
|---|---|---|---|---|
| (a) | 1 | 0.82 | 0.99 | 1 |
| (b) | 0.99 | 0 | 0.66 | 0.93 |
| (c) | 0.99 | 0 | 0.59 | 0.99 |
| (d) | 0.99 | 0.87 | 0.90 | 0.98 |
| (e) | 0.35 | 0 | 0.22 | 0 |
| Conditions | (1) | (2) | (3) | (4) |
|---|---|---|---|---|
| (a) | 1 | 0.99 | 0.99 | 1 |
| (b) | 0.88 | 0 | 0.91 | 0.91 |
| (c) | 0.86 | 0 | 0.35 | 0.58 |
| (d) | 0.99 | 0.99 | 0.90 | 0.99 |
| (e) | 0.44 | 0 | 0.96 | 0.28 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Morge-Rollet, L.; Le Jeune, D.; Le Roy, F.; Canaff, C.; Gautier, R. Drone Detection and Classification Using Physical-Layer Protocol Statistical Fingerprint. Sensors 2022, 22, 6701. https://doi.org/10.3390/s22176701
Morge-Rollet L, Le Jeune D, Le Roy F, Canaff C, Gautier R. Drone Detection and Classification Using Physical-Layer Protocol Statistical Fingerprint. Sensors. 2022; 22(17):6701. https://doi.org/10.3390/s22176701
Chicago/Turabian StyleMorge-Rollet, Louis, Denis Le Jeune, Frédéric Le Roy, Charles Canaff, and Roland Gautier. 2022. "Drone Detection and Classification Using Physical-Layer Protocol Statistical Fingerprint" Sensors 22, no. 17: 6701. https://doi.org/10.3390/s22176701
APA StyleMorge-Rollet, L., Le Jeune, D., Le Roy, F., Canaff, C., & Gautier, R. (2022). Drone Detection and Classification Using Physical-Layer Protocol Statistical Fingerprint. Sensors, 22(17), 6701. https://doi.org/10.3390/s22176701






