An Anonymous Authentication and Key Update Mechanism for IoT Devices Based on EnOcean Protocol
Abstract
:1. Introduction
- In this paper, we use CPN theory and the Dolev–Yao attacker model to formally analyze the EnOcean protocol. Through a security analysis, we find that the EnOcean protocol is able to provide authentication and message integrity verification services, but the EnOcean protocol does not anonymize the identity information of the communication devices, so attackers can analyze a user’s living habits based on the eavesdropped device identity information. The formal analysis reveals that the EnOcean protocol cannot resist a KCIA.
- To address the above security issues, this paper proposes the EnOcean-A protocol with higher security. The EnOcean-A protocol introduces a trusted third-party server to distribute communication keys to communication devices, and the devices can obtain new communication keys from the trusted third-party server before communication, which can resist KCIA and provide forward security. The EnOcean-A protocol uses a homomorphic hash function to anonymize the device identity information and adds a dynamic update mechanism for device identity information so that an attacker cannot obtain the real identity information of the device, thus providing unlinkability of the device identity information.
- Finally, the security of EnOcean-A protocol is analyzed by a formal analysis method, and it is found that the EnOcean-A protocol has higher security compared with the EnOcean protocol.
2. Related Works
3. Preliminary Knowledge
3.1. EnOcean Protocol
3.2. Homomorphic Hash Function
3.3. CPN Modeling Tool
3.4. Dolev–Yao Attacker Model
- The attacker has access to the open channel. The data transmitted between entities while the protocol is executing can be intercepted, altered, and replayed by the attacker;
- The attacker can encrypt, decrypt, split, and combine the original message through the known content to forge the message content;
- Using the identity of the sensor that was eavesdropped, the attacker can determine whether it was delivered by the same device;
- The attacker can break the long-used key and simulate the device to launch an attack using this key.
4. EnOcean Protocol HCPN Modeling
4.1. EnOcean Protocol Color Set Definition
4.2. Formal Analysis of EnOcean Protocol
4.3. EnOcean Protocol Consistency Analysis
4.4. EnOcean Protocol Security Evaluation Based on Dolev–Yao Attacker Model
4.5. EnOcean Protocol Security Attribute Verification Analysis
5. Device Anonymity and Key Update Scheme Based on EnOcean Protocol
5.1. EnOcean-A Protocol
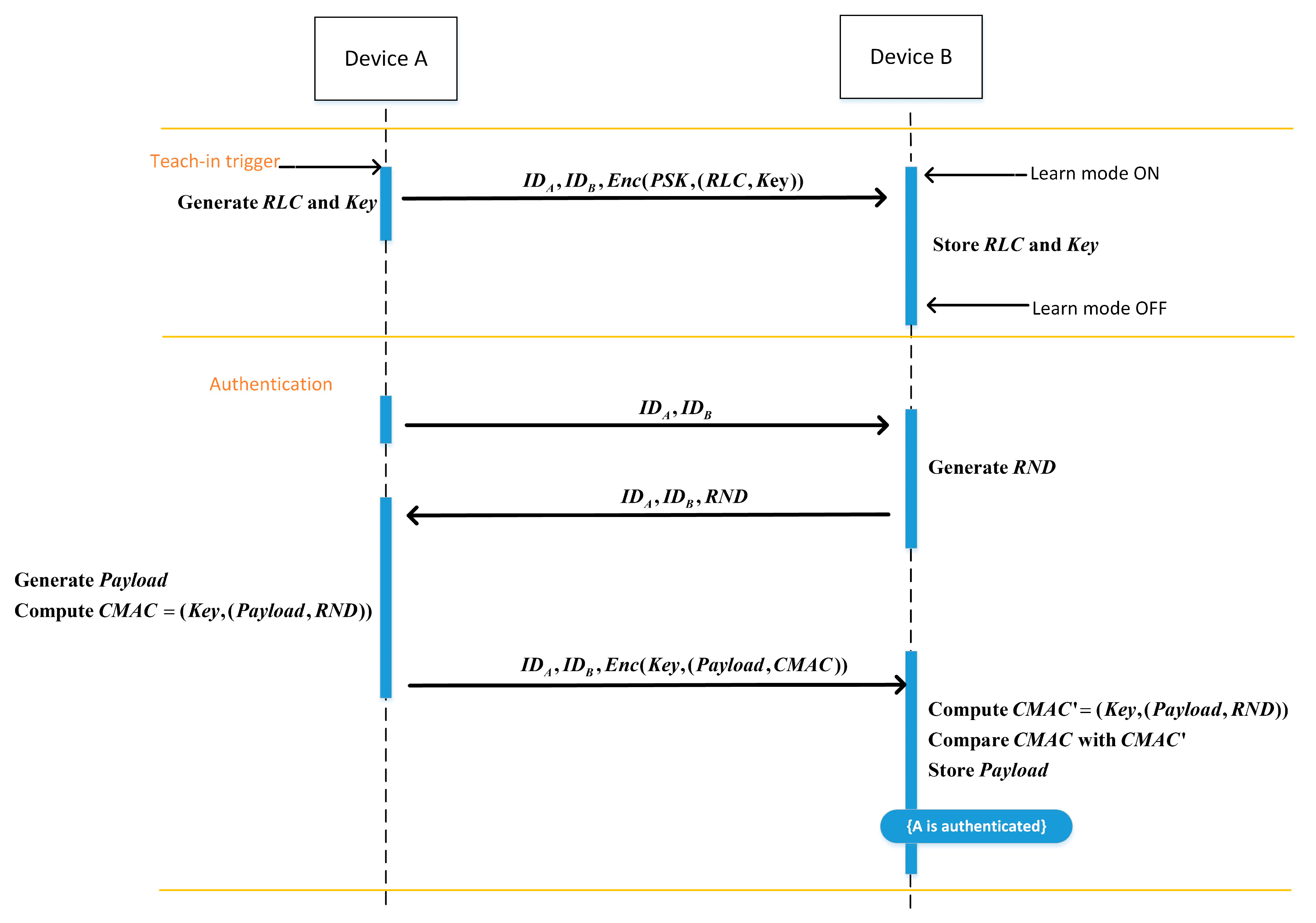
5.2. EnOcean-A Protocol Communication Process
- Teach-in phase:
- Authentication phase:
6. Formal Analysis of EnOcean-A Protocol
6.1. EnOcean-A Protocol HCPN Model
6.2. EnOcean-A Protocol Security Assessment
6.3. EnOcean-A Security Analysis
- Replay attack: The attacker eavesdropped the transmitted data and resent the eavesdropped data to the receiver in the next round of inter-node communication to achieve the purpose of cheating the receiver. In the EnOcean-A protocol, the sender and receiver sent hash values that generated random numbers when communicating with the server, so when the device received a message, it first determined whether the random number hash value in the message already existed; if it did, it directly discarded the message. The teach-in message sent by the sender also included a random number. When the receiver received the message, it checked whether the random number was already received. If it was found that the random number was already received, then the message was discarded directly.
- Impersonation attack: The attacker used the intercepted device identity information to initiate a session request to other devices. In the EnOcean protocol, the attacker could not obtain the device’s identity launch impersonation attack because the device information was anonymized before communication, and the device anonymization information was updated at each communication.
- Tamper attack: The attacker intercepted the message transmitted using plaintext and sent the tampered message to the receiving end. In the EnOcean-A protocol, the sender and receiver used partial hashes of identity for transmission when communicating with the server. Even if an attacker intercepted and tampered with the hash value of the message, when the two communicating parties received the message, they compared it with the hash value of their own saved identity and discarded the message if they found that the hash value was different. In the authentication phase, the sender used the session key to encrypt the calculated CMAC value, and the attacker could not tamper with the message without knowing the session key.
- Eavesdropping attack: The attacker used a passive attack to eavesdrop on the data transmitted in the network and analyzed the data to launch an attack on the node. In the EnOcean-A protocol, since the sender and receiver sent partial hash values of the devices when communicating with the server, even if the attacker eavesdropped on the transmitted messages, they could not construct a complete hash of the device identity.
- KCIA: In the EnOcean-A protocol, the communication key was sent from the trusted third-party server to both communicating parties, and both communicating parties obtained the communication key from the trusted third-party server before each communication. Even if an attacker broke the communication key used during a certain communication, he could not use this communication key to decrypt the contents of messages transmitted before or after. The freshness of the communication key was also guaranteed. This scheme could provide backward and forward security.
- Anonymity: In the EnOcean-A protocol, the sender must obtain the hash of the receiver’s identity from the trusted third-party before communicating with the receiver, and when the sender communicated with the receiver, the sender also used the hash of the identity for message delivery. Therefore, the communication process could ensure the anonymity of device information.
- Unlinkability: In the EnOcean-A protocol, the sender used an updated hash each time it communicated with the trusted third-party, and the trusted third-party server also updated the hash of the receiver. Therefore, the attacker could not deduce the specific communication device from all the hash values eavesdropped after obtaining the communication information.
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Soheilian, M.; Fischl, G.; Aries, M. Smart Lighting Application for Energy Saving and User Well-Being in the Residential Environment. Sustainability 2021, 13, 6198. [Google Scholar] [CrossRef]
- Shen, S. Practice and Research on the Combination of Interior Design and Smart Home in Internet Information Age. In Proceedings of the 2021 International Conference on Computer Technology and Media Convergence Design (CTMCD), Sanya, China, 23–25 April 2021; pp. 273–276. [Google Scholar]
- Schomakers, E.M.; Hannah, B.; Martina, Z. Users’ Preferences for Smart Home Automation–Investigating Aspects of Privacy and Trust. Telemat. Inform. 2021, 64, 101689. [Google Scholar] [CrossRef]
- Iqbal, W.; Haider, A.; Bilal, R.; Yawar, A.; Faisal, A.; Ahmed, H. PCSS: Privacy Preserving Communication Scheme for SDN Enabled Smart Homes. IEEE Sens. J. 2021, 1, 7779. [Google Scholar] [CrossRef]
- Ompal; Vishnu, M.M.; Adesh, K. FPGA Integrated IEEE 802.15.4 ZigBee Wireless Sensor Nodes Performance for Industrial Plant Monitoring and Automation. Nucl. Eng. Technol. 2022, 54, 2444–2452. [Google Scholar] [CrossRef]
- Farha., F.; Ning, H. Enhanced Timestamp Scheme for Mitigating Replay Attacks in Secure ZigBee Networks. In Proceedings of the 2019 IEEE International Conference on Smart Internet of Things (SmartIoT), Tianjin, China, 9–11 August 2019; pp. 469–473. [Google Scholar] [CrossRef]
- Khanji, S.; Farkhund, I.; Patrick, H. ZigBee Security Vulnerabilities: Exploration and Evaluating. In Proceedings of the 2019 10th International Conference on Information and Communication Systems (ICICS), Irbid, Jordan, 11–13 June 2019; pp. 52–57. [Google Scholar]
- Chen, X.Y.; Chen, Y.X.; Yu, Q.M. Smart Home System with Bluetooth and Wi-Fi as Communication Mode. In Proceedings of the 2021 International Conference on Digital Society and Intelligent Systems (DSInS), Chengdu, China, 19–21 November 2021; pp. 143–147. [Google Scholar]
- Mori, G.N.; Swaminarayan, P.R. Measuring IoT Security Issues and Control Home Lighting System by Android Application Using Arduino Uno and HC-05 Bluetooth Module. In Data Science and Intelligent Applications; Springer: Singapore, 2021; pp. 375–382. [Google Scholar]
- Lonzetta, A.M.; Cope, P.; Joseph, C.; Bassam, J.M.; Thaier, H. Security Vulnerabilities in Bluetooth Technology as Used in IoT. J. Sens. Actuator Netw. 2018, 7, 28. [Google Scholar] [CrossRef]
- Zhang, Y.; Jian, W.; Rajib, D.; Jin, Y.E.; Lin, Z.Q.; Fu, X.W. On the (In)Security of Bluetooth Low Energy One-Way Secure Connections Only Mode. arXiv 2019, 1908, 10497. [Google Scholar]
- Arshad, J.; Aziz, M.; Al-Huqail, A.A.; Zaman, M.H.u.; Husnain, M.; Rehman, A.U.; Shafiq, M. Implementation of a LoRaWAN Based Smart Agriculture Decision Support System for Optimum Crop Yield. Sustainability 2022, 14, 827. [Google Scholar] [CrossRef]
- Hofer, F.; Barbara, R. Architecture and Its Vulnerabilities in Smart-Lighting Systems. In Technologies for Smart Cities; Springer: Boston, MA, USA, 2021; pp. 155–181. [Google Scholar] [CrossRef]
- Kannayeram, G.; Madhumitha, M.; Mahalakshmi, S.; Menaga Devi, P.; Monika, K.; Prakash, N.B. Smart Environmental Monitoring Using LoRaWAN. In Proceedings of the 3rd International Conference on Communication, Devices and Computing, Haldia, India, 16–18 August 2022; pp. 513–520. [Google Scholar]
- Hakeem, S.A.A.; El-Kader, S.M.A.; Kim, H. A Key Management Protocol Based on the Hash Chain Key Generation for Securing LoRaWAN Networks. Sensors 2021, 21, 5838. [Google Scholar] [CrossRef]
- Han, J.; Wang, J. An Enhanced Key Management Scheme for LoRaWAN. Cryptography 2018, 2, 34. [Google Scholar] [CrossRef] [Green Version]
- You, I.; Kwon, S.; Choudhary, G.; Sharma, V.; Seo, J.T. An Enhanced LoRaWAN Security Protocol for Privacy Preservation in IoT with a Case Study on a Smart Factory-Enabled Parking System. Sensors 2018, 18, 1888. [Google Scholar] [CrossRef]
- Naoui, S.; Mohamed Elhoucine, E.; Leila, A.S. Novel Enhanced LoRaWAN Framework for Smart Home Remote Control Security. Wirel. Pers. Commun. 2020, 110, 2109–2130. [Google Scholar] [CrossRef]
- Sanchez-Iborra, R.; Sánchez-Gómez, J.; Pérez, S.; Fernández, P.J.; Santa, J.; Hernández-Ramos, J.L.; Skarmeta, A.F. Enhancing LoRaWAN Security through a Lightingweight and Authenticated Key Management Approach. Sensors 2018, 18, 1833. [Google Scholar] [CrossRef] [PubMed]
- Butun, I.; Nuno, P.; Mikael, G. Analysis of LoRaWAN v1.1 Security: Research Paper. In Proceedings of the 4th ACM MobiHoc Workshop on Experiences with the Design and Implementation of Smart Objects, New York, NY, USA, 25 June 2018. [Google Scholar] [CrossRef]
- Tsai, K.L.; Fang-Yie, L.; Li-Ling, H.; Chia-Yin, K. Secure Session Key Generation Method for LoRaWAN Servers. IEEE Access 2020, 8, 54631–54640. [Google Scholar] [CrossRef]
- ISO/IEC 14543-3-10:2012. Available online: http://www.iso.org/cms/render/live/en/sites/isoorg/contents/data/standard/05/98/59865.html (accessed on 6 August 2022).
- Kambourakis, G.; Kolias, C.; Geneiatakis, D.; Karopoulos, G.; Makrakis, G.M.; Kounelis, I. A State-of-the-Art Review on the Security of Mainstream IoT Wireless PAN Protocol Stacks. Symmetry 2020, 12, 579. [Google Scholar] [CrossRef]
- Sadri, M.J.; Asaar, M.R. An Anonymous Two-Factor Authentication Protocol for IoT-Based Applications. Comput. Netw. 2021, 199, 108460. [Google Scholar] [CrossRef]
- Banerjee, S.; Odelu, O.; Das, A.K.; Jangirala, S.; Kumar, N.; Chattopadhyay, S.; Choo, K.K.R. A Provably-Secure and Lightweight Anonymous User Authenticated Session Key Exchange Scheme for Internet of Things Deployment. IEEE Internet Things J. 2019, 6, 8739–8752. [Google Scholar] [CrossRef]
- Fakroon, M.; Alshahrani, M.; Gebali, F.; Traore, I. Secure Remote Anonymous User Authentication Scheme for Smart Home Environment. Internet Things 2020, 9, 100158. [Google Scholar] [CrossRef]
- Hajian, R.; Haghighat, A.; Erfani, S.H. A Secure Anonymous D2D Mutual Authentication and Key Agreement Protocol for IoT. Internet Things 2022, 18, 100493. [Google Scholar] [CrossRef]
- Li, F.Y.; Yu, X.Y.; Yang, C.; Yu, S.Q.; Sun, Y.H.; Wang, Y.L.; Zhou, H.Y. An Anonymous Authentication and Key Agreement Protocol in Smart Living. Comput. Commun. 2022, 186, 110–120. [Google Scholar] [CrossRef]
- Hasan, Q.; Abdelbasit, S.; Alblooshi, H.; Almobaideen, W.; Al-Habashneh, M. Anonymous Authentication Scheme for Smart Home Environment. In Proceedings of the 2021 International Conference on Electrical, Computer and Energy Technologies (ICECET), Cape Town, South Africa, 9–10 December 2021; pp. 1–6. [Google Scholar]
- Banerjee, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Park, Y. An Efficient, Anonymous and Robust Authentication Scheme for Smart Home Environments. Sensors 2020, 20, 1215. [Google Scholar] [CrossRef]
- Rasheed, A.; Hashemi, R.R.; Bagabas, A.; Young, J.; Badri, C.; Patel, K. Configurable Anonymous Authentication Schemes For The Internet of Things (IoT). In Proceedings of the 2019 IEEE International Conference on RFID (RFID), Phoenix, AZ, USA, 2–4 April 2019; pp. 1–8. [Google Scholar]
- Shuai, M.X.; Yu, N.H.; Wang, H.X.; Xiong, L. Anonymous Authentication Scheme for Smart Home Environment with Provable Security. Comput. Secur. 2019, 86, 132–146. [Google Scholar] [CrossRef]
- Kumar, P.; Braeken, A.; Gurtov, A.; Iinatti, J.; Ha, P.H. Anonymous Secure Framework in Connected Smart Home Environments. IEEE Trans. Inf. Forensics Secur. 2017, 12, 968–979. [Google Scholar] [CrossRef]
- Hofer-Schmitz, K. A Formal Analysis of EnOcean’s Teach-in and Authentication. In Proceedings of the 16th International Conference on Availability, Reliability and Security, Vienna, Austria, 17–20 August 2021; pp. 1–8. [Google Scholar] [CrossRef]
- Security of EnOcean Radio Networks v2.5. Available online: https://www.enocean-alliance.org/wp-content/uploads/2019/04/Security-of-EnOcean-Radio-Networks-v2_5.pdf (accessed on 6 August 2022).
- Garcia-Escartin, J.C.; Gimeno, V.; Julio José, M.F. Quantum Collision Finding for Homomorphic Hash Functions. arXiv 2021, 2108, 00100. [Google Scholar] [CrossRef]
- Matsunaga, S.; Adachi, N. Message Authentication Scheme for Ad Hoc Networks with Homomorphic Hash Function. In Proceedings of the 2019 2nd World Symposium on Communication Engineering (WSCE), Nagoya, Japan, 20–23 December 2019; pp. 138–141. [Google Scholar]
- Jensen, K.; Kristensen, L.M.; Wells, L. Coloured Petri Nets and CPN Tools for Modelling and Validation of Concurrent Systems. Int. J. Softw. Tools Technol. Transf. 2007, 9, 213–254. [Google Scholar] [CrossRef]
- Ratzer, A.V.; Wells, L.; Lassen, H.M.; Laursen, M.; Qvortrup, J.F.; Stissing, M.S.; Westergaard, M.; Christensen, S.; Jensen, K. CPN Tools for Editing, Simulating, and Analysing Coloured Petri Nets. In Applications and Theory of Petri Nets; Springer: Berlin/Heidelberg, Germany, 2003; pp. 450–462. [Google Scholar]
- Dolev, D.; Yao, A. On the Security of Public Key Protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
















| Main Contribution | Drawbacks | |
|---|---|---|
| Sadri et al. [24] | Proposed a two-factor authentication protocol | These three authentication schemes required user’s physical information and were not applicable to device-to-device authentication protocol |
| Banerjee et al. [25] | Presented a three-factor authentication scheme | |
| Fakroon et al. [26] | Proposed a new authentication scheme that combined physical context | |
| Hajian et al. [27] | Suggested an authentication protocol between two devices | Neither of these protocols used a third-party server. The computational performance of lightweight sensor devices could not perform the key computation and complex encryption algorithms, so such designs were not suitable for communication between lightweight sensor devices with limited computational power and storage space |
| Li et al. [28] | Proposed an anonymous authentication and key negotiation protocol | |
| Hasan et al. [29] | Proposed a lightweight, secure smart home protocol based on mutual anonymous authentication and key negotiation of devices | These two schemes were only applicable for authentication between three points: the user, sensor node, and gateway node. They were not applicable to device-to-device authentication services |
| Banerjee et al. [30] | Suggested a more secure and robust authentication scheme | |
| Rasheed et al. [31] | Proposed a zero-knowledge proof-based authentication mechanism | This approach could be used with a multicast environment’s identity authentication protocol. It was not necessary to authenticate between two nodes |
| Shuai et al. [32] | Proposed an efficient, anonymous authentication scheme based on ECC for smart home environments | The ECC public key encryption scheme was used in this scheme, which has a certain demand on the performance of the device. However, the computational performance of lightweight sensor devices could not accomplish the key computation and the complex encryption algorithm |
| Kumar et al. [33] | Suggested an anonymous security framework for smart home environments | The device information in this scheme did not change dynamically and did not provide untraceability of communication devices |
| Symbol | Definition |
|---|---|
| Chip ID of sending device | |
| Chip ID of receiving device | |
| Sender A, Receiver B | |
| Rolling code | |
| Pre-shared key | |
| Session key | |
| Random number | |
| Payload of telegram | |
| Cipher-based message authentication code | |
| Encryption function |
| Key Elements | Color Set Definition |
|---|---|
| ID | colset ID = with ida | idb; |
| RANDOM | colset RANDOM = with rlc | rndb | rndb’ | none; |
| KEY | colset KEY = with S | SA; |
| PAYLOAD | colset PAYLOAD = STRING; |
| MSG1 | colset MSG1 = record ida:ID × idb:ID × enc:ENC_IN1; |
| MSG2 | colset MSG2 = record ida:ID × idb:ID; |
| MSG3 | colset MSG3 = record ida:ID × idb:ID × rnd:Random; |
| MSG4 | colset MSG4 = record ida:ID × idb:ID × enc2:ENC2; |
| Type | Number |
|---|---|
| State-Space Nodes | 1380 |
| State-Space Arcs | 3582 |
| Scc Graph Nodes | 1380 |
| Scc Graph Arcs | 3582 |
| Dead Marking | 1 |
| Dead Transition | 0 |
| Type | Tamper Attack | Replay Attack | KCIA |
|---|---|---|---|
| State Space Nodes | 7380 | 131 | 4537 |
| State Space Arcs | 24,672 | 280 | 12,318 |
| Scc Graph Nodes | 7380 | 131 | 4537 |
| Scc Graph Arcs | 24,672 | 280 | 12,318 |
| Dead Markings | 1 | 1 | 1 |
| Dead Transitions | 0 | 23 | 0 |
| Symbol | Definition |
|---|---|
| Old ID of device X | |
| New ID of device X | |
| One-way hash function | |
| random number | |
| String | |
| Device name | |
| Rolling data | |
| Payload | |
| SK | Session key |
| CK | Communication key |
| Random number | |
| Hash value of device I’s ID | |
| Device A, Device B, and Server S | |
| Cipher-based message authentication code | |
| XOR operation | |
| Concatenation operation | |
| Encryption function |
| Type | EnOcean-A | Tamper Attack | Replay Attack | KCIA |
|---|---|---|---|---|
| State-Space Nodes | 726 | 48 | 9 | 1326 |
| State-Space Arcs | 944 | 47 | 8 | 2224 |
| Scc Graph Nodes | 726 | 48 | 9 | 1326 |
| Scc Graph Arcs | 944 | 47 | 8 | 2224 |
| Dead Markings | 1 | 1 | 1 | 1 |
| Dead Transitions | 0 | 40 | 81 | 4 |
| Protocol | Tamper Attack | Replay Attack | Impersonation Attack | KCIA | Anonymity | Unlinkability |
|---|---|---|---|---|---|---|
| EnOcean | × | × | √ | √ | √ | √ |
| EnOcean-A | × | × | × | × | × | × |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Y.; Feng, T. An Anonymous Authentication and Key Update Mechanism for IoT Devices Based on EnOcean Protocol. Sensors 2022, 22, 6713. https://doi.org/10.3390/s22176713
Wu Y, Feng T. An Anonymous Authentication and Key Update Mechanism for IoT Devices Based on EnOcean Protocol. Sensors. 2022; 22(17):6713. https://doi.org/10.3390/s22176713
Chicago/Turabian StyleWu, Yi, and Tao Feng. 2022. "An Anonymous Authentication and Key Update Mechanism for IoT Devices Based on EnOcean Protocol" Sensors 22, no. 17: 6713. https://doi.org/10.3390/s22176713






