Collaborative Learning Based Sybil Attack Detection in Vehicular AD-HOC Networks (VANETS)
Abstract
:1. Introduction
- This study aims to detect Sybil’s attack in VANET using a collaborative machine learning technique based on Majority Voting.
- The proposed mechanism employs occasional features to describe a mobility pattern of vehicular nodes, allowing an evaluation of the mobility of real vehicle nodes in front of the inaccurate Sybil node displacement patterns.
- Different Sybil’s and non-Sybil’s scenarios are simulated in VANETS using SUMO and Ns2 for three different vehicle densities to evaluate the performance of the proposed technique in different environments. The data gathered through simulation are used to feed machine learning models.
- Supervised machine learning classifiers including K-Nearest Neighbor (K-NN), Naïve Bayes (NB), Decision Tree (DT), Support Vector Machine (SVM), and Logistic Regression (LR) are used as base classifiers in the proposed mechanism and are applied to the dataset in a parallel fashion.
- Majority voting mechanism based on Hard and Soft is adopted to predict the final output of classifiers
- A comparison between soft and hard majority voting is also presented at the end of the study.
- The results indicate that the proposed mechanism is a suitable strategy for detecting Sybil attacks and preserving VANET service delivery.
2. Related Work
3. System Design
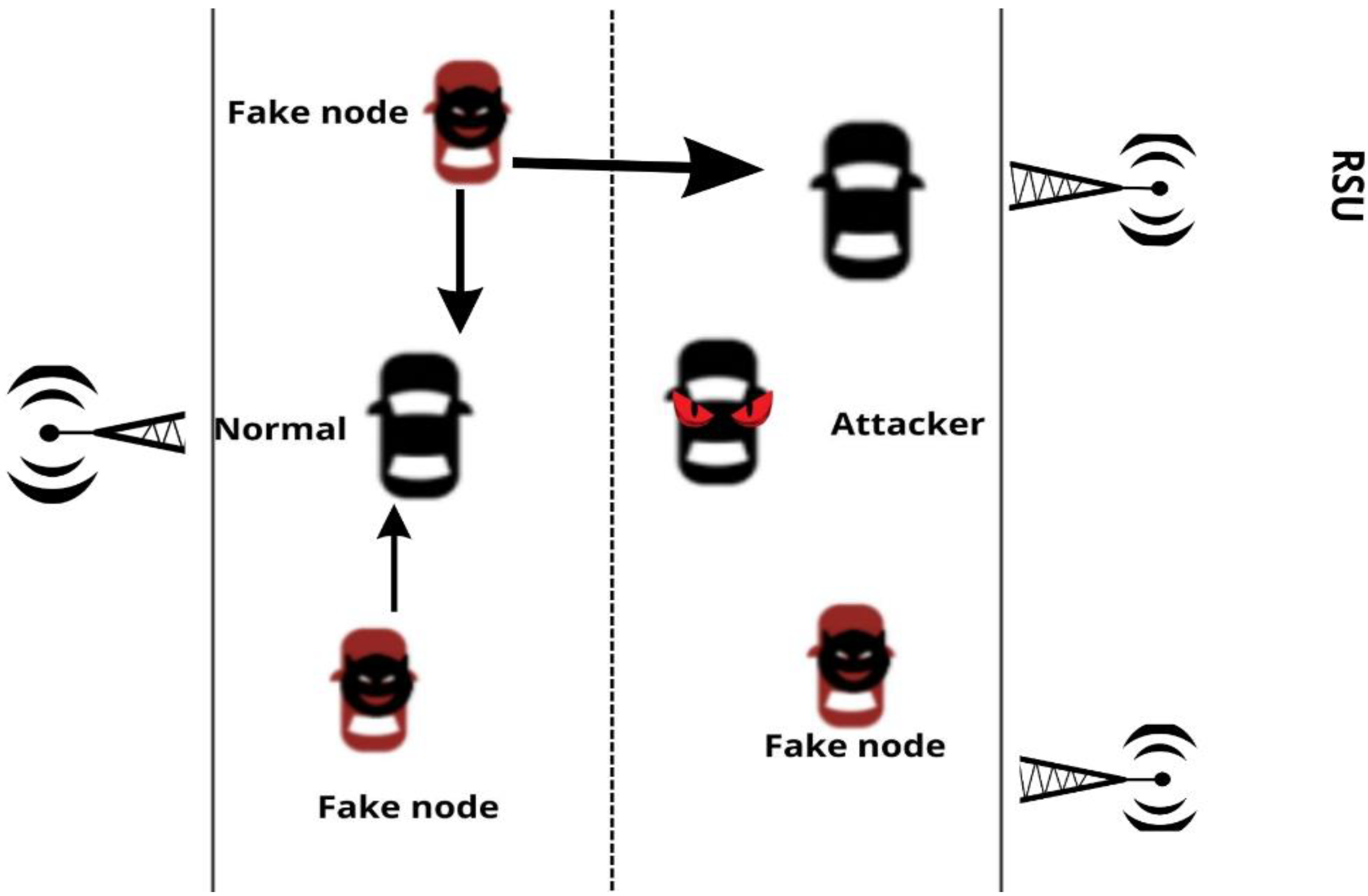
3.1. Simulation Setup and Attack Model
3.2. Traffic Data
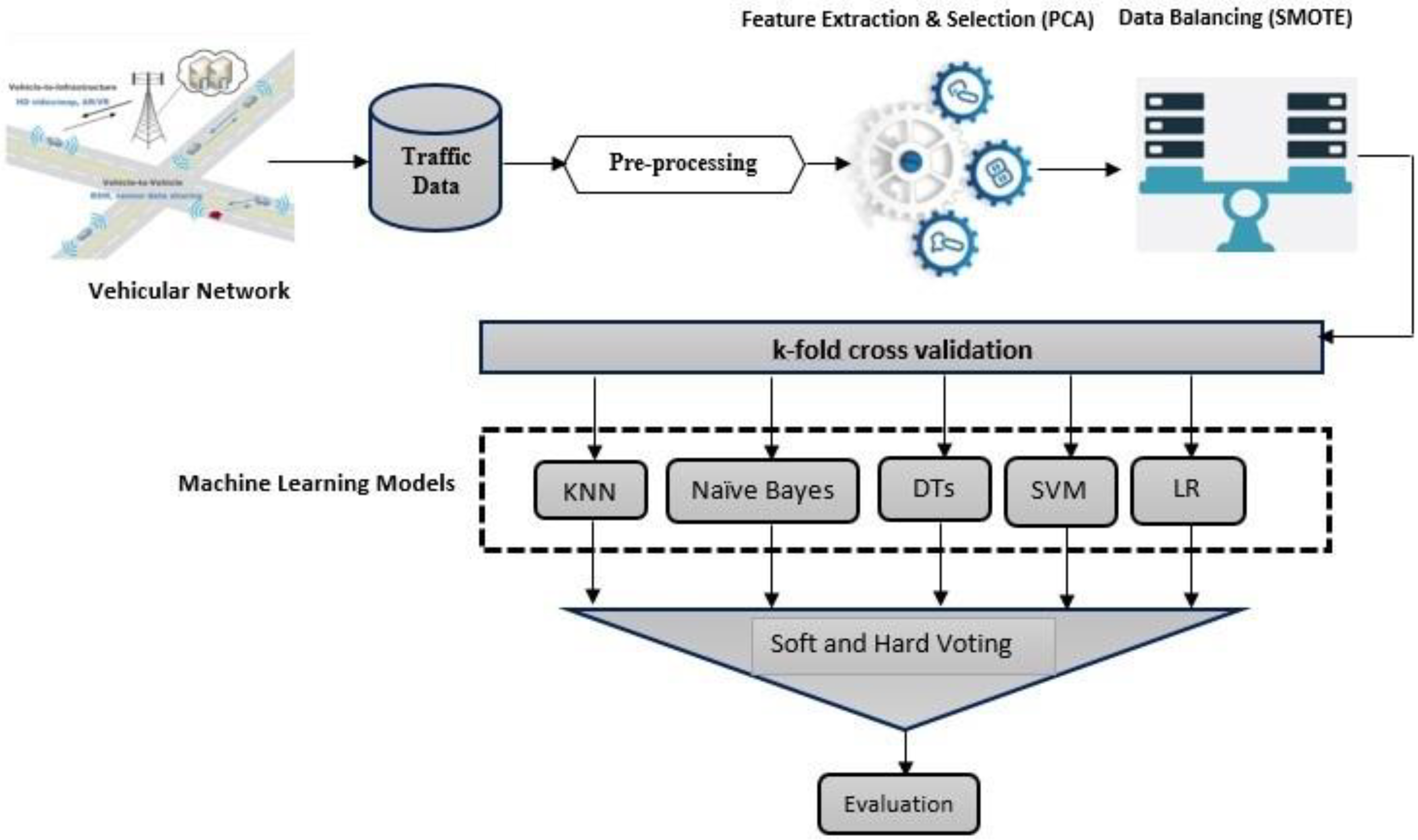
4. Proposed Ensemble Framework for Sybil Node Detection
4.1. Data Pre-Processing
- x x,1 represents vehicle time
- x x,2 represents vehicle location
- x x,3 represents vehicle speed
- x x,4 represents vehicle acceleration
- X x,5 represents acceleration difference
- Centralized the data
- Calculate covariance matrix
- Calculate the eigenvectors of the covariance matrix
- Select m eigenvalues corresponding to m eigenvalues
4.2. Sybil Attack Detection
4.2.1. K-Fold Cross-Validation
4.2.2. K-Nearest Neighbor(K-NN)
4.2.3. Naïve Bayes
4.2.4. Decision Tree
4.2.5. Support Vector Machine (SVM)
4.2.6. Logistic Regression
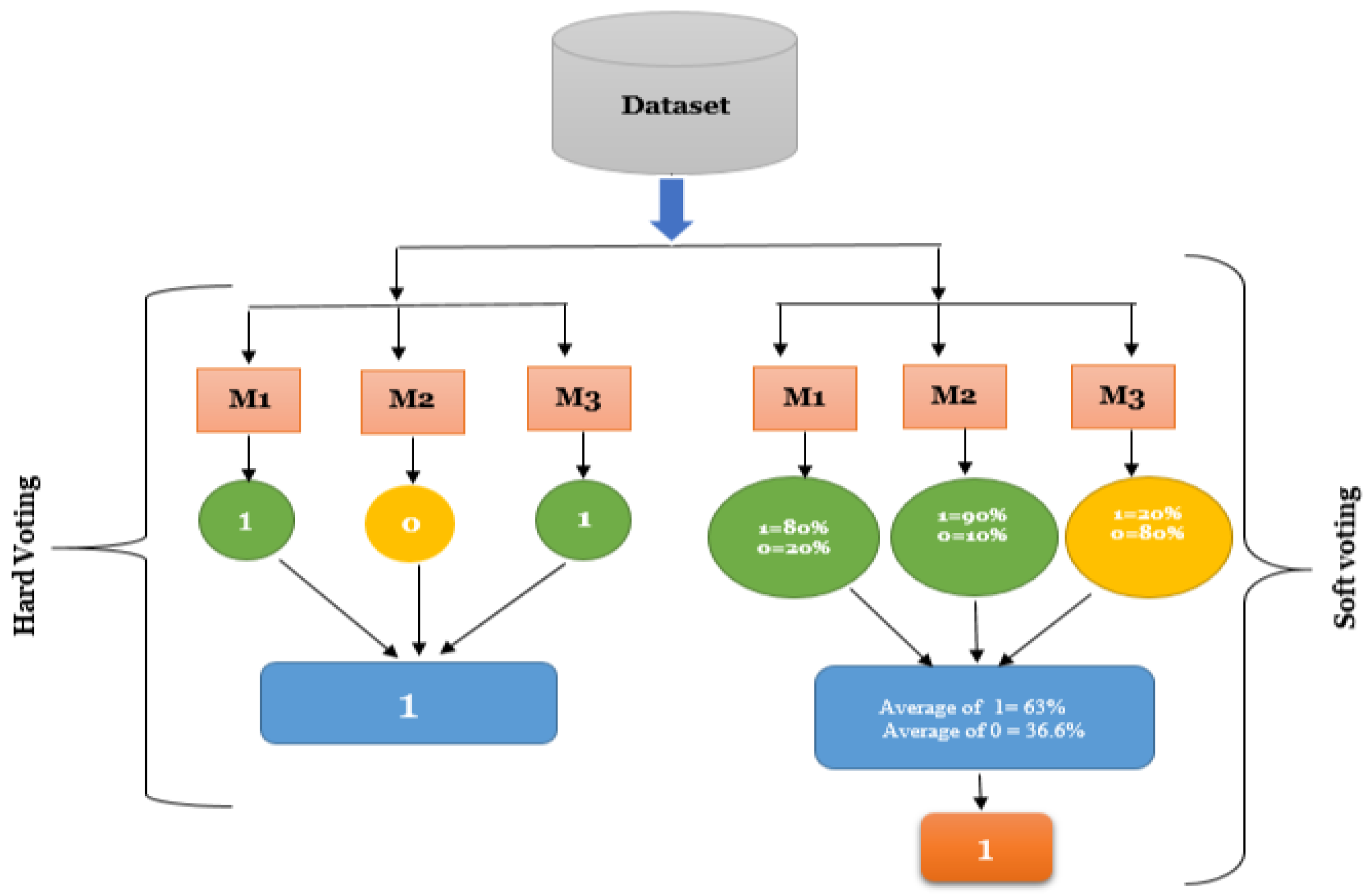
4.2.7. Majority Voting (Hard and Soft)
4.2.8. Evaluations
5. Results and Discussion
- Performance evaluation of proposed ensemble framework using classifiers based on Majority Voting (Hard and Soft)
- Comparative analysis between soft majority voting and hard majority voting methods
- Comparative analysis between the proposed framework and earlier investigated methods used for Sybil node detection
5.1. Performance Evaluation of Majority Voting
5.2. Effect on Applying SMOTE on Dataset
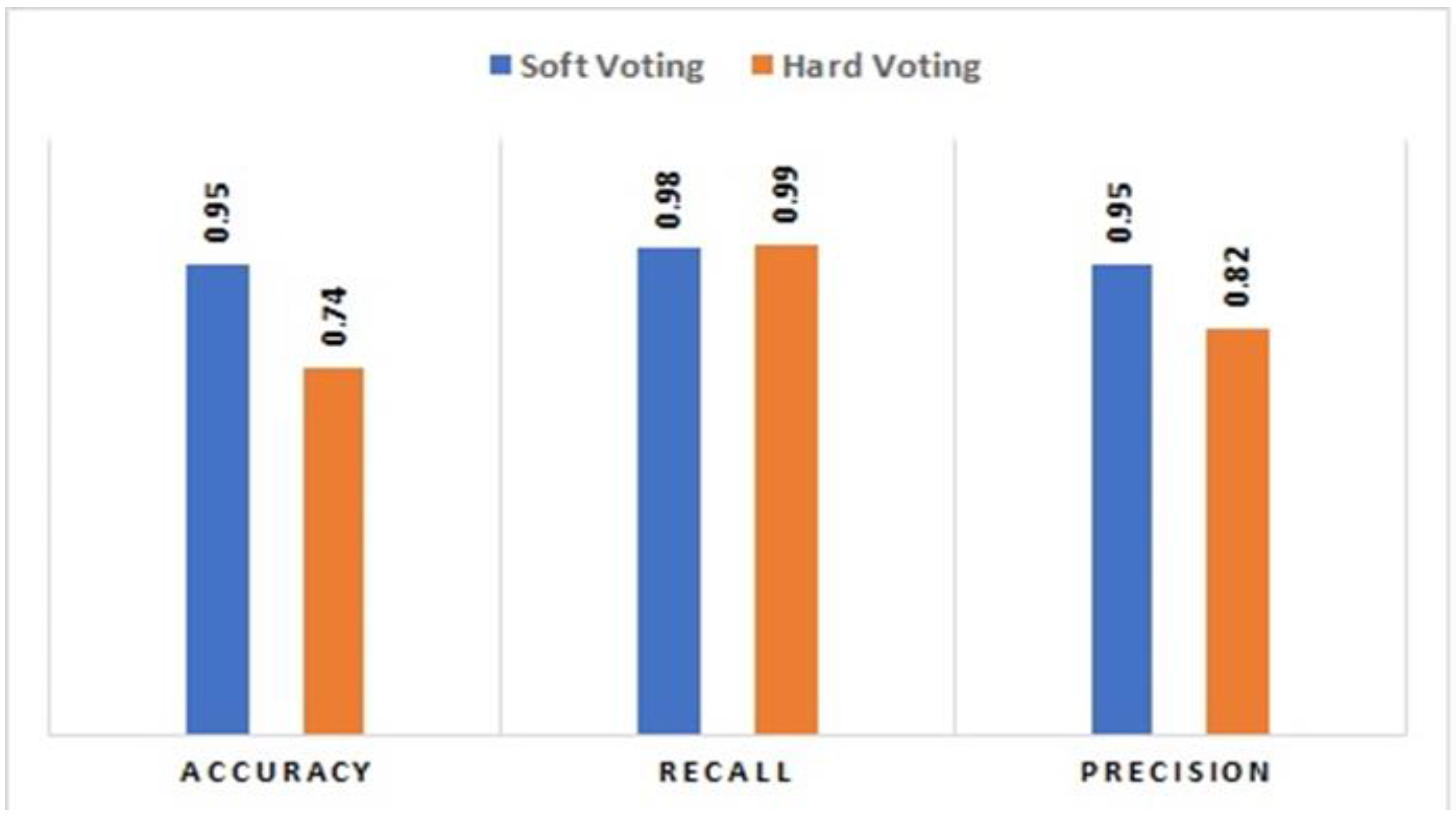
5.3. Comparative Analysis between Majority Voting Hard and Soft
5.4. Comparative Analysis between the Proposed Ensemble Framework and Earlier Investigated Classifiers
- K-NN shows the same performance for the dataset of 300 and 500 nodes with accuracy, recall, and precision values of 99%, however Majority Voting soft shows a little decrease in performance as compared to KNN with accuracy, recall and precision values of 97, 98 and 97 percent, respectively.
- For the dataset of 800 nodes the K-NN shows 95% accuracy, 96% recall and 95% precision. Majority Voting Soft has equal performance to K-NN for the 800 nodes dataset. Majority Voting Soft shows accuracy and precision values of 95% same as K-NN, however recall value of Majority Voting Soft is higher as compared to KNN i.e., 98%.
- For the dataset of 300 nodes, SVM shows 89% accuracy, 83% recall and 90% precision. The performance of the proposed Majority Voting Soft is higher for the same data with accuracy, recall, and precision values of 97%, 98%, and 97%, respectively.
- The performance of SVM increases for the dataset of 500 nodes as compared to a dataset of 300 nodes. Now, accuracy and precision values for SVM are 96% and recall is 95%. In comparison to SVM, Majority Voting Soft has a slight increase in performance.
- For 800 nodes data, the performance of SVM decreases to 74 and 82 percent for accuracy and precision, respectively. Performance of SVM usually decreases on large datasets such as network and system data [44]. Majority Voting Soft for the same experiment show 95% accuracy and precision values. However, the recall value for both individual classifier (SVM) and ensemble classifier (Majority Voting Soft) is the same i.e., 98%.
- For the dataset of 300 and 500 nodes, logistic regression shows accuracy and precision of 94%. However, the recall value of logistic regression is higher for 500 nodes as compared to the 300 nodes i.e., 98 percent. In comparison to the same data, the proposed Majority Voting Soft shows higher performance for both datasets.
- Logistic regression shows a high decrease in accuracy for data of 800 nodes in comparison to Majority Voting Soft. Logistic regression shows an accuracy of 74% whereas the accuracy value of Majority voting Soft is 95% which is reasonably high. The recall values for both classifiers are the same i.e., 98%. The precision of Majority Voting Soft is 95% which is greater as compared to the precision values of Logistic regression i.e., 82 percent.
6. Conclusions and Future Directions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mustafa, A.S.; Hamdi, M.M.; Mahdi, H.F.; Abood, M.S. VANET: Towards Security Issues Review. In Proceedings of the 2020 IEEE 5th International Symposium on Telecommunication Technologies (ISTT), Shah Alam, Malaysia, 9–11 November 2020; pp. 151–156. [Google Scholar] [CrossRef]
- Sheikh, M.S.; Liang, J.; Wang, W. A Survey of Security Services, Attacks, and Applications for Vehicular Ad Hoc Networks (VANETs). Sensors 2019, 19, 3589. [Google Scholar] [CrossRef]
- Kadam, N.; Sekhar, K.R. Machine Learning Approach of Hybrid KSVN Algorithm to Detect DDoS Attack in VANET. Int. J. Adv. Comput. Sci. Appl. 2021, 12. [Google Scholar] [CrossRef]
- Malhi, A.; Batra, S.; Pannu, H. Security of Vehicular Ad-hoc Networks: A Comprehensive Survey. Comput. Secur. 2019, 89, 101664. [Google Scholar] [CrossRef]
- Ghaleb, F.A.; Saeed, F.; Al-Sarem, M.; Al-Rimy, B.A.S.; Boulila, W.; Eljialy, A.E.M.; Aloufi, K.; Alazab, M. Misbehavior-Aware On-Demand Collaborative Intrusion Detection System Using Distributed Ensemble Learning for VANET. Electronics 2020, 9, 1411. [Google Scholar] [CrossRef]
- Awan, M.J.; Farooq, U.; Babar, H.M.A.; Yasin, A.; Nobanee, H.; Hussain, M.; Hakeem, O.; Zain, A.M. Real-Time DDoS Attack Detection System Using Big Data Approach. Sustainability 2021, 13, 10743. [Google Scholar] [CrossRef]
- Zaidi, T. An Overview: Various Attacks in VANET. In Proceedings of the 2018 4th International Conference on Computing Communication and Automation (ICCCA), Greater Noida, India, 14–15 December 2018. [Google Scholar] [CrossRef]
- Yao, Y.; Xiao, B.; Yang, G.; Hu, Y.; Wang, L.; Zhou, X. Power Control Identification: A Novel Sybil Attack Detection Scheme in VANETs Using RSSI. IEEE J. Sel. Areas Commun. 2019, 37, 2588–2602. [Google Scholar] [CrossRef]
- Mane, A. Sybil Attack in VANET. 2017. Available online: https://www.semanticscholar.org/paper/Sybil-attack-in-VANET-Mane/438bb036ee8e2ceca11732302241cb76ab475008 (accessed on 31 July 2022).
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Chen, S.; Liu, D.; Li, J. Performance comparison and current challenges of using machine learning techniques in cybersecurity. Energies 2020, 13, 2509. [Google Scholar] [CrossRef]
- Hatim, S.M.; Elias, S.J.; Awang, N.; Darus, M.Y. VANETs and Internet of Things (IoT): A Discussion. Indones. J. Electr. Eng. Comput. Sci. 2018, 12, 218–224. [Google Scholar] [CrossRef]
- Shaukat, K.; Alam, T.M.; Hameed, I.A.; Khan, W.A.; Abbas, N.; Luo, S. A review on security challenges in internet of things (IoT). In Proceedings of the 2021 26th International Conference on Automation and Computing (ICAC), Portsmouth, UK, 2–4 September 2021; pp. 1–6. [Google Scholar]
- Alam, T.M.; Shaukat, K.; Khelifi, A.; Aljuaid, H.; Shafqat, M.; Ahmed, U.; Nafees, S.A.; Luo, S. A Fuzzy Inference-Based Decision Support System for Disease Diagnosis. Comput. J. 2022, bxac068. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Abbas, N.; Alam, T.M.; Tahir, M.E.; Hameed, I.A. An analysis of blessed Friday sale at a retail store using classification models. In Proceedings of the 2021 The 4th International Conference on Software Engineering and Information Management, Yokohama, Japan, 16–18 January 2021; pp. 193–198. [Google Scholar]
- Batool, D.; Shahbaz, M.; Asif, H.S.; Shaukat, K.; Alam, T.M.; Hameed, I.A.; Ramzan, Z.; Waheed, A.; Aljuaid, H.; Luo, S. A Hybrid Approach to Tea Crop Yield Prediction Using Simulation Models and Machine Learning. Plants 2022, 11, 1925. [Google Scholar] [CrossRef]
- Ibrar, M.; Hassan, M.A.; Shaukat, K.; Alam, T.M.; Khurshid, K.S.; Hameed, I.A.; Aljuaid, H.; Luo, S. A Machine Learning-Based Model for Stability Prediction of Decentralized Power Grid Linked with Renewable Energy Resources. Wirel. Commun. Mob. Comput. 2022, 2022, e2697303. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Xu, M. A survey on machine learning techniques for cyber security in the last decade. IEEE Access 2020, 8, 222310–222354. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Chen, S.; Liu, D. Cyber threat detection using machine learning techniques: A performance evaluation perspective. In Proceedings of the 2020 International Conference on Cyber Warfare and Security (ICCWS), Islamabad, Pakistan, 20–21 October 2020; pp. 1–6. [Google Scholar]
- Shaukat, K.; Alam, T.M.; Luo, S.; Shabbir, S.; Hameed, I.A.; Li, J.; Abbas, S.K.; Javed, U. A Review of Time-Series Anomaly Detection Techniques: A Step to Future Perspectives. In Advances in Information and Communication; Springer: Cham, Switzerland, 2021; pp. 865–877. [Google Scholar] [CrossRef]
- Zhou, T.; Choudhury, R.R.; Ning, P.; Chakrabarty, K. P2DAP—Sybil Attacks Detection in Vehicular Ad Hoc Networks. IEEE J. Sel. Areas Commun. 2011, 29, 582–594. [Google Scholar] [CrossRef]
- Reddy, D.S.; Bapuji, V.; Govardhan, A.; Sarma, S.S.V.N. Sybil attack detection technique using session key certificate in vehicular ad hoc networks. In Proceedings of the 2017 International Conference on Algorithms, Methodology, Models and Applications in Emerging Technologies (ICAMMAET), Chennai, India, 16–18 February 2017; pp. 1–5. [Google Scholar] [CrossRef]
- Gu, P.; Khatoun, R.; Begriche, Y.; Serhrouchni, A. Support Vector Machine (SVM) Based Sybil Attack Detection in Vehicular Networks. In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Gu, P.; Khatoun, R.; Begriche, Y.; Serhrouchni, A. k-Nearest Neighbours classification based Sybil attack detection in Vehicular networks. In Proceedings of the 2017 Third International Conference on Mobile and Secure Services (MobiSecServ), Miami Beach, FL, USA, 11–12 February 2017. [Google Scholar] [CrossRef]
- Hamed, H.; Keshavarz-Haddad, A.; Haghighi, S.G. Sybil Attack Detection in Urban VANETs Based on RSU Support. In Proceedings of the Iranian Conference on Electrical Engineering (ICEE), Mashhad, Iran, 8–10 May 2018; pp. 602–606. [Google Scholar] [CrossRef]
- Javed, I.; Tang, X.; Shaukat, K.; Sarwar, M.U.; Alam, T.M.; Hameed, I.A.; Saleem, M.A. V2X-Based Mobile Localization in 3D Wireless Sensor Network. Secur. Commun. Netw. 2021, 2021, e6677896. [Google Scholar] [CrossRef]
- Eziama, E.; Tepe, K.; Balador, A.; Nwizege, K.S.; Jaimes, L.M.S. Malicious Node Detection in Vehicular Ad-Hoc Network Using Machine Learning and Deep Learning. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Lim, K.; Islam, T.; Kim, H.; Joung, J. A Sybil Attack Detection Scheme based on ADAS Sensors for Vehicular Networks. In Proceedings of the 2020 IEEE 17th Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Quevedo, C.H.O.O.; Quevedo, A.M.B.C.; Campos, G.A.; Gomes, R.L.; Celestino, J.; Serhrouchni, A. An Intelligent Mechanism for Sybil Attacks Detection in VANETs. In Proceedings of the ICC 2020—2020 IEEE International Conference on Communications (ICC), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Beg, S.; Anjum, A.; Ahmad, M.; Hussain, S.; Ahmad, G.; Khan, S.; Choo, K.-K.R. A privacy-preserving protocol for continuous and dynamic data collection in IoT enabled mobile app recommendation system (MARS). J. Netw. Comput. Appl. 2021, 174, 102874. [Google Scholar] [CrossRef]
- Helmi, Z.; Adriman, R.; TYArif Walidany, H.; Fatria, M. Sybil Attack Prediction on Vehicle Network Using Deep Learning|Jurnal RESTI (Rekayasa Sistem dan Teknologi Informasi). Available online: https://jurnal.iaii.or.id/index.php/RESTI/article/view/4089 (accessed on 23 August 2022).
- Laouiti, D.E.; Ayaida, M.; Messai, N.; Najeh, S.; Najjar, L.; Chaabane, F. Sybil Attack Detection in VANETs using an AdaBoost Classifier. In Proceedings of the 2022 International Wireless Communications and Mobile Computing (IWCMC), Dubrovnik, Croatia, 30 May–3 June 2022; pp. 217–222. [Google Scholar] [CrossRef]
- Akshaya, K.; Sarath, T.V. Detecting Sybil Node in Intelligent Transport System. In Innovative Data Communication Technologies and Application; Springer: Singapore, 2022; pp. 595–607. [Google Scholar] [CrossRef]
- Velayudhan, N.C.; Anitha, A.; Madanan, M. Sybil attack detection and secure data transmission in VANET using CMEHA-DNN and MD5-ECC. J. Ambient Intell. Humaniz. Comput. 2021. [Google Scholar] [CrossRef]
- Bouk, S.H.; Kim, G.; Ahmed, S.H.; Kim, D. Hybrid Adaptive Beaconing in Vehicular Ad Hoc Networks: A Survey. Int. J. Distrib. Sens. Netw. 2015, 11, 390360. [Google Scholar] [CrossRef]
- Lim, K.G.; Lee, C.H.; Chin, R.K.Y.; Yeo, K.B.; Teo, K.T.K. SUMO enhancement for vehicular ad hoc network (VANET) simulation. In Proceedings of the 2017 IEEE 2nd International Conference on Automatic Control and Intelligent Systems (I2CACIS), Kota Kinabalu, Malaysia, 21 October 2017; pp. 86–91. [Google Scholar] [CrossRef]
- Kumar, K.R.; Karyemsetty, N.; Samatha, B. Performance Analysis of Vehicular Network Scenarios Using SUMO and NS2 Simulators. In Data Engineering and Communication Technology; Springer: Singapore, 2021; pp. 337–344. [Google Scholar] [CrossRef]
- Engoulou, R.; Bellaïche, M.; Pierre, S.; Quintero, A. VANET security surveys. Comput Commun 2014, 44, 1–13. [Google Scholar] [CrossRef]
- Larriva-Novo, X.; Villagrá, V.A.; Vega-Barbas, M.; Rivera, D.; Rodrigo, M.S. An IoT-Focused Intrusion Detection System Approach Based on Preprocessing Characterization for Cybersecurity Datasets. Sensors 2021, 21, 656. [Google Scholar] [CrossRef] [PubMed]
- Naseriparsa, M.; Kashani, M.M.R. Combination of PCA with SMOTE Resampling to Boost the Prediction Rate in Lung Cancer Dataset. Int. J. Comput. Appl. 2013, 77, 33–38. [Google Scholar] [CrossRef]
- Chawla, N.V.; Bowyer, K.W.; Hall, L.O.; Kegelmeyer, W.P. SMOTE: Synthetic Minority Over-sampling Technique. J. Artif. Intell. Res. 2002, 16, 321–357. [Google Scholar] [CrossRef]
- Han, J.; Kamber, M. Data Mining Concept and Techniques; Elsevier: Amsterdam, The Netherlands, 2006. [Google Scholar]
- Carter, J.V.; Pan, J.; Rai, S.N.; Galandiuk, S. ROC-ing along: Evaluation and interpretation of receiver operating characteristic curves. Surgery 2016, 159, 1638–1645. [Google Scholar] [CrossRef] [PubMed]
- Akanbi, O.A.; Amiri, I.S.; Fazeldehkordi, E. Chapter 5—Implementation and Result. In A Machine-Learning Approach to Phishing Detection and Defense; Akanbi, O.A., Amiri, I.S., Fazeldehkordi, E., Eds.; Syngress: Boston, MA, USA, 2015; pp. 55–73. [Google Scholar] [CrossRef]
- Ahmad, I.; Basheri, M.; Iqbal, M.J.; Rahim, A. Performance Comparison of Support Vector Machine, Random Forest, and Extreme Learning Machine for Intrusion Detection. IEEE Access 2018, 6, 33789–33795. [Google Scholar] [CrossRef]


| Proposed ML Techniques | Advantages | Disadvantages | References |
|---|---|---|---|
| SVM and KNN | High detection frequency in a low-density environment. | Computational complexity is high. | [22,23] |
| Deep Learning (In combination with Bayesian and Neural network) | High detection rate in real-time. | Vehicle mobility patterns weren’t taken into account. | [26] |
| Extreme Learning Machine (SyDVELM) | High Performance and less time complexity. | No analysis in the low-density environment. | [28] |
| Deep Learning (Neural Network architecture) | Less time complexity. | Fewer variables were considered in the analysis. Results could be made better by including more variables. | [30] |
| AdaBoost, XGBoost and DT | Tested on the VeReMi dataset, shown good performance. | High time complexity | [31] |
| SVM, Logistic regression and Random Forest | High-performance rate | Less number of vehicles were used in simulation and attack strategy | [32] |
| Collaborative Learning(Majority Voting) | Simple and has High performance | Can be improved when tested with better resources and also with other ensemble techniques |
| Simulation | Constraints |
|---|---|
| Simulator | Sumo and Ns2 |
| Time | 300 s |
| Distance | 1 km |
| Street Lane | Double Lane |
| Vehicle Speed | 40–60 km/h |
| Total number of vehicles in simulation | 300–800 |
| Communication Range | 300 m |
| Time | Location | Speed | Acceleration | Acceleration Difference | |
|---|---|---|---|---|---|
| X-axis | Y-axis | ||||
| 0.753 | 365.804 | 289.84 | 0.4598 | 6.8844 | 6.8843 |
| 0.775 | 335.75 | 144.285 | 0.4513 | 9.0976 | 0.9706 |
| 0.794 | 780.624 | 232.654 | 0.4790 | 15.2455 | 14.7678 |
| 0.800 | 190.757 | 580.954 | 0.3977 | 4.9510 | 4.5510 |
| Classifiers Used in study | 300 Nodes Data | 500 Nodes Data | 800 Nodes Data | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Accuracy | Recall | Precision | Accuracy | Recall | Precision | Accuracy | Recall | Precision | |
| Naïve Bayes | 0.85 | 0.98 | 0.88 | 0.83 | 0.98 | 0.86 | 0.71 | 0.99 | 0.81 |
| Decision Tree | 0.99 | 0.99 | 0.99 | 0.99 | 0.99 | 0.99 | 0.95 | 0.97 | 0.96 |
| K-NN | 0.99 | 0.99 | 0.99 | 0.99 | 0.99 | 0.99 | 0.95 | 0.96 | 0.95 |
| Logistic Regression | 0.94 | 0.96 | 0.94 | 0.94 | 0.98 | 0.94 | 0.74 | 0.98 | 0.82 |
| SVM | 0.89 | 0.83 | 0.90 | 0.96 | 0.97 | 0.96 | 0.74 | 0.98 | 0.82 |
| Hard voting | 0.97 | 0.98 | 0.97 | 0.97 | 0.98 | 0.97 | 0.74 | 0.99 | 0.82 |
| Soft voting | 0.97 | 0.98 | 0.97 | 0.97 | 0.98 | 0.97 | 0.95 | 0.98 | 0.95 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Azam, S.; Bibi, M.; Riaz, R.; Rizvi, S.S.; Kwon, S.J. Collaborative Learning Based Sybil Attack Detection in Vehicular AD-HOC Networks (VANETS). Sensors 2022, 22, 6934. https://doi.org/10.3390/s22186934
Azam S, Bibi M, Riaz R, Rizvi SS, Kwon SJ. Collaborative Learning Based Sybil Attack Detection in Vehicular AD-HOC Networks (VANETS). Sensors. 2022; 22(18):6934. https://doi.org/10.3390/s22186934
Chicago/Turabian StyleAzam, Sofia, Maryum Bibi, Rabia Riaz, Sanam Shahla Rizvi, and Se Jin Kwon. 2022. "Collaborative Learning Based Sybil Attack Detection in Vehicular AD-HOC Networks (VANETS)" Sensors 22, no. 18: 6934. https://doi.org/10.3390/s22186934
APA StyleAzam, S., Bibi, M., Riaz, R., Rizvi, S. S., & Kwon, S. J. (2022). Collaborative Learning Based Sybil Attack Detection in Vehicular AD-HOC Networks (VANETS). Sensors, 22(18), 6934. https://doi.org/10.3390/s22186934







