Abstract
Wireless Sensor Networks (WSNs) enhance the ability to sense and control the physical environment in various applications. The functionality of WSNs depends on various aspects like the localization of nodes, the strategies of node deployment, and a lifetime of nodes and routing techniques, etc. Coverage is an essential part of WSNs wherein the targeted area is covered by at least one node. Computational Geometry (CG) -based techniques significantly improve the coverage and connectivity of WSNs. This paper is a step towards employing some of the popular techniques in WSNs in a productive manner. Furthermore, this paper attempts to survey the existing research conducted using Computational Geometry-based methods in WSNs. In order to address coverage and connectivity issues in WSNs, the use of the Voronoi Diagram, Delaunay Triangulation, Voronoi Tessellation, and the Convex Hull have played a prominent role. Finally, the paper concludes by discussing various research challenges and proposed solutions using Computational Geometry-based techniques.
1. Introduction
Wireless Sensor Networks (WSNs) have attracted considerable global attention recently. These networks enwrap tiny devices, commonly known as sensor nodes. Although these devices have very limited energy and a slow processing speed, they can sense and transmit the collected data from the required area of interest to the sink node for processing. The sensor network life span can be described as the time span for which the sensing task is performed by the network nodes and the time span for which the data is transmitted towards the base station. Due to the hardware disruption of power exhaustion, certain transmitting nodes become unreachable during this phase. The applicability of WSNs has been seen in various fields depending on the working arena; these include: military, security, healthcare, environment, target detection, and data collection. It is pertinent to mention that certain unique qualities are linked to various applications, each requiring specific features from a WSN solution [1,2]. WSNs can be categorized as Terrestrial WSNs, Underwater WSNs, Mobile WSNs, Underground WSNs, and Multimedia WSNs [3,4]. Various redundant issues commonly seen in WSNs are related to coverage and connectivity. Organizing a limited number of sensors optimally in a complex networking environment is also a challenging task. In order to solve these issues in existing literature, many approaches have been proposed to date. The ongoing research on coverage and connectivity improvement has overwhelmingly generated a lot of interest in new researchers [3,5,6,7,8,9,10]. The key focus is on designing and developing energy-efficient networks with a minimum cost.
For an efficient working model, the Prioritized Geometric Area Coverage (PGAC) approach to improve the coverage area based on the Voronoi Diagram is discussed in [11]. Voronoi cells are classified as smaller, medium, and larger cells based on the working direction of the sensor nodes. The working direction of the sensor is selected on the basis of the relationship between the sensor’s covered area and the cell area. This approach benefits from the reduced overlapped area and the increased network lifetime. For better scalability, an energy-efficient hole detection algorithm based on Delaunay Triangulation is given in [12]. In this approach, triangles are categorized as acute, obtuse, and right-angled triangles based on the angles of the Delaunay Triangulations. Efficient deployment of nodes leads to network optimization and directly impacts the overall performance of WSNs. To enhance the target localization accuracy, a Delaunay Triangulation-based method is discussed in [13]. This localization algorithm can also be upgraded from a two-dimensional to a three-dimensional co-ordinates system. For the accurate estimation of the target’s location, the geometric structures such as the triangle or the tetrahedron are identified firstly in the neighborhood of the target. Then, a localization algorithm is used to find the co-ordinates of the target’s location. The dimensions upgrading from two-dimensional to three-dimensional are very useful for practical applications. As a limitation of the proposed work, authors have also suggested verifying the network lifetime and the delay of the proposed algorithm in real-world scenarios for both the two-dimensional and three-dimensional cases. Two algorithms, namely Delaunay Triangulation with moving sensors and the Convex Hull with moving sensors, for the detection and boundary refinement of Intangible Continuous Objects are described in [14]. Firstly, sensors are grouped into covered and uncovered sensor sets. Then, the concepts of Delaunay Triangulation and the Convex Hull are applied to static sensors to determine the rough boundary of the Intangible Continuous Objects. For refinement of the enclosed area of the Intangible Continuous Objects, a moving mechanism is introduced to the sensors in order to adjust their positions. The results show that 135–157% and 102–145% of the actual area of the Intangible Continuous Objects is covered by Delaunay Triangulation with moving sensors and the Convex Hull with moving sensors, respectively. In order to resolve the fundamental issue of node’s positions a Voronoi diagram-based scheme is discussed in [15]. First of all, the whole area is partitioned into several small regions using a Voronoi diagram. Then, to optimize and accurately estimate the position of the target node, a support vector machine is used. The proposed scheme is compared with the Optimal Region Selection Strategy based on the Voronoi and the Weighted Voronoi diagrams. The results show that the proposed localization scheme is better than both of the above-mentioned strategies.
This paper contributes through the following aspects:
- The present study introduces effective methods and ideas for accomplishing a constructive system for modeling WSNs;
- With the help of scientometric analysis, this paper throws light upon the significance of Computational Geometry (CG)-based techniques and their utilization in WSNs;
- It sheds light on the critical role of Computational Geometry-based techniques in addressing issues related to coverage and connectivity, which are considered to be inherent problems of WSNs;
- This opens a new frontier for future research scholars to address the problems of coverage and connectivity holes efficiently and strategically, based on the Computational Geometry techniques in WSNs.
The primary goals of this study are to answer some relevant questions given as follows:
- −
- Q1. How is the issue of coverage and connectivity in WSNs for two-dimensional or three-dimensional networks addressed?
- −
- Q2. How can coverage and connectivity in Directional Senor Networks be improved?
- −
- Q3. How can the issue of coverage and connectivity within the mobile environment (where sensor nodes, target points or both can be in motion) and the heterogeneous environment be addressed?
- −
- Q4. How can the issue of coverage and connectivity when obstacles are present in the environment be addressed?
- −
- Q5. How efficiently can the discovery and healing of coverage and communication holes can be achieved?
- −
- Q6. How perfectly can energy resources be managed?
- −
- Q7. How can the issue of coverage and connectivity on the boundaries of the area of interest be resolved?
This paper briefly recapitulates the importance of CG-based Techniques in WSNs. Section 2 defines the connection between Computational Geometry and WSNs and Section 3 illustrates the role of CG Techniques in improving Coverage and Connectivity in WSNs. Section 4 describes the present research challenges and their solution with the help of CG Techniques. Lastly, Section 5 concludes the paper and provides the scope for future studies.
2. Computational Geometry and WSNs
2.1. Computational Geometry (CG)
Computational Geometry arose in the late 1970s from the field of algorithms design and analysis. It focused on various recurring problems arising from scientific computing, geographic information systems, robotics, computer graphics, and recent scenarios that have gained interest in wireless networks during the nascent stages, wherein geometric algorithms might play a crucial role. Geometric algorithms are developed explicitly to analyze the structural properties and to explore the inclusion and exclusion relationships between two points or hyperplanes (or both). The Convex Hull, the Voronoi Diagram, Triangulation (Regular, Delaunay, and so on), the Hyperplane arrangement, and the Intersections are just a few structural properties [16]. Computational Geometry describes various geometrical objects such as points, line segments, and polygons. The same can be applied to overcome the famous problem in the art gallery, where at least one of the security guards observes the boundary of the gallery [17]. There are a variety of data structures related to Computational Geometry. Some essential data structures are the Voronoi Diagram, Delaunay Triangulation, the Convex Hull, the Largest Empty Circle, the Euclidean Shortest Path, Polygon Triangulation, and the Closest Pair of Points, etc. However, in WSNs, data structures like the Voronoi Diagram, Delaunay Triangulation, Voronoi Tessellation, and the Convex Hull have been used infrequently in recent years. These promising Computational Geometric data structures play a crucial role in node deployment, coverage hole detection, and the healing process.
2.2. The Significance of CG Techniques in WSNs
It is pertinent to mention that network design for a wireless sensor is challenging. An efficient network needs to address a few important issues like limited batteries and memories, fault tolerance, dimensionality, and node location. Figure 1 shows the word cloud of keywords and the size of each keyword determines its importance in the given field.
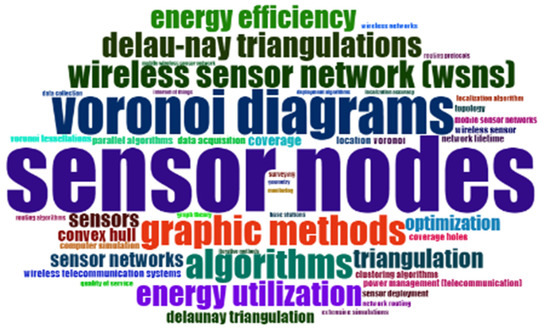
Figure 1.
A word cloud of keywords.
The authors in [16] have described the use of a network topology control that can be constructed locally with a subgraph of the unit disk graph created with the underlying sparse features. The topology control in WSN aims at three things: i.e., maintenance of network connectivity, optimizing network lifetime, and designing power-efficient routing. The authors have also focused on the power expansion factor of numerous sparse geometric structures to be used as the network topology of WSN. It includes geometric structures such as the Low-Weight Structures, the Planar Structures, the Bounded Degree Planar Structures, the Bounded Degree structures, and the Bounded Degree Planar, among others. In WSN, the most common failure observed is an individual node failure. Hence, a fault-free network topology should have multiple-path connectivity between two sensors, including k-connectivity (k ≥ 1).
The authors in [18] have elaborated 14-connectivity and 6-connectivity among nodes by implementing two Voronoi Polyhedrons to maintain a fault-free network: two Voronoi Polyhedron Truncated Octahedron and Hexagonal Prisms to maintain a fault-free network.
The Voronoi Diagram, Voronoi Tessellation, and Delaunay Triangulation are some of the most commonly used geometric structures. These geometric structures facilitate viable solutions for WSN problems such as Coverage assessment, reducing overall memory requirements, avoiding transmission of superfluous communication messages, and network optimization. Also, it is deliberately discussed in [5] that the Voronoi Diagram and the power diagram are also used as solutions for coverage problems in d-dimension (d ≥ 1) WSNs. The authors in [19] have proposed 3D sensors deployment based on Voronoi Tessellation to solve the coverage problem. The authors in [20] have presented a method based on a localized Voronoi Diagram to solve the localization problem in sensor nodes. Directional antennas can provide the necessary location information about neighboring nodes. This algorithm reduces the cost of location-finding devices and power consumption because it does not require a global positioning system.
2.3. Scientometric Analysis of CG and WSN
The scientometric analysis mainly focuses on the scientific study of available literature. This scientometric analysis aims to visualize the impact of the published literature time. This can be done using the information from the literature records such as the keywords, the authors, the countries, and the references. In the present study, the scientometric analysis assesses terms like computational geometry, sensor network, wireless sensor network, coverage, connectivity, and many more related words in the same domain. This scientometric analysis aims to visualize the impact of published literature over time. With this analysis, researchers can trust how influential the core area of their associated research is. Table 1 gives the preliminary information on which this analysis is performed.

Table 1.
The Main Information Needed to Perform Scientometric Analysis.
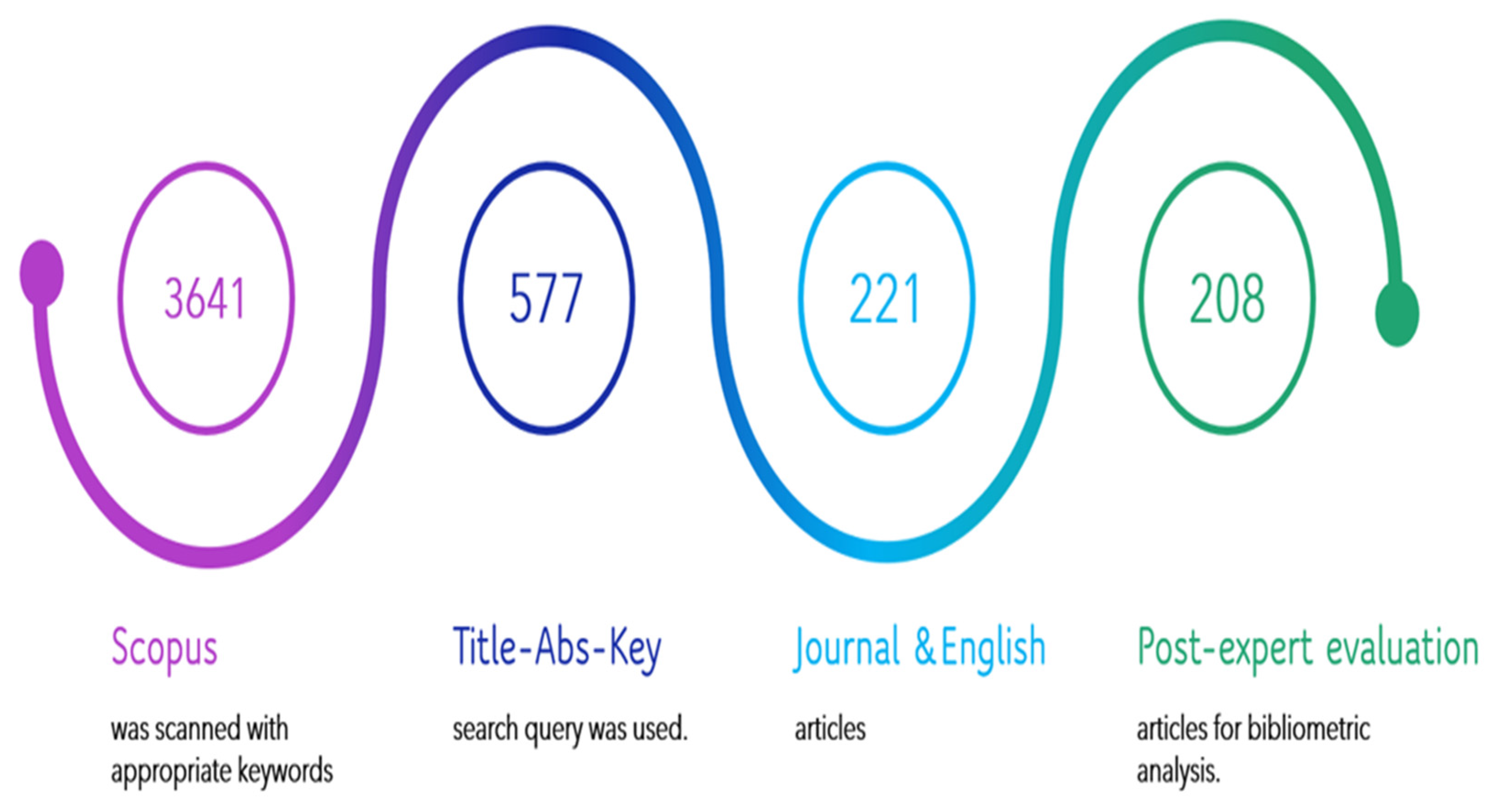
The process of article selection needed for the present study to perform scientometric analysis is represented by Figure 2.
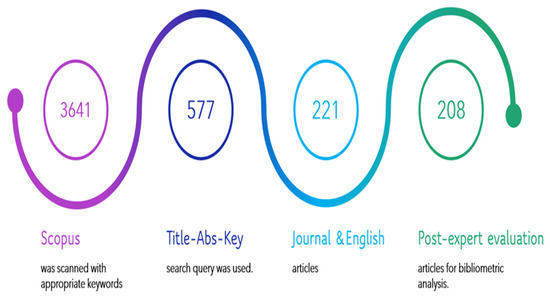
Figure 2.
The Article Selection Process.
This analysis covers (i) how the development of related terms, methods, and techniques cover different countries, (ii) how these are growing with time, and (iii) which authors are associated with, or working with, these terms, methods, and techniques, etc. The information presented in Table 1 has been extracted from the Scopus database and processed using the VOSviewer-Visualizing scientific landscapes, which is basically an online tool to construct and visualize bibliometric networks.
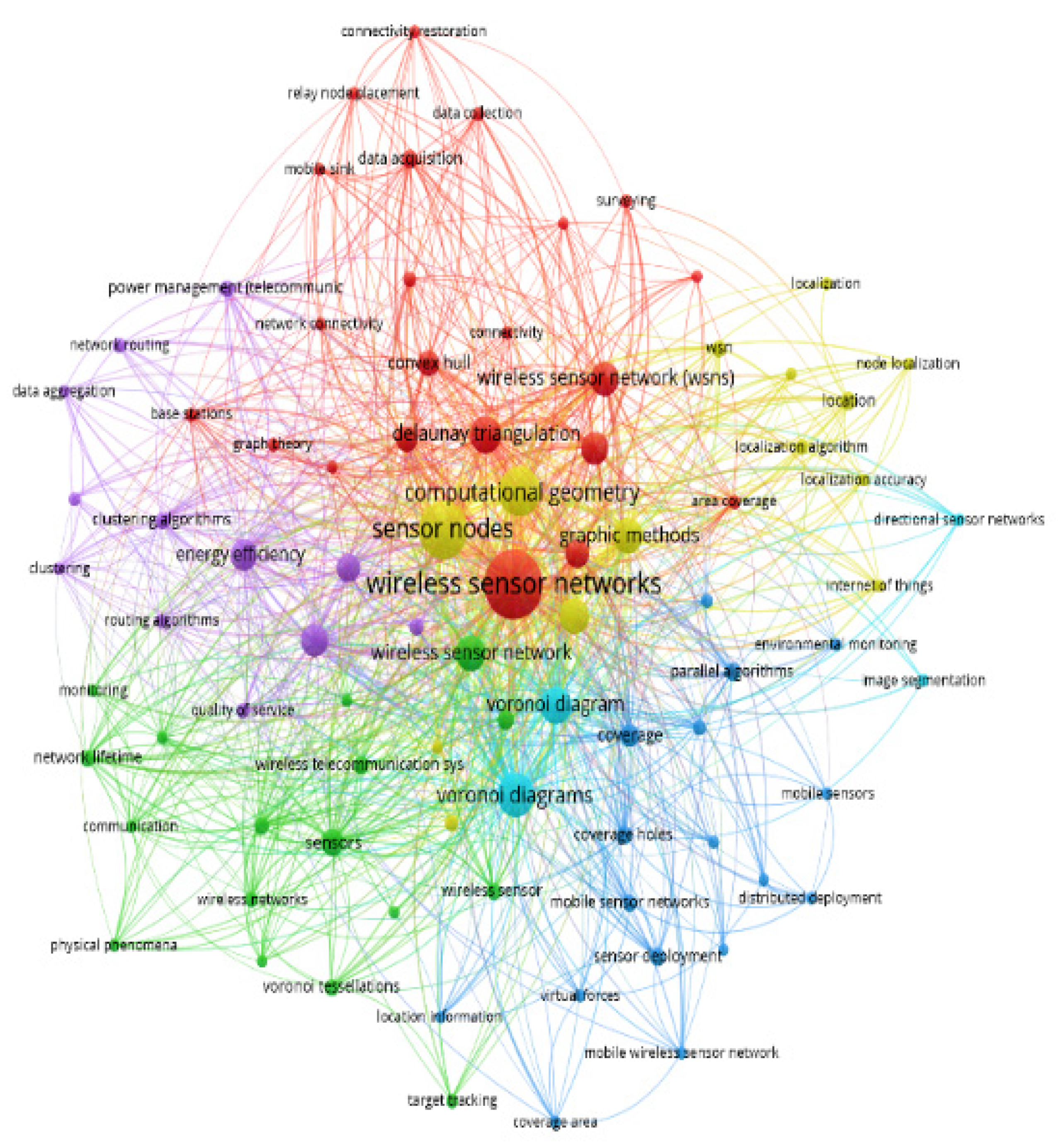
Figure 3 presents the complex web of related keywords based on the co-occurrence of all keywords. Each sphere defines a keyword and its size is proportional to its occurrence. Therefore, the bigger sphere size represents a higher occurrence of the keyword. The different colors in the given figure divide all keywords into their sub-domains. Also, these sub-domains are interconnected with each other either directly or indirectly. The given figure shows how all keywords are bound to each other. This inter and intra-boundedness of keywords leads work with new dimensions, in the same and in interdisciplinary domains, to proceed further.
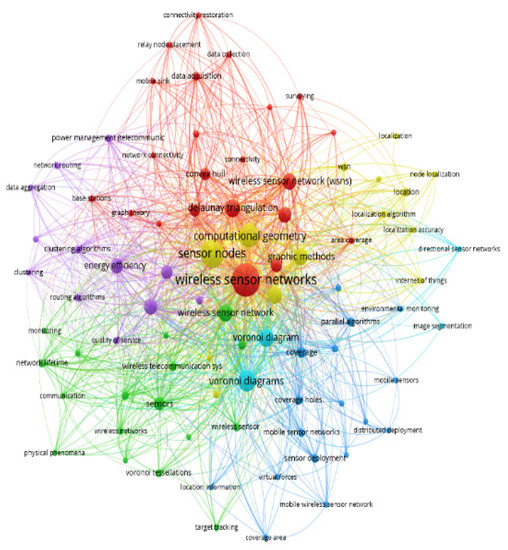
Figure 3.
The network visualization of co-occurrence of all keywords using the VOSviewer.
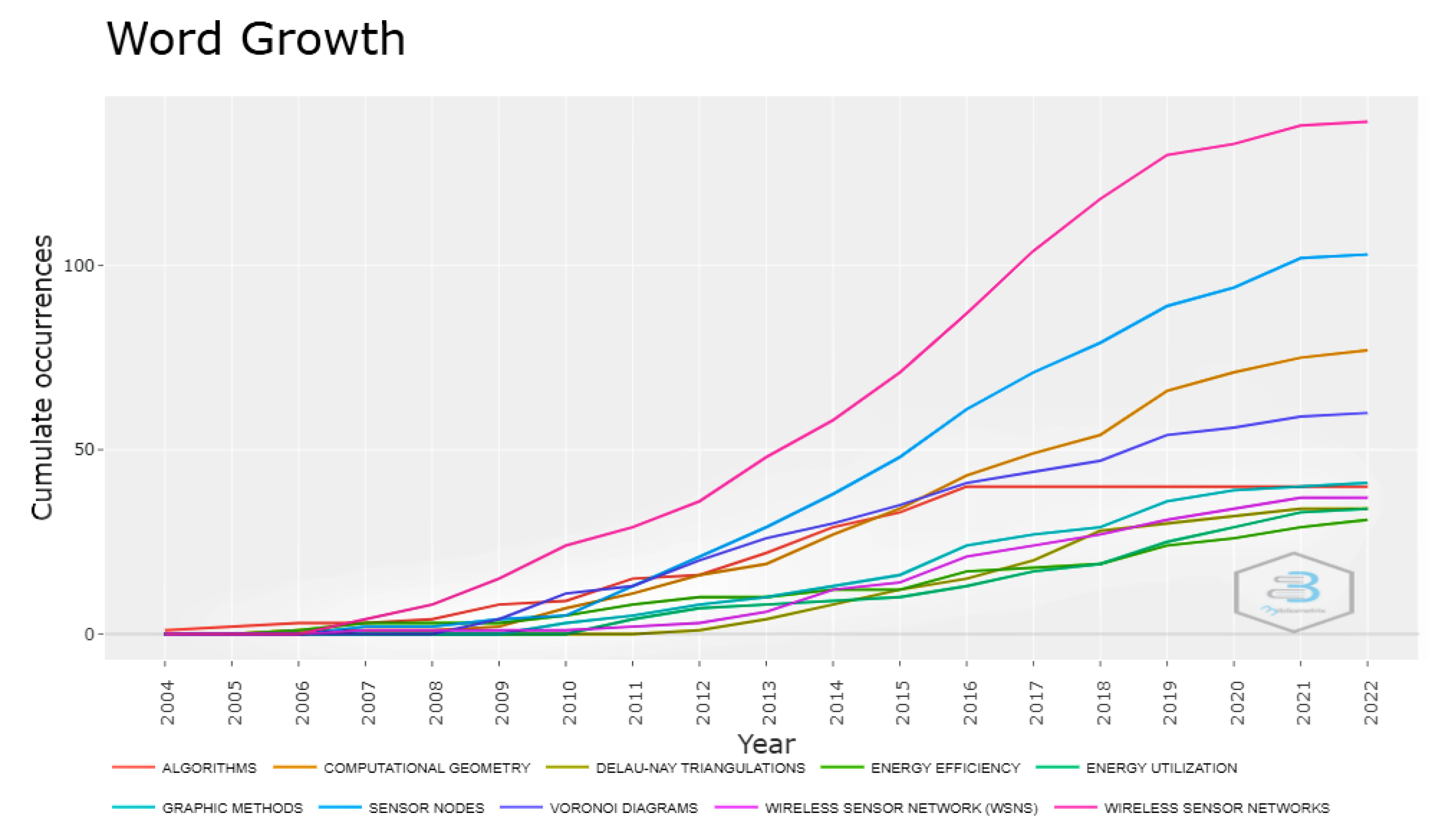
Figure 4 shows how related terms such as Wireless Sensor Networks, Sensor Nodes, Computational Geometry, and Delaunay Triangulations, etc., are growing over time. The term Wireless Sensor Networks shows the highest growth in the given period. Other keywords such as Computational Geometry and Delaunay Triangulations also show a rapid growth in the defined period. This rapid growth shows the potential significance of Computational Geometry, other related terms, and WSNs to take the research to new heights in the given area.
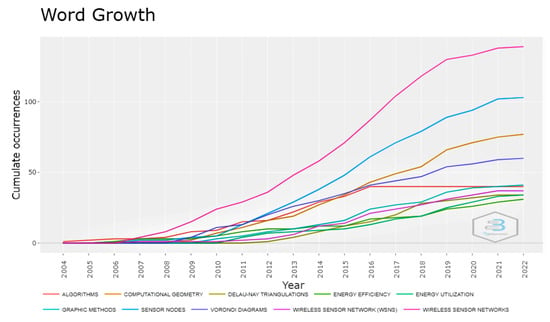
Figure 4.
Word growth over time during the period 2004–2022.
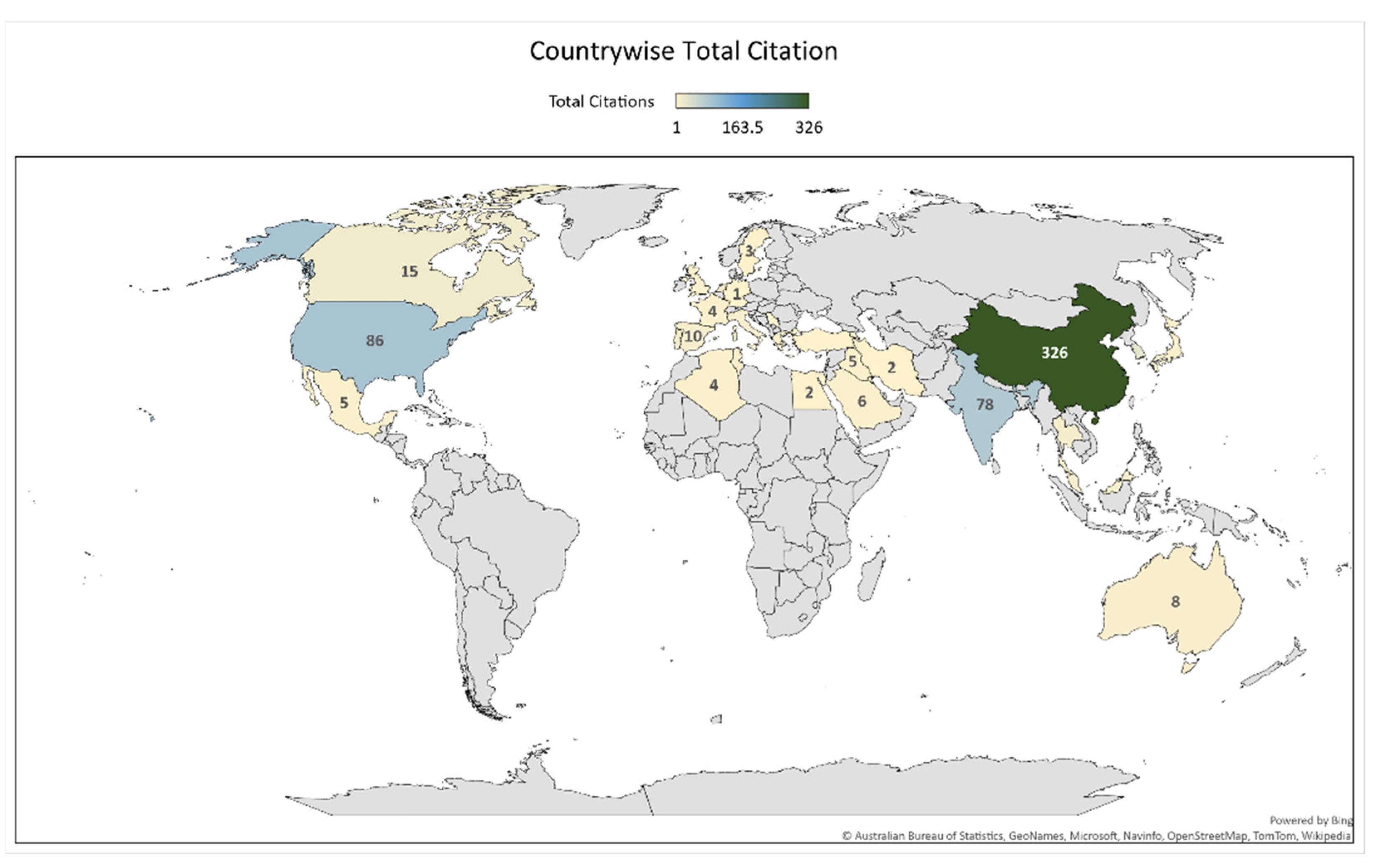
Figure 5 gives the total citations of given terms as contributed by each country. China is in the first rank as shown by the dark green color with a citation score of 326; followed by the USA and India (with citation scores of 86 and 78, respectively) as shown by a different shade of light blue. The other countries with a lower citation score are shown by a light dust color. The citation outcome reflected by China shows how extensively researchers in the country are working in this domain. China’s continued advancement in research is aided by four factors: a high population density and human capital base; a labor market that rewards academic meritocracy; a significant diaspora of scientists of Chinese origin; and a centralized government that is eager to fund science [21]. Also, this is a valuable indication for researchers worldwide that there is much scope for work associated with this domain.
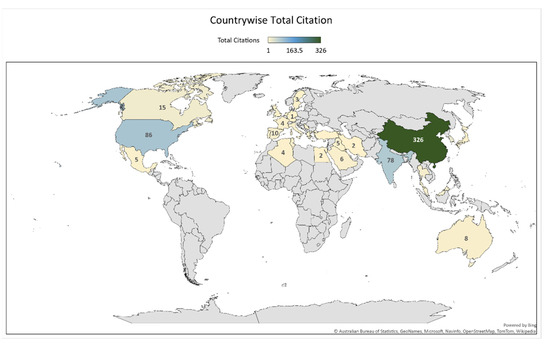
Figure 5.
The total citations per country.
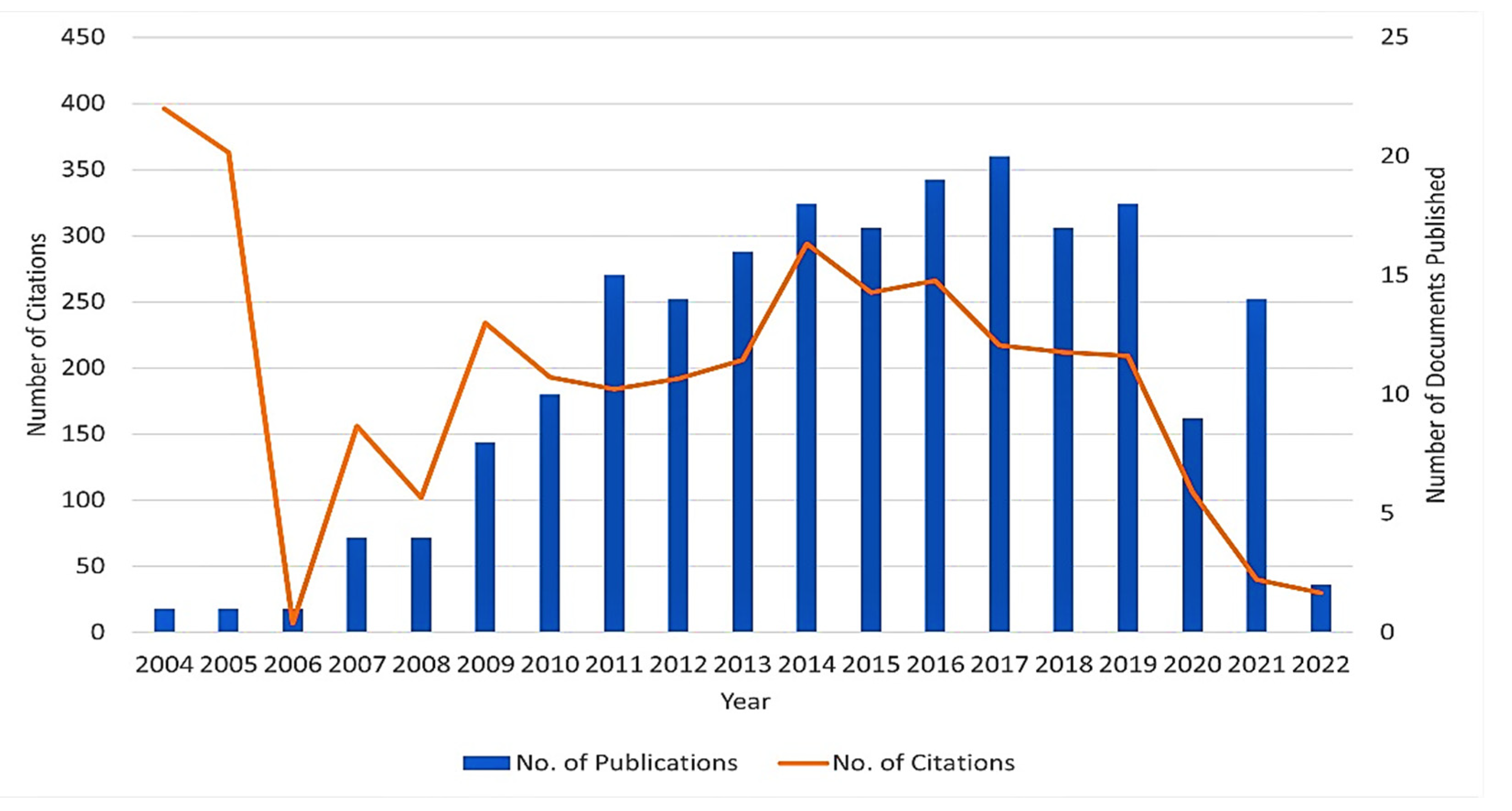
Figure 6 provides a two-way graph showing the yearly publication of the documents and respective citation counts relating to keywords chosen for this study. From 2004 to 2005, articles in this domain were frequently cited and 2017 is considered the year of the highest number of published documents based on the information obtained from the Scopus database in a specified time zone.
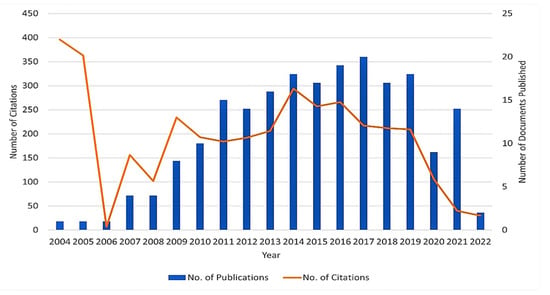
Figure 6.
Documents and citations published yearly.
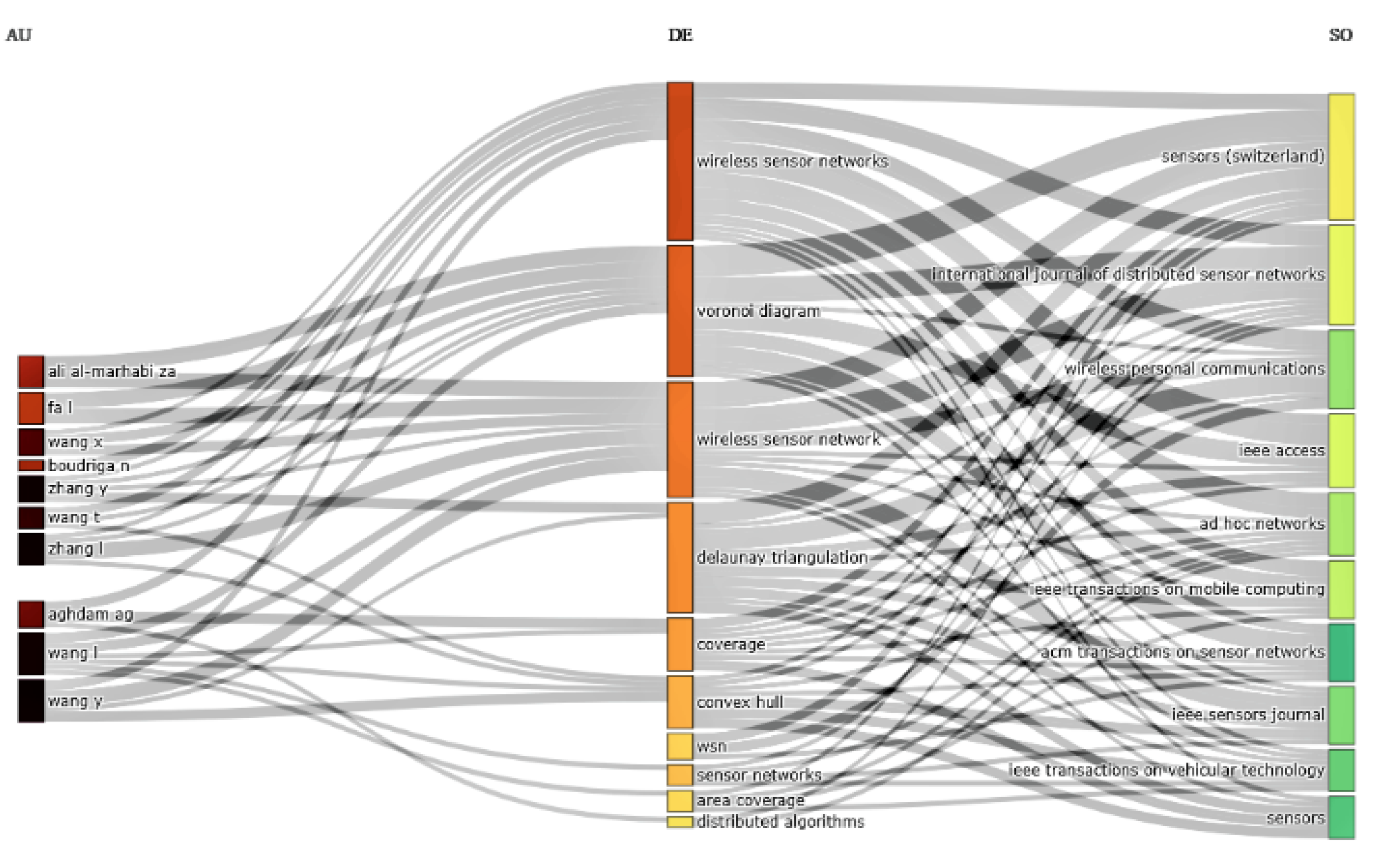
Figure 7 shows a three-field plot of associated authors, keywords, and publication sources in this domain. The figure displays the ten most influential authors and their publication sources as reputable journals, along with the most frequently used keywords. This study shows that the keywords: Wireless Sensor Networks, Voronoi Diagram, Delaunay Triangulation, coverage, and Convex Hull are the significant keywords and that Wang I., Wany Y., Zhang I., and Ali Al-Marhabi Za are the authors who have mainly used these keywords. Moreover, Sensors, International Journal of Distributed Sensor Networks, Wireless Personal Communication, and IEEE Access are the major journals which are publishing the many articles in this domain.
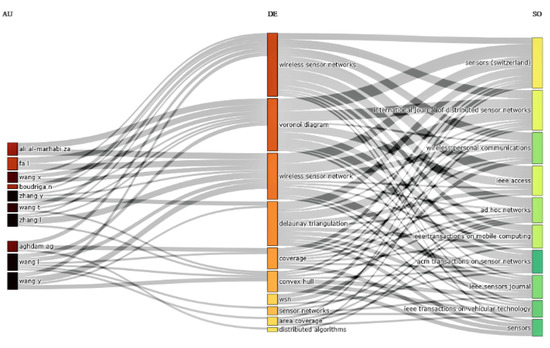
Figure 7.
A three-field plot of authors, keywords, and publication sources.
2.4. Coverage and Connectivity in WSNs
The efficiency of WSNs largely depends on two main aspects, i.e., coverage and connectivity. The reliability factor of WSNs is guaranteed by these having full coverage in a given area of interest. Coverage falls into two broad categories: the area coverage and the target coverage. A particular region is covered by placing sensor nodes in the area coverage. On the other hand, a specific target region is covered by the pre-determined coordinates or positions in the target coverage. To enhance the coverage naturally, the phenomenon of m-coverage has been introduced wherein at least the ‘m’ sensors cover each target. It acts like a fail-proof system in which the target remains covered until the time the m-1 devices fail. A fully connected network has all the nodes communicating with each other either directly in a one-to-one fashion or via relay nodes. In WSNs, the connectivity is modeled using a graph. A network is k-connected if it contains at least k edge-disjoint paths connecting any pair of nodes at any point in time. Similarly, the network is connected until the time that the k-1 devices fail. The WSN coverage strategies are divided into three main categories: self-scheduling, meta-heuristic, and classical deployment. The classical deployment techniques are further categorized into Computational Geometry, Force-based, and Grid-based techniques.
The authors in [5] have explained the construction of minimal-connected cover sets to solve coverage and connectivity problems and enhance QoS in WSNs. The fundamental concept is to compute and then connect a cover set. The authors also discussed an algorithm that identifies fully supported sensor nodes without error with the help of Voronoi Tessellation. Such supported sensor nodes can be recognized by estimating the coverage redundancy of the Voronoi cells. The Voronoi partition and the Clique partition are used to predict the mobility of sensor nodes to get the desired network connectivity and target coverage. One of the major goals of future research is to reduce the number of sensor nodes deployed in a particular area while maintaining the network connectivity and the coverage of the target area [17].
3. CG Techniques for Improving Coverage and Connectivity in WSNs
In WSNs, Computational Geometry plays an essential role in enhancing the Quality of Service (QoS) of several sensor nodes that can be optimized using new computational techniques; and the longevity of WSNs can be increased to some extent. Coverage holes can be formed in the target field due to the inherent nature and the random deployment of WSNs. Certain strategies must be used to guarantee that the area of interest is entirely free of any coverage flaws. Furthermore, Computational Geometry is an essential strategy for efficiently detecting and healing coverage holes, enhancing network quality, and extending the network’s life. The geometric distribution of sensors considerably affects the design of WSNs.
3.1. The Voronoi Diagram-Based Technique
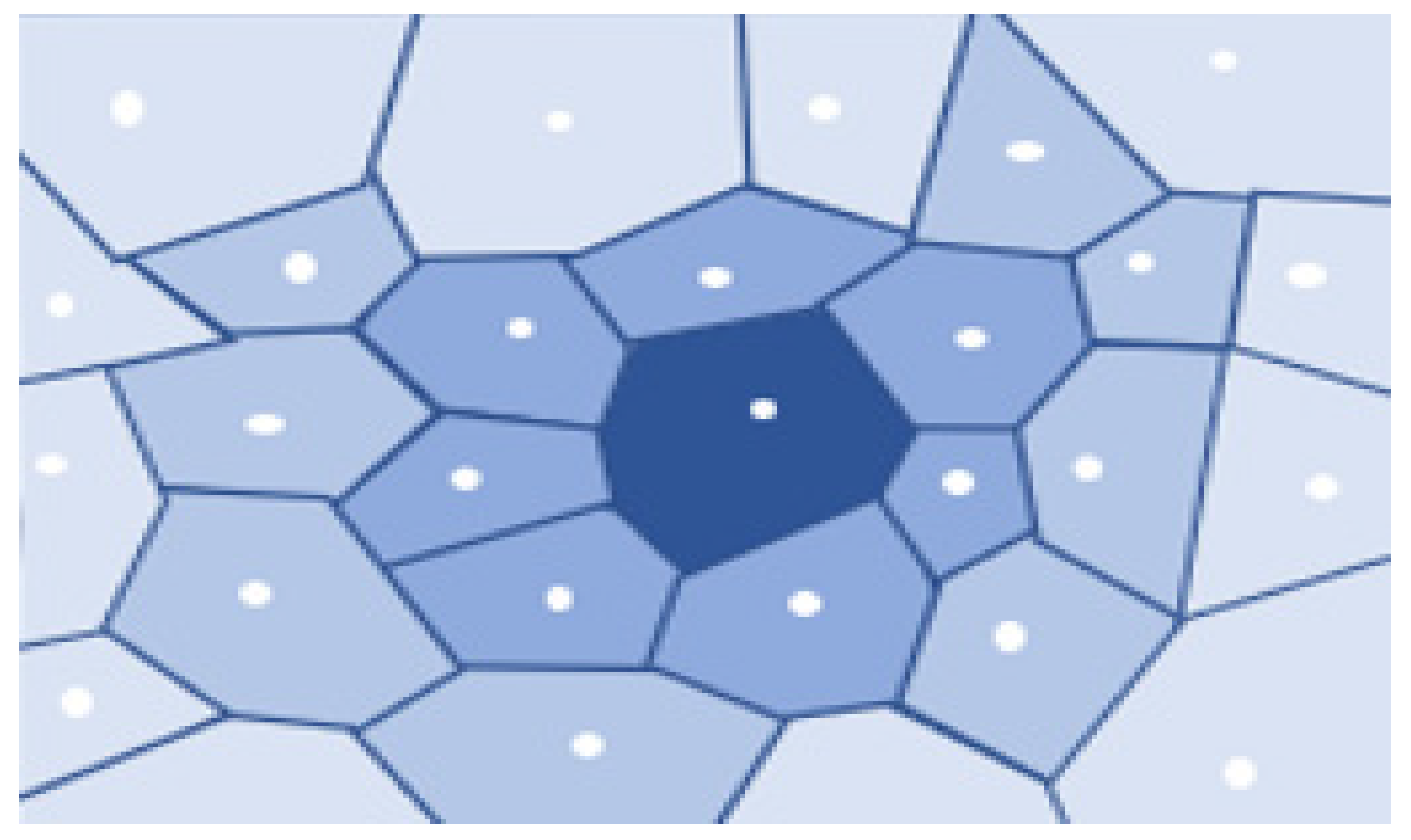
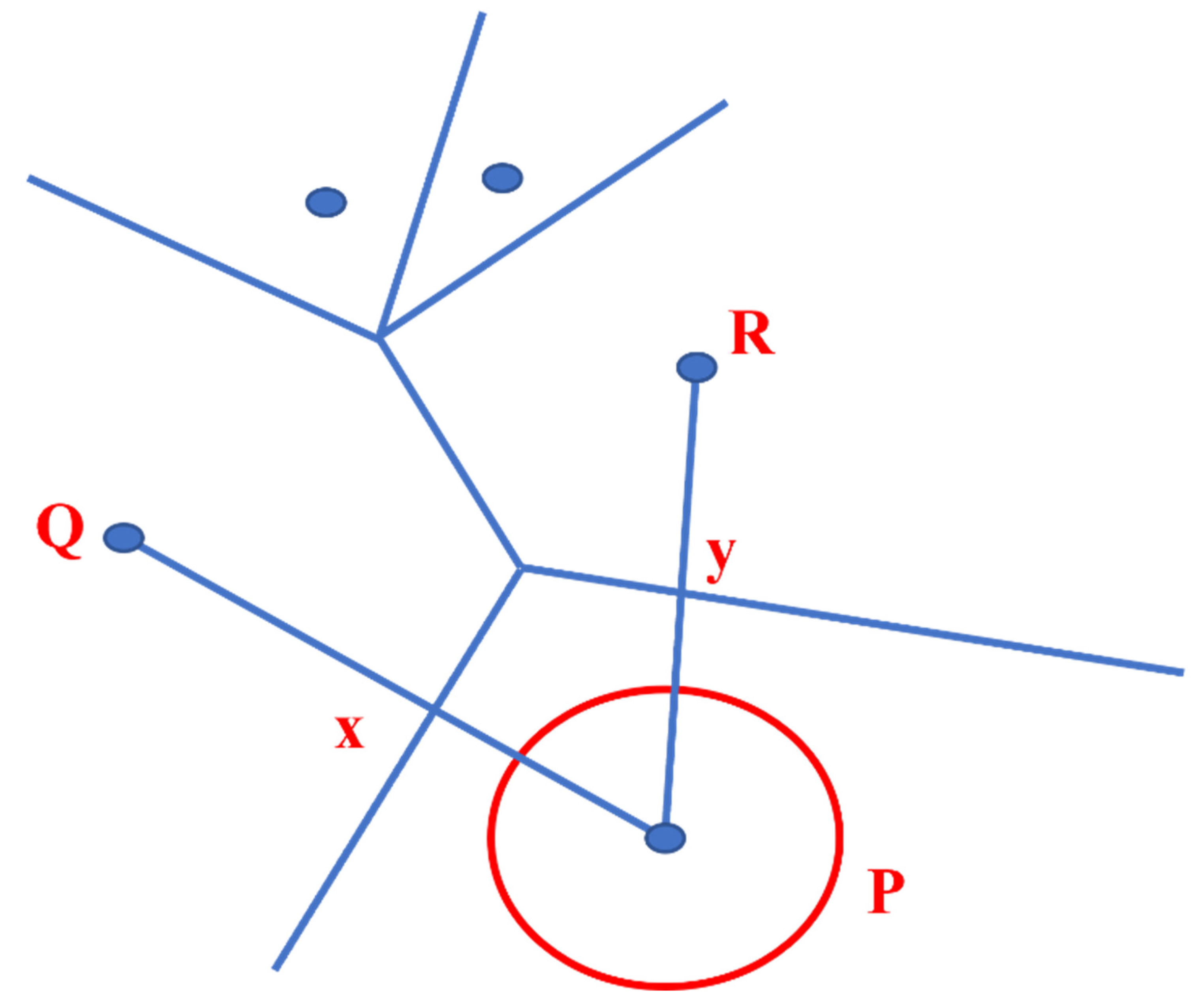
In Computational Geometry, Voronoi Diagrams are integral data structures. They regenerate a specific region into many regions with the help of generators (points). A dominant part represents each point, which is termed a Voronoi cell, consisting of all topics closer to it than any other issue, as shown in Figure 8.

Figure 8.
A Voronoi Diagram.
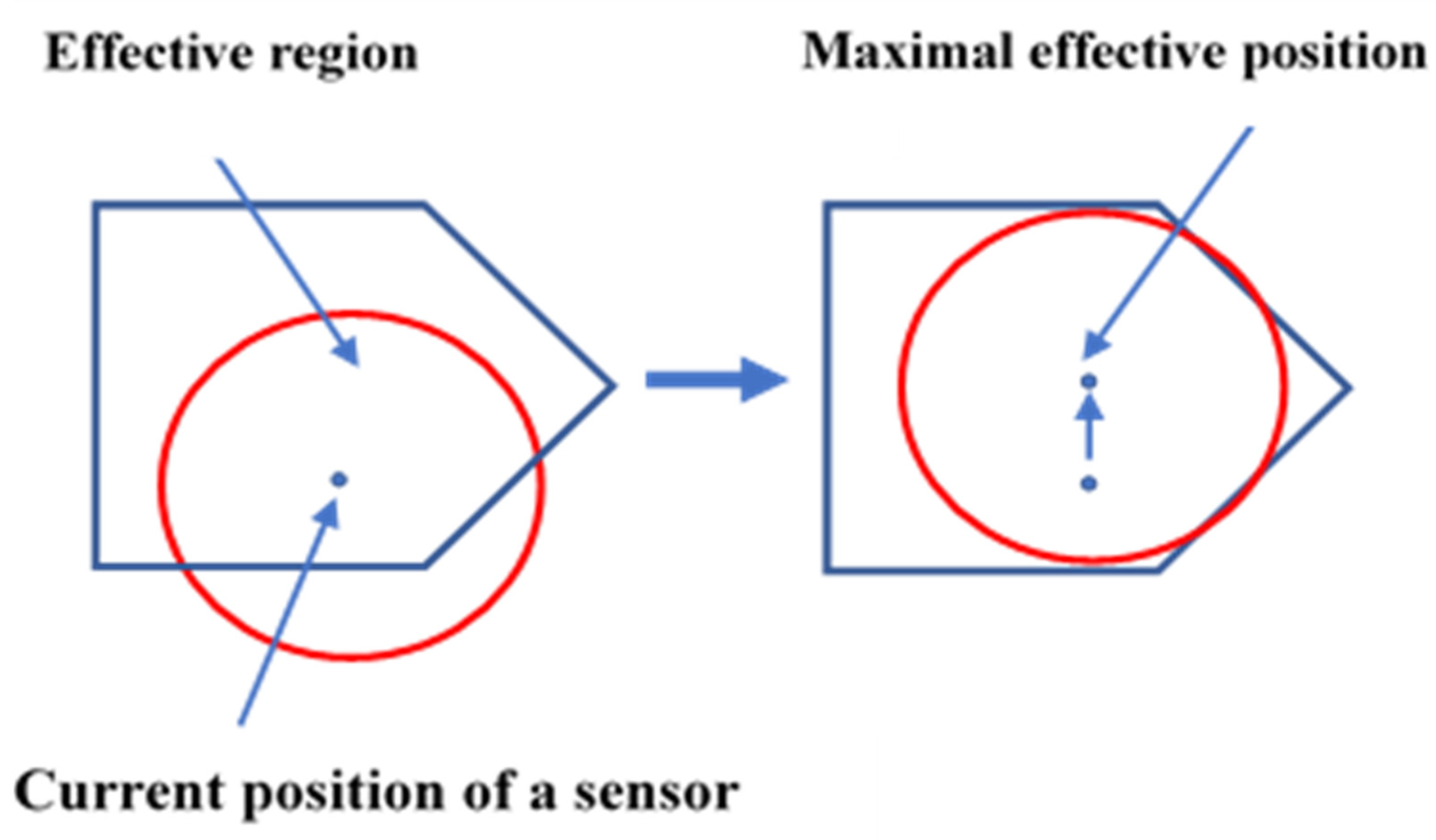
The primary objective of WSNs is to provide maximum coverage with a limited number of node deployments when the sensing area has unfavorable conditions. In most research, Computational Geometry has played a significant role in sensor deployment schemes in WSNs. One of the essential types of research on coverage hole detection and healing has been proposed in [22]. The research shows that the movement of sensors can be controlled by using two methods: the Basic Method and Virtual Movement. In the Basic Method, sensors move iteratively until they cover the maximum part of the coverage hole. On the other hand, there is no actual movement of sensors in Virtual Movement. Based on Virtual Movement, the final effect is calculated on the coverage hole; however, the real action takes place only if it covers the coverage holes. The movement of sensors becomes reduced, as only one movement is noticed at any given time. In both the activities, i.e., Basic and Virtual, three algorithms are commonly used: the Vector-based algorithm (VEC) from a dense area, where sensor nodes are pushed away; the Voronoi-based algorithm (VOR) where sensors move towards the coverage holes; and the Min–Max, where sensors move towards coverage holes without generating new holes. The authors in [23] have proposed a Voronoi Coverage Hole Discovery algorithm (VCHDA). This algorithm helps find a hole by calculating the distance between the sensor node vertex and the Voronoi cell’s edges. The algorithm can recognize coverage holes efficiently and even provide labels for the border nodes adjacent to the coverage holes. The authors in [24] have presented an energy-efficient scheme using attractive and repulsive forces for self-node deployment. In this scheme, every node of the confined Voronoi Polygon is assigned a sensing task. The overall coverage problem can be converted to a local coverage problem by using a constrained Voronoi Polygon, as depicted in Figure 9.
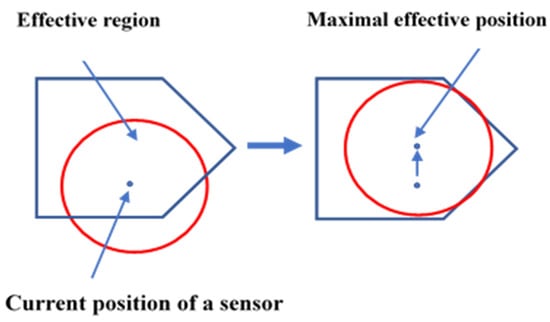
Figure 9.
The effective region and the maximal effective position.
The attractive force is generated from the Centroid of the Voronoi Polygon, and the repulsive force is generated from the obstacle or the neighboring node. This scheme offers a solution for uneven node distribution and thus provides maximum coverage in a shorter timeframe with less node movement.
The authors in [25] have focused on improving the area coverage of the Directional Sensor Network (DSN) in accordance with the rotatable directional sensors. To solve the difficulty of field coverage in the case of DSN, the authors have used the Voronoi Diagram and implemented a distributed greedy algorithm to reach an optimal solution. The direction of sensors could be selected and adjusted with the help of three principles: to enlarge the sensing area as much as possible within the cell, to reduce the overlapping of coverage with neighbors, and to keep away the sensor coverage from outside the field of interest. To cover the coverage holes faster, the authors in [26] have introduced two new schemes to deploy the nodes efficiently. These proposed approaches are called the Centroid and Dual Centroid approaches based on the Centroid of Voronoi Polygon. In the Centroid Scheme, the sensor moves to the center of the local Voronoi Polygon. However, the Centroid of the neighboring node polygon is calculated in dual Centroid. Then, the sensor moves to the center point of the line created by the local Voronoi Centroid and the neighbor node Polygon Centroid. The calculated new value is further used to get the new location for node deployment to get better coverage.
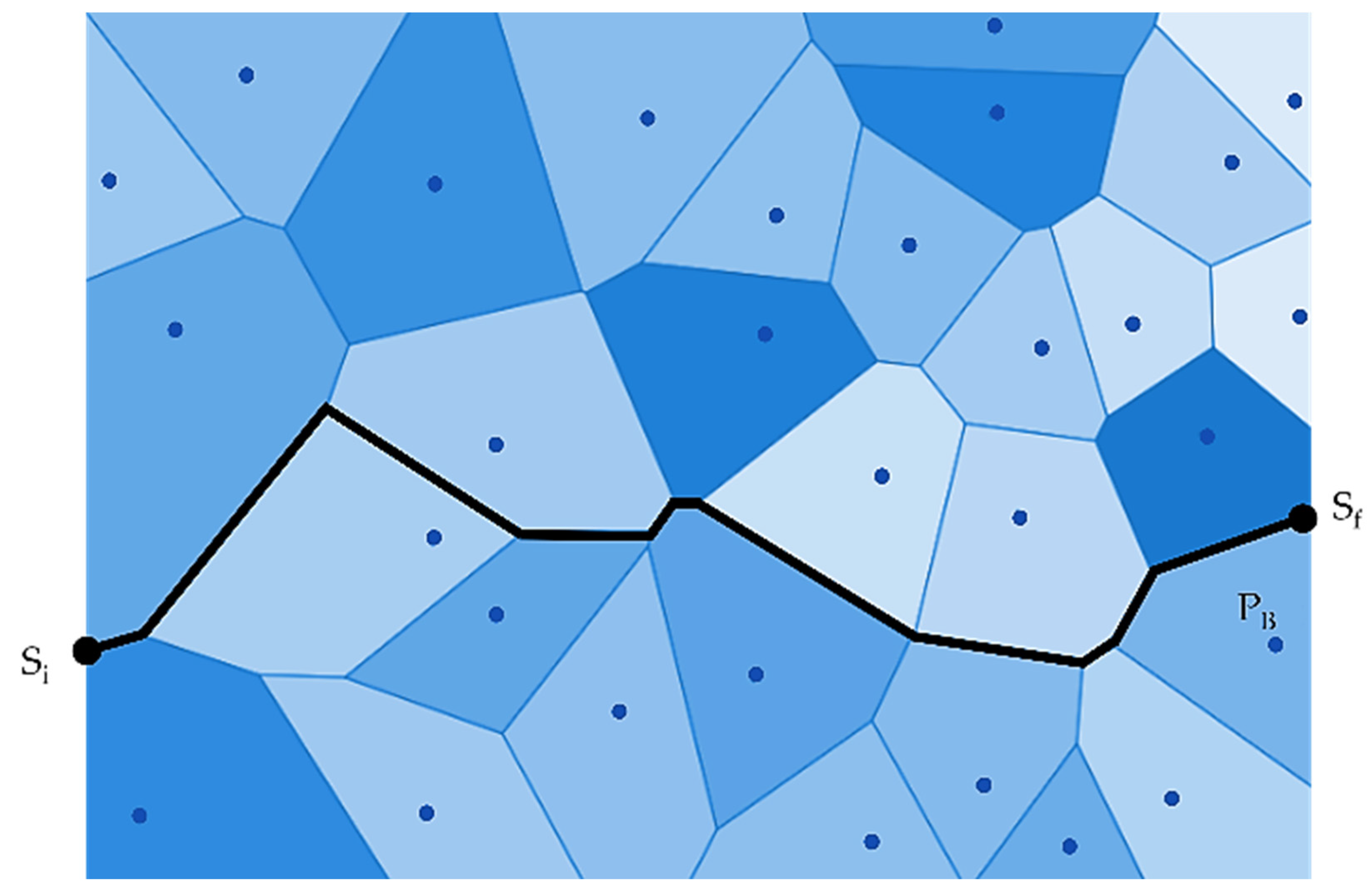
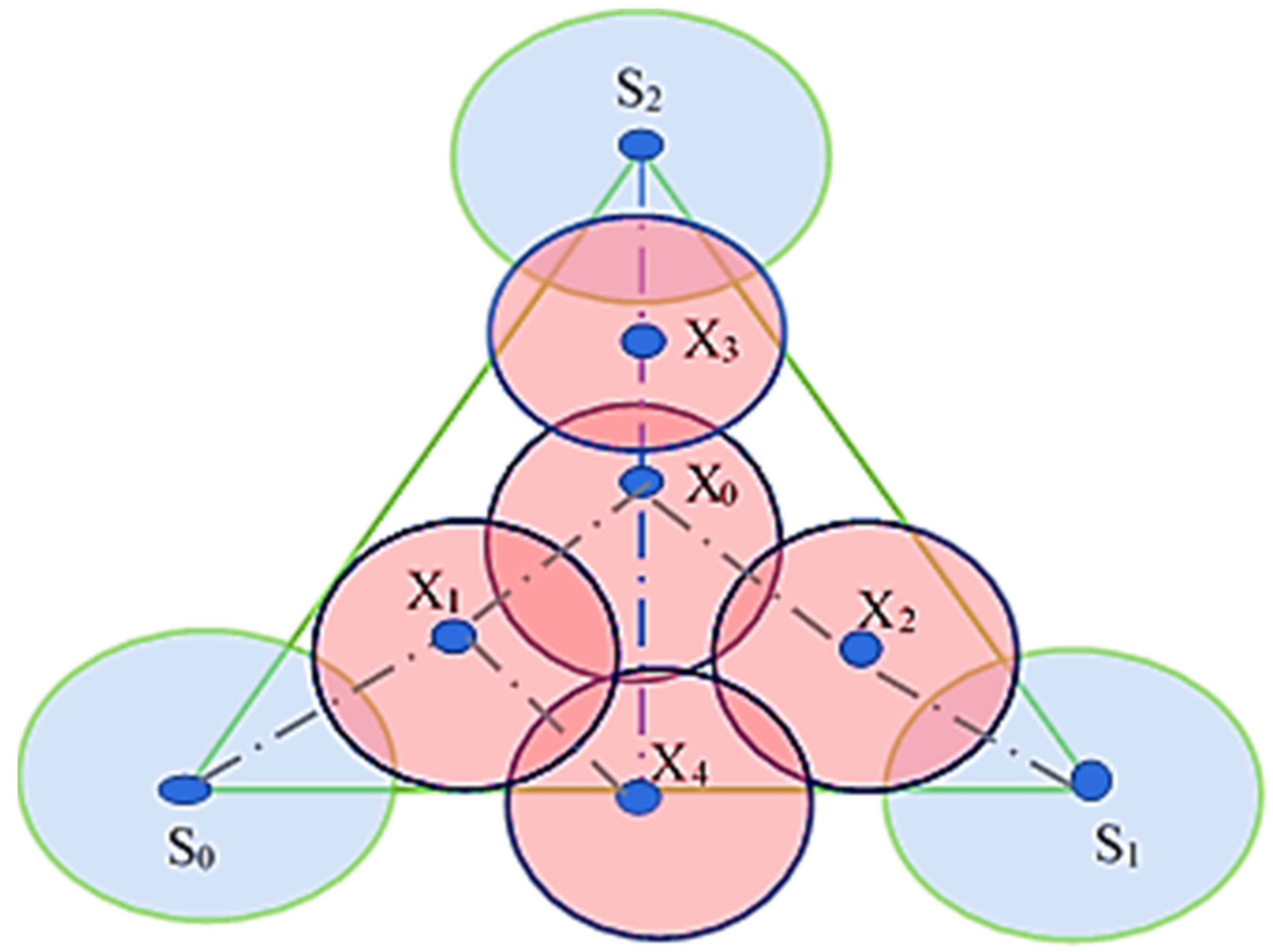
The authors in [27] have used Computation Geometry and Graph-Theoretic techniques. In Computation Geometry, the authors have used the Voronoi Diagram and later combined it with the Graph Search algorithm. The authors have also proposed that the “worst-case coverage-maximal breach path” and the “best-case coverage-maximal support path” algorithms can be used to find the optimal coverage in WSN. In the maximal breach path case, the Voronoi Diagram is used to deploy sensors, and then, subsequently, graph theory abstractions are used, as shown in Figure 10.
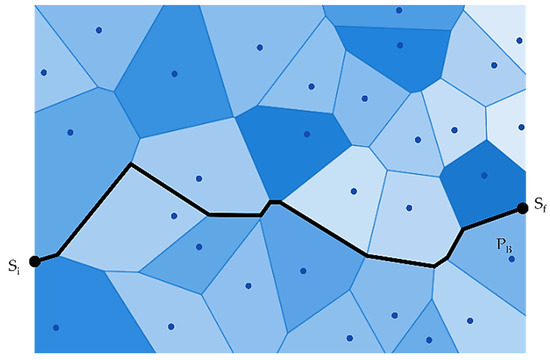
Figure 10.
A maximal breach path (PB).
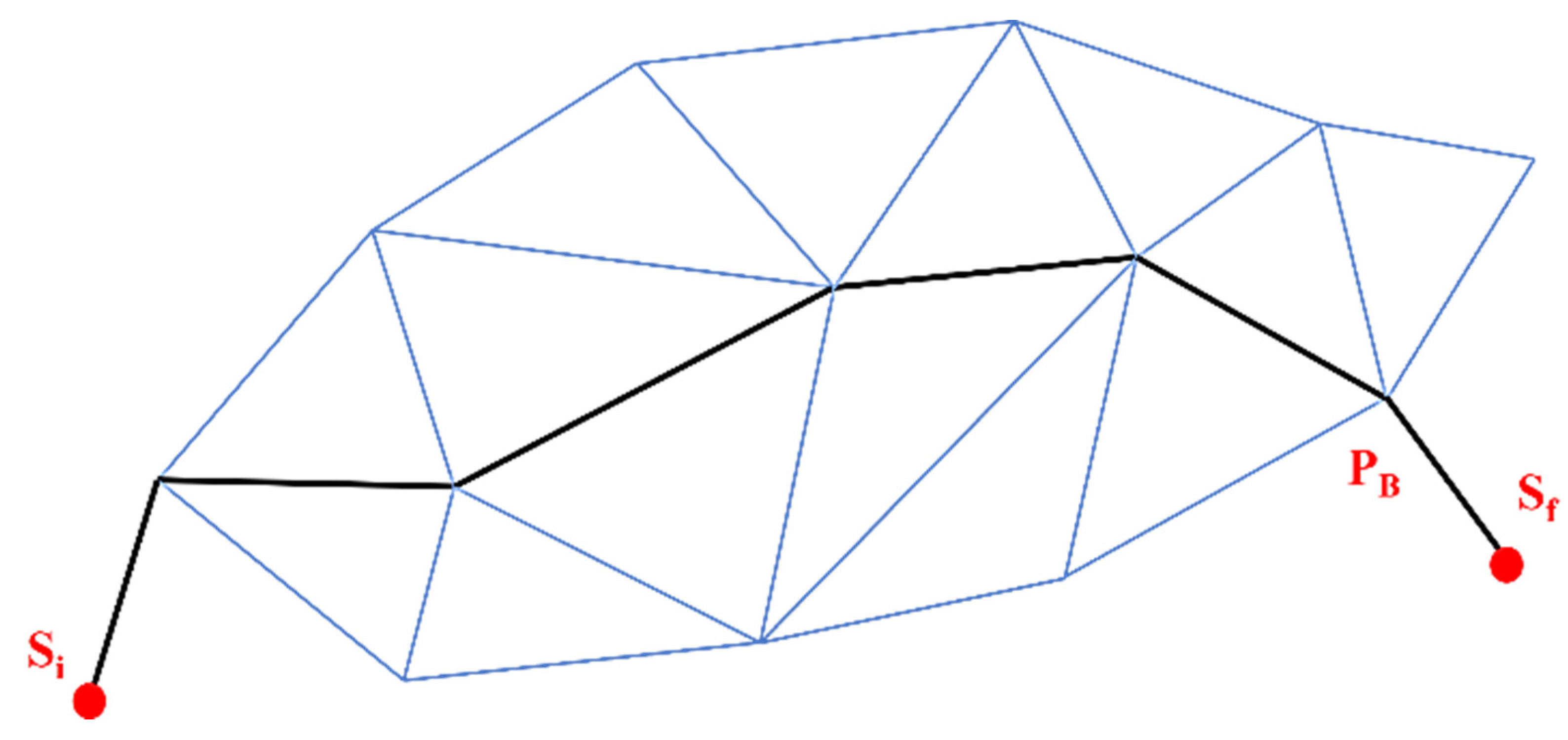
On the other hand, in the maximal support path, the Voronoi Diagram is replaced with Delaunay Triangulation, and some weights are assigned according to line segments in Delaunay Triangulation. As explained in Figure 11, two additional edges are set up to connect Si (initial location) and Sf (final place) adjoining sensors in the configuration. After deployment of a single node, results have shown a 10% improvement in coverage when 100 sensors are deployed randomly.
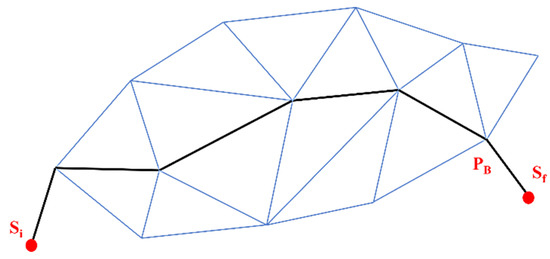
Figure 11.
A maximal support path (PS).
The authors in [28] have designed two novel schemes to solve the coverage problem. The Blind Zone Centroid-based method directs the sensor to the Centroid of the Voronoi Blind Zone Polygon’s Centroid rather than the Voronoi Polygon’s Centroid. The second proposed scheme by the authors is the Distributed Centroid-based system to enhance coverage in case the sensors are stagnated.
The authors in [29] developed a new coverage control method to ensure optimal coverage. To cover the region with changing boundaries, a blanket coverage area is used along the edge of the region. The newly proposed method provides a solution for moving coverage regions. The coverage area can be expanded or compressed according to the coverage domain. The authors in [30] have proposed an efficient self-deployment algorithm (ESA). The ESA describes the movement of a particular node towards the best position after initially putting it at a random position. Based on neighbor distance, the ESA identifies the accurate direction and distance from the existing sensor. This newly proposed approach gives healthier results than the Centroid, the Dual Centroid, the VOR, and the Min-Max algorithms. It has shown a significant improvement in the coverage and connectivity of WSN. The authors in [20] have resolved coverage issues by using the Voronoi Diagram. The authors avoided using the Global Positioning System (GPS) to corroborate the data for the construction of the Voronoi Diagram because of the cost factor and the lack of a guarantee of providing a solution in all the expected situations. They have proposed a region-coverage algorithm where GPS is not required for data corroboration. With the help of the Voronoi Diagram, a fully engaged sensor can be discovered.
The authors in [31] have explained how a Voronoi Diagram can be used to deploy sensor nodes that help inefficient energy utilization compared to the other available grid coverage strategies. A Voronoi Diagram is preferred over other geometrical data structures because its complexity is maintained by only one parameter, i.e., the total number of sensor nodes. This parameter uplifts effective energy consumption because that increases the network’s lifetime. The authors in [32] have proposed the concept of Prioritized Geometric Area Coverage to enhance the coverage in directional sensor networks. The proposed algorithm establishes a relationship between the cell area and the area covered by the sensor node during the selection of the sensor’s direction to maximize the coverage. The Voronoi Diagram marks the best sensor node as the node itself to cover the corresponding Voronoi-cell area. Also, the categorization has been carried out based on geometric shapes of the Voronoi cells formed. Also, the authors have focused on the network lifetime by switching off the redundant nodes. The authors in [33] have covered the issues of coverage and energy efficiency in the Voronoi-Glowworm Swarm Optimization K-means algorithm. The authors have used the K-means algorithm for cluster formation and cluster center selection in the proposed paper. The concept of the Voronoi cell is used to mark the appropriate sensing radius to obtain optimized coverage. A Glowworm Swarm Optimization is applied to decide the optimum location points to deploy the sensor nodes. Then, the active and sleep modes are used to utilize network energy efficiently. The authors improve coverage of heterogeneous WSN in [33] by using the coverage gap-fixing method with the help of the Voronoi polygons. The coverage gaps have been fixed with the help of Computational Geometry techniques and graph theory. The coverage holes created near the static nodes were defined and highlighted with the help of the Voronoi polygons. Redundant mobile nodes covered these holes. Table 2 gives a quick overview of the different Voronoi diagram-based techniques to improve coverage and connectivity in WSNs.

Table 2.
An Overview of the Different Voronoi Diagram-Based Techniques to Improve Coverage and Connectivity in WSNs.
3.2. Delaunay Triangulation Based Techniques
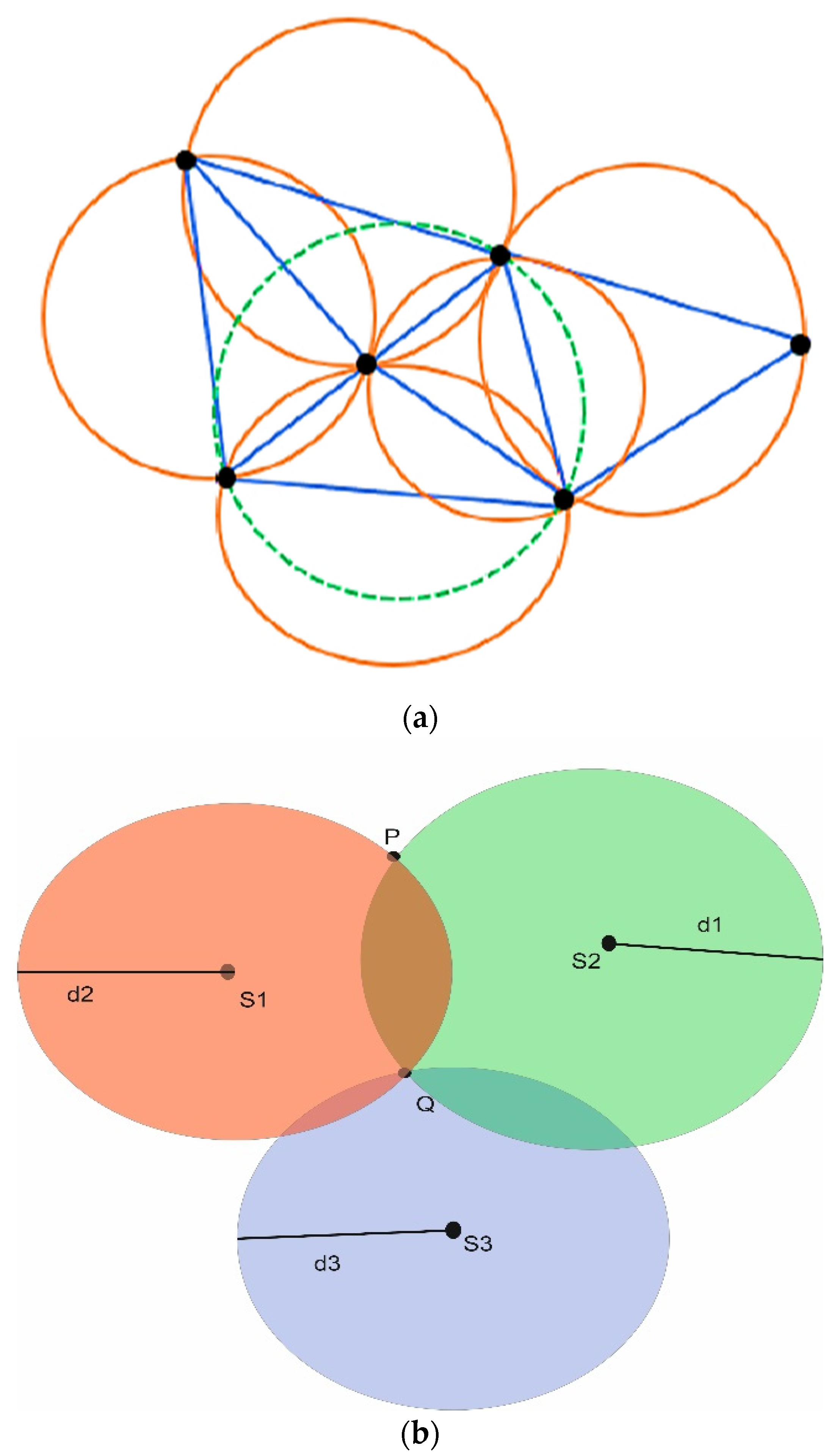
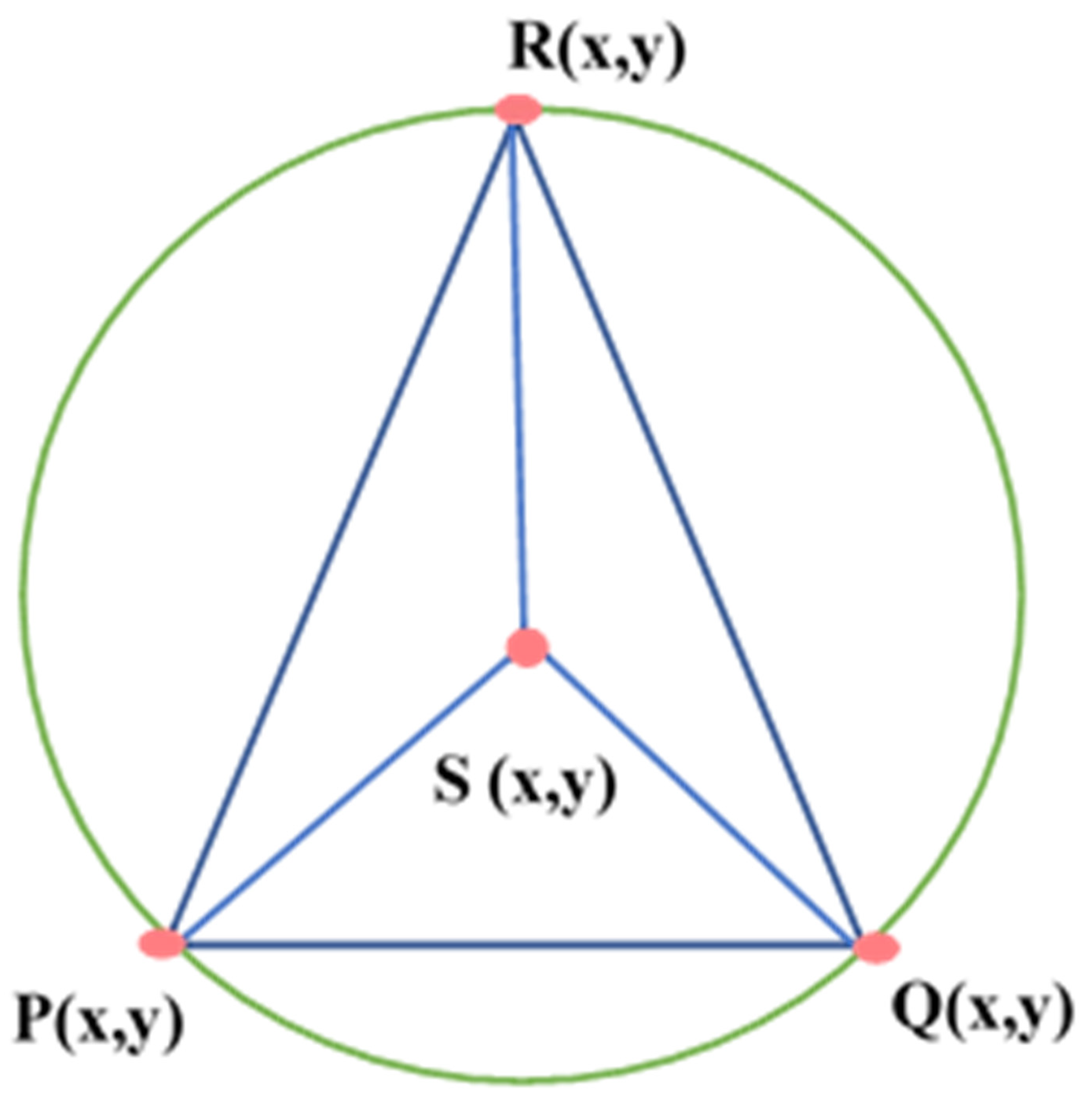
Delaunay Triangulation (DT) is constructed by segmenting a specified area into several triangles so that the circumcircle of each triangle contains no points, as illustrated in Figure 12a. It is a kind of dual graph of the Voronoi Diagram for a discrete point set P. DT can be constructed by connecting the consecutive nodes in the Voronoi Diagram that share at least one standard edge. The two nearest neighboring sites can similarly be determined using the shortest edge in triangulation [34]. Trilateration is used for sensor node localization by using the geometry of a triangle, a circle, or a sphere with the help of neighboring nodes as shown in Figure 12b. Quadrilaterals or Polygons are formed by Trilateration made up of overlapping of triangles [35]. Trilateration is used to measure the side length of triangulation instead of the horizontal angle.
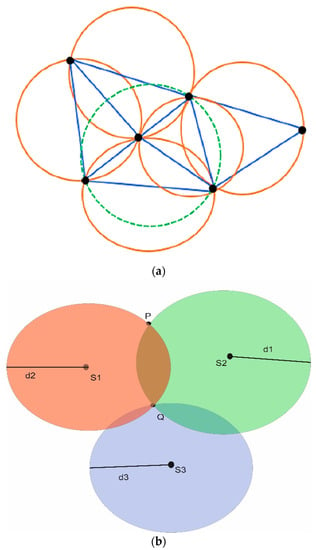
Figure 12.
(a) Delaunay triangulation; (b) Trilateration.
The Delaunay-based Coordinate-free Mechanism (DECM) was proposed by the authors in [36] to heal the coverage holes with less sensor movement by using a cooperative movement mechanism. The DECM is more efficient than other schemes for coverage hole detection and healing and even ideal nodes can also be addressed. In addition, it is a distributed scheme that prevents new hole generation during the healing process. The author in [37] has used Constrained Delaunay Triangulation (CDT) to solve the problem of coverage in WSNs. The CDT phenomenon optimally reduces the energy requirement by minimizing the information sent to the base station. In the concept of CDT, the author has focused on extra user-defined edges that do not form part of DT. Furthermore, CDT is also used to construct a set that contains the maximum number of nodes to supervise the area of interest.
The authors in [38] have discussed two major node deployment schemes: Random and Grid-based. In a Random deployment scheme, nodes are not deployed effectively as some nodes are kept in the same place while other locations remain uncovered. Triangular, Hexagon, and Square are the basic Grid-based deployment schemes. In the Grid-based deployment scheme, the nodes are placed regularly, but the deployment fields are kept regular. Hence, the author discussed a deployment method using DT by keeping all these issues in mind. For node deployment, firstly, the trusted region is divided into different triangles using the DT method, and then finally, the nodes are deployed on the triangle’s vertices.
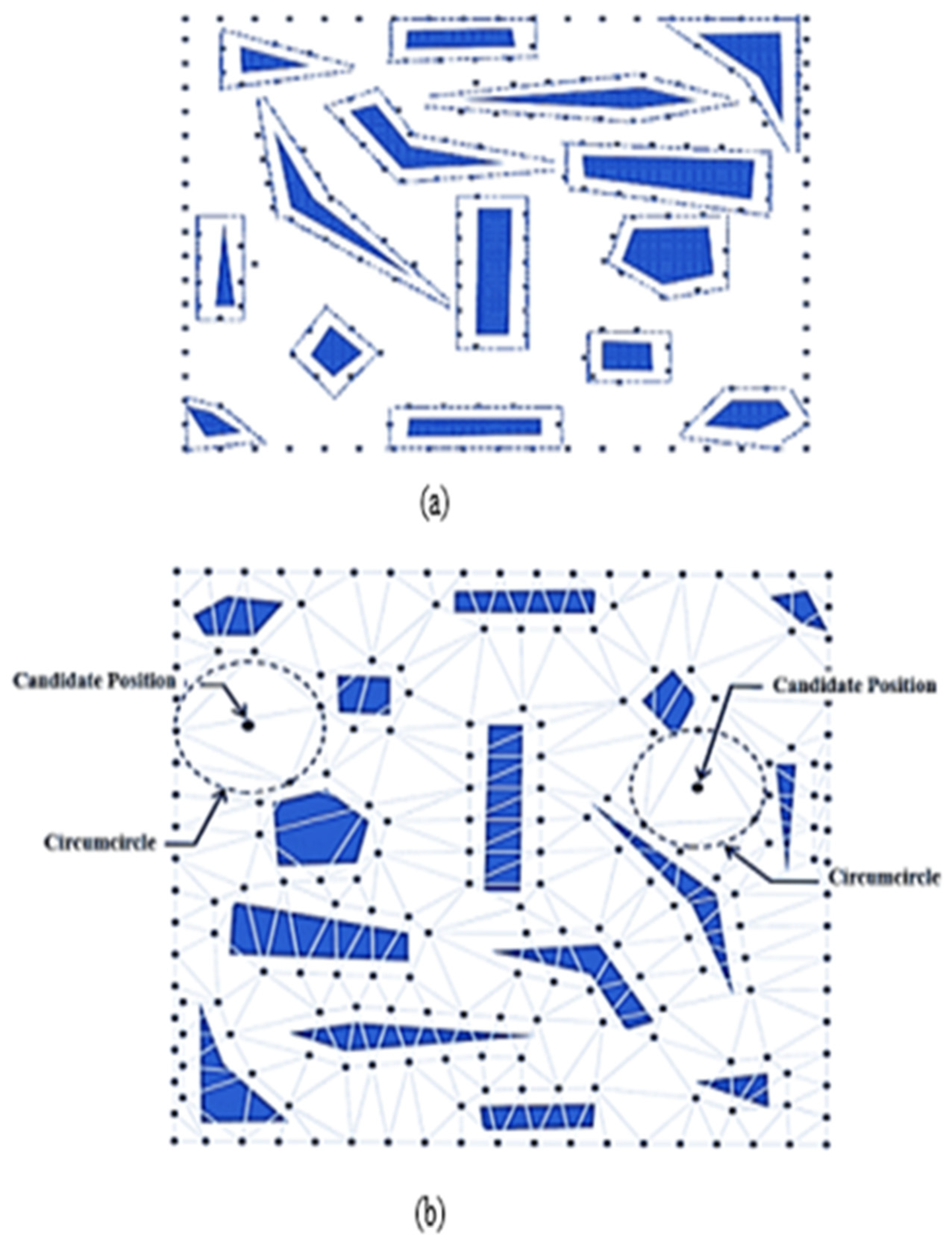
The authors in [39] have described DT in the 2D plane as a dual structure of the Voronoi Diagram. DT has satisfied the empty circle property, which is described as a circle passing through edge endpoints without containing other points. The DT empty circle property is used to find a suitable node deployment position. The two phases commonly used in DT are Contour Deployment and Refined Deployment. In the first phase, contour points are generated at the coverage area boundary and near the obstacles, in order to remove the coverage holes, as shown in Figure 13a. In the second phase, the node positions can be extracted by using DT for maximum coverage gain, as shown in Figure 13b. Finally, after determining all possible positions, the candidate with the best score is chosen for the final node deployment.
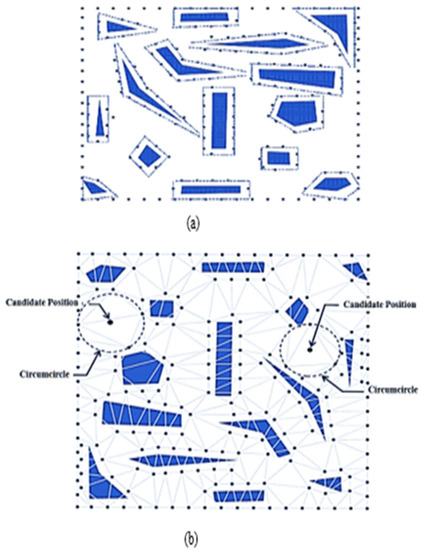
Figure 13.
(a) The contour points generation step and (b) Delaunay triangulation of given sensors.
The authors in [40] have proposed a Delaunay-based Connected Cover (DBCC), which is a two-phase algorithm. The first phase focused on providing coverage over the network area when a tiny number of nodes were selected. Based on DT, the selection of the number of nodes is defined. In the second phase, the search algorithm is used to maintain the network connectivity breadth and more nodes are added subsequently. The shortest path between the connected components is determined to identify the subset of activated nodes when needed. All nodes selected for a particular path are switched on. The authors in [41] have used a dual DT to deploy nodes at each vertex of triangulation. The authors have also considered 3D surfaces for node deployment. The vertex positions are selected based on the sensing radius to gain maximum coverage. However, to find out the actual coverage rate, the issue of superposition is also handled. The same is checked to confirm whether the node deployed fulfills the communication requirements of WSNs.
The authors in [42] have used the basic idea of the Voronoi Diagram and DT. It has been used to make a cover set and a schedule cover set. The main goal is to cover the target area entirely by splitting the sensor into separate cover sets. Every sensor in a cover set must sleep or wake up at a desired time. The main focus is on finding a cover set so that the area covered by every sensor can be effectively minimized. These cover sets are scheduled for sleep and wake-up modes in order to enhance the network life. This is achieved by using a Geometric-based Activity Scheduling scheme (GAS). There are two phases in this algorithm: the Initialization phase and the Sensing phase. The sensors are scheduled for the wake-up and sleep modes by using the Initialization phase and the Sensing phase in continuum. The main aim of the GAS scheme is to minimize the number of active sensors at any given time.
Based on DT, the authors in [43] have described a new measurement scheme that gives essential information and correlates the distance between sensors—fat, thin, healthy—and areas between sensors. By using DT, this method provides a finer, more acceptable quality of service than other schemes that are only related to field coverage. DT is an optimal triangulation technique for a network having more than three sensors with the properties as described:
- For a given set of points, the outer polygon of the triangulation is convex;
- The triangle edges of each sensor connect it to its closest neighbors;
- Each sensor has a degree of at least two, if not three, sensors that are on the same shared straight line;
- There are no other sensors on the circumcircle of each triangle.
Four concepts explained by the authors which explicate Quality of Coverage (QoC) are:
- ■
- The distance between each point in the field and its closest sensor is represented by the Probabilistic Distribution Function (PDF) (Coverage Resolution Model);
- ■
- Coverage uniformity;
- ■
- Areas that are perfect or scattered;
- ■
- The distance between sensors with the emptiest space.
The area coverage issue for the area of interest, which is of irregular shape, is resolved by the authors in [44]. The authors presented a DT-based method, namely the Heal Coverage Holes algorithm (HCHA), to discover and heal coverage holes. A hybrid sensor network has been used for area coverage. In this, both types of sensors are used, i.e., mobile and static sensors, as depicted in Figure 14. Static sensors are used to find the size of coverage holes, and aided mobile nodes are deployed to heal the coverage holes. This algorithm detects coverage holes and healing is subsequently carried out using DT.
Figure 14.
The position of assisted sensors.
To detect coverage holes in a given area of interest, the authors in [45] have used a Coverage Hole-Detection algorithm (CHDAE). A DT with an empty circle property, as shown in Figure 15, was created to define the network topology. DT is a collection of points where the circumcircle of every triangle is empty. The authors have described three phases: (1) creating the Delaunay Triangle by using the approximation method to find the position of sensor nodes, (2) coverage hole detection in a comprehensive WSN, and (3) the estimation of the area of detected coverage hole, based on Computational Geometry.
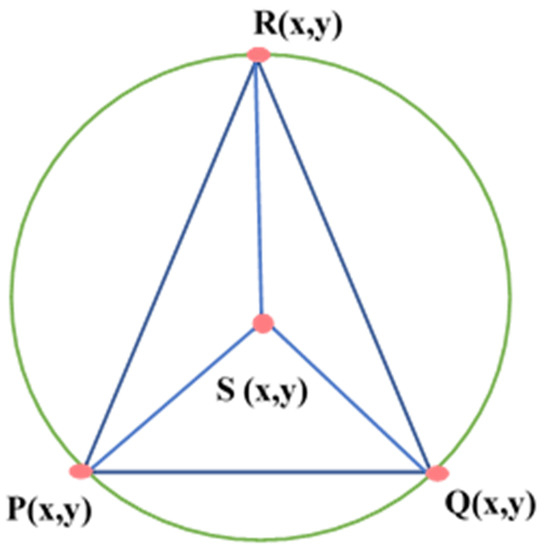
Figure 15.
A representation of the empty circle property.
A three-phase sink-and-sensors deployment strategy, the Evaluated Delaunay Triangulation-based Deployment for Smart Cities (EDTD-SC), is popular and outperforms random and regular deployments in terms of the area coverage and the end-to-end-delay by 29.6% and 29.7%, respectively [46]. The authors considered the indoor as well as the outdoor obstacles. The first phase is the configuration phase which includes a city map and obstacle information. The second phase is deploying the sensor nodes within the city based on the configuration phase. After deploying the sensor nodes, different triangles have been created using Delaunay Triangulation. The coverage evaluation step is defined to find the location of the new sensors. The coverage ratio helps in discovering the area with fewer sensors. It is calculated using the triangle’s center point. The third phase explained the proper position of sink deployment to gain a high network performance. The K- means clustering algorithm has been defined to make clusters based on the sensors deployment phase. Regarding area coverage and end-to-end delay, the EDTD-SC gives excellent results by considering the regular and the random deployment of sensor nodes. Various Computational Techniques based on Delaunay Triangulation have been described in Table 3.

Table 3.
Overview of Different Delaunay Triangulation-Based Techniques to Improve Coverage and Connectivity in WSNs.
3.3. The Voronoi Tessellation-Based Techniques
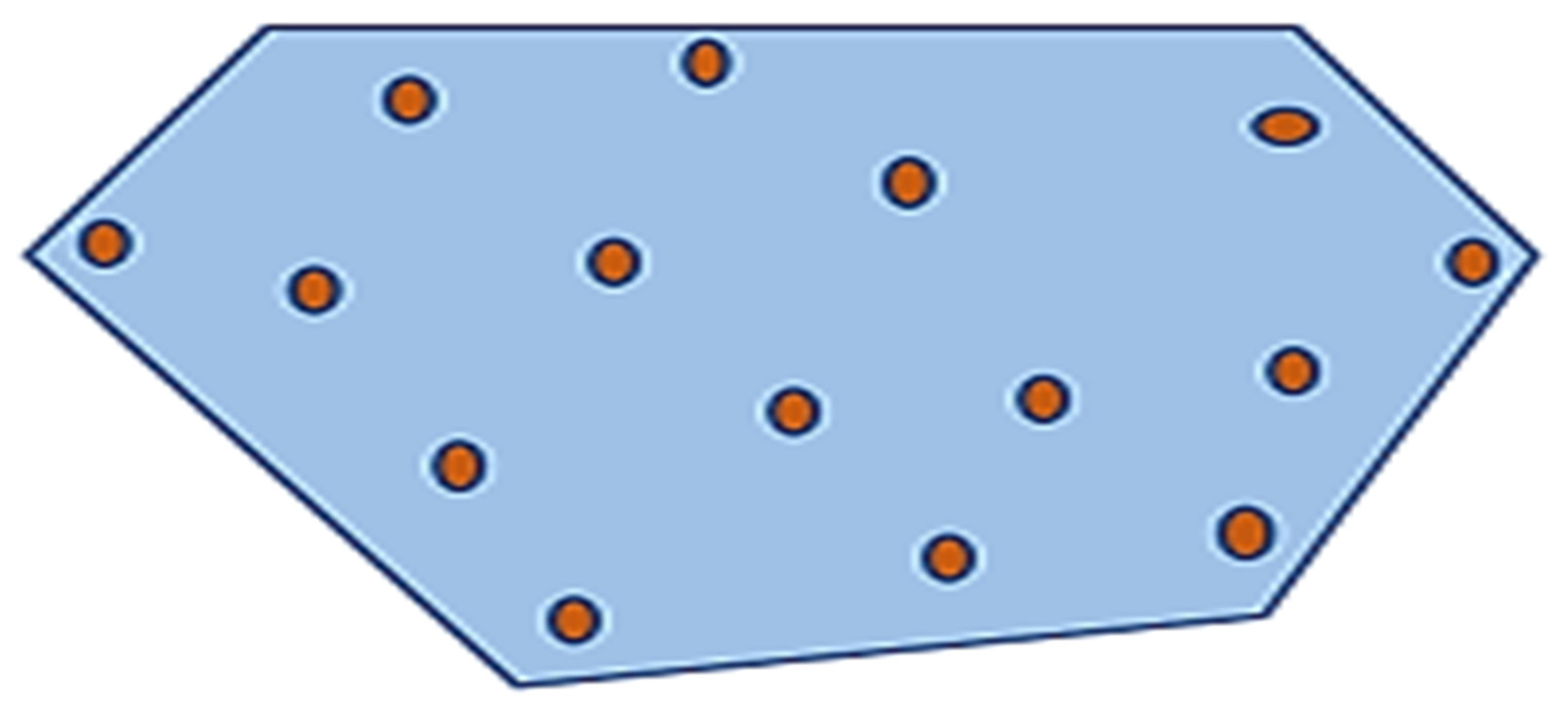
Voronoi Tessellation is an approach that is used to divide the given region into n units to structure uniform and non-uniform meshes. Voronoi Tessellations have various applications in computer science, chemistry, and the social sciences, etc. The Voronoi partition monitors the collection of disjoint regions by using sensors. Figure 16 describes the basic idea of Voronoi Tessellation. As shown in Figure 15 the given region is divided into n number of cells to create a tessellation. White dots depict the sensor nodes residing within the specific area. Every cell consists of only one sensor node, which is nearest to every point in the cell as compared to other neighboring sensor nodes. One of the best algorithms to create Voronoi Tessellation is Fortune’s algorithm.
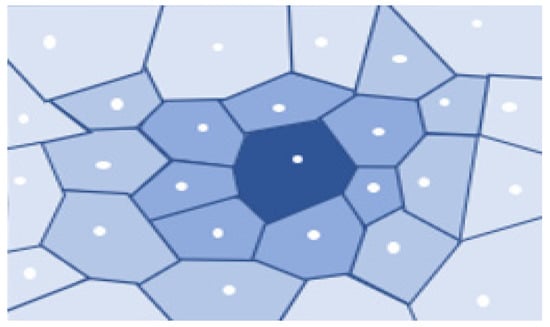
Figure 16.
Voronoi tessellation.
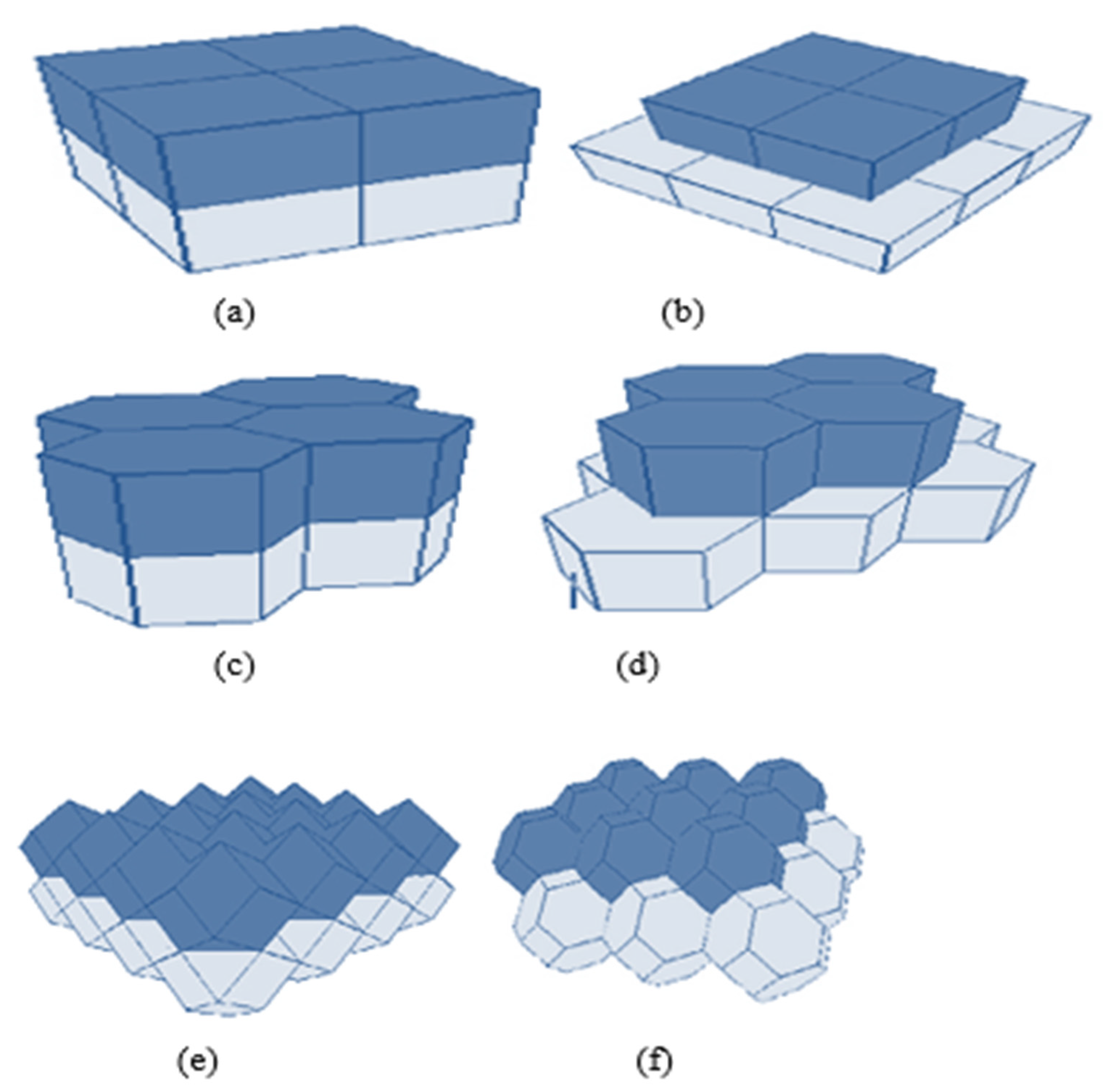
The authors in [19] have proposed a placement strategy based on the minimum number of nodes using Voronoi Tessellation. A truncated octahedron is used to cover the 3D sphere with a high volumetric quotient, as shown in Figure 17. A truncated Octahedron renders the best strategy compared to other data structures like the “Hexagonal Prism and Rhombic Dodecahedron.” The basic idea is taken from Kelvin’s conjecture, which explains: “What is the optimal way to fill a 3D space with cells of equal volume, so that surface area is minimized?”. Kelvin provided a solution with a truncated octahedron of 14 sides with isoperimetric inequality, but could not prove its optimality.
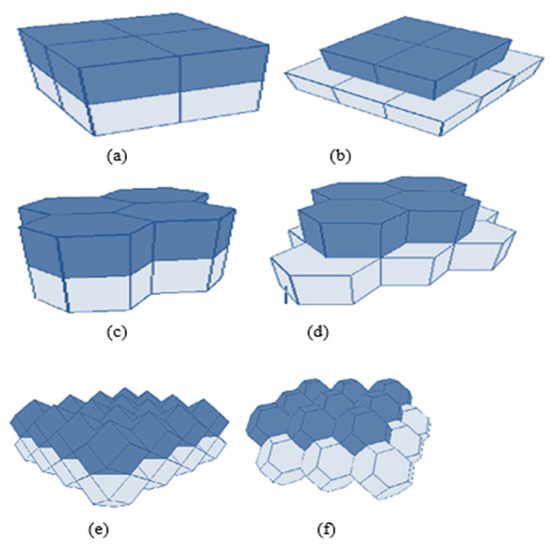
Figure 17.
Different 3D space-partitioning shapes (a) a Cube, (b) an Alternative-cube, (c) a Hexagonal Prism, (d) an Alternative- hexagonal prism, (e) a Rhombic Dodecahedron, and (f) a Truncated Octahedron.
The authors in [18] have used two Voronoi Polyhedrons, a Truncated Octahedron and a Hexagonal Prism, to accomplish full coverage and 14-connectivity and 6-connectivity, respectively. The authors have considered a Truncated Octahedron lattice pattern for 14-connectivity, eight of its 14-connected neighbor sensors are placed at the cube’s corner, and six are placed at the center of the six neighbor cubes. A Hexagonal Prism is used to achieve 6-connectivity; therefore, sensors at the cube’s center have six connected neighbors. Different Grid-based node deployment strategies are proposed by the authors in [47], such as a triangle, a square, a hexagon, a pentagon, and an octagon in a 2-D space. The authors equated all strategies with a respective number of sensors and coverage areas. It is resolved by them and the results that the octagon has the highest coverage, but the triangle and the hexagon have the least range. Although the octagon has the highest coverage, it requires the maximum number of nodes. Comparing these coverage issues and the number of nodes required, it has been concluded that a square is the best and most practical scheme.
The authors in [48] have proposed a three-dimensional coverage pattern based on cuboids by analyzing the regular polyhedron model. The minimum number of the sensor ensures complete network area coverage. The sensor nodes are deployed in the area of interest in the finite 3D grid. The authors assumed all the sensors were perceived in a uniformly sized sphere-shaped sensing field. As a result, the need for complete coverage of the monitored area can be met. This deployment method effectively reduces the number of nodes compared to the traditional random way. The authors in [49] have developed a method based on Voronoi Polygons for boundary node detection. A cluster can be defined by two types of boundaries: outside and inside edges. The coverage boundary problem needs to be transferred to identify all boundary nodes and there is a sudden reply to change the coverage without placing any communication burdens. For WSN coverage boundary node detection, the authors have developed a deterministic and localized algorithm. The technique relies entirely on one-hop information and a few easy local computations.
The author in [50] has given the solution to the optimal polyhedron for 3D space filler, which maximizes the coverage of sensors. It is found that the great rhombi cuboctahedron is the single largest enclosed convex polyhedral space filler. A Sensor selection algorithm is proposed for deterministic sensor placement, wherein the sensor is placed at the Centroid in a non-overlapping polyhedral space filler. The authors in [51] have designed a redeployment algorithm to achieve full coverage in 3D space. Every consumption factor is also considered as the sensor nodes have minimal energy. The authors have extended the Voronoi partitioning of 2D space to 3D, optimized according to the 3D partitioning. The author proposed a three-dimensional distributed virtual forces algorithm (3D-DVFA) commonly used for target detection. The algorithm is based on virtual forces where every node has attractive and repulsive forces.
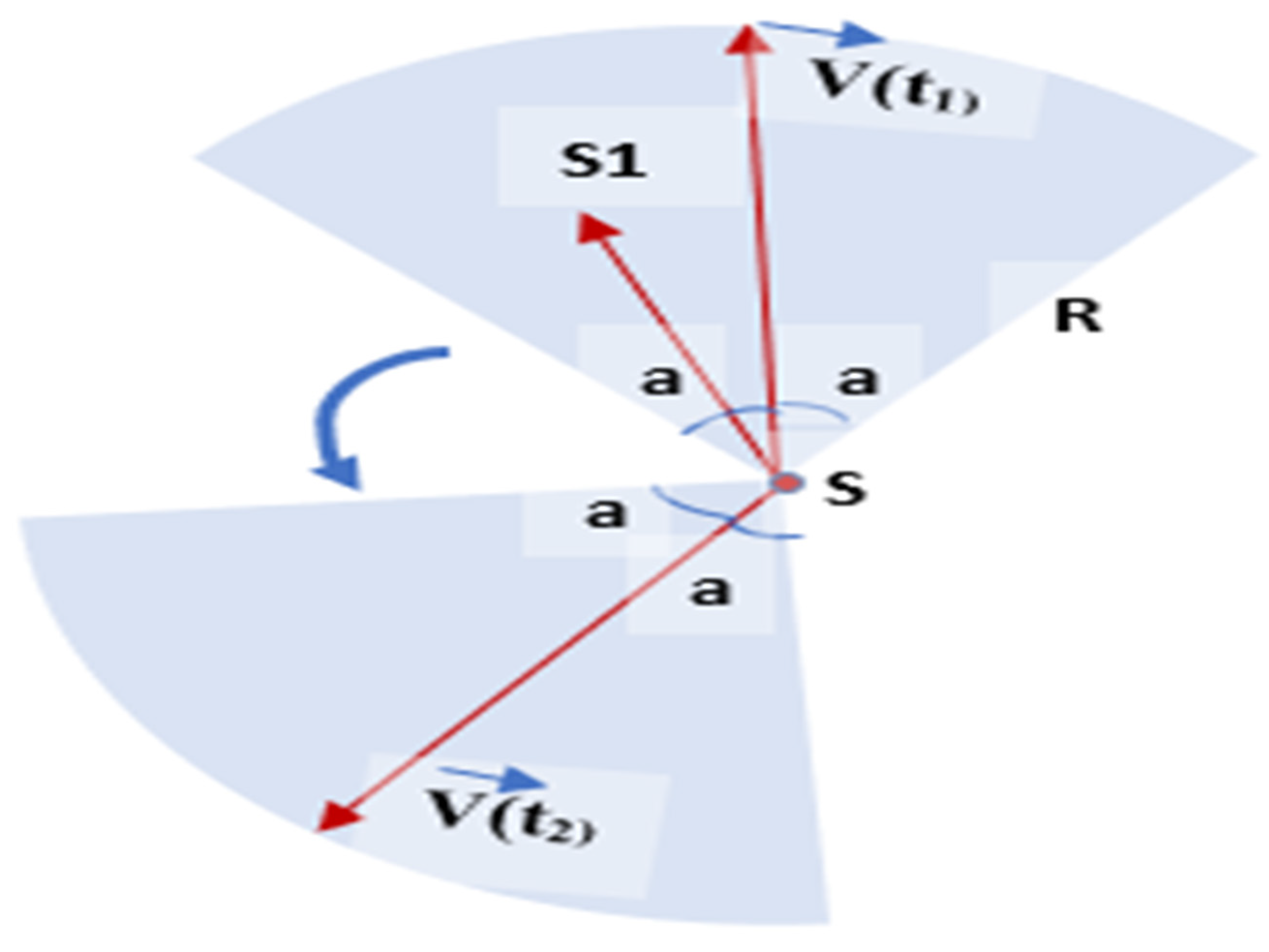
The K-Voronoi-based mobility model manipulates the coverage according to the target. Based on the Voronoi Diagram, a simplified mobility model is shown in Figure 18. This model enhances the overall coverage while maintaining more mobility choices. This mobility model preserves k-coverage by maintaining ground sensors in motion. These models allow multiple nodes to sense the area of interest simultaneously. The activity scheduling approach is also used to reduce the redundant nodes and save energy. The K-order Voronoi Diagram controls the sensor node mobility and the activity schedule [52].
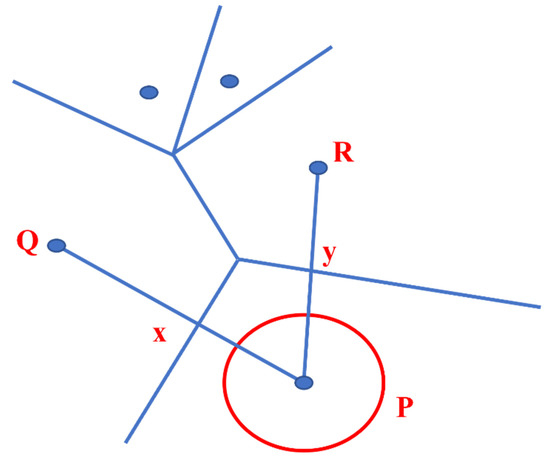
Figure 18.
A simplified mobility model.
The authors have proposed a heterogeneous sensor network in [53] to detect and heal holes in the coverage. The sensing radius of the new sensor deployed is different from the initially deployed sensors because some coverage holes of different sizes exist in the networks. The relationship between the radii of the nodes deployed initially, and the radii of nodes deployed later are explained to fill the various holes such as the trigonal, tetrahedral, octahedral, and interstitial holes. The sensors with the small radii have been deployed to fill the coverage hole and reduce the overall area’s cost. Table 4 expounds on different Voronoi Tessellation-based techniques to improve coverage and connectivity in WSNs.

Table 4.
An Overview of Different Voronoi Tessellation-Based Techniques to Improve Coverage and Connectivity in WSNs.
3.4. The Convex Hull-Based Techniques
The smallest convex polygon containing a particular set of nodes is called the Convex Hull of ‘n’ nodes. Graham’s Scan algorithm can be used to construct it in O (n log n) time [54,55]. In the two-dimensional Convex Hull, the set of points, i.e., set p = {pt, t = 1, 2,3, …, n} on a 2D plane V, and any limited points at set p, form all of the convex grouping and then construct a set H, which is called the Convex Hull of set p and can be represented by H(p) [56]:
In a two-dimensional plane V, H is the smallest convex polygon encompassing all the points in the set p and can be thought of as a two-dimensional Convex Hull containing the set p. The same is illustrated in Figure 19, where the geometry is a Convex Hull surrounding the point set in solid lines.
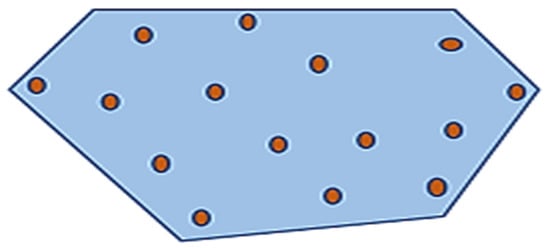
Figure 19.
A 2D Convex Hull.
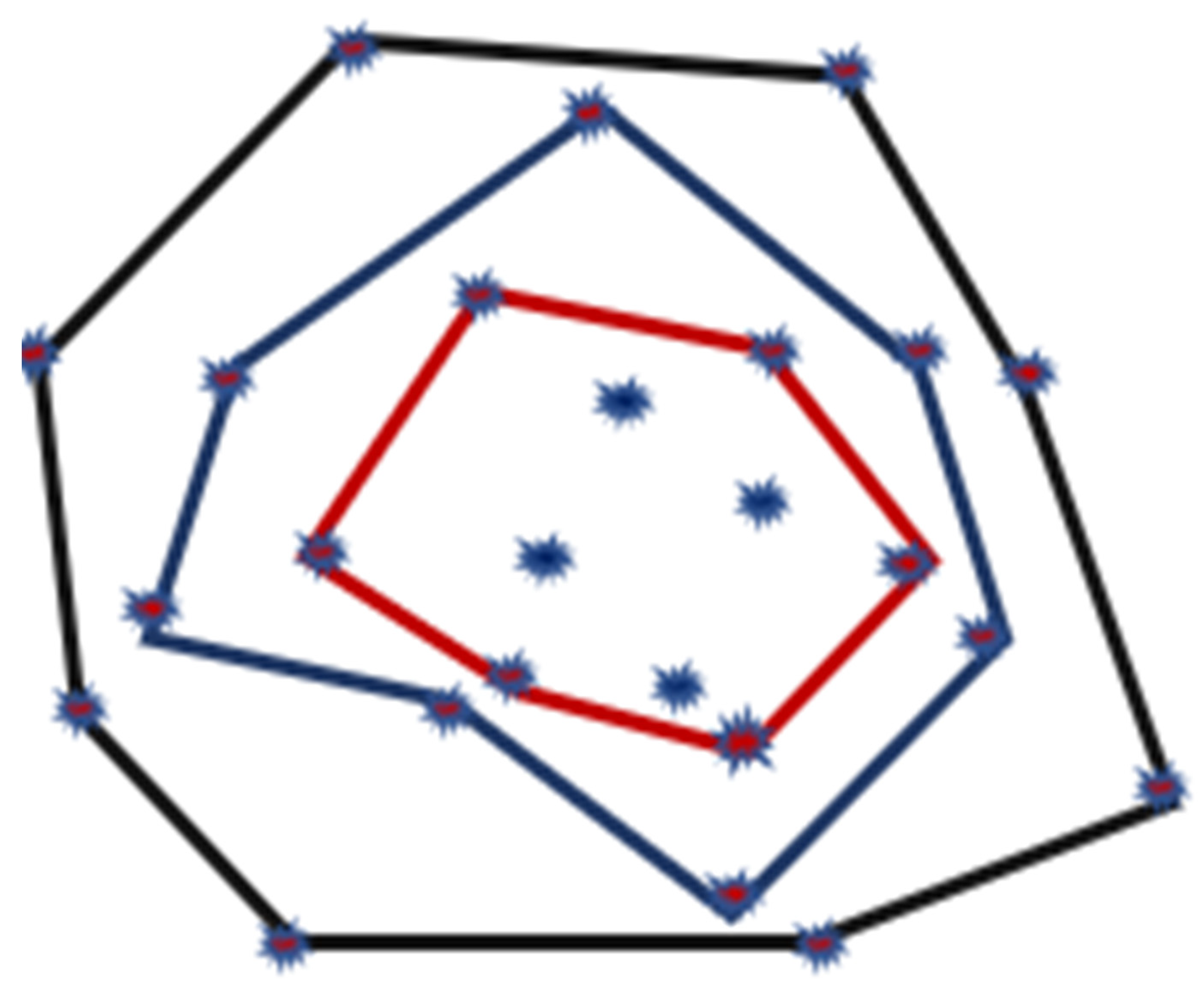
The minimum area convex set of a planar set having the original set known as the Convex Hull provides many solutions for existing problems. These problems are like Pattern Recognition, Image Processing, and Computer Graphics, in which a set consists of either an ‘n’ sided polygon or a set of n-points. The authors in [57] offer a coverage enhancement approach for reducing the overlapping sensing areas encompassed by many neighboring directional nodes. The directional sensing model estimates the total number of directional nodes used for a given area coverage. A sensing-connected sub-graph effectively divides the sensing area into distributed components. To improve coverage, a multi-layered Convex Hull set is employed to simulate each sensor-connected subgraph, as illustrated in Figure 20. Firstly, each sensing-connected subgraph forms a multi-layered Convex Hull set. Then, the direction of directed nodes is rotated to acquire the maximum sensing coverage area, as shown in Figure 21.
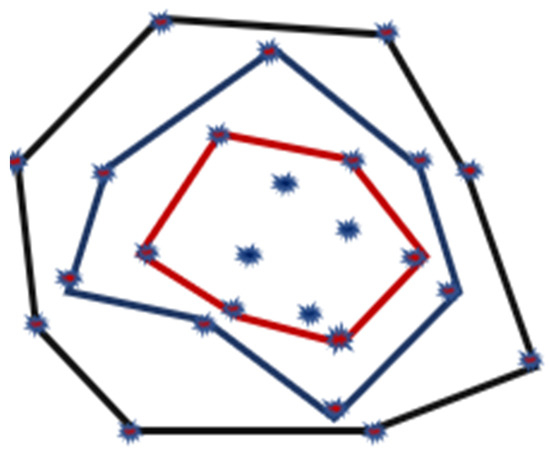
Figure 20.
The Multi-layered Convex Hull set.
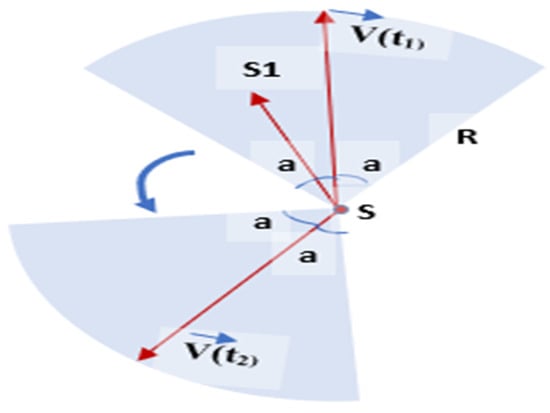
Figure 21.
Sensing directions of directional nodes.
The authors in [58] have proposed a source localization approach. When the source exists outside the Convex Hull, the authors examined the local convergence problem and the problem with the projection onto the convex set (POCS). A fast, low, complexity approach, i.e., a semi-definite programming algorithm, has been created based on a problem revolution for two different source localization models.
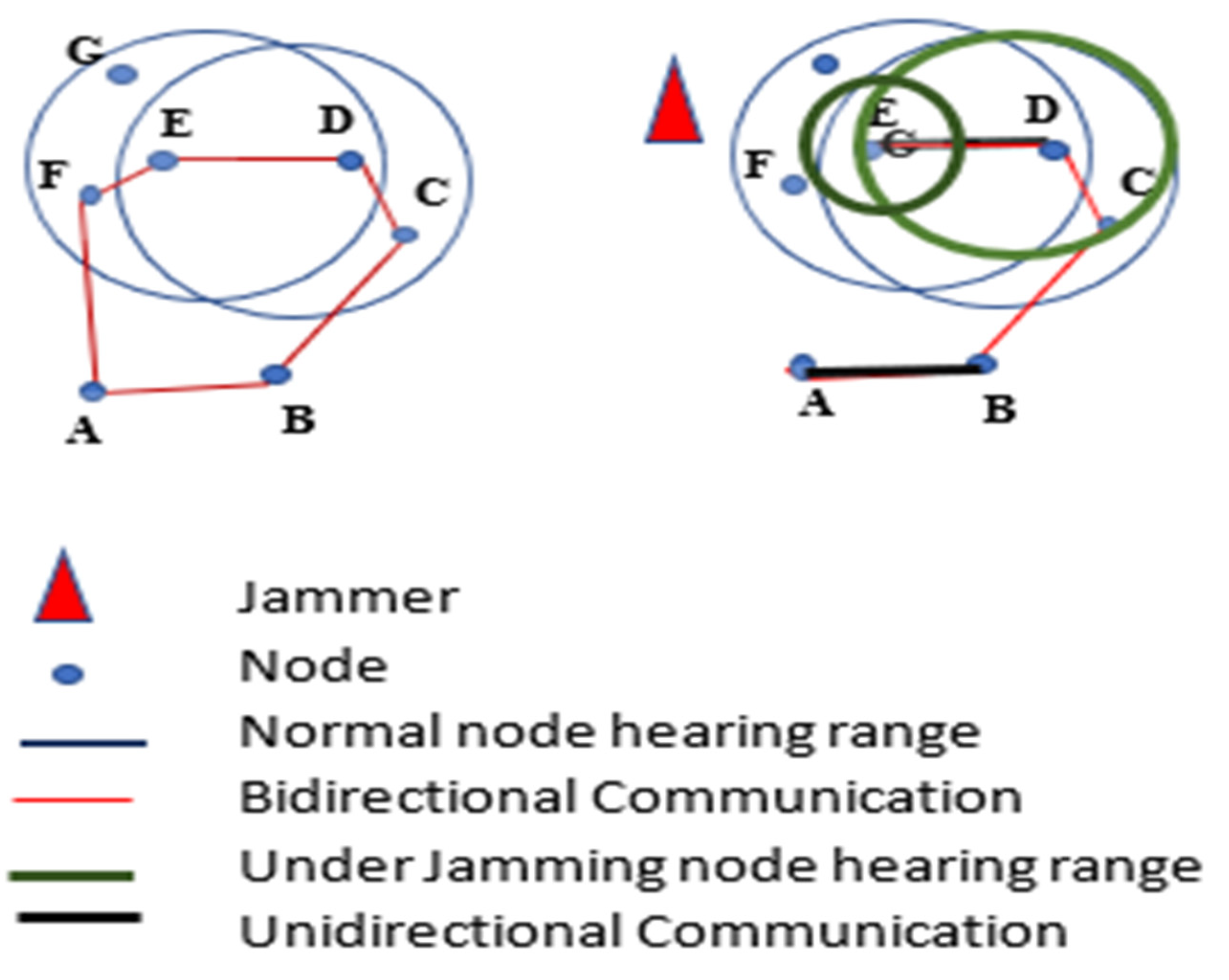
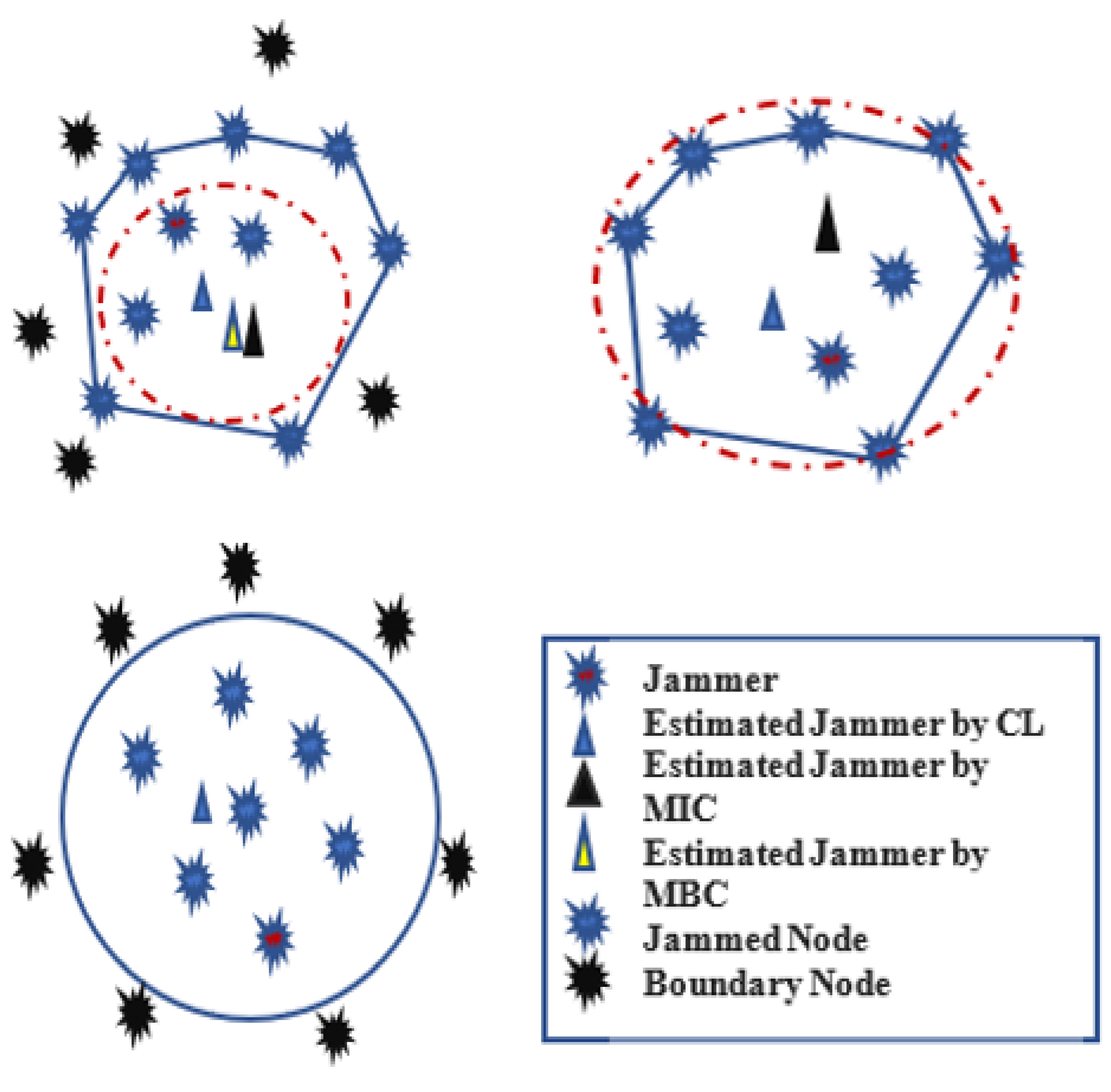
The authors in [59] proposed a Maximum Inscribed Circle (MIC) and Minimum Boundary Circle (MBC) -based approach called a Double Circle Localization (DCL) to address the problem of jammer localization. Figure 22 depicts the jammer model and the impacts of jamming on communication. Figure 23 shows the algorithm with no other assumptions regarding the crowded area. Different existing algorithms like Centroid Localization (CL), Weighted Centroid Localization (WCL), and Virtual Force Iterative Localization (VFIL) have been compared with the new algorithm DCL, which performs better in all proposed conditions.
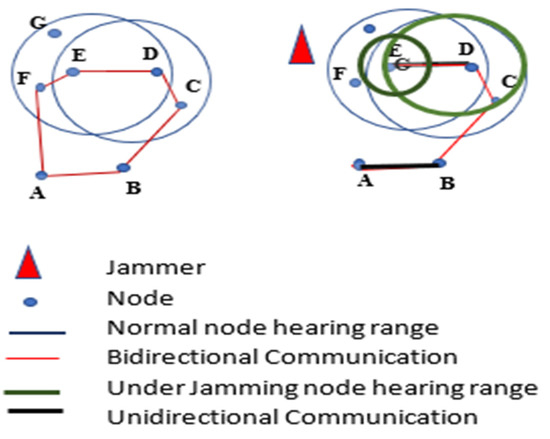
Figure 22.
Jamming effects on WSNs.
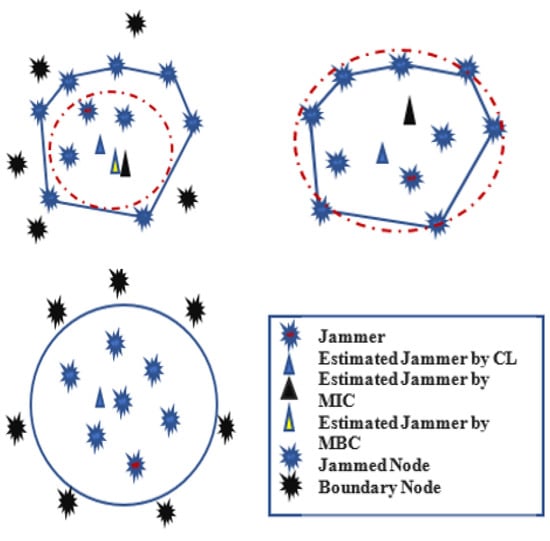
Figure 23.
Double circle localization (DCL).
The authors use the Convex Hull in [60] to solve the minimum path data gathering problem. This research selects a delegation node in every sub-network and then the Convex Hull-based algorithm is designed. Two properties have been used: (1) the Convex Hull boundary nodes must be present in the optimal solution of the Euclidean traveling salesman problem, and (2) the Convex Hull never intersects with itself. As compared to the greedy algorithm, the Convex Hull is closer to the optimal solution, and its complexity is O(N + n3).
The authors [61] presented the Voronoi Diagram Greedy (VD-GREEDY) and the Convex Hull Most Forward Progress within the Radius (CH-MFR) routing algorithms to address the twin issues of routing and geocaching. The VD-GREEDY is predicated on identifying node neighbors close to a potential target location and several methods have been discussed for determining such neighbors. The CH-MFR has described the Convex Hull problem on neighboring nodes, and the range directional (R-DIR) is a modified version of the presented directional methods. Loop avoidance, success rates, and flooding rates are the advantages of using CH-MFR and VD-GREEDY schemes. The authors in [62] have described a Second-Order Cone Programming (SOCP) -based two-step method for distributed localization. Based on limited information, the sensor nodes initially find their location, and subsequently, the anchor nodes upgrade their positions using information from neighbors. SOCP is used because of its straightforward structure and ability to solve problems faster. This technique improves the position of the anchor nodes in their neighbors’ Convex Hulls. In [63], two approaches are explored to resemble the forest fire forms with shared WSNs that work in a fully distributed manner without a base station and with the information collected by each node through broadcast. In the first approach, the punctual model is considered in which every node stores and forwards all information as received. This approach requires the distribution of a large number of data packets. To handle such a massive quantity of data packets, the Convex Hull-based model has been used. The nodes process all the information collected and discard what is irrelevant.
Consequently, each network node would be aware of the set of points reached so far by the fire at any given time. An interpretation of the fire processed with this data would be fairly true. In-network, the data aggregation technique is applied as the second approach to obtain a more compact fire model. The authors in [64] provide the geographic routing technique k-MLP (Multi-Lane Routing Path) to address caverns around a complex-shaped coverage hole. This scheme extends the network lifetime and the load balancing compared to other existing routing algorithms. The routing scheme consists of two phases: (i) the initialization phase and (ii) the routing phase. The boundary nodes inside a cavern compute the Convex Hull of the hole shape. The shortest routing path is determined in the routing phase with the idea of achieving almost k parallel lines. The authors in [65] have tried to reduce the overall cost of network establishment. For this, the authors have focused on the locations of node placement and trajectory determination for Mobile Sink (MS) so that targets are under the coverage of sensors and information packets are transferred to MS. Also, many studies resolve wireless sensor networks using artificial intelligent techniques such as in [66,67,68,69,70].
Moreover, the authors have utilized the concept of the convex polygon in the 2D plane and a graph-based approach to optimize the number of sensor nodes. Thus, reducing the total cost of network deployment. An overview of the different Convex Hull-based techniques is given in Table 5.

Table 5.
An Overview of the Different Convex Hull-Based Techniques to Improve Coverage and Connectivity in WSNs.
4. Current Research Challenges and Solutions
After knowing the sensor nodes’ positions, Computational Geometry approaches can be used to address several challenges in WSNs. Using the idea of CG Techniques, a number of sensor nodes can be optimized, and the longevity of WSNs can be improved to a certain extent. Due to the nature and deployment of WSNs, the creation of coverage holes is inherent, and these coverage holes can be detected and healed using CG Techniques. A summary of various problems that have been addressed and the corresponding contribution of various articles included in this study is presented in Table 6. Also, Table 7 which is showing the research issues/challenges which were covered or not covered (treated as limitations) is given in the same section.

Table 6.
Summary of various Problem Statements and the corresponding solution/contribution of by various articles.

Table 7.
The research issues/challenges covered or not covered (limitations) by various articles.
5. Conclusions and Future Scope
This paper expounds on the existing work done in WSNs using Computational Geometry-based techniques. In comprising Wireless Sensor Networks, the arrangement of sensor nodes and their communication links, that is, network topology, plays a vital role. The structural properties of various Computational Geometric structures can be applied to network topology control. Computational Geometry is very helpful to maintain network connectivity and to optimize its lifetime and throughput, so that an efficient routing for the network can be designed. Furthermore, a network is fault tolerant only if it is k-connected. By merely employing various data structures, it has been made possible to solve recurring complications like fault tolerance, dimensionality, the discovery and healing of the coverage holes, the minimization of the number of node deployments, and the cutting down on costs, etc. Various optimization techniques have been examined to conclude the world-beating solution to overcome the existing loopholes. The proposed solutions would aid curious researchers in exploring existing data structures of Computational Geometry. During detailed analysis of actual work done, it has been ascertained that the research using the 2D computational models has been comprehensive. However, to bridge the dimensionality gap, it is pertinent to mention the 3D models as they simulate the real operating environment. The 3D savvy models would also attract the inherent challenges embedded in 3D computational models. In addition, techniques for reducing the number of nodes deployed for particular WSNs, while maintaining the coverage and connectivity, also draw the attention of research scholars. Hence, future aspirants need to be future-ready with the required aptitude to address these burning issues. On the basis of research articles included in the present work, some of these current issues are listed below-
- (a)
- Future researchers should focus on working with the two-dimensional, and specifically the three-dimensional, heterogeneous environments where the sensing and communication ranges or the deployment of sensors with different sensing ranges may be different, etc.
- (b)
- Researchers must direct attention towards achieving k-Coverage where k ≥ 1 in sensitive regions.
- (c)
- Research should be performed within an environment where obstacles are present, as obstacles are always present in real scenarios.
- (d)
- Researchers should also focus on issues like mobility of target events as well as the testing of sensors in physical environments.
- (e)
- Researchers should try to work out the techniques for finding and repairing the coverage holes without creating new holes.
- (f)
- Researchers should also address the issue of finding the shortest path for sensor node movement.
Author Contributions
S.D., A.S. (Anju Sangwan): Conceptualization, Investigation, Methodology, Resources, Software, Writing—original draft. A.S. (Anupama Sangwan), M.A.M., K.K., J.N., R.M., P.Z.: Investigation, Validation, Review and Editing. All authors have read and agreed to the published version of the manuscript.
Funding
This research work was partially supported by the Ministry of Education of the Czech Republic (Project No. SP2022/18 and No. SP2022/34) and partially by the European Regional Development Fund in Research Platform focused on Industry 4.0 and Robotics in Ostrava project, CZ.02.1.01/0.0/0.0/17_049/0008425 within the Operational Program Research, Development, and Education.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Dang, X.; Shao, C.; Hao, Z. Target detection coverage algorithm based on 3D-Voronoi partition for three-dimensional wireless sensor networks. Mob. Inf. Syst. 2019, 2019, 7542324. [Google Scholar] [CrossRef]
- Olatinwo, S.O.; Joubert, T.-H. Enabling communication networks for water quality monitoring applications: A survey. IEEE Access 2019, 7, 100332–100362. [Google Scholar] [CrossRef]
- Li, J.; Andrew, L.L.; Foh, C.H.; Zukerman, M.; Chen, H.H. Connectivity, coverage and placement in wireless sensor networks. Sensors 2009, 9, 7664–7693. [Google Scholar] [CrossRef] [PubMed]
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: A survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Tripathi, A.; Gupta, H.P.; Dutta, T.; Mishra, R.; Shukla, K.K.; Jit, S. Coverage and connectivity in WSNs: A survey, research issues and challenges. IEEE Access 2018, 6, 26971–26992. [Google Scholar] [CrossRef]
- Maheshwari, A.; Chand, N. A Survey on Wireless Sensor Networks Coverage Problems. In Proceedings of the 2nd International Conference on Communication, Computing and Networking, Haldia, India, 14–15 March 2019. [Google Scholar]
- Khoufi, I.; Minet, P.; Laouiti, A.; Mahfoudh, S. Survey of deployment algorithms in wireless sensor networks: Coverage and connectivity issues and challenges. Int. J. Auton. Adapt. Commun. Syst. 2017, 10, 341–390. [Google Scholar] [CrossRef]
- Krishnan, M.; Rajagopal, V.; Rathinasamy, S. Performance evaluation of sensor deployment using optimization techniques and scheduling approach for K-coverage in WSNs. Wirel. Netw. 2018, 24, 683–693. [Google Scholar] [CrossRef]
- Zhang, H.; Hou, J.C. Maintaining sensing coverage and connectivity in large sensor networks. Ad Hoc Sens. Wirel. Netw. 2005, 1, 124–189. [Google Scholar]
- Bala, T.; Bhatia, V.; Kumawat, S.; Jaglan, V. A survey: Issues and challenges in wireless sensor network. Int. J. Eng. Technol. 2018, 7, 53–55. [Google Scholar] [CrossRef]
- Zarei, Z.; Bag-Mohammadi, M. Coverage improvement using Voronoi diagrams in directional sensor networks. IET Wirel. Sens. Syst. 2021, 11, 111–119. [Google Scholar] [CrossRef]
- Sharma, P.; Singh, R.P. Energy-Efficient Deterministic Approach for Coverage Hole Detection in Wireless Underground Sensor Network: Mathematical Model and Simulation. Computer 2022, 11, 86. [Google Scholar] [CrossRef]
- Shao, C. Wireless Sensor Network Target Localization Algorithm Based on Two- and Three-Dimensional Delaunay Partitions. J. Sens. 2021, 2021, 4047684. [Google Scholar] [CrossRef]
- Huang, S.-C.; Huang, C.-H. Algorithms for Detecting and Refining the Area of Intangible Continuous Objects for Mobile Wireless Sensor Networks. Algorithms 2022, 15, 31. [Google Scholar] [CrossRef]
- Hao, Z.; Dang, J.; Yan, Y.; Wang, X. A node localization algorithm based on Voronoi diagram and support vector machine for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2021, 7, 1–15. [Google Scholar] [CrossRef]
- Li, X.Y.; Wang, Y. Wireless Sensor Networks and Computational Geometry. In Handbook of Sensor Networks; Ilyas, M., Ed.; CRC Press: Boca Raton, FL, USA, 2003; pp. 1025–1028. [Google Scholar]
- Farsi, M.; Elhosseini, M.A.; Badawy, M.; Ali, H.A.; Eldin, H.Z. Deployment techniques in wireless sensor networks, coverage and connectivity: A survey. IEEE Access 2019, 7, 28940–28954. [Google Scholar] [CrossRef]
- Bai, X.; Zhang, C.; Xuan, D.; Jia, W. Full-Coverage and k-Connectivity (k = 14, 6) Three Dimensional Networks. In Proceedings of the IEEE INFOCOM, Rio de Janeiro, Brazil, 19–25 April 2009; pp. 388–396. [Google Scholar]
- Alam, S.N.; Haas, Z.J. Coverage and connectivity in three-dimensional networks with random node deployment. Ad. Hoc. Netw. 2015, 34, 157–169. [Google Scholar] [CrossRef]
- Boukerche, A.; Fei, X. A Voronoi Approach for Coverage Protocols in Wireless Sensor Networks. In Proceedings of the IEEE GLOBECOM 2007- IEEE Global Telecommunications Conference, Washington, DC, USA, 26–30 November 2007; pp. 5190–5194. [Google Scholar]
- Xie, Y.; Zhang, C.; Lai, Q. China’s rise as a major contributor to science and technology. Proc. Natl. Acad. Sci. USA 2014, 111, 9437–9442. [Google Scholar] [CrossRef]
- Wang, G.; Cao, G.; La, T.F. Porta Movement-assisted sensor deployment. IEEE Trans. Mob. Comput. 2006, 5, 640–652. [Google Scholar] [CrossRef]
- Dai, G.; Lv, H.L.; Chen; Zhou, B.; Xu, P. A novel coverage holes discovery algorithm based on voronoi diagram in wireless sensor networks. Int. J. Hybrid Inf. Technol. 2016, 9, 273–282. [Google Scholar] [CrossRef]
- Han, Y.H.; Kim, Y.; Kim, W.; Jeong, Y.S. An energy-efficient self-deployment with the centroid-directed virtual force in mobile sensor networks. Simulation 2012, 88, 1152–1165. [Google Scholar] [CrossRef]
- Sung, T.W.; Yang, C.S. Voronoi-based coverage improvement approach for wireless directional sensor networks. J. Netw. Comput. Appl. 2014, 39, 202–213. [Google Scholar] [CrossRef]
- Lee, H.J.; Kim, Y.; Han, Y.H.; Park, C.Y. Centroid-Based Movement Assisted Sensor Deployment Schemes in Wireless Sensor Networks. In Proceedings of the 70th IEEE Vehicular Technology Conference Fall, Anchorage, AK, USA, 20–23 September 2009; pp. 1–5. [Google Scholar]
- Megerian, S.; Koushanfar, F.; Potkonjak, M.; Srivastava, M.B. Worst and best-case coverage in sensor networks. IEEE Trans. Mob. Comput. 2005, 4, 84–92. [Google Scholar]
- Fang, W.; Song, X.; Wu, X.; Sun, J.; Hu, M. Novel efficient deployment schemes for sensor coverage in mobile wireless sensor networks. Inf. Fusion 2018, 41, 25–36. [Google Scholar] [CrossRef]
- Abbasi, F.; Mesbahi, A.; Velni, J.M. A new voronoi-based blanket coverage control method for moving sensor networks. IEEE Trans. Control Syst. Technol. 2017, 27, 409–417. [Google Scholar] [CrossRef]
- Khelil, A.; Beghdad, R. Esa: An efficient self-deployment algorithm for coverage in wireless sensor networks. Procedia Comput. Sci. 2016, 98, 40–47. [Google Scholar] [CrossRef][Green Version]
- Ingle, M.R.; Bawane, N. An Energy Efficient Deployment of Nodes in Wireless Sensor Network Using Voronoi Diagram. In Proceedings of the 3rd International Conference on Electronics Computer Technology, Kanyakumari, India, 8–10 April 2011; Volume 6, pp. 307–311. [Google Scholar]
- Sung, T.W.; Yang, C.S. Coverage Improvement for Directional Sensor Networks. In Advances in Intelligent Systems and Applications—Volume 1. Smart Innovation, Systems and Technologies; Chang, R.S., Jain, L., Peng, S.L., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; Volume 20. [Google Scholar] [CrossRef]
- Chowdhury, A.; De, D. Energy-efficient coverage optimization in wireless sensor networks based on Voronoi-Glowworm Swarm Optimization-K-means algorithm. Ad Hoc Netw. 2021, 122, 102660. [Google Scholar] [CrossRef]
- Delaunay Triangulation Wikipedia. Available online: https://en.wikipedia.org/wiki/Delaunay_triangulation (accessed on 22 June 2022).
- Rahman, M.N.; Hanuranto, M.I.; Mayasari, S.R. Trilateration and Iterative Multilateration Algorithm for Localization Schemes on Wireless Sensor Network. In Proceedings of the 2017 International Conference on Control, Electronics, Renewable Energy and Communications (ICCREC), Yogyakarta, Indonesia, 26–28 September 2017; pp. 88–92. [Google Scholar]
- Qiu, C.; Shen, H. A delaunay-based coordinate-free mechanism for full coverage in wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2013, 25, 828–839. [Google Scholar] [CrossRef]
- Dubey, R. Constrained Delaunay Triangulation for Wireless Sensor Network. IOSR J. Comput. Eng. 2013, 8, 46–53. [Google Scholar] [CrossRef]
- Surekha, S.; KalyanRam, M. Coverage of total Target Field to Form WSN using Delaunay Triangulation. Int. J. Comput. Sci. Inf. Technol. 2013, 4, 796–799. [Google Scholar]
- Wu, C.-H.; Lee, K.C.; Chung, Y.C. A Delaunay triangulation based method for wireless sensor network deployment. Comput. Commun. 2007, 30, 2744–2752. [Google Scholar] [CrossRef]
- Tahmasbi, M.; Malazi, H.T.; Eltejaei, F. Delaunay Based Two-Phase Algorithm for Connected Cover in WSNs. In Proceedings of the 19th International Symposium on Computer Architecture and Digital Systems (CADS), Kish Island, Iran, 21–22 December 2017; pp. 1–5. [Google Scholar]
- Nespolo, R.; Neves, L.A.; Roberto, G.; Ribeiro, M.; Nascimento, M.Z.D.; Cansian, A. Method Based on Triangulation for Sensor Deployment on 3D Surfaces. In Proceedings of the 29th SIBGRAPI Conference on Graphics, Patterns and Images (SIBGRAPI), Sao Paulo, Brazil, 4–7 October 2016; pp. 136–143. [Google Scholar]
- Wang, S.Y.; Shih, K.P.; Chen, Y.D.; Ku, H.H. Preserving Target Area Coverage in Wireless Sensor Networks by Using Computational Geometry. In Proceedings of the IEEE Wireless Communication and Networking Conference, Sydney, NSW, Australia, 18–21 April 2010; pp. 1–6. [Google Scholar]
- Chizari, H.; Hosseini, M.; Poston, T.; Razak, S.A.; Abdullah, A.H. Delaunay triangulation as a new coverage measurement method in wireless sensor network. Sensors 2011, 11, 3163–3176. [Google Scholar] [CrossRef] [PubMed]
- Zhang, G.; Qi, C.; Zhang, W.; Ren, J.; Wang, L. Estimation and healing of coverage hole in hybrid sensor networks: A simulation approach. Sustainability 2017, 9, 1733. [Google Scholar] [CrossRef]
- Das, S.; DebBarma, M.K. Computational geometry based coverage hole-detection and hole-area estimation in wireless sensor network. J. High Speed Netw. 2018, 24, 281–296. [Google Scholar] [CrossRef]
- Alablani, I.; Alenazi, M. EDTD-SC: An IoT sensor deployment strategy for smart cities. Sensors 2020, 20, 7191. [Google Scholar] [CrossRef]
- Katti, A.; Lobiyal, D.K. Node Deployment Strategies for a 2D Wireless Sensor Network. In Proceedings of the International Conference on Computing, Communication and Automation (ICCCA), Greater Noida, India, 5–6 May 2017; pp. 658–663. [Google Scholar]
- Xiao, F.; Yang, Y.; Wang, R.; Sun, L. A novel deployment scheme based on three-dimensional coverage model for wireless sensor networks. Sci. World J. 2014, 2014, 846784. [Google Scholar] [CrossRef]
- Zhang, C.; Zhang, Y.; Fang, Y. Detecting Coverage Boundary Nodes in Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Networking, Sensing and Control, Ft. Lauderdale, FL, USA, 23–25 April 2006; pp. 868–873. [Google Scholar]
- Ammari, H.M. Connected Coverage in Three-Dimensional Wireless Sensor Networks Using Convex Polyhedral Space-Fillers. In Proceedings of the 13th International Conference on Distributed Computing in Sensor Systems (DCOSS), Ottawa, ON, Canada, 5–7 June 2017; pp. 183–190. [Google Scholar]
- Boufares, N.; Khoufi, I.; Minet, P.; Saidane, L.; Saied, Y.B. Three Dimensional Mobile Wireless Sensor Networks Redeployment Based on Virtual Forces. In Proceedings of the International Wireless Communications and Mobile Computing Conference (IWCMC), Dubrovnik, Croatia, 24–28 August 2015; pp. 563–568. [Google Scholar]
- Abdelkader, M.; Hamdi, M.; Boudriga, N. Multi-target Tracking Using Wireless Sensor Networks Based on Higher-Order Voronoi Diagrams. J. Netw. 2009, 4, 589–597. [Google Scholar] [CrossRef]
- Sangwan, A.; Singh, R.P. Coverage hole detection and healing to enhance coverage and connectivity in 3D spaces for WSNs: A mathematical analysis. Wirel. Pers. Commun. 2017, 96, 2863–2876. [Google Scholar] [CrossRef]
- O’Rourke, J. Computational Geometry in C; Cambridge University Press: Cambridge, UK, 1998. [Google Scholar]
- Gries, D.; Stojmenovic, I. A Note on Graham’s Cot\Ivex Hull Algorithm. Inf. Processing Lett. 1987, 25, 323–327. [Google Scholar] [CrossRef]
- Jiang, P.; Liu, S.; Liu, J.; Wu, F.; Zhang, L. A depth-adjustment deployment algorithm based on two-dimensional convex hull and spanning tree for underwater wireless sensor networks. Sensors 2016, 7, 1087. [Google Scholar] [CrossRef]
- Tao, D.; Ma, H.; Liu, L. Coverage-Enhancing Algorithm for Directional Sensor Networks. In Proceedings of the International Conference on Mobile Ad-Hoc and Sensor Networks, Hong Kong, China, 13–15 December 2006; pp. 256–267. [Google Scholar]
- Meng, C.; Ding, Z.; Dasgupta, S. A semidefinite programming approach to source localization in wireless sensor networks. IEEE Signal Processing Lett. 2008, 15, 253–256. [Google Scholar] [CrossRef]
- Cheng, T.; Li, P.; Zhu, S. An Algorithm for Jammer Localization in Wireless Sensor networks. In Proceedings of the 26th IEEE International Conference on Advanced Information Networking and Applications, Fukuoka, Japan, 26–29 March 2012; pp. 724–731. [Google Scholar]
- Wu, F.J.; Huang, C.F.; Tseng, Y.C. Data Gathering by Mobile Mules in a Spatially Separated Wireless Sensor Network. In Proceedings of the Tenth International Conference on Mobile Data Management: Systems, Services and Middleware, Taipei, Taiwan, 18–20 May 2009; pp. 293–298. [Google Scholar]
- Stojmenovic, I.; Ruhil, A.P.; Lobiyal, D.K. Voronoi diagram and convex hull based geocasting and routing in wireless networks. Wirel. Commun. Mob. Comput. 2006, 6, 247–258. [Google Scholar] [CrossRef]
- Srirangarajan, S.; Tewfik, A.H.; Luo, Z.Q. Distributed Sensor Network Localization with Inaccurate Anchor Positions and Noisy Distance Information. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP’07), Honolulu, HI, USA, 15–20 April 2007; p. III-521. [Google Scholar]
- Serna, M.A.; Bermudez, A.; Casado, R.; Kulakowski, P. A convex hull-based approximation of forest fire shape with distributed wireless sensor networks. In Proceedings of the Seventh International Conference on Intelligent Sensors, Sensor Networks and Information Processing, Adelaide, SA, Australia, 6–9 December 2011; pp. 419–424. [Google Scholar]
- Nguyen, K.V.; Nguyen, C.H.; Nguyen, P.L.; Do, T.V.; Chlamtac, I. Energy-efficient routing in the proximity of a complicated hole in wireless sensor networks. Wirel. Netw. 2021, 27, 3073–3089. [Google Scholar] [CrossRef]
- Dinh, M.H.; Hoang, N.T.; Nguyen, M.P.; Nguyen, P.L.; Do, P.T. Node Deployment Optimization for Target Coverage and Connectivity in WSNs with a Delay-Constrained Mobile Sink. In Proceedings of the 8th IEEE International Conference on Communications and Electronics (ICCE), Phu Quoc Island, Vietnam, 13–15 January 2021; pp. 515–520. [Google Scholar] [CrossRef]
- Mahdi, O.A.; Al-Mayouf, Y.B.; Ghazi, A.B.; Wahab, A.A.; Idris, M.Y.I.B. An energy-aware and load-balancing routing scheme for wireless sensor networks. Indones. J. Electr. Eng. Comput. Sci. 2018, 12, 1312–1319. [Google Scholar]
- Sharma, P.; Singh, R.P.; Mohammed, M.A.; Shah, R.; Nedoma, J. A survey on holes problem in wireless underground sensor networks. IEEE Access 2021, 10, 7852–7880. [Google Scholar] [CrossRef]
- Lakhan, A.; Mohammed, M.A.; Rashid, A.N.; Kadry, S.; Abdulkareem, K.H. Deadline aware and energy-efficient scheduling algorithm for fine-grained tasks in mobile edge computing. Int. J. Web Grid Serv. 2022, 18, 168–193. [Google Scholar] [CrossRef]
- Azizan, A.H.; Mostafa, S.A.; Mustapha, A.; Foozy, C.F.M.; Wahab, M.H.A.; Mohammed, M.A.; Khalaf, B.A. A machine learning approach for improving the performance of network intrusion detection systems. Ann. Emerg. Technol. Comput. (AETiC) 2021, 5, 201–208. [Google Scholar] [CrossRef]
- Kumar, S.; Raw, R.S.; Bansal, A.; Mohammed, M.A.; Khuwuthyakorn, P.; Thinnukool, O. 3D location oriented routing in flying ad-hoc networks for information dissemination. IEEE Access 2021, 9, 137083–137098. [Google Scholar] [CrossRef]
- Lu, X.; Su, Y.; Wu, Q.; Wei, Y.; Wang, J. An improved coverage gap fixing method for heterogenous wireless sensor network based on Voronoi polygons. Alex. Eng. J. 2021, 60, 4307–4313. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).