A Kamm’s Circle-Based Potential Risk Estimation Scheme in the Local Dynamic Map Computation Enhanced by Binary Decision Diagrams
Abstract
:1. Introduction
- Layer 1: Contains permanent static information. It is a map database that preferably contains detailed road map information with application to advanced driver assistance systems (ADAS).
- Layer 2: This layer is an extension of layer 1. It includes quasi-static information, e.g., traffic signs, trees, and buildings.
- Layer 3: LDM stores temporary information for a particular region in this layer, e.g., traffic jams, weather conditions, and traffic signals.
- Layer 4: Contains temporary information about dynamic or highly dynamic objects, e.g., moving vehicles and pedestrians.
- The vehicle’s future geographical occupancy over time as a feature in the LDM.
- A extended method of data representation for a vehicle’s geographical occupancy information using a BDD.
- Possible algebraic operations between the exchanged BDDs can confirm the possibility of future interaction, which is consistent with the C-ITS nature of data sharing.
- Ways of data insertion and database operations for vehicle properties in the linked-list-based BDD running on the PostgreSQL database-based LDM.
2. Literature Review
3. Materials and Methods
3.1. Geohash
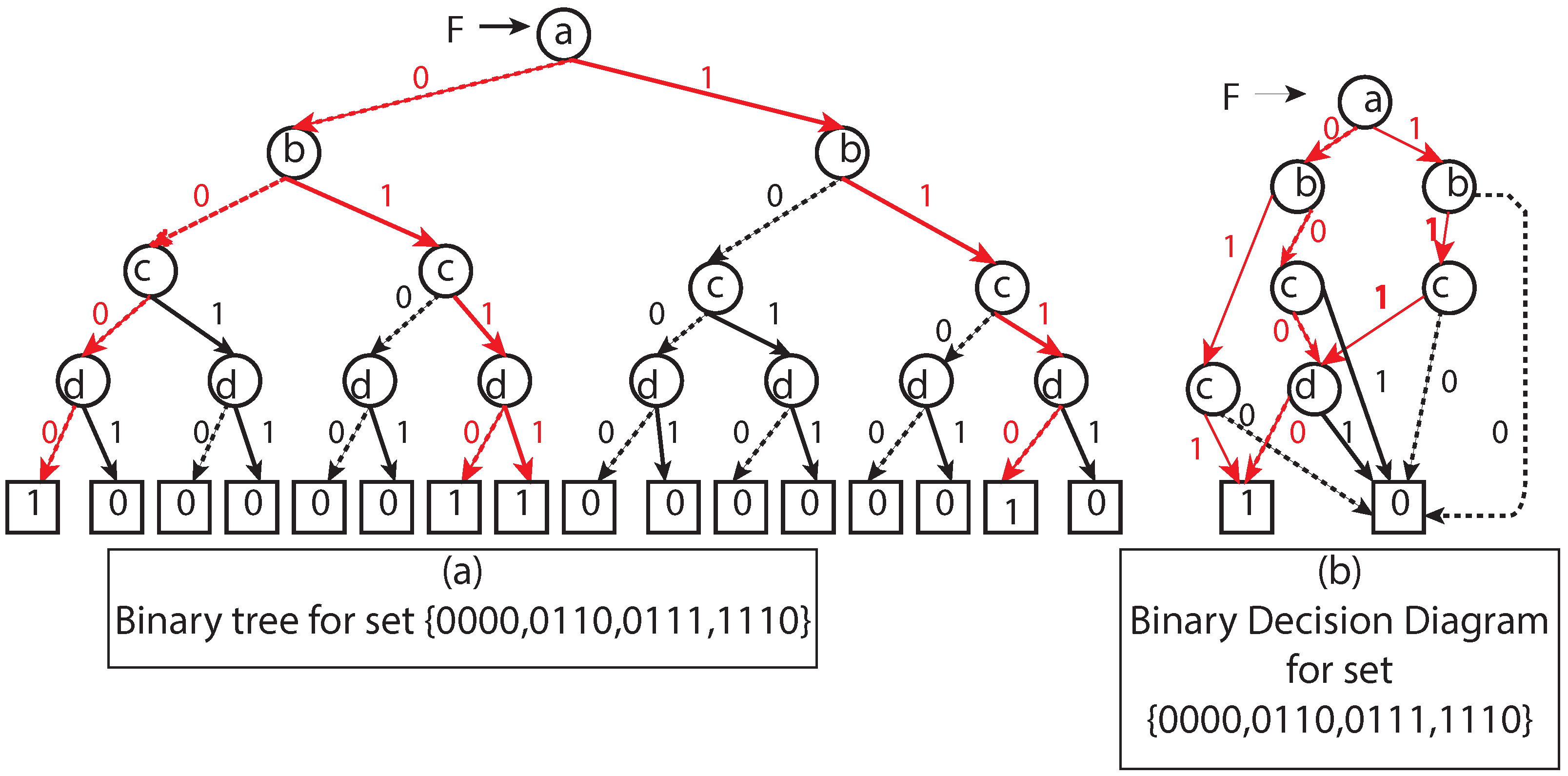
3.2. Boolean Function and Reduced Ordered Binary Decision Diagrams (ROBDD)
3.2.1. Boolean Function
3.2.2. Reduced Ordered Binary Decision Diagrams (ROBDD)
- is a rooted directed acyclic graph. Q is a finite set of nodes. is the root node and . Each non-leaf node has its successors, namely low and high.
- V is a finite set of Boolean variables.
- < is a total order on .
- L is a mapping satisfying the following conditions:
- –
- Leafs are mapped to 0 and 1 and non-leaf nodes are mapped to V.
- –
- If (v,v’) then L(v) < L(v’).
- Merge all zero and one nodes to a single unit of zero and one node.
- Merge any isomorphic nodes, i.e., if and then merge these nodes into one and point all incoming nodes to any one of them. Here l and h represent the low and high child of any given node of a graph.
- Eliminate any node that has two children nodes as isomorphic.
3.3. Geohash Set as a BDD
- BDD representation of a unit Geohash: A Geohash is a unique symbolic representation of all the points available within the given area on the earth. For each character in Geohash, 32 values (English letters except “a”, “i”, “l”, “o”, and decimal system digits 0–9) are possible to use, and, therefore, in our model, five Boolean variables () were applied correspondingly (Figure 1). Consequently, five nodes in a BDD were used to represent the corresponding Boolean variables for a binary representation of a given character in a Geohash. For a given Geohash, each character had five corresponding nodes in the BDD. For a Geohash of 10 characters/levels, 50 nodes were needed for corresponding bits, plus two extra nodes representing zero (false) and one (true) leaf node in a BDD. (for experiments, the vehicle was assumed to be within a Geohash, having a distance of 4872 m (north to south) and 3955 m (east to west); hence, a five-level BDD with 25 nodes served the purpose), i.e., the first five levels of Geohash did not change in our setting. Every corresponding node, low or high, has its values depending on the Boolean function represented. Therefore, to represent a single Geohash using BDD corresponding binary string ends at one (1) node of a BDD, and all other binary strings end in zero (0) (Figure 3).
- BDD representation of a set of Geohash: A synthesis of BDD was applied (we borrowed the term “synthesis" from [28]) to represent a set of Geohashes in a single BDD. In the BDD synthesis, BDDs were built for complex sets/functions representing Geohash locations (e.g., BDD for function f can combine with function g to represent BDD for , , , ). Corresponding set interpretations were necessary for a given BDD representing f and g sets (here Geohash sets) of the above synthesis operations. The method in [23] was introduced to achieve the following operations:
- (a)
- is the set union operation.
- (b)
- is the set intersection operation.
- (c)
- is the set symmetric difference operation.
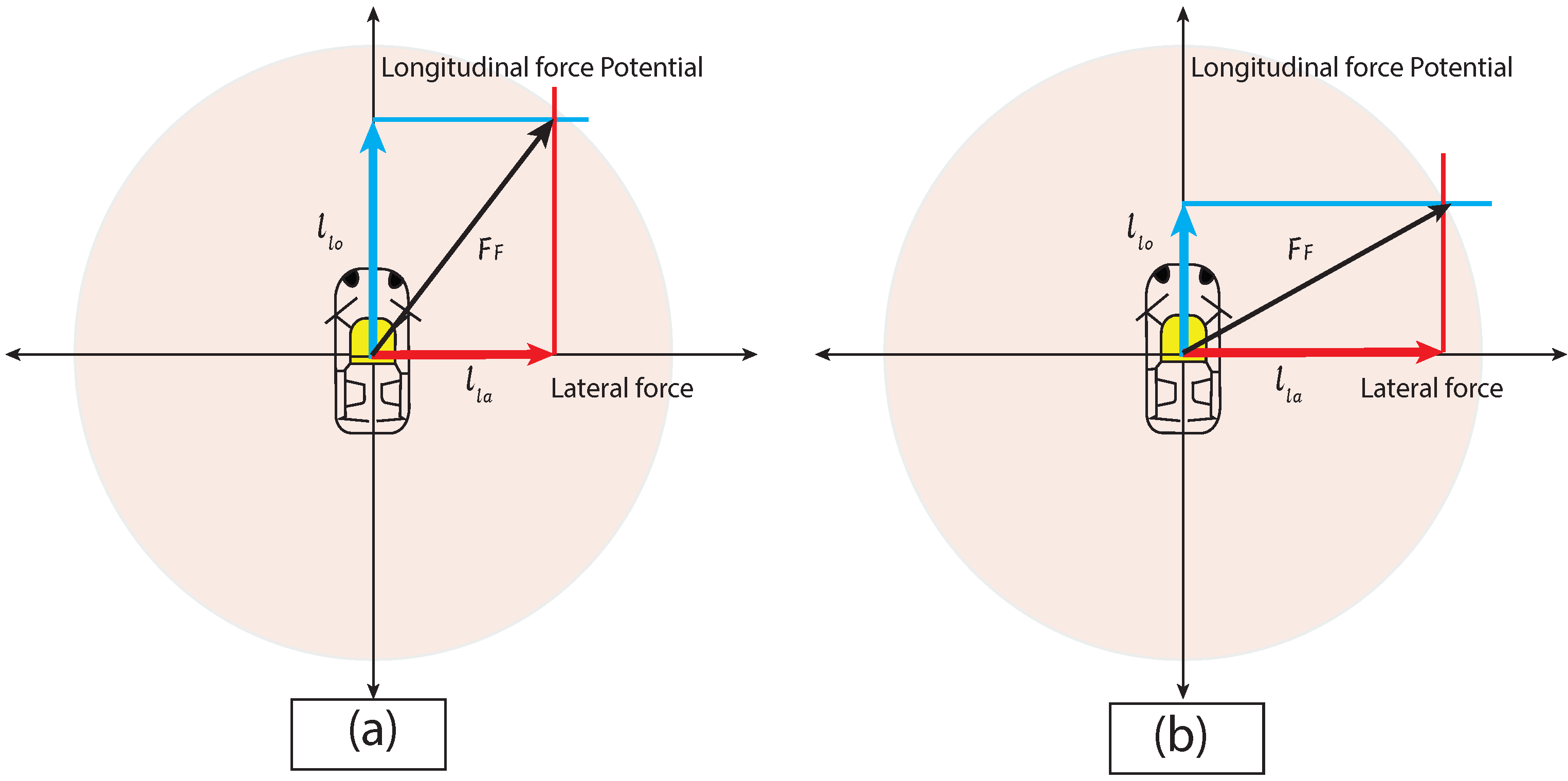
3.4. Reachable Positions by a Vehicle over Time t
Reach/Reachable Sets and Abstraction
- Reach Set—The set of states x at time t for which sequence of control inputs exists from the initial states are known as reach set [31].
- Reachable Set—Reachable set at time t is the union of all the reach sets
- Abstraction—For a model (refer to definition in [29]) M of a given vehicle, abstraction was defined as the model if the reachable set of the abstraction contains the reachable set of the model M (Figure 6).Figure 6. Abstraction of a model contains all reachable states which are reachable by the original model. Here states reachable by all abstraction models contain reachable states by a vehicle model M.Figure 6. Abstraction of a model contains all reachable states which are reachable by the original model. Here states reachable by all abstraction models contain reachable states by a vehicle model M.
- is a position of a vehicle at time t.
- is the position of the vehicle at time t = 0.
- is the velocities in the x and y directions of the vehicle at time t = 0.
- is the radius of a Kamm’s/traction circle at time t.
- is the maximum acceleration possible of a given vehicle.
3.5. BDD for Geohash Set Enclosing Kamm’s Circle
- Reduce: Give reduced BDD in its canonical form.
- Apply: Perform synthesis operation between two BDDs. .
- Satisfy-One: Returns any one element in , where is the set of all Geohash represented by a given BDD.
- Satisfy-All: Output . All Geohashes, a given BDD, satisfy.
| Algorithm 1: Algorithm to find neighboring Geohash BDD. |
1 Input: inpGeo -Geohash BDD. h in {west, east, null}, v in {south, north, null}. 2 Output: Neighbour in east, west, north, south, north-west, north-east, south-east, south-west Geohash BDD. 3 S = Satisfy-One(inpGeo) 4 T = [1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1,1] 5 for i = 0 to T.: 6 for j = 0 to i: 7 If then: 8 If then: 9 T[j] = T[j] (S[j]) 10 elif then: 11 T[j] = T[j] and S[j] 12 else: 13 If then: 14 T[j] = T[j] (S[j]) 15 elif then: 16 T[j] = T[j] and S[j] 17 if : 18 T[T.-1] = 1 19 if : 20 T[T.-2] = 1 21 for i = 0 to T.: 22 S[i] = S[i] T[i] 23 return createStringtoBDD(S) |
- If then:= and new is calculated as
- else:= and new is calculated as
- if :
- Generate east BDD and union it with circle_BDD. Additionally, update the value , and record the north limit of this BDD from the center. Finally, update the value of the decision parameter as .
- else:
- Generate southeast BDD and union it with circle_BDD. Additionally, update the value and record the north and east limit of this BDD from the center. Finally, update the value of the decision parameter as .
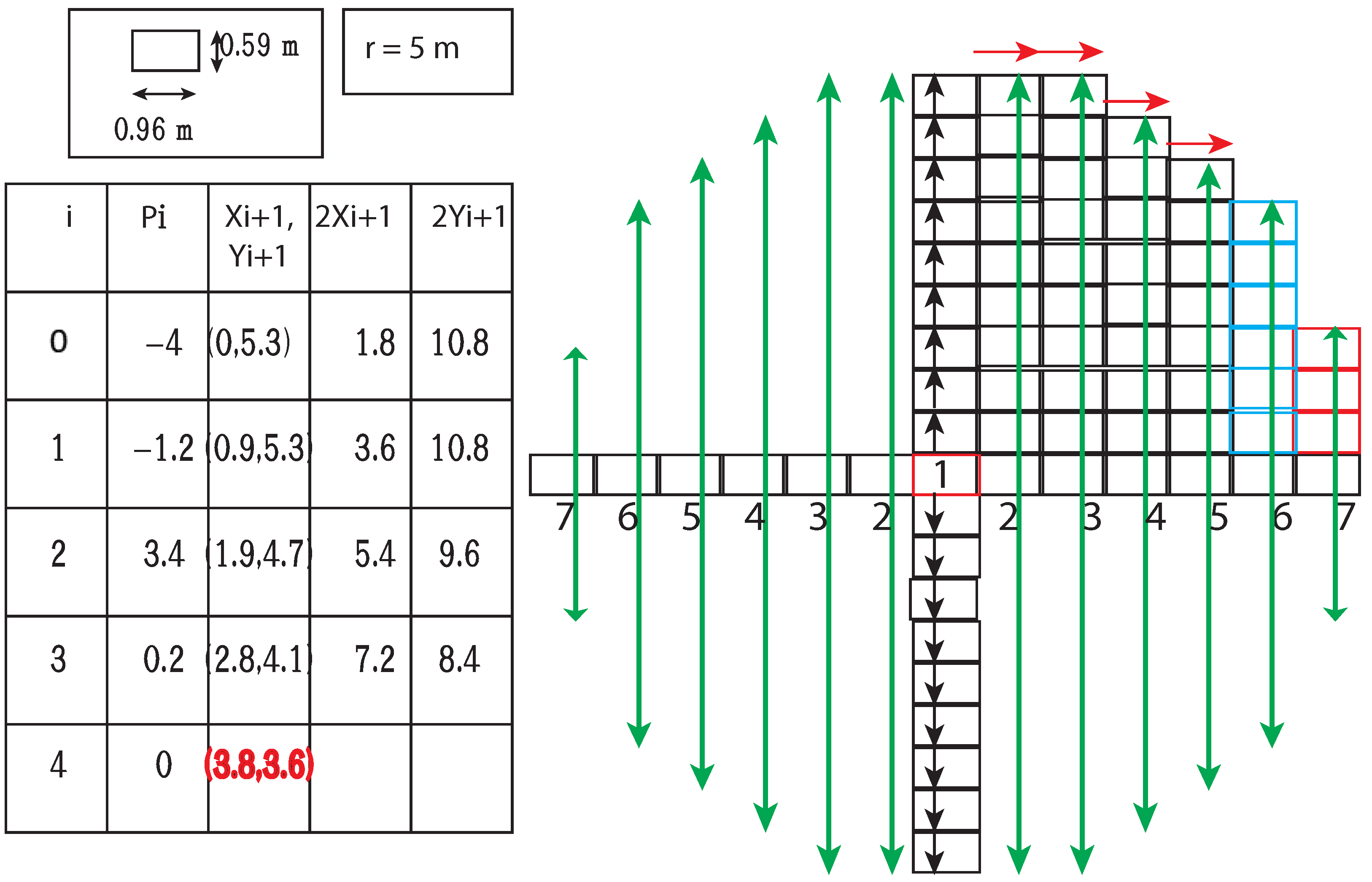
| Algorithm 2: Modified midpoint circle generation algorithm. |
1 Input: inpGeo—Center Geohash BDD, r—radius in meters unit. 2 Output: BDD for a set of Geohashes enclosing Kamm’s circle. 3 /*Step I.*/ 4 up_count = 5 quad1_north_limit = quad1_east_limit = [] 6 circle_BDD = inpGeo 7 BDD1 = BDD2 = BDD3 = BDD4 = inpGeo 8 x_k = y_k = 0 9 n_count = e_count = 0 10 /*Step II.*/ 11 for k = 0 to up_count: 12 BDD1 = Generate north BDD of BDDs. 13 BDD2 = Generate south BDD of BDDs. 14 y_k = y_k + 0.59 15 n_count = n_count + 1 16 /*Apply union with circle_BDD*/ 17 /*Step III.*/ 18 p = INT(ROUND(5/4) - r) 19 /*Step IV.*/ 20 while : 21 if : 22 BDD1 = Generate east BDD of BDD1. 23 x_k = x_k + 0.96 24 e_count = e_count + 1 25 quad1_north_limit.append(n_count) 26 27 p = p + 2 * x_k + 1 28 else: 29 BDD1 = Generate south east BDD of BDD1. 30 31 x_k = x_k + 0.96 32 y_k = y_k - 0.59 33 quad1_east_limit.append(e_count) 34 e_count = e_count + 1 35 n_count = n_count - 1 36 quad1_north_limit.append(n_count) 37 p = p + 2 * x_k + 1 - 2 * y_k 38 quad1_east_limit.append(x_count) 39 /*Step V.*/ 40 for w = 0 to quad1_east_limit.-1: 41 Generate BDD3 and BDD4 east and west of BDD3 respectively. 42 43 for k = 0 to quad1_north_limit[w]: 44 Generate BDD5 and BDD6 north and south of BDD3 respectively. 45 Generate BDD7 and BDD8 north and south of BDD4 respectively. 46 47 /*Step VI.*/ 48 for w = quad1_east_limit.-1 to 0: 49 Generate BDD3 and BDD4 east and west of BDD3 respectively. 50 51 a = /*1.6, Geohash (10 level) breadth to height ratio*/ 52 if then: 53 a = quad1_north_limit[w] 54 for k = 0 to a: 55 Generate BDD5 and BDD6 north and south of BDD3 respectively. 56 Generate BDD7 and BDD8 north and south of BDD4 respectively. 57 58 return circle_BDD |
| Algorithm 3: Midpoint circle generation algorithm. |
1 Input: r—radius of a circle, (,) center of the circle. 2 Output: Squares to include on a square grid to form a circle of radius r. 3 I. First square to include () 4 II. Calculate the initial value for the decision parameter. III. For successive values of k, is determined as follows. If then: = and new is calculated as else: = and new is calculated as IV. Determine the symmetry points in the other seven octants. V. Repeat Steps III to IV until . |
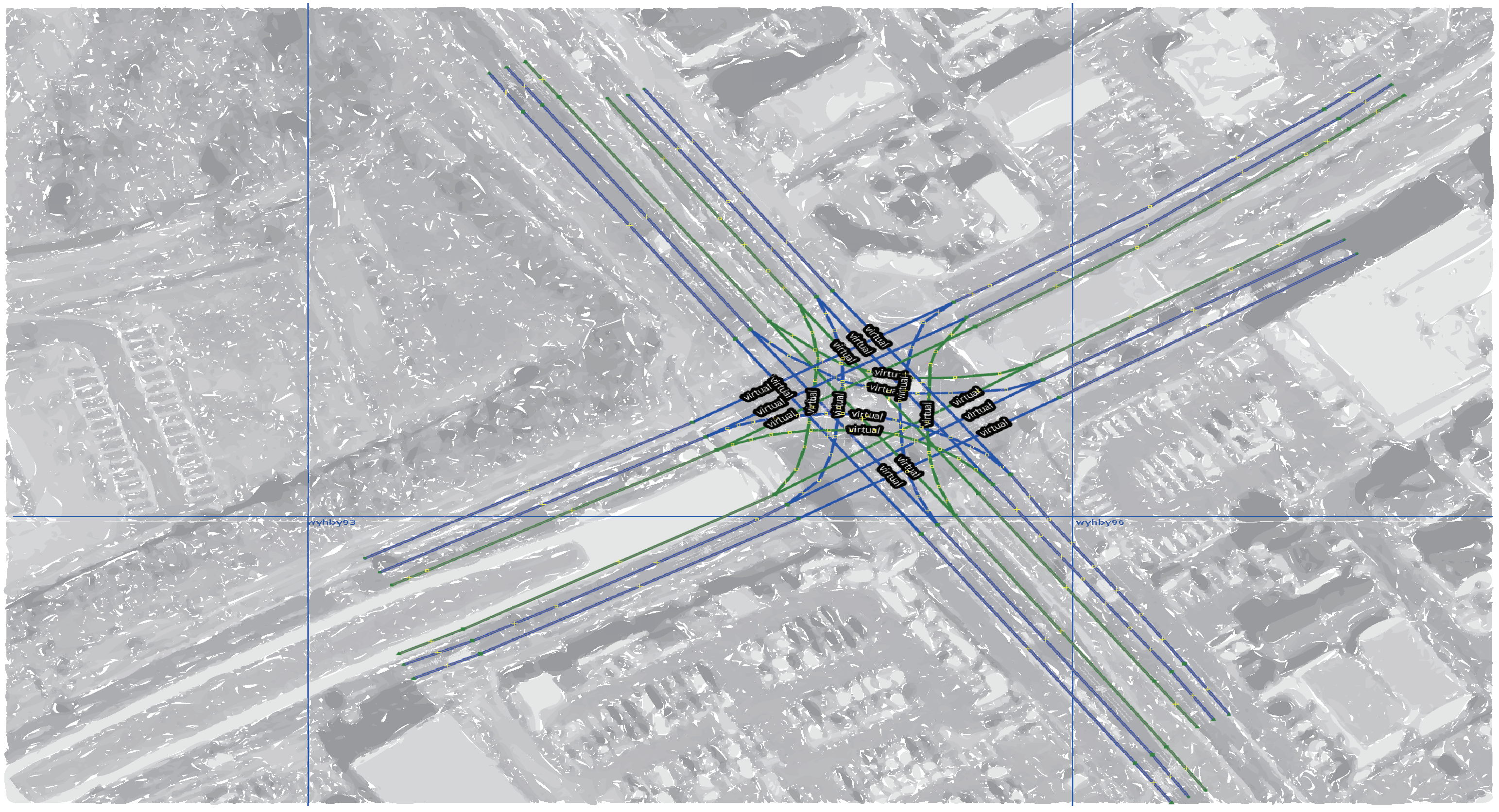
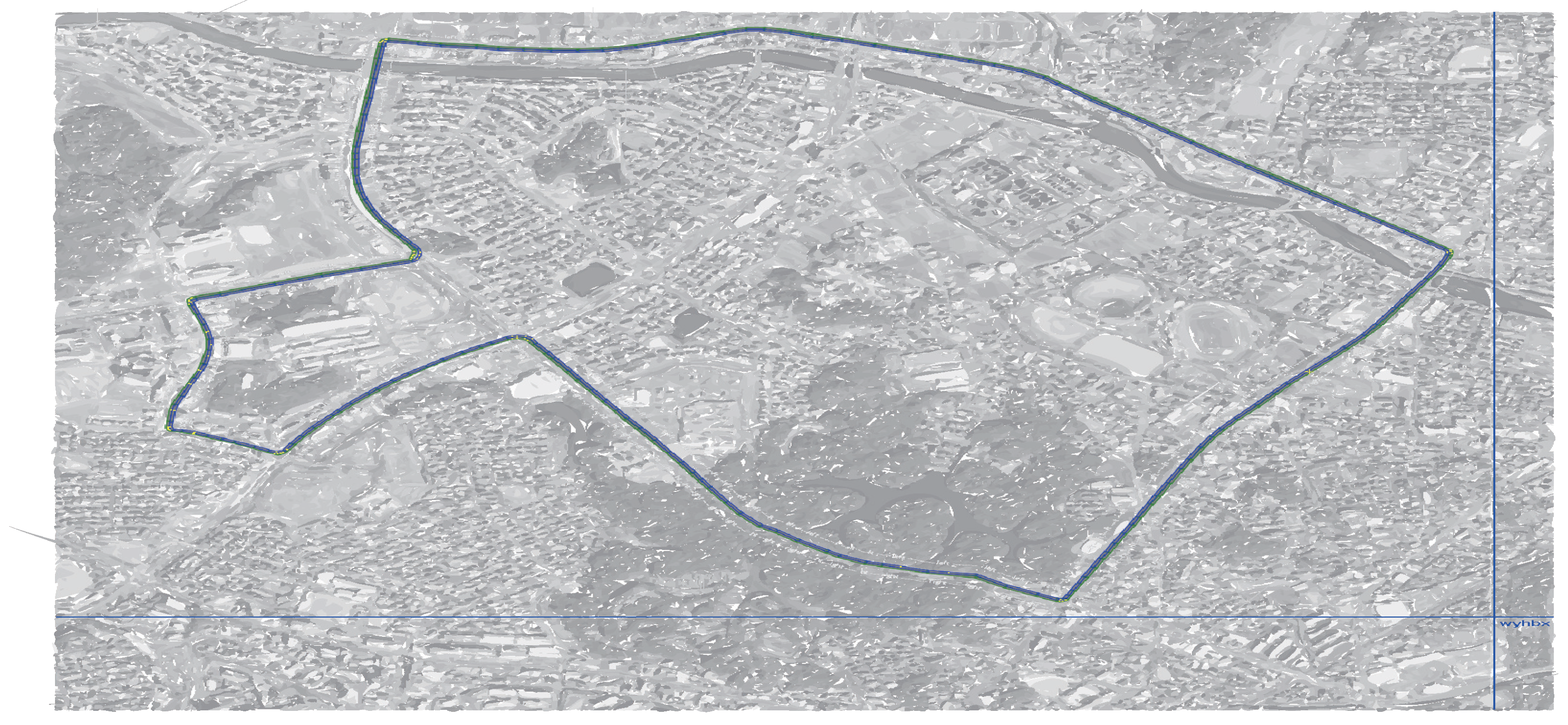
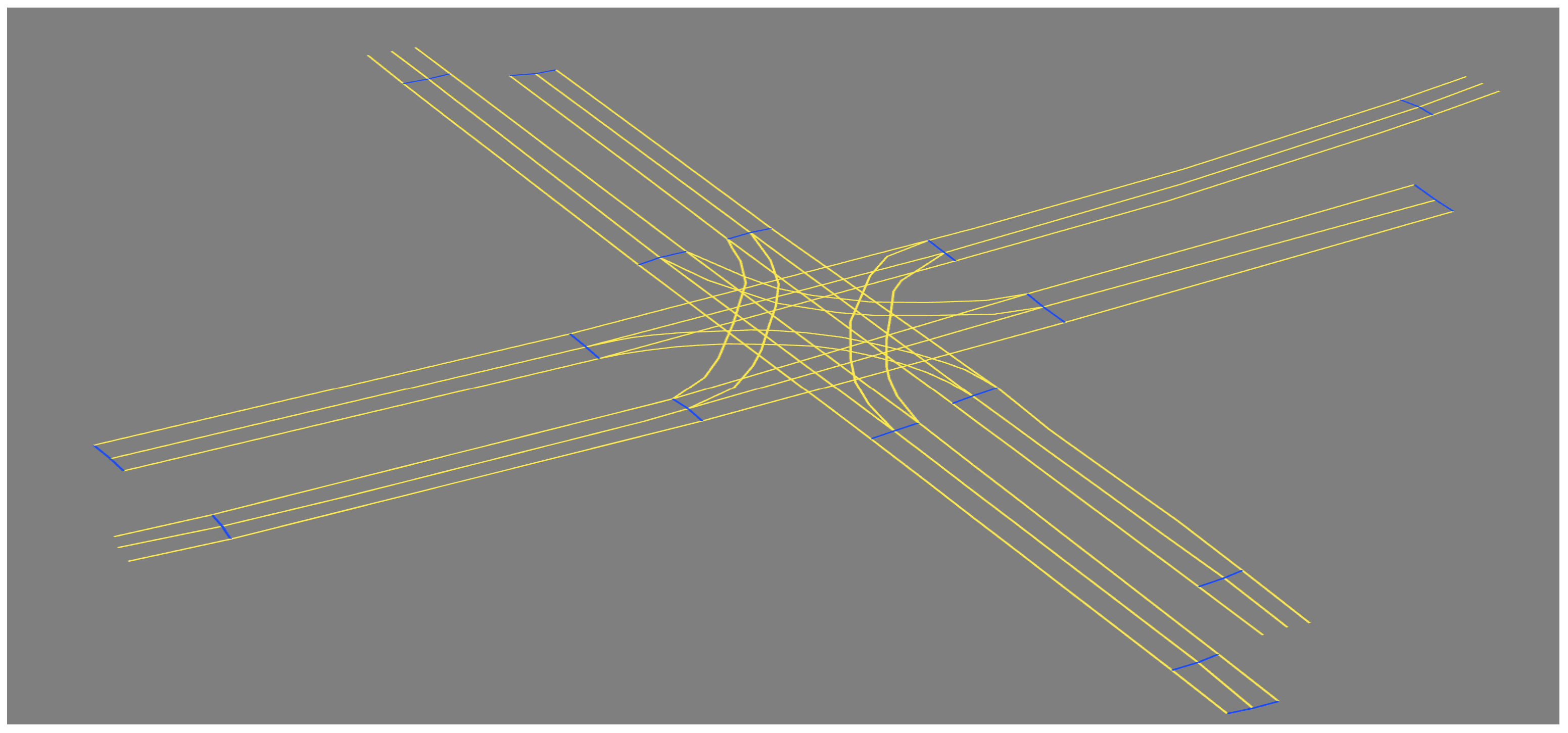
4. Experiment
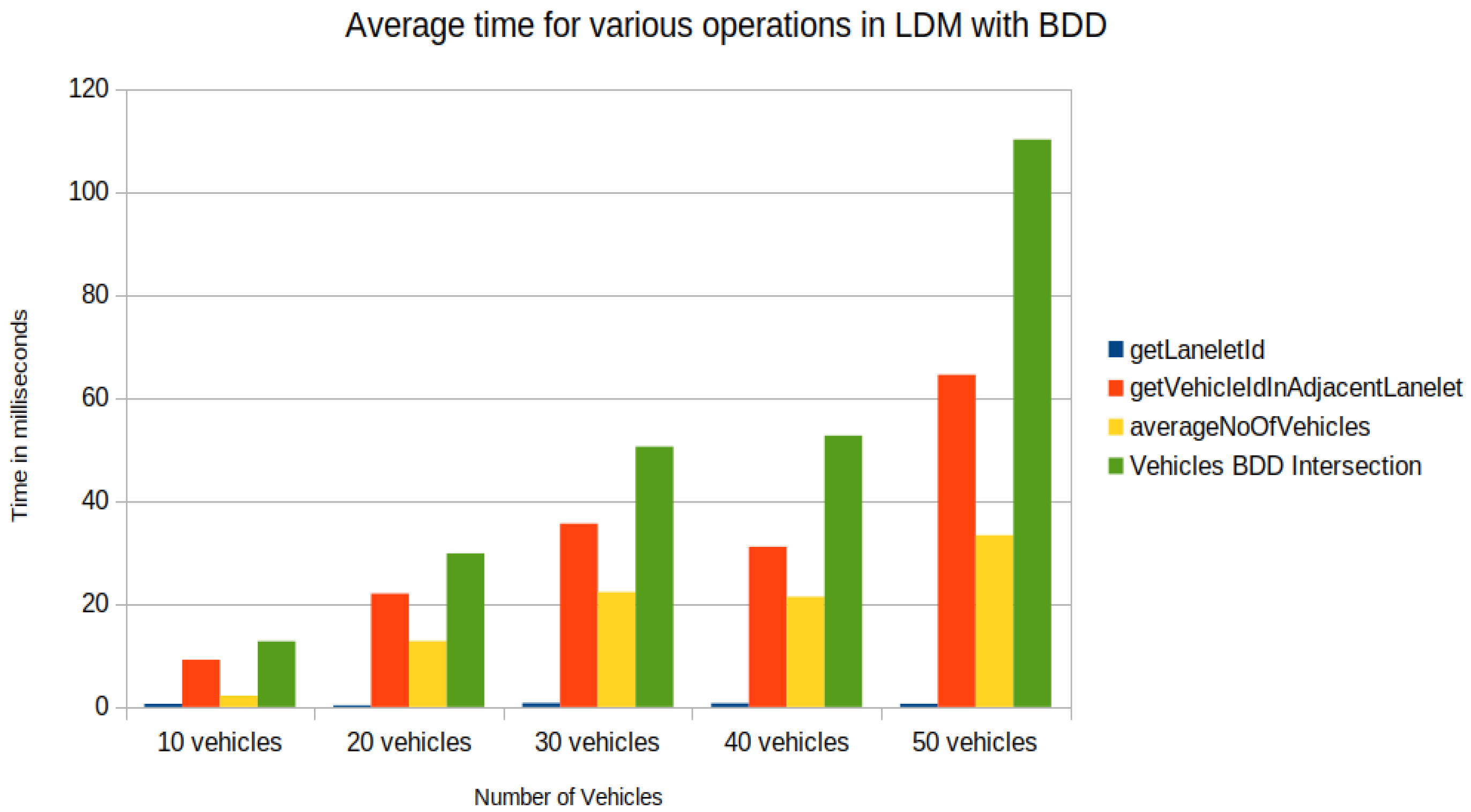
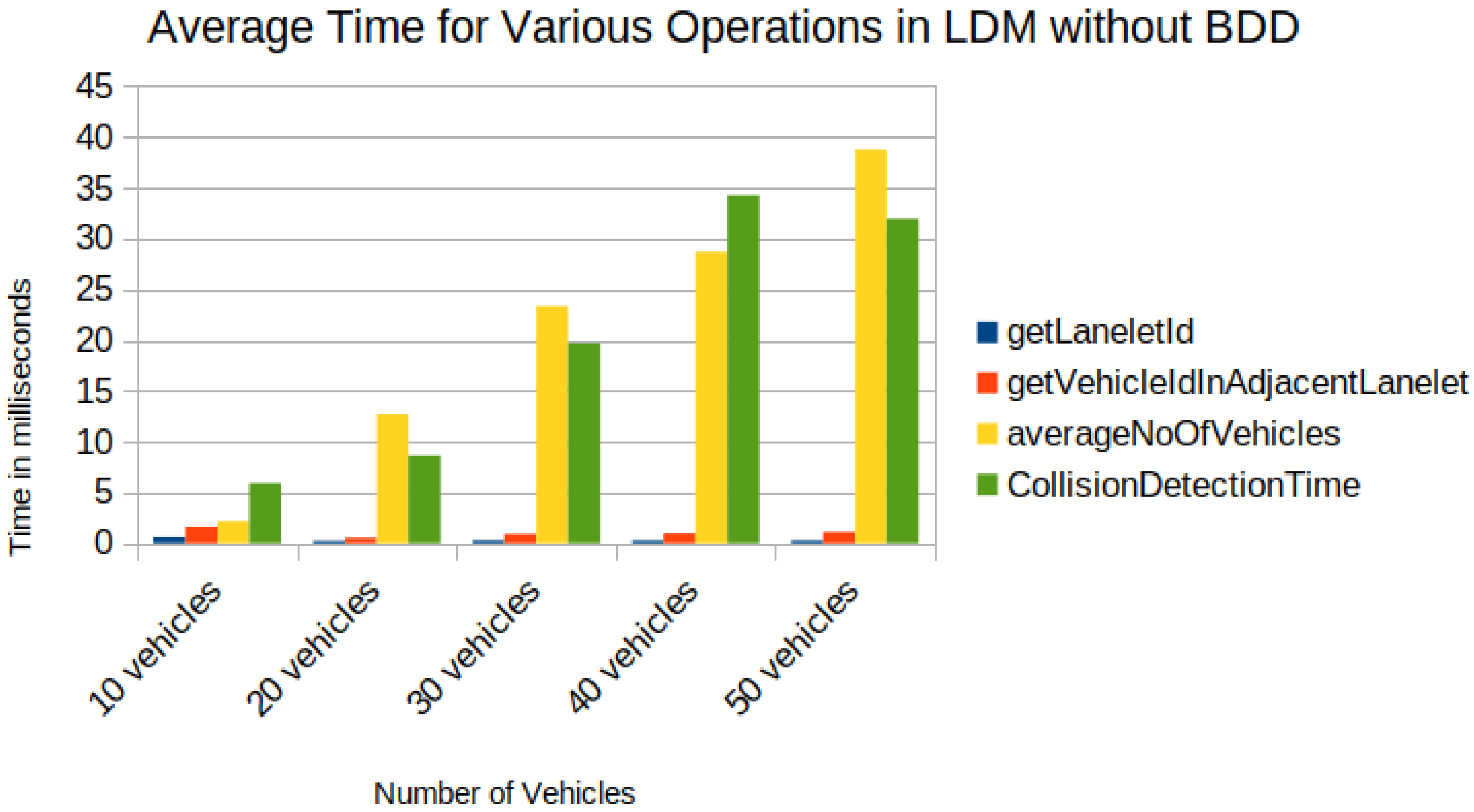
5. Results
- Task1—getLaneletId (to get the lanelet id and data corresponding to an ego vehicle).
- Task2—getVehicleInAdjacentLanelet (to retrieve data of all vehicles (other than ego) present in the ego vehicle’s current lanelet or its adjacent lanelets).
- Task3—averageNoOfVehicles (to retrieve the number of vehicles present around an ego vehicle for a given scenario).
6. Discussions
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Safe Driving Protecting Yourself Behind the Wheel. Available online: https://newsinhealth.nih.gov/2020/06/safe-driving (accessed on 9 January 2022).
- Taxonomy and Definitions for Terms Related to Driving Automation Systems for On-Road Motor Vehicles J3016_202104. Available online: https://www.sae.org/standards/content/j3016_202104/ (accessed on 9 January 2022).
- Vargas, J.; Alsweiss, S.; Toker, O.; Razdan, R.; Santos, J. An overview of autonomous vehicles sensors and their vulnerability to weather conditions. Sensors 2021, 21, 5397. [Google Scholar] [CrossRef]
- SAFESPOT SP 7 SCORE—SAFESPOT Core Architecture, D7.3.1 Annex2—LDM API and Usage Reference (2010). Available online: http://www.safespot-eu.org/documents/SF_D7.3.1_Annex2_LDM_API_and_Usage_Reference_v0.7.pdf (accessed on 9 January 2022).
- Eggert, J.; Salazar, D.A.; Puphal, T.; Flade, B. Relational Local Dynamic Maps for Driving Situation Analysis. In Proceedings of the Conference: International Symposium on Future Active Safety Technology towards Zero-Traffic-Accidents (FAST-Zero), Nara, Japan, 13–15 September 2017. [Google Scholar]
- Shimada, H.; Yamaguchi, A.; Takada, H.; Sato, K. Implementation and Evaluation of Local Dynamic Map in Safety Driving Systems. J. Transp. Technol. 2015, 5, 102–112. [Google Scholar] [CrossRef]
- Eiter, T.; Füreder, H.; Kasslatter, F.; Parreira, J.X.; Schneider, P. Towards a Semantically Enriched Local Dynamic Map. Int. J. Intell. Transp. Syst. Res. 2019, 17, 32–48. [Google Scholar] [CrossRef]
- Kumar, A.; Kawano, K.; Trung, H.L.P.; Wagatsuma, H. A Binary Decision Diagram Based Approach for Refining Road Safety Scenarios in the Local Dynamic Map. ICIC Express Lett. Part B Appl. (ICIC-ELB) 2022, 13, 597–605. [Google Scholar]
- ETSI TR 102 863 (V1.1.1); Intelligent Transport Systems (ITS); Vehicular Communications; Basic Set of Applications; Local Dynamic Map (LDM); Rationale for and Guidance on Standardization. ETSI: Sophia Antipolis, France, 2011.
- ETSI EN 302 895 (V1.1.0); Intelligent Transport Systems (ITS); Vehicular Communications; Basic Set of Applications; Local Dynamic Map (LDM). ETSI: Sophia Antipolis, France, 2014.
- ISO/TS 17931:2013; Intelligent Transport Systems—Extension of Map Database Specifications for Local Dynamic Map for applications of Cooperative ITS. ISO: Geneva, Switzerland, 2013.
- ISO/TS 18750:2015; Intelligent Transport Systems—Cooperative Systems—Definition of a Global Concept for Local Dynamic Maps. ISO: Geneva, Switzerland, 2015.
- Netten, B.; Kester, L.J.H.M.; Wedemeijer, H.; Passchier, I.; Driessen, B. DynaMap: A Dynamic Map for road side ITS stations. In Proceedings of the 20th ITS World Congress Tokyo 2013, Tokyo Japan, 14–18 October 2013. [Google Scholar]
- Koenders, E.; Oort, D.; Rozema, K. An open local dynamic map. In Proceedings of the 10th ITS European Congress 2014, Helsinki, Finland, 16–19 June 2014. [Google Scholar]
- Zoghby, N.E.; Cherfaoui, V.; Denoeux, T. Evidential distributed dynamic map for cooperative perception in vanets. In Proceedings of the 2014 IEEE Intelligent Vehicles Symposium, Dearborn, MI, USA, 8–11 June 2014; pp. 1421–1426. [Google Scholar]
- Nieto, M.; Garcia, M.; Urbieta, I.; Otaegui, O. RTMaps-based Local Dynamic Map for multi-ADAS data fusion. arXiv 2022, arXiv:2205.06497. [Google Scholar]
- Biral, F.; Valenti, G.; Bertolazzi, E.; Steccanella, A. Cooperative safety applications for c-its equipped and non-equipped vehicles supported by an extended local dynamic map built on safe strip technology. In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini Island, Greece, 29–31 May 2019; pp. 733–740. [Google Scholar]
- Lee, J.; Lee, W.; Kim, K. An algorithm for local dynamic map generation for safe UAV navigation. Drones 2021, 5, 88. [Google Scholar] [CrossRef]
- García, M.; Urbieta, I.; Nieto, M.; González de Mendibil, J.; Otaegui, O. iLDM: An Interoperable Graph-Based Local Dynamic Map. Vehicles 2022, 4, 42–59. [Google Scholar] [CrossRef]
- Morton, G.M. A computer Oriented Geodetic Data Base and a New Technique in File Sequencing; International Business Machines Company: New York, NY, USA, 1966. [Google Scholar]
- Geohash. Available online: https://en.wikipedia.org/wiki/Geohash (accessed on 8 July 2022).
- Akers, S.B. Binary decision diagrams. IEEE Trans. Comput. 1978, 27, 509–516. [Google Scholar] [CrossRef]
- Bryant, R.E. Graph-Based Algorithms for Boolean Function Manipulation. IEEE Trans. Comput. 1986, 8, 677–691. [Google Scholar] [CrossRef]
- Havelund, K.; Peled, D. BDDs for Representing Data in Runtime Verification. In RV 2020. Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2020; pp. 107–128. [Google Scholar]
- Minato, S. Zero-Suppressed BDDs for Set Manipulation in Combinatorial Problems. In Proceedings of the 30th international Design Automation Conference DAC ’93, Dallas, TX, USA, 14–18 June 1993; pp. 272–277. [Google Scholar]
- Minato, S.; Ishiura, N.; Yajima, S. Shared binary decision diagram with attributed edges for efficient Boolean function manipulation. In Proceedings of the 27th ACM/IEEE Design Automation Conference, Orlando, FL, USA, 24–27 June 1990; pp. 52–57. [Google Scholar]
- Fujita, M.; McGeer, P.C.; Yang, J.C. Multi-Terminal Binary Decision Diagrams: An Efficient Data Structure for Matrix Representation. Form. Methods Syst. Des. 1997, 10, 149–169. [Google Scholar] [CrossRef]
- Knuth, D.E. A draft of section 7.1.4. Binary Decision Diagrams In The Art of Computer Programming; Addison-Wesley: New York, NY, USA, 2008; Volume 4, p. 3. [Google Scholar]
- Matthias, A.; Silvia, M. Set-Based Prediction of Traffic Participants on Arbitrary Road Networks. IEEE Trans. Intell. Veh. 2016, 1, 187–202. [Google Scholar]
- Althoff, M. Reachability Analysis and Its Application to the Safety Assessment of Autonomous Cars. Doctoral Dissertation, Technische Universität München, München, Germany, 2010. [Google Scholar]
- Cognitive Robotics. Available online: https://ocw.mit.edu/courses/16-412j-cognitive-robotics-spring-2016/c71b2cf371b216faa50aca186b305a9f_MIT16_412JS16_L18.pdf (accessed on 21 June 2022).
- Orzechowski, P.F.; Meyer, A.; Lauer, M. Tackling Occlusions & Limited Sensor Range with Set-based Safety Verification. In Proceedings of the 21st International Conference on Intelligent Transportation Systems (ITSC), Maui, HI, USA, 4–7 November 2018; pp. 1729–1736. [Google Scholar]
- Leelapatra, W.; Kanchanasut, K.; Lursinsap, C. Geometric Transformations of BDD Encoded Image. IAENG Int. J. Appl. Math. 2007, 36. Available online: http://www.iaeng.org/IJAM/issues_v36/issue_1/IJAM_36_1_10.pdf (accessed on 21 March 2022).
- Poggenhans, F.; Jan-Hendrik, P.; Johannes, J.; Stefan, O.; Maximilian, N.; Florian, K.; Matthias, M. Lanelet2: A high-definition map framework for the future of automated driving. In Proceedings of the 2018 21st International Conference on Intelligent Transportation Systems (ITSC), Maui, HI, USA, 4–7 November 2018; pp. 1672–1679. [Google Scholar]
- Naumann, M.; Poggenhans, F.; Lauer, M.; Stiller, C. CoInCar-Sim: An Open-Source Simulation Framework for Cooperatively Interacting Automobiles. In Proceedings of the 2018 IEEE Intelligent Vehicles Symposium (IV), Suzhou, China, 26–30 June 2018; pp. 1–6. [Google Scholar]
- Java OpenStreetMap Editor. Available online: https://josm.openstreetmap.de/ (accessed on 30 June 2022).
- EN 302 637-2-V1.3.1; Intelligent Transport Systems (ITS); Vehicular Communications; Basic Set of Applications; Part 2: Specification of Cooperative Awareness Basic Service. ETSI: Sophia Antipolis, France, 2014.
- Jo, K.; Kim, C.; Sunwoo, M. Simultaneous Localization and Map Change Update for the High Definition Map-Based Autonomous Driving Car. Sensors 2018, 18, 3145. [Google Scholar] [CrossRef] [PubMed] [Green Version]
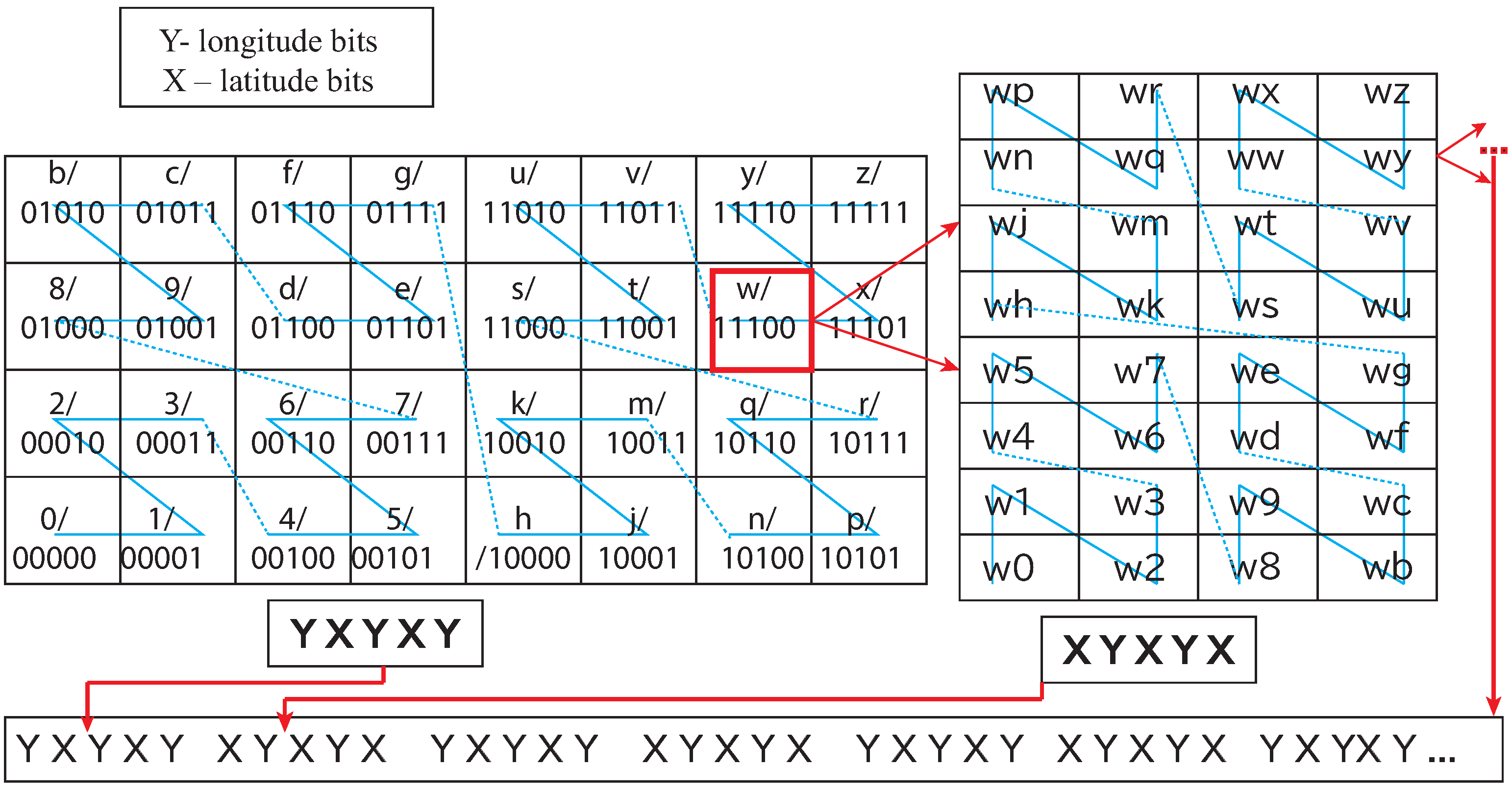






| #Label in Geohash | Distance in North and South (m) | Distance in East and West (m) | A Geohash Example |
|---|---|---|---|
| 1 | 4,989,600 | 4,050,000 | w |
| 2 | 623,700 | 1,012,500 | wy |
| 3 | 155,925 | 126,562.5 | wyh |
| 4 | 19,490.625 | 31,640.625 | wyhb |
| 5 | 4872.65625 | 3955.07813 | wyhby |
| 6 | 609.082031 | 988.769531 | wyhby3 |
| 7 | 152.270508 | 123.596191 | wyhby3k |
| 8 | 19.0338135 | 30.8990479 | wyhby3kf |
| 9 | 4.75845337 | 3.86238098 | wyhby3kf5 |
| 10 | 0.59480667 | 0.96559525 | wyhby3kf5f |
| 11 | 0.14870167 | 0.12069941 | wyhby3kf5fs |
| 12 | 0.01858771 (≈ 1.86 (cm)) | 0.03017485 (≈ 3.02 [cm]) | wyhby3kf5fst |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kumar, A.; Wagatsuma, H. A Kamm’s Circle-Based Potential Risk Estimation Scheme in the Local Dynamic Map Computation Enhanced by Binary Decision Diagrams. Sensors 2022, 22, 7253. https://doi.org/10.3390/s22197253
Kumar A, Wagatsuma H. A Kamm’s Circle-Based Potential Risk Estimation Scheme in the Local Dynamic Map Computation Enhanced by Binary Decision Diagrams. Sensors. 2022; 22(19):7253. https://doi.org/10.3390/s22197253
Chicago/Turabian StyleKumar, Arvind, and Hiroaki Wagatsuma. 2022. "A Kamm’s Circle-Based Potential Risk Estimation Scheme in the Local Dynamic Map Computation Enhanced by Binary Decision Diagrams" Sensors 22, no. 19: 7253. https://doi.org/10.3390/s22197253
APA StyleKumar, A., & Wagatsuma, H. (2022). A Kamm’s Circle-Based Potential Risk Estimation Scheme in the Local Dynamic Map Computation Enhanced by Binary Decision Diagrams. Sensors, 22(19), 7253. https://doi.org/10.3390/s22197253







