Survey of Collision Avoidance Systems for Underground Mines: Sensing Protocols
Abstract
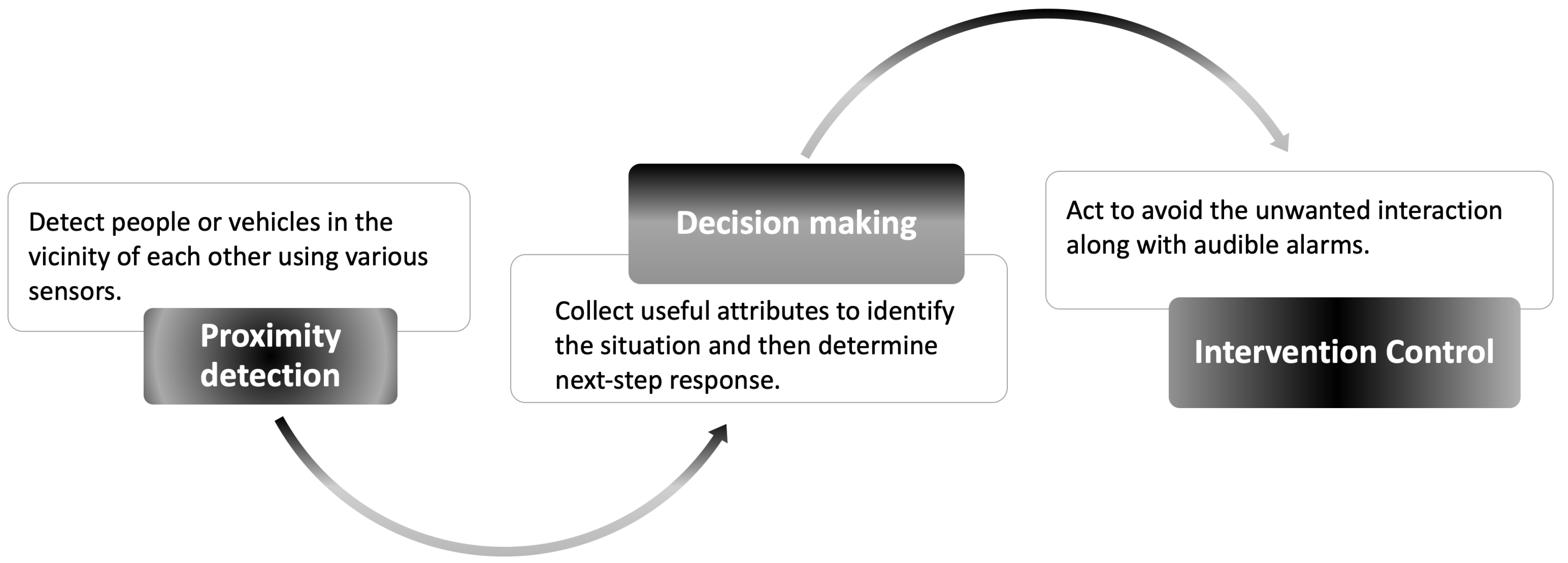
:1. Introduction
2. Ranging Algorithms and Positioning Techniques
2.1. Time-Of-Flight (TOF)
2.2. TOA
2.3. TDOA
2.4. AOA
3. Communication Requirements
3.1. Narrowband
3.1.1. Sigfox
3.1.2. Telensa
3.1.3. Weightless
3.1.4. Narrowband Internet of Things (NB-IoT)
3.2. Spread Spectrum
3.2.1. Long Range—LoRa
3.2.2. RPMA
4. Medium Access Control Methods and Communication Protocols
4.1. Desired MAC Protocol Design for CAS
4.1.1. Distributed Networks
4.1.2. Contention-Free Communication
4.1.3. Scheduling Protocols
4.1.4. Latency
4.1.5. Energy Consumption
Overhearing
Overhead
Duty-Cycling
4.1.6. Scalability
4.1.7. Traffic Adaptability and Throughput
4.1.8. Handling Mobility
4.1.9. Wake-Up Radio Enabled
4.2. Review of Existing Wireless Standards and MAC Protocols
4.2.1. Related Wireless Standards
IEEE 802.11ah
IEEE 802.15.4
4.2.2. Typical MAC Protocols
Latency
- SR-MAC
- SW-MAC
- DW-MAC
- LDC-MAC
Energy Consumption Due to Overhearing
- BBAD Mechanism
- RANO Mechanism
Energy Consumption Due to Overhead
- LO-MAC
- LoBigMAC
- LCO-MAC
Energy Consumption Due to Duty-Cycling
- BN-MAC
- AP-MAC
- SLACK-MAC
Scalability
- SE-MAC
- A Hybrid Protocol
- SQ-MAC
Handling Mobility
Wake-Up Radio Enabled
5. Summarised Features and Properties
- Summary of Commercially Available CAS Products
- Summary of Proximity Detection Technologies
- Summary of Positioning Techniques
- Summary of LPWA Communication Technologies
- Summarised Useful Information Obtained From Existing MAC Protocols
6. Discussion
6.1. Ranging Process
6.2. Communication System
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
Nomenclature
| Two-dimensional | |
| Three-dimensional | |
| Third-Generation Partnership Project | |
| Adaptable Application Independent Aggregation | |
| Increase/Multiplicative Decrease | |
| Angle of Arrival | |
| Access Point | |
| Bit-by-bit Address Decoding | |
| Bluetooth Low Energy | |
| Binary phase shift keying | |
| Collision avoidance system | |
| Code-division Multiple Access | |
| Carrier-sense multiple access with collision avoidance | |
| Carrier Sense Multiple Access | |
| Chirp spread spectrum | |
| Clear to Send | |
| Differential binary phase-shift keying | |
| Depth First Search | |
| Differential phase shift keying | |
| Direct-Sequence Spread Spectrum | |
| Electromagnetic | |
| Frequency-division Multiple Access | |
| Frequency shift keying | |
| Fault Tolerant Slot | |
| Gaussian frequency shift keying | |
| Global navigation satellite system | |
| Global Positioning System | |
| Global System for Mobile Communications | |
| High frequency | |
| Internet of Things | |
| Industrial, Scientific and Medical | |
| Low frequency | |
| Long range | |
| Line of Sight | |
| Low-Power Wide-Area | |
| Low-Power Wide-Area Network | |
| Long-Term Evolution Machine-Type Communication | |
| Long-Term Evolution | |
| Medium access control | |
| Multiple Input Multiple Output | |
| Narrow-band Internet of Things | |
| Narrow Band | |
| Non-Line of Sight | |
| Orthogonal frequency-division multiplexing | |
| Orthogonal frequency division multiple access | |
| Offset quadrature phase shift keying | |
| Pioneer | |
| Quadrature amplitude modulation | |
| Quality of Service | |
| Quadrature phase shift keying | |
| Reservation Aloha for No Overhearing | |
| Radio frequency | |
| Radio-frequency Identification | |
| Random Phase Multiple Access | |
| Request to Send | |
| Scheduling frame | |
| Super-high frequency | |
| Slot-reserved frame | |
| Spread Spectrum | |
| Time-Division Multiple Access | |
| Time Difference of Arrival | |
| Time of Arrival | |
| Time of Flight | |
| Ultra-high frequency | |
| Universal Mobile Telecommunications System | |
| Ultra-wideband | |
| Vehicles and infrastructure | |
| Vehicles and personnel | |
| Vehicles and vehicles | |
| Very low frequency | |
| Wireless Local Area Network | |
| Wireless Personal Area Network | |
| Wireless Wide Area Network |
References
- Rasche, T. Too Close for Comfort’ —The Case for Proximity Detection and Vehicle Collision Avoidance Systems. Technical Report. 2009. Available online: https://www.qmihsconference.org.au/wp-content/uploads/qmihsc-2009-writtenpaper-rasche.pdf (accessed on 25 March 2022).
- Guidance Note QGN 27 Collision Prevention; Technical Report; Mines Inspectorate of the Department of Natural Resources, Mines and Energy: Melbourne, VIC, Australia, 2017.
- Vehicle Collisions in the Western Australian Mining Industry 2015-16; Technical Report; Department of Mines, Industry Regulation and Safety: East Perth, WA, Australia, 2019.
- Guenther, N.; Salow, H. Collision Avoidance and Operator Guidance—Innovating Mine Vehicle Safety; Technical report; SICK: Melbourne, Australia, 2012. [Google Scholar]
- Zhou, Z.; Zhang, J.; Gong, C. Automatic detection method of tunnel lining multi-defects via an enhanced You Only Look Once network. Comput.-Aided Civ. Infrastruct. Eng. 2022, 37, 762–780. [Google Scholar] [CrossRef]
- Kai, H.; Xianmin, M. Research on avoidance obstacle strategy of coal underground inspection robot based on binocular vision. In Proceedings of the 2017 29th Chinese Control And Decision Conference (CCDC), Chongqing, China, 28–30 May 2017; pp. 6732–6737. [Google Scholar] [CrossRef]
- Adam, S.; Coward, B.; DeBerry, G.; Glazier, C.; Magnusson, E.; Boukhechba, M. Investigating Novel Proximity Monitoring Techniques Using Ubiquitous Sensor Technology. In Proceedings of the 2021 Systems and Information Engineering Design Symposium (SIEDS), Charlottesville, VA, USA, 29–30 April 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Wang, Z.; Xu, G.; Zhang, M.; Guo, Y. Collision Avoidance Models and Algorithms in the Era of Internet of Vehicles. In Proceedings of the 2020 IEEE 3rd International Conference of Safe Production and Informatization (IICSPI), Chongqing, China, 28–30 November 2020; pp. 123–126. [Google Scholar] [CrossRef]
- Ali, R.; Liu, R.; He, Y.; Nayyar, A.; Qureshi, B. Systematic Review of Dynamic Multi-Object Identification and Localization: Techniques and Technologies. IEEE Access 2021, 9, 122924–122950. [Google Scholar] [CrossRef]
- Sivasakthiselvan, S.; Nagarajan, V. Localization Techniques of Wireless Sensor Networks: A Review. In Proceedings of the 2020 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 28–30 July 2020; pp. 1643–1648. [Google Scholar] [CrossRef]
- Li, L.; Liu, H.; Xu, Y.; Zheng, Y. Measurement Linearity and Accuracy Optimization for Time-of-Flight Range Imaging Cameras. In Proceedings of the 2020 IEEE 4th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chongqing, China, 12–14 June 2020; Volume 1, pp. 520–524. [Google Scholar] [CrossRef]
- Mazomenos, E.; De Jager, D.; Reeve, J.; White, N. A two-way time of flight ranging scheme for wireless sensor networks. In Wireless Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6567, pp. 163–178. [Google Scholar]
- Shen, J.; Molisch, A.F.; Salmi, J. Accurate Passive Location Estimation Using TOA Measurements. IEEE Trans. Wirel. Commun. 2012, 11, 2182–2192. [Google Scholar] [CrossRef]
- Li, B.; Zhao, K.; Shen, X. Dilution of Precision in Positioning Systems Using Both Angle of Arrival and Time of Arrival Measurements. IEEE Access 2020, 8, 192506–192516. [Google Scholar] [CrossRef]
- Jiaxi, W.; Yan, C.; Shuo, S. An Improved TDOA Algorithm Applied Person Localization System in Coal Mine. In Proceedings of the 2011 Third International Conference on Measuring Technology and Mechatronics Automation, Washington, DC, USA, 6–7 January 2011; Volume 1, pp. 428–431. [Google Scholar]
- Gendler, A.; Yaron Peleg, S.; Amar, A. A Diffusion-Based Distributed Time Difference Of Arrival Source Positioning. In Proceedings of the 2021 IEEE 24th International Conference on Information Fusion (FUSION), Sun City, South Africa, 1–4 November 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Zandian, R.; Witkowski, U. Implementation Challenges of Synchronisation of UWB Nodes in TDoA Structures. In Proceedings of the 2018 International Conference on Indoor Positioning and Indoor Navigation (IPIN), Nantes, France, 24–27 September 2018; pp. 1–8. [Google Scholar]
- Mototolea, D.; Nicolaescu, I.; Mîndroiu, A.; Vlăsceanu, A. Evaluation of Errors Caused by Inaccurate Clock Synchronization in Time Difference of Arrival-Based Localization Systems. In Proceedings of the 2019 International Symposium on Signals, Circuits and Systems (ISSCS), Iasi, Romania, 11–12 July 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Mekki, K.; Bajic, E.; Chaxel, F.; Meyer, F. A comparative study of LPWAN technologies for large-scale IoT deployment. ICT Express 2019, 5, 1–7. [Google Scholar] [CrossRef]
- SUDO, H.; KOSAKA, K.; ODANI, A.; GEJOH, N.; YASUNAGA, T. Study on Communication Parameter Control for LPWA Network using Radio Environment Monitoring. In Proceedings of the 2020 IEEE 92nd Vehicular Technology Conference (VTC2020-Fall), Victoria, BC, Canada, 18 November–16 December 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Chen, Y.; Sambo, Y.A.; Onireti, O.; Imran, M.A. A Survey on LPWAN-5G Integration: Main Challenges and Potential Solutions. IEEE Access 2022, 10, 32132–32149. [Google Scholar] [CrossRef]
- Patel, D.; Won, M. Experimental Study on Low Power Wide Area Networks (LPWAN) for Mobile Internet of Things. In Proceedings of the 2017 IEEE 85th Vehicular Technology Conference (VTC Spring), Sydney, NSW, Australia, 4–7 June 2017; Volume 2018, pp. 1–5. [Google Scholar]
- Raza, U.; Kulkarni, P.; Sooriyabandara, M. Low Power Wide Area Networks: An Overview. IEEE Commun. Surv. Tutor. 2017, 19, 855–873. [Google Scholar] [CrossRef]
- Lee, J. Multichannel WPAN Protocol for Coexistence Under Densely Deployed Bluetooth LE in ISM. IEEE Trans. Veh. Technol. 2019, 68, 8103–8116. [Google Scholar] [CrossRef]
- Bernatin, T.; Nisha, S.A.; Revathy; Chitra, P. Implementation of communication aid using zigbee technology. In Proceedings of the 2021 5th International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 6–8 May 2021; pp. 29–32. [Google Scholar] [CrossRef]
- Sharma, K.; Dhir, N. A study of wireless networks: WLANs, WPANs, WMANs, and WWANs with comparison. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 7810–7813. [Google Scholar]
- Foubert, B.; Mitton, N. Long-Range Wireless Radio Technologies: A Survey. Future Internet 2020, 12, 13. [Google Scholar] [CrossRef]
- Lee, J.; Park, M.; Kim, Y.S.; Park, P.S.; Jeong, J. A novel cell design approach for LTE underground tunnels coverage. In Proceedings of the PEMWN 2017—6th IFIP International Conference on Performance Evaluation and Modeling in Wired and Wireless Networks, Paris, France, 28–30 November 2017; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2018; Volume 2018, pp. 1–5. [Google Scholar]
- Popli, S.; Jha, R.K.; Jain, S. A Survey on Energy Efficient Narrowband Internet of Things (NBIoT): Architecture, Application and Challenges. IEEE Access 2019, 7, 16739–16776. [Google Scholar] [CrossRef]
- Rico-Alvarino, A.; Vajapeyam, M.; Xu, H.; Wang, X.; Blankenship, Y.; Bergman, J.; Tirronen, T.; Yavuz, E. An overview of 3GPP enhancements on machine to machine communications. IEEE Commun. Mag. 2016, 54, 14–21. [Google Scholar] [CrossRef]
- Beyene, Y.D.; Jantti, R.; Tirkkonen, O.; Ruttik, K.; Iraji, S.; Larmo, A.; Tirronen, T.; Torsner, J. NB-IoT Technology Overview and Experience from Cloud-RAN Implementation. IEEE Wirel. Commun. 2017, 24, 26–32. [Google Scholar] [CrossRef]
- Xu, J.; Yao, J.; Wang, L.; Ming, Z.; Wu, K.; Chen, L. Narrowband Internet of Things: Evolutions, Technologies, and Open Issues. IEEE Internet Things J. 2018, 5, 1449–1462. [Google Scholar] [CrossRef]
- Beyene, Y.D.; Jantti, R.; Ruttik, K.; Iraji, S. On the Performance of Narrow-Band Internet of Things (NB-IoT). In Proceedings of the 2017 IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar]
- Wang, H.; Fapojuwo, A.O. A Survey of Enabling Technologies of Low Power and Long Range Machine-to-Machine Communications. IEEE Commun. Surv. Tutor. 2017, 19, 2621–2639. [Google Scholar] [CrossRef]
- Drubin, C. NB-IoT, CAT-M, SIGFOX and LoRa Battle for LPWA Network Dominance. Microw. J. 2018, 61, 47. [Google Scholar]
- Sanchez-Iborra, R.; Cano, M.D. State of the art in LP-WAN solutions for industrial IoT services. Sensors 2016, 16, 708. [Google Scholar] [CrossRef]
- Naik, N. LPWAN Technologies for IoT Systems: Choice Between Ultra Narrow Band and Spread Spectrum. In Proceedings of the 2018 IEEE International Systems Engineering Symposium (ISSE), Rome, Italy, 1–3 October 2018; pp. 1–8. [Google Scholar]
- Adelantado, F.; Vilajosana, X.; Tuset-Peiro, P.; Martinez, B.; Melia-Segui, J.; Watteyne, T. Understanding the Limits of LoRaWAN. IEEE Commun. Mag. 2017, 55, 34–40. [Google Scholar] [CrossRef]
- Finnegan, J.; Brown, S. A Comparative Survey of LPWA Networking. arXiv 2018, arXiv:1802.04222. [Google Scholar]
- Alleven, M. After W and N, Weightless-P Seeks to Revolutionize LPWAN for the IoT; FierceWirelessTech: West Chester, PA, USA, 2015. [Google Scholar]
- Ratasuk, R.; Mangalvedhe, N.; Zhang, Y.; Robert, M.; Koskinen, J. Overview of narrowband IoT in LTE Rel-13. In Proceedings of the 2016 IEEE Conference on Standards for Communications and Networking (CSCN), Berlin, Germany, 31 October–2 November 2016; pp. 1–7. [Google Scholar]
- Visan, D.A.; Jurian, M.; Lita, I.; Ionescu, L.M.; Mazare, A.G. Direct Sequence Spread Spectrum Communication Module for Efficient Wireless Sensor Networks. In Proceedings of the 2019 11th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Pitesti, Romania, 27–29 June 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Dunlop, B.; Nguyen, H.H.; Barton, R.; Henry, J. Interference Analysis for LoRa Chirp Spread Spectrum Signals. In Proceedings of the 2019 IEEE Canadian Conference of Electrical and Computer Engineering (CCECE), Edmonton, AB, Canada, 5–8 May 2019; pp. 1–5. [Google Scholar]
- Ikpehai, A.; Adebisi, B.; Rabie, K.M.; Anoh, K.; Ande, R.E.; Hammoudeh, M.; Gacanin, H.; Mbanaso, U.M. Low-Power Wide Area Network Technologies for Internet-of-Things: A Comparative Review. IEEE Internet Things J. 2019, 6, 2225–2240. [Google Scholar] [CrossRef]
- Goldhammer, M. License Exempt Spectrum and Advanced Technologies; White paper; ITU: Geneva, Switzerland, 2018. [Google Scholar]
- Dhillon, H.S.; Huang, H.; Viswanathan, H. Wide-area Wireless Communication Challenges for the Internet of Things. IEEE Commun. Mag. 2017, 55, 168–174. [Google Scholar] [CrossRef]
- Bandyopadhyay, L.K. Wireless Communication in Underground Mines: RFID-Based Sensor Networking; Springer: Boston, MA, USA, 2010. [Google Scholar]
- Shelar, P.; Gogate, U. Performance Evaluation of FMAC Protocol in Healthcare Monitoring System based on Wireless Sensor Network. In Proceedings of the 2020 International Conference on Smart Innovations in Design, Environment, Management, Planning and Computing (ICSIDEMPC), Aurangabad, India, 30–31 October 2020; pp. 100–104. [Google Scholar] [CrossRef]
- Walrand, J.; Varaiya, P. (Eds.) CHAPTER 7—Wireless Networks. In High-Performance Communication Networks, 2nd ed.; Morgan Kaufmann: San Francisco, CA, USA, 2000; pp. 305–361. [Google Scholar] [CrossRef]
- Petrosky, E.E.; Michaels, A.J.; Ridge, D.B. Network Scalability Comparison of IEEE 802.15.4 and Receiver-Assigned CDMA. IEEE Internet Things J. 2019, 6, 6060–6069. [Google Scholar] [CrossRef]
- Carreño, J.; Silva, L.; Neves, S.; Aguayo, L.; Braga, A.; Barreto, A.N.; Uzeda Garcia, L.G. Through-The-Earth (TTE) Communications for Underground Mines. J. Commun. Inf. Syst. 2016, 31, 164–176. [Google Scholar] [CrossRef]
- Zhang, C.Y.; Han, S.Y.; Zhou, J.; Li, B.Z.; Yu, X.J.; Yao, K. A Merge Collision Prediction TDMA-MAC Protocol in Distributed VANET. In Proceedings of the 2021 8th International Conference on Information, Cybernetics, and Computational Social Systems (ICCSS), Beijing, China, 10–12 December 2021; pp. 13–18. [Google Scholar] [CrossRef]
- van Dam, T.; Langendoen, K. An adaptive energy-efficient MAC protocol for wireless sensor networks. In Proceedings of the 1st International Conference on Embedded Networked Sensor Systems, Los Angeles, CA, USA, 5–7 November 2003; ACM: New York, NY, USA, 2003; pp. 171–180. [Google Scholar]
- Havinga, P.; Smit, G. E2MaC: An Energy Efficient MAC Protocol for Multimedia Traffic; University of Twente: Enschede, The Netherlands, 1998. [Google Scholar]
- Song, W.Z.; Huang, R.; Shirazi, B.; LaHusen, R. TreeMAC: Localized TDMA MAC protocol for real-time high-data-rate sensor networks. Pervasive Mob. Comput. 2009, 5, 750–765. [Google Scholar] [CrossRef]
- Ahmed, N.; Rahman, H.; Hussain, M. A comparison of 802.11ah and 802.15.4 for IoT. ICT Express 2016, 2, 100–102. [Google Scholar] [CrossRef]
- Cooklev, T. Wireless Communication Standards: A Study of IEEE 802.11, 802.15, and 802.16; IEEE Standards Wireless Networks Series, Standards Information Network; IEEE Press: New York, NY, USA, 2009. [Google Scholar]
- Long, C. Mobile and Wireless Design Essentials; Wiley Publishing: Hoboken, NJ, USA, 2003. [Google Scholar]
- Ziemer, R. Fundamentals of spread spectrum modulation. Synth. Lect. Commun. 2007, 3, 1–79. [Google Scholar]
- Tang, H.; Cao, J.; Liu, X.; Sun, C. SR-MAC: A Low Latency MAC Protocol for Multi-Packet Transmissions in Wireless Sensor Networks. J. Comput. Sci. Technol. 2013, 28, 329–342. [Google Scholar] [CrossRef]
- Liang, L.; Liu, X.; Wang, Y.; Feng, W.; Yang, G. SW-MAC: A Low-Latency MAC Protocol with Adaptive Sleeping for Wireless Sensor Networks. Wirel. Pers. Commun. 2014, 77, 1191–1211. [Google Scholar] [CrossRef]
- Sun, Y.; Du, S.; Gurewitz, O.; Johnson, D. DW-MAC: A low latency, energy efficient demand-wakeup MAC protocol for wireless sensor networks. In Proceedings of the 9th ACM International Symposium on Mobile Ad Hoc Networking and Computing, 26–30 May 2008; ACM: New York, NY, USA, 2008; pp. 53–62. [Google Scholar]
- Chauhan, S.; Gore, M. LDC-MAC: Low latency DC-MAC protocol for wireless sensor network. In Proceedings of the CUBE International Information Technology Conference, Pune, India, 3–5 September 2012; ACM: New York, NY, USA, 2012; pp. 133–137. [Google Scholar]
- Ghose, D.; Froytlog, A.; Li, F.Y. Reducing Overhearing Energy in Wake-Up Radio-Enabled WPANs: Scheme and Performance. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Lee, C.S.; Kim, D.H.; Kim, J.D. An Energy Efficient Active RFID Protocol to Avoid Overhearing Problem. IEEE Sens. J. 2014, 14, 15–24. [Google Scholar] [CrossRef]
- Nguyen, K.; Ji, Y.; Yamada, S. Low Overhead MAC Protocol for Low Data Rate Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2013, 9, 217159. [Google Scholar] [CrossRef]
- Wei, Z.; Oh, H. A Low Control Overhead Big Slot Scheduling MAC Protocol for Reducing Competition in Wireless Sensor Networks. In Proceedings of the 5th International Conference on Communications and Broadband Networking, Bali, Indonesia, 20–22 February 2017; ACM: New York, NY, USA, 2017; pp. 1–5. [Google Scholar]
- Nguyen, K.; Ji, Y. LCO-MAC: A Low Latency, Low Control Overhead MAC Protocol for Wireless Sensor Networks. In Proceedings of the 2008 The 4th International Conference on Mobile Ad-hoc and Sensor Networks, Wuhan, China, 10–12 December 2008; pp. 271–275. [Google Scholar]
- Razaque, A.; Elleithy, K.M. Low Duty Cycle, Energy-Efficient and Mobility-Based Boarder Node—MAC Hybrid Protocol for Wireless Sensor Networks. J. Signal Process. Syst. 2014, 81, 265–284. [Google Scholar] [CrossRef]
- Zhang, D.g.; Zhou, S.; Tang, Y.m. A Low Duty Cycle Efficient MAC Protocol Based on Self-Adaption and Predictive Strategy. Mob. Netw. Appl. 2018, 23, 828–839. [Google Scholar] [CrossRef]
- Therese Aby, A.; Guitton, A.; Lafourcade, P.; Misson, M. History-based MAC Protocol for Low Duty-Cycle Wireless Sensor Networks: The SLACK-MAC Protocol. EAI Endorsed Trans. Mob. Commun. Appl. 2017, 2, 1–10. [Google Scholar] [CrossRef]
- Razaque, A.; Elleithy, K. Scalable and energy efficient medium access control protocol for wireless sensor networks. In Proceedings of the 2015 Long Island Systems, Applications and Technology, Farmingdale, NY, USA, 1 May 2015; pp. 1–4. [Google Scholar]
- Liu, Y.; Yuen, C.; Chen, J.; Cao, X. A scalable Hybrid MAC protocol for massive M2M networks. In Proceedings of the 2013 IEEE Wireless Communications and Networking Conference (WCNC), Shanghai, China, 7–10 April 2013; IEEE, 2013; pp. 250–255. [Google Scholar]
- On, J.; Jeon, H.; Lee, J. A Scalable MAC Protocol Supporting Simple Multimedia Traffic QoS in WSNs. Int. J. Distrib. Sens. Netw. 2011, 7, 495127. [Google Scholar] [CrossRef]
- Pham, H.; Jha, S. An adaptive mobility-aware MAC protocol for sensor networks (MS-MAC). In Proceedings of the 2004 IEEE International Conference on Mobile Ad-hoc and Sensor Systems, Fort Lauderdale, FL, USA, 25–27 October 2004; pp. 558–560. [Google Scholar]
- Lee, W.; Datta, A.; Cardell-Oliver, R. FlexiMAC: A flexible TDMA-based MAC protocol for fault-tolerant and energy-efficient wireless sensor networks. In Proceedings of the 2006 14th IEEE International Conference on Networks, Singapore, 13–15 September 2006; Volume 2, pp. 1–6. [Google Scholar]
- Macoir, N.; Bauwens, J.; Jooris, B.; Van Herbruggen, B.; Rossey, J.; Hoebeke, J.; De Poorter, E. UWB Localization with Battery-Powered Wireless Backbone for Drone-Based Inventory Management. Sensors 2019, 19, 467. [Google Scholar] [CrossRef] [PubMed]
- Li, B.; Zhao, K.; Saydam, S.; Rizos, C.; Wang, Q.; Wang, J. Investigation of indoor positioning technologies for underground mine environments. IPIN (Short Papers/Work-in-Progress Papers). Far East J. Electron. Commun. 2019, 18, 871–893. [Google Scholar] [CrossRef]
- Li, B.; Zhao, K.; Saydam, S.; Rizos, C.; Wang, J.; Wang, Q. Third Generation Positioning System for Underground Mine Environments: An Update on Progress. 2018. Available online: https://www.ignss2016.unsw.edu.au/sites/ignss2016/files/u80/Papers/non-reviewed/IGNSS2016_paper_28.pdf (accessed on 28 March 2022).
- Li, B.; Zhao, K.; Sandoval, E.B. A UWB-Based Indoor Positioning System Employing Neural Networks. J. Geovisualization Spat. Anal. 2020, 4, 1–9. [Google Scholar] [CrossRef]
- Han, H.; Wang, J.; Liu, F.; Zhang, J.; Yang, D.; Li, B. An Emergency Seamless Positioning Technique Based on ad hoc UWB Networking Using Robust EKF. Sensors 2019, 19, 3135. [Google Scholar] [CrossRef] [Green Version]







| Characteristics | Importance | Typical Examples |
|---|---|---|
| Distributed network | Mandatory | N/A |
| Contention-free Communication | Mandatory | N/A |
| Scheduling Protocol | Optional, good to have | N/A |
| Latency | Mandatory | SR-MAC, SW-MAC, DW-MAC, LDC-MAC |
| Energy consumption/overhearing | Mandatory | BBAD Mechanism, RANO Mechanism |
| Energy consumption/overhead | Mandatory | LO-MAC, LoBigMAC, LCO-MAC |
| Energy consumption/duty-cycling | Mandatory | BN-MAC, AP-MAC, SLACK-MAC |
| Scalability | Optional, good to have | SE-MAC, A Hybrid Protocol, SQ-MAC |
| Traffic Adaptability & Throughput | Optional, good to have traffic adaptability and high throughput | N/A |
| Handling mobility | Mandatory | N/A |
| Wake-up radio enabled | Optional, good to have | N/A |
| Purpose | Company | Product | Technology | Application | Notes | URL |
|---|---|---|---|---|---|---|
| Mine Site Technologies | Proximity Detection | low-frequency magnetic field | surface & underground mine | detection range: 0.5–20 m | https://mstglobal.com/technologies/safety-tracking/ (accessed on 1 June 2022) | |
| Situational Awareness | on-board Wi-Fi or Bluetooth tag, RFID tracking tag | surface & underground mine | detection range: 60–120 m | |||
| NewTrax Technologies | Collision Warning System L7 | multiple radio frequency (RF) technologies | underground mine | precise ranging | https://newtrax.com/solution/collision-warning-system-l7 (accessed on 1 June 2022) | |
| Collision Warning System L8 | modular Newtrax Proximity Ranging Sensors (PRS) + L7 | underground mine | 360 degree awareness & ranging | https://newtrax.com/solution/collision-warning-system-l8 (accessed on 1 June 2022) | ||
| Collsion Avoidance System L9 | Same as L8 | underground mine | intervention controls | https://newtrax.com/solution-collision-avoidance-system (accessed on 1 June 2022) | ||
| Stanley Black & Decker | AeroScout | active RFID, WiFi (for communication) | underground mine | mobileView software; secure communications based on Cisco unified wireless networks | https://www.cisco.com/c/dam/en_us/solutions/industries/docs/manufacturing/Aeroscout-Cisco-Brochure.pdf (accessed on 1 June 2022) | |
| Minlog & MapTek | MineSuite | RFID tag (@ 433 MHz), WiFi tag (@ 2.4 GHz) | N/A | RFID: average detection range 50 m; WiFi: detection range, up to 100 m | https://africanminingbrief.com/minlog-deploys-underground-proximity-awareness-bhp-billitons-world-renowned-olympic-dam-mine/ (accessed on 1 June 2022) | |
| CAS | Mine Radio Systems | Helian Underground Safety Solution | UHF RFID Tag, VLF RF communication | underground mine | visual alert via cap-lamp | https://mininglifeonline.net/equipment/mrs-stc-platform/helian/861 (accessed on 1 June 2022) |
| underground communication solutions | N/A | underground mine | voice, data and video | https://www.mining-technology.com/contractors/communications/mine-radio/#company-details (accessed on 1 June 2022) | ||
| Industrea Limited | CAS GPS node | GPS, radio transceiver, Bluetooth wireless technology | mining | typically for light vehicles | https://usermanual.wiki/Industrea-Mining-Technology/PROD10522/html (accessed on 1 June 2022) | |
| Waytronic Security | collision avoidance | camera, ultrasonic detection | manufacturing | Forklift & pedestrian collision avoidance | http://www.wt-safe.com/factorycoll_1.html?device=c&kyw=proximity%20detection%20system&gclid=CjwKCAjwj975BRBUEiwA4whRByB8bQ_ftzM0Zs4B4TWE9d342FB1mn1fTV5bhIOnry_M_8gmXjuehRoCJXcQAvD_BwE (accessed on 1 June 2022) | |
| InfoTronix | collision avoidance system | VLF magnetic fields | underground mine | special tag arrangement | http://www.infotronix.com.au/productcategory/collision-avoidance-system/ (accessed on 1 June 2022) | |
| Booyco Electronics | proximity detection, collision warning | RFID: close proximity detection—VLF; long range detection—UHF | underground mine | adjustable warning and danger zones | https://www.booyco-electronics.co.za/product-range/proximity-detection-system-pds (accessed on 1 June 2022) | |
| Blue Glue (BG) | Third Eye | active RFID Tags | mining | V2P, V2V and V2I (Vehicle to Infrastructure protection) | https://www.blueglue.com.au/products/collision-avoidance-and-proximity-detection/ (accessed on 1 June 2022) | |
| Blue electronics | Buddy Alert | TOF measuring (@ 2.4 hGHz, 900 MHz), GPS | outdoor | device mounted in vehicles | http://www.blueelectronics.com.au/product_detail/165/PPD-02/ (accessed on 1 June 2022) | |
| Orbit Communications | Body Guard | i-Tag | outdoor | magnetic mounting | https://www.bodyguardsafety.com.au/proximity-warning-system/ (accessed on 1 June 2022) | |
| Advanced Mining Technologies (AMT) | CAS-CAM/RF | camera, active sensing—RFID | surface mine | support speed detection | https://www.slideshare.net/nswdre/advanced-mining-technologies-manufacturer-presentation (accessed on 1 June 2022) | |
| AcuMine | 4CAST | GPS and radio frequency signal strength | surface & underground mine | works effectively at both low and high speeds with the same sensitivity | https://im-mining.com/2011/10/19/komatsu-and-acumine-sign-agreement-for-distribution-of-4cast-collision-avoidance-system/#more-4874 (accessed on 1 June 2022) | |
| PBE | proximity alert system | RFID, GPS, electromagnetics and bidirectional radar | surface & underground mine | combine multiple detection technologies; versatile configurations, suitable for different vehicle types | https://pbegrp.com/safety/proximity-alerts/ (accessed on 1 June 2022) | |
| Minecom | Dynamic Anti Collision System (DACS600) | UHF RFID tags (operating @ 400 MHz) | mining | None | https://core.ac.uk/download/pdf/39671161.pdf (accessed on 1 June 2022) | |
| Gamma & Geosteering | TramGuard | low frequency magnetic field | underground, coal mine | fairly short operation range: 3.66 m | https://www.miningmonthly.com/markets/international-coal-news/1303839/massey-demonstrates-proximity-detection-technology (accessed on 1 June 2022) | |
| EV Alert | collision warning system | VHF short-range coded signal | rail crossing | selected frequency can ‘penetrate’ vehicles and buildings | https://www.parliament.vic.gov.au/images/stories/committees/rsc/Safety_at_Level_Crossing/Submissions/21_EV_Alert.pdf (accessed on 1 June 2022) | |
| CAS | Ivolve | PAMS Proximiti | GPS, radar | mining | long-range, high-speed GPS-based proximity awareness system; short-range, low-speed radar proximity detection capabilities | https://www.mining-technology.com/contractors/resource/ivolve/attachment/ivolve2/ (accessed on 1 June 2022) |
| LSM technologies | RadarEye | camera, radar | mining | virtually 360 degree viewing; radar sensor, detection range 2–20 m | https://www.lsm.com.au/item.cfm?category_id=2869&site_id=3 (accessed on 1 June 2022) | |
| IIT solutions | safe mine system | GPS, radar | mining | a special patented algorithm to calculate the path of vehicles | https://www.australianmining.com.au/product/vehicle-collision-system/ (accessed on 1 June 2022) | |
| HxGN MineProtect Collision Avoidance System | GNSS, RF technologies | open pit mines | require no support infrastructure | https://hexagonmining.com/solutions/safety-portfolio/collision-avoidance (accessed on 1 June 2022) | ||
| Hexagon Mining | HxGN MineProtect Tracking Radar | tracking radar | open pit mines | operating range up to 30m | https://hexagonmining.com/solutions/safety-portfolio/hxgn-mineprotect-tracking-radar (accessed on 1 June 2022) | |
| HxGN MineProtect Safety Center | smart camera and combination of above two systems | open pit mines | speed adaptability | https://hexagonmining.com/solutions/safety-portfolio/hxgn-mineprotect-safety-center (accessed on 1 June 2022) | ||
| Minetec | SafeDetect | RF-based mobile nodes, WASP technology developed by CSIRO | surface & underground mine | high-accuracy, low-latency, cm-level proximity detection | http://minetec.com.au/wp-content/uploads/2018/03/MIN-12714-Safedetect-2pp-A4-Flyer.pdf (accessed on 1 June 2022) | |
| Minewest & Nautilus technology | BUDDY | magnetic field | underground, coal mine | integrated into cap-lamp | http://www.nautilus-intl.com/proximity-detection/nautilus-coal-buddy-operators-proximity-detection-system-for-underground-coal-mines-operating-in-an-explosive-methane-gas-environment-class-i-div-ii/ (accessed on 1 June 2022) | |
| Becker | collision avoidance system | UHF, radar and electromagnetic field | surface & underground mine | a tri-technology solution | https://www.becker-mining.com/en/products/smartcom/proximity-detection-system-pds (accessed on 1 June 2022) | |
| Modular Mining | MineAlert | GPS | surface mine | vehicle-to-vehicle only; intelligent path prediction based on vehicle velocity, acceleration and yaw rate | https://www.mining-technology.com/products/minealert-collision/ (accessed on 1 June 2022) | |
| Matrix Design Group | IntelliZone | magnetic field with optional Lidar/Radar/ camera integration | underground, coal mine | machine-specific straight-line and angled zones | https://www.matrixteam.com/wp-content/uploads/2018/08/IntelliZone-8_18.pdf (accessed on 1 June 2022) | |
| Preco electronics | PreView | radar, camera | surface & underground mine | various series of products | https://preco.com/product-manuals/ (accessed on 1 June 2022) | |
| Caterpillar | MineStar Detect | camera, radar, GNSS | surface & underground mine | provide fatigue or distraction detection | https://www.westrac.com.au/en/technology/minestar/minestar-detect (accessed on 1 June 2022) | |
| Cat Detect | GPS, Bluetooth, WiFi, camera, radar | surface & underground mine | https://www.cat.com/en_US/by-industry/mining/surface-mining/surface-technology/detect.html (accessed on 1 June 2022) | |||
| Strata worldwide | HazardAvert | electromagnetic field | surface & underground mine | programmable at specific speeds | https://www.strataworldwide.com/proximity-detection/surface-and-underground (accessed on 1 June 2022) | |
| HazardAlarm | electromagnetic field | surface & underground mine | a single-generator system creates a large electromagnetic field | https://www.strataworldwide.com/company/newsroom/alarm-only-proximity-detection-system (accessed on 1 June 2022) | ||
| CAS | GE mining | CAS | surface—GPS tracking, RF unit and camera; underground—VLF magnetic and WiFi | surface & underground mine | real-time data connectivity; 12-year proven lifetime | https://www.ge.com/digital/sites/default/files/download_assets/GE-Digital-Mine-Collision-Avoidance-System-datasheet.pdf (accessed on 1 June 2022) |
| Jannatec | SmartHelmet | RFID tagging, camera | industrial environments | tailored to each individual customer | https://www.jannatec.com/ensosmarthelmet (accessed on 1 June 2022) | |
| SmartView | multi-camera, WiFi & Bluetooth (for communication) | mining | voice/text/video communication | https://www.jannatec.com/ensosmartview (accessed on 1 June 2022) | ||
| SmartTalk | N/A | industrial environments | 4G LTE radio | https://www.jannatec.com/ensosmarttalk (accessed on 1 June 2022) | ||
| Schauenburg Systems | SCAS surface PDS | RFID, GPS, GSM, camera | surface mine | use time of flight, accuracy <1 m | http://schauenburg.co.za/product/scas-surface-proximity-detection-system/ (accessed on 1 June 2022) | |
| SCAS underground PDS | cameras | underground mine | tag-less, artificial intelligent | http://schauenburg.co.za/mimacs/ (accessed on 1 June 2022) | ||
| Mine Wide Integrated Monitoring and Control System (MIMACS) | dual-band RF technology | surface & underground mine | 2-way Paging & Distress call | http://schauenburg.co.za/wp-content/uploads/2017/03/Schauenburg-MIMACS-Brochure-2017.pdf (accessed on 1 June 2022) | ||
| A&R Engineering | CAS | dual RF technology & time of flight | mining | detection accuracy of better than 1 m to a range of 30 m | http://areng.co.za/collision-avoidance/ (accessed on 1 June 2022) | |
| Sense technologies | Gaurdian alert | doppler radar | outdoor driving | intended for light vehicles | https://www.businesswire.com/news/home/20050613005521/en/Sense-Technologies-Introduces-Guardian-Alert-ScopeOut-Integrated (accessed on 1 June 2022) | |
| SICK | proximity sensors | capacitor / magnetic field | manufacturing | N/A | https://www.sick.com/au/en/c/products (accessed on 1 June 2022) | |
| detection and ranging | Lidar scanning, radar sensing | indoor & outdoor | 2D & 3D lidar scanning | |||
| distance sensors | optic and ultrasonic solutions | positioning | using triangulation and time-of-flight modes | |||
| Ogden safety systems | Sensor Vision System | multi-beam radar (@ 13.4–14.0 GHz) | quarry vehicles | FMCW principle | http://www.ogdenradar.com/the-radar.php?content=2 (accessed on 1 June 2022) | |
| VMS (Quarry Vehicle Auto Braking System) | ||||||
| Joy Global, P&H (acquired by Komatsu) | Smartzone PDS | electromagnetic field | mining | faceboss integration—easy and quick troubleshooting | https://mining.komatsu/technology/proximity-detection/smartzone-proximity-detection (accessed on 1 June 2022) | |
| HawkEye camera system | fisheye cameras with infrared filters | mining | Digital Video Recorder (DVR)—100 to 200 h video | https://mining.komatsu/en-au/technology/proximity-detection/hawkeye-camera-system (accessed on 1 June 2022) | ||
| Intec Video Systems | Car Vision | camera | industrial | vehicle safety camera systems | http://www.intecvideo.com/products.html (accessed on 1 June 2022) | |
| PreView | radar, camera | low power 5.8 GHz radar signal | ||||
| Provix | proximity detection system | RFID, Radar and Sonar object detection | surface & underground mine | N/A | http://provix.net/information/minprodet.asp (accessed on 1 June 2022) | |
| Septentrio | GNSS receivers | UHF radio, WiFi and Bluetooth (for communication) | mining and construction | N/A | https://www.septentrio.com/en/applications/mining-construction (accessed on 1 June 2022) | |
| CAS | MSHA | MSHA Proximity Detection | electromagnetic field | underground mine | tag-based | http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.179.1447&rep=rep1&type=pdf (accessed on 1 June 2022) |
| Wabtec & GE Transportation | Digital Mine Collision Alert system (CAS) | magnetic field, RF and GPS | surface and underground mine | tag-based | https://www.youtube.com/watch?v=GDFNByOYV60 (accessed on 1 June 2022) | |
| Ifm Efector | O3M 3D Smart Sensor | optical technology | outdoor | 3D image data based on PMD technology | http://eval.ifm-electronic.com/ifmza/web/mobile-3d-app-02-Kollisionsvorhersage.htm (accessed on 1 June 2022) | |
| Frederick Energy Products | HIT-NOT | magnetic field | warehouse and industry workplaces | N/A | https://hitnot.com/ (accessed on 1 June 2022) | |
| Rio Tinto (Borax mine) | positioning system | GPS | surface mine | N/A | http://w3.leica-geosystems.com/media/new/product_solution/Dez2004_mining_engineering_GPS.pdf (accessed on 1 June 2022) | |
| Motion Metrics | ShovelMetrics | radar, thermal imaging | mining and construction | interface with our centralised data analysis platform | https://www.motionmetrics.com/shovel-metrics/ (accessed on 1 June 2022) | |
| 3D Laser Mapping | SiteMonitor | laser scanning | mining | accuracy of 10 mm out of range up to 6000 m | https://www.mining-technology.com/contractors/exploration/3d-laser-mapping/ (accessed on 1 June 2022) | |
| Hitachi Mining | SkyAngle | camera | mining | bird’s-eye view | https://www.mining.com/web/hitachi-introduces-skyangle-advanced-peripheral-vision-support-system-at-minexpo-international/ (accessed on 1 June 2022) | |
| Aerial Angle | millimetre wave radar technology | mining | a peripheral vision display system with object detection technology | https://www.mining.com/web/hitachi-construction-machinery-introduces-aerial-angle-peripheral-vision-display-system-with-object-detect-assist-technology-at-minexpo-2/ (accessed on 1 June 2022) | ||
| Vision only | Guardvant | ProxGuard CAS | GPS, radar and camera | mining | light vehicles and heavy equipment | https://www.mining-technology.com/contractors/health-and-safety/guardvant/pressreleases/pressguardvant-proxguard-collision-avoidance/ (accessed on 1 June 2022) |
| PROXIP | proximity detection system | encoded magnetic field | manufacturing | magnetic field generated by antenna works with electronic marker | https://www.proxipi.com/technologie/?lang=en (accessed on 1 June 2022) | |
| Safety Vision | vision system | camera | wide range of application | N/A | http://www.safetyvision.com/products (accessed on 1 June 2022) | |
| ECCO | vision system | camera | wide range of application | N/A | https://www.eccoesg.com/us/en/products/camera-systems (accessed on 1 June 2022) | |
| Flir Systems | vision system | thermal camera | wide range of application | N/A | https://www.flir.com.au/applications/camera-cores-components/ (accessed on 1 June 2022) | |
| Nautitech | vision system | thermal camera | harsh environment | marker band identification during cutting cycles | https://nautitech.com.au/wp-content/uploads/2019/05/Nautitech-Camera-Brochure-2019.pdf (accessed on 1 June 2022) | |
| HD and IR camera | harsh environment | available with Wi-Fi | ||||
| High Bandwidth Networks | N/A | surface and underground mine | fiber optic cables, Wi-Fi APs and mesh | https://mstglobal.com/technologies/network-infrastructure/ (accessed on 1 June 2022) | ||
| Mine Site Technologies | Through-The-Earth Transmission | surface & underground mine | ultra low frequency RF signal | |||
| Leaky Feeder Radio | surface & underground mine | two-way voice and low-bandwidth data solution | ||||
| Communi- cation only | Becker Varis | Vital Alert | underground mine | 2-way voice and data; VLF, electromagnetic induction | https://mininglifeonline.net/equipment/our-products/vital-alert/459 (accessed on 1 June 2022) | |
| Cattron | SIAMnet | underground mine | voice and data; cable modem technology and coaxial cable | http://catce.cl/wp-content/uploads/2019/03/SAIMnet.pdf (accessed on 1 June 2022) | ||
| OTN systems | telecom network for mining | underground mine | N/A | https://www.otnsystems.com/industries/mining (accessed on 1 June 2022) | ||
| MeshDynamics | third-generation of mesh network | surface and underground mine, coal mine | based on the Wi-Fi 802.11 protocol | https://www.meshdynamics.com/documents/Mesh_Mining_July08.pdf (accessed on 1 June 2022) |
| Technology | Operating Range | Distance Accuracy | Update Rate | False Alarms | Interference | Deployment Effort | Operation Condition |
|---|---|---|---|---|---|---|---|
| Normal Camera | typically >150 m, min 10 m | vision only | real-time | unlikely | unlikely | high | LOS only |
| Thermal Camera | typically <100 m | vision only | real-time | likely | unlikely | high | LOS only |
| Infrared Camera | typically <10 m | vision only | real-time | likely | likely | high | LOS only |
| EM field (approx. 70–140 kHz) | typically 10–100 m (depends on power) | typically m level, ideally <1 m | typically ms level | often | likely | medium | slightly affected by NLOS |
| Radar | continuous wave: short range; pulsed radar: <30 km | typically submeter level | typically ms level, <70 ms | likely | unlikely | low | LOS only |
| Lidar | long range: typically >100 m; short range: <50 m | typically cm or mm level | typically ms level, <10 ms | likely | unlikely | low | LOS only |
| Ultrasonic | typically <10 m | typically submetre level, ideally cm level | typically ms level | likely | unlikely | low | LOS only |
| RF signals | LF passive (@125 kHz, 134.3 kHz & 225 kHz): typically 10–30 cm, max 2 m; HF passive (@13.56 MHz): typically <1.5 m; UHF passive (@860–960 MHz): 1–50 m; UHF active (@433 MHz): typically 30 m–3 km; SHF active (@2.45 GHz): typically <100 m | proximity only | typically <100 ms (depends on frequency and distance) | often | likely | medium | LF: slightly affected by NLOS; HF: affected by NLOS; UHF & SHF: affected by NLOS profoundly |
| Bluetooth | Bluetooth 4.0: typically 10–30 m; BLE: average 80 m; long range beacon: typically 200 m | proximity only | Bluetooth: typically 100 ms; BLE: typically 3 ms | likely | likely | low | affected by NLOS |
| Zigbee | LOS: >300 m; indoor: average <100 m | 3–5 m | typically s level (depends on data rate) | likely | likely | medium | affected by NLOS |
| UWB | high data rate: <100 m; LOS using IEEE 802.15.4a: <200 m (depends on data rate) | <10 cm (based on ToF) | typically ns level | unlikely | unlikely | low | slightly affected by NLOS |
| Method | Accuracy | Power Consumption | System Capacity | Synchronisation Requirements | Out-Of-Area Positioning |
|---|---|---|---|---|---|
| TOF | High | High | Low | No | No |
| TDOA | High | Low | High | Yes | Yes |
| TOA | High | Low | High | Yes | Yes |
| AOA | Low | Low | High | No | Yes |
| Criteria | LECIM | RPMA | LoRa | SigFox | NB-IoT | Telensa | Weightless | LTE-M | IEEE 802.15.4 | IEEE 802.11ah |
|---|---|---|---|---|---|---|---|---|---|---|
| Latency | critical message delay: 15 s | typically 10–100 ms | typically 10–100 ms | typically 10–100 ms | typically 10–100 ms | typically 10–100 ms | typically 10–100 ms | typically <150 ms (excluding handover latency) | 0–20 s | 0–10 s |
| Cost | N/A | Low | Low | Low | High | Low | Low | High | N/A | |
| Operation range | LOS: 20 km; NLOS: 5 km | urban: 15 km; LOS: 500 km | urban: 5 km; rural: 15 km | urban: 10 km; rural: 50 km | urban: 1km; rural: 10 km; typically <15 km | urban: 3 km; rural: 8 km | typically <10 km | typically <11 km | LOS: up to 20 km; NLOS: 5 km | 100–1000 m |
| Battery lifetime | typically 3 years | 10 years + | 10 years + | 10 years + | 5–10 years | 10 years + | 10 years + | 3–10 years | 802.15.4 is more energy efficient than 802.11ah | |
| Data rate | 0.00153-125 kbps | uplink: 624 kbps; downlink: 156 kbps | CSS: typically 0.3-5 kbps, up to 10 kbps; FSK: 50 kbps | uplink: 100 bps; downlink: 600 bps | uplink: 64/158.5 kbps; downlink: 128/106 kbps | uplink: 62.5 bps; downlink: 500 bps | downlink: 0.0025-16.0 Mbps; uplink: 0.00025-0.5 Mbps | uplink: 1Mbps, up to 7 Mbps; downlink: 1 Mbps, up to 4 Mbps | 0.00153-125 kbps; 250 kbps (in 2.4 GHz) | 78 Mbps; 16 Mbps in sub-1 GHz |
| Frequency band | 433 MHz | 2.4 GHz ISM | sub-1 GHz ISM | sub-1 GHz ISM | 7–900 MHz | sub-1 GHz ISM | sub-1 GHz ISM | LTE band | sub-1 GHz ISM; 2.4 GHz (depends on different countries) | sub-1 GHz ISM |
| Spectrum license | unlicensed only in Region 1, not including Australia (Region 3) | unlicensed | unlicensed | unlicensed | licensed | unlicensed | unlicensed | licensed | unlicensed | unlicensed |
| Modulation | DPSK, GFSK | RPMA, DSSS | CSS, FSK | uplink: BPSK, DBPSK; downlink: GFSK | QPSK | 2-FSK | QAM, OQPSK, BPSK | uplnik: SC-FDMA, QAM; downlink: OFDMA, QAM | BPSK, FSK, OQPSK | OFDM |
| Application | Critical infrastructure, environmental monitoring | Smart metering, Smart cities, Smart lighting | Smart metering, Smart cities, Smar building | Smart metering, Smart cities, Smart parking | Smart metering | Smart cities, Smart lighting, Smart parking | Smart metering, Asset tracking, Health monitoring | Smart street lighting, environmental conditions monitoring | Smart agriculture, Environment monitoring | Smart Cities, Smart Home |
| Year | Protocol | Categorization | Latency | Energy Consumption | Scalability | Traffic Adaptability | Throughput | Handling Mobility | Wake-Up Radio Enabled | Notes | ||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Overhearing | Overhead | Low Duty Cycle | ||||||||||
| 1988 | E2MaC | contention-free | YES | YES | QoS support | |||||||
| 2003 | T-MAC | contention-based | YES | YES | balance between overhearing avoidance and maximum throughput | |||||||
| 2004 | MS-MAC | contention-based | YES | YES | YES | QoS support | ||||||
| 2005 | S-MAC | contention-based | YES | YES | YES | YES | per-node fairness; collision avoidance | |||||
| 2006 | FlexiMAC | contention-free | YES | YES | YES | fair access; data delivery guarantee | ||||||
| 2008 | DW-MAC | contention-based | YES | YES | YES | YES | aim for bursty and high-traffic loads | |||||
| LCO-MAC | contention-based | YES | YES | allow multi-hop transmission within one duty cycle | ||||||||
| eL-MAC | contention-based | YES | YES | YES | suitable for low data rate networks | |||||||
| SASW-CR | contention-based | YES | YES | UWB-PHY; QoS support | ||||||||
| 2009 | TreeMAC | contention-free | YES | YES | 2D frame-slot assignment; for high data rate networks | |||||||
| 2010 | - | contention-free | YES | aim for low-data-rate WSNs | ||||||||
| VLA-MAC | contention-based | YES | YES | YES | YES | optimised for burst transmission | ||||||
| 2011 | SQ-MAC | contention-based | YES | multimedia traffic QoS; self recovery | ||||||||
| GLASS | contention-free | YES | YES | YES | YES | aim for data-intensive sensor networks | ||||||
| 2012 | LDC-MAC | contention-based | YES | YES | dual-channel transmission | |||||||
| 2013 | - | hybrid | YES | YES | for massive M2M networks | |||||||
| SR-MAC | contention-based | YES | YES | multi-packet transmission within one operational cycle | ||||||||
| LO-MAC | contention-based | YES | YES | YES | YES | YES | aim for low-data-rate WSNs | |||||
| PD-MAC | contention-free | YES | optimisation of scheduling scheme and slot assignment to maximise spatial reuse factor | |||||||||
| FTDMA | contention-free | YES | YES | YES | YES | YES | YES | controlled by cluster heads assigned distributively | ||||
| ECOMP | contention-free | YES | YES | clustering; ring configuration | ||||||||
| 2014 | - | hybrid | YES | convention-based CSMA + reservation-based TDMA; QoS support | ||||||||
| SW-MAC | contention-based | YES | YES | YES | scout-based scheduling | |||||||
| BN-MAC | hybrid | YES | YES | YES | Least Distance Smart Neighbouring Search model | |||||||
| RANO | contention-based | YES | YES | active RFID protocol | ||||||||
| CT-MAC | contention-based | YES | suitable for direct sequence UWB system | |||||||||
| 2015 | SE-MAC | contention-based | YES | YES | YES | Adaptable Application Independent Aggregation model | ||||||
| OPC | contention-based | YES | YES | parallel transmission based on local concurrency map | ||||||||
| EH-RDFSA | contention-based | YES | YES | energy harvesting for temporary energy shortages | ||||||||
| H-TSAC | contention-free | YES | YES | hierarchical link scheduling with proactive time slots acquisition | ||||||||
| 2016 | - | contention-free | YES | modifies IEEE 802.15.4; minimum risk of frame collisions | ||||||||
| 2017 | BigMAC | contention-free | YES | receiver-initiated; tree topology | ||||||||
| SLACK-MAC | contention-based | YES | self-adaptive; history-based | |||||||||
| 2018 | AP-MAC | contention-based | YES | YES | self-adaption; collision reconnect mechanism | |||||||
| BBAD | contention-based | YES | YES | YES | address decoding and validation; increased system capacity | |||||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qian, M.; Zhao, K.; Li, B.; Gong, H.; Seneviratne, A. Survey of Collision Avoidance Systems for Underground Mines: Sensing Protocols. Sensors 2022, 22, 7400. https://doi.org/10.3390/s22197400
Qian M, Zhao K, Li B, Gong H, Seneviratne A. Survey of Collision Avoidance Systems for Underground Mines: Sensing Protocols. Sensors. 2022; 22(19):7400. https://doi.org/10.3390/s22197400
Chicago/Turabian StyleQian, Meilin, Kai Zhao, Binghao Li, Henry Gong, and Aruna Seneviratne. 2022. "Survey of Collision Avoidance Systems for Underground Mines: Sensing Protocols" Sensors 22, no. 19: 7400. https://doi.org/10.3390/s22197400







