An Efficient Metaheuristic-Based Clustering with Routing Protocol for Underwater Wireless Sensor Networks
Abstract
:1. Introduction
2. Literature Review
3. The Proposed Model
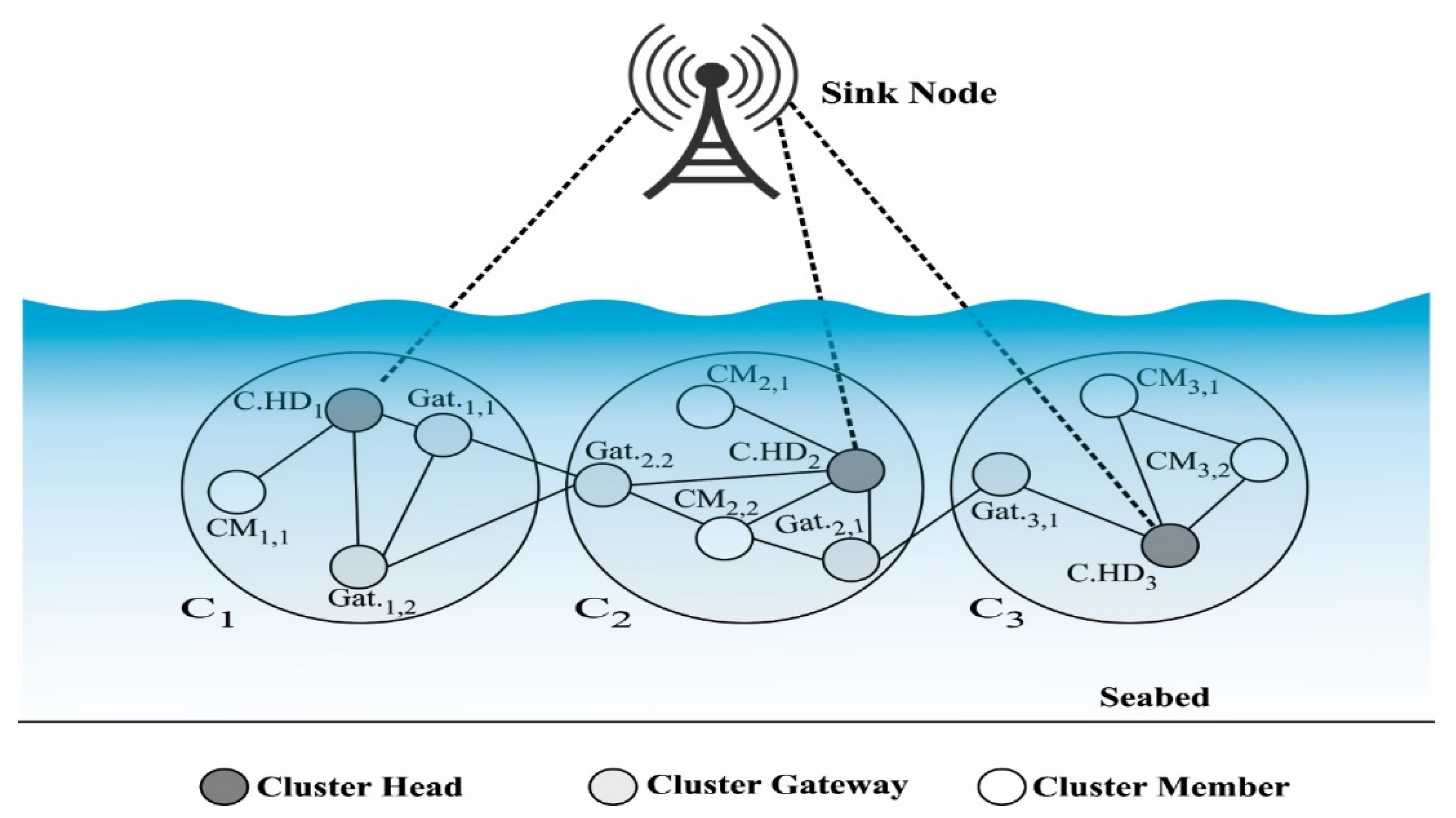
3.1. System Model
- The nodes know its position and the position of SN on initial placement;
- Nodes might become the CH, and clusters member/relay;
- The CH is rotated among the sensors for conserving energy.
3.2. Design of CEPOC Technique
3.3. Design of MHR-GOA Technique
| Algorithm 1: Pseudo code of GOA |
| Initialize , and maximal amounts of iteration; Evaluate the fitness of every search agent; T = optimal search agent; amounts of iteration) Upgrade c; for every search agent Regulate the distance amongst grasshopper in [1,4]; Upgrade the location of the present search agent; Bring the present search agent back when it drives outside the boundary; end for when it has an optimal solution; ; end while ; End |
4. Performance Validation
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Awan, K.M.; Shah, P.A.; Iqbal, K.; Gillani, S.; Ahmad, W.; Nam, Y. Underwater wireless sensor networks: A review of recent issues and challenges. Wirel. Commun. Mob. Comput. 2019, 2019, 6470359. [Google Scholar] [CrossRef]
- Jouhari, M.; Ibrahimi, K.; Tembine, H.; Ben-Othman, J. Underwater wireless sensor networks: A survey on enabling technologies, localization protocols and internet of underwater things. IEEE Access 2019, 7, 96879–96899. [Google Scholar] [CrossRef]
- Arjunan, S.; Pothula, S.; Ponnurangam, D. F5N-based unequal clustering protocol (F5NUCP) for wireless sensor networks. Int. J. Commun. Syst. 2018, 31, e3811. [Google Scholar] [CrossRef]
- Xiao, X.; Huang, H. A Clustering Routing Algorithm Based on Improved Ant Colony Optimization Algorithms for Underwater Wireless Sensor Networks. Algorithms 2020, 13, 250. [Google Scholar] [CrossRef]
- Rout, R.; Parida, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. Skin Lesion Extraction Using Multiscale Morphological Local Variance Reconstruction Based Watershed Transform and Fast Fuzzy C-Means Clustering. Symmetry 2021, 13, 2085. [Google Scholar] [CrossRef]
- Zhou, Y.; Yang, H.; Hu, Y.; Kung, S. Cross-layer network lifetime maximization in underwater wireless sensor networks. IEEE Syst. J. 2020, 14, 220–231. [Google Scholar] [CrossRef]
- Gokul Anand, J. Trust based optimal routing in MANET’s. In Proceedings of the International Conference on Emerging Trends in Electrical and Computer Technology, Nagercoil, India, 23–24 March 2011; pp. 1150–1156. [Google Scholar] [CrossRef]
- Yu, W.; Chen, Y.; Wan, L.; Zhang, X.; Zhu, P.; Xu, X. An energy optimization clustering scheme for multi-hop underwater acoustic cooperative sensor networks. IEEE Access 2020, 8, 89171–89184. [Google Scholar] [CrossRef]
- Zhang, J.; Cai, M.; Han, G.; Qian, Y.; Shu, L. Cellular clustering-based interference-aware data transmission protocol for underwater acoustic sensor networks. IEEE Trans. Veh. Technol. 2020, 69, 3217–3230. [Google Scholar] [CrossRef]
- Hou, R.; He, L.; Hu, S.; Luo, J. Energy-balanced unequal layering clustering in underwater acoustic sensor networks. IEEE Access 2018, 6, 39685–39691. [Google Scholar] [CrossRef]
- Ramalingam, C.; Prakash, M. An efficient applications cloud interoperability framework using I-Anfis. Symmetry 2021, 13, 268. [Google Scholar] [CrossRef]
- Khan, A.; Khan, M.; Ahmed, S.; Abd Rahman, M.A.; Khan, M. Energy harvesting based routing protocol for underwater sensor networks. PLoS ONE 2019, 14, e0219459. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Bhattacharjya, K.; Alam, S.; De, D. CUWSN: Energy efficient routing protocol selection for cluster based underwater wireless sensor network. Microsyst. Technol. 2019, 1–17. [Google Scholar] [CrossRef]
- Madhan, E.S.; Annamalai, R. A Novel Approach for Vehicle Type Classification and Speed Prediction Using Deep Learning. J. Comput. Theoret. Nanosci. 2020, 17, 2237–2242. [Google Scholar] [CrossRef]
- Sahana, S.; Singh, K. Fuzzy based energy efficient underwater routing protocol. J. Discret. Math. Sci. Cryptogr. 2019, 22, 1501–1515. [Google Scholar] [CrossRef]
- Fang, W.; Zhang, W.; Chen, W.; Liu, J.; Ni, Y.; Yang, Y. MSCR: Multidimensional secure clustered routing scheme in hierarchical wireless sensor networks. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 1–20. [Google Scholar] [CrossRef]
- Gomathi, R.M.; Manickam, J.M.L.; Sivasangari, A.; Ajitha, P. Energy efficient dynamic clustering routing protocol in underwater wireless sensor networks. Int. J. Netw. Virtual Organ. 2020, 22, 415–432. [Google Scholar] [CrossRef]
- Sher, A.; Javaid, N.; Azam, I.; Ahmad, H.; Abdul, W.; Ghouzali, S.; Niaz, I.A.; Khan, F.A. Monitoring square and circular fields with sensors using energy-efficient cluster-based routing for underwater wireless sensor networks. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717717189. [Google Scholar] [CrossRef] [Green Version]
- Karim, S.; Shaikh, F.K.; Aurangzeb, K.; Chowdhry, B.S.; Alhussein, M. Anchor nodes assisted cluster-based routing protocol for reliable data transfer in underwater wireless sensor networks. IEEE Access 2021, 9, 36730–36747. [Google Scholar] [CrossRef]
- Zhu, F.; Wei, J. An energy efficient routing protocol based on layers and unequal clusters in underwater wireless sensor networks. J. Sens. 2018, 2018, 5835730. [Google Scholar] [CrossRef]
- Saravana Kumar, C. An Authentication Technique for Accessing De-Duplicated Data from Private Cloud using One Time Password. Int. J. Inf. Secur. Priv. 2017, 11, 1–10. [Google Scholar] [CrossRef]
- Neelakandan, S.; Paulraj, D. A gradient boosted decision tree-based sentiment classification of twitter data. Int. J. Wavelets Multiresolution Inf. Processing 2020, 18, 1–21. [Google Scholar] [CrossRef]
- Yang, J.; Gao, H. Cultural emperor penguin optimizer and its application for face recognition. Math. Probl. Eng. 2020, 2020, 9579538. [Google Scholar] [CrossRef]
- Berlin, M.A.; Tripathi, S. IoT-based traffic prediction and traffic signal control system for smart city. Soft Comput. 2021, 25, 12241–12248. [Google Scholar] [CrossRef]
- Khan, M.F.; Bibi, M.; Aadil, F.; Lee, J.W. Adaptive Node Clustering for Underwater Sensor Networks. Sensors 2021, 21, 4514. [Google Scholar] [CrossRef]
- Pretty Diana Cyril, C.; Rene Beulah, J.; Neelakandan, S.; Prakash, M.; Harshavardhan, A.; Sivabalaselvamani, D. An automated learning model for sentiment analysis and data classification of Twitter data using balanced CA-SVM. Concurrent Eng. 2021, 29, 386–395. [Google Scholar] [CrossRef]
- Paulraj, D. An Automated Exploring And Learning Model For Data Prediction Using Balanced CA-SVM. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 4979–4990. [Google Scholar] [CrossRef]
- Subbulakshmi, P.; Ramalakshmi, V. Honest Auction Based Spectrum Assignment and Exploiting Spectrum Sensing Data Falsification Attack Using Stochastic Game Theory in Wireless Cognitive Radio Network. Wirel. Pers. Commun.—Int. J. 2018, 102, 799–816. [Google Scholar] [CrossRef]
- Mirjalili, S.Z.; Mirjalili, S.; Saremi, S.; Faris, H.; Aljarah, I. Grasshopper optimization algorithm for multi-objective optimization problems. Appl. Intell. 2018, 48, 805–820. [Google Scholar] [CrossRef]
- Subahi, A.F.; Alotaibi, Y.; Khalaf, O.I.; Ajesh, F. Packet drop battling mechanism for energy aware detection in wireless networks. Comput. Mater. Contin. 2020, 66, 2077–2086. [Google Scholar] [CrossRef]
- Veeraiah, N.; Khalaf, O.I.; Prasad, C.V.P.R.; Alotaibi, Y.; Alsufyani, A.; Alghamdi, S.A.; Alsufyani, N. Trust aware secure energy efficient hybrid protocol for manet. IEEE Access 2021, 9, 120996–121005. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Badotra, S.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Alassery, F. Energy-Efficient Clustering Scheme for Flying Ad-Hoc Networks Using an Optimized LEACH Protocol. Energies 2021, 14, 6016. [Google Scholar] [CrossRef]
- Palanisamy, S.; Thangaraju, B.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Alassery, F. A Novel Approach of Design and Analysis of a Hexagonal Fractal Antenna Array (HFAA) for Next-Generation Wireless Communication. Energies 2021, 14, 6204. [Google Scholar] [CrossRef]
- Alotaibi, Y.; Malik, M.N.; Khan, H.H.; Batool, A.; ul Islam, S.; Alsufyani, A.; Alghamdi, S. Suggestion Mining from Opinionated Text of Big Social Media Data. CMC-Comput. Mater. Contin. 2021, 68, 3323–3338. [Google Scholar] [CrossRef]
- Alotaibi, Y. A New Database Intrusion Detection Approach Based on Hybrid Meta-Heuristics. CMC-Comput. Mater. Contin. 2021, 66, 1879–1895. [Google Scholar] [CrossRef]
- Suryanarayana, G.; Chandran, K.; Khalaf, O.I.; Alotaibi, Y.; Alsufyani, A.; Alghamdi, S.A. Accurate Magnetic Resonance Image Super-Resolution Using Deep Networks and Gaussian Filtering in the Stationary Wavelet Domain. IEEE Access 2021, 9, 71406–71417. [Google Scholar] [CrossRef]
- Kamalraj, R.; Ranjith Kumar, V.; Rao, C.S.; Anand, R.; Singh, H. Interpretable filter based convolutional neural network (IF-CNN) for glucose prediction and classification using PD-SS algorithm. Measurement 2021, 183, 109804. [Google Scholar] [CrossRef]
- Kavitha, T.; Mathai, P.P.; Karthikeyan, C.; Ashok, M.; Kohar, R.; Avanija, J.; Neelakandan, S. Deep Learning Based Capsule Neural Network Model for Breast Cancer Diagnosis Using Mammogram Images. Interdiscip. Sci. Comput. Life Sci. 2021, 1–17. [Google Scholar] [CrossRef]
- Reshma, G.; Al-Atroshi, C.; Nassa, V.K.; Geetha, B.; Sunitha, G.; Galety, M.G.; Neelakandan, S. Deep Learning-Based Skin Lesion Diagnosis Model Using Dermoscopic Images. Intell. Autom. Soft Comput. 2022, 31, 621–634. [Google Scholar] [CrossRef]
- Arun, A.; Bhukya, R.R.; Hardas, B.M.; Kumar, T.C.A.; Ashok, M. An Automated Word Embedding with Parameter Tuned Model for Web Crawling. Intell. Autom. Soft Comput. 2022, 32, 1617–1632. [Google Scholar]
- Li, G.; Liu, F.; Sharma, A.; Khalaf, O.I.; Alotaibi, Y.; Alsufyani, A.; Alghamdi, S. Research on the natural language recognition method based on cluster analysis using neural network. Math. Probl. Eng. 2021, 2021, 9982305. [Google Scholar] [CrossRef]
- Alsufyani, A.; Alotaibi, Y.; Almagrabi, A.O.; Alghamdi, S.A.; Alsufyani, N. Optimized intelligent data management framework for a cyber-physical system for computational applications. Complex Intell. Syst. 2021, 1–13. [Google Scholar] [CrossRef]
- Annamalai, R.; Rayen, S.J.; Arunajsmine, J. Social Media Networks Owing To Disruptions for Effective Learning. Procedia Comput. Sci. 2020, 172, 145–151. [Google Scholar] [CrossRef]
- Divyabharathi, S. Large scale optimization to minimize network traffic using MapReduce in big data applications. In Proceedings of the International Conference on Computation of Power, Energy Information and Communication (ICCPEIC), Melmaruvathur, India, 20–21 April 2016; pp. 193–199. [Google Scholar] [CrossRef]
- Jain, D.K.; Sah Tyagi, S.K.K.; Prakash, M.; Natrayan, L. Metaheuristic Optimization-based Resource Allocation Technique for Cybertwin-driven 6G on IoE Environment. IEEE Trans. Ind. Inform. 2021. [Google Scholar] [CrossRef]
- Asha, P.; Natrayan, L.; Geetha, B.T.; Rene Beulah, J.; Sumathy, R.; Varalakshmi, G. IoT enabled environmental toxicology for air pollution monitoring using AI techniques. Environ. Res. 2022, 205, 112574. [Google Scholar] [CrossRef] [PubMed]
- Venu, D.; Mayuri, A.V.R.; Murthy, G.L.N.; Arulkumar, N.; Shelke, N. An Efficient Low Complexity Compression based Optimal Homomorphic Encryption for Secure Fiber Optic Communication. Optik 2021, 168545. [Google Scholar] [CrossRef]
- Supreet, K.; Rajiv, M. Hybrid meta-heuristic optimization based energy efficient protocol for wireless sensor networks. Egypt. Inform. J. 2018, 19, 145–150. [Google Scholar] [CrossRef]
- Jha, N.; Prashar, D.; Khalaf, O.I.; Alotaibi, Y.; Alsufyani, A.; Alghamdi, S. Blockchain Based Crop Insurance: A Decentralized Insurance System for Modernization of Indian Farmers. Sustainability 2021, 13, 8921. [Google Scholar] [CrossRef]






| Number of Rounds | ||||||
|---|---|---|---|---|---|---|
| LEACH | LEACH-ANT | CUWSN | EOCA | ACOCR | MCR-UWSN | |
| FND | 424 | 560 | 629 | 689 | 805 | 852 |
| HND | 646 | 813 | 891 | 949 | 1050 | 1121 |
| LND | 710 | 906 | 989 | 1021 | 1165 | 1187 |
| Number of Rounds for Energy Exhausted (NREE) | ||||||
|---|---|---|---|---|---|---|
| Number of Nodes | LEACH | LEACH-ANT | CUWSN | EOCA | ACOCR | MCR-UWSN |
| 300 | 463 | 631 | 718 | 775 | 919 | 1000 |
| 325 | 523 | 691 | 751 | 859 | 952 | 1045 |
| 350 | 619 | 793 | 823 | 904 | 1000 | 1093 |
| 375 | 670 | 826 | 919 | 991 | 1111 | 1186 |
| 400 | 709 | 913 | 985 | 1027 | 1168 | 1264 |
| 425 | 781 | 946 | 1021 | 1111 | 1201 | 1288 |
| 450 | 826 | 1045 | 1090 | 1156 | 1252 | 1336 |
| 475 | 868 | 1099 | 1138 | 1225 | 1306 | 1387 |
| 500 | 928 | 1138 | 1231 | 1267 | 1411 | 1489 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Subramani, N.; Mohan, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. An Efficient Metaheuristic-Based Clustering with Routing Protocol for Underwater Wireless Sensor Networks. Sensors 2022, 22, 415. https://doi.org/10.3390/s22020415
Subramani N, Mohan P, Alotaibi Y, Alghamdi S, Khalaf OI. An Efficient Metaheuristic-Based Clustering with Routing Protocol for Underwater Wireless Sensor Networks. Sensors. 2022; 22(2):415. https://doi.org/10.3390/s22020415
Chicago/Turabian StyleSubramani, Neelakandan, Prakash Mohan, Youseef Alotaibi, Saleh Alghamdi, and Osamah Ibrahim Khalaf. 2022. "An Efficient Metaheuristic-Based Clustering with Routing Protocol for Underwater Wireless Sensor Networks" Sensors 22, no. 2: 415. https://doi.org/10.3390/s22020415
APA StyleSubramani, N., Mohan, P., Alotaibi, Y., Alghamdi, S., & Khalaf, O. I. (2022). An Efficient Metaheuristic-Based Clustering with Routing Protocol for Underwater Wireless Sensor Networks. Sensors, 22(2), 415. https://doi.org/10.3390/s22020415








