Data Center Traffic Prediction Algorithms and Resource Scheduling
Abstract
1. Introduction
2. Related Works
3. Proposed System
3.1. Tree–Seed Optimizer Algorithm
| Algorithm 1 Lévy Flight Improved Tree–Seed Algorithm (LTSA) |
| 1. Initialization algorithm Generate N random trees in the D-dimensional search space by using the formula; Calculate the position of the tree according to the problem objective function; Choose the optimal solution according to the formula. |
| 2. Search for torrentsDetermine the number of seeds this tree produces; Each dimension of the FOR seed; Update this dimension according to the formula; Choose the best seed and compare it with this lesson tree; If the seed is in a better position than the tree, replace the tree with the seed. 3. Select the optimal solution in the population If the newly generated optimal solution is better than the previous optimal solution, the new optimal solution and its corresponding tree are generated.; Or replace the original optimal solution and the corresponding tree. 4. Check whether the iteration termination condition is meet If not satisfied, go back to Step2. 5. Output the optimal solution |
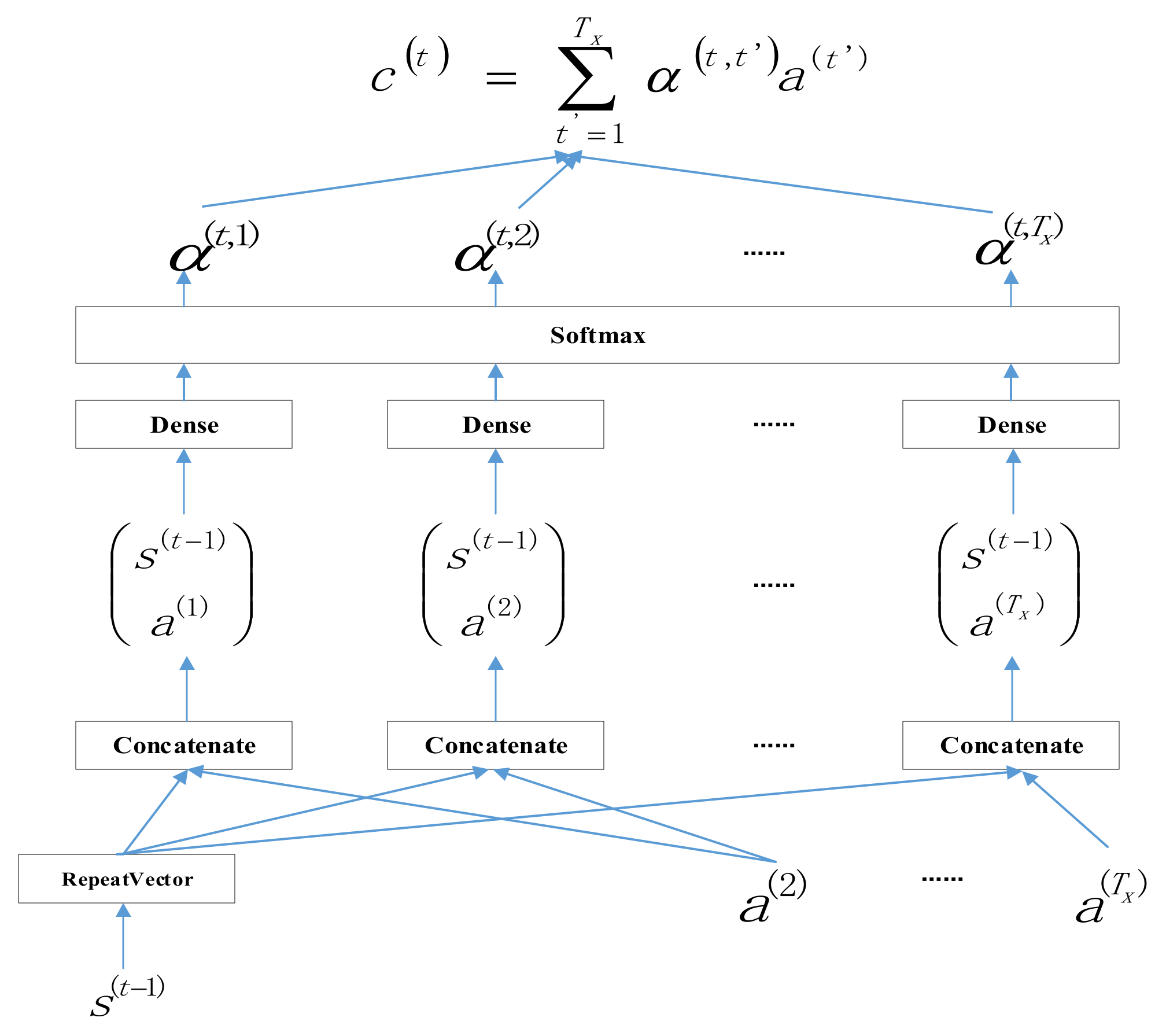
3.2. Attention Mechanism
3.3. AM-Based LSTM Prediction Model
3.4. AM-LSTM Model Training Steps
| Algorithm 2 Long Short-Term Memory Model (AM-LSTM) Introducing Attention Mechanism |
| Input: Network traffic and its impact factor training set and test set. Output: The network traffic value at a certain moment. Complete the forward propagation calculation of the prediction model at the AMLSTM network layer; |
| 1. Initialize the parameters to be learned in AMLSTM; 2. Introduce the attention mechanism (AM) into the LSTM neural network layer. Multiple memory units use the attention mechanism to calculate the probability distribution of the output features multiple times, and reweigh the output features as the input of post-LSTM; 3. Backpropagation is performed in the LSTM neural network layer. At this time, the error value of each neuron on the hidden layer of the LSTM network needs to be calculated, and the partial derivative is obtained, and the corresponding weight and bias are updated; 4. Iterative training to the set number of iterations, ending the model parameter training; 5. Test the model, and judge whether the model is good or bad through the evaluation indicators; 6. Back-normalize the output data with the time series Y test data and compare it with the real value to evaluate the predictive ability of the model. |
4. Business Scheduling Algorithm
4.1. Business Collaborative Cache and Load Balancing
4.2. Multi-Priority Queue Cache Management Method
4.3. Load Balancing Scheduling Method
5. Experiments and Results
5.1. Preparation before Experiment
5.2. Traffic Prediction Experiment Results
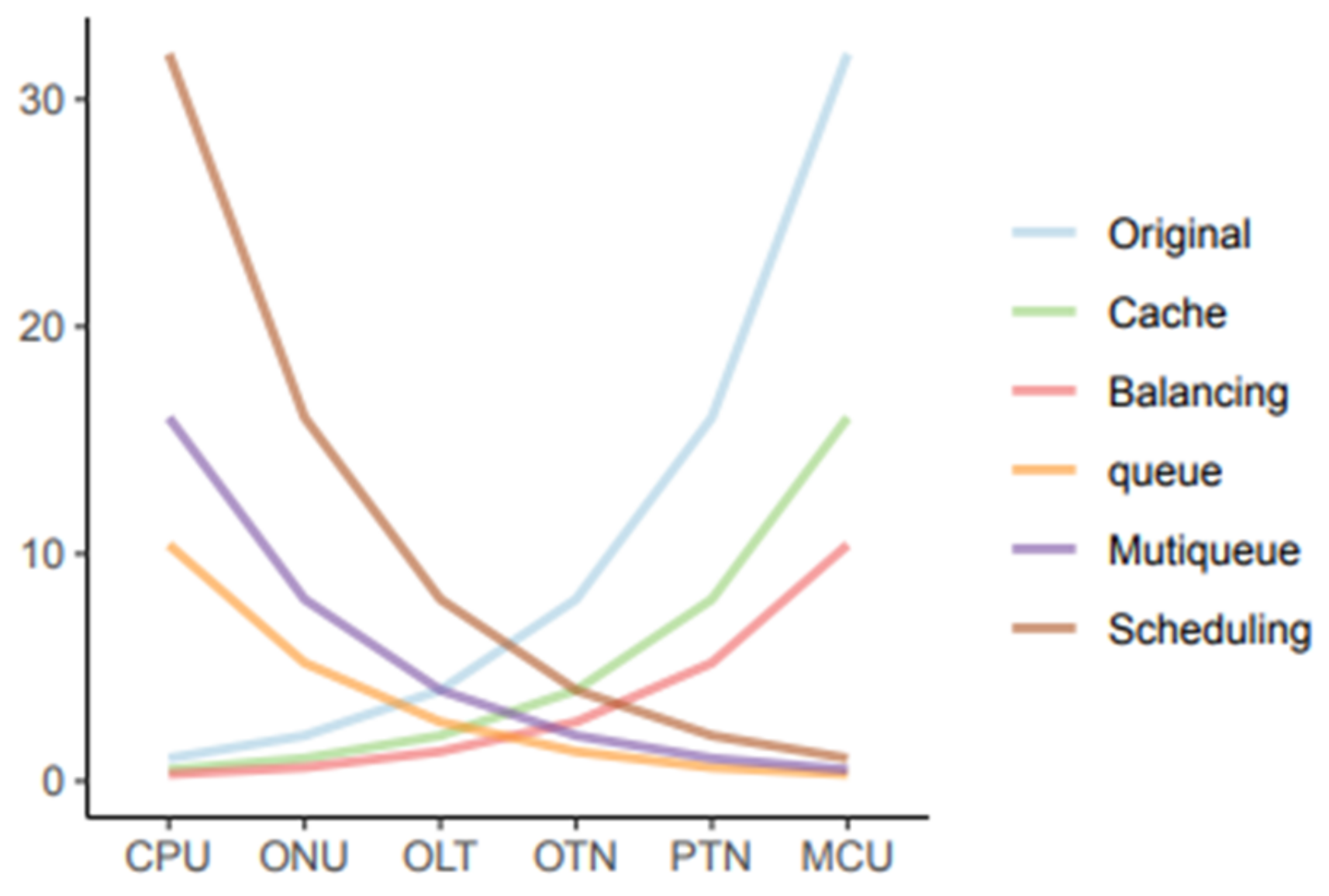
5.3. Analysis of the Results of Resource Optimization Experiments
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kamal, M.A.; Raza, H.W.; Alam, M.M.; Su’ud, M.M.; Sajak, A.B.A.B. Resource Allocation Schemes for 5G Network: A Systematic Review. Sensors 2021, 21, 6588. [Google Scholar] [CrossRef] [PubMed]
- Chien, W.; Huang, S.; Lai, C.F.; Chao, H. Resource management in 5g mobile networks: Survey and challenges. J. Inf. Process. Syst. 2020, 16, 896–914. [Google Scholar]
- Yu, A.; Yang, H.; Bai, W.; He, L.; Xiao, H.; Zhang, J. Leveraging Deep Learning to Achieve Efficient Resource Allocation with Traffic Evaluation in Datacenter Optical Networks. In Proceedings of the Optical Fiber Communication Conference, San Diego, CA, USA, 11–15 March 2018; pp. 1–3. [Google Scholar]
- Guo, P.; Wang, K.; Luo, A.-L.; Xue, M.-Z. Computational Intelligence for Big Data Analysis: Current Status and Future Prospect. J. Softw. 2015, 26, 3010–3025. [Google Scholar]
- Kang, B.; Jo, G.; Choo, H. A History-based Predictive Handover Scheme for Wireless Networks. J. Internet Technol. 2018, 19, 1487–1497. [Google Scholar]
- Wang, C.; Liang, C.; Yu, F.R.; Chen, Q.; Tang, L. Computation Offloading and Resource Allocation in Wireless Cellular Networks with Mobile Edge Computing. IEEE Trans. Wirel. Commun. 2017, 16, 4924–4938. [Google Scholar] [CrossRef]
- Zhou, Y.; Liu, H.; Pan, Z.; Tian, L.; Shi, J. Cooperative Multicast with Location Aware Distributed Mobile Relay Selection: Performance Analysis and Optimized Design. IEEE Trans. Veh. Technol. 2017, 66, 8291–8302. [Google Scholar] [CrossRef]
- Liu, H.; Cheng, Z.; Qian, L. The Three Primary Colors of Mobile Systems. IEEE Commun. Mag. 2016, 54, 15–21. [Google Scholar] [CrossRef]
- Kirantion, M. TSA: Tree-seed algorithm for continuous optimization. Expert Syst. Appl. 2015, 42, 6686–6698. [Google Scholar] [CrossRef]
- Chen, H.; Huang, L.; Chen, J.; Pao, T. Fuzzy Decision Load-balancing Algorithm for Cloud-based Terminal Services. J. Internet Technol. 2018, 19, 689–695. [Google Scholar]
- Ren, L.; Wang, W. An SVM-based collaborative filtering approach for Top-N web services recommendation. Future Gener. Comput. Syst. 2018, 78, 531–543. [Google Scholar] [CrossRef]
- Abaker, I.; Hashem, T.; Yaqoob, I.; Anuar, N.-B.; Mokhtar, S.; Gani, A.; Khan, S.-U. The rise of “big data” on cloud computing: Review and open research issues. Inf. Syst. 2015, 47, 98–115. [Google Scholar]
- Zeng, B.; Yang, S.; Yin, X. Robotic Relocalization Algorithm Assisted by Industrial Internet of Things and Artificial Intelligence. J. Internet Technol. 2020, 21, 1517–1530. [Google Scholar]
- Sanodiya, R.K.; Mathew, J.; Saha, S.; Thalakottur, M.D. A New Transfer Learning Algorithm in Semi-Supervised Setting. IEEE Access 2019, 7, 42956–42967. [Google Scholar] [CrossRef]
- Hoang, D.; Kang, H. Rolling element bearing fault diagnosis using convolutional neural network and vibration image. Cogn. Syst. Res. 2019, 53, 42–50. [Google Scholar] [CrossRef]
- Liu, X.; Meng, G.; Pan, C. Scene text detection and recognition with advances in deep learning: A survey. Int. J. Doc. Anal. Recognit. 2019, 22, 143–162. [Google Scholar] [CrossRef]
- Zhou, Z.H. Machine Learning (Chinese Edition); Tsinghua University Press: Beijing, China, 2016. [Google Scholar]




| Type | Settings |
|---|---|
| Processor | No less than 10 cores |
| Many-core general-purpose computing processor | Single-precision floating-point performance not less than 10 Tera FLOPS |
| Memory | No less than 64 GB |
| Client minimum | WebKit or Chromium-based browsers |
| Type | Technical Selection |
|---|---|
| Operating system | Windows, Linux |
| Application server | Flask-Server |
| Database | MySQL 8 |
| Library management | Anaconda |
| Integrated Development Environment | PyCharm |
| Data processing framework | NumPy, Pandas |
| AI development framework | TensorFlow 2 |
| AI development interface | Keras |
| Persistence | openpyxl, SQLAlchemy |
| Part Name | Parts Description |
|---|---|
| Web front | Asynchronous update interface developed based on JQuery and Semantic UI |
| System Settings Module | Set system parameters |
| data archiving module | Set data archiving parameters, mainly monitor folders, and perform data archiving |
| data extraction module | Select data types and traffic characteristics, and perform data extraction |
| Data cleaning module | Set data cleaning parameters and perform data cleaning |
| Data Enhancement Module | Set data augmentation parameters and perform data augmentation |
| Cluster Analysis Module | Perform cluster analysis, giving category candidates |
| Model training module | Set model training hyperparameters and perform training |
| Forecast display module | Graphical display of evaluation value, actual value, and predicted value |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tan, M.; Ba, R.; Li, G. Data Center Traffic Prediction Algorithms and Resource Scheduling. Sensors 2022, 22, 7893. https://doi.org/10.3390/s22207893
Tan M, Ba R, Li G. Data Center Traffic Prediction Algorithms and Resource Scheduling. Sensors. 2022; 22(20):7893. https://doi.org/10.3390/s22207893
Chicago/Turabian StyleTan, Min, Ruixuan Ba, and Guohui Li. 2022. "Data Center Traffic Prediction Algorithms and Resource Scheduling" Sensors 22, no. 20: 7893. https://doi.org/10.3390/s22207893
APA StyleTan, M., Ba, R., & Li, G. (2022). Data Center Traffic Prediction Algorithms and Resource Scheduling. Sensors, 22(20), 7893. https://doi.org/10.3390/s22207893







