An Order-Preserving Encryption Scheme Based on Weighted Random Interval Division for Ciphertext Comparison in Wearable Systems
Abstract
1. Introduction
1.1. Related Works
1.2. Our Contributions
- (1)
- Some existing OPES usually convert each character into the corresponding ASCII code while processing CSD. With such a simple method, the attackers can easily deduce the mapping between each pair of plaintext and ciphertext. For example, the most frequently used 52 English characters have only 52 ASCII codes; therefore, only by using the exhaustive method, the attackers can obtain the code book;
- (2)
- Some existing OPES encrypt each character into a float value, and then convert the float value to hexadecimal string or byte array with fixed size; therefore, the scheme is vulnerable to the size-based attacks. Once the size of ciphertext is obtained, attackers can easily deduce the size of plaintext and the content of the plaintext as well;
- (3)
- Most existing OPES are determined encryption schemes with one-to-one mapping between the ciphertext and plaintext. Moreover, how to balance the security and computation efficiency also need more attention. For example, to improve the security, the domain size should be increased; however, when the domain size is increased, the computation efficiency declines exponentially.
- (1)
- We designed a new character encoding method according to the occurrence frequency in preprocess phase. Based on this method, the CSD is converted into ND based on Basic Multilingual Plane ((BMP) Unicode from U+0000 to U+FFFF);
- (2)
- We proposed a weighted random interval division algorithm (WRID). This algorithm guarantees that the partition ratio of each interval is random and that the distribution of division ratios is closed to the predetermined weight value. The division ratio refers to the size of the divided sub-intervals;
- (3)
- We constructed an order-preserving random interval tree (OPRIT) based on WRID. Based on OPRIT, we implemented the numeric string encryption scheme, which divides the numeric string into segments and maps each segment into the cryptogram space and can achieve the IND-OCPA security strength.
2. Our Proposed Solution
2.1. The Pre-Process Method of Character Strings
- (1)
- The first one is order-preserving, which means that the converted data should preserve the order of original data;
- (2)
- The second one is reversibility, so that we are able to retrieve the original data according to the converted data.
- (1)
- Codes from “0000” to “007F” cover the basic Latin characters, including the English characters, Arabic numerals, and symbols. They are frequently used in the English texts. At the same time, the prefix “00” makes converted ND to be periodic. Therefore, we deleted the same prefix and use their ASCII code as the change code;
- (2)
- Codes between “0080” to “3FFF” cover the native characters and other types of characters. The native characters include the expanded Latin characters, Greek characters, Hebrew characters, Arabic characters, etc. Other types of characters include mathematical operators, square elements, etc. These characters often appear in specialized texts only. So, in this paper, we added a prefix “8” to preserve the order;
- (3)
- CJK characters refer to the characters in Chinese, Japanese, and Korean, whose occurrence frequency is high. In this paper, we did not add any additional prefix for these characters but transform them to the interval between “9000” and “EFFF” to preserve order as well;
- (4)
- The code between “A000” to “FFFF” refers to other East Asian characters, diacritics characters, and reserved characters. We added a prefix “F” to the original code to preserve order.
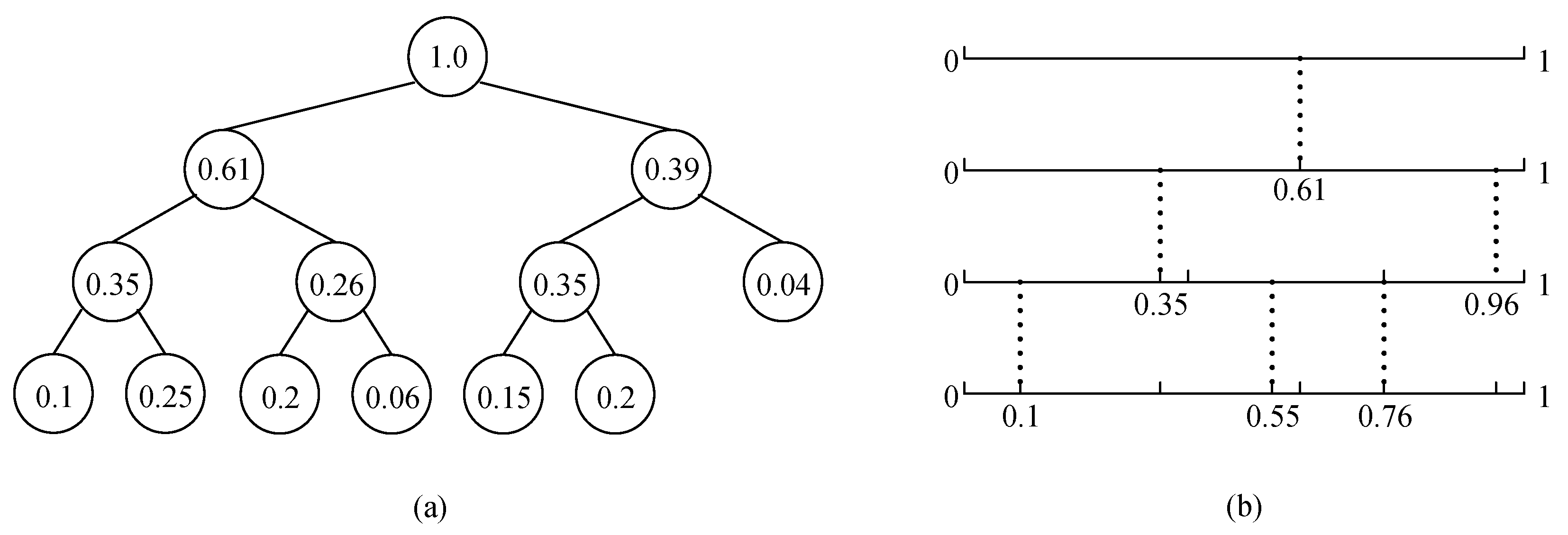
2.2. The Weighted Random Interval Division Algorithm (WRID)
- (1)
- For a single interval division, each interval must be randomly divided in WRID;
- (2)
- After multiple interval divisions, the expectation of division percentage for each interval must be close to the predetermined weight value.
- (1)
- The number of leaf nodes in the weighted tree equals the number of sub-intervals;
- (2)
- The weight of the i-th leaf node equals to the proportion of the i-th sub-interval in the original interval when dividing the interval with fixed ratio.
2.2.1. The Design of WRID Algorithm
| Algorithm 1: The weighted random interval division algorithm (WRID) | |
| Input Output | I = [α, β), sd, m Im |
| Step1 | Initial node n as the root node of the weighted tree, assign nextLeft (sd) to sdl and nextRight (sd) to sdr. |
| Step2 | If n is leaf node, assign [α,β) to Im and exit this algorithm; otherwise, go to step 3 |
| Step3 | For the node n (weight is w), its children nodes are nl (left child node, weight is wl) and nr (right child node, weight is wr). Constructing the independent uniform random variable Rl (sdl) and Rr (sdr) in the domain [0,1). Then computing x = (wl * rl)/(wl * rl + wr * rr), where rl and rr are two random number generated according to Rl (sdl) and Rr (sdr). |
| Step4 | If the m-th leaf node of weighted tree is in the left children tree of n, then computing as follows: β = α + (β-α) * x, n = nl, sdl = nextleft (sdl), sdr = nextLeft (sdr). Then go to step 2. |
| Step5 | If the m-th leaf node of weighted tree is in the right children tree of n, then computing as follows: α = α + (β-α) * x, n = nr, sdl = nextRight (sdl), sdr = nextRight (sdr). Then go to step 2. |
2.2.2. The Randomness of Intervals in WRID
- (1)
- Compute the weight (W) according to the generated samples;
- (2)
- Divide the definition domain repeatedly for 1000 times by using WRID with two different seeds, and taking the lower boundary value of each sub-interval as the random variable;
- (3)
- Calculate R composed by the lower boundary values.
- (1)
- Divide the definition domain repeatedly for 1000 times by using WRID, and taking the length of each sub-interval as the random variable;
- (2)
- Calculate Vσ of the set composed by the length of each sub-interval.
2.2.3. The Expectations of Interval Division Percentage in WRID
2.3. The Encryption of Numerical String Based on WRID and OPRIT
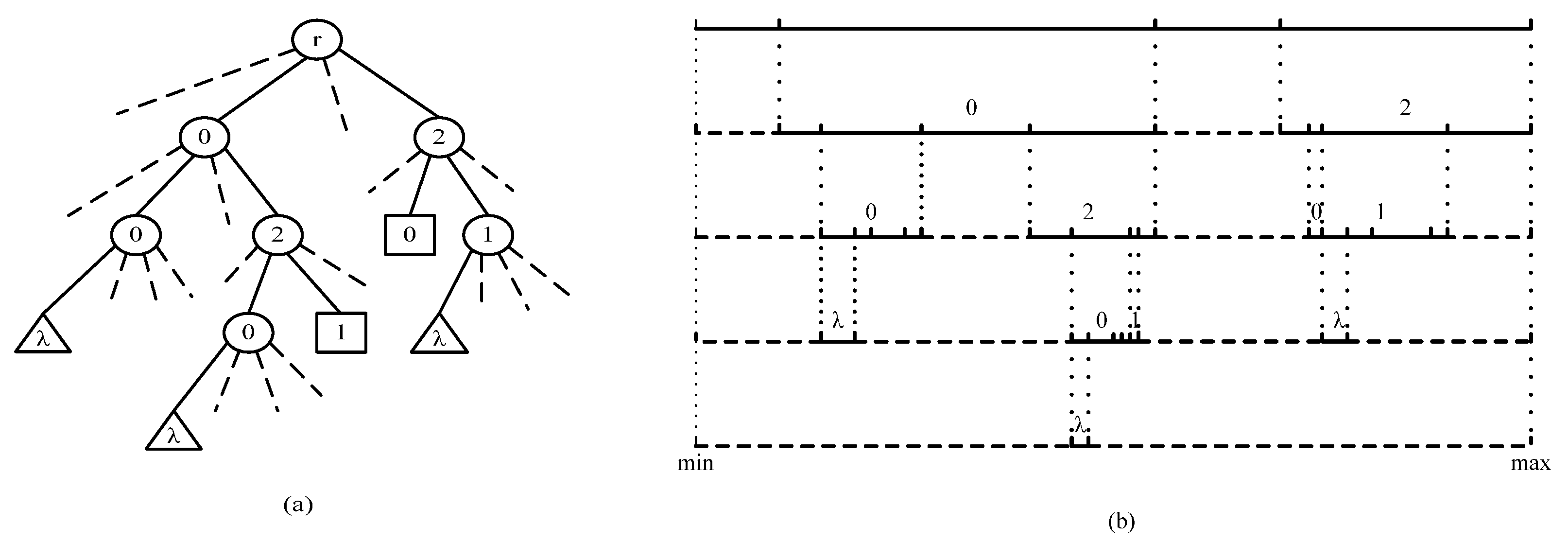
2.3.1. The Order-Preserving Random Interval Tree (OPRIT)
2.3.2. The Encryption of Numerical String Using OPRIT
- (1)
- The encryption keys of WRID-OPES
- (2)
- The encryption processes of numerical string using OPRIT
| Algorithm 2: The encryption processes of numerical string using OPRIT and WRID | |
| Input Output | Userkey, DD, N, ns Ciphertext string: ci |
| Step1 | Dividing uniformly the definition domain DD = [min,max) into N non-intersect buckets J(1),…J(k),…J(N). The size of each bucket is (max-min)/N; |
| Step2 | Adding the termination symbol λ in the last of numerical string ns (e.g., ns + λ→ns). Then initial ci into a null string. |
| Step3 | Initialing the root node interval and seed: I = DD, seedp = seed (Userkey). |
| Step4 | Obtaining the first unprocessed numerical character m from ns, where m∈{λ, 0, … 9, A,…,F}. |
| Step5 | Using Im = WRID (I, seedp) to obtain Im, and assign Im to I, e.g., Im→I. |
| Step6 | Computing the ciphertext r from Im using seedp, and converting the r to a numerical string r’ and appended to the last of ciphertext ci, (e.g., ci + r’→ci). |
| Step7 | If there is I⊆J(k) (k = 1,…,N), which means that the algorithm is processing the undivided value node, then, go to step 3. |
| Step8 | If there is m = λ, it means that the end of ns has reached, then, output ci and exit the algorithm. |
| Step9 | Computing the new seed seedp for the next division using m and seedp, e.g., seedp = Seed (seedp, m). Go to step 4 |
2.4. The Encryption and Decryption of Character String in WRID-OPES
| Algorithm 3: The encryption scheme of WRID-OPES | |
| Input Output | Userkey, DD, N, PS = {ps1,ps2,…psk,...,psλ} Ciphertext string: CS |
| Step1 | Using the pre-process method of character String in Section 2.1, encoding the {ps1,ps2,…psk,...,psλ} into the numerical string set {ns1,ns2,…nsk,...nsλ} where the numerical value is hexadecimal and k is the number of strings. |
| Step2 | Counting the occurrence times of each hexadecimal numerical character 0 to F in {ns1,ns2,…nsk,...,nsλ}. The occurrence times of λ is defined as the number of sub-string in {ns1,ns2,…nsk,...,nsλ}. Then we can obtain the occurrence frequency weight W = (wλ,w0,…,wF). |
| Step3 | Generating the main seed seedp according to {Userkey, DD, N}. |
| Step4 | Appending W to {Userkey, DD, N} as the decryption Keys. |
| Step5 | Initialing the ciphertext set: ∅→CS. |
| Step6 | Constructing the weighted tree according to W. |
| Step7 | If all strings be processed in {ns1,ns2,…nsk,...,nsλ}, then we output CS and the decryption Keys, and exit the algorithm, otherwise go to step 8. |
| Step8 | Obtain an unprocessed string nsk from {ns1,ns2,…nsk,…,nsλ}. Using Algorithm 2 to encrypt this numerical string and obtain the ciphertext csi. Appending csi to the ciphertext set CS, e.g., CS = CS + {csi} |
| Step9 | Go to step 6. |
| Algorithm 4: The decryption scheme of WRID-OPES | |
| Input Output | Userkey, DD, N, CS, W Plaintext string: PS |
| Step1 | Obtaining W from the decryption Keys. |
| Step2 | Generating the main seed seedp according to {Userkey, DD, N, W}. |
| Step3 | Initialing the plain text set: ∅→PS. |
| Step4 | Constructing the weighted tree according to W |
| Step5 | If all strings be processed in CS, then we output PS and exit the algorithm. |
| Step6 | Obtain the unprocessed string csi from CS, CS = CS − {csi} |
| Step7 | Using the Algorithm 2 to decrypt csi and obtain the plaintext string psi, appending psi to the plaintext string set PS, e.g., PS = PS + {psi}. |
3. Experiments and Evaluations
3.1. The Efficiency Tests
3.1.1. The Tests of Computing Time Costs
- (1)
- The complexity of WRID-OPES.
- (2)
- The complexity of OPES.
- (3)
- The complexity of LazySample.
3.1.2. The Tests of Storage Spaces
3.2. The Security Evaluations of WRID-OPES
3.2.1. The Security Analysis of WRID-OPES
3.2.2. The Analysis with Exhaustive Attacks
3.2.3. The Attacks with Statistical Analysis
3.3. Discussion on Related Works
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Krishna, P.S.; Malarkodi, B. A Secured Healthcare Model for Sensor Data Sharing With Integrated Emotional Intelligence. IEEE Sens. J. 2022, 22, 16306–16313. [Google Scholar]
- Tang, W.; Ren, J.; Deng, K.; Zhang, Y. Secure Data Aggregation of Lightweight E-Healthcare IoT Devices With Fair Incentives. IEEE Internet Things J. 2019, 6, 8714–8726. [Google Scholar] [CrossRef]
- Agrawal, R.; Kiernan, J.; Srikant, R.; Xu, Y. Order preserving encryption for numeric data. In Proceedings of the 2004 ACM SIGMOD International Conference on Management of Data-SIGMOD’04, Paris, France, 13–18 June 2004; pp. 563–574. [Google Scholar]
- Boldyreva, A.; Chenette, N.; Lee, Y.; O’Neill, A. Order-preserving symmetric encryption. In Advances in Cryptology—Proceedings of the EUROCRYPT 2009, 28th Annual International Cryptology Conference, Cologne, Germany, 26–30 April 2009; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; pp. 224–241. [Google Scholar]
- Boldyreva, A.; Chenette, N.; O’Neill, A. Order-preserving encryption revisited: Improved security analysis and alternative solutions. In Advances in Cryptology—Proceedings of the CRYPTO 2011: 31st Annual Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2011; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2011; pp. 578–595. [Google Scholar]
- Kadhem, H.; Amagasa, T.; Kitagawa, H. MV-OPES: Multivalued-Order Preserving Encryption Scheme: A Novel Scheme for Encrypting Integer Value to Many Different Values. IEICE Trans. Inf. Syst. 2010, 93, 2520–2533. [Google Scholar] [CrossRef]
- Liu, D.; Wang, S. Nonlinear order preserving index for encrypted database query in service cloud environments. Concurr. Comput. Pract. Exp. 2013, 25, 1967–1984. [Google Scholar] [CrossRef]
- Yum, D.H.; Kim, D.S.; Kim, J.S.; Lee, P.J.; Hong, S.J. Order-preserving encryption for non-uniformly distributed plaintexts. Lect. Notes Comput. Sci. 2012, 7115, 84–97. [Google Scholar]
- Popa, R.A.; Li, F.H.; Zeldovich, N. An ideal-security protocol for order-preserving encoding. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; pp. 463–477. [Google Scholar]
- Seungmin, L.; Donghyeok, L.; Taekyong, N.; Sehun, K. Chaotic order preserving encryption for efficient and secure queries on databases. IEICE Trans. Inf. Syst. 2009, 92, 2207–2217. [Google Scholar]
- Martinez, S.; Miret, J.M.; Tomas, R.; Valls, M. Securing Databases by using Diagonal-based Order Preserving Symmetric Encryption. Appl. Math. Inf. Sci. 2014, 8, 2085–2094. [Google Scholar] [CrossRef]
- Lee, H.; Song, Y.; Chang, J.W. GOPES: Group Order-Preserving Encryption Scheme Supporting Query Processing over Encrypted Data. J. Inf. Process. Syst. 2018, 14, 1087–1101. [Google Scholar]
- Quan, H.Y.; Wang, B.Y.; Zhang, Y.Q. Efficient and Secure Top-k Queries with Top Order-Preserving Encryption. IEEE Access 2018, 6, 31525–31540. [Google Scholar] [CrossRef]
- Liu, Z.L.; Chen, X.F.; Yang, J. New order preserving encryption model for outsourced databases in cloud environments. J. Netw. Comput. Appl. 2016, 59, 198–207. [Google Scholar] [CrossRef]
- Florian, K. Frequency-Hiding Order-Preserving Encryption. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security (CCS), Denver, CO, USA, 12–16 October 2015; pp. 656–667. [Google Scholar]
- Yang, C.; Zhang, W.M.; Yu, N.H. Semi-order preserving encryption. Inf. Sci. 2017, 387, 266–279. [Google Scholar] [CrossRef]
- Li, K.; Zhang, W.M.; Yang, C. Security Analysis on One-to-Many Order Preserving Encryption-Based Cloud Data Search. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1918–1926. [Google Scholar]
- Kim, M.; Park, J.H.; Roh, D. Comment on the Security of an Order-Preserving Encryption Scheme Using Pseudo-Random Function. IEICE Trans. Commun. 2016, E99B, 2108–2111. [Google Scholar] [CrossRef]
- Shen, N.; Yeh, H.; Sun, H.M.; Chen, C.M. A Practical and Secure Stateless Order Preserving Encryption for Outsourced Databases. In Proceedings of the IEEE 26th Pacific Rim International Symposium on Dependable Computing (PRDC 2021), Electronic Network, Perth, Australia, 1–4 December 2021; pp. 133–142. [Google Scholar]
- Han, T.S.; Hoshi, M. Interval algorithm for random number generation. IEEE Trans. Inf. Theory 1997, 43, 599–611. [Google Scholar]
- Xiao, L.J.; Yen, I.L. A Note for the Ideal Order-Preserving Encryption Object and Generalized Order-Preserving Encryption. Available online: https://eprint.iacr.org/2012/350 (accessed on 19 March 2022).
- Teranishi, I.; Yung, M.; Malkin, T. Order-Preserving Encryption Secure Beyond One-Wayness. In Advances in Cryptology—Proceedings of the ASIACRYPT 2014, 20th Annual International Conference on the Theory and Application of Cryptology and Information Security, Kaoshiung, Taiwan, 7–11 December 2014; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8874, pp. 42–61. [Google Scholar]





| Character Type | Frequency | Original Code | Changed Code |
|---|---|---|---|
| Basic Latin characters | High | 0000~007F | 00~7F |
| Native characters and other types of characters | Low | 0080~3FFF | 80080~83FFF |
| Chinese, Japanese, and Korean (CJK) characters | High | 4000~9FFF | 9000~EFFF |
| Other East Asian characters | Low | A000~FFFF | FA000~FFFFF |
| ID of Sub-Intervals | Correlation Coefficient R | Standard Deviation σ (108) | Expectation E(X) (108) | Variation Coefficient Vσ (%) |
|---|---|---|---|---|
| 0 | / | 7.9818 | 3.9719 | 200.96 |
| 1 | 0.0449 | 5.7371 | 4.1860 | 137.05 |
| 2 | 0.0195 | 6.1134 | 4.5972 | 132.98 |
| 3 | 0.0061 | 4.7926 | 4.7304 | 101.32 |
| 4 | −0.0133 | 10.1264 | 11.5040 | 88.03 |
| 5 | 0.0228 | 10.1896 | 9.2981 | 109.59 |
| 6 | 0.0330 | 6.8511 | 7.6025 | 90.12 |
| 7 | 0.0403 | 9.9952 | 8.9188 | 112.07 |
| 8 | −0.0034 | 9.3557 | 7.6329 | 122.57 |
| 9 | −0.0145 | 5.5705 | 4.8888 | 113.94 |
| 10 | −0.0163 | 6.6836 | 3.9849 | 167.72 |
| 11 | −0.0135 | 7.2979 | 5.2302 | 139.53 |
| 12 | −0.0185 | 6.4425 | 5.0115 | 128.56 |
| 13 | −0.0275 | 4.9870 | 4.9973 | 99.79 |
| 14 | −0.0315 | 5.7014 | 4.8240 | 118.19 |
| 15 | −0.0583 | 7.0227 | 5.2525 | 133.70 |
| 16 | −0.0455 | 4.5780 | 3.3692 | 135.88 |
| Character Type | Plaintext Length | Ciphertext Length in Hexadecimal | MER in Hexadecimal Encoding | Ciphertext Length in Unicode | MER in Unicode Encoding |
|---|---|---|---|---|---|
| English | 20 | 63 | 3.15 | 15 | 0.75 |
| English | 100 | 282 | 2.82 | 70 | 0.7 |
| English | 1024 | 2812 | 2.75 | 696 | 0.68 |
| Chinese | 20 | 145 | 7.25 | 36 | 1.8 |
| Chinese | 100 | 694 | 6.94 | 174 | 1.74 |
| Chinese | 1024 | 7026 | 6.86 | 1775 | 1.73 |
| Scheme | Computing Costs | Storage Costs | Security Level | Data Types |
|---|---|---|---|---|
| Agrawal04 [3] | Medium | Middle | Low | Integer |
| Boldyreval09 [4] | High | Low | Medium | Integer |
| Liu13 [7] | Low | Middle | Low | Integer, Float |
| Popa13 [9] | High | High | High | All data Types |
| Liu16 [14] | Middle | Middle | Middle | Integer, Float |
| Our Scheme | Low | Middle | High | All data Types |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gui, R.; Yang, L.; Gui, X. An Order-Preserving Encryption Scheme Based on Weighted Random Interval Division for Ciphertext Comparison in Wearable Systems. Sensors 2022, 22, 7950. https://doi.org/10.3390/s22207950
Gui R, Yang L, Gui X. An Order-Preserving Encryption Scheme Based on Weighted Random Interval Division for Ciphertext Comparison in Wearable Systems. Sensors. 2022; 22(20):7950. https://doi.org/10.3390/s22207950
Chicago/Turabian StyleGui, Ruowei, Liu Yang, and Xiaolin Gui. 2022. "An Order-Preserving Encryption Scheme Based on Weighted Random Interval Division for Ciphertext Comparison in Wearable Systems" Sensors 22, no. 20: 7950. https://doi.org/10.3390/s22207950
APA StyleGui, R., Yang, L., & Gui, X. (2022). An Order-Preserving Encryption Scheme Based on Weighted Random Interval Division for Ciphertext Comparison in Wearable Systems. Sensors, 22(20), 7950. https://doi.org/10.3390/s22207950






