Design and Analysis of Area and Energy Efficient Reconfigurable Cryptographic Accelerator for Securing IoT Devices
Abstract
:1. Introduction
- At tier1 of the functional configurability, the proposed reconfigurable cryptographic accelerator can perform either block ciphers (DES/AES/SM4) alone, or hash functions (SHA-1/SHA-256/SM3) alone or both block cipher and hash function simultaneously. This is achieved by having two separate unified reconfigurable engines (i.e., one for the block ciphers, and another for the hash functions), that account for latency optimization for actual application scenarios including authentication and encryption/decryption processes.
- At tier2 of the datapath configurability, the datapath for the block ciphers and for the hash functions are optimized. This is achieved by first having a detailed and comprehensive algorithmic analysis of both the block ciphers and hash functions in terms of basic algorithm structures and common cryptographic operators to guide efficient reconfigurable architecture design, which provides a practical design reference for the reconfigurable hardware design of cryptographic algorithms. Through this analysis, in the proposed design implementation, the datapath for the block ciphers is optimized to have a 33.65% smaller area, and the datapath for the hash functions a 56.18% smaller area.
- At tier3 of the S-Box configurability, a reconfigurable S-Box module for AES and SM4 is designed based on the composite Galois field (GF) GF(((22)2)2) instead of GF(28), which significantly reduces hardware overhead by more than 30% as compared to the conventional implementations of LUTs.
2. Algorithm Analysis of Block Ciphers and Hash Functions
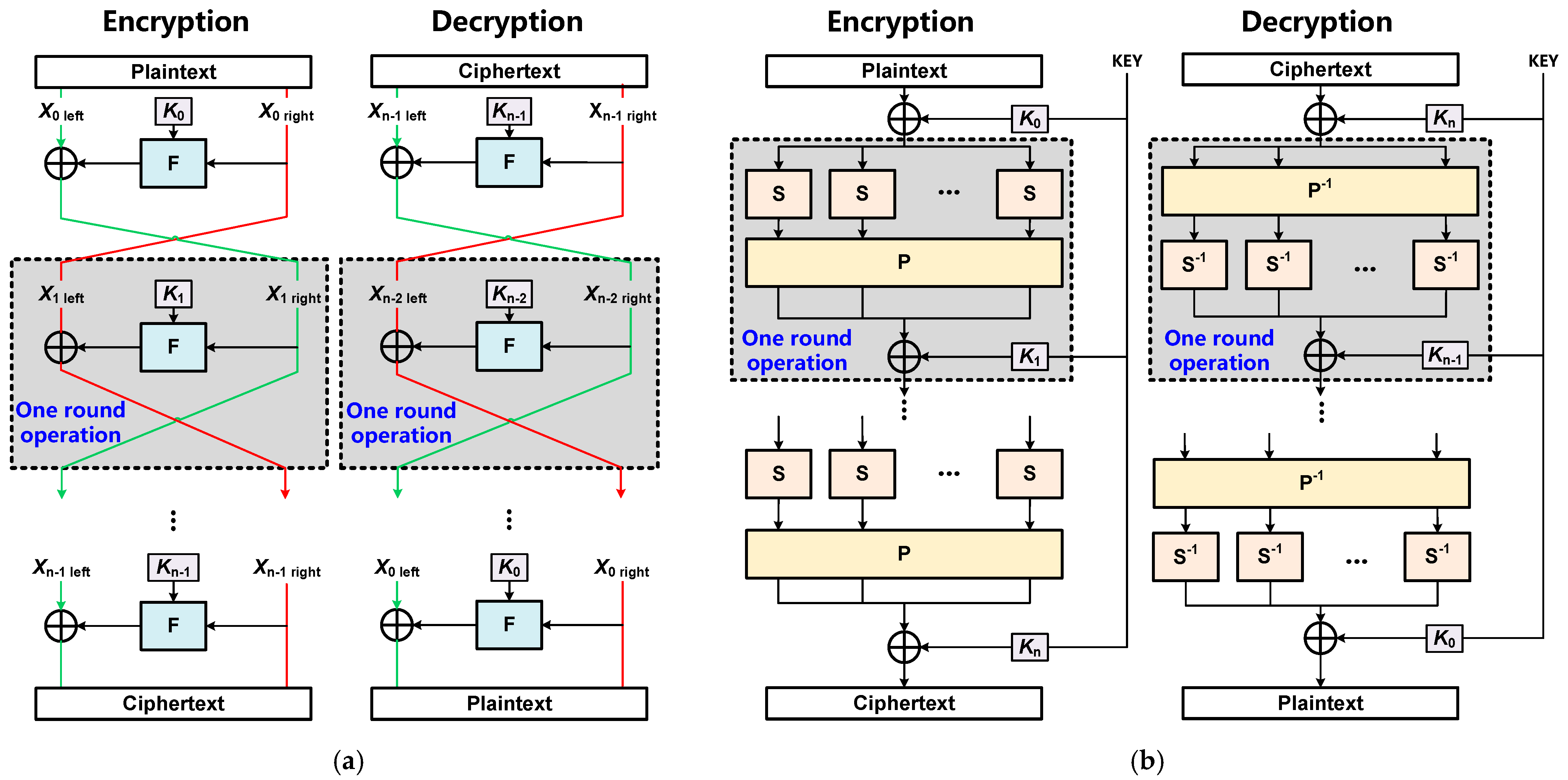
2.1. Review of Cryptographic Algorithms in IoT Security Applications
2.2. Introduction of Major Block Ciphers and Hash Functions
2.2.1. Algorithm Analysis of Major Block Ciphers
2.2.2. Algorithm Analysis of Major Hash Functions
2.2.3. Algorithm Comparison between Block Ciphers and Hash Functions
- The principle of the block ciphers and hash functions is fundamentally different. From the processing perspective. Block ciphers work in two ways that are reversible, i.e., data encryption and decryption, while hash functions are irreversible that convert original data into message digest. From the application perspective, block ciphers are used to secure the data from the reach of third parties, while hash functions help protect the integrity of the information.
- The structure of round operations in the two cryptographic primitives is different. The round operation structure of the block cipher is based on Feistel or SP, while the round operation structure of hash functions is Merkle–Damgård based on one-way compression. The different structures of the two cryptographic primitives make the hardware data path quite different, which raises a great challenge to the development of a unified data path for efficient reconfigurable hardware design.
- The basic operators in the two cryptographic primitives are different. The key operator of block ciphers is an S-Box performing data substitution, while the key operators of hash functions are logical functions (i.e., Ft, Ch, Ma, FFt, GGt). The different basic operators actually impede the reconfigurable design of the two kinds of primitives.
3. Hardware Architecture of Proposed Reconfigurable Cryptographic Accelerator
3.1. Reconfigurable Cipher Unit
- In the DES encryption/decryption mode using the logical operators highlighted by red boxes, eight data iteration register files (X0–X7) are used to store the 64-bit plaintext. The data path is configured to use the extended permutation module, 48-bit XOR logic, eight S-Boxes, P-Box permutation module and the final 32-bit XOR logic, which are all dedicated to DES due to the distinct difference of operators between DES and AES/SM4.
- In the AES encryption mode using the logical operators highlighted by green boxes, sixteen data iteration register files (X0–X15) are used to store the 128-bit plaintext. The data path is configured to use the sixteen reconfigurable S-Boxes, circular shift module, MixColum module and the final 128-bit XOR logic to realize SubBytes, ShiftRows, MixColumns and AddRoundKey, respectively. In AES decryption mode, there are two differences from the AES encryption mode. First, the mode of the sixteen reconfigurable S-Boxes and circular shift module are changed to the AES decryption mode. Second, the MixColum module is replaced by the InvMixColum module according to the AES standard. Note that the modules, including circular shift, MixColum and InvMixColum, are dedicated to the AES mode as there are no such operations in the other two block ciphers.
- In the SM4 encryption/decryption mode using the logical operators highlighted by blue boxes, and as with the AES, sixteen data iteration register files (X0–X15) in light blue color are reused to store the 128-bit plaintext. The data path is configured to use the 32-bit XOR logic, four reused reconfigurable S-Boxes, linear transformation module and the final 32-bit XOR logic. Note that the linear transformation module is dedicated to the SM4 mode.
3.2. Reconfigurable Hash Unit
- The preprocessing module mainly performs the original message padding to assure that the input data block is a multiple of 512 bits.
- The message expansion module expands each 512-bit input data block into a predefined round number of words, i.e., round number × Wt, which is 80 × 32 bits in SHA-1 and 64 × 32 bits in SHA-256/SM3.
- The reconfigurable round function iteration module with a unified compressed data path performs 80/64/64 round operations to achieve the one-way compression function f of SHA-1/SHA-256/SM3 for one 512-bit input data block. As a result, the final hash value is obtained after all the 512-bit data blocks have been computed.
- The constant Kt storage module stores the constant Kt used for each round operation.
- The iteration register files (A, B, ···, H) store the initial IV in the first round operation and intermediate value obtained from each round operation.
- The finite state machine (FSM) control logic controls the reconfigurable hash unit mainly by generating control signals from counters to control MUXes for realizing reconfigurable computation of the three algorithms.
- For the SM3 mode, the hardware data path is implemented by direct mapping from the signal flow data path shown in Figure 4d. Specifically, part 1 calculates the intermediate value SS1 and SS2 by using constant Kt and values in input register files A and E. At the same time, part 2 calculates the intermediate value TT2 by using the expanded value Wt, the SS1 from part 1, and values in input register files E, F, G and H. Part 3 calculates the value TT1 by using SS2 from part 1, the expanded value Wt’ and values in input register files A, B, C and D.
- For the SHA-256 mode, three carry save adders (CSAs) in the light blue color are reused to calculate the intermediate value T1 in part 2. Another CSA and one ADD in light blue color are reused to calculate the value in output register file E in part 2. Two extra CSAs and one ADD in light blue color are also reused to calculate the value in output register file A in part 3. In summary, there are six CSAs and two ADDs reused in the SHA-256 mode. The other logic operators are designed to be dedicated to SHA-256 as they are difficult to be reused for reconfigurable design.
- For the SHA-1 mode, similar to the SHA-256 mode, three CSAs in light blue color are reused to calculate the intermediate value T in part 2. Two extra CSAs and one ADD in light blue color are reused to calculate the value in output register file A in part 3. In summary, there are five CSAs and one ADD reused in the SHA-1 mode. The other logic operators are also designed to be dedicated to SHA-1 as they are difficult to be reused for reconfigurable design.
4. Implementation Results and Discussions
4.1. FPGA Implementation and Evaluation
4.2. ASIC Implementation and Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Conflicts of Interest
References
- Lin, J.; Yu, W.; Zhang, N.; Yang, X.; Zhang, H.; Zhao, W. A Survey on Internet of Things: Architecture, Enabling Technologies, Security and Privacy, and Applications. IEEE Internet Things J. 2017, 4, 1125–1142. [Google Scholar] [CrossRef]
- Yang, Y.; Wu, L.; Yin, G.; Li, L.; Zhao, H. A Survey on Security and Privacy Issues in Internet-of-Things. IEEE Internet Things J. 2017, 4, 1250–1258. [Google Scholar] [CrossRef]
- Buenrostro, E.; Cyrus, D.; Le, T.; Emamian, V. Security of IoT Devices. J. Cyber Secur. Technol. 2018, 2, 1–13. [Google Scholar] [CrossRef]
- Bhuiyan, M.N.; Rahman, M.M.; Billah, M.M.; Saha, D. Internet of Things (IoT): A Review of Its Enabling Technologies in Healthcare Applications, Standards Protocols, Security, and Market Opportunities. IEEE Internet Things J. 2021, 8, 10474–10498. [Google Scholar] [CrossRef]
- Chaves, R.; Kuzmanov, G.; Sousa, L.; Vassiliadis, S. Cost-Efficient SHA Hardware Accelerators. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2008, 16, 999–1008. [Google Scholar] [CrossRef]
- Ao, T.; He, Z.; Rao, J.; Dai, K.; Zou, X. A Compact Hardware Implementation of SM3 Hash Function. In Proceedings of the 2014 IEEE 13th International Conference on Trust, Security and Privacy in Computing and Communications, Beijing, China, 24–26 September 2014; pp. 846–850. [Google Scholar]
- Nishikawa, N.; Iwai, K.; Kurokawa, T. High-performance Symmetric Block Ciphers on Multicore CPU and GPUs. Int. J. Netw. Comput. 2012, 2, 251–268. [Google Scholar] [CrossRef] [Green Version]
- Mathew, S.; Satpathy, S.; Suresh, V.; Anders, M.; Kaul, H.; Agarwal, A.; Hsu, S.; Chen, G.; Krishnamurthy, R. 340 mV–1.1 V, 289 Gbps/W, 2090-gate NanoAES Hardware Accelerator with Area-optimized Encrypt/decrypt GF(24)2 Polynomials in 22 nm Tri-gate CMOS. In Proceedings of the 2014 Symposium on VLSI Circuits Digest of Technical Papers, Honolulu, HI, USA, 10–13 June 2014; pp. 1048–1058. [Google Scholar]
- Mathew, S.; Sheikh, F.; Agarwal, A.; Kounavis, M.; Hsu, S.; Kaul, H.; Anders, M.; Krishnamurthy, R. 53 Gbps Native GF(24)2 Composite-Field AES-Encrypt/Decrypt Accelerator for Content-Protection in 45 nm High-Performance Microprocessors. IEEE J. Solid-State Circuits 2011, 46, 767–776. [Google Scholar] [CrossRef]
- Liu, L.; Wang, B.; Deng, C.; Zhu, M.; Yin, S.; Wei, S. Anole: A Highly Efficient Dynamically Reconfigurable Crypto-Processor for Symmetric-Key Algorithms. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2018, 37, 3081–3094. [Google Scholar] [CrossRef]
- Deng, C.; Wang, B.; Liu, L.; Zhu, M.; Wu, Y.; Li, H.; Yin, S.; Wei, S. A 60 Gb/s-Level Coarse-Grained Reconfigurable Cryptographic Processor with Less Than 1-W Power. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 375–379. [Google Scholar] [CrossRef]
- Du, Y.; Li, W.; Dai, Z.; Nan, L. PVHArray: An Energy-Efficient Reconfigurable Cryptographic Logic Array with Intelligent Mapping. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2020, 28, 1302–1315. [Google Scholar] [CrossRef]
- Nyberg, K. Generalized Feistel Networks. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Kyongju, Republic of Korea, 3–7 November 1996; pp. 91–104. [Google Scholar]
- Kam, J.B.; Davida, G.I. Structured Design of Substitution-Permutation Encryption Networks. IEEE Trans. Comput. 1979, 28, 747–753. [Google Scholar] [CrossRef]
- Coron, J.S.; Dodis, Y. Merkle-Damgård revisited: How to construct a hash function. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; pp. 430–448. [Google Scholar]
- Liu, Y. The Design of Reconfigurable AES/SM4 IP Core against Side-Channel Attack. Master’s Thesis, Nanjing University of Aeronautics and Astronautics, Nanjing, China, 2017. [Google Scholar]
- Hao, L.; Wu, L.; Zhang, X. Design and Implementation of SM4 Block Cipher Based on Composite Field. Microelectron. Comput. 2015, 32, 16–20. [Google Scholar]
- Canright, D. A Very Compact S-Box for AES. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Edinburgh, UK, 29 August–1 September 2005; pp. 441–455. [Google Scholar]
- Energizer CR1220 Lithium Coin Battery Product Datasheet. Available online: https://data.energizer.com/pdfs/cr1220.pdf (accessed on 18 November 2022).
- Myers, J.; Savanth, A.; Gaddh, R.; Howard, D.; Prabhat, P.; Flynn, D. A Subthreshold ARM Cortex-M0+ Subsystem in 65 nm CMOS for WSN Applications with 14 Power Domains, 10T SRAM, and Integrated Voltage Regulator. IEEE J. Solid-State Circuits 2016, 51, 31–44. [Google Scholar]
- Zhou, J.; Wang, C. An Ultra-Low Power Turning Angle Based Biomedical Signal Compression Engine with Adaptive Threshold Tuning. Sensors 2017, 17, 1809. [Google Scholar] [CrossRef] [Green Version]
- Shan, W.; Fu, X.; Xu, Z. A Secure Reconfigurable Crypto IC with Countermeasures against SPA, DPA, and EMA. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2015, 34, 1201–1205. [Google Scholar] [CrossRef]












| Algorithms | Security Protocols | Applicable Countries/Regions | Organization | Typical Application Example | |
|---|---|---|---|---|---|
| Block Cipher | DES | IPsec/SSL/TLS | USA/CHN/EUR | NIST | Ethernet |
| AES | Most communication standards/protocols | USA/CHN/EUR | NIST | WLAN/ZigBee/Bluetooth/5G/LTE/Ethernet | |
| SM4 | IPsec/TLS/DTLS/SSL/WAPI | CHN | SCA | WLAN/Ethernet | |
| Hash function | SHA-1 | IPsec/SSL/TLS | USA/CHN/EUR | NIST | RFID/Ethernet |
| SHA-256 | Most communication standards/protocols | USA/CHN/EUR | NIST | WLAN/Bluetooth/5G/LTE/Ethernet | |
| SM3 | IPsec/SSL/TLS | CHN | SCA | WLAN/Ethernet |
| Block Ciphers | Round Operation Structure Type | Key Operators in Round Operation |
|---|---|---|
| DES | Feistel | XOR/S-Box/Permutation |
| AES | SP | XOR/S-Box/Shift/Column Mix |
| SM4 | Feistel | XOR/S-Box/Shift |
| Key Operators | Input/Output Bit-Widths | Number of Operators Used in One Round Operation of Block Cipher | ||
|---|---|---|---|---|
| DES | AES | SM4 | ||
| Permutation | 64-56 bits | 1 | - | - |
| 56-48 bits | 1 | - | - | |
| 32-48 bits | 1 | - | - | |
| 32-32 bits | 1 | - | - | |
| XOR | 48 bits | 1 | - | - |
| 128 bit | - | 1 | 1 | |
| 32 bit | 1 | 4 | 14 | |
| S-Box | 6-4 bit S-Box | 8 | - | - |
| 8-8 bit S-Box | - | 20 | 8 | |
| Shift | 28-bit circular left shift | 2 | - | - |
| 32-bit circular left shift | - | 4 | 6 | |
| Column Mix (Inverse Column Mix) | 32-bit (Inverse) column mix | - | 4 | - |
| Key Operators | Input and Output Bit-Widths | Number of Operators in One Round Operation of Hash Functions | ||
|---|---|---|---|---|
| SHA-1 | SHA-256 | SM3 | ||
| XOR | 32 bit | 5 | 11 | 10 |
| Shift | 32-bit circular left shift | 3 | - | 11 |
| 32 bits circular right shift | - | 10 | - | |
| 32 bits right shift | - | 2 | - | |
| Modulo addition | 32 bits ADD mod 232 | 4 | 9 | 7 |
| Algorithm Type | Implementation | Gate Count | Saving |
|---|---|---|---|
| AES | LUT | 586 | N/A |
| GF | 335 | 42.83% | |
| SM4 | LUT | 368 | N/A |
| GF | 244 | 33.70% |
| Structure Type | Algorithm Type | Gate Count | Saving |
|---|---|---|---|
| Separate | DES-64 | 1956 | N/A |
| AES-128/192/256 | 19,518 | N/A | |
| SM4-128 | 5635 | N/A | |
| Total | DES+AES+SM4 | 27,109 | N/A |
| Reconfigurable | DES/AES/SM4 | 17,986 | 33.65% |
| Structure Type | Algorithm Type | Gate Count | Saving |
|---|---|---|---|
| Separate | SHA-1 | 16,055 | N/A |
| SHA-256 | 18,627 | N/A | |
| SM3 | 17,921 | N/A | |
| Total | SHA-1+SHA-256+SM3 | 52,603 | N/A |
| Reconfigurable | SHA-1/SHA-256/SM3 | 23,050 | 56.18% |
| Structure Type | Algorithm Type | LUTs | Registers | F7 MUXes | F8 MUXes |
|---|---|---|---|---|---|
| Separate | DES-64 | 342 | 74 | 96 | 0 |
| AES-128/192/256 | 3756 | 685 | 649 | 256 | |
| SM4-128 | 732 | 266 | 103 | 20 | |
| Total | DES+AES+SM4 | 4830 | 1025 | 848 | 276 |
| Reconfigurable | DES/AES/SM4 | 5555 | 849 | 83 | 0 |
| Separate | SHA-1 | 1980 | 2910 | 0 | 0 |
| SHA-256 | 2549 | 2922 | 0 | 0 | |
| SM3 | 2043 | 2939 | 0 | 0 | |
| Total | SHA-1+SHA-256+SM3 | 6572 | 8771 | 0 | 0 |
| Reconfigurable | SHA-1/SHA-256/SM3 | 3140 | 2951 | 0 | 0 |
| TCAD’2018 [10] | TCAS-II’2020 [11] | TVLSI’2020 [12] | Ours Proposed Design | |
|---|---|---|---|---|
| Major key algorithms | DES/AES/SM4 ZUC/SNOW/RC4 SHA-256/SM3 | DES/AES/SM4 ZUC/SNOW/RC4 SHA-256/SM3 | DES/AES/SM4 ZUC/RC4 SHA-256 | DES/AES/SM4 SHA-1/SHA-256/SM3 |
| Architecture | Reconfigurable architecture based on one unified data path | Reconfigurable architecture based on one unified data path | Reconfigurable architecture based on one unified data path | Reconfigurable architecture based on two unified data paths for cipher block and hash function algorithms |
| Technology | 65 nm | 65 nm | 55 nm | 65 nm |
| Area (mm2) | 7.75 | 9.91 | 12.25 | 0.11 |
| Gate count | 1910 K | N/A | N/A | 41 K |
| Memory | 97.9 | N/A | N/A | 0 |
| Frequency (MHz) | 400 | 500 | 110 | 323 |
| Power (mW) | 620 (155 *) | 625 (125 *) | 35 (31.81 *) | 23 (7.12) * |
| Throughput (Gbps) | 51.2 (12.8 *) | 64 (12.8 *) | 0.44 (0.4 *) | 4.13 (1.28) * |
| Energy efficiency (Gbps/W) | 82.6 | 102.4 | 15.71 | 441 |
| Area efficiency (Gbps/mm2) | 6.61 (1.65 *) | 6.46 (1.29 *) | 0.04 (0.03 *) | 37.55 (11.64) * |
| S-Box topology | LUT | LUT | LUT | GF(((22)2)2) |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, X.; Liu, B.; Zhao, Y.; Hu, X.; Shen, Z.; Zheng, Z.; Liu, Z.; Chong, K.-S.; Yu, G.; Wang, C.; et al. Design and Analysis of Area and Energy Efficient Reconfigurable Cryptographic Accelerator for Securing IoT Devices. Sensors 2022, 22, 9160. https://doi.org/10.3390/s22239160
Zhang X, Liu B, Zhao Y, Hu X, Shen Z, Zheng Z, Liu Z, Chong K-S, Yu G, Wang C, et al. Design and Analysis of Area and Energy Efficient Reconfigurable Cryptographic Accelerator for Securing IoT Devices. Sensors. 2022; 22(23):9160. https://doi.org/10.3390/s22239160
Chicago/Turabian StyleZhang, Xvpeng, Bingqiang Liu, Yaqi Zhao, Xiaoyu Hu, Zixuan Shen, Zhaoxia Zheng, Zhenglin Liu, Kwen-Siong Chong, Guoyi Yu, Chao Wang, and et al. 2022. "Design and Analysis of Area and Energy Efficient Reconfigurable Cryptographic Accelerator for Securing IoT Devices" Sensors 22, no. 23: 9160. https://doi.org/10.3390/s22239160
APA StyleZhang, X., Liu, B., Zhao, Y., Hu, X., Shen, Z., Zheng, Z., Liu, Z., Chong, K.-S., Yu, G., Wang, C., & Zou, X. (2022). Design and Analysis of Area and Energy Efficient Reconfigurable Cryptographic Accelerator for Securing IoT Devices. Sensors, 22(23), 9160. https://doi.org/10.3390/s22239160






