Getting Smarter about Smart Cities: Improving Data Security and Privacy through Compliance
Abstract
:1. Introduction
- Highlight various aspects of data breaches in various sectors of smart cities.
- Present a taxonomy to show the impact of data breaches in smart cities.
- Present multiple preventive measures and best practices to minimize data breach incidents; and also include the impact of non-compliance with these principles.
- Propose future directions in developing a continuous data breach risk assessment framework.
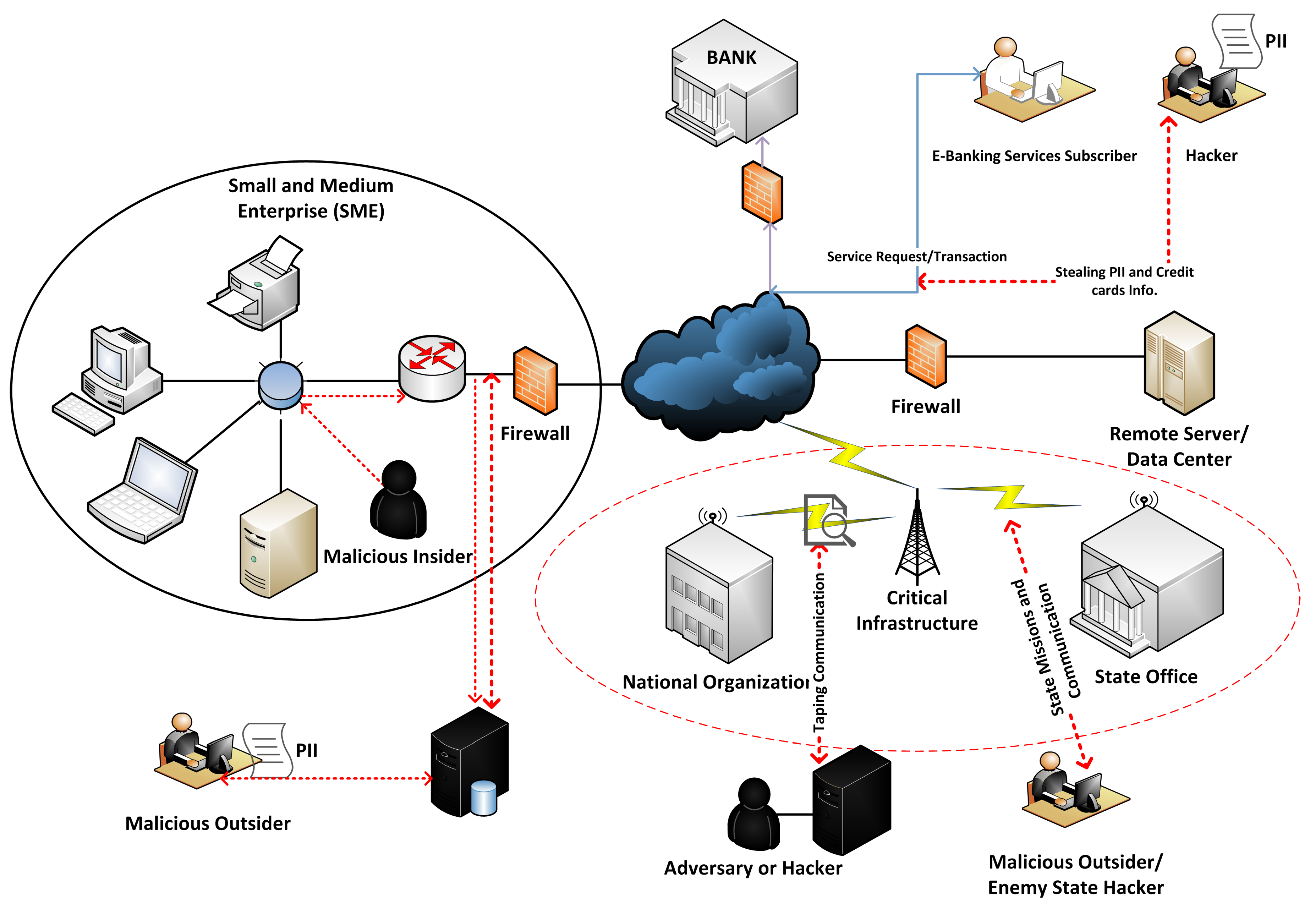
2. Data Breaches in Smart Cities
3. Impact on Assets
3.1. Financial
3.2. People
4. Preventive Measures for Data Breach Incidents
4.1. Security Models and Techniques
4.2. Standards, Regulations, Policies, Procedures, and Best Practices
- Ensure Confidentiality, Integrity and Availability (CIA) of e-PHI during creation and communication.
- Identify and protect against potential threats.
- Protect against all possible impermissible uses and disclosure.
- Ensure compliance.
4.3. Legal Obligations
- Depute an employee to coordinate financial institutions’ information security programs.
- Identify all internal and external potential security risks to the PII and other confidential data using risk assessment.
- Design and implement controls against the identified risks and regularly monitor the effectiveness of the implemented controls.
- Select and maintain service providers capable of protecting customers’ data through continuous compliance.
- Oversee testing and monitoring results and adjust information security program accordingly [37].
- Encryption and hiding the identity of personal data.
- Ensure confidentiality, integrity, and availability of system and processes.
- Accountability and auditing of the organizational and technical measures for the security of processes.
5. Analysis and Future Directions
Future Directions
- There is a need of a generic framework for the continuous risk assessment of data breaches and their overall impact so that appropriate risk treatment (mitigation, avoidance, insurance or acceptance) can be done. A preliminary conceptual framework could include four major phases (shown in Figure 8). In the first phase, potentially critical data which could be breached and can impact the organization is identified using data governance approaches. In phase 2, the organization assesses breach risk in the processes, functions, and systems. Next, in phase 3, based on the prioritized breach risks, the organization implements controls, policies, procedures, standards, and regulations. Last, in phase 4, the organization monitors the effectiveness of the implemented controls on its processes, functions, and systems. Finally, the continuity of the model is ensured by going through all phases in case of any lapse or any addition to data, assets, actors, and processes.
- Different methods to quantify and calculate breach cost are presented in the literature, which somehow calculates the cost associated with data breaches. However, these cost calculators and quantifiers are based on breach windows identified by organizations. It is a matter of great concern that the organization, large or small, hides the issues caused by breaches, which are not disclosed publicly. Therefore, these cost estimation calculators do not calculate the real cost of a breach. Thus, there is a need for such calculators and quantifiers that calculate the exact cost associated with breaching incidents by analyzing both notified and associated hidden breaches resulting from notified breaches.
- A possible solution to reduce the data breach’s impact is to enforce an effective consent framework. In this framework, data access, deletion, and usage are only granted to legitimate owners. Ever-changing trends, environments, and technology bring new challenges and privacy issues. Therefore, a privacy framework may also be designed to test system applications continually and log each installed application activity, including permission grants and access violations, formulate policies accordingly, and block such applications that escalate and creep any privilege. Moreover, any unauthorized activity should be notified to legitimate users, and any unauthorized data movement, if so detected, may be self-destroyed or encrypted.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Tang, V.; Cheng, S.W.; Choy, K.L.; Siu, P.K.; Ho, G.T.; Lam, H.Y. An intelligent medical replenishment system for managing the medical resources in the healthcare industry. In Proceedings of the 2016 IEEE International Conference on Fuzzy Systems (FUZZ-IEEE 2016), Vancouver, BC, Canada, 24–29 July 2016. [Google Scholar] [CrossRef]
- Mehmood, A.; Natgunanathan, I.; Xiang, Y.; Hua, G.; Guo, S. Protection of Big Data Privacy. IEEE Access 2016, 4, 1821–1834. [Google Scholar] [CrossRef] [Green Version]
- Siddiqui, F.; Matloob, G. Data at rest and it’s security solutions—A survey. Int. J. Adv. Res. Comput. Sci. 2017, 8, 1491–1493. [Google Scholar]
- Kim, G.H.; Trimi, S.; Chung, J.H. Big-data applications in the government sector. Commun. ACM 2014, 57, 78–85. [Google Scholar] [CrossRef]
- Jang-Jaccard, J.; Nepal, S. A survey of emerging threats in cybersecurity. J. Comput. Syst. Sci. 2014, 80, 973–993. [Google Scholar] [CrossRef]
- Razzaq, A.; Hur, A.; Ahmad, H.F.; Masood, M. Cyber security: Threats, reasons, challenges, methodologies and state of the art solutions for industrial applications. In Proceedings of the 2013 IEEE Eleventh International Symposium on Autonomous Decentralized Systems (ISADS), Mexico City, Mexico, 6–8 March 2013; pp. 1–6. [Google Scholar]
- Fonseca, B.; Rosen, J.D. Cybersecurity in the US: Major Trends and Challenges. In The New US Security Agenda; Springer: Berlin/Heidelberg, Germany, 2017; pp. 87–106. [Google Scholar]
- Verizon. 2017 Data Breach Investigations Report 10th Edition. Technical Report. arXiv 2017, arXiv:1011.1669v3.
- Verizon: 2019 Data Breach Investigations Report. Comput. Fraud. Secur. 2019, 2019, 4. [CrossRef]
- Nofer, M.; Hinz, O.; Muntermann, J.; Roßnagel, H. The economic impact of privacy violations and security breaches. Bus. Inf. Syst. Eng. 2014, 6, 339–348. [Google Scholar] [CrossRef] [Green Version]
- Sherstobitoff, R. Anatomy of a data breach. Inf. Secur. J. 2008, 17, 247–252. [Google Scholar] [CrossRef]
- Adebayo, A.O. A foundation for breach data analysis. J. Inf. Eng. Appl. 2012, 2, 17–23. [Google Scholar]
- Heimes, R. Global InfoSec and Breach Standards. IEEE Secur. Priv. 2016, 14, 68–72. [Google Scholar] [CrossRef]
- Acquisti, A.; Friedman, A.; Telang, R. Is there a cost to privacy breaches? An event study. In Proceedings of the ICIS 2006 Proceedings, Milwaukee, WI, USA, 10–13 December 2006; p. 94. [Google Scholar]
- Lehman, R.; Loder, E. Missing clinical trial data. BMJ 2012, 344, d8158. [Google Scholar] [CrossRef] [PubMed]
- Herath, T.; Rao, H.R. Encouraging information security behaviors in organizations: Role of penalties, pressures and perceived effectiveness. Decis. Support Syst. 2009, 47, 154–165. [Google Scholar] [CrossRef]
- Choo, K.K.R. The cyber threat landscape: Challenges and future research directions. Comput. Secur. 2011, 30, 719–731. [Google Scholar] [CrossRef]
- PwC. A matter of when, not if, a breach will occur. Information Security Breaches Survey 2016. Available online: https://www.pwc.be/en/documents/media-centre/publications/2016/information-security-breaches-survey-2016.pdf (accessed on 20 November 2022).
- Ford, J.C.; White, B.J.; White, K.M. After the data breach: Notification laws and more. Issues Inf. Syst. 2015, 16, 86–94. [Google Scholar]
- Confente, I.; Siciliano, G.G.; Gaudenzi, B.; Eickhoff, M. Effects of data breaches from user-generated content: A corporate reputation analysis. Eur. Manag. J. 2019, 37, 492–504. [Google Scholar] [CrossRef]
- Romanosky, S.; Telang, R.; Acquisti, A. Do data breach disclosure laws reduce identity theft? J. Policy Anal. Manag. 2011, 30, 256–286. [Google Scholar] [CrossRef] [Green Version]
- Beales, J.H., III; Muris, T.J. Choice or consequences: Protecting privacy in commercial information. Univ. Chic. Law Rev. 2008, 75, 109. [Google Scholar]
- Wigan, M.R.; Clarke, R. Big data’s big unintended consequences. Computer 2013, 46, 46–53. [Google Scholar] [CrossRef]
- Ponemon Institute. Cost of a Data Breach Report; Technical Report; Ponemon Institute: Traverse City, MI, USA, 2019. [Google Scholar]
- ITRC Data Breach Analysis H1 2022; Technical Report; Identity Theft Resource Center: El Cajon, CA, USA, 2022.
- Cost of a Data Breach; Technical Report; IBM: New York, NY, USA, 2022.
- Filkins, B. Health Care Cyberthreat Report: Widespread Compromises Detected, Compliance Nightmare on Horizon; SANS Institute: Bethesda, MD, USA, 2014. [Google Scholar]
- Choong, P.; Hutton, E.; Richardson, P.; Rinaldo, V. Assessing the cost of security breach: A marketer’s perspective. In Allied Academies International Conference, Academy of Marketing Studies. Proceedings; Jordan Whitney Enterprises, Inc.: Arden, NC, USA, 2016; Volume 21, p. 1. [Google Scholar]
- Ponemon Institute. Cost of Data Breach Study: Global Analysis; Technical Report; Ponemon Institute: Traverse City, MI, USA, 2015. [Google Scholar]
- Harris, K.D. California Data Breach Report; California Department of Justice: Sacramento, CA, USA, 2016.
- Smith, T.T. Examining Data Privacy Breaches in Healthcare; Walden University: Minneapolis, MN, USA, 2016. [Google Scholar]
- Choi, B.C.; Kim, S.S.; Jiang, Z. Influence of firm’s recovery endeavors upon privacy breach on online customer behavior. J. Manag. Inf. Syst. 2016, 33, 904–933. [Google Scholar] [CrossRef]
- Layton, R.; Watters, P.A. A methodology for estimating the tangible cost of data breaches. J. Inf. Secur. Appl. 2014, 19, 321–330. [Google Scholar] [CrossRef]
- Pirounias, S.; Mermigas, D.; Patsakis, C. The relation between information security events and firm market value, empirical evidence on recent disclosures: An extension of the GLZ study. J. Inf. Secur. Appl. 2014, 19, 257–271. [Google Scholar] [CrossRef]
- Telang, R. Policy framework for data breaches. IEEE Secur. Priv. 2015, 13, 77–79. [Google Scholar] [CrossRef]
- Azmi, I.M.A.G.; Zulhuda, S.; Jarot, S.P.W. Data breach on the critical information infrastructures: Lessons from the wikileaks. In Proceedings of the 2012 International Conference on Cyber Security, Cyber Warfare and Digital Forensic (CyberSec), Kuala Lumpur, Malaysia, 26–28 June 2012; pp. 306–311. [Google Scholar]
- Huson, M.L.; Hewitt, B. Would Increased Regulation Reduce the Number of Information Breaches? In Proceedings of the 2016 49th Hawaii International Conference on System Sciences (HICSS), Koloa, HI, USA, 5–8 January 2016; pp. 2633–2641. [Google Scholar]
- Disterer, G. ISO/IEC 27000, 27001 and 27002 for information security management. J. Inf. Secur. 2013, 4, 92–100. [Google Scholar] [CrossRef] [Green Version]
- Payment Card Industry Data Security Standard; Version 4.0; PCI Security Standards Council: Wakefield, MA, USA, 2022.
- Hulitt, E.; Vaughn, R.B. Information system security compliance to FISMA standard: A quantitative measure. Telecommun. Syst. 2010, 45, 139–152. [Google Scholar] [CrossRef]
- Janger, E.J.; Schwartz, P.M. The Gramm-Leach-Bliley Act, information privacy, and the limits of default rules. Minn. L. Rev. 2001, 86, 1219. [Google Scholar] [CrossRef] [Green Version]
- Federal Trade Commission. Marketing Violent Entertainment to Children: A Review of Self-Regulation and Industry Practices in the Motion Picture, Music Recording & Electronic Game Industries [with] Appendices AK. Report; ERIC Clearinghouse: New York, NY, USA, 2000.
- Henderson, G.C. The Federal Trade Commission: A Study in Administrative Law and Procedure; Yale University Press: London, UK, 1924. [Google Scholar]
- Act, A. Health insurance portability and accountability act of 1996. Public Law 1996, 104, 191. [Google Scholar]
- Watzlaf, V.J.; Moeini, S.; Matusow, L.; Firouzan, P. VOIP for telerehabilitation: A risk analysis for privacy, security and HIPAA compliance: Part II. Int. J. Telerehabilit. 2011, 3, 3. [Google Scholar] [CrossRef] [Green Version]
- Rajkumar, R.; Lee, I.; Sha, L.; Stankovic, J. Cyber-physical systems: The next computing revolution. In Proceedings of the Design Automation Conference, Anaheim, CA, USA, 13–18 June 2010; pp. 731–736. [Google Scholar]
- Levy, M.J.; Bissell, R. Overview of Critical Infrastructure. In Preparedness and Response for Catastrophic Disasters; Taylor & Francis Group: Boca Raton, FL, USA, 2013; p. 151. [Google Scholar]
- Austin, A.; Wetle, V. The United States Health Care System: Combining Business, Health, and Delivery; Pearson Higher Education: New York, NY, USA, 2011. [Google Scholar]
- Laudon, K.C.; Laudon, J.P. Management Information Systems: New Approaches to Organization and Technology; Prentice Hall College: Upper Saddle River, NJ, USA, 1998. [Google Scholar]
- Block, H.; Dobell, B. The e-Bang Theory, Education Industry Overview; Equity Research, Bank of America Securities, Montgomery Division: San Francisco, CA, USA, 1999.
- Choi, S.J.; Johnson, M.E.; Lehmann, C.U. Data breach remediation efforts and their implications for hospital quality. Health Serv. Res. 2019, 54, 971–980. [Google Scholar] [CrossRef]
- Floyd, T.; Grieco, M.; Reid, E.F. Mining hospital data breach records: Cyber threats to us hospitals. In Proceedings of the 2016 IEEE Conference on Intelligence and Security Informatics (ISI), Tucson, AZ, USA, 26–30 September 2016; pp. 43–48. [Google Scholar]
- Stachel, R.D.; DeLaHaye, M. Security breaches in healthcare data: An application of the actor-network theory. Issues Inf. Syst. 2015, 16, 185–194. [Google Scholar]
- Ghayur, A. Computer Animation and Gaming Industry; Animation Gaming, 2007; Volume 19, Available online: https://www.pide.org.pk/pdfseminar/seminar-2007-48-seminar99.pdf (accessed on 20 November 2022).
- Hinz, O.; Nofer, M.; Schiereck, D.; Trillig, J. The influence of data theft on the share prices and systematic risk of consumer electronics companies. Inf. Manag. 2015, 52, 337–347. [Google Scholar] [CrossRef]
- Joseph, R.C. Data breaches: Public sector perspectives. IT Prof. 2017, 20, 57–64. [Google Scholar] [CrossRef]
- Neama, G.; Alaskar, R.; Alkandari, M. Privacy, security, risk, and trust concerns in e-commerce. In Proceedings of the 17th International Conference on Distributed Computing and Networking, Singapore, 4–7 January 2016; pp. 1–6. [Google Scholar]
- Martin, C.; Kadry, A.; Abu-Shady, G. Quantifying the financial impact of it security breaches on business processes. In Proceedings of the 2014 Twelfth Annual International Conference on Privacy, Security and Trust, Toronto, ON, Canada, 23–24 July 2014; pp. 149–155. [Google Scholar]
- Algarni, A.M.; Malaiya, Y.K. A consolidated approach for estimation of data security breach costs. In Proceedings of the 2016 2nd International Conference on Information Management (ICIM), London, UK, 7–8 May 2016; pp. 26–39. [Google Scholar]
- Hirschprung, R.; Toch, E.; Bolton, F.; Maimon, O. A methodology for estimating the value of privacy in information disclosure systems. Comput. Hum. Behav. 2016, 61, 443–453. [Google Scholar] [CrossRef]
- Schatz, D.; Bashroush, R. The impact of repeated data breach events on organisations’ market value. Inf. Comput. Secur. 2016, 24, 73–92. [Google Scholar] [CrossRef] [Green Version]
- Jeong, C.Y.; Lee, S.Y.T.; Lim, J.H. Information security breaches and IT security investments: Impacts on competitors. Inf. Manag. 2019, 56, 681–695. [Google Scholar] [CrossRef]
- Holm, E.; Mackenzie, G. The importance of mandatory data breach notification to identity crime. In Proceedings of the 2014 Third International Conference on Cyber Security, Cyber Warfare and Digital Forensic (CyberSec), Beirut, Lebanon, 29 April–1 May 2014; pp. 6–11. [Google Scholar]
- Hauer, B. Data and information leakage prevention within the scope of information security. IEEE Access 2015, 3, 2554–2565. [Google Scholar] [CrossRef]
- Alneyadi, S.; Sithirasenan, E.; Muthukkumarasamy, V. A survey on data leakage prevention systems. J. Netw. Comput. Appl. 2016, 62, 137–152. [Google Scholar] [CrossRef]
- Shabtai, A.; Elovici, Y.; Rokach, L. A Survey of Data Leakage Detection and Prevention Solutions; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Alneyadi, S.; Sithirasenan, E.; Muthukkumarasamy, V. Detecting data semantic: A data leakage prevention approach. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Washington, DC, USA, 20–22 August 2015; Volume 1, pp. 910–917. [Google Scholar]
- Khan, M.F.F.; Sakamura, K. A patient-centric approach to delegation of access rights in healthcare information systems. In Proceedings of the 2016 International Conference on Engineering & MIS (ICEMIS), Agadir, Morocco, 22–24 September 2016; pp. 1–6. [Google Scholar]
- Home—Centers for Medicare & Medicaid Services. 2020. Available online: https://www.cms.gov/ (accessed on 1 September 2012).
- McLeod, A.; Dolezel, D. Cyber-analytics: Modeling factors associated with healthcare data breaches. Decis. Support Syst. 2018, 108, 57–68. [Google Scholar] [CrossRef]
- ISO/IEC 27001:2022; Information Security, Cybersecurity and Privacy Protection—Information Security Management Systems—Requirements. International Organization for Standardization: Geneva, Switzerland, 2022.
- ISO/IEC 27002:2022; Information Security, Cybersecurity and Privacy Protection—Information Security Controls. International Organization for Standardization: Geneva, Switzerland, 2022.
- Rao, U.H.; Nayak, U.; Gopalkrishnan, R. PCI DSS—Penalty of not being compliant. Int. J. Audit. Technol. 2014, 2, 37–46. [Google Scholar] [CrossRef]
- Yaraghi, N.; Gopal, R.D. The role of HIPAA omnibus rules in reducing the frequency of medical data breaches: Insights from an empirical study. Milbank Q. 2018, 96, 144–166. [Google Scholar] [CrossRef]
- Hirsch, R.; Deixler, H. Final HIPAA Omnibus Rule brings sweeping changes to health care privacy law: HIPAA privacy and security obligations extended to business associates and subcontractors. BNA Priv. Secur. Law Rep. 2013, 12, 1–11. [Google Scholar]
- Renaud, K. Blaming noncompliance is too convenient: What really causes information breaches? IEEE Secur. Priv. 2011, 10, 57–63. [Google Scholar] [CrossRef]
- Voigt, P.; Von dem Bussche, A. The EU General Data Protection Regulation (GDPR), 1st ed.; A Practical Guide; Springer International Publishing: Cham, Switzerland, 2017. [Google Scholar]
- Manley, J. Personal Information Protection and Electronic Documents Act (PIPEDA); 36th Parliament, bill c-6; Parliament of Canada: Ottawa, ON, Canada, 2019. [Google Scholar]
- Fair Credit Reporting Act. 15 u.s.c. §§ 1681-1681x; Federal Trade Commission: Washington, DC, USA, 2018.
- Goel, S.; Shawky, H.A. The Impact of Federal and State Notification Laws on Security Breach Announcements. Commun. Assoc. Inf. Syst. 2014, 34, 37–50. [Google Scholar] [CrossRef]
- Calder, A. Nine Steps to Success: An ISO 27001 Implementation Overview; IT Governance Ltd.: Ely, UK, 2017. [Google Scholar]







| 1. | Organizational Controls (37) | 2. | People Controls (8) |
| 3. | Physical Controls (14) | 4. | Technological Controls (34) |
| Requirement | Issues | Solutions |
|---|---|---|
| 8 | Monthly Premium Payment | Unique Agent ID for Every Organization. |
| 3,4 | Plaintext Email Attachment | Use of Application to generate encryption and decryption code for every card. |
| 7 | Accessibility of Card Holder User Data | Implementation of Access Control Policy and Regular Review of Control Policy. |
| 2 | Leaking of Encryption Keys by Former Employees | Fixing Administrative Controls and Continual Key Update. |
| 6,11 | Lack of Standardization of Used Applications | Using Validated and Certified Third-Party Applications. |
| 10 | Lack of Mechanism to Monitor and Analyze Logs | Acquiring tools for Continual Monitoring and Analyzing of logs. |
| 12 | Lack of IS policy propagation and Awareness | Using NIST 2003 mandatory video sessions to carry out businesses without losing reputation. |
| Other | Lack of Effective Vulnerability and Pen Testing | Experienced Involvement and adapting to new PCI-DSS 3.0 requirements. |
| Lack of Identification and Management of CIA issues | Continuous Auditing to ensure information. | |
| Continued Sustenance of PCI-DSS Compliance | Continuous effort to stay compliant. |
| 1. | Identification and Authentication | 2. | Access Control |
| 3. | Awareness and Training | 4. | Auditing and Accountability |
| 5. | Assessment and Certification | 6. | Incident Response |
| 7. | Contingency Planning | 8. | Configuration Management |
| 9. | Physical and Environment Protection | 10. | System and Information Integrity |
| 11. | Maintenance | 12. | Planning |
| 13. | Risk Assessment | 14. | System and Communication Protection |
| 15. | System and Service Acquisition | 16. | Media Protection |
| 17. | Personnel Security | ||
| SECTOR | FINANCIAL | PEOPLE | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Health-Care | Critical Cyber-Physical | Gaming | IT/ SMEs | Financial | Cost | Rev-Enue | Market Value | Stock Price | Employee-Customer | |
| [18] | ✓ | ✓ | R, C | |||||||
| [19] | ✓ | |||||||||
| [28] | ✓ | ✓ | ✓ | ✓ | ||||||
| [30] | ✓ | ✓ | ✓ | ✓ | C | |||||
| [31] | ✓ | ✓ | R, C | |||||||
| [32] | ✓ | ✓ | ✓ | R, C | ||||||
| [33] | ✓ | ✓ | ✓ | ✓ | ||||||
| [34] | ✓ | ✓ | ✓ | |||||||
| [36] | ✓ | ✓ | ✓ | ✓ | ✓ | |||||
| [52] | ✓ | ✓ | C | |||||||
| [53] | ✓ | Tr, R, C | ||||||||
| [55] | ✓ | ✓ | ✓ | |||||||
| [58] | ✓ | ✓ | ✓ | |||||||
| [59] | ✓ | |||||||||
| [60] | ✓ | C | ||||||||
| [61] | ✓ | ✓ | ✓ | |||||||
| [80] | ✓ | |||||||||
| Identity | Fraud | Unintended | Negligence of | Lack of | Lack of | Budget | |
|---|---|---|---|---|---|---|---|
| Theft | Exposure | Employees | Skilled Staff | Security | Constraints | ||
| [18] | ✓ | ||||||
| [19] | ✓ | ||||||
| [28] | ✓ | ✓ | ✓ | ||||
| [30] | ✓ | ✓ | |||||
| [31] | ✓ | ✓ | ✓ | ||||
| [32] | ✓ | ✓ | |||||
| [33] | ✓ | ||||||
| [52] | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [53] | ✓ | ✓ | ✓ | ✓ | ✓ | ||
| [61] | ✓ | ✓ | ✓ | ||||
| [63] | ✓ | ||||||
| [70] | ✓ | ✓ | |||||
| [76] | ✓ | ✓ | ✓ | ||||
| [80] | ✓ |
| Proposed Model and Techniques | Regulations, Policy and Procedures | Standards | Best Practices | Legal Obligations | |
|---|---|---|---|---|---|
| [13] | GDPR | ||||
| [19] | ✓ | ||||
| [31] | ✓ | ||||
| [32] | ✓ | ||||
| [34] | ✓ | ||||
| [35] | PCI DSS | GLBA * FCRA * | |||
| [36] | ✓ | ✓ | |||
| [37] | PCI DSS | FISMA * HIPAA * GLBA * | |||
| [53] | ✓ | ✓ | ✓ | ||
| [58,59] | ✓ | ||||
| [61] | ✓ | ||||
| [63] | ✓ | ||||
| [64,65,66,67] | ✓ | ||||
| [68] | ✓ | ||||
| [70] | ✓ | ||||
| [73] | PCI DSS | ||||
| [74] | HIPAA * | ||||
| [76] | ✓ | ✓ | |||
| [80] | ✓ |
| Impact Category | Effects | Reasons | Treatment | Mitigation | Follow-Up | |
|---|---|---|---|---|---|---|
| Data Breaches | Sectors [46,47,48,49,50] | Critical/Cyber-physical System [35,36,56,57] | No Regulation [13,35,36,80] Non-Compliance [19] Lack of Incidence Response [31] No or less effective Risk Mitigation Plan [81] Resist Change [73] Untrained Staff [53,76] Less IT staff [53] Non-Effective Access Controls [68,73] Low Security budget [18,28] Non-Compliance by Vendors and Service Providers [31,53] | Incidence Response or Breach Recovery Process [19,30] Disclosure/Notification Laws [13,19,32,33,51,60,77] | Policies, Procedures and standards [33,35,36,37,53,61,73,74,76] Legal Obligations [19,34,35,37,63,80] More IT Staff [53] More security Budget [18,27,28,34,35] Incidence Response or Breach Recovery Process [19,31] Accountability Effective Access Controls [37,68,73,81] Implement Proposed Models and Techniques [32,33,53,58,59,64,65,66,67,68,70] Follow Best Practices [31,53,76] Breach Risk Assessment and Management [38,81] Ensure Vendor and Provider Compliance [31,53] | Continuous Auditing [13,33,53,73] Continuous Monitoring [37,38,40,73,76] Continuous Compliance [37] Breach Risk Reassessment [38,81] |
| Healthcare [31,52,53,70,74] | ||||||
| Gaming [32,55] | ||||||
| IT Firms/ other Businesses (Large/Small) [18,30] | ||||||
| Financial [56] | Market Value [34,61] | No Regulation [13,35,36,80] Non-Compliance [19] Lack of Incidence Response [31] No or less effective Risk Mitigation Plan [81] | Incidence Response or Breach Recovery Process [19,30] Disclosure/Notification Laws [13,19,32,33,51,60,77] | Disclosure/Notification Laws [13,19,33,34,53,63,80] Implementation of Economic and Financial Models [33,58,59] Cost Calculators and Estimators [33,58] | ||
| Cost [19,58,59,60] | ||||||
| Revenue [58] | ||||||
| Stock Prices [61] | ||||||
| People [30,31,52] | Company data/ information [18,28,52,53] | Human Errors [30,31] Negligence [30,31,52,53,76] Unintended Exposure [30,52,53,76] | Incidence Response or Breach Recovery Process [19,30] Disclosure/Notification Laws [13,19,32,33,51,60,77] | Staff Training [53,76] Auditing [53] Accountability [53] | ||
| User name and Passwords [32,52,55] | ||||||
| Loss of Customer [19,28,30,31,32,33,52,61,63,76,80] | Identity Theft [19,28,31,32,33,52,53,61,63,76,80] Customer Privacy Exposure [30,52,53,76] Fraud [26,29,30,51,60] Less IT Staff [53] Low Security Measures [52,53] | Disclosure/ Notification Laws [13,19,33,34,53,63,80] Incidence Response Plan [19,31] Ensuring Privacy of data using Encryption [13,53,73] Compliance with Industry Standards [37,38,39,40,44] | ||||
| Loss of Reputation and Trust [20,28,32,52,61,80] |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aslam, M.; Khan Abbasi, M.A.; Khalid, T.; Shan, R.u.; Ullah, S.; Ahmad, T.; Saeed, S.; Alabbad, D.A.; Ahmad, R. Getting Smarter about Smart Cities: Improving Data Security and Privacy through Compliance. Sensors 2022, 22, 9338. https://doi.org/10.3390/s22239338
Aslam M, Khan Abbasi MA, Khalid T, Shan Ru, Ullah S, Ahmad T, Saeed S, Alabbad DA, Ahmad R. Getting Smarter about Smart Cities: Improving Data Security and Privacy through Compliance. Sensors. 2022; 22(23):9338. https://doi.org/10.3390/s22239338
Chicago/Turabian StyleAslam, Mudassar, Muhammad Abbas Khan Abbasi, Tauqeer Khalid, Rafi us Shan, Subhan Ullah, Tahir Ahmad, Saqib Saeed, Dina A. Alabbad, and Rizwan Ahmad. 2022. "Getting Smarter about Smart Cities: Improving Data Security and Privacy through Compliance" Sensors 22, no. 23: 9338. https://doi.org/10.3390/s22239338
APA StyleAslam, M., Khan Abbasi, M. A., Khalid, T., Shan, R. u., Ullah, S., Ahmad, T., Saeed, S., Alabbad, D. A., & Ahmad, R. (2022). Getting Smarter about Smart Cities: Improving Data Security and Privacy through Compliance. Sensors, 22(23), 9338. https://doi.org/10.3390/s22239338









