Abstract
In recent years, due to the rapid development of Internet of things (IoTs), various physical things (objects) in IoTs are smart enough to make their own decisions without the involvement of humans. The smart devices embedded in a drone can sense, collect, and transmit real-time data back to the controller from a designated environment via wireless communication technologies. The mobility, flexibility, reliability and energy efficiency of drones makes them more widely used in IoT environments such as commercial, military, entertainment applications, traffic surveillance and aerial photography. In a generalized IoD architecture, we have communications among the drones in a flying zone, among the drones and the control server, and also among the drones and authorized user. IoD still has many critical issues that need to be addressed, such as data access being carried out through a public channel and battery operated drones. To address these concerns in IoD communications, in this paper, an efficient authentication and secure communication scheme with privacy preservation is proposed and it only uses secure one-way hash function and bitwise XOR operations when control server, drone and user mutually authenticate each other. After the successful authentication, both IoD-based participants can agree on a common session key to secure the subsequent communication messages. The widely accepted ProVerif and BAN logic analysis have been used to assure that the proposed scheme is provably secure against existing well-known security attacks and ensures privacy. Finally, a comparative analysis is presented to demonstrate the proposed scheme preserves efficiency when compared to existing competitive schemes.
1. Introduction
For the past few years, as information and communication technology (ICT) advances and smart devices increase dramatically, the Internet of Things (IoT) has become a much-talked-about topic among many experts and large ICT companies [1]. Due to its capability to extend the traditional human-to-human network communication connection for fulfilling communication and dialogue between humans and objects, or further to achieve communication and dialogue between objects, these objects can be distinguished into physical objects and virtual objects. The physical objects include sensors, drones, surveillance cameras, smartphones, self-driving vehicles, and smart homes, while the virtual objects include electronic wallets, electronic tickets, and electronic agendas. The strength of using various smart objects in the IoT environment is that they can operate autonomously without human intervention and can be easily integrated into various smart network applications. Especially, drones can be also named unmanned aerial vehicles (UAVs), which is an aircraft that can be controlled remotely or by an onboard computer. Drones can navigate autonomously without human intervention and are comprised of several IoT smart devices, such as light pulse range sensors (laser), radio detection and distance measuring sensors, magnetic field change sensors, sonar range sensors, time of flight sensors, thermal sensors, chemical sensors, and direction sensors. Along with the miniaturization trend of different devices (processors, microcontrollers, sensors, wireless transceivers) inside the drones, it can be seen as a hint that IoT technology makes the drone network or IoDs a part of IoTs [2,3,4,5,6,7,8].
When combined with various sensing elements, location services, wireless transmission reading, content services, and other technologies, many different types of drone applications have been derived. The application scopes of several drones were described and organized, as shown below:
- For civilian purposes [9]:
- i.
- For photography purposes: Allowing TV/film producers to take aerial photography in a new manner by using drones, thus enhancing the aerial view to a higher extent.
- ii.
- For natural disaster assessment and control purposes: After Hurricane Katrina hit the United States in 2005, drones were used for disaster control and assessment to observe which roads were blocked by fallen trees, cars, and road barriers, or to search for missing, injured, and trapped people.
- iii.
- For emergency response purposes: Like ambulances, drones can be used as portable medical kits which can send medical supplies to emergency units on site, particularly when the emergency site is inaccessible for vehicles. Furthermore, affected by the recent COVID-19 pandemic, drones have been deployed on the streets of Spain and China (mainly Wuhan), to raise people’s awareness of the crisis via cameras and broadcasters, or aerial spraying for disinfection. Furthermore, drones can be used as a means of delivering food and medication to infected patients, aiming to transport tested samples at a higher speed, and reduce human contact.
- iv.
- For environmental monitoring purposes: Drones can be used to perform tasks of measuring environmental pollution, such as those for air quality measurement and analysis; perform agricultural tasks, such as soil analysis, crop/livestock management/disease, and pest control; perform animal protection tasks, such as nature/wildlife protection/anti-poaching/endangered species protection.
- For police purposes [10]:
- i.
- For traffic monitoring purposes: Drones can be used to monitor traffic and accident scenes. For example, the Spanish government has adopted drones to monitor traffic bottlenecks since 2015.
- ii.
- For criminal-tracking purposes: Drones can be used to monitor crime scenes and prison fugitives. For example, the Ohio State Police Station used a drone to track an escaped prisoner and track him down in 2016.
- iii.
- For forensic search-and-rescue purposes: Drones can be used to tackle crimes, such as the missing person and murder case of Ms. Tara Grinstead in 2015, for whom Georgia police used a fixed-wing drone called Spectra to search.
- For military purposes [11]:
- i.
- For aerial surveillance/reconnaissance purposes: Drones can be deployed in the air to collect intelligence and information and further identify and track the locations of terrorist camps, vehicles, weapons, plants, and improvised explosive devices. For example, Russia collected new drone footage that unveiled how Turkey used artillery operations to attack the Syrian army in 2020.
- ii.
- For airstrike purposes: As early as 2002, the U.S. military used drones for airstrike missions and then developed them for application with British allies in the global anti-terrorism war. In addition, Israel also made use of drones to conduct airstrikes against military installations/key targets/people in Iraq and Syria on the west coast.
- iii.
- For drone hijacking purposes: Drone hijacking is mainly achieved via GPS intervention/spoofing, which was used to resolve the conflict in Ukraine and stood up to the threat from the Islamic State until the city of Mosul was finally liberated from the Islamic State in 2017.
- For criminal attack purposes [12]:
- i.
- Physical attacks: Drones can easily be used to destroy people’s privacy and threaten their private property by crashing into people or their property intentionally or unintentionally to cause them serious damage. Moreover, some drones can fly as high as 500 m in the air, just like bird strikes, which can cause serious damages to aircrafts in flight.
- ii.
- Logical attacks: They include spoofing a hotspot of a mobile Wi-Fi network, allowing the victim users to connect and monitor their sensitive messages, such as account passwords and credit card data, or implanting malware into smartphones and mobile devices that are connected to the malicious hotspot. Furthermore, a Raspberry Pi device connected to a drone can also be maliciously coded to intercept or hijack other drones nearby.
From the perspective of security and threat analysis, drone-assisted public safety networks require a stricter manner rather than traditional wireless networks such as wireless sensor networks (WSN) [13] and mobile ad hoc networks (MANET) [14] to restrict the unauthorized collection of images and videos by drones. Though drones carry less information and less power, they can cover a wider range than WSNs and MANETs. As a result, the challenge of drone network security is how to provide communication channels with confidentiality, integrity, availability, authentication, and non-repudiation over the resource constraints and latency constraints of drones. Actually, kinds of technologies for drone operations and their specific properties are being explored and misused for potential attacks including performing terrorist attacks and reconnaissance, tracking specific people, and monitoring certain properties, thus arousing security and privacy concerns. Furthermore, if a drone is out of order and crashes into nearby private houses, public facilities, parked cars, or civilians, it could also lead to casualties and damage to property. On the other hand, drones mainly make use of Wi-Fi, short-range Wi-Fi, Bluetooth, or other wireless devices, such as Bluetooth-connected keyboards, while, if there are inadequate security measures for connection to these devices, such as insecure single factor authentication and easy-to-break typical passwords, the attackers can easily intercept messages and destroy private buildings and public areas.
In plenty of authentication and key agreement (AKA) schemes [15,16,17,18,19,20,21,22,23], symmetric and asymmetric cryptosystems have been proposed to implement a comprehensive authentication on the use of IoT and IoD environments. However, with the resource-constrained nature of drones, it cannot consume a high amount of energy for executing complex cryptographic operations on large datasets and AKA scheme shall be sufficiently lightweight both in terms of computational complexity, communication overhead and memory demand. Turkanović et al. first proposed an IoT-based AKA scheme [24] for WSNs and their scheme is highly efficient as it only uses lightweight hash and bitwise XOR computations. Although it achieves the condition of lightweight authentication, Farash et al. [25] pointed out that their devised scheme is prone to man-in-the-middle attack, node impersonation attack, and additionally does not render nodes anonymity and user traceability. In order to provide better security, Wazid et al. designed a novel AKA scheme [26] for UAV distributed networks. However, the protocol was pointed out by Lei et al. [27] as not being provided to perfect forward secrecy. Meanwhile, Rodrigues et al. [28] designed two methods for the drone communication environment. The first one is modified based on the AKA scheme of Farash et al. [25], allowing for a direct connection between a drone and another one; the second one is modified based on the AKA scheme of Jiang et al. [18], which allows a drone to communicate with another one through a ground control station. However, their AKA schemes fail to resist ephemeral secret leakage (ESL) attacks under the Canetti–Krawczyk (CK) threat model. Recently, Zhang et al. proposed a lightweight AKA scheme [29] with anonymity and untraceability for IoD environments and their AKA scheme can be proven secure under random oracle model. All the drones and the users are registered with a central trusted authority, control server (namely ) prior to their deployment. By verifying the validation of the transmitted messages, all participants in IoD can ensure mutual authentication and establish a common session key securely. In this paper, we will propose an improved version of Zhang et al.’s scheme that not only provides the same level of security with anonymity and untraceability but also protects the scheme from various known attacks.
In order to achieve the aforementioned security requirements of previous authentication schemes in IoD environments, in this paper, we propose a lightweight mutual authentication and privacy preservation scheme to resist several security attacks and provide a series of important features cited above. The main contributions of this paper are given as follows: (1) In our lightweight authentication scheme, the properties of drone anonymity and drone untraceability can be guaranteed at authentication and key agreement phase when involved participants transmitted messages via a public IoD channel. (2) In comparison with existing IoT-assisted authentication schemes for IoD communications, our proposed scheme can not only maintain the efficiency of computational and computation overheads, but also achieve basic security features mentioned in prior studies. (3) Informal security analysis and BAN logic analysis are performed and ProVerif-based formal security simulation is implemented, to demonstrate that our scheme is secure against various security attacks.
The remainder of the paper is organized as follows. Section 2 presents a new security architecture along with the threat model for IoD communication environments. Section 3 introduces our authentication and key agreement scheme with privacy preserving for IoD communications. The informal security analysis with the formal security verification using the widely accepted ProVerif simulation and BAN logic of the proposed scheme are given in Section 4. An in-depth performance comparison of the proposed scheme with existing IoD authentication schemes is given in Section 5. Finally this paper is concluded in Section 6.
2. System Architecture in IoD Communications
In this section, we will illustrate the proposed system architecture for the IoD paradigm. Subsequently we define two adversary models to evaluate its security and usability.
2.1. System Model
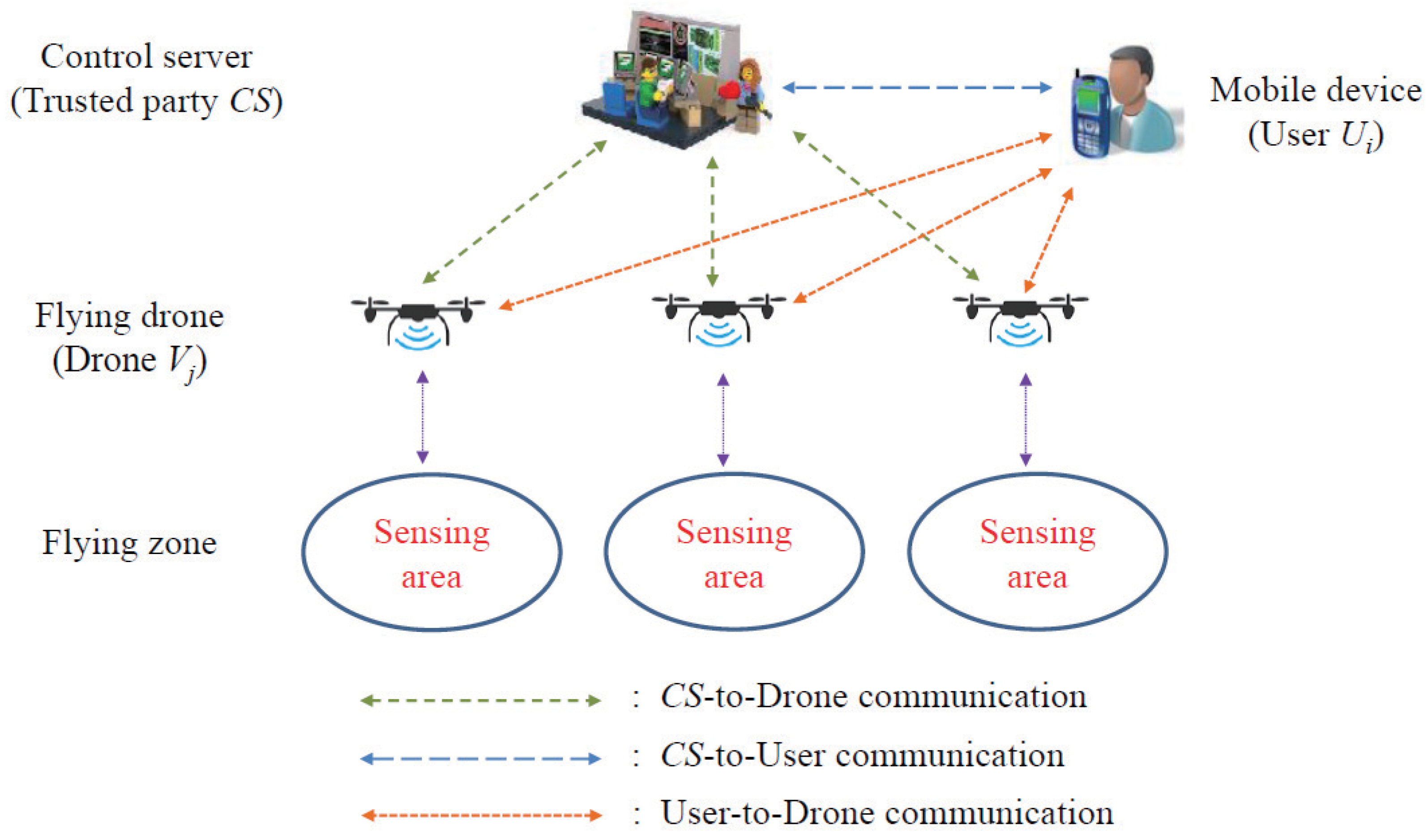
In terms of the design, the main participants in this paper were control server (), the trusted registration authority, users who could access IoD data using mobile devices, some mobile-type drone nodes deployed in the application fields to collect and broadcast data from the fly zone. is a trusted unit responsible for registering and issuing unique identifiers and generating secret parameters for users and drones. By deploying drone nodes via in fly zones for authority control, these drone nodes can be seen as cluster heads for a specific fly zone, providing an efficient and well-designed communication and authentication mechanism for IoD environments to avoid the single point of failure of traditional single centralized certificate centers. An external user can access certain specific drone nodes in the IoD environment via Internet communication and his/her mobile device, given that he/she is authenticated and authorized by the to access these drones. In this paper, the IoD communication and authentication mechanism for IoD applications included three modes, namely -to-Drone communication, -to-User communication, and User-to-Drone communication. The overall communication architecture diagram of IoD is illustrated in Figure 1.
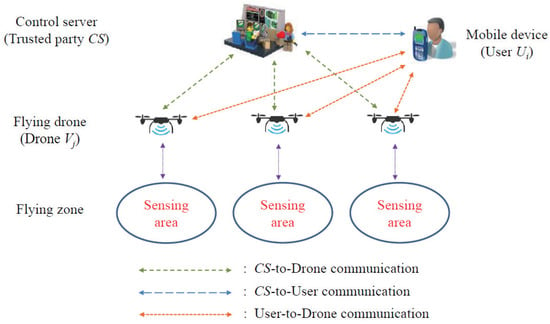
Figure 1.
Communication architecture diagram of IoD.
2.2. Threat Model
According to the system architecture shown in Figure 1, drones, mobile users and control servers can communicate with each other and all communications of IoD take place over the public channels. In threat model, we will adopt the widely-used Dolev–Yao (DY) threat model and Canetti–Krawczyk (CK) adversary model. According to the definition of DY model, the communication channel between any two entities is open and insecure, and also the end-point entities are not trusted. An adversary can eavesdrop and collect on the messages exchanged on IoD network, and can also delete or tamper the transmitted messages over public channel. According to the definition of CK model, the mobile device of an may be lost or stolen. The system parameters stored in that device can be also extracted by using power analysis attack. Furthermore, an adversary may physically capture some drone node and extract the stored parameters in with the help of complicated power analysis attack. Therefore, the compromised data will be used to undermine the security of IoD communications such as session key exposure, impersonation attack, replay attack, privacy exposure attack and man-in-the-middle attack etc. Note that is a trusted party and it will not be compromised by adversaries.
3. The Proposed Scheme
In this section, we propose a new lightweight authentication and key agreement scheme with privacy preservation for IoD communications. The proposed scheme consists of the following four phases: system setup, user registration, drone registration, and authentication and key agreement phase. The details of the proposed scheme are described in the following subsections. The notations used in the proposed scheme are summarized as follows.
- : The ith mobile user.
- : The jth drone.
- : The control server.
- : The identity and password of .
- : The identity of .
- : 160 bits secret value and master key of .
- n: 160 bits public parameter selected by .
- : The current timestamp of , and , respectively.
- : 160 bits random numbers of and , respectively.
- : An active drone list.
- : A collision free one-way hash function.
- : The maximum time threshold of accepting messages.
- : The current time received message.
- : The common session key shared between and .
- ⊕: The bitwise exclusive OR operation.
- : The string concatenation operation.
3.1. System Setup Phase
In this phase, first generates and k as its master key and secret value, respectively. Then, chooses a secure one-way hash function , where n is a 160-bits public parameter chosen by . Finally, saves secretly and publishes .
3.2. User Registration Phase
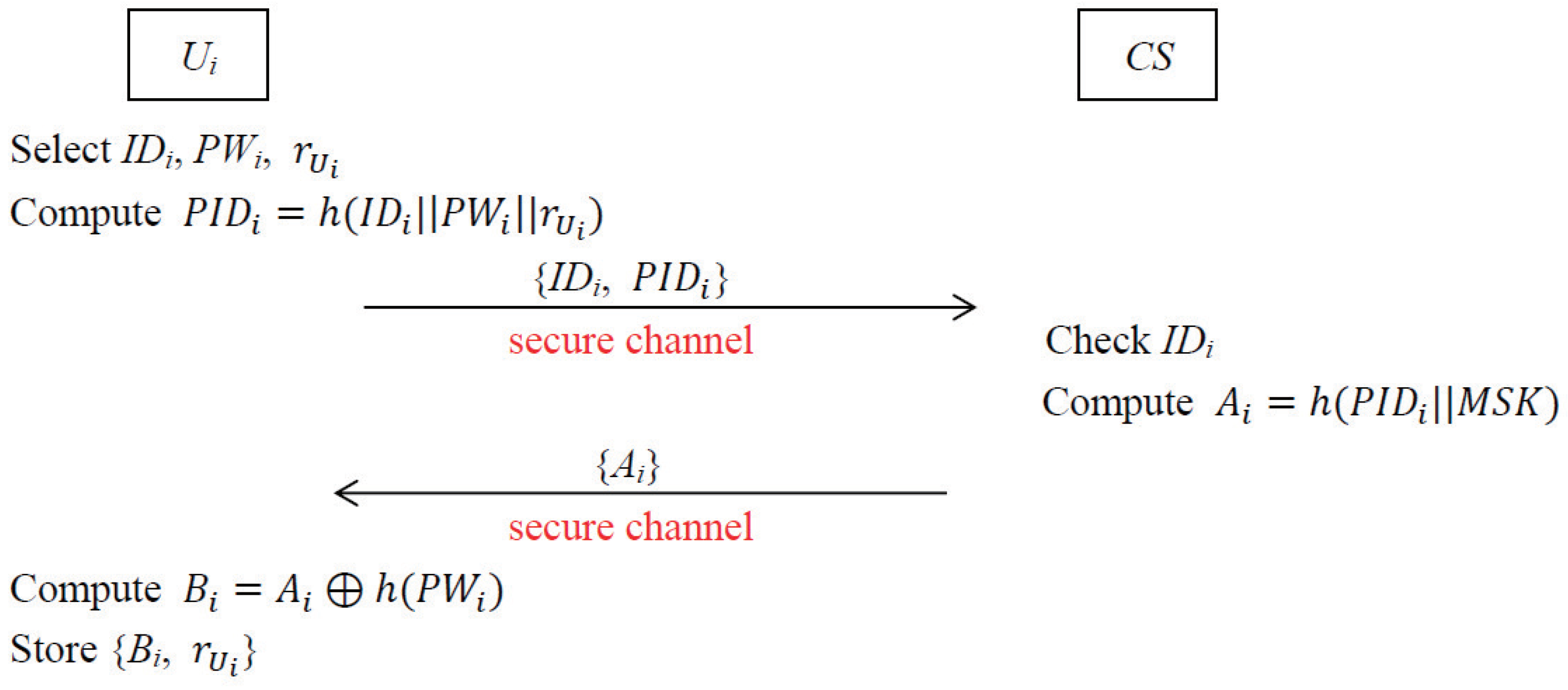
In this phase, every mobile user needs to perform the user registration procedure with via a secure channel. The graphical representation of the registration procedure of the user is depicted in Figure 2.
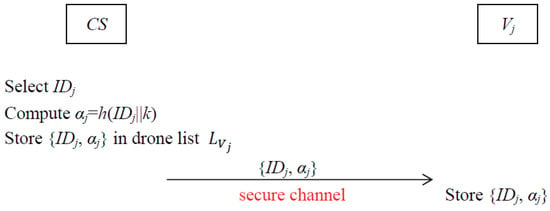
Figure 2.
Registration procedure of user.
- Step 1.
- chooses his/her identity , password and a random number and computes . Then sends the registration request {} to via a secure channel.
- Step 2.
- After receiving the registration request from , checks the uniqueness of ’s identity. If the uniqueness of is satisfied, computes and sends it to securely.
- Step 3.
- After receiving from , computes and stores {} in the tamper-proof memory, which means that the parameters and can be used during the computation, but it is unable to extract them from the mobile device of .
3.3. Drone Registration Phase
In this phase, every drone needs to complete the drone registration procedure with via a secure channel. The graphical representation of the registration procedure of the drone is depicted in Figure 3.
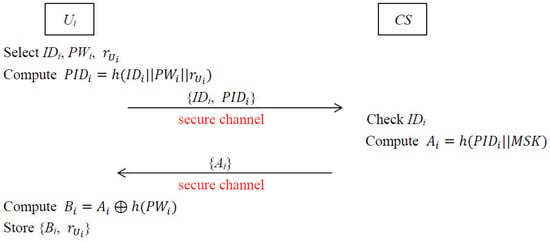
Figure 3.
Registration procedure of drone.
- Step 1.
- selects an unique identity for and computes . Then saves () in list and sends {} to securely.
- Step 2.
- After receiving the registration parameters from , stores and in its memory securely.
3.4. Authentication and Key Agreement Phase
After registration, and can communicate with each other and establish a common session key for securing future communications. The graphical representation of the proposed authentication and key agreement phase is depicted in Figure 4.

Figure 4.
Authentication and key agreement procedure of IoD communications.
- Step 1.
- opens the login portal and inputs his/her identity and password into the mobile device. Then the mobile device retrieves () and computes and . Then it randomly generates two 160 bits random numbers and computes , , , , where is the current timestamp of . Then sends authentication request message {} to via a public channel.
- Step 2.
- After receiving the authentication request from , checks whether holds or not. If not, rejects the authentication request immediately. Otherwise, computes , , , and .
- Step 3.
- checks whether holds or not. If yes, authenticates the legality of . Otherwise, rejects ’s authentication request. Now, randomly assigns an active drone in IoD for and computes , , , , , and , where is retrieved from list and is the current timestamp of . Finally sends the message {} to through a public channel.
- Step 4.
- After receiving the message from , checks whether holds or not. If not, rejects this session. Otherwise, retrieves and computes , , and .
- Step 5.
- checks whether holds or not. If not, rejects the request. Otherwise, authenticates the legality of and . Then, randomly chooses a 160 bits random number and computes the common session key , , and , where is the current timestamp of . Finally sends the message {} to through a public channel.
- Step 6.
- After receiving the message from , checks whether holds or not. If not, rejects this session. Otherwise, computes and . Then further checks if holds or not. If it is true, it implies that is authenticated to . In order to verify the legality of , computes , the common session key , and and checks whether holds or not. If not, rejects the communication request. Otherwise, it implies that is also authenticated to and the common session key will be used for securing IoD communications between and . Finally, computes and replaces {} with {} for the next login.
4. Security Analysis of the Proposed Scheme
In this section, meticulous informal security analysis and the security verification are carried out using ProVerif to prove the security and the validity of the proposed scheme. In addition, BAN logic is utilized to corroborate the logical exactitude of the proposed scheme.
4.1. Simulation Verification with ProVerif
ProVerif is a proper tool that can automatically analyze cryptographic protocols and verify the security and reliability of authentication protocols. The specific operation of ProVerif is described in detail below.
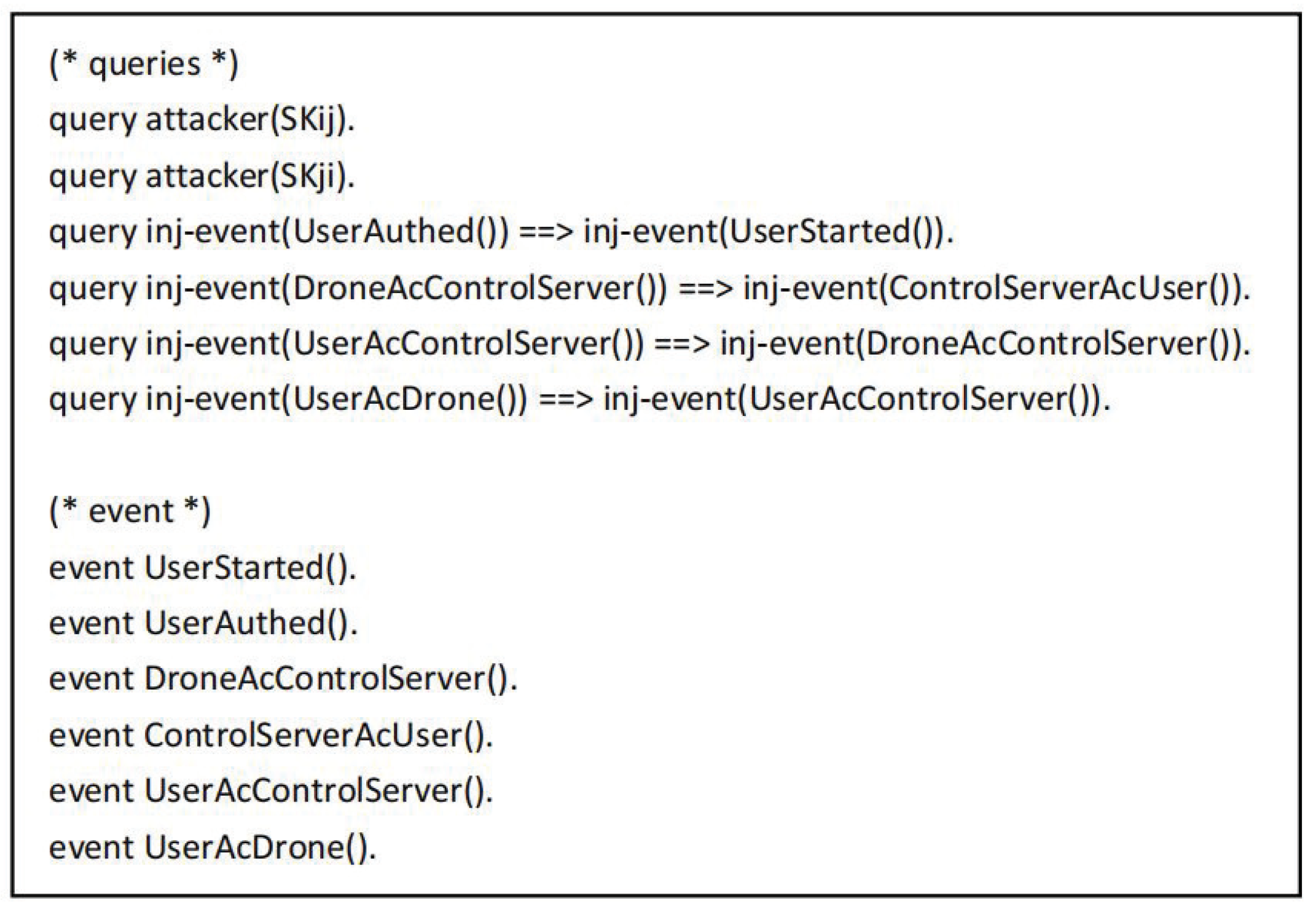
The symbols used in the proof process are defined as shown in Figure 5. The “” and “” refer to the secure channel and the common channel. The functions used mainly include , and , which represent the hash operation, XOR operation and join operation, respectively. Figure 6 shows the defined queries and events. Here, and represent the common session keys of the user and the drone, respectively. The event indicates that the user starts working, the event indicates that the user is authenticated, the event indicates that the control server authenticates the user event, the event indicates that the drone authenticates the control server event, the event indicates that the user authenticates the control server event, and the event means that the user authenticates the drone event.

Figure 5.
The definition of the proposed protocol in the ProVerif tool.
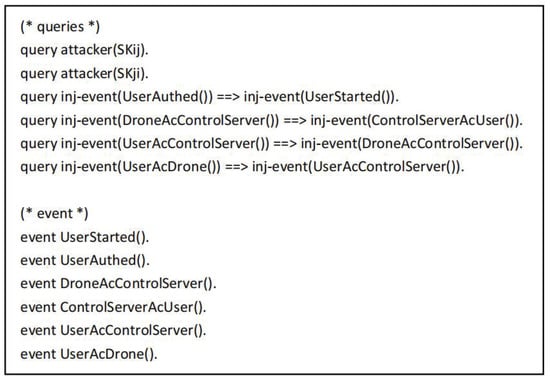
Figure 6.
The queries and events in the ProVerif tool.
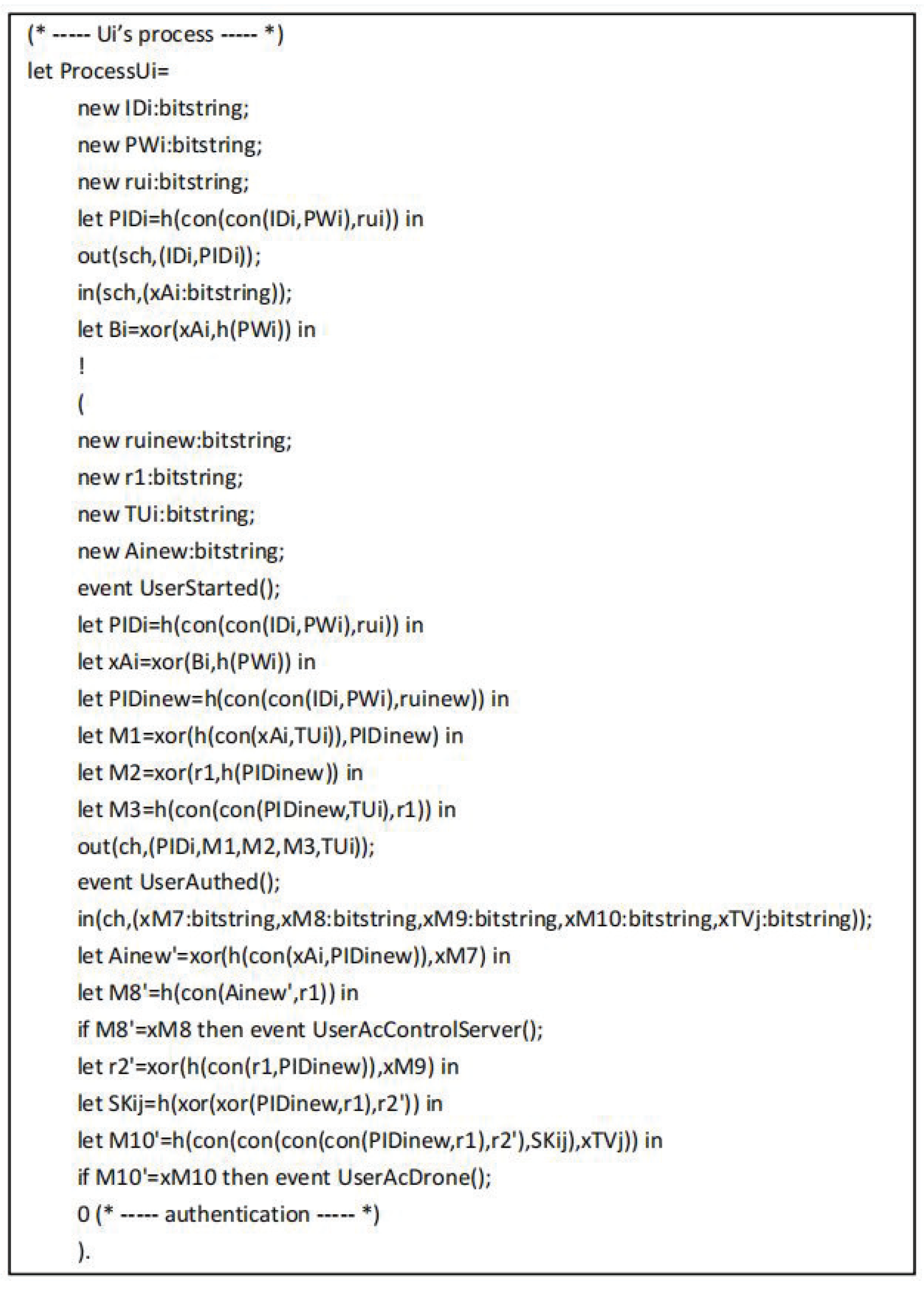
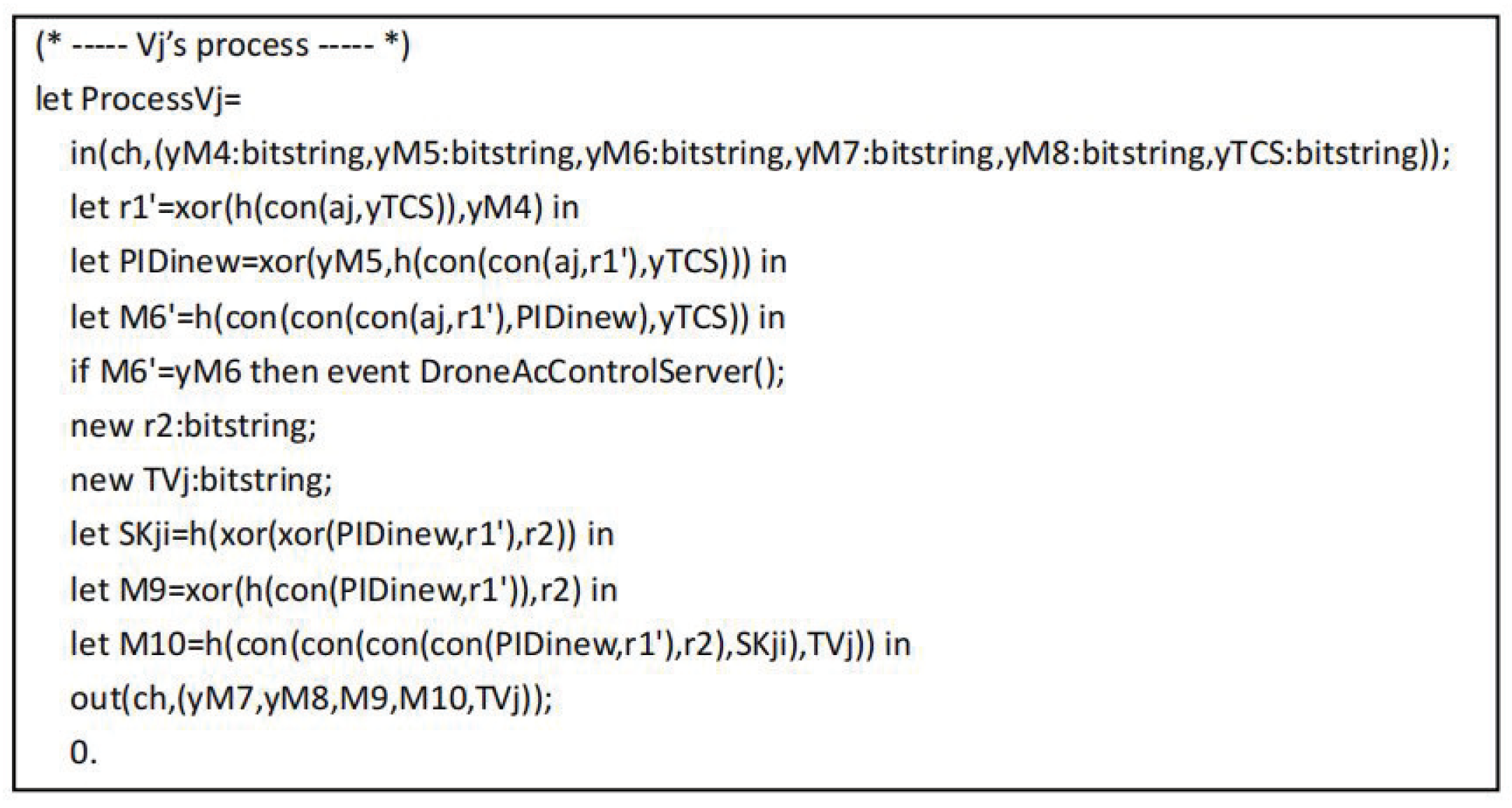
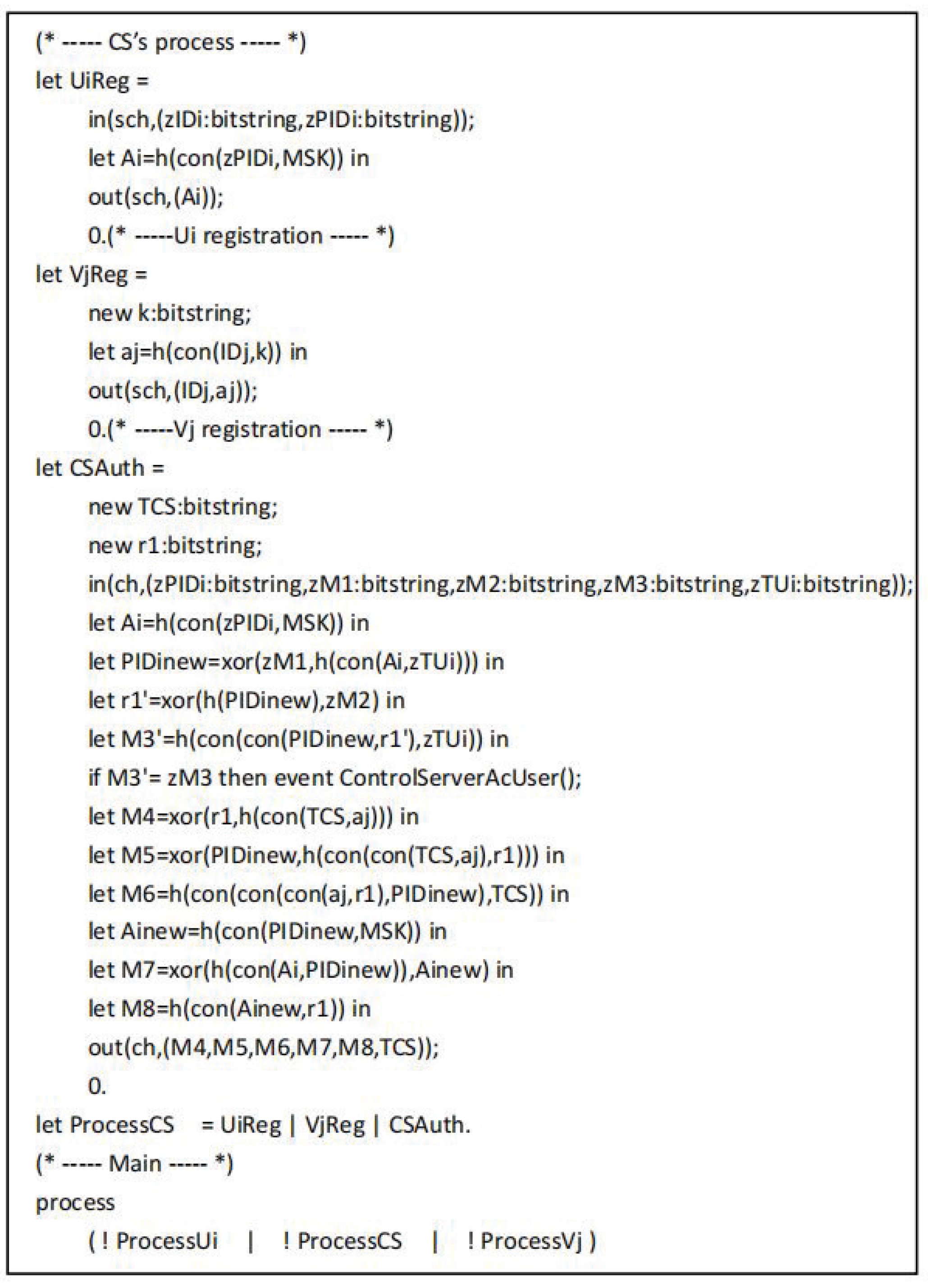
The tripartite agreement of user , drone and control server are converted into ProVerif code as shown in Figure 7, Figure 8 and Figure 9, respectively. In the working process of , and represent the messages sent and received by through the secure channel during the registration phase. After completing the registration, starts authentication by executing the event UserStarted(). Next, represents the message is transmitted from to over the common channel, represents the message is transmitted from to over the common channel. In addition, the working process of includes for registration by , for registration by , and means the authentication operation of .

Figure 7.
The process of .

Figure 8.
The process of .

Figure 9.
The process of .
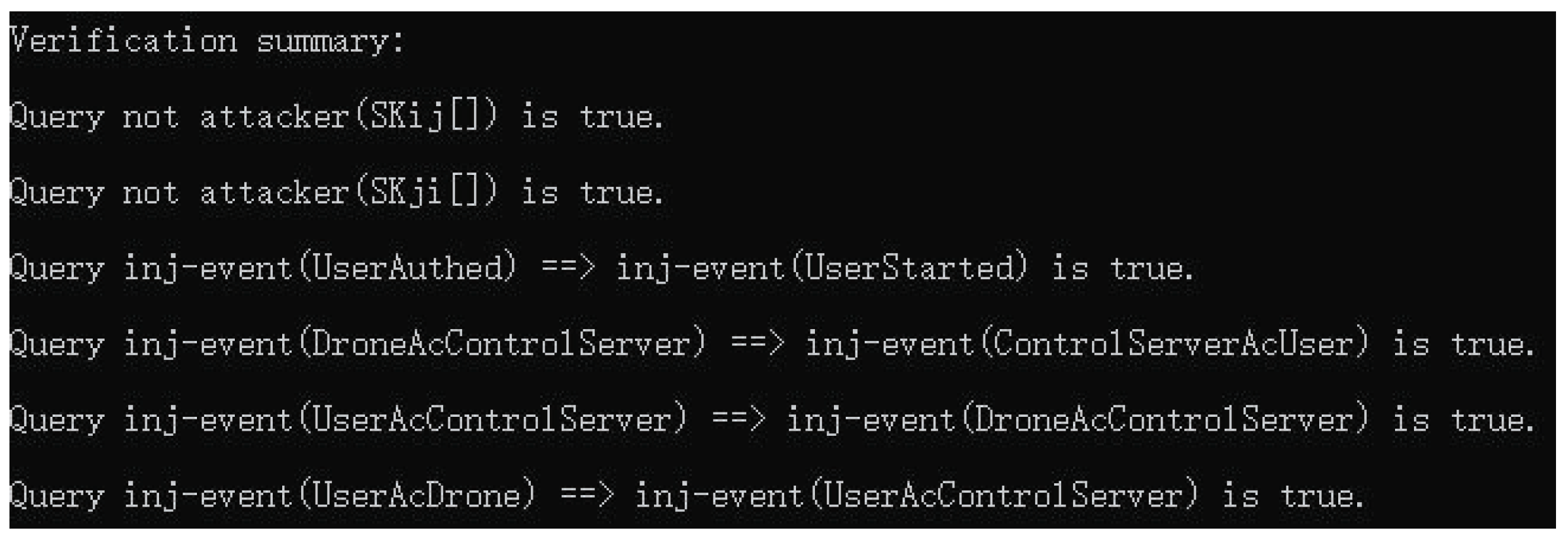
Finally, the results of the execution of the ProVerif code are shown in Figure 10. Based on the results of Figure 10, it shows that the sequence of events is normal and it can be proved that the attacker cannot derive the common session key shared among and during IoD communications.
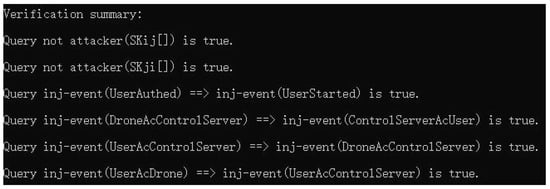
Figure 10.
ProVerif results.
4.2. BAN Logic Analysis
In the proposed scheme, when the mobile device wants to communicate with the flying drone, they must authenticate each other. In the following description, we use the BAN logic model to prove the security of the proposed scheme. The notation of BAN logic is described as follows:
- -:
- P believes X or P would be entitled to believe X.
- -:
- P sees X. Someone has sent a message containing X to P, who can read and repeat X.
- -:
- P has jurisdiction over X. P is an authority on X and should be trusted on this matter.
- -:
- P once said X. P at some time sent a message including X.
- -:
- This represents X combined with Y.
- -:
- The formula X is fresh, that is, X has not been sent in a message at any time before the current run of the protocol.
- -:
- P and Q may use the shared key K to communicate.
- -:
- The formula S is a secret known only to P and Q and possibly to principals trusted by them.
In the authentication and key-agreement phase of the proposed scheme, the main goal of our scheme is to authenticate the session key establishment between a mobile user and the flying drone .
- G1:
- G2:
- G3:
- G4:
- G5:
- G6:
According to the authentication and key agreement phase, we use BAN logic to produce an idealized form as follows:
- M1:
- M2:
To analyze the proposed scheme, we make the following assumptions:
- A1:
- A2:
- A3:
- A4:
- A5:
- A6:
- A7:
According to these assumptions and rules of BAN logic, we show the main proof of the session key establishment between a mobile user and the flying drone as follows:
Flying drone authenticates mobile device . By M1 and the seeing rule, we can derive:
- S1:
By A2 and the freshness rule, we can derive:
- S2:
By S1, A4 and the message meaning rule, we can derive:
- S3:
By S2, S3, and the nonce verification rule, we can derive:
- S4:
By S4 and the belief rule, we can derive:
- S5:
By S5, A6 and the jurisdiction rule, we can derive:
- S6:
By S6 and the belief rule, we can derive:
- S7:
By S7, A7 and the jurisdiction rule, we can derive:
- S8:
Mobile device authenticates flying drone . By M2 and the seeing rule, we can derive:
- S9:
By A1 and the freshness rule, we can derive:
- S10:
By S9, A3 and the message meaning rule, we can derive:
- S11:
By S10, S11, and the message meaning rule, we can derive:
- S12:
By S12, A5, and the jurisdiction rule, we can derive:
- S13:
By S5, S8, S12 and S13, it can be proved that, in our authentication scheme, the mobile device and the flying drone authenticate each other with the help of control server CS. In addition, we are also able to prove that the proposed scheme can establish a common session key SKij between the mobile device Ui and the remote flying drone Vj with the help of CS. Finally, the authentication and key agreement phase of our scheme thus guarantee the security of between and .
- Scenario:
- A malicious attacker uses an illegal flying drone to authenticate a legal mobile device .
- Analysis:
- The attacker will not succeed because the illegal flying drone has not been registered to the legal control server , and the illegal flying drone cannot calculate the correct session key . Thus, it will fail when the legal mobile device attempts to authenticate the illegal flying drone . In the proposed scheme, the attacker cannot achieve their purpose using an illegal flying drone . In the same scenario, the proposed scheme can also defend against a malicious attack using an illegal mobile device to connect to a legal flying drone . This is because the illegal mobile device has not been registered to the legal control server , and thus the illegal mobile device cannot calculate the correct session key SK. Therefore, the attack will fail when the legal flying drone attempts to authenticate the illegal mobile device .
4.3. Informal Security Analysis
In this subsection, we present the informal security analysis of the proposed scheme and show it can satisfy the following security features and attack resilience in IoD environments.
Proposition 1.
The proposed scheme ensures anonymous interactions between , and and no adversaries can ascribe any session to a particular user during authentication and key agreement phase.
Proof.
According to DY threat model defined in Section 2.2, an adversary can collect all the communication messages transmitted in IoD, such as , {}, and {}, which are communicated during the authentication and key agreement phase of the proposed scheme. From these messages, it is hard for to derive ’s real identity from without knowing the random number because is protected with cryptographic hash function . That is to say, ’s real identity are transmitted in cipher format instead of plaintext. Therefore, the user anonymity can be provided in the proposed authentication scheme. □
Proposition 2.
The proposed scheme ensures untraceability between a mobile user and the control server and also between a mobile and its associated drone.
Proof.
In the proposed authentication mechanism, the generation of messages {} incorporate the fresh random numbers , , and and the pseudonym ID and session key is updated after each successful authentication. As a result, it is impossible for to correlate the communicated messages from the current and previous AKA process and the proposed scheme can provide untraceability. □
Proposition 3.
The proposed scheme supports mutual authentication between any two communicating parties, and also between a drone and its associated .
Proof.
During the proposed authentication process as presented in Section 3.4, a drone verifies its associated ’s legitimacy before establishment of a session key. In the session, first checks the freshness of ’s login request by validating the timestamp in the messages . Later, checks to authenticate . When receiving {} from , checks and to authenticate and . If both the conditions are validated successfully, agrees a session key with . In the similar way, when receiving {}, checks and to authenticate and also agrees a session key with . Finally, the proposed scheme achieves mutual authentication and both and ensure that they shared the same session key with the help of for securing the future IoD communications. □
Proposition 4.
The proposed scheme is secure against session key exposure attack.
Proof.
After the successful authentication process, and can establish a common session key and the adversary may try to derive to damage the later IoD communications between them. However, in Step 1 of the authentication and key agreement phase, cannot get and from and without knowing the knowledge of . Similarity, in Step 5 of the authentication and key agreement phase, cannot obtain from without knowing the knowledge of . Therefore, cannot get success from session key disclosure attack in the proposed AKA scheme. □
Proposition 5.
The proposed scheme is resilient against known session key attack.
Proof.
It can be observed from Section 3.4 that the session key is the combination of both session-specific credential and two 160 bits random numbers and . Moreover, usage of session-specific credentials and random numbers in computation of session keys between and over different sessions make always-unique session keys. Even if a session key is disclosed for a specific session, it will not result in computing the session keys over other sessions. Thus, the contributed scheme is protected from known session key attack. □
Proposition 6.
The proposed scheme is protected against drone capture attack.
Proof.
According to CK adversary model defined in Section 2.2, an adversary may physically capture the drone in the sensing environment and maliciously extract the stored contents from its memory by using power analysis attacks. In this way, can get {} from the memory of compromised drone . By capturing , can only compromise the session key between a victim user and . Since all the identities and credentials for all are distinct in IoD network, cannot compromise other non-captured drone due to the distinct as well as uniqueness property of the contents stored in the remote drones. Finally, compromise of a drone does not result in damaging secure IoD communications among a user and other non-compromised drones and the contributed scheme is resilient against drone capture attack. □
Proposition 7.
The proposed scheme is secure against stolen device attack.
Proof.
Suppose an adversary somehow gets or steals the mobile device of user and extracts the stored contents {} from its memory by using power analysis attacks. Thus, can get access to IoD environment. However, cannot drive the valid secret credential due to the protection of ’s password. Moreover, the password is protected in the form of a one-way hash function which is a non-invertible function. Although can guess the password of , he/she cannot verify the correctness without having ’s identity and the login parameters of previous session. Therefore, the contributed scheme can resist stolen device attack. □
Proposition 8.
The proposed scheme is resilient secure against three kinds of impersonation attacks, including: user impersonation, impersonation and drone impersonation.
Proof.
The following impersonation attacks related to the contributed scheme are taken into account.
- (a)
- User impersonation attack: Let an adversary try to behave himeself/herself as a legitimate user and he/she wants to generate an authorized login request, say . can intercept the login request of and forge messages by extracting the important credential of to prove ’s authenticity. In order to perform this operation, needs to choose two random numbers and and a timestamp and computes , and . However, due to the lack of knowledge about , will fail to compute as valid login parameter. Therefore, the proposed scheme is secure against user impersonation attack.
- (b)
- impersonation attack: To perform this attack, we assume intercepts the message {} and generates a bogus message {} to the drone , to make and convince the message is from a legitimate , where is a timestamp generated by . However, does not have the knowledge of and , thus, and can distinguish the impersonated from real control server and the proposed scheme is secure against impersonation attack.
- (b)
- Drone impersonation attack: In this attack, will try to make believe by seizing the message {} and attempt to construct another legitimate message, which is authenticated to . First, randomly chooses a random number and a timestamp and tries to forge and . However, in the design process of the proposed AKA scheme, without having the knowledge of , and , cannot generate the valid convinced response to impersonate as an accurate drone.
□
5. Performance Evaluation
This section shows a detailed comparison among the proposed scheme and those of the most relevant state-of-the-art schemes in the IoD environment, such as the schemes of Singh et al. [30] and Zhang et al. [29] in terms of security features, computational and communication overheads.
5.1. Comparison of Security Features
We highlight on the comparison of security features and attacks protection of the contributed scheme against relevant schemes [29,30] in this section. It is clear from the Table 1 that the scheme of Singh et al. [30] is insecure against session key exposure attack, impersonation attack, drone capture attack and stolen device attack and Zhang et al. [29] is unprotected against session key exposure attack and impersonation attack. Furthermore, the scheme of Singh et al. [30] lacks mutual authentication, user anonymity and untraceability and Zhang et al. [29] does not provide user anonymity and untraceability. Therefore, the proposed AKA scheme can provide more security features and protect against all kinds of attack which makes it more suitable for generic secure communications in IoD-based environments.

Table 1.
Comparison of security features.
5.2. Comparison of Computational Overhead
In order to provide the analysis of the comparative computation overhead, the symbols listed in Table 2 with their executing time as per the experiment presented in [31] on a mobile (drone) device with 2.45 G processor and 2 GB memory, performed on the Android 4.4.2 operation system. The control server is simulated on a PC I5-4460S with 2.90 GHz processor and 4 GB memory, performed on Window 8 operation system:

Table 2.
Execution time of the various cryptographic operations.
As shown in Table 3, total computational overhead of the proposed scheme, the scheme of Singh et al. [30], Zhang et al. [29] is 27 1.022 ms, 4+12 9.092 ms, 24 1.001 ms, respectively. The computational overhead of the proposed scheme is slightly higher than Zhang et al., whereas the proposed scheme has less computational overhead as compared with the scheme of Singh et al. Moreover, the proposed scheme is more secure than the all rest of the related schemes as proved earlier.

Table 3.
Comparison of Computational Overhead.
5.3. Comparison of Communication Overhead
This section presents another significant performance factor, namely communication overhead, to demonstrate the efficiency of the proposed scheme. For comparison purposes and to keep simplicity, let denote the 1024 bits length of element in G and denote the 160 bits length of the element in . The symbol denotes a timestamp 32 bits in lengts and participant identities. We compare the communication overhead of different participants during the login and authentication phases, where the bits sent over communication channel and the number of messages transmitted between them are also considered.
As shown in Table 4, the number of transmitted messages in Singh et al. scheme are from user side and from drone side, where are 32-bit timestamps and are 32-bit user identities. Therefore, the total communication cost of Singh et al. scheme is 4+4 about 4256 bits. In addition, the number of transmitted messages in Zhang et al. scheme are from user side, from control server side and from drone side, where and is a 32-bit timestamp. Thus the total communication cost of Zhang et al. scheme is 9+ about 1472 bits. In the proposed scheme, three message transmissions complete the authentication and key agreement process: (1) user sends {} to ; this consumes {160 + 160 + 160 + 160 + 32} = 672 bits, and (2) control server sends {} to , consuming {160 + 160 + 160 + 160 + 160 + 32} = 832 bits, and (3) drone sends {} to , which also needs {160 + 160 + 160 + 160 + 32} = 672 bits. Therefore, the total communication cost of the proposed scheme is 13+3, about 2176 bits.

Table 4.
Comparison of Communication Overhead.
6. Conclusions
In this paper, we proposed a lightweight hash-based authenticated key agreement and privacy preservation scheme without using symmetric/asymmetric cryptographic operations for IoD environments. The proposed scheme is a three-party AKA mechanism, which enables mobile users to communicate securely, through the public communication channel, with the IoD participants such as control server and drones. Moreover, the proposed scheme can provide anonymity and untraceability of the participants in IoD. We proved the security of the proposed scheme formally through the ProVerif tool and BAN logic analysis as well as informally. The comparative analysis depicts that the proposed scheme achieves better trade-off among security features, computational overhead and communication cost. From the results, it is concluded that the proposed scheme not only supports more security features but is also suitable for the drones or resource-constrained sensing devices in the IoD environments.
Author Contributions
Conceptualization, C.-T.L. and C.-Y.W.; methodology, C.-T.L. and Y.-Y.D.; software, C.-L.C.; validation, C.-T.L., C.-Y.W. and C.-L.C.; formal analysis, C.-C.L. and A.L.I.; investigation, Y.-Y.D.; resources, Y.-Y.D.; data curation, C.-L.C. and A.L.I.; writing—original draft preparation, C.-T.L.; writing—review and editing, C.-L.C. and A.L.I.; visualization, C.-C.L.; supervision, C.-C.L.; project administration, C.-T.L.; funding acquisition, C.-C.L. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Science and Technology Council, Taiwan, R.O.C., under contract no.: MOST 110-2410-H-165-001-MY2.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
The work of Agbotiname Lucky Imoize is supported in part by the Nigerian Petroleum Technology Development Fund (PTDF) and in part by the German Academic Exchange Service (DAAD) through the Nigerian-German Postgraduate Program under grant 57473408.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Chen, C.L.; Deng, Y.Y.; Li, C.T.; Zhu, S.; Chiu, Y.J.; Chen, P.Z. An IoT-based traceable drug anti-counterfeiting management system. IEEE Access 2017, 8, 224532–224548. [Google Scholar] [CrossRef]
- Altawy, R.; Youssef, A.M. Security, Privacy, and Safety Aspects of Civilian Drones: A Survey. ACM Trans. Cyber-Phys. Syst. 2016, 1, 1–25. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Alsharif, M.H.; Alghtani, A.H.; Aly, A.A.; Chen, C.M. An Efficient Certificate-Based Aggregate Signature Scheme for Internet of Drones. Secur. Commun. Netw. 2022, 2022, 9718580. [Google Scholar] [CrossRef]
- Lilhore, U.K.; Imoize, A.L.; Li, C.T.; Simaiya, S.; Pani, S.K.; Goyal, N.; Kumar, A.; Lee, C.C. Design and Implementation of an ML and IoT Based Adaptive Traffic-Management System for Smart Cities. Sensors 2022, 22, 2908. [Google Scholar] [CrossRef] [PubMed]
- Sedjelmaci, H.; Senouci, S.M. Cyber security methods for aerial vehicle networks: Taxonomy, challenges and solution. J. Supercomput. 2018, 74, 4928–4944. [Google Scholar] [CrossRef]
- Shi, X.; Yang, C.; Xie, W.; Liang, C.; Shi, Z.; Chen, J. Anti-Drone System with Multiple Surveillance Technologies: Architecture, Implementation, and Challenges. IEEE Commun. Mag. 2018, 56, 68–74. [Google Scholar] [CrossRef]
- Wu, T.; Guo, X.; Chen, Y.; Kumari, S.; Chen, C. Amassing the Security: An Enhanced Authentication Protocol for Drone Communications over 5G Networks. Drones 2022, 6, 10. [Google Scholar] [CrossRef]
- Yaacoub, J.P.; Noura, H.; Salman, O.; Chehab, A. Security analysis of drones systems: Attacks, limitations, and recommendations. Internet Things 2020, 11, 100218. [Google Scholar] [CrossRef]
- Shakhatreh, H.; Sawalmeh, A.H.; Al-Fuqaha, A.; Dou, Z.; Almaita, E.; Khalil, I.; Othman, N.S.; Khreishah, A.; Guizani, M. Unmanned Aerial Vehicles (UAVs): A Survey on Civil Applications and Key Research Challenges. IEEE Access 2019, 7, 48572–48634. [Google Scholar] [CrossRef]
- Straub, J. Unmanned aerial systems: Consideration of the use of force for law enforcement applications. Technol. Soc. 2014, 39, 100–109. [Google Scholar] [CrossRef]
- Cook, K.L.B. The Silent Force Multiplier: The History and Role of UAVs in Warfare. In Proceedings of the 2007 IEEE Aerospace Conference, Big Sky, MT, USA, 3–10 March 2007; pp. 1–7. [Google Scholar]
- Horsman, G. Unmanned aerial vehicles: A preliminary analysis of forensic challenges. Digit. Investig. 2016, 16, 1–11. [Google Scholar] [CrossRef]
- Lee, C.C.; Lai, Y.M.; Li, C.T. Two attacks on a two-factor user authentication in wireless sensor networks. Parallel Process. Lett. 2011, 21, 21–26. [Google Scholar] [CrossRef]
- Li, C.T.; Yang, C.C.; Hwang, M.S. A secure routing protocol with node selfishness resistance in MANETs. Int. J. Mob. Commun. 2012, 10, 103–118. [Google Scholar] [CrossRef]
- Chen, C.M.; Li, C.T.; Liu, S.; Wu, T.Y.; Pan, J.S. A Provable Secure Private Data Delegation Scheme for Mountaineering Events in Emergency System. IEEE Access 2017, 5, 3410–3422. [Google Scholar] [CrossRef]
- Gaikwad, V.P.; Tembhurne, J.V.; Meshram, C.; Lee, C.C.; Li, C.T. An Efficient Provably Secure Verifier-Based Three-Factor Authentication Technique Using PDL for Data Exchange in TMIS. IEEE Access 2021, 9, 108586–108600. [Google Scholar] [CrossRef]
- Hong, S. Authentication techniques in the Internet of Things environment: A survey. Int. J. Netw. Secur. 2019, 21, 462–470. [Google Scholar]
- Jiang, Q.; Kumar, N.; Ma, J.; Shen, J.; He, D.; Chilamkurti, N. A privacy-aware two-factor authentication protocol based on elliptic curve cryptography for wireless sensor networks. Int. J. Netw. Manag. 2017, 27, e1937. [Google Scholar] [CrossRef]
- Lee, C.C.; Lai, Y.M.; Li, C.T. An improved secure dynamic ID based remote user authentication scheme for multi-server environment. Int. J. Secur. Its Appl. 2012, 6, 203–209. [Google Scholar]
- Li, C.T.; Hwang, M.S.; Chu, Y.P. Further improvement on a novel privacy preserving authentication and access control scheme for pervasive computing environments. Comput. Commun. 2008, 3, 4255–4258. [Google Scholar] [CrossRef]
- Li, C.T.; Lee, C.C.; Liu, C.J.; Lee, C.W. A robust remote user authentication scheme against smart card security breach. In IFIP Annual Conference on Data and Applications Security and Privacy; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6818, pp. 231–238. [Google Scholar]
- Weng, C.Y.; Li, C.T.; Chen, C.L.; Lee, C.C.; Deng, Y.Y. A Lightweight Anonymous Authentication and Secure Communication Scheme for Fog Computing Services. IEEE Access 2021, 9, 145522–145537. [Google Scholar] [CrossRef]
- Yang, C.; Li, C. Design of key management protocols for Internet of Things. Int. J. Netw. Secur. 2020, 22, 476–485. [Google Scholar]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreeement scheme for heterogeneous ad hoc wireless sensor netwroks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Farash, M.S.; Turkanović, M.; Kumari, S.; Hölbl, M. An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the Internet of Things environment. Ad Hoc Netw. 2016, 36, 152–176. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.P.C. Design and analysis of secure lightweight remote user authentication and key agreement scheme in Internet of Drones deployment. IEEE Internet Things J. 2019, 6, 3572–3584. [Google Scholar] [CrossRef]
- Lei, Y.; Zeng, L.; Li, Y.X.; Wang, M.X.; Qin, H. A Lightweight Authentication Protocol for UAV Networks Based on Security and Computational Resource Optimization. IEEE Access 2021, 9, 53769–53785. [Google Scholar] [CrossRef]
- Rodrigues, M.; Amaro, J.; Osrio, F.S.; Kalinka, R.L.J.C. Authentication Methods for UAV Communication. In Proceedings of the 2019 IEEE Symposium on Computers and Communications, Barcelona, Spain, 29 June–3 July 2019; pp. 1210–1215. [Google Scholar]
- Zhang, Y.; He, D.; Li, L.; Chen, B. A lightweight authentication and key agreement scheme for Internet of Drones. Comput. Commun. 2020, 154, 455–464. [Google Scholar] [CrossRef]
- Singh, J.; Gimekar, A.; Venkatesan, S. An efficient lightweight authentication scheme for human-centered industrial Internet of Things. Int. J. Commun. Syst. 2019, e4189. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kumar, N.; Wu, W. Efficient and Anonymous Mobile User Authentication Protocol Using Self-Certified Public Key Cryptography for Multi-Server Architectures. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2052–2064. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).