A Traceable Vaccine Supply Management System
Abstract
:1. Introduction
1.1. Background
- The records generated from the manufacture, procurement, distribution, and vaccination up to the diagnosis of vaccine side effects and the identity information of each player will be permanently stored in the blockchain system. All information is guaranteed with integrity and security. In addition, each user in the system can trace the corresponding records based on his or her identity, ensuring the transparency of the whole system.
- The use of Burrows-Abadi-Needham (BAN) logic ensures that two unfamiliar nodes confirm each other’s identity, ensuring the authenticity of each other’s identity and the trustworthiness of the information exchanged between nodes.
- The system using blockchain can resist potential risks, such as replay attacks and man-in-the-middle attacks.
1.2. Related Works
2. Preliminary
2.1. Smart Contract
2.2. EdDSA
2.3. BAN Logic
2.4. Security Requirements
- Mutual authentication: The exchange of data is necessary for the operation of the system. To guarantee the security and privacy of the exchanged information, both parties need to authenticate the identity of the other node.
- Integrity: The integrity of the data exchanged throughout the vaccine management system should be ensured to prevent possible data tampering and loss.
- High-quality random number: The system needs to generate high-quality random numbers to ensure that the digital signature is not easily forged, thereby ensuring the security of the whole system.
- Non-repudiation: Each node should not deny its actions and send messages.
- Man-in-the-Middle Attacks: Illegal third-party nodes intercept and obtain the messages being exchanged between two communicating parties in some way.
- Replay attack: The attacker pretends to be a legitimate message sender and sends a message to the receiving node that it has received. This process can easily cause the disclosure of node identity information.
- Sybil attack: Sybil attack is an online network security system threat in which an attacker attempts to control a network by creating multiple fake account identities, multiple nodes, or computer coordinates.
3. Method
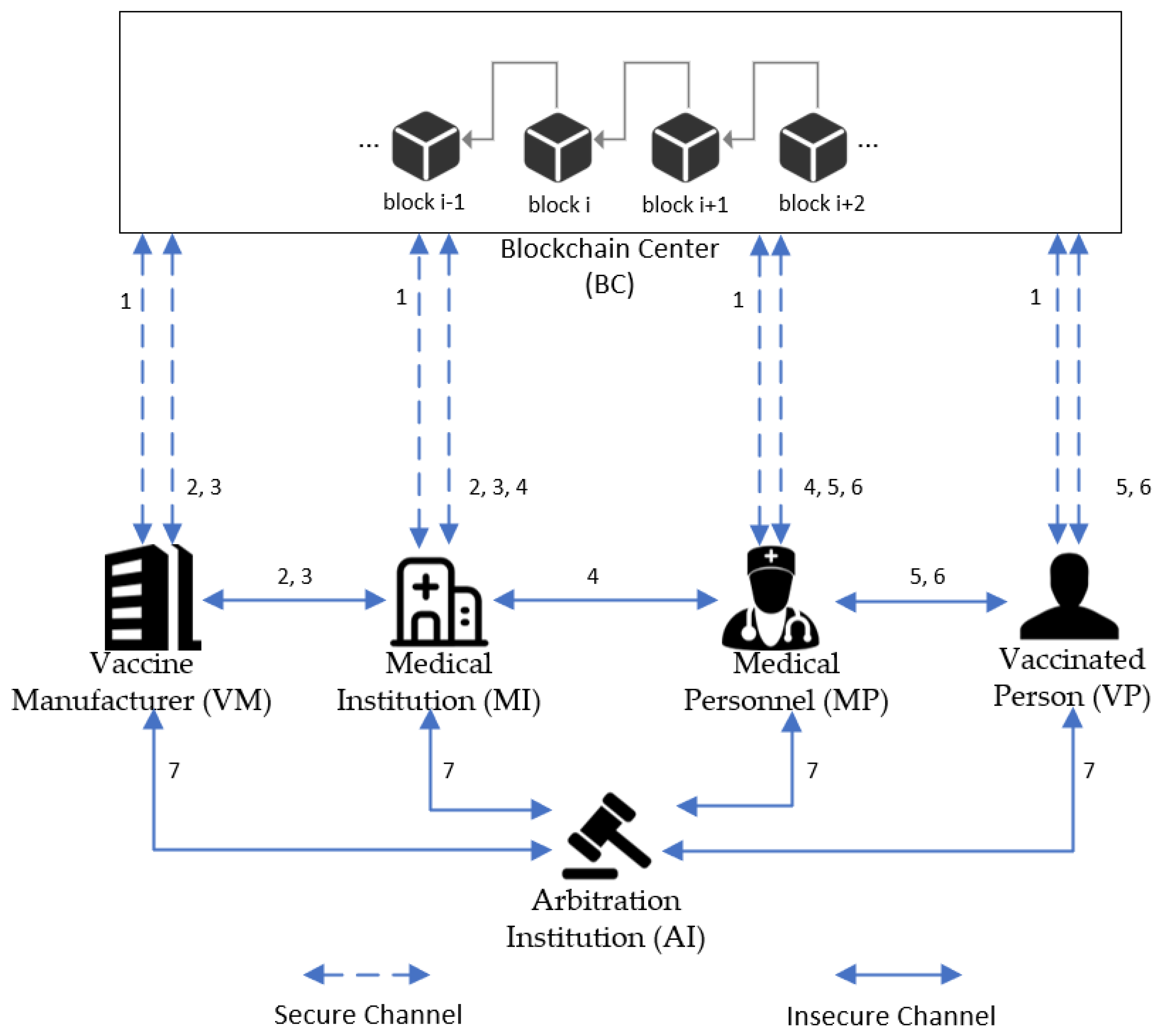
3.1. System Architecture
- Blockchain Center (BC): The blockchain center keeps most of the important information during the operation of the whole system. The registration of all nodes and the generation of public and private key pairs are done by this role. The mutual authentication between nodes will also be realized through the blockchain.
- Vaccine Manufacturer (VM): A vaccine manufacturer is generally a third-party company that is qualified to manufacture vaccines. The vaccine is produced according to the vaccine procurement requirements of the medical institution. The vaccine manufacturer distributes the vaccine to the appropriate medical institutions in agreement with the medical institution. Moreover, it has regulatory responsibility for the transportation process.
- Medical Institution (MI): Medical institutions purchase vaccines according to the targets given by the government. Upon receipt of the vaccine from the vaccine manufacturer, the medical institution is required to confirm the eligibility of the vaccine and store the vaccine. When the vaccine is about to be used, the medical institution needs to distribute the vaccine to the medical staff responsible for the vaccination.
- Medical Personnel (MP): Medical personnel must be employed at the appropriate medical institution and have medical vaccination capabilities. After receiving the vaccines to be vaccinated on the day, medical personnel need to inoculate the vaccinated person.
- Vaccinated Person (VP): Vaccinated persons are the group of people who are currently suitable for vaccination. Before vaccination, medical personnel will determine whether the vaccinated persons are eligible for vaccination by scanning the QR code. If vaccinated persons have some adverse reactions after vaccination, they will be required to submit details of the adverse reactions for further diagnosis.
- Arbitration Institution (AI): In the case of a medical dispute that is difficult to reconcile, the arbitration institution will make a corresponding decision.
- Step 1
- Each role needs to register through the BC and obtain its corresponding public and private key pairs.
- Step 2
- The MI submits a vaccine request to a confirmed VM. Upon receiving the request, the VM verifies the identity of the MI. After confirming that the identity is correct, the VM starts to produce the vaccine and uploads the relevant data (vaccine lot number, vaccine manufacturer id, vaccine shelf life, etc.).
- Step 3
- Once the vaccine is made, the VM uploads the vaccine information to the BC and transports the vaccine to the corresponding MI. The vaccine transportation process requires strict compliance with transportation rules, such as the storage temperature range for each vaccine and the transport time requirements. After receiving the vaccine, the MI needs to verify that the vaccine information is correct. All related records need to be uploaded to the blockchain.
- Step 4
- MI needs to store vaccines after receiving them. Storage rules include a temperature between 2 °C and 8 °C, storage time cannot be longer than the remaining shelf life of the vaccine, etc. The information generated during storage needs to be uploaded to the BC. Then, the MI distributes the vaccine to be administered to qualified MP. After receiving the vaccine, the MP needs to confirm that the records related to the vaccine are accurate. Finally, the records in the blockchain are updated again.
- Step 5
- The VP goes to the vaccination site and submits his or her personal information and vaccination status to the MP before the vaccination. Vaccination can be carried out only after the MP has verified the information of the VP and confirmed that the VP is suitable for vaccination. After a vaccination is finished, the MP is required to update the vaccination information of the VP. The VP confirms that the vaccination information is correct. Then, the relevant records in BC will be updated.
- Step 6
- If a VP experiences side effects after receiving the vaccine, the VP must first provide the MP with his or her personal information, vaccination status, and details of the adverse reaction. After verifying the identity of the VP, the MP determines whether the adverse reaction is a vaccination side effect. If the adverse reaction is confirmed to be caused by the vaccination, the relevant records are uploaded to the BC. Meanwhile, the VP will receive further treatment.
- Step 7
- In the case of irreconcilable disputes throughout the system process, the arbitration department will obtain information from various parties for adjudication.
3.2. Notation
| The identity of | |
| The certificate of | |
| A k-bit prime number | |
| Finite group | |
| The elliptic curve defined on finite group | |
| A generating point based on | |
| An integer with | |
| The th bit of the hash value | |
| An integer with | |
| The EdDSA private key and public key of | |
| The EdDSA signature of | |
| The public key and private key of | |
| The message from | |
| Encrypted the message M with the public key of | |
| Decrypted the message M with the private key of | |
| One-way hash function | |
| The random value of based on | |
| Timestamp message of | |
| The threshold for checking the validity of timestamps | |
| Verify whether A is equal to B |
3.3. Initial Phase
3.4. Registration Phase
- Step 1: Each AP sends basic information about itself (e.g., role ID) to the BC.
- Step 2: The BC uses the EdDSA algorithm to generate a private key , then calculates and the corresponding public key by the following:
| Algorithm 1: The smart contract of registration. |
- Step 3: The AP stores the for later signature and verification.
3.5. EdDSA Authentication Phase
- Step 1: Role A calculates a random number by encrypting the sent message with the high bits of the hash of the private key:
| Algorithm 2: The process of the EdDSA signature between role A and role B. |
- Step 2: After receiving the message, role B first decrypts the message using its private key :
- Step 3: Firstly, role A decrypts the message using its private key :
| Algorithm 3: The process of EdDSA verification between role A and role B. |
3.6. Vaccine Purchasing Phase
- Step 1: MI sends a message to VM. needs to include the required vaccine details of the MI’s beside the primary information. Then, the MI calculates a random number by encrypting with the high bits of the hash of the private key:
- Step 2: After receiving the message, VM first decrypts the message using its private key :
- Step 3: First, MI decrypts the message using its private key :
3.7. Vaccine Transport Phase
- Step 1: VM sends a message to MI. needs to include the vaccine lot number , the vaccine transport details , and the primary information. Then, MI calculates a random number by encrypting with the high bits of the hash of the private key:
- Step 2: After receiving the message, MI first decrypts the message using its private key :
- Step 3: First, VM decrypts the message using its private key :
3.8. Vaccine Distributing Phase
- Step 1: MI sends a message to MP. needs to include the vaccine lot number , the vaccine storage details in MI , and the primary information. Then, MI calculates a random number by encrypting with the high bits of the hash of the private key:
- Step 2: After receiving the message, MP first decrypts the message using its private key :
- Step 3: First, MI decrypts the message using its private key :
3.9. Vaccination Phase
- Step 1: VP sends a message to MP. needs to include the vaccination certificate of the VP , the VP details , and the primary information. Then, VP calculates a random number by encrypting with the high b bits of the hash of the private key:
- Step 2: After receiving the message, MP first decrypts the message using its private key :
- Step 3: First, VP decrypts the message using its private key :
3.10. Side Effect Phase
- Step 1: VP sends a message to MP. needs to include the vaccination certificate of VP , the VP details , the description of side effects , and the primary information. Then, VP calculates a random number by encrypting with the high bits of the hash of the private key:
- Step 2: After receiving the message, MP first decrypts the message using its private key :
- Step 3: First, VP decrypts the message using its private key :
4. Security Analysis
4.1. Mutual Authentication
| believes | |
| sees | |
| said | |
| controls | |
| The message is fresh | |
| and communicate with a shared key | |
| is encrypted with a key |
- Role B authenticates role A.The statement can be derived from the seeing rule:The statement can be derived from and the freshness rule:The statement can be derived from , and the message meaning rule:The statement can be derived by , and the nonce verification rule:The statement can be derived from and the belief rule:The statement can be derived from , and the jurisdiction rule:The statement can be derived from and the belief rule:The statement can be derived from , and the belief rule:
- Role A authenticates role B.The statement can be derived from and the seeing rule:The statement can be derived from and the freshness rule:The statement can be derived from , and the message meaning rule:The statement can be derived by , and the nonce verification rule:The statement can be derived from and the belief rule:The statement can be derived from , and the jurisdiction rule:The statement can be derived from and the belief rule:The statement can be derived from , and the belief rule:
4.2. Decentralization and Information Sharing
4.3. Traceable
4.4. High-Quality Random Number
4.5. Integrity and Non-Repudiation
4.6. Man-in-the-Middle Attacks
4.7. Replay Attack
4.8. Sybil Attack
5. Discussion
5.1. Computation Cost
5.2. Comparison
5.3. Performance Analysis
5.4. Comparison of Blockchain Platforms
6. Conclusions
- Blockchain technology and smart contracts are used to ensure the security and traceability of vaccines from manufacturing, distribution, vaccination, and side-effect reporting. The system protects the privacy of each role while providing certain information about the vaccine based on the role’s identity.
- The entire vaccine supply management system architecture and usage scenarios are presented.
- The use of the EdDSA algorithm for digital signatures not only guarantees the integrity of vaccine-related records but also improves the security and efficiency of digital signatures.
- Use BAN logic to guarantee mutual authentication between unfamiliar nodes.
- Analyzed the potential security risks of the system.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nardo, D. The Black Death; Greenhaven Publishing LLC: New York, NY, USA, 2011; pp. 76–77. [Google Scholar]
- Taubenberger, J.K.; Morens, D.M. 1918 Influenza: The mother of all pandemics. Rev. Biomed. 2006, 17, 69–79. [Google Scholar] [CrossRef]
- Henderson, D.A.; Moss, B. Smallpox and Vaccinia; Saunders: Yorba Linda, CA, USA, 1999. [Google Scholar]
- Roos, D. How 5 of History’s Worst Pandemics Finally Ended; History News Network: Seattle, WA, USA, 2020. [Google Scholar]
- World Health Organization. Global Vaccine Safety Blueprint; World Health Organization: Geneva, Switzerland, 2012. [Google Scholar]
- Chen, R.T.; Shimabukuro, T.T.; Martin, D.B.; Zuber, P.L.; Weibel, D.M.; Sturkenboom, M. Enhancing vaccine safety capacity globally: A lifecycle perspective. Vaccine 2015, 33, D46–D54. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Almagrabi, A.O.; Ali, R.; Alghazzawi, D.; AlBarakati, A.; Khurshaid, T. Blockchain-as-a-utility for next-generation healthcare internet of things. CMC Comput. Mater. Contin. 2021, 68, 359–376. [Google Scholar] [CrossRef]
- Imran, M.; Zaman, U.; Imtiaz, J.; Fayaz, M.; Gwak, J. Comprehensive survey of iot, machine learning, and blockchain for health care applications: A topical assessment for pandemic preparedness, challenges, and solutions. Electronics 2021, 10, 2501. [Google Scholar] [CrossRef]
- Gordon, W.J.; Catalini, C. Blockchain technology for healthcare: Facilitating the transition to patient-driven interoperability. Comput. Struct. Biotechnol. J. 2018, 16, 224–230. [Google Scholar] [CrossRef]
- Chen, S.; Wu, Z.; Christofides, P.D. Cyber-security of centralized, decentralized, and distributed control-detector architectures for nonlinear processes. Chem. Eng. Res. Des. 2021, 165, 25–39. [Google Scholar] [CrossRef]
- Mbunge, E.; Dzinamarira, T.; Fashoto, S.G.; Batani, J. Emerging technologies and COVID-19 digital vaccination certificates and passports. Public Health Pract. 2021, 2, 100136. [Google Scholar] [CrossRef]
- Ganty, S. The veil of the COVID-19 vaccination certificates: Ignorance of poverty, injustice towards the poor. Eur. J. Risk Regul. 2021, 12, 343–354. [Google Scholar] [CrossRef]
- Kamerow, D. Immunized? There’s an app for that. BMJ 2021, 372, n85. [Google Scholar] [CrossRef]
- Karopoulos, G.; Hernandez-Ramos, J.L.; Kouliaridis, V.; Kambourakis, G. A survey on digital certificates approaches for the covid-19 pandemic. IEEE Access 2021, 9, 138003–138025. [Google Scholar] [CrossRef]
- Ministry of Health, Labour and Welfare. Available online: https://www.mhlw.go.jp/stf/covid-19/certificate.html (accessed on 20 December 2021).
- Hernández-Ramos, J.L.; Karopoulos, G.; Geneiatakis, D.; Martin, T.; Kambourakis, G.; Fovino, I.N. Sharing pandemic vaccination certificates through blockchain: Case study and performance evaluation. Wirel. Commun. Mob. Comput. 2021, 2021, 1530–8669. [Google Scholar] [CrossRef]
- World Health Organization. Available online: https://www.who.int/news-room/articles-detail/world-health-organization-open-call-for-nomination-of-experts-to-contribute-to-the-smart-vaccination-certificate-technical-specifications-and-standards-application-deadline-14-december-2020 (accessed on 2 December 2020).
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. [Google Scholar]
- Zhou, L.; Wang, L.; Sun, Y. MIStore: A blockchain-based medical insurance storage system. J. Med. Syst. 2018, 42, 1–17. [Google Scholar] [CrossRef] [Green Version]
- Zhang, P.; White, J.; Schmidt, D.C.; Lenz, G.; Rosenbloom, S.T. FHIRChain: Applying blockchain to securely and scalably share clinical data. Comput. Struct. Biotechnol. J. 2018, 16, 267–278. [Google Scholar] [CrossRef] [PubMed]
- Uddin, M.; Salah, K.; Jayaraman, R.; Pesic, S.; Ellahham, S. Blockchain for drug traceability: Architectures and open challenges. Health Inform. J. 2021, 27, 4571–4579. [Google Scholar] [CrossRef]
- European Parliamentary Research Service. Available online: https://www.europarl.europa.eu/thinktank/en/document/EPRS_IDA(2020)641543 (accessed on 22 April 2020).
- Mettler, M. Blockchain technology in healthcare: The revolution starts here. In Proceedings of the 2016 IEEE 18th International Conference on E-Health Networking, Applications and Services (Healthcom), Munich, Germany, 14–16 September 2016. [Google Scholar] [CrossRef]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. Medrec: Using blockchain for medical data access and permission management. In Proceedings of the 2016 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016. [Google Scholar] [CrossRef]
- Kumar, M.; Chand, S. MedHypChain: A patient-centered interoperability hyperledger-based medical healthcare system: Regulation in COVID-19 pandemic. J. Netw. Comput. Appl. 2021, 179, 102975. [Google Scholar] [CrossRef]
- Kumar, R.; Tripathi, R. A Secure and Distributed Framework for sharing COVID-19 patient Reports using Consortium Blockchain and IPFS. In Proceedings of the 2020 Sixth International Conference on Parallel, Distributed and Grid Computing (PDGC), Waknaghat, India, 6–8 November 2020. [Google Scholar] [CrossRef]
- Sigwart, M.; Borkowski, M.; Peise, M.; Schulte, S.; Tai, S. Blockchain-based data provenance for the Internet of Things. In Proceedings of the 9th International Conference on the Internet of Things, Bilbao, Spain, 22–25 October 2019. [Google Scholar] [CrossRef] [Green Version]
- Yong, B.; Shen, J.; Liu, X.; Li, F.; Chen, H.; Zhou, Q. An intelligent blockchain-based system for safe vaccine supply and supervision. Int. J. Inf. Manag. 2020, 52, 102024. [Google Scholar] [CrossRef]
- Ricci, L.; Maesa, D.D.F.; Favenza, A.; Ferro, E. Blockchains for covid-19 contact tracing and vaccine support: A systematic review. IEEE Access 2021, 9, 37936–37950. [Google Scholar] [CrossRef]
- Deka, S.K.; Goswami, S.; Anand, A. A blockchain-based technique for storing vaccination records. In Proceedings of the 2020 IEEE Bombay section signature conference (IBSSC), Mumbai, India, 4–6 December 2020. [Google Scholar] [CrossRef]
- Antal, C.; Cioara, T.; Antal, M.; Anghel, I. Blockchain platform for COVID-19 vaccine supply management. IEEE Open J. Comput. Soc. 2021, 2, 164–178. [Google Scholar] [CrossRef]
- Chauhan, H.; Gupta, D.; Gupta, S.; Singh, A.; Aljahdali, H.M.; Goyal, N.; Noya, I.D.; Kadry, S. Blockchain Enabled Transparent and Anti-Counterfeiting Supply of COVID-19 Vaccine Vials. Vaccines 2021, 9, 1239. [Google Scholar] [CrossRef]
- Chen, J.; Chen, X.; Chen, C.L. A Traceable Blockchain-Based Vaccination Record Storage and Sharing System. J. Healthc. Eng. 2022, 2022, 2211065. [Google Scholar] [CrossRef] [PubMed]
- Szabo, N. Smart contracts: Building blocks for digital markets. Extropy J. Transhumanist Thought 1996, 18, 28. [Google Scholar]
- Buterin, V. A next-generation smart contract, and decentralized application platform. White Pap. 2014, 3, 2-1. [Google Scholar]
- Bernstein, D.J.; Duif, N.; Lange, T.; Schwabe, P.; Yang, B.Y. High-speed high-security signatures. J. Cryptogr. Eng. 2012, 2, 77–89. [Google Scholar] [CrossRef] [Green Version]
- Josefsson, S.; Liusvaara, I. Edwards-curve digital signature algorithm (EdDSA). RFC 8032 2017. [Google Scholar] [CrossRef]
- Wang, D.I. Secure Implementation of ECDSA Signatures in Bitcoin. MSc Inf. Secur. 2014, 1–78. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. Proc. R. Soc. London. Math. Phys. Sci. 1989, 426, 233–271. [Google Scholar] [CrossRef]











| Phase | Sender | Receiver | Signature | Verification |
|---|---|---|---|---|
| Authentication Phase | A | B | ||
| B | A | |||
| Vaccine Purchasing Phase | MI | VM | ||
| VM | MI | |||
| Vaccine transport Phase | VM | MI | ||
| MI | VM | |||
| Vaccine Distributing Phase | MI | MP | ||
| MP | MI | |||
| Vaccination Phase | VP | MP | ||
| MP | VP | |||
| Side Effect Phase | VP | MP | ||
| MP | VP |
| Phase | 1st Party | 2nd Party |
|---|---|---|
| Authentication Phase | Role A: | Role B: |
| Vaccine Purchasing Phase | ||
| Vaccine Transport Phase | ||
| Vaccine Distributing Phase | ||
| Vaccination Phase | ||
| Side Effect Phase |
| Authors | Year | Objective | 1 | 2 | 3 | 4 | 5 | 6 |
|---|---|---|---|---|---|---|---|---|
| Sigwart et al. [27] | 2019 | Proposed the feasibility of blockchain application in the vaccine supply chain. | Y | N | Y | N | N | N |
| Yong et al. [28] | 2019 | Proposed to use of blockchain and machine learning to ensure vaccine safety. | Y | Y | Y | N | N | N |
| Deka et al. [30] | 2020 | Proposed to use of blockchain and IPFS to maintain personal vaccination records. | Y | Y | Y | N | N | N |
| Antal et al. [31] | 2021 | Proposed to use of smart contracts to monitor COVID-19 vaccine supply management. | Y | Y | N | N | N | Y |
| Chauhan et al. [32] | 2021 | Proposed to use of blockchain to ensure transparency and anti-counterfeiting of the COVID-19 vaccine. | Y | Y | N | N | N | Y |
| Chen et al. [33] | 2022 | Proposed a traceable blockchain-based vaccination record storage and share system. | Y | Y | Y | Y | Y | N |
| Our scheme | 2022 | Propose a blockchain-based traceable vaccine system. | Y | Y | Y | Y | Y | Y |
| Characteristics | Bitcoin | Ethereum | Hyperledger Fabric |
|---|---|---|---|
| Type | Public blockchain | Public blockchain | Consortium blockchain |
| Consensus | Proof of work (POW) | Proof of work (POW) | PBFT |
| Scripting | Limited stack-based scripting | Solidity | Go, Java, JavaScript |
| Authentication | No | No | Yes |
| Smart Contract | No | No | Yes |
| Scalability | Low scalability | Low scalability | High scalability |
| Currency | Bitcoin | Ether | No |
| Speed of transactions | 7 TPS | 20 TPS | 1000 TPS-10000 TPS |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ai, Y.; Chen, C.-L.; Weng, W.; Chiang, M.-L.; Deng, Y.-Y.; Lim, Z.-Y. A Traceable Vaccine Supply Management System. Sensors 2022, 22, 9670. https://doi.org/10.3390/s22249670
Ai Y, Chen C-L, Weng W, Chiang M-L, Deng Y-Y, Lim Z-Y. A Traceable Vaccine Supply Management System. Sensors. 2022; 22(24):9670. https://doi.org/10.3390/s22249670
Chicago/Turabian StyleAi, Yaohong, Chin-Ling Chen, Wei Weng, Mao-Lun Chiang, Yong-Yuan Deng, and Zi-Yi Lim. 2022. "A Traceable Vaccine Supply Management System" Sensors 22, no. 24: 9670. https://doi.org/10.3390/s22249670
APA StyleAi, Y., Chen, C.-L., Weng, W., Chiang, M.-L., Deng, Y.-Y., & Lim, Z.-Y. (2022). A Traceable Vaccine Supply Management System. Sensors, 22(24), 9670. https://doi.org/10.3390/s22249670









