A Secure Pseudonym-Based Conditional Privacy-Preservation Authentication Scheme in Vehicular Ad Hoc Networks
Abstract
:1. Introduction
2. Related Work
2.1. ID Bilinear Pair Based
2.2. ID Vulnerable to Insider Attack Based
2.3. ID RSU Authentication Based
3. Preliminaries
3.1. Network Model
- TA: The TAs are trusted parties in VANETs with high resources such as computation and communication. The TA issues the system’s public parameters, pseudo-ID, and the private keys for each vehicle and transmits them to each respective vehicle;
- RSU: The RSU is a wireless base station deployed on the road as a brigade interface between the TA and OBUs. The RSU connects with the TA by wired technology and connects with vehicles by wireless technology;
- OBU: Each vehicle is fit with an On-Board Unit (OBU), enabling the vehicle to process, receive, and broadcast messages in the VANET. Each OBU is equipped with a Tamper-Proof Device (TPD) that is usually utilized to keep secrets. Therefore, it is difficult for any adversary to obtain the information stored in the TPD.
3.2. Security Requirements
- Authentication and integrity: The vehicle or RSU must be able to identify any alteration of the received message and must have the ability to authenticate the integrity and validity of the received messages to ensure communication security;
- Identity privacy preservation: An attacker must not have the ability to reveal the vehicle’s identity by capturing multiple messages transmitted by it. Therefore, the vehicle’s identity must remain anonymous to other legal and illegal nodes to ensure users’ privacy;
- Traceability: The TA must have the ability to reveal the vehicle’s identity from its message in case of any misbehavior to prevent misbehaving vehicles from denying their responsibility for disrupting the system by broadcasting false messages to other registered vehicles;
- Unlinkability: The misbehaving vehicles and RSUs cannot link two or more messages transmitted by the same source to ensure privacy preservation.
3.3. Adversary Model
- Replay attacks. Malicious nodes replay the previously generated legitimate signature to the recipient;
- Modification attacks. Malicious nodes alter authentic messages and broadcast them to other users [32];
- Impersonation attacks. Malicious nodes impersonate an authentic node and broadcast a legitimate message to other nodes;
3.4. Elliptic Curve Cryptography
- –
- Scalar multiplication. Denote P ∈, n ∈, then the scalar multiplication is L · P = P + P + P +…+P (for all the L times).
4. The Proposed Scheme
4.1. Initialization
- The TA sets the chosen elliptic curve E determined by the non-singular equation ( mod p), where and p is a large prime number;
- The TA chooses a point P on as an adaptive group generator G of prime order q;
- The TA selects the private key s∈ of the system and computes the respective public key = of the system;
- The TA selects three secure cryptographic hash functions ;
- The TA publishes the functions and the public parameters of the system to all RSUs via public channels.
4.2. Vehicle Registration
- The owner of the vehicle submits personal information including the identity and password to the TA through a secure communication channel;
- After the personal information is received, the TA first starts the authenticity of ;
- After checking the validity of , the TA chooses n random secret values ∈, where , and calculates a family of unlinkable pseudo-IDs as follows:where l = 1,2, …n;
- For each pseudo-ID ∈, , the TA calculates the respective signature key as follows and organizes :
- The TA then transmits the n of , , and to the vehicle via a secret technology.
4.3. Message Signing
- randomly chooses a pseudo-ID with the respective and ;
- computes the message signature , where T is the current timestamp;
- computes ;
- sets the authentic signature as for ;
- Finally, the message signature tuple {, , T, } is sent to the neighboring recipient.
4.4. Individual Signature Authentication
- Once the message signature tuple {, , T, } is received, the OBU first verifies the validity of timestamp T. If (T> − ), where is the time of receiving and is the time of the predefined delay, then T is fresh. Otherwise, the message is rejected;
- The OBU utilizes the public parameter and functions of the system and authentic signature on the message . Therefore, if Equation (3) holds, the OBU accepts it.
4.5. Batch Signature Authentication
- The OBU checks the validity of timestamp T. If (T>−), T is fresh. Otherwise, the message is rejected;
- The OBU utilizes the following Equation (4) to accept them.
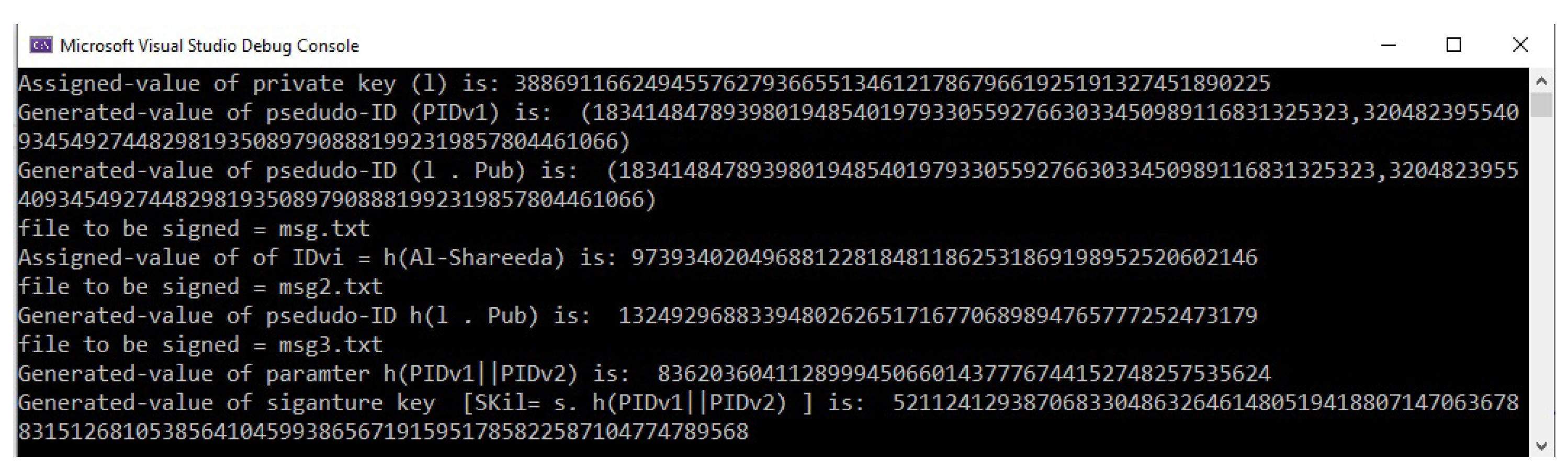
5. Illustrative Example
5.1. Example of Initialization Phase
5.2. Example of the Vehicle Registration Phase
| 973934020496881228184811862531869198952520602146 ⊕ |
| 1324929688339480262651716770689894765777252473179 = |
| 379900236377609805635535841290573035328518392697 |
5.3. Example of the Message Signing Phase
5.4. Example of the Individual Signature Authentication Phase
5.5. Example of the Batch Signature Authentication Phase
6. Security Proof and Analysis
6.1. Security Proof
6.2. Security Analysis
- Authentication and integrity: Consistent with Theorem 1, no malicious node can return the ECDL problem and generate the legitimate signature; it is considered to be forged otherwise. In our scheme, the verifying recipient can test the authenticity and integrity of the message signature tuple {, , T, } sent from the vehicle by checking the equation before accepting it. If verified and validated, the recipient accepts traffic-related message ; otherwise, the message is rejected. Thus, our scheme can satisfy messages’ authentication and integrity requirements;
- Identity privacy preservation: After the identity of a vehicle is received, the TA converts it to pseudo-ID in the proposed scheme. The main purpose of this requirement is to support anonymous communication and preserve the driver’s privacy. The pseudo-ID involves two secret values and s selected randomly by the OBU and TA, respectively. It is impossible for an attacker to disclose identity from pseudo-ID = of any vehicle without knowing and s. Therefore, it cannot calculate from and to obtain the identity of the vehicle because it is a difficult CDHP problem. Thus, the proposed scheme can satisfy the identity privacy-preservation requirement in the VANET;
- Traceability: If a malicious node broadcasts a bogus message, i.e., to participating vehicles to disrupt the system managing the road, the TA can revoke the malicious node’s identity after tracing him/her during traveling. Suppose a vehicle issues a false message and sends it to a vehicle . The TA receives a report on the forged message from vehicle . The TA verifies the pseudo-ID on message for vehicle in its database registration list. When the pseudo-ID is match stored, the TA uses its private key s to disclose the identity of vehicle by calculating the following:After tracing the vehicle’s identity, the TA revokes its database registration list, saves it in the Certificate Renovation List (CRL). The vehicle cannot send traffic-related messages in the VANET. Therefore, our scheme can satisfy the traceability requirement in the VANET;
- Unlinkability: Each message signature tuple {, , T, } involves a pseudo-ID , where and ∈ is a random secret value; therefore, the particular vehicle generates the different pseudo-ID in our scheme. Furthermore, since vehicles utilize different pseudo-IDs to sign every message , an attacker cannot link multiple messages transmitted by the same source. Thus, the proposed scheme can satisfy the unlinkability requirement in the VANET;
- Security attack resistance: The proposed scheme can resist the common attacks as follows. Figure 6 shows the process of the system resisting replay, modification, and impersonation attacks;
- -
- Replay attacks. In the proposed scheme, timestamp T in the message signature tuple {, , T, } allows the recipient to check the authenticity of the message . Once the vehicle receives the message , it verifies the freshness of the timestamp by verifying whether the inequalities (T>−) hold. If it is fresh, the message is accepted; otherwise, the vehicle does not accept message . The proposed scheme can detect the message replay in the VANET. Therefore, our scheme can withstand replay attacks in the VANET;
- -
- Modification attacks. An attacker cannot modify a message signature tuple {, , T, } consistent with Theorem 1 since the vehicle can expose any alteration in the tuple by verifying the equation . Therefore, the alteration probability of the signature for the message is minimal. Therefore, the proposed scheme can withstand modification attacks in the VANET;
- -
- Impersonation attacks. It is impossible for an attacker to forge a legitimate message signature tuple {, , T, } consistent with Theorem 1 because the recipient verifies the authenticity of the tuple {, , T, } by checking the equation . The forged signature probability for message is trivial. Therefore, the proposed scheme can resist impersonation attacks in the VANET;
- -
- Man-In-The-Middle (MITM) attacks. In the proposed scheme, mutual authentication is executed among the nodes in the VANET. If an attacker tries an MITM attack, forged messages must link with the signer and the receiver. Nevertheless, consistent with Theorem 1, it is impossible for an attacker to launch this attack type. Therefore, the proposed scheme can resist MITM attacks in the VANET.
6.3. Security Comparison
7. Performance Analysis and Comparison
7.1. Experimental
7.2. Computation Cost Analysis and Comparison
- indicates the time needed to perform a bilinear pairing operation. Hence, the time cost of is 5.811 ms;
- indicates the time needed to perform the point addition operation for the bilinear pairing in . Hence, the time cost of is 0.0106 ms;
- indicates the time needed to perform a small scalar multiplication operation for the bilinear pairing in . Hence, the time cost of is 0.1829 ms;
- indicates the time needed to perform a scalar multiplication operation for the bilinear pairing in . Hence, the time cost of is 1.5654 ms;
- indicates the time needed to perform a map-to-point function for the bilinear pairing in . Hence, the time cost of is 4.1724 ms;
- indicates the time needed to perform a scalar multiplication operation for ECC in an additive group G. Hence, the time cost of is 0.6718 ms;
- indicates the time needed to perform a point addition operation for ECC in an additive group G. Hence, the time cost of is 0.0031 ms;
- indicates the time needed to perform a small scalar multiplication for ECC in G. Hence, the time cost of is 0.0665 ms;
- indicates the time required to perform a secure hash cryptography function. Hence, the time cost of is 0.001 ms.
7.3. Communication Cost Analysis and Comparison
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Zhang, J.; Cui, J.; Zhong, H.; Chen, Z.; Liu, L. PA-CRT: Chinese remainder theorem based conditional privacy-preserving authentication scheme in vehicular ad hoc networks. IEEE Trans. Dependable Secur. Comput. 2019, 18, 722–735. [Google Scholar] [CrossRef] [Green Version]
- Alazzawi, M.A.; Chen, K.; Yassin, A.A.; Lu, H.; Abedi, F. Authentication and revocation scheme for VANETs based on Chinese remainder theorem. In Proceedings of the 2019 IEEE 21st International Conference on High Performance Computing and Communications; IEEE 17th International Conference on Smart City; IEEE 5th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Zhangjiajie, China, 10–12 August 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1541–1547. [Google Scholar]
- Lloyd, D. Reported Road Casualties in Great Britain: Main Results 2015. 2016. Available online: https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/533293/rrcgb-main-results-2015.pdf (accessed on 19 January 2022).
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. SE-CPPA: A Secure and Efficient Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-Hoc Networks. Sensors 2021, 21, 8206. [Google Scholar] [CrossRef]
- Aung, N.; Zhang, W.; Dhelim, S.; Ai, Y. Accident prediction system based on hidden markov model for vehicular ad hoc network in urban environments. Information 2018, 9, 311. [Google Scholar] [CrossRef] [Green Version]
- Cheng, H.; Liu, Y. An improved RSU-based authentication scheme for VANET. J. Internet Technol. 2020, 21, 1137–1150. [Google Scholar]
- Kerrache, C.A.; Lakas, A.; Lagraa, N. Detection of intelligent malicious and selfish nodes in VANET using threshold adaptive control. In Proceedings of the 2016 5th International Conference on Electronic Devices, Systems and Applications (ICEDSA), Ras Al Khaimah, United Arab Emirates, 6–8 December 2016; pp. 1–4. [Google Scholar]
- Yang, X.; Yi, X.; Khalil, I.; Zeng, Y.; Huang, X.; Nepal, S.; Yang, X.; Cui, H. A lightweight authentication scheme for vehicular ad hoc networks based on MSR. Veh. Commun. 2019, 15, 16–27. [Google Scholar] [CrossRef]
- Muhammad, M.; Safdar, G.A. Survey on existing authentication issues for cellular-assisted V2X communication. Veh. Commun. 2018, 12, 50–65. [Google Scholar] [CrossRef]
- Manvi, S.S.; Tangade, S. A survey on authentication schemes in VANETs for secured communication. Veh. Commun. 2017, 9, 19–30. [Google Scholar] [CrossRef]
- Leaby, A.K.; Yassin, A.; Hasson, M.; Rashid, A. Towards design strong emergency and COVID-19 authentication scheme in VANET. Indones. J. Electr. Eng. Comput. Sci. 2021, 21, 1808–1819. [Google Scholar] [CrossRef]
- Alazzawi, M.A.; Lu, H.; Yassin, A.A.; Chen, K. Robust conditional privacy-preserving authentication based on pseudonym root with cuckoo filter in vehicular ad hoc networks. KSII Trans. Internet Inf. Syst. (TIIS) 2019, 13, 6121–6144. [Google Scholar]
- Alazzawi, M.; Lu, H.; Yassin, A.; Chen, K. Efficient Conditional Anonymity with Message Integrity and Authentication in a Vehicular Ad hoc Network. IEEE Access 2019, 7, 71424–71435. [Google Scholar] [CrossRef]
- Raya, M.; Papadimitratos, P.; Hubaux, J.P. Securing vehicular communications. IEEE Wirel. Commun. 2006, 13, 8–15. [Google Scholar] [CrossRef] [Green Version]
- Alazzawi, M.A.; Al-behadili, H.A.; Almalki, M.N.S.; Challoob, A.L.; Al-shareeda, M.A. ID-PPA: Robust Identity-Based Privacy-Preserving Authentication Scheme for a Vehicular Ad-Hoc Network. In Proceedings of the International Conference on Advances in Cyber Security, Penang, Malaysia, 8–9 December 2020; Springer: Berlin/Heidelberg, Germany, 2020; pp. 80–94. [Google Scholar]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Workshop on the Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 1984; pp. 47–53. [Google Scholar]
- Zhang, C.; Lu, R.; Lin, X.; Ho, P.; Shen, X. An efficient identity-based batch verification scheme for vehicular sensor networks. In Proceedings of the IEEE INFOCOM 2008-The 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 246–250. [Google Scholar]
- Zhang, C.; Ho, P.H.; Tapolcai, J. On batch verification with group testing for vehicular communications. Wirel. Netw. 2011, 17, 1851. [Google Scholar] [CrossRef]
- Jiang, Y.; Shi, M.; Shen, X.; Lin, C. BAT: A robust signature scheme for vehicular networks using binary authentication tree. IEEE Trans. Wirel. Commun. 2008, 8, 1974–1983. [Google Scholar] [CrossRef] [Green Version]
- Huang, D.; Misra, S.; Verma, M.; Xue, G. PACP: An efficient pseudonymous authentication-based conditional privacy protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2011, 12, 736–746. [Google Scholar] [CrossRef]
- Chim, T.W.; Yiu, S.M.; Hui, L.; Li, V. SPECS: Secure and Privacy Enhancing Communications Schemes for VANETs. Ad Hoc Netw. 2011, 9, 189–203. [Google Scholar] [CrossRef] [Green Version]
- Lee, C.C.; Lai, Y.M. Toward a Secure Batch Verification with Group Testing for VANET. Wirel. Netw. 2013, 19, 1441–1449. [Google Scholar] [CrossRef]
- Horng, S.J.; Tzeng, S.F.; Pan, Y.; Fan, P.; Wang, X.; Li, T.; Khan, M.K. b-SPECS+: Batch Verification For Secure Pseudonymous Authentication in VANET. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1860–1875. [Google Scholar] [CrossRef]
- Jianhong, Z.; Min, X.; Liying, L. On The Security of a Secure Batch Verification With Group Testing for VANET. Int. J. Netw. Secur. 2014, 16, 351–358. [Google Scholar]
- He, D.; Zeadally, S.; Xu, B.; Huang, X. An Efficient Identity-based Conditional Privacy-preserving Authentication Scheme for Vehicular Ad hoc Networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 2681–2691. [Google Scholar] [CrossRef]
- Zhong, H.; Wen, J.; Cui, J.; Zhang, S. Efficient Conditional Privacy-preserving and Authentication Scheme for Secure Service Provision in VANET. Tsinghua Sci. Technol. 2016, 21, 620–629. [Google Scholar] [CrossRef]
- Lo, N.W.; Tsai, J.L. An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks without pairings. IEEE Trans. Intell. Transp. Syst. 2015, 17, 1319–1328. [Google Scholar] [CrossRef]
- Wu, L.; Fan, J.; Xie, Y.; Wang, J.; Liu, Q. Efficient location-based conditional privacy-preserving authentication scheme for vehicle ad hoc networks. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717700899. [Google Scholar] [CrossRef]
- Xie, Y.; Wu, L.; Shen, J.; Alelaiwi, A. EIAS-CP: New efficient identity-based authentication scheme with conditional privacy-preserving for VANETs. Telecommun. Syst. 2017, 65, 229–240. [Google Scholar] [CrossRef]
- Cui, J.; Zhang, J.; Zhong, H.; Xu, Y. SPACF: A secure privacy-preserving authentication scheme for VANET with cuckoo filter. IEEE Trans. Veh. Technol. 2017, 66, 10283–10295. [Google Scholar] [CrossRef]
- Zhong, H.; Huang, B.; Cui, J.; Xu, Y.; Liu, L. Conditional privacy-preserving authentication using registration list in vehicular ad hoc networks. IEEE Access 2017, 6, 2241–2250. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. Password-Guessing Attack-Aware Authentication Scheme Based on Chinese Remainder Theorem for 5G-Enabled Vehicular Networks. Appl. Sci. 2022, 12, 1383. [Google Scholar] [CrossRef]
- Ahmad, F.; Adnane, A.; Franqueira, V.N.; Kurugollu, F.; Liu, L. Man-in-the-middle attacks in vehicular ad hoc networks: Evaluating the impact of attackers’ strategies. Sensors 2018, 18, 4040. [Google Scholar] [CrossRef] [Green Version]
- Sheikh, M.S.; Liang, J.; Wang, W. A Survey of Security Services, Attacks, and Applications for Vehicular Ad Hoc Networks (VANETs). Sensors 2019, 19, 3589. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Cui, J.; Wu, D.; Zhang, J.; Xu, Y.; Zhong, H. An efficient authentication scheme based on semi-trusted authority in VANETs. IEEE Trans. Veh. Technol. 2019, 68, 2972–2986. [Google Scholar] [CrossRef]
- Ali, I.; Lawrence, T.; Li, F. An efficient identity-based signature scheme without bilinear pairing for vehicle-to-vehicle communication in VANETs. J. Syst. Archit. 2020, 103, 101692. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Hasbullah, I.H.; Manickam, S.; Hanshi, S.M. Efficient Conditional Privacy Preservation with Mutual Authentication in Vehicular Ad Hoc Networks. IEEE Access 2020, 8, 144957–144968. [Google Scholar] [CrossRef]
- Li, J.; Choo, K.K.R.; Zhang, W.; Kumari, S.; Rodrigues, J.J.; Khan, M.K.; Hogrefe, D. EPA-CPPA: An efficient, provably-secure and anonymous conditional privacy-preserving authentication scheme for vehicular ad hoc networks. Veh. Commun. 2018, 13, 104–113. [Google Scholar] [CrossRef]
- Varga, A. Discrete event simulation system. In Proceedings of the European Simulation Multiconference (ESM’2001), Prague, Czech Republic, 6–9 June 2001; pp. 1–7. [Google Scholar]
- Sommer, C.; German, R.; Dressler, F. Bidirectionally coupled network and road traffic simulation for improved IVC analysis. IEEE Trans. Mob. Comput. 2010, 10, 3–15. [Google Scholar] [CrossRef] [Green Version]
- Scott, M. MIRACL-A Multiprecision Integer and Rational Arithmetic C/C++ Library. 2003. Available online: http://www.shamus.ie (accessed on 19 January 2022).
- Ltd, S.S. Multi Precision Integer and Rational Arithmetic Cryptographic Library (MIRACL). 2018. Available online: http://www.certivox.com/miracl/ (accessed on 19 January 2022).
- Haklay, M.; Weber, P. Openstreetmap: User-generated street maps. IEEE Pervasive Comput. 2008, 7, 12–18. [Google Scholar] [CrossRef] [Green Version]
- Abenza, P.P.G.; Malumbres, M.P.; Peral, P.P. 10 GatcomSUMO: A Graphical Tool for VANET Simulations Using SUMO and OMNeT+. In SUMO 2017–Towards Simulation for Autonomous Mobility; Deutsches Zentrum für Luft- und Raumfahrt e. V.: Cologne, Germany, 2017; p. 113. [Google Scholar]
- Behrisch, M.; Bieker, L.; Erdmann, J.; Krajzewicz, D. SUMO–simulation of urban mobility: An overview. In Proceedings of the SIMUL 2011, The Third International Conference on Advances in System Simulation, ThinkMind, Barcelona, Spain, 23–28 October 2011. [Google Scholar]











| Notations | Descriptions |
|---|---|
| Two large prime numbers | |
| p | A large prime number |
| E | The elliptic curve |
| G | The additive group based on E |
| P | The base generator P∈ G |
| The three functions of the one-way hash | |
| , | The identity and password of the vehicle |
| s, | The private and public key of the system |
| , | The pseudo-identity of the vehicle |
| ⊕ | The XOR operator |
| The list of pseudo-identities | |
| The random secret value | |
| ‖ | The concatenation operation |
| The list of signature keys |
| [17,18,19,20,21,22,23,24] | [25,26,27,28,29] | [30,31] | Proposed | |
|---|---|---|---|---|
| SC-1 | ✓ | ✗ | ✗ | ✗ |
| SC-2 | ✓ | ✓ | ✗ | ✗ |
| SC-3 | ✗ | ✗ | ✓ | ✗ |
| Parameters | Value |
|---|---|
| Simulation time | 200 s |
| Playground size | x = 3463 m, y = 4270 m and z = 50 m |
| Mac layer | IEEE 1609.4 |
| Physical layer | IEEE 802.11p |
| Maximum transmission | 20 mW |
| Bit rate | 6 Mbps |
| Number of vehicles | 500 |
| Minimum speed | 30 Km/H |
| Maximum speed | 60 Km/H |
| Scheme | |||
|---|---|---|---|
| Jianhong et al. [24] | |||
| He et al. [25] | |||
| Wu et al. [28] | |||
| Cui et al. [30] | |||
| Our scheme |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. A Secure Pseudonym-Based Conditional Privacy-Preservation Authentication Scheme in Vehicular Ad Hoc Networks. Sensors 2022, 22, 1696. https://doi.org/10.3390/s22051696
Al-Shareeda MA, Anbar M, Manickam S, Hasbullah IH. A Secure Pseudonym-Based Conditional Privacy-Preservation Authentication Scheme in Vehicular Ad Hoc Networks. Sensors. 2022; 22(5):1696. https://doi.org/10.3390/s22051696
Chicago/Turabian StyleAl-Shareeda, Mahmood A., Mohammed Anbar, Selvakumar Manickam, and Iznan H. Hasbullah. 2022. "A Secure Pseudonym-Based Conditional Privacy-Preservation Authentication Scheme in Vehicular Ad Hoc Networks" Sensors 22, no. 5: 1696. https://doi.org/10.3390/s22051696
APA StyleAl-Shareeda, M. A., Anbar, M., Manickam, S., & Hasbullah, I. H. (2022). A Secure Pseudonym-Based Conditional Privacy-Preservation Authentication Scheme in Vehicular Ad Hoc Networks. Sensors, 22(5), 1696. https://doi.org/10.3390/s22051696








