Cyberattack Models for Ship Equipment Based on the MITRE ATT&CK Framework
Abstract
:1. Introduction
2. Background
MITRE ATT&CK Framework
- Express cyberattack technology correctly; and
- Suggest specific security measures.
- Tactics: the methods and objectives used in the attack;
- Techniques: 185 techniques and 367 sub-techniques have been identified as technical cyberattack methods for achieving tactical objectives;
- Procedures: the sequential processes of an attack.
3. MITRE ATT&CK-Based Ship Cyberattack Analysis
3.1. MITRE ATT&CK-Based Ship Cyberattack Cases
- Case 1: the IRGC plan to attack and sink ships;
- Case 2: cyberattacks on the INSs on ships, analyzed using the MITRE;
- Case 3: security vulnerabilities of the ECDIS of real training ships;
- Case 4: a threat analysis report of a ship’s OT system.
- (1)
- Use Case 1: The IRGC BWMS Cyberattack Plans to Cause a Ship to Sink or Overturn
- (2)
- Use Case 2: INS Attack [17]
- (3)
- Use Case 3: ECDIS Attack [7]
- (4)
- Use Case 4: Ship Operating Technology (OT) System Threat Analysis [27]
3.2. TTPs Analysis
- (1)
- MITRE ATT&CK Enterprise
- (2)
- MITRE ATT&CK ICS
4. Considerations and Limitations
5. Conclusions
- Design of cybersecurity risk management and risk assessment framework for various ship types [33].
- Threat analysis and security requirements analysis for NMEA 0183, 2000 protocol [34].
- A honeypot system to detect new cyberattacks onboard and reduce false positives in IDS [35]. In particular, a honeypot system has been developed [36] that can be installed in an L2 layer switch environment using VLAN when the deployment location of the honeypot is the ship’s internal network. For analyzing the attack type on the ship’s satellite communication system from outside the ship, a cloud-based ICS/SCADA honeypot system has been proposed [37].
- Artificial intelligence-based ship cyber threat response technology for an independent system of an autonomous vessel at sea to recognize an attack and respond by itself.
- The ship equipment whitelisting technique and data set [38].
- Maritime cyberthreat intelligence: technology for the classification and evaluation of threat information tailored to ships, the maritime industry, and stakeholders [39].
- Ship digital forensic technology to collect and analyze digital evidence in security incidents of onboard systems.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Perera, L.P. Handling big data in ship performance and navigation monitoring. Smart Ship Technol. 2017, 89–97. [Google Scholar] [CrossRef]
- Inmarsat. A Superyacht Connectivity Report; Inmarsat: London, UK, 2020. [Google Scholar]
- The Maritime Executive. Naval Dome: Cyberattacks on OT Systems on the Rise. 26 July 2020. Available online: https://www.maritime-executive.com/article/naval-dome-cyberattacks-on-ot-systems-on-the-rise (accessed on 2 August 2021).
- Santamarta, R. SATCOM Terminals: Hacking by Air, Sea, and Land; IOActive: Seattle, WA, USA, 2014. [Google Scholar]
- Rundle, J. Coast Guard Details February Cyberattack on Ship. The Wall Street Journal 26 July 2019. Available online: https://www.wsj.com/articles/coast-guard-details-february-cyberattack-on-ship-11564133401 (accessed on 2 August 2021).
- US Coast Guard. Marine Safety Alert (06-19), Cyber Incident Expose Potential Vulerabilities Onboard Commercial Vessels; USCG: Washington, DC, USA, 2019. [Google Scholar]
- Svilicic, B.; Kamahara, J.; Rooks, M.; Yano, Y. Maritime cyber risk management: An experimental ship assessment. J. Navig. 2019, 72, 1108–1120. [Google Scholar] [CrossRef]
- Hyra, B. Analyzing the Attack Surface of Ships. Master’s Thesis, Technical University of Denmark, Kongens Lyngby, Denmark, 2019. [Google Scholar]
- Tran, K.; Keene, S.; Fretheim, E.; Tsikerdekis, M. Marine network protocols and security risks. J. Cybersecur. Priv. 2021, 1, 239–251. [Google Scholar] [CrossRef]
- Staff, T. Secret files show alleged Iranian plans to sink ships using cyberattacks. The Times of Israel 28 July 2021. Available online: https://www.timesofisrael.com/secret-files-show-alleged-iranian-plans-to-sink-ships-using-cyberattacks/ (accessed on 10 August 2021).
- International Maritime Organization. Guidelines on Maritime Cyber Risk Management. 5 July 2017. Available online: https://wwwcdn.imo.org/localresources/en/OurWork/Security/Documents/MSC-FAL.1-Circ.3%20-%20Guidelines%20On%20Maritime%20Cyber%20Risk%20Management%20(Secretariat).pdf (accessed on 2 August 2021).
- BIMCO. The Guidelines on Cyber Security Onboard Ships; BIMCO: Copenhagen, Denmark, 2020. [Google Scholar]
- Strom, B.E.; Applebaum, A.; Miller, D.P.; Nickels, K.C.; Pennington, A.G.; Thomas, C.B. MITRE ATT&CK: Design and Philosophy; MITRE Corporation: McLean, VA, USA, 2018. [Google Scholar]
- Yoon, Y.; Kim, J.; Lee, J.; Yu, S.; Lee, S. A research on cyber kill chain and TTP by APT attack case study. Converg. Secur. J. 2020, 20, 91–101. [Google Scholar] [CrossRef]
- Alexander, O.; Belisle, M.; Steele, J. MITRE ATT&CK for Industrial Control Systems: Design and Philosophy; MITRE: McLean, VA, USA, 2020. [Google Scholar]
- Kessler, G.C.; Craiger, J.P.; Haass, J.C. A taxonomy framework for maritime cybersecurity: A demonstration using the automatic identification system. TransNav 2018, 12, 429. [Google Scholar] [CrossRef] [Green Version]
- Santamarta, R. Maritime Security: Hacking into a Voyage Data Recorder (VDR); IOActive: Seattle, WA, USA, 2015; Available online: https://ioactive.com/maritime-security-hacking-into-a-voyage-data-recorder-vdr/ (accessed on 30 January 2022).
- Lund, M.S.; Hareide, O.S.; Jøsok, Ø. An attack on an integrated navigation system. Necesse 2018, 3, 149–163. [Google Scholar]
- Svilicic, B.; Brčić, D.; Žuškin, S.; Kalebić, D. Raising awareness on cyber security of ECDIS. TransNav 2019, 13, 231–236. [Google Scholar] [CrossRef] [Green Version]
- Svilicic, B.; Rudan, I.; Frančić, V.; Doričić, M. Shipboard ECDIS cyber security: Third-party component threats. Pomorstvo 2019, 33, 176–180. [Google Scholar] [CrossRef]
- Svilicic, B.; Rudan, I.; Jugović, A.; Zec, D. A study on cyber security threats in a shipboard integrated navigational system. J. Mar. Sci. Eng. 2019, 7, 364. [Google Scholar] [CrossRef] [Green Version]
- Shang, W.; Gong, T.; Chen, C.; Hou, J.; Zeng, P. Information security risk assessment method for ship control system based on fuzzy sets and attack trees. Secur. Commun. Netw. 2019, 2019, 1–11. [Google Scholar] [CrossRef]
- Awan, M.S.K.; Al Ghamdi, M.A. Understanding the vulnerabilities in digital components of an integrated bridge system (IBS). J. Mar. Sci. Eng. 2019, 7, 350. [Google Scholar] [CrossRef] [Green Version]
- Caprolu, M.; Di Pietro, R.; Raponi, S.; Sciancalepore, S.; Tedeschi, P. Vessels cybersecurity: Issues, challenges, and the road ahead. IEEE Commun. Mag. 2020, 58, 90–96. [Google Scholar] [CrossRef]
- Pavur, J.; Moser, D.; Strohmeier, M.; Lenders, V.; Martinovic, I. A tale of sea and sky on the security of maritime VSAT communications. Proc. IEEE Symp. Secur. Priv. 2020, 2020, 1384–1400. [Google Scholar]
- Tierney, A. Serious Vulnerabilities in Dualog Connection Suite. 10 December 2020. Available online: https://www.pentestpartners.com/security-blog/serious-vulnerabilities-in-dualog-connection-suite/ (accessed on 10 January 2022).
- Tierney, A. Speed 2—The Poseidon Adventure–Part One. 8 September 2020. Available online: https://www.pentestpartners.com/security-blog/speed-2-the-poseidon-adventure-when-cruise-ships-attack-part-1/ (accessed on 2 August 2021).
- Dumbala, R. A Study of Mitigation Measures for Cyber Risks in Shipboard OT Systems. 1 April 2021. Available online: https://itrust.sutd.edu.sg/wp-content/uploads/sites/3/2021/04/Webinar-2_Slides_Latest.pdf (accessed on 11 August 2021).
- Jones, K.D.; Tam, K.; Papadaki, M. Threats and impacts in maritime cyber security. In Engineering & Technology Reference; University of Plymouth: Plymouth, UK, 2016; Volume 1. [Google Scholar]
- Alcaide, J.I.; Llave, R.G. Critical infrastructures cybersecurity and the maritime sector. Transp. Res. Procedia 2020, 45, 547–554. [Google Scholar] [CrossRef]
- Haynes, D. Iran’s Secret Cyber Files. 27 July 2021. Available online: https://news.sky.com/story/irans-secret-cyber-files-on-how-cargo-ships-and-petrol-stations-could-be-attacked-12364871 (accessed on 11 August 2021).
- Even, N. What We’ve Learned from the December 1st Attack on an Israeli Water Reservoir. OTORIO. 3 December 2020. Available online: https://www.otorio.com/blog/what-we-ve-learned-from-the-december-1st-attack-on-an-israeli-water-reservoir/ (accessed on 13 August 2021).
- Tam, K.; Jones, K. MaCRA: A model-based framework for maritime cyber-risk assessment. WMU J. Marit. Aff. 2019, 18, 129–163. [Google Scholar] [CrossRef]
- Kessler, G.C. The CAN Bus in the Maritime Environment–Technical Overview and Cybersecurity Vulnerabilities. Int. J. Mar. Navig. Saf. Sea Transp. 2021, 3, 531–540. [Google Scholar] [CrossRef]
- Baykara, M.; Das, R. A novel honeypot based security approach for real-time. J. Inf. Secur. 2018, 41, 103–116. [Google Scholar]
- Baykara, M.; Das, R. SoftSwitch: A centralized honeypot-based security approach using software-defined switching for secure management of VLAN networks. Turk. J. Elec. Eng. Comp. Sci. 2019, 27, 3309–3325. [Google Scholar] [CrossRef]
- Jicha, A.; Patton, M.; Chen, H. SCADA honeypots: An in-depth analysis of Conpot. In Proceedings of the IEEE Conference on Intelligence and Security Informatics (ISI), Tucson, AZ, USA, 28–30 September 2016. [Google Scholar]
- Barbosa, R.R.R.; Sadre, R.; Pras, A. Flow whitelisting in SCADA networks. Int. J. Crit. Infrastruct Prot. 2013, 150–158. [Google Scholar] [CrossRef] [Green Version]
- Mavroeidis, V.; Bromander, S. Cyber threat intelligence model: An evaluation of taxonomies, sharing standards, and ontologies within cyber threat intelligence. In Proceedings of the 2017 European Intelligence and Security Informatics Conference (EISIC), Athens, Greece, 11–13 September 2017. [Google Scholar]
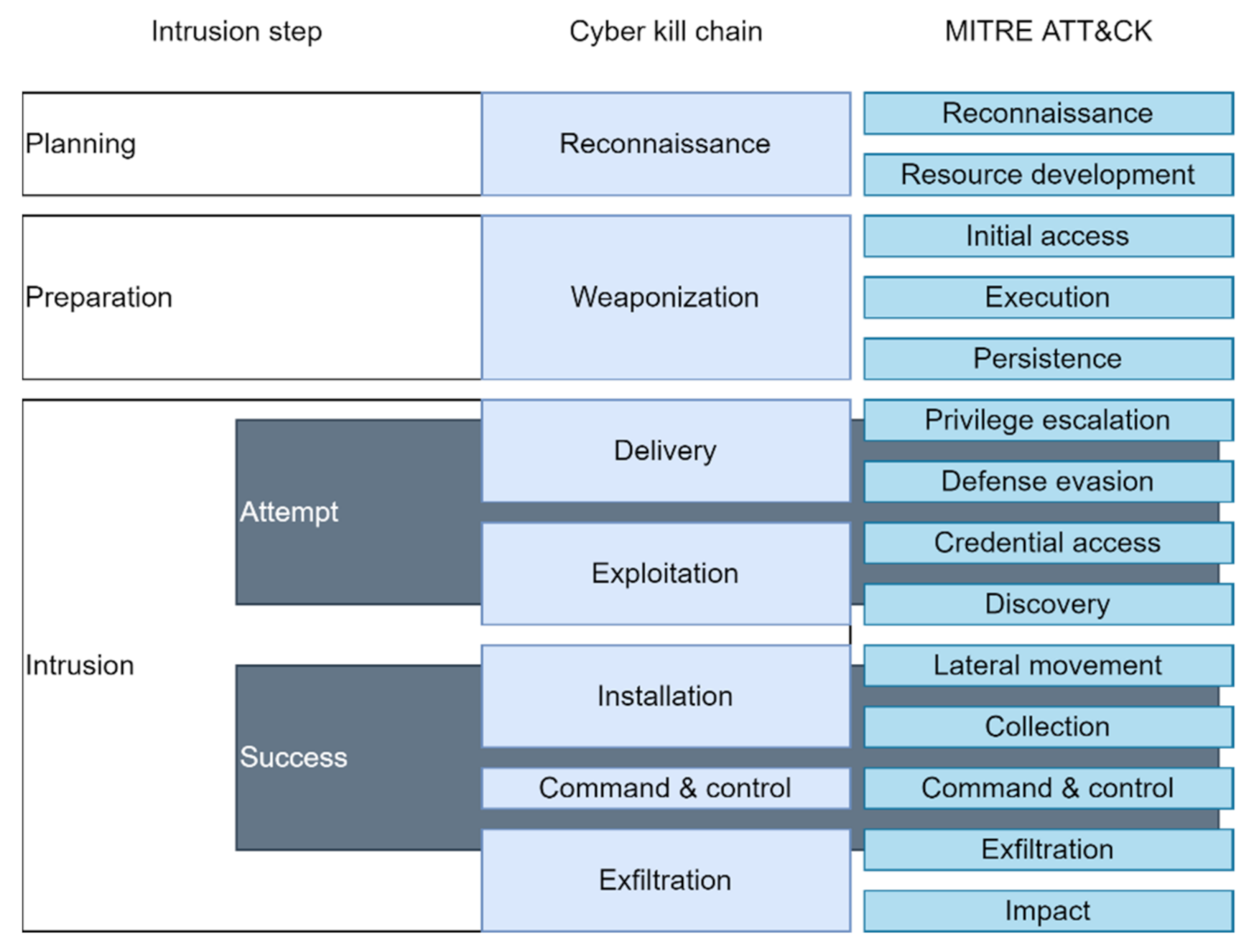







| Tactic | Description |
|---|---|
| Reconnaissance | The adversary attempts to gather information they can use to plan future operations. |
| Resource Development | The adversary attempts to establish resources they can use to support operations. |
| Initial Access | The adversary attempts to gain access to the target network. |
| Execution | The adversary attempts to run malicious code. |
| Persistence | The adversary attempts to maintain their progress. |
| Privilege Escalation | The adversary attempts to obtain higher-level permissions. |
| Defense Evasion | The adversary attempts to avoid detection. |
| Credential Access | The adversary attempts to steal account names and passwords. |
| Discovery | The adversary attempts to determine the target environment. |
| Lateral Movement | The adversary attempts to move through the target environment. |
| Collection | The adversary attempts to gather data of interest to their goal. |
| Command and Control | The adversary attempts to communicate with compromised systems to control them. |
| Exfiltration | The adversary attempts to steal data. |
| Impact | The adversary attempts to manipulate, interrupt, or destroy the target systems and data. |
| System | Threat | Impact | Reference |
|---|---|---|---|
| AIS | AIS malfunction, jamming, spoofing | Not mentioned | Kessler et al. [16] |
| Spoofing, replay attack, frequency hopping attack | Not mentioned | Dumbala [28] | |
| Designed without security, malicious version, malware | Hijacking, smuggling, theft | Jones, K.D. et al. [29] | |
| False signals, represent nonexistent emergencies | Collisions, pollution, grounding, interruption of port operations | Alcaide and Llave [30] | |
| ECDIS | Physical access Internet connection establishment Authorized access Operating system support and security patches Operating system configuration etc. | Provides physical/logical access Exploitation of well-known vulnerabilities Reduces performance and opens backdoor | Svilicic et al. [7] |
| Vulnerable versions of SMB and Remote Desktop Protocol (RDP) | Infection and dysfunctionality of all ECDIS stations in the network | Svilicic et al. [19] | |
| Outdated Apache web server Vulnerable version of SMB | Gain unauthorized access Remote attacker | Svilicic et al. [20] | |
| Vulnerable versions of SMB and Remote Desktop Protocol (RDP) | Execute arbitrary code without authentication Disclose sensitive information | Svilicic et al. [21] | |
| Designed without security, malicious version, malware | Hijacking, smuggling, theft | Jones, K.D. et al. [29] | |
| GNS spoofing by malware | Sails to different coordinates Crash the operator station | Lund et al. [18] | |
| Virus, DoS, spoofing | Not mentioned | Dumbala [28] | |
| SATCOM | Backdoors Hardcoded credentials Insecure protocols Undocumented protocols Password reset weaknesses | Install malicious firmware Execute arbitrary code | Santamarta [4] |
| Unencrypted protocols | Disclose sensitive information | Pavur et al. [25] | |
| Default credentials, not updated software, etc. | Not mentioned | Dumbala [28] | |
| Cyberattack by hostile states | Disclose sensitive information | Haynes [31] | |
| BWMS | Phishing emails, malware | Ransomware, false command | Dumbala [28] |
| Cyberattack by hostile states | Sinking of the ship | Haynes [31] | |
| Designed without security, malicious version, malware | Hijacking, smuggling, theft | Jones, K.D et al. [29] | |
| other | NMEA: unencrypted message DoS attacks | Injection of fake messages System shutdown | Caprolu et al. [24] |
| Inaccurate ENC file | Sinking of the ship | Awan and Ghamdi [23] | |
| Default account and password | Elevation privilege | Tierney et al. [26] | |
| Default password and the passenger’s Wi-Fi | Access system inside the ship Information intercept | Tierney et al. [27] | |
| Described the risk levels of these attack surfaces using risk assessment methodologies | Hyra et al. [8] | ||
| Proposed a risk assessment method for ship control systems using fuzzy sets and attack trees | Shang et al. [22] | ||
| Tactic | Description |
|---|---|
| Reconnaissance |
|
| Resource Development |
|
| Initial Access |
|
| Lateral Movement |
|
| Command and Control |
|
| Impact |
|
| Tactic | Description |
|---|---|
| Reconnaissance |
|
| Initial Access |
|
| Defense Evasion |
|
| Execution |
|
| Persistence |
|
| Collection |
|
| Command and Control |
|
| Impact |
|
| Tactic | Description |
|---|---|
| Resource Development |
|
| Initial Access |
|
| Reconnaissance |
|
| Execution |
|
| Discovery |
|
| Lateral Movement |
|
| Impact |
|
| Type | System |
|---|---|
| Communication Systems |
|
| Propulsion, Machinery and Power Control Systems |
|
| Navigation Systems |
|
| Cargo Management System |
|
| Tactic | Description |
|---|---|
| Command and Control |
|
| Lateral Movement |
|
| Execution |
|
| Initial Access |
|
| Discovery |
|
| Inhibit Response Function |
|
| Impact |
|
| Tactic | Description |
|---|---|
| Initial Access |
|
| Collection |
|
| Impact |
|
| Tactic | Description |
|---|---|
| Initial Access |
|
| Persistence |
|
| Privilege Escalation |
|
| Evasion |
|
| Discovery |
|
| Lateral Movement |
|
| Inhibit Response Function |
|
| Impair Process Control |
|
| Impact |
|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jo, Y.; Choi, O.; You, J.; Cha, Y.; Lee, D.H. Cyberattack Models for Ship Equipment Based on the MITRE ATT&CK Framework. Sensors 2022, 22, 1860. https://doi.org/10.3390/s22051860
Jo Y, Choi O, You J, Cha Y, Lee DH. Cyberattack Models for Ship Equipment Based on the MITRE ATT&CK Framework. Sensors. 2022; 22(5):1860. https://doi.org/10.3390/s22051860
Chicago/Turabian StyleJo, Yonghyun, Oongjae Choi, Jiwoon You, Youngkyun Cha, and Dong Hoon Lee. 2022. "Cyberattack Models for Ship Equipment Based on the MITRE ATT&CK Framework" Sensors 22, no. 5: 1860. https://doi.org/10.3390/s22051860
APA StyleJo, Y., Choi, O., You, J., Cha, Y., & Lee, D. H. (2022). Cyberattack Models for Ship Equipment Based on the MITRE ATT&CK Framework. Sensors, 22(5), 1860. https://doi.org/10.3390/s22051860






