Application and Advances in Radiographic and Novel Technologies Used for Non-Intrusive Object Inspection
Abstract
:1. Introduction
- The Schengen Information System (SIS). This system takes its roots from 2001, and currently coordinates the databases of 26 countries. Technically, SIS is based on classic star data processing architecture, with the reference database located in the French Republic, while all other states have a copy of this database. SIS stores data on persons that are refused entry; suspected of a crime; data referred to lost or stolen weapons, motor vehicles, identity documents, etc. France manages the SIS reference database and is responsible for its constant update every five minutes [17].
- Eurodac. European Asylum Dactyloscopy Database (Eurodac) is a database that includes fingerprints of asylum seekers and irregular border crossers [18]. This database is used by 27 EU Member States and Associated Countries and is aimed at controlling both the legal and illegal movement of asylum seekers within Eurodac countries.
- The Visa Information System (VIS). This database contains information required from visa applicants wishing to enter Schengen Area countries, including biometric data, such as fingerprint and facial images. Similar systems are implemented in other parts of the globe, namely, in the USA it is known as the Arrival and Departure Information System (ADIS) [19], SmartGate in Australia, and others [20].
2. Technology Used for X-ray Screening
2.1. Planar Radiography
2.2. X-ray Computed Tomography (CT)
2.3. Dual- and Multi-Energy Imaging
2.4. Backscatter Techniques
2.5. X-ray Diffraction Imaging
2.6. X-ray Technology Implementation Use-Cases
3. Technology Used for Results Analysis
- (1)
- Supervised learning;
- (2)
- Unsupervised learning;
- (3)
- Reinforcement learning.
3.1. Pattern Recognition
3.2. Support Vector Machines (SVM)
3.3. Artificial Neural Networks (ANNs)
3.4. Deep Learning
4. Novel Approaches
4.1. Electronic Nose
4.2. Mimicking Animal Sense Receptors
4.3. Other Techniques
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Polner, M. Customs and Illegal Trade: Old Game–New Rules. J. Borderl. Stud. 2015, 30, 329–344. [Google Scholar] [CrossRef]
- Baird, T. Functional Actorness? Border Security in the EU and Turkey. Int. J. Public Adm. 2015, 38, 849–859. [Google Scholar] [CrossRef]
- Bevir, M.; Phillips, R. Genealogies of European governance. Comp. Eur. Politics 2017, 15, 685–704. [Google Scholar] [CrossRef] [Green Version]
- Borzel, T.A.; Risse, T. From the Euro to the Schengen Crises: European Integration Theories, Politicization, and Identity Politics. J. Eur. Public Policy 2018, 25, 83–108. [Google Scholar] [CrossRef]
- Ceccorulli, M. Back to Schengen: The Collective Securitisation of the EU Free-Border Area. West Eur. Politics 2019, 42, 302–322. [Google Scholar] [CrossRef]
- Thorleifsson, C. Disposable Strangers: Far-Right Securitisation of Forced Migration in Hungary. Soc. Anthropol. 2017, 25, 318–334. [Google Scholar] [CrossRef]
- Trauner, F.; Ripoll Servent, A. The Communitarization of the Area of Freedom, Security and Justice: Why Institutional Change Does Not Translate into Policy Change. JCMS J. Common Mark. Stud. 2016, 54, 1417–1432. [Google Scholar] [CrossRef] [Green Version]
- Vollmer, B.A. A Hermeneutical Approach to European Bordering. J. Contemp. Eur. Stud. 2017, 25, 1–15. [Google Scholar] [CrossRef]
- Williams, J.M. The Safety/Security Nexus and the Humanitarianisation of Border Enforcement. Geogr. J. 2016, 182, 27–37. [Google Scholar] [CrossRef]
- Frontex. Available online: https://frontex.europa.eu (accessed on 4 February 2022).
- Tholen, B. The Changing Border: Developments and Risks in Border Control Management of Western Countries. Int. Rev. Adm. Sci. 2010, 76, 259–278. [Google Scholar] [CrossRef]
- Broeders, D. The New Digital Borders of Europe: EU Databases and the Surveillance of Irregular Migrants. Int. Sociol. 2007, 22, 71–92. [Google Scholar] [CrossRef]
- Cornelius, W.A. Death at the Border: Efficacy and Unintended Consequences of US Immigration Control Policy. Popul. Dev. Rev. 2001, 27, 661–685. [Google Scholar] [CrossRef] [Green Version]
- SmartGate. Available online: https://www.abf.gov.au/entering-and-leaving-australia/smartgates (accessed on 4 February 2022).
- US-VISIT. Available online: https://ois.usc.edu/students/travel/usvisit/ (accessed on 4 February 2022).
- e-Borders (UK). Available online: https://www.nao.org.uk/report/home-office-e-borders-and-successor-programmes/ (accessed on 4 February 2022).
- The Schengen Information System. Available online: https://ec.europa.eu/home-affairs/policies/schengen-borders-and-visa/schengen-information-system_en (accessed on 4 February 2022).
- European Asylum Dactyloscopy Database (Eurodac). Available online: https://data.europa.eu/data/datasets/eurodac-statistics?locale=en (accessed on 4 February 2022).
- The Visa Information System (VIS). Available online: https://ec.europa.eu/home-affairs/policies/schengen-borders-and-visa/visa-information-system_en (accessed on 4 February 2022).
- Brouwer, E. Digital Borders and Real Rights: Effective Remedies for Third-Country Nationals in the Schengen Information System; Martinus Nijhoff: Boston, MA, USA, 2008. [Google Scholar]
- Reims, N.; Schoen, T.; Boehnel, M.; Sukowski, F.; Firsching, M. Strategies for efficient scanning and reconstruction methods on very large objects with high-energy X-ray computed tomography. Dev. X-ray Tomogr. IX 2014, 9212, 921209. [Google Scholar] [CrossRef]
- Chen, G.; Bjorkholm, P.; Fox, T.R.; Wilson, Z.; Bonsergent, X.; McDaniel, F.D.; Doyle, B.L. X-ray Cargo Inspection: Status and Trends. AIP Conf. Proc. 2009, 1099, 570–573. [Google Scholar] [CrossRef]
- Macdonald, R.D.R. Design and implementation of a dual-energy X-ray imaging system for organic material detection in an airport security application. In Proceedings of the SPIE 4301, Machine Vision Applications in Industrial Inspection IX, San Jose, CA, USA, 20–26 January 2001; Volume 4301, pp. 31–41. [Google Scholar] [CrossRef]
- Wells, K.; Bradley, D.A. A review of X-ray explosives detection techniques for checked baggage. Appl. Radiat. Isot. 2012, 70, 1729–1746. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Martz, H.E.; Crawford, C.R. Explosive detection in aviation applications using CT. In Proceedings of the 11th International Meeting on Fully Three-Dimensional Image Reconstruction in Radiology and Nuclear Medicine, Potsdam, Germany, 11–15 July 2011. [Google Scholar]
- Knoll, G.F. Radiation Detection & Measurement; Wiley: New York, NY, USA, 2000. [Google Scholar]
- Anderson, N.G.; Butler, A.P.; Scott, N.J.; Cook, N.J.; Butzer, J.S.; Schleich, N.; Firsching, M.; Grasset, R.; Ruiter, N.; Campbell, M.; et al. Spectroscopic (multi-energy) CT distinguishes iodine and barium contrast material in MICE. Eur. Radiol. 2010, 20, 2126–2134. [Google Scholar] [CrossRef] [PubMed]
- Boll, D.T.; Patil, N.A.; Paulson, E.K.; Merkle, E.M.; Nelson, R.C.; Schindera, S.T.; Roessl, E.; Martens, G.; Proksa, R.; Fleiter, T.R.; et al. Focal cystic high-attenuation lesions: Characterization in renal phantom by using photon-counting spectral CT-improved differentiation of lesion composition. Radiology 2009, 254, 270–276. [Google Scholar] [CrossRef]
- Roessl, E.; Proksa, R. K-edge imaging in X-ray computed tomography using multi-bin photon counting detectors. Phys. Med. Biol. 2007, 52, 4679–4696. [Google Scholar] [CrossRef]
- Harding, G.; Kosanetzky, J. Scattered X-ray beam nondestructive testing. Nucl. Instrum. Methods Phys. Res. 1989, A280, 517–528. [Google Scholar] [CrossRef]
- Harding, G.; Jordan, B.; Kosanetzky, J. A new fluorescent X-ray source for photon scattering investigations. Phys. Med. Biol. 1991, 36, 1573–1583. [Google Scholar] [CrossRef]
- Harding, G.; Harding, A. X-ray diffraction imaging for explosives detection. In Counterterrorist Detection Techniques of Explosives; Yinon, J., Ed.; Elsevier: Amsterdam, The Netherlands; London, UK, 2007; pp. 199–236. [Google Scholar]
- Gil, Y.; Oh, Y.; Cho, M.; Namkung, W. Radiography simulation on single-shot dual-spectrum X-ray for cargo inspection system. Appl. Radiat. Isot. 2011, 69, 389–393. [Google Scholar] [CrossRef] [PubMed]
- Stevenson, J.; Gozani, T.; Elsalim, M.; Condron, C.; Brown, C. Linac based photofission inspection system employing novel detection concepts. Nucl. Instrum. Methods Phys. Research. Sect. A Accel. Spectrometers Detect. Assoc. Equip. 2011, 652, 124–128. [Google Scholar] [CrossRef]
- Duan, X.; Cheng, J.; Zhang, L.; Xing, Y.; Chen, Z.; Zhao, Z. X-ray cargo container inspection system with few-view projection imaging. Nucl. Instrum. Methods Phys. Research. Sect. A Accel. Spectrometers Detect. Assoc. Equip. 2009, 598, 439–444. [Google Scholar] [CrossRef]
- Han, Y.P.; Han, Y.; Wang, L.M.; Pan, J.X. Development of X-ray digital radiography automatic inspection system for testing the interior structure of complex product. Binggong Xuebao/Acta Armamentarii 2012, 3, 881–885. [Google Scholar]
- Malyshev, V.P.; Sidorov, A.V.; Klinovskiy, P.O.; Smekalkin, V.S.; Efremov, D.V. The IDK-6/9MeV linear electron accelerator and its application in the customs inspection system. In Proceedings of the 23rd Russian Particle Accelerator Conference, Saint Petersburg, Russia, 27–28 September 2012; pp. 549–550. [Google Scholar]
- Miller, E.A.; Caggiano, J.A.; Runkle, R.C.; White, T.A.; Bevill, A.M. Scatter in cargo radiography. Appl. Radiat. Isot. 2011, 69, 594–603. [Google Scholar] [CrossRef]
- Pourghassem, H.; Fesharaki, N.; Tahmasebi, A. Material detection based on GMM-based power density function estimation and fused image in dual-energy X-ray images. In Proceedings of the 4th International Conference on Computational Intelligence and Communication Networks, CICN, Mathura, India, 3–5 November 2012; Volume 6375134, pp. 364–368. [Google Scholar]
- Franzel, T.; Shmidt, U.; Roth, S. Object detection in multi-view X-ray images. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics; Springer: Berlin/Heidelberg, Germany, 2012; Volume 7476 LNCS, pp. 144–154. [Google Scholar]
- Frosio, I.; Borghese, N.A.; Lissandrello, F.; Venturino, G.; Rotondo, G. Optimized acquisition geometry for X-ray inspection. In Proceedings of the Conference Record–IEEE Instrumentation and Measurement Technology Conference, Hangzhou, China, 10–12 May 2011; Volume 5944195, pp. 300–305. [Google Scholar]
- Alan, A. Patent application. In Cargo Inspection System; Rapiscan Systems, Inc.: Torrance, CA, USA, 2015. [Google Scholar]
- Joseph, B. Patent application. In Mobile Aircraft Inspection System; Rapiscan Systems, Inc.: Torrance, CA, USA, 2014. [Google Scholar]
- Joseph, B.; Mathew, B.C.; Tsahi, G. Langeveld Willem Gerhardus Johannes, Stevenson John David Patent application. In A High-Energy X-ray Spectroscopy-Based Inspection System and Methods to Determine the Atomic Number of Materials; Rapiscan Systems Inc.: Torrance, CA, USA, 2013. [Google Scholar]
- Liang, C.X.; Li, C.; Chun, H.M.; Rui, Y.L.; Wen, D.M.; Wu, K.W.; Yang, X.Y.; Kai, X.; Qing, L.Y.; Qing, L.G.; et al. Patent application. In Dual-Energy X-ray Body Scanning Device and Image Processing Method; First Res Inst of Ministry of Public Security of p r c.; Beijing Zhongdun Anmin Analysis Technology Co., Ltd.; European Patent Office: Munich, Germany, 2012. [Google Scholar]
- Toshiyasu, S.; Tadashi, M.; Toshihide, S.; Junichi, S.; Shinji, T. Patent application. In Radiation Detection Device, Radiation Image Acquisition System, Radiation Inspection System, and Radiation Detection Method; Hamamatsu Photonics KK; United States Patent: Alexandria, VA, USA, 2011. [Google Scholar]
- Katz Jonathan, I.; Morris Christopher, L. Patent application. In X-ray Radiography for Container Inspection; The United States of America as Represented by the United States Department of Energy; United States Patent: Alexandria, VA, USA, 2011. [Google Scholar]
- Satpal, S.; Satpal, S. Patent application. In Multiview X-ray Inspection System; United States Patent: Alexandria, VA, USA, 2011. [Google Scholar]
- Uwe, S. Patent application. In Method for Improving the Ability to Recognize Materials in an X-ray Inspection System, and X-ray Inspection System; Smiths Heimann GmbH: Wiesbaden, Germany, 2010. [Google Scholar]
- Tsutomu, Y.; Shuichiro, Y.; Masashi, Y. Patent application. In X-ray Inspection Apparatus and X-ray Inspection Method; JOB CORPORATION; United States Patent: Alexandra, VA, USA, 2020. [Google Scholar]
- Mitchell, T. Machine Learning; McGraw Hill: New York, NY, USA, 1997; ISBN 0-07-042807-7. [Google Scholar]
- Vinuesa, R.; Azizpour, H.; Leite, I.; Balaam, M.; Dignum, V.; Domisch, S.; Felländer, A.; Langhans, S.D.; Tegmark, M.; Nerini, F.F. The role of artificial intelligence in achieving the Sustainable Development Goals. Nat. Commun. 2020, 11, 233. [Google Scholar] [CrossRef] [Green Version]
- El Naqa, I.; Li, J.; Murphy, M.J. What Is Machine Learning? Machine Learning in Radiation Oncology: Theory and Applications; Springer: Cham, Germany, 2015; pp. 3–11. [Google Scholar] [CrossRef]
- Pérez, J.M.; Le Clainche, S.; Vega, J.M. Reconstruction of three-dimensional flow fields from two-dimensional data. J. Comput. Phys. 2020, 407, 109239. [Google Scholar] [CrossRef]
- Bell, E.; Mendez, C.; Le Clainche, S.; Vega, J.M. A reduced order model to create two-dimensional flow fields from uni-dimensional data. In AIAA Scitech 2019 Forum; American Institute of Aeronautics and Astronautics: San Diego, CA, USA, 2019. [Google Scholar] [CrossRef]
- Le Clainche, S. An Introduction to Some Methods for Soft Computing in Fluid Dynamics. In 14th International Conference on Soft Computing Models in Industrial and Environmental Applications (SOCO 2019). SOCO 2019; Martínez Álvarez, F., Troncoso Lora, A., Sáez Muñoz, J., Quintián, H., Corchado, E., Eds.; Advances in Intelligent Systems and Computing; Springer: Cham, Germany, 2020; Volume 950. [Google Scholar] [CrossRef]
- Vega, J.M.; Le Clainche, S.L. Higher Order Dynamic Mode Decomposition and Its Applications; Elsevier: Amsterdam, The Netherlands, 2020; ISBN 9780128197431. [Google Scholar]
- Abadía-Heredia, R.; López-Martín, M.; Carro, B.; Arribas, J.I.; Pérez, J.M.; Le Clainche, S. A predictive hybrid reduced order model based on proper orthogonal decomposition combined with deep learning architectures. Expert Syst. Appl. 2022, 187, 115910. [Google Scholar] [CrossRef]
- Eivazi, H.; Le Clainche, S.; Hoyas, S.; Viuesa, R. Towards extraction of orthogonal and parsimonious non-linear modes from turbulent flows. arXiv 2021, arXiv:2109.01514. [Google Scholar]
- Bishop, C.M. Neural Networks for Pattern Recognition; Oxford University Press: New York, NY, USA, 1995. [Google Scholar]
- Bishop, C.M. Pattern Recognition and Machine Learning; Springer: New York, NY, USA, 2013. [Google Scholar]
- Zurada, J.M. Introduction to Artificial Neural Systems; West Publishing House: St. Paul, MN, USA, 1992. [Google Scholar]
- Thazin, Y.; Pobkrut, T.; Kerdcharoen, T. Prediction of acidity levels of fresh roasted coffees using e-nose and artificial neural network. In Proceedings of the 10th International Conference on Knowledge and Smart Technology, Chiang Mai, Thailand, 31 January–3 February 2018; pp. 210–215. [Google Scholar] [CrossRef]
- Zhang, L.; Tian, F.C. Performance study of multilayer perceptrons in a low-cost electronic nose. IEEE Trans. Instrum. Meas. 2014, 63, 1670–1679. [Google Scholar] [CrossRef]
- Wang, L.P. Support Vector Machines: Theory and Applications; Springer: Berlin, Germany, 2005. [Google Scholar]
- Laref, R.; Losson, E.; Sava, A.; Adjallah, K.; Siadat, M. A comparison between SVM and PLS for E-nose based gas concentration monitoring. In Proceedings of the IEEE International Conference on Industrial Technology, Lyon, France, 20–22 February 2018; pp. 1335–1339. [Google Scholar] [CrossRef]
- Duda, R.O.; Hart, P.E.; Stork, D.G. Pattern Classification, 2nd ed.; John Wiley and Sons: New York, NY, USA, 2000. [Google Scholar]
- Jolliffe, I. Principal Component Analysis. International Encyclopedia of Statistical Science; Lovric, M., Ed.; Springer: Berlin, Germany, 2011. [Google Scholar] [CrossRef]
- Baskar, C.; Nesakumar, N.; Rayappan, J.B.B.; Doraipandian, M. A framework for analysing E-nose data based on fuzzy set multiple linear regression: Paddy quality assessment. Sens. Actuators A Phys. 2017, 267, 200–209. [Google Scholar] [CrossRef]
- Amemiya, T. Advanced Econometrics; Harvard University Press: Cambridge, MA, USA, 1985. [Google Scholar]
- McLachlan, G.J. Discriminant Analysis and Statistical Pattern Recognition; Wiley: New York, NY, USA, 2005. [Google Scholar]
- Theodoridis, S.; Koutroumbas, K. Pattern Recognition, 4th ed.; Academic Press Inc.: Orlando, FL, USA, 2009. [Google Scholar]
- Tian, X.J.; Wang, J.; Cui, S.Q. Analysis of pork adulteration in minced mutton using electronic nose of metal oxide sensors. J. Food Eng. 2013, 119, 744–749. [Google Scholar] [CrossRef]
- Burges, C.J.C. A tutorial on support vector machines for pattern recognition. Data Min. Knowl. Discov. 1998, 2, 121–167. [Google Scholar] [CrossRef]
- Goudjil, M.; Koudil, M.; Bedda, M.; Ghoggali, N. A novel active learning method using SVM for text classification. Int. J. Autom. Comput. 2018, 15, 290–298. [Google Scholar] [CrossRef]
- Barghout, L. Spatial-Taxon Information Granules as Used in Iterative Fuzzy-Decision-Making for Image Segmentation. In Granular Computing and Decision-Making; Springer International Publishing: Berlin/Heidelberg, Germany, 2015; pp. 285–318. [Google Scholar]
- Wei, Z.B.; Xiao, X.Z.; Wang, J.; Wang, H. Identification of the rice wines with different marked ages by electronic nose coupled with smartphone and cloud storage platform. Sensors 2017, 17, 2500. [Google Scholar] [CrossRef] [Green Version]
- Saha, P.; Ghorai, S.; Tudu, B.; Bandyopadhyay, R.; Bhattacharyya, N. Multi-class support vector machine for quality estimation of black tea using electronic nose. In Proceedings of the 6th International Conference on Sensing Technology, Kolkata, India, 18–21 December 2012; pp. 571–576. [Google Scholar] [CrossRef]
- Chang, Z.Y.; Lv, J.H.; Qi, H.Y.; Ma, Y.H.; Chen, D.H.; Xie, J.; Sun, Y.H. Bacterial infection potato tuber soft rot disease detection based on electronic nose. Open Life Sci. 2017, 12, 379–385. [Google Scholar] [CrossRef]
- Leal, R.V.; Quiming, A.X.C.; Villaverde, J.F.; Yumang, A.N.; Linsangan, N.B.; Caya, M.V.C. Determination of schizophrenia using electronic nose via support vector machine. In Proceedings of the 9th International Conference on Biomedical Engineering and Technology, Tokyo, Japan, 28–30 March 2019; pp. 13–17. [Google Scholar] [CrossRef]
- Zell, A. Chapter 5.2. In Simulation Neuronaler Netze [Simulation of Neural Networks] (German), 1st ed.; Addison-Wesley: Boston, MA, USA, 1994; ISBN 3-89319-554-8. [Google Scholar]
- Jain, A.K.; Mao, J.C.; Mohiuddin, K.M. Artificial neural networks: A tutorial. Computer 1996, 29, 31–44. [Google Scholar] [CrossRef] [Green Version]
- Thakral, B.; Gupta, S. Artificial neural networks for e-NOSE: A review. Int. J. Appl. Eng. Res. 2012, 7, 1601–1604. [Google Scholar]
- Srinivasan, P.A.; Guastoni, L.; Azizpour, H.; Schlatter, P.; Vinuesa, R. Predictions of turbulent shear flows using deep neural networks. Phys. Rev. Fluids 2019, 4, 054603. [Google Scholar] [CrossRef] [Green Version]
- Khan, S.; Rahmani, H.; Shah SA, A.; Bennamoun, M.; Medioni, G.; Dickinson, S. A Guide to Convolutional Neural Networks for Computer Vision; Morgan & Claypool Publishers: San Rafael, CA, USA, 2018; Volume 8, pp. 1–207. [Google Scholar] [CrossRef]
- Hubel, D.H.; Wiesel, T.N. Receptive fields, binocular interaction and functional architecture in the cat′s visual cortex. J. Physiol. 1962, 160, 106–154. [Google Scholar] [CrossRef]
- Guastoni, L.; Güemes, A.; Ianiro, A.; Discetti, S.; Schlatter, P.; Azizpour, H.; Vinuesa, R. Convolutional-network models to predict wall-bounded turbulence from wall quantities. J. Fluid Mech. 2021, 928, A27. [Google Scholar] [CrossRef]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef] [PubMed]
- Güemes, A.; Discetti, S.; Ianiro, A.; Sirmacek, B.; Azizpour, H.; Vinuesa, R. From coarse wall measurements to turbulent velocity fields through deep learning. Phys. Fluids 2021, 33, 075121. [Google Scholar] [CrossRef]
- Buda, T.S.; Caglayan, B.; Assem, H. DeepAD: A generic framework based on deep learning for time series anomaly detection. In Proceedings of the 22nd Pacific-Asia Conference Advances in Knowledge Discovery and Data Mining, Melbourne, Australia, 3–6 June 2018; Springer: Melbourne, Australia, 2018; pp. 577–588. [Google Scholar] [CrossRef]
- Litjens, G.; Kooi, T.; Bejnordi, B.E.; Setio, A.A.A.; Ciompi, F.; Ghafoorian, M.; van der Laak, J.A.W.M.; van Ginneken, B.; Sánchez, C.I. A survey on deep learning in medical image analysis. Med. Image Anal. 2017, 42, 60–88. [Google Scholar] [CrossRef] [Green Version]
- Chen, L.C.; Papandreou, G.; Kokkinos, I.; Murphy, K.P.; Yuille, A.L. DeepLab: Semantic image segmentation with deep convolutional nets, atrous convolution, and fully connected CRFs. IEEE Trans. Pattern Anal. Mach. Intell. 2018, 40, 834–848. [Google Scholar] [CrossRef] [Green Version]
- Yao, Z.J.; Bi, J.; Chen, Y.X. Applying deep learning to individual and community health monitoring data: A survey. Int. J. Autom. Comput. 2018, 15, 643–655. [Google Scholar] [CrossRef]
- Wu, C.Y.; Karanasou, P.; Gales, M.J.F.; Sim, K.C. Stimulated deep neural network for speech recognition. In Interspeech 2016, International Speech Communication Association, San Francisco, USA; International Speech Communication Association (ISCA): Baixas, France, 2016; pp. 400–404. [Google Scholar] [CrossRef] [Green Version]
- Sun, X.D.; Wu, P.C.; Hoi, S.C.H. Face detection using deep learning: An improved faster RCNN approach. Neurocomputing 2018, 299, 42–50. [Google Scholar] [CrossRef] [Green Version]
- Ranjan, R.; Sankaranarayanan, S.; Bansal, A.; Bodla, N.; Chen, J.C.; Patel, V.M.; Castillo, C.D.; Chellappa, R. Deep learning for understanding faces: Machines may be just as good, or better, than humans. IEEE Signal Process. Mag. 2018, 35, 66–83. [Google Scholar] [CrossRef]
- Lu, Y.Z. A novel face recognition algorithm for distinguishing faces with various angles. Int. J. Autom. Comput. 2008, 5, 193–197. [Google Scholar] [CrossRef]
- Tao, J.H.; Huang, J.; Li, Y.; Lian, Z.; Niu, M.Y. Semi-supervised ladder networks for speech emotion recognition. Int. J. Autom. Comput. 2019, 16, 437–448. [Google Scholar] [CrossRef]
- Chan, T.H.; Jia, K.; Gao, S.H.; Lu, J.W.; Zeng, Z.N.; Ma, Y. PCANet: A simple deep learning baseline for image classification? IEEE Trans. Image Process. 2015, 24, 5017–5032. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- He, K.M.; Zhang, X.Y.; Ren, S.Q.; Sun, J. Deep residual learning for image recognition. In Proceedings of the Conference on Computer Vision and Pattern Recognition, Las Vegas, NV, USA, 27–30 June 2016; pp. 770–778. [Google Scholar]
- Zhao, B.; Feng, J.S.; Wu, X.; Yan, S.C. A survey on deep learning-based fine-grained object classification and semantic segmentation. Int. J. Autom. Comput. 2017, 14, 119–135. [Google Scholar] [CrossRef]
- Li, A.X.; Zhang, K.X.; Wang, L.W. Zero-shot fine grained classification by deep feature learning with semantics. Int. J. Autom. Comput. 2019, 16, 563–574. [Google Scholar] [CrossRef] [Green Version]
- Qi, P.F.; Meng, Q.H.; Zeng, M. A CNN-based simplified data processing method for electronic noses. In Proceedings of the ISOCS/IEEE International Symposium on Olfaction and Electronic Nose, Montreal, QC, Canada, 28–31 May 2017; pp. 1–3. [Google Scholar] [CrossRef]
- Peng, P.; Zhao, X.J.; Pan, X.F.; Ye, W.B. Gas classification using deep convolutional neural networks. Sensors 2018, 18, 157. [Google Scholar] [CrossRef] [Green Version]
- Wei, G.F.; Li, G.; Zhao, J.; He, A.X. Development of a Le-Net-5 gas identification CNN structure for electronic noses. Sensors 2019, 19, 217. [Google Scholar] [CrossRef] [Green Version]
- Arshak, K.; Moore, E.; Lyons, G.M.; Harris, J.; Clifford, S. A review of gas sensors employed in electronic nose applications. Sens. Rev. 2004, 24, 181–198. [Google Scholar] [CrossRef] [Green Version]
- Alassi, A.; Benammar, M.; Brett, D. Quartz crystal microbalance electronic interfacing systems: A review. Sensors 2017, 17, 2799. [Google Scholar] [CrossRef] [Green Version]
- Yan, Y.; Lu, D.D.; Hao, H.; Hou, H.P.; Zhang, T.; Wu, L.M.; Cai, L.K. Polyaniline-modified quartz crystal microbalance sensor for detection of formic acid gas. Water Air Soil Pollut. 2012, 223, 1275–1280. [Google Scholar] [CrossRef]
- Jha, S.K.; Hayashi, K. A quick responding quartz crystal microbalance sensor array based on molecular imprinted polyacrylic acids coating for selective identification of aldehydes in body odor. Talanta 2014, 134, 105–119. [Google Scholar] [CrossRef]
- Wasilewski, T.; Szulczynski, B.; Wojciechowski, M.; Kamysz, W.; Gebicki, J. A highly selective biosensor based on peptide directly derived from the HarmOBP7 aldehyde binding site. Sensors 2019, 19, 4284. [Google Scholar] [CrossRef] [Green Version]
- Soares, D. The Evolution of Dome Pressure Receptors in Crocodiles. Evol. Nerv. Syst. 2007, 2, 157–162. [Google Scholar] [CrossRef]
- Di-Poï, N.; Milinkovitch, M.C. Crocodylians evolved scattered multi-sensory micro-organs. Evodevo 2013, 4, 19. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Kanhere, E.; Wang, N.; Kottapalli, A.G.P.; Asadnia, M.; Subramaniam, V.; Miao, J.; Triantafyllou, M. Crocodile-inspired dome-shaped pressure receptors for passive hydrodynamic sensing. Bioinspir. Biomim. 2016, 11, 056007. [Google Scholar] [CrossRef] [PubMed]
- Mares, J.O.; Miller, J.K.; Sharp, N.D.; Moore, D.S.; Adams, D.E.; Groven, L.J.; Rhoads, J.F.; Son, S.F. Thermal and mechanical response of PBX 9501 under contact excitation. J. Appl. Phys. 2013, 113, 084904. [Google Scholar] [CrossRef] [Green Version]
- Zrimsek, A.B.; Bykov, S.V.; Asher, S.A. Deep Ultraviolet Standoff Photoacoustic Spectroscopy of Trace Explosives. Appl. Spectrosc. 2019, 73, 601–609. [Google Scholar] [CrossRef]
- Bloomfield, M.; Andrews, D.; Loeffen, P.; Tombling, C.; York, T.; Matousek, P. Non-invasive identification of incoming raw pharmaceutical materials using Spatially Offset Raman Spectroscopy. J. Pharm. Biomed. Anal. 2013, 76, 65–69. [Google Scholar] [CrossRef]
- Vinuesa, R.; Sirmacek, B. Interpretable deep-learning models to help achieve the Sustainable Development Goals. Nat. Mach. Intell. 2021, 3, 926. [Google Scholar] [CrossRef]
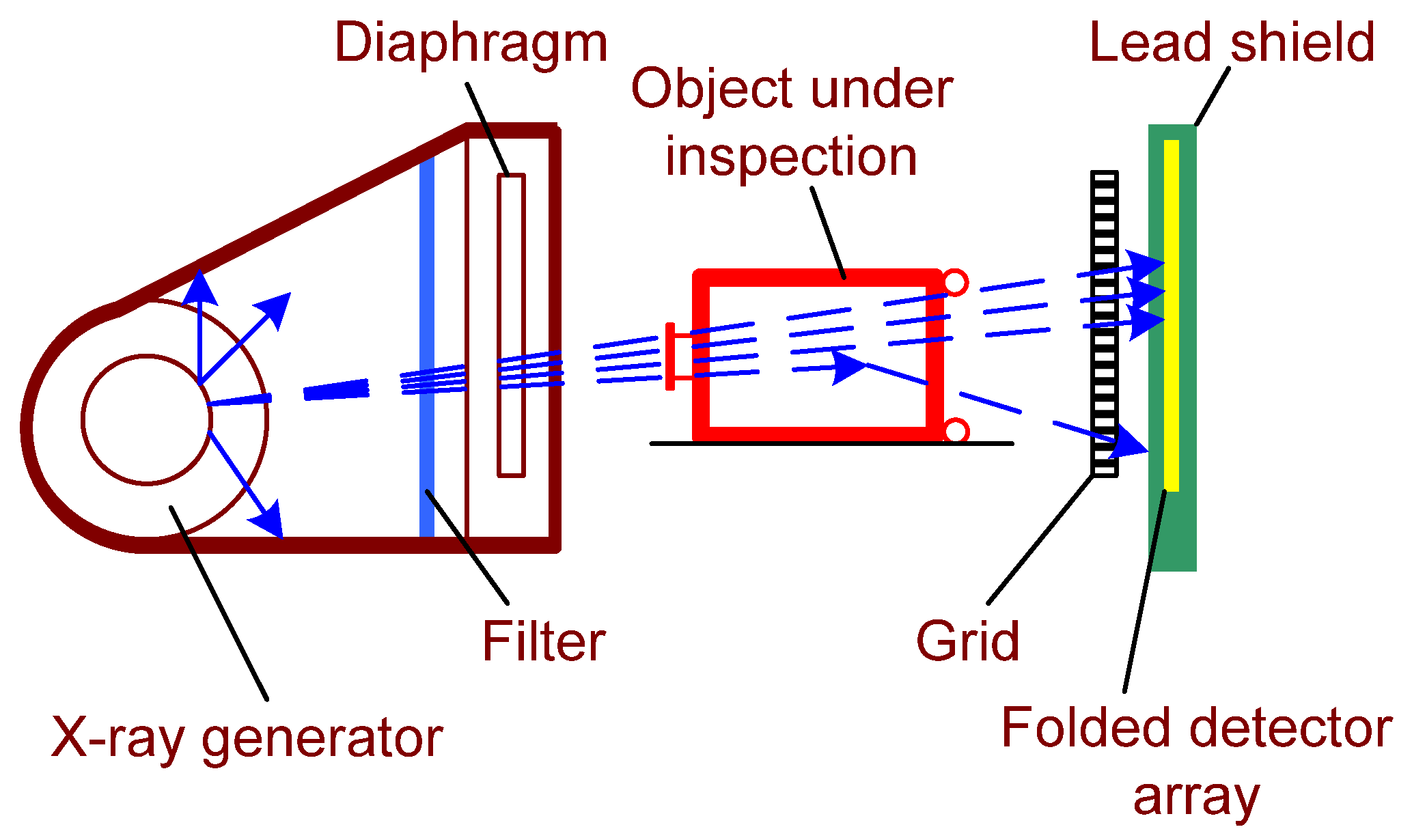
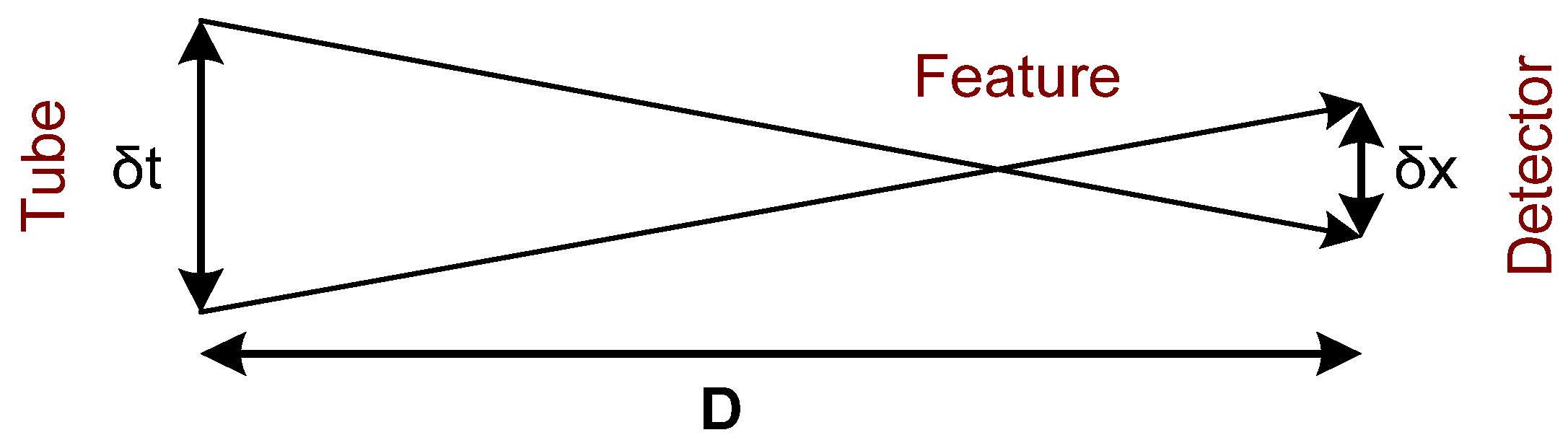
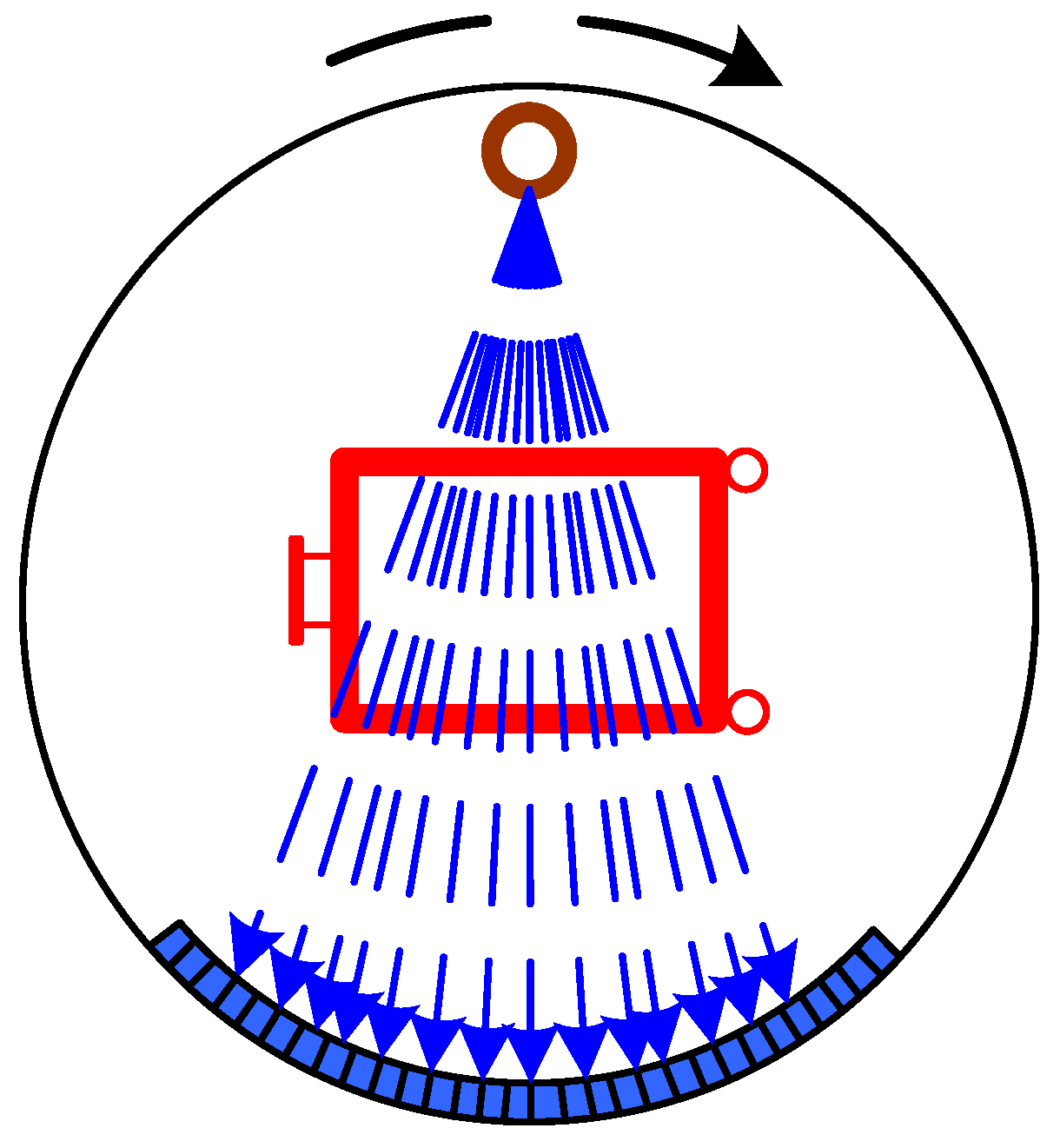
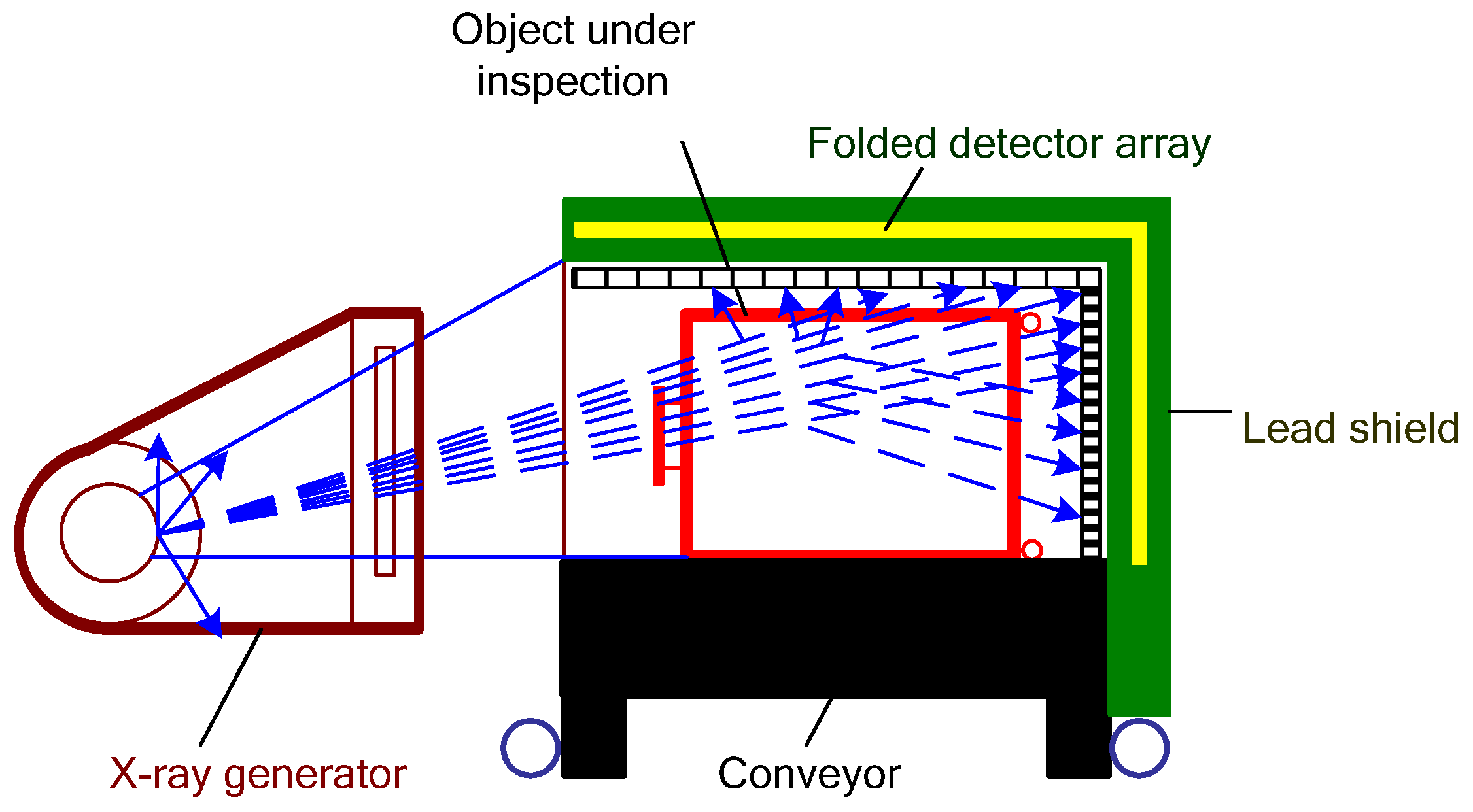

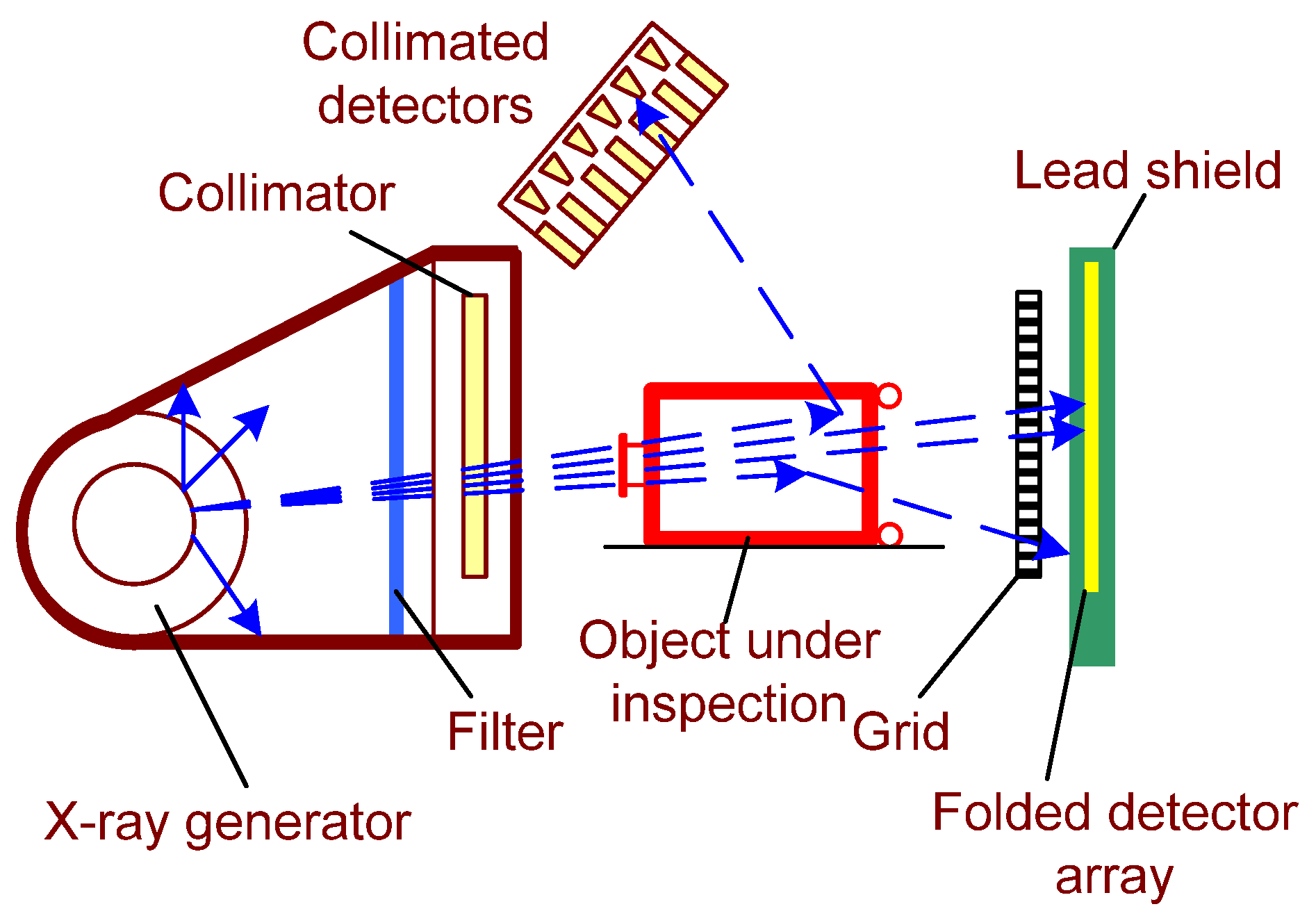
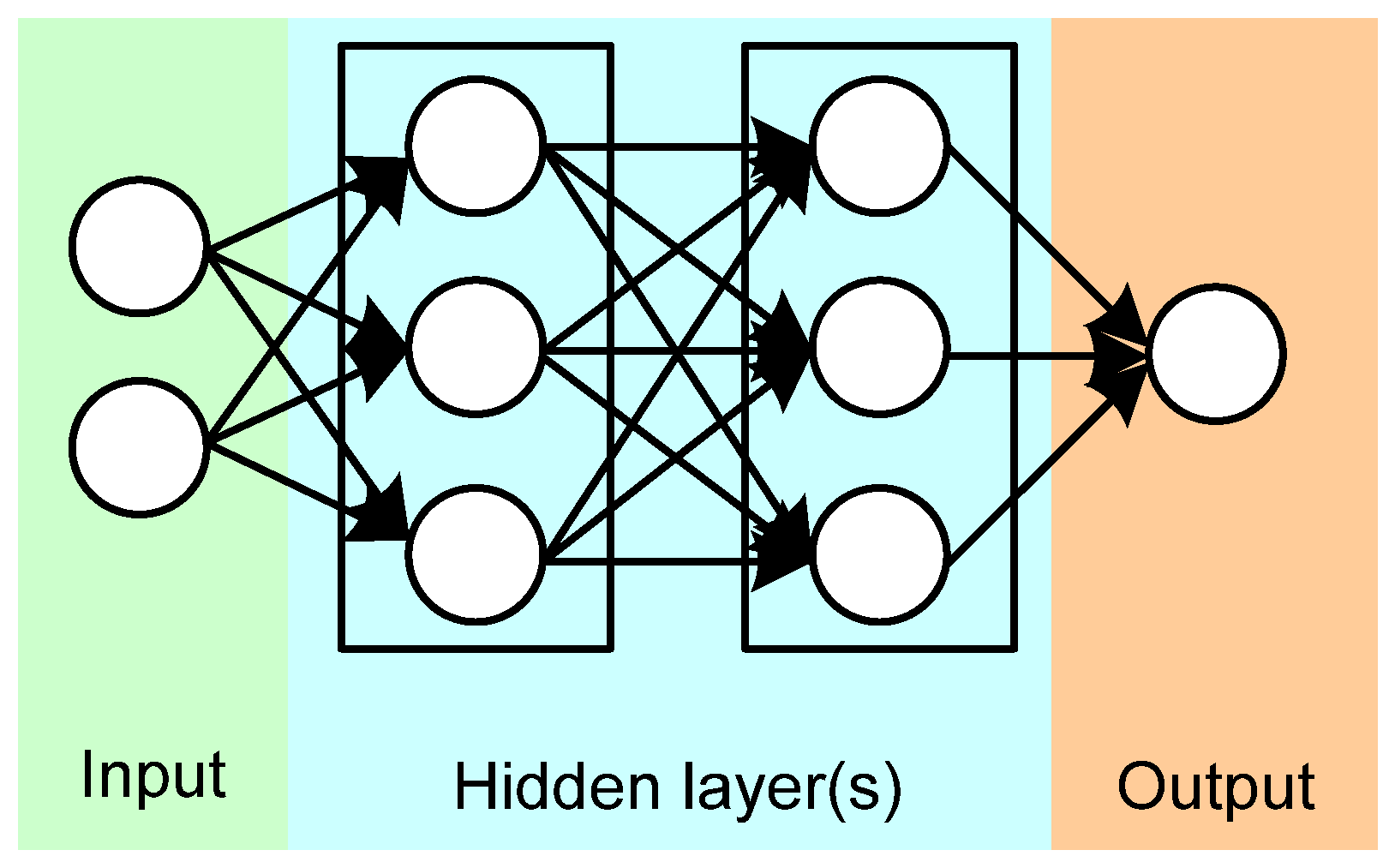
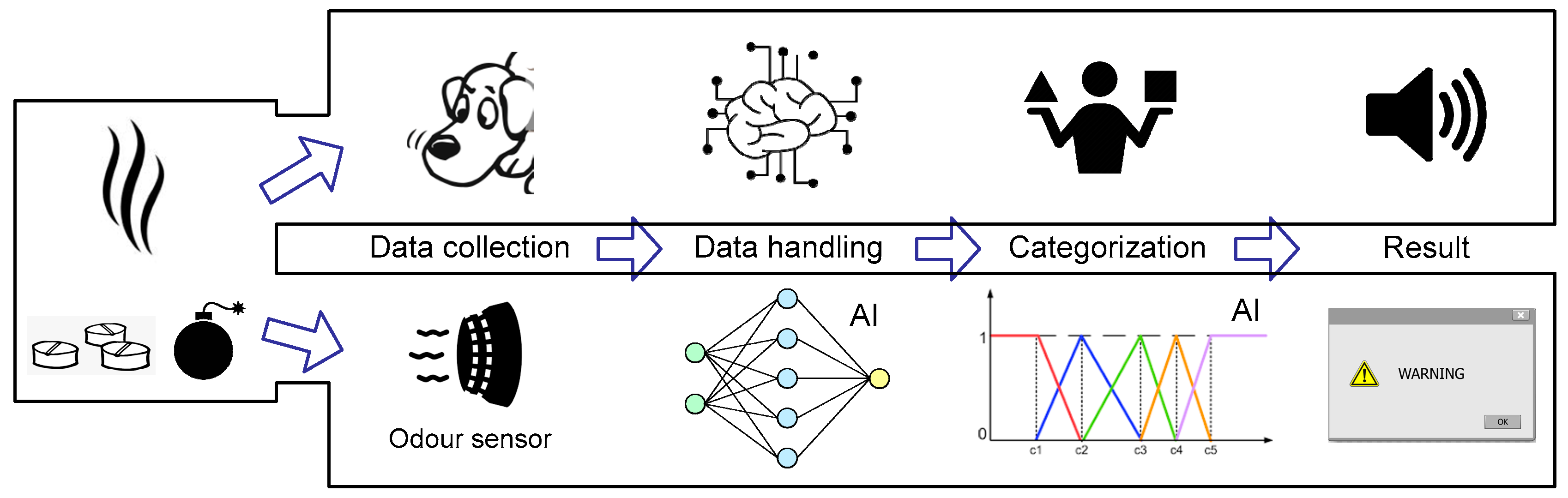
| Technique | Shape | Density | Structure | Suspicious Substances |
|---|---|---|---|---|
| Planar radiography | possible, limitations while superpositioning | not possible | not possible | based on shape only [24,25] |
| X-ray computed tomography | clear, absence of superposition | possible, using multi-energy analysis | limited | based on shape and density analysis [26] |
| Dual- and multi-energy imaging | clear, absence of superposition | possible, using multi-energy analysis | limited | based on shape and density analysis [27,28,29] |
| Backscatter techniques | clear, absence of superposition | possible | possible | drugs, explosives, ceramic weapons [30,31] |
| X-ray diffraction imagining | clear, absence of superposition | possible | organics, non-organics, liquids | wide range of explosives, including crystalline, amorphous, liquid, home-made [32] |
| Method | Pros | Cons |
|---|---|---|
| Principle component analysis | Relatively fast due to data dimension reduction Could be applied for probability estimation for multi-dimensional data | Large computational time for huge datasets processing |
| SVM | Efficient for solving problems in multi-dimensional spaces Efficient in-memory consumption Rapid both for binary and multi-class classification Excellent result for nonlinear data processing Could be used for tasks with the number of data samples less than the number of dimensions | A relatively large computational time when a huge amount of data are processed Results significantly depend on noisy data which can lead to overlapping of classification classes |
| ANNs | Possible to apply for data with the incomplete initial knowledge High fault tolerance Could be implemented with parallel processing techniques Fast results after ANN being trained Efficient with the large datasets Could be applied both for regression and classification tasks | Hardware-dependent computational time Hard to find optimal network structure Overfitting may occur |
| Deep learning | Highly reliable recognition and classification results | Relatively more complex for training and implementation compared to other methods |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mamchur, D.; Peksa, J.; Le Clainche, S.; Vinuesa, R. Application and Advances in Radiographic and Novel Technologies Used for Non-Intrusive Object Inspection. Sensors 2022, 22, 2121. https://doi.org/10.3390/s22062121
Mamchur D, Peksa J, Le Clainche S, Vinuesa R. Application and Advances in Radiographic and Novel Technologies Used for Non-Intrusive Object Inspection. Sensors. 2022; 22(6):2121. https://doi.org/10.3390/s22062121
Chicago/Turabian StyleMamchur, Dmytro, Janis Peksa, Soledad Le Clainche, and Ricardo Vinuesa. 2022. "Application and Advances in Radiographic and Novel Technologies Used for Non-Intrusive Object Inspection" Sensors 22, no. 6: 2121. https://doi.org/10.3390/s22062121







