Chaotic Search-and-Rescue-Optimization-Based Multi-Hop Data Transmission Protocol for Underwater Wireless Sensor Networks
Abstract
:1. Introduction
2. Related Works
3. The Proposed Model
3.1. System Model
- The bulges identify their place and the place of the SN in a primary situation.
- The node can develop the and the CM/relay.
- The CH rotates amongst the sensors to conserve energy.
3.2. Process Involved in a WCA
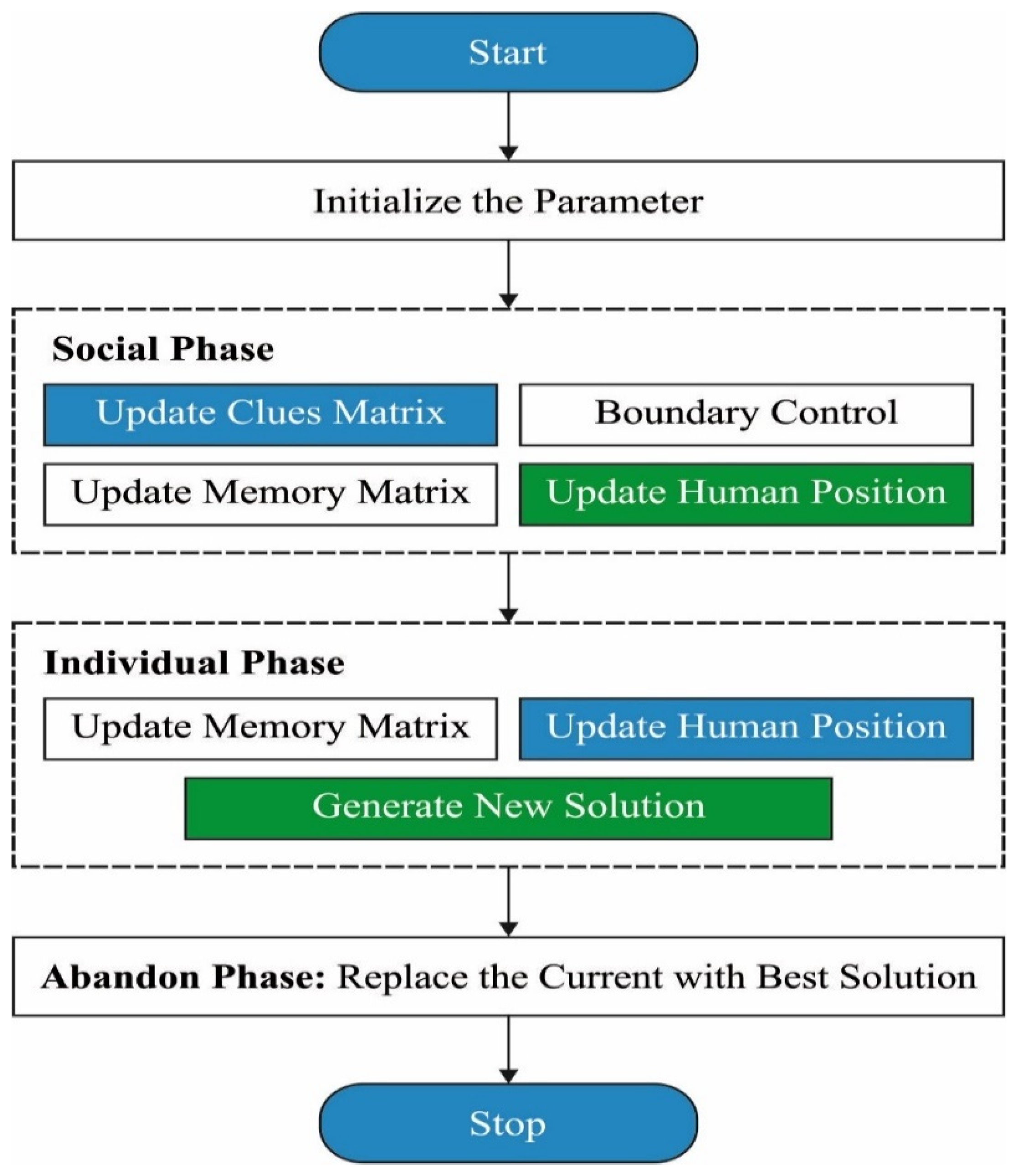
3.3. Design of the CSRO Algorithm
- Remember to save a clue: A member of the exploration group is present and searching the surrounding area.
- Forgotten clue: Members of the group discovered the clue, but no one is in the location to solve it. To put it another way, the person who discovered the hint has abandoned it in search of further potentially relevant information. Members of the group, on the other hand, have access to the information about that clue.
3.4. Application of CSRO Algorithm for Data Transmission
4. Performance Validation
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Awan, K.M.; Shah, P.A.; Iqbal, K.; Gillani, S.; Ahmad, W.; Nam, Y. Underwater wireless sensor networks: A review of recent issues and challenges. Wirel. Commun. Mob. Comput. 2019, 2019, 6470359. [Google Scholar] [CrossRef]
- Khalaf, O.I.; Abdulsahib, G.M. Optimized dynamic storage of data (ODSD) in IoT based on blockchain for wireless sensor networks. Peer-Peer Netw. Appl. 2021, 14, 2858–2873. [Google Scholar] [CrossRef]
- Srilakshmi, U.; Alghamdi, S.; Ankalu, V.V.; Veeraiah, N.; Alotaibi, Y. A secure optimization routing algorithm for mobile ad hoc networks. IEEE Access 2022, 10, 14260–14269. [Google Scholar] [CrossRef]
- Choudhary, M.; Goyal, N. A rendezvous point-based data gathering in underwater wireless sensor networks for monitoring applications. Int. J. Commun. Syst. 2022, 14, e5078. [Google Scholar] [CrossRef]
- Alotaibi, Y.; Subahi, A.F. New goal-oriented requirements extraction framework for e-health services: A case study of diagnostic testing during the COVID-19 outbreak. Bus. Process Manag. J. 2021, 38, 1–19. [Google Scholar] [CrossRef]
- Rajendran, S.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S. MapReduce-based big data classification model using feature subset selection and hyperparameter tuned deep belief network. Sci. Rep. 2021, 11, 24138. [Google Scholar] [CrossRef]
- Xiao, X.; Huang, H.; Wang, W. Underwater wireless sensor networks: An energy-efficient clustering routing protocol based on data fusion and genetic algorithms. Appl. Sci. 2021, 11, 312. [Google Scholar] [CrossRef]
- Palanisamy, S.; Thangaraju, B.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S. Design and Synthesis of Multi-Mode Bandpass Filter for Wireless Applications. Electronics 2021, 10, 2853. [Google Scholar] [CrossRef]
- Rout, R.; Parida, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. Skin Lesion Extraction Using Multiscale Morphological Local Variance Reconstruction Based Watershed Transform and Fast Fuzzy C-Means Clustering. Symmetry 2021, 13, 2085. [Google Scholar] [CrossRef]
- Jouhari, M.; Ibrahimi, K.; Tembine, H.; Ben-Othman, J. Underwater wireless sensor networks: A survey on enabling technologies, localization protocols, and internet of underwater things. IEEE Access 2019, 7, 96879–96899. [Google Scholar] [CrossRef]
- Palanisamy, S.; Thangaraju, B.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Alassery, F. A Novel Approach of Design and Analysis of a Hexagonal Fractal Antenna Array (HFAA) for Next-Generation Wireless Communication. Energies 2021, 14, 6204. [Google Scholar] [CrossRef]
- Bharany, S.; Sharma, S.; Badotra, S.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Alassery, F. Energy-Efficient Clustering Scheme for Flying Ad-Hoc Networks Using an Optimized LEACH Protocol. Energies 2021, 14, 6016. [Google Scholar] [CrossRef]
- Zhang, J.; Cai, M.; Han, G.; Qian, Y.; Shu, L. Cellular clustering-based interference-aware data transmission protocol for underwater acoustic sensor networks. IEEE Trans. Veh. Technol. 2020, 69, 3217–3230. [Google Scholar] [CrossRef]
- Alsufyani, A.; Alotaibi, Y.; Almagrabi, A.O.; Alghamdi, S.A.; Alsufyani, N. Optimized intelligent data management framework for a cyber-physical system for computational applications. Complex Intell. Syst. 2021, 192, 1–13. [Google Scholar] [CrossRef]
- Yu, W.; Chen, Y.; Wan, L.; Zhang, X.; Zhu, P.; Xu, X. An energy optimization clustering scheme for multi-hop underwater acoustic cooperative sensor networks. IEEE Access 2020, 8, 89171–89184. [Google Scholar] [CrossRef]
- Khalaf, O.I.; Ghaida, M.A. Energy Efficient Routing and Reliable Data Transmission Protocol in WSN. Int. J. Adv. Soft Comput. Its Appl. 2020, 12, 45–53. [Google Scholar]
- Subahi, A.F.; Alotaibi, Y.; Khalaf, O.I.; Ajesh, F. Packet Drop Battling Mechanism for Energy Aware Detection in Wireless Networks. CMC-Computers. Mater. Contin. 2020, 66, 2077–2086. [Google Scholar]
- Zhou, Y.; Yang, H.; Hu, Y.; Kung, S. Cross-layer network lifetime maximization in underwater wireless sensor networks. IEEE Syst. J. 2020, 14, 220–231. [Google Scholar] [CrossRef]
- Paulraj, D. An Automated Exploring and Learning Model for Data Prediction Using Balanced CA-SVM. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 4979–4990. [Google Scholar]
- Wang, Z.; Han, G.; Qin, H.; Zhang, S.; Sui, Y. An energy-aware and void-avoidable routing protocol for underwater sensor networks. IEEE Access 2018, 6, 7792–7801. [Google Scholar] [CrossRef]
- Chithambaramani, R.; Prakash, M. An Efficient Applications Cloud Interoperability Framework UsingI-Anfis. Symmetry 2021, 13, 268. [Google Scholar]
- Khan, H.; Hassan, S.A.; Jung, H. On underwater wireless sensor networks routing protocols: A review. IEEE Sens. J. 2020, 20, 10371–10386. [Google Scholar] [CrossRef]
- Yahya, A.; Islam, S.U.; Zahid, M.; Ahmed, G.; Raza, M.; Pervaiz, H.; Yang, F. Cooperative routing for energy efficient underwater wireless sensor networks. IEEE Access 2019, 7, 141888–141899. [Google Scholar] [CrossRef]
- Mohan, P.; Subramani, N.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I.; Ulaganathan, S. Improved Metaheuristics-Based Clustering with Multihop Routing Protocol for Underwater Wireless Sensor Networks. Sensors 2022, 22, 1618. [Google Scholar] [CrossRef] [PubMed]
- Srilakshmi, U.; Veeraiah, N.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I.; Subbayamma, B.V. An Improved Hybrid Secure Multipath Routing Protocol for MANET. IEEE Access 2021, 9, 163043–163053. [Google Scholar] [CrossRef]
- Durrani, M.Y.; Tariq, R.; Aadil, F.; Maqsood, M.; Nam, Y.; Muhammad, K. Adaptive node clustering technique for smart ocean under water sensor network (SOSNET). Sensors 2019, 19, 1145. [Google Scholar] [CrossRef] [Green Version]
- Rajeswari, A.; Duraipandian, N.; Shanker, N.; Samuel, B.E. Improving packet delivery performance in water column variations through LOCAN in underwater acoustic sensor network. J. Sens. 2020, 2020, 7960654. [Google Scholar] [CrossRef]
- Khalaf, O.I.; Abdulsahib, G.M.; Sabbar, B.M. Optimization of Wireless Sensor Network Coverage using the Bee Algorithm. J. Inf. Sci. Eng. 2020, 36, 377–386. [Google Scholar]
- Gola, K.K.; Gupta, B. Underwater acoustic sensor networks: An energy efficient and void avoidance routing based on grey wolf optimization algorithm. Arab. J. Sci. Eng. 2021, 46, 3939–3954. [Google Scholar] [CrossRef]
- Feng, P.; Qin, D.; Ji, P.; Zhao, M.; Guo, R.; Berhane, T.M. Improved energy-balanced algorithm for underwater wireless sensor network based on depth threshold and energy level partition. EURASIP J. Wirel. Commun. Netw. 2019, 2019, 228. [Google Scholar] [CrossRef] [Green Version]
- Suryanarayana, G.; Chandran, K.; Khalaf, O.I.; Alotaibi, Y.; Alsufyani, A.; Alghamdi, S.A. Accurate Magnetic Resonance Image Super-Resolution Using Deep Networks and Gaussian Filtering in the Stationary Wavelet Domain. IEEE Access 2021, 9, 71406–71417. [Google Scholar] [CrossRef]
- Sindu, V.; Prakash, M. Comparative Analysis Among Decision Tree vs. Naive Bayes for Prediction of Weather Prognostication. Smart Intell. Comput. Commun. Technol. 2021, 38, 94–100. [Google Scholar]
- Li, G.; Liu, F.; Sharma, A.; Khalaf, O.I.; Alotaibi, Y.; Alsufyani, A.; Alghamdi, S. Research on the natural language recognition method based on cluster analysis using neural network. Math. Probl. Eng. 2021, 2021, 9982305. [Google Scholar] [CrossRef]
- Neelakandan, S.; Berlin, S.; Brindha Devi, V.; Indu, B.; Arulkumar, N. IoT Based Traffic Prediction and Traffic Signal Control System for Smart City. Soft Comput. 2021, 25, 12241–12248. [Google Scholar] [CrossRef]
- Jha, N.; Prashar, D.; Khalaf, O.I.; Alotaibi, Y.; Alsufyani, A.; Alghamdi, S. Blockchain Based Crop Insurance: A Decentralized Insurance System for Modernization of Indian Farmers. Sustainability 2021, 13, 8921. [Google Scholar] [CrossRef]
- Abdulsahib, G.M.; Khalaf, O.I. Accurate and effective data collection with minimum energy path selection in wireless sensor networks using mobile sinks. J. Inf. Technol. Manag. 2021, 13, 139–153. [Google Scholar]
- Fei, W.; Hexiang, B.; Deyu, L.; Jianjun, W. Energy-efficient clustering algorithm in underwater sensor networks based on fuzzy C means and Moth-flame optimization method. IEEE Access 2020, 8, 97474–97484. [Google Scholar] [CrossRef]
- Alotaibi, Y. A New Database Intrusion Detection Approach Based on Hybrid Meta-Heuristics. CMC-Comput. Mater. Contin. 2021, 66, 1879–1895. [Google Scholar] [CrossRef]
- Kamalraj, R.; Neelakandan, S.; Ranjithkumar, M.; Chandra Sekhar, R.; Rohit Anand, R.; Harinder, S. Interpretable Filter Based Convolutional Neural Network (IF-CNN) For Glucose Prediction and Classification Using PD-SS Algorithm. Measurement 2021, 183, 109804. [Google Scholar] [CrossRef]
- Alotaibi, Y. A New Secured E-Government Efficiency Model for Sustainable Services Provision. J. Inf. Secur. Cybercrimes Res. 2020, 3, 75–96. [Google Scholar] [CrossRef]
- Khan, H.H.; Malik, M.N.; Zafar, R.; Goni, F.A.; Chofreh, A.G.; Klemeš, J.J.; Alotaibi, Y. Challenges for sustainable smart city development: A conceptual framework. Sustain. Dev. 2020, 28, 1507–1518. [Google Scholar] [CrossRef]
- Subramani, N.; Mohan, P.; Alotaibi, Y.; Alghamdi, S.; Khalaf, O.I. An Efficient Metaheuristic-Based Clustering with Routing Protocol for Underwater Wireless Sensor Networks. Sensors 2022, 22, 415. [Google Scholar] [CrossRef] [PubMed]
- Khan, M.F.; Bibi, M.; Aadil, F.; Lee, J.W. Adaptive Node Clustering for Underwater Sensor Networks. Sensors 2021, 21, 4514. [Google Scholar] [CrossRef] [PubMed]
- Houssein, E.H.; Saber, E.; Ali, A.A.; Wazery, Y.M. Centroid mutation-based Search and Rescue optimization algorithm for feature selection and classification. Expert Syst. Appl. 2022, 191, 116235. [Google Scholar] [CrossRef]
- Satpathy, S.; Debbarma, S.; Sengupta Aditya, S.C.; Bhattacaryya Bidyut, K.D. Design a FPGA, fuzzy based, insolent method for prediction of multi-diseases in rural area. J. Intell. Fuzzy Syst. 2019, 37, 7039–7046. [Google Scholar] [CrossRef]
- Li, M.; Xu, G.; Lai, Q.; Chen, J. A chaotic strategy-based quadratic Opposition-Based Learning adaptive variable-speed whale optimization algorithm. Math. Comput. Simul. 2022, 193, 71–99. [Google Scholar] [CrossRef]
- Veeraiah, N.; Khalaf, O.I.; Prasad, C.V.P.R.; Alotaibi, Y.; Alsufyani, A.; Alghamdi, S.A.; Alsufyani, N. Trust aware secure energy efficient hybrid protocol for manet. IEEE Access 2021, 9, 120996–121005. [Google Scholar] [CrossRef]
- Pretty Diana Cyril, C.; Rene Beulah, J.; Harshavardhan, A.; Sivabalaselvamani, D. An automated learning model for sentiment analysis and data classification of Twitter data using balanced CA-SVM. Concurr. Eng. Res. Appl. 2021, 29, 386–395. [Google Scholar] [CrossRef]
- Reshma, G.; Al-Atroshi, C.; Nassa, V.K.; Geetha, B. Deep Learning-Based Skin Lesion Diagnosis Model Using Dermoscopic Images. Intell. Autom. Soft Comput. 2022, 31, 621–634. [Google Scholar] [CrossRef]
- Arun, A.; Bhukya, R.R.; Hardas, B.M.; Anil Kumar, C.T.; Ashok, M. An Automated Word Embedding with Parameter Tuned Model for Web Crawling. Intell. Autom. Soft Comput. 2022, 32, 1617–1632. [Google Scholar]
- Asha, P.; Natrayan, L.; Geetha, B.T.; Beulah, J.R.; Sumathy, R.; Varalakshmi, G. IoT enabled environmental toxicology for air pollution monitoring using AI techniques. Environ. Res. 2022, 205, 112574. [Google Scholar] [CrossRef] [PubMed]
- Paulraj, D. A gradient boosted decision tree-based sentiment classification of twitter data. Int. J. Wavelets. Multiresolut. Inf. Processing 2020, 18, 205027. [Google Scholar] [CrossRef]
- Annamalai, R.; Rayen, S.J.; Arunajsmine, J. Social Media Networks Owing to Disruptions for Effective Learning. Procedia Comput. Sci. 2020, 172, 145–151. [Google Scholar] [CrossRef]
- Anand, J.G. Trust based optimal routing. In Proceedings of the MANET’s 2011 International Conference on Emerging Trends in Electrical and Computer Technology, Nagercoil, India, 23–24 March 2011; pp. 1150–1156. [Google Scholar] [CrossRef]
- Divyabharathi, S. Large scale optimization to minimize network traffic using MapReduce in big data applications. In Proceedings of the 2016 International Conference on Computation of Power, Energy Information and Commuincation, Melmaruvathur, India, 20–21 April 2016; pp. 193–199. [Google Scholar] [CrossRef]
- Beulah, J.R.; Prathiba, L.; Murthy, G.L.N.; Fantin Irudaya Raj, E.; Arulkumar, N. Blockchain with deep learning-enabled secure healthcare data transmission and diagnostic model. Int. J. Modeling Simul. Sci. Computing. 2021, 15, 1–14. [Google Scholar] [CrossRef]
- Venu, D.; Mayuri, A.V.R.; Murthy, G.L.N.; Arulkumar, N.; Shelke, N. An efficient low complexity compression based optimal homomorphic encryption for secure fiber optic communication. Optik 2022, 252, 168545. [Google Scholar] [CrossRef]
- Jain, D.K.; Tyagi, S.K.K.S.; Prakash, M.; Natrayan, L. Metaheuristic Optimization-based Resource Allocation Technique for Cybertwin-driven 6G on IoE Environment. IEEE Trans. Ind. Inform. 2021. [Google Scholar] [CrossRef]
- Alotaibi, Y.; Malik, M.N.; Khan, H.H.; Batool, A.; ul Islam, S.; Alsufyani, A.; Alghamdi, S. Suggestion Mining from Opinionated Text of Big Social Media Data. CMC-Comput. Mater. Contin. 2021, 68, 3323–3338. [Google Scholar] [CrossRef]
- Alotaibi, Y. Automated Business Process Modelling for Analyzing Sustainable System Requirements Engineering. In Proceedings of the 2020 6th International Conference on Information Management, London, UK, 27–29 March 2020; pp. 157–161. [Google Scholar]
- Kavitha, T.; Mathai, P.P.; Karthikeyan, C.; Ashok, M.; Kohar, R.; Avanija, J.; Neelakandan, S. Deep Learning Based Capsule Neural Network Model for Breast Cancer Diagnosis Using Mammogram Images. Interdiscip. Sci. Comput. Life Sci. 2021, 14, 113–129. [Google Scholar] [CrossRef]
- Sunitha, G.; Geetha, K.; Neelakandan, S.; Pundir, A.K.; Hemalatha, S.; Kumar, V. Intelligent deep learning based ethnicity recognition and classification using facial images. Image Vis. Comput. 2022, 121, 104404. [Google Scholar] [CrossRef]
- Su, Y.; Wang, M.L. Optimal cooperative relaying and power control for IoUT networks with reinforcement learning. IEEE Internet Things J. 2021, 8, 791–801. [Google Scholar] [CrossRef]
- Jin, Z. RCAR: A reinforcement-learning-based routing protocol for congestion-avoided underwater acoustic sensor networks. IEEE Sens. J. 2019, 19, 10881–10891. [Google Scholar] [CrossRef]
- Harinder Singh, D.; Ramya, R. Saravanakumar, Nayani Sateesh, Rohit Anand, Swarnjit Singh Artificial intelligence based quality of transmission predictive model for cognitive optical networks. Optik 2022, 257, 168789. [Google Scholar] [CrossRef]
- Chen, Y.; Tang, Y. PB-ACR: Node Payload Balanced Ant Colony Optimal Cooperative Routing for Multi-Hop Under water Acoustic Sensor Networks. IEEE Access 2021, 9, 57165–57178. [Google Scholar] [CrossRef]
- Chen, Y.; Zhu, J.; Wan, L.; Huang, S.; Zhang, X.; Xu, X. ACOA-AFSA Fusion Dynamic Coded Cooperation Routing for Different Scale Multi- Hop Underwater Acoustic Sensor Networks. IEEE Access 2020, 8, 186773–186788. [Google Scholar] [CrossRef]
- Bhargava, S.; Mohan, K.; Robert, N.R.; Upadhye, S. Optimal Stacked Sparse Autoencoder Based Traffic Flow Prediction in Intelligent Transportation Systems. Innov. Vis. Appl. Stud. Syst. Decis. Control. 2022, 412, 111–127. [Google Scholar] [CrossRef]
- Jayapradha, J.; Prakash, M.; Alotaibi, Y.; Khalaf, O.I.; Alghamdi, S. Heap Bucketization Anonymity-An Efficient Privacy-Preserving Data Publishing Model for Multiple Sensitive Attributes. IEEE Access 2022, 10, 28773–28791. [Google Scholar] [CrossRef]
- Rawat, S.S.; Alghamdi, S.; Kumar, G.; Alotaibi, Y.; Khalaf, O.I.; Verma, L.P. Infrared Small Target Detection Based on Partial Sum Minimization and Total Variation. Mathematics 2022, 10, 671. [Google Scholar] [CrossRef]
- Hemavathi; Akhila, S.R.; Alotaibi, Y.; Khalaf, O.I.; Alghamdi, S. Authentication and Resource Allocation Strategies during Handoff for 5G IoVs Using Deep Learning. Energies 2022, 15, 2006. [Google Scholar] [CrossRef]
- Alotaibi, Y. A New Meta-Heuristics Data Clustering Algorithm Based on Tabu Search and Adaptive Search Memory. Symmetry 2022, 14, 623. [Google Scholar] [CrossRef]





| Reference No. | Published Year | Approach | Advantages | Disadvantages |
|---|---|---|---|---|
| [26] | 2019 | Adaptive node clustering | Throughput and reliability are high in clustering process | Network life time |
| [27] | 2020 | LOCAN methodology | Energy consumption | Packet loss |
| [28] | 2020 | Bee algorithm | Reliable transmission | Not suitable for deep UWSNs |
| [29] | 2021 | Grey wolf optimization algorithm | Reducing packet loss and traffic systems | Sensor failure |
| [30] | 2019 | Threshold and energy level partition | Reducing delay and high throughput | Maximizing energy Resources |
| [36] | 2021 | Path selection strategy | High throughput | Time delay |
| [37] | 2020 | Fuzzy C means and moth–flame optimization method | Reducing energy consumption | Time delay Packet loss |
| Proposed Approach | 2022 | Chaotic search and rescue optimization | Reliable transmission, Reducing time delay and high throughput | Packet loss in high level nodes |
| No. of Alive Nodes | ||||||
|---|---|---|---|---|---|---|
| No. of Rounds | CSRO-MHDT | EECRP | FCMMFO | FBCPSO | EGRC | LEACH-ERE |
| 0 | 300 | 300 | 300 | 300 | 300 | 300 |
| 40 | 300 | 300 | 300 | 300 | 300 | 300 |
| 80 | 300 | 300 | 300 | 300 | 300 | 300 |
| 120 | 300 | 300 | 300 | 300 | 300 | 300 |
| 160 | 300 | 300 | 300 | 300 | 300 | 300 |
| 200 | 300 | 300 | 300 | 300 | 300 | 300 |
| 240 | 300 | 300 | 300 | 300 | 300 | 300 |
| 280 | 300 | 300 | 300 | 300 | 300 | 299 |
| 320 | 300 | 300 | 300 | 300 | 299 | 297 |
| 360 | 300 | 300 | 300 | 297 | 298 | 295 |
| 400 | 300 | 300 | 298 | 298 | 297 | 290 |
| 440 | 300 | 296 | 290 | 299 | 298 | 287 |
| 480 | 296 | 294 | 287 | 290 | 290 | 285 |
| 520 | 294 | 288 | 279 | 284 | 281 | 271 |
| 560 | 287 | 276 | 268 | 262 | 264 | 254 |
| 600 | 279 | 264 | 253 | 240 | 243 | 238 |
| 640 | 269 | 234 | 230 | 202 | 228 | 218 |
| 680 | 253 | 217 | 211 | 188 | 187 | 179 |
| 720 | 226 | 183 | 172 | 169 | 160 | 152 |
| 760 | 214 | 142 | 132 | 130 | 140 | 50 |
| 800 | 183 | 113 | 121 | 89 | 95 | 3 |
| 840 | 139 | 72 | 94 | 56 | 20 | 0 |
| 880 | 116 | 28 | 37 | 12 | 0 | 0 |
| 920 | 68 | 20 | 0 | 0 | 0 | 0 |
| 960 | 28 | 0 | 0 | 0 | 0 | 0 |
| 1000 | 0 | 0 | 0 | 0 | 0 | 0 |
| No. of Rounds | ||||||
|---|---|---|---|---|---|---|
| CSRO-MHDT | EECRP | FCMMFO | FBCPSO | EGRC | LEACH-ERE | |
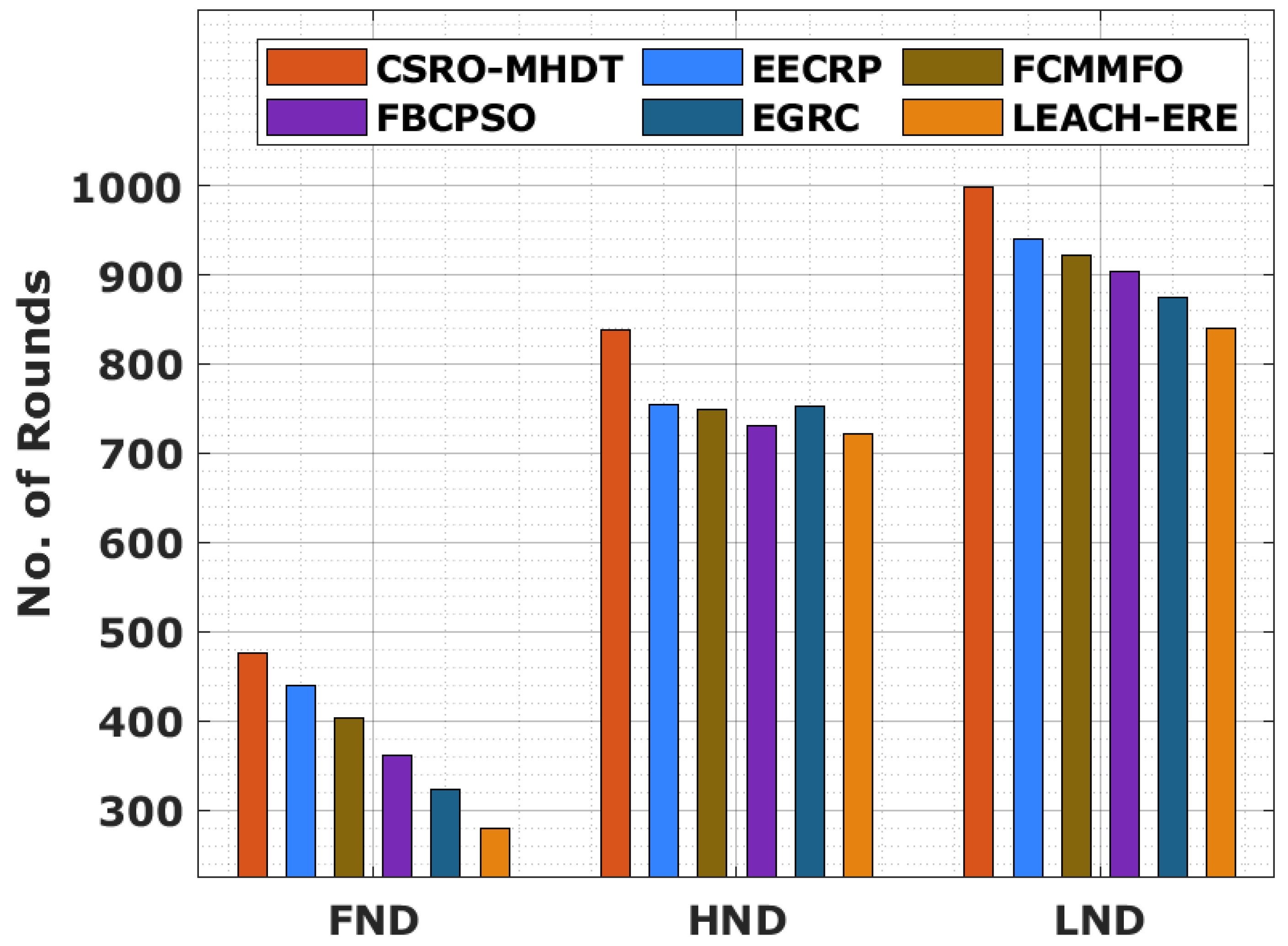
| FND | 476 | 440 | 403 | 361 | 323 | 280 |
| HND | 838 | 754 | 749 | 730 | 753 | 722 |
| LND | 998 | 940 | 921 | 903 | 874 | 840 |
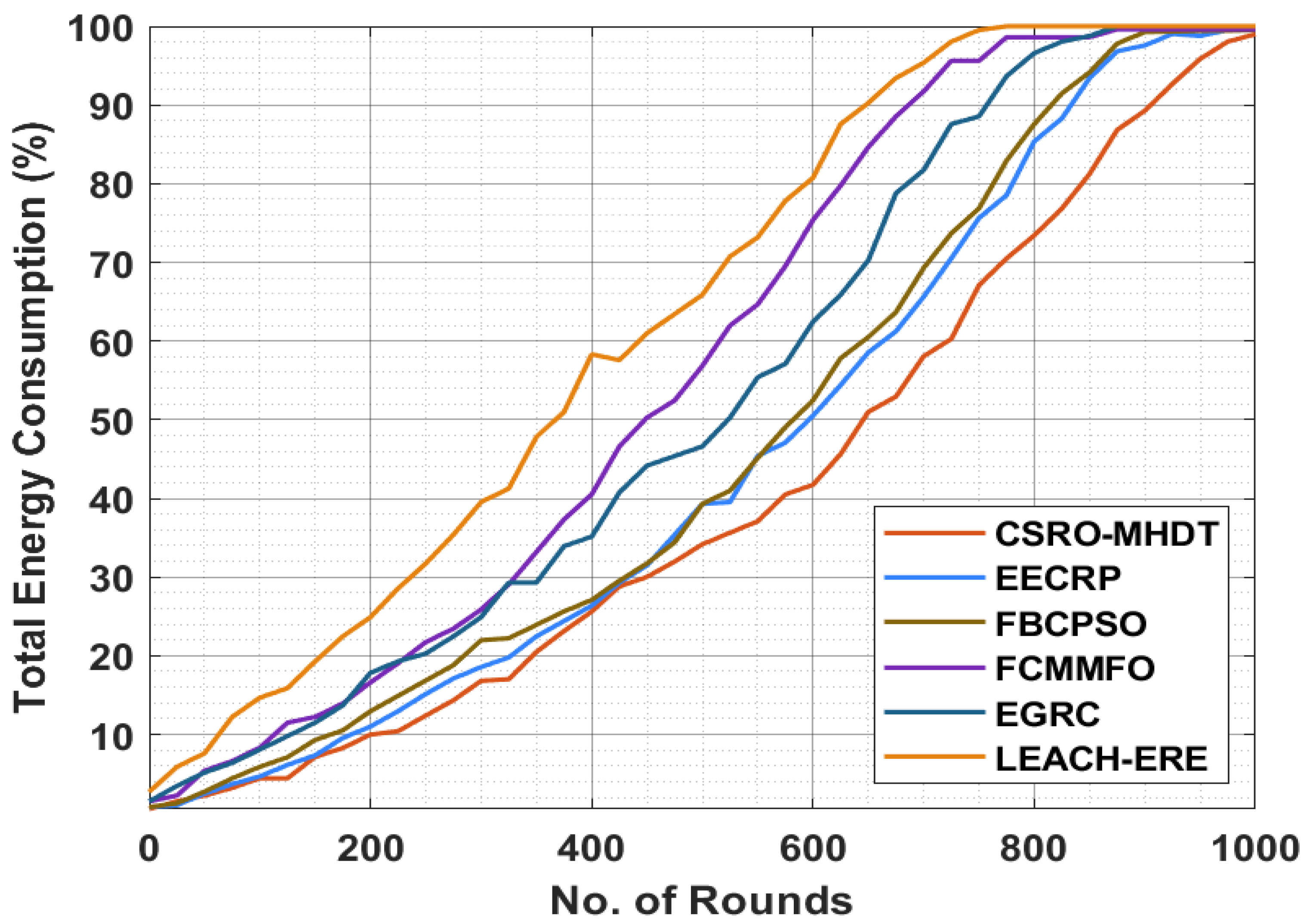
| Total Energy Consumption (%) | ||||||
|---|---|---|---|---|---|---|
| No. of Rounds | CSRO-MHDT | EECRP | FBCPSO | FCMMFO | EGRC | LEACH-ERE |
| 0 | 0.51 | 0.76 | 0.76 | 1.49 | 1.49 | 2.71 |
| 25 | 1.49 | 1.00 | 1.25 | 2.22 | 3.44 | 5.88 |
| 50 | 2.22 | 2.46 | 2.71 | 5.39 | 5.15 | 7.59 |
| 75 | 3.20 | 3.68 | 4.42 | 6.61 | 6.37 | 12.22 |
| 100 | 4.43 | 4.66 | 5.88 | 8.32 | 8.07 | 14.66 |
| 125 | 4.42 | 6.12 | 7.10 | 11.49 | 9.78 | 15.88 |
| 150 | 7.14 | 7.34 | 9.29 | 12.22 | 11.49 | 19.29 |
| 175 | 8.27 | 9.54 | 10.51 | 13.93 | 13.68 | 22.46 |
| 200 | 9.97 | 11.00 | 12.95 | 16.61 | 17.83 | 24.90 |
| 225 | 10.41 | 12.95 | 14.90 | 19.05 | 19.29 | 28.56 |
| 250 | 12.39 | 15.14 | 16.85 | 21.73 | 20.27 | 31.73 |
| 275 | 14.34 | 17.10 | 18.80 | 23.44 | 22.46 | 35.38 |
| 300 | 16.80 | 18.56 | 21.97 | 25.87 | 24.90 | 39.53 |
| 325 | 17.02 | 19.78 | 22.22 | 29.04 | 29.29 | 41.24 |
| 350 | 20.48 | 22.46 | 23.92 | 33.19 | 29.29 | 47.82 |
| 375 | 23.14 | 24.41 | 25.63 | 37.33 | 33.92 | 50.99 |
| 400 | 25.61 | 26.36 | 27.09 | 40.50 | 35.14 | 58.31 |
| 425 | 28.80 | 29.29 | 29.53 | 46.60 | 40.75 | 57.57 |
| 450 | 30.02 | 31.48 | 31.73 | 50.26 | 44.16 | 60.99 |
| 475 | 31.97 | 35.38 | 34.41 | 52.45 | 45.38 | 63.43 |
| 500 | 34.16 | 39.29 | 39.29 | 56.84 | 46.60 | 65.87 |
| 525 | 35.63 | 39.53 | 40.99 | 61.96 | 50.26 | 70.74 |
| 550 | 37.09 | 45.38 | 45.14 | 64.65 | 55.38 | 73.18 |
| 575 | 40.50 | 47.09 | 49.04 | 69.52 | 57.09 | 77.81 |
| 600 | 41.72 | 50.50 | 52.45 | 75.38 | 62.45 | 80.74 |
| 625 | 45.63 | 54.40 | 57.82 | 79.76 | 65.87 | 87.57 |
| 650 | 50.99 | 58.55 | 60.50 | 84.64 | 70.25 | 90.25 |
| 675 | 52.94 | 61.23 | 63.67 | 88.54 | 78.79 | 93.42 |
| 700 | 58.06 | 65.62 | 69.28 | 91.71 | 81.72 | 95.37 |
| 725 | 60.26 | 70.50 | 73.67 | 95.61 | 87.57 | 98.05 |
| 750 | 67.08 | 75.62 | 76.84 | 95.61 | 88.54 | 99.52 |
| 775 | 70.50 | 78.55 | 82.93 | 98.61 | 93.66 | 100.00 |
| 800 | 73.42 | 85.37 | 87.57 | 98.61 | 96.59 | 100.00 |
| 825 | 76.84 | 88.30 | 91.47 | 98.61 | 98.05 | 100.00 |
| 850 | 81.23 | 93.42 | 94.15 | 98.61 | 98.78 | 100.00 |
| 875 | 86.84 | 96.83 | 97.81 | 99.61 | 100.00 | 100.00 |
| 900 | 89.27 | 97.57 | 99.27 | 99.61 | 100.00 | 100.00 |
| 925 | 92.69 | 99.03 | 99.34 | 99.61 | 100.00 | 100.00 |
| 950 | 95.86 | 98.78 | 99.43 | 99.61 | 100.00 | 100.00 |
| 975 | 98.05 | 99.52 | 99.45 | 99.61 | 100.00 | 100.00 |
| 1000 | 99.00 | 99.55 | 99.52 | 99.61 | 100.00 | 100.00 |
| Packet Loss Ratio (%) | ||||||
|---|---|---|---|---|---|---|
| No. of Rounds | CSRO-MHDT | EECRP | FBCPSO | FCMMFO | EGRC | LEACH-ERE |
| 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 50 | 1 | 1 | 1 | 1 | 1 | 1 |
| 100 | 1 | 1 | 1 | 1 | 1 | 2 |
| 150 | 1 | 1 | 1 | 2 | 3 | 3 |
| 200 | 1 | 1 | 2 | 3 | 4 | 3 |
| 250 | 1 | 2 | 3 | 3 | 4 | 4 |
| 300 | 1 | 2 | 3 | 4 | 5 | 5 |
| 350 | 2 | 3 | 4 | 5 | 6 | 6 |
| 400 | 2 | 3 | 5 | 6 | 7 | 7 |
| 450 | 2 | 4 | 6 | 7 | 8 | 9 |
| 500 | 2 | 5 | 7 | 8 | 9 | 10 |
| 550 | 3 | 6 | 8 | 9 | 10 | 11 |
| 600 | 4 | 7 | 9 | 10 | 11 | 12 |
| 650 | 5 | 8 | 10 | 11 | 12 | 14 |
| 700 | 6 | 8 | 11 | 11 | 14 | 15 |
| 750 | 7 | 9 | 12 | 14 | 15 | 16 |
| 800 | 7 | 10 | 13 | 15 | 18 | 17 |
| 850 | 8 | 12 | 15 | 17 | 19 | 19 |
| 900 | 9 | 13 | 16 | 17 | 20 | 21 |
| 950 | 10 | 15 | 18 | 21 | 22 | 23 |
| 1000 | 12 | 17 | 19 | 22 | 23 | 25 |
| No. of Packets Received (%) | ||||||
|---|---|---|---|---|---|---|
| No. of Rounds | CSRO-MHDT | EECRP | FBCPSO | FCMMFO | EGRC | LEACH-ERE |
| 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 50 | 3792 | 3400 | 2549 | 2876 | 2026 | 1554 |
| 100 | 7391 | 5755 | 4970 | 6736 | 3334 | 3054 |
| 150 | 10,073 | 8503 | 7587 | 8568 | 4970 | 4751 |
| 200 | 11,251 | 10,335 | 9550 | 9419 | 6736 | 6521 |
| 250 | 13,279 | 11,970 | 10,858 | 10,138 | 7718 | 7310 |
| 300 | 14,522 | 13,213 | 12,363 | 11,185 | 8830 | 8336 |
| 350 | 15,503 | 14,457 | 14,064 | 12,167 | 10,008 | 9679 |
| 400 | 16,746 | 15,176 | 14,718 | 13,410 | 11,054 | 10,595 |
| 450 | 17,074 | 16,877 | 15,503 | 13,933 | 11,709 | 11,442 |
| 500 | 17,924 | 17,401 | 16,027 | 14,784 | 12,167 | 11,837 |
| 550 | 18,709 | 18,120 | 17,204 | 15,045 | 13,148 | 12,789 |
| 600 | 19,887 | 18,775 | 17,532 | 15,700 | 13,737 | 13,521 |
| 650 | 20,410 | 20,018 | 18,055 | 16,485 | 14,391 | 14,034 |
| 700 | 21,523 | 20,410 | 18,317 | 17,204 | 14,653 | 14,276 |
| 750 | 21,850 | 20,868 | 19,102 | 17,597 | 15,111 | 14,642 |
| 800 | 22,046 | 20,999 | 19,756 | 18,186 | 14,980 | 14,623 |
| 850 | 22,569 | 21,195 | 20,214 | 18,513 | 14,849 | 14,445 |
| 900 | 22,766 | 21,457 | 20,214 | 18,578 | 14,849 | 14,570 |
| 950 | 23,027 | 21,457 | 20,083 | 18,775 | 14,784 | 14,358 |
| 1000 | 23,093 | 21,457 | 19,887 | 18,775 | 14,849 | 14,427 |
| Packet Delivery Ratio (%) | ||||||
|---|---|---|---|---|---|---|
| No. of Rounds | CSRO-MHDT | EECRP | FBCPSO | FCMMFO | EGRC | LEACH-ERE |
| 0 | 100 | 100 | 100 | 100 | 100 | 100 |
| 50 | 99 | 99 | 99 | 99 | 99 | 99 |
| 100 | 99 | 99 | 99 | 99 | 99 | 98 |
| 150 | 99 | 99 | 99 | 98 | 97 | 97 |
| 200 | 99 | 99 | 98 | 97 | 96 | 97 |
| 250 | 99 | 98 | 97 | 97 | 96 | 96 |
| 300 | 99 | 98 | 97 | 96 | 95 | 95 |
| 350 | 98 | 97 | 96 | 95 | 94 | 94 |
| 400 | 98 | 97 | 95 | 94 | 93 | 93 |
| 450 | 98 | 96 | 94 | 93 | 92 | 91 |
| 500 | 98 | 95 | 93 | 92 | 91 | 90 |
| 550 | 97 | 94 | 92 | 91 | 90 | 89 |
| 600 | 96 | 93 | 91 | 90 | 89 | 88 |
| 650 | 95 | 92 | 90 | 89 | 88 | 86 |
| 700 | 94 | 92 | 89 | 89 | 86 | 85 |
| 750 | 93 | 91 | 88 | 86 | 85 | 84 |
| 800 | 93 | 90 | 87 | 85 | 82 | 83 |
| 850 | 92 | 88 | 85 | 83 | 81 | 81 |
| 900 | 91 | 87 | 84 | 83 | 80 | 79 |
| 950 | 90 | 85 | 82 | 79 | 78 | 77 |
| 1000 | 88 | 83 | 81 | 78 | 77 | 75 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Anuradha, D.; Subramani, N.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Rajagopal, M. Chaotic Search-and-Rescue-Optimization-Based Multi-Hop Data Transmission Protocol for Underwater Wireless Sensor Networks. Sensors 2022, 22, 2867. https://doi.org/10.3390/s22082867
Anuradha D, Subramani N, Khalaf OI, Alotaibi Y, Alghamdi S, Rajagopal M. Chaotic Search-and-Rescue-Optimization-Based Multi-Hop Data Transmission Protocol for Underwater Wireless Sensor Networks. Sensors. 2022; 22(8):2867. https://doi.org/10.3390/s22082867
Chicago/Turabian StyleAnuradha, Durairaj, Neelakandan Subramani, Osamah Ibrahim Khalaf, Youseef Alotaibi, Saleh Alghamdi, and Manjula Rajagopal. 2022. "Chaotic Search-and-Rescue-Optimization-Based Multi-Hop Data Transmission Protocol for Underwater Wireless Sensor Networks" Sensors 22, no. 8: 2867. https://doi.org/10.3390/s22082867
APA StyleAnuradha, D., Subramani, N., Khalaf, O. I., Alotaibi, Y., Alghamdi, S., & Rajagopal, M. (2022). Chaotic Search-and-Rescue-Optimization-Based Multi-Hop Data Transmission Protocol for Underwater Wireless Sensor Networks. Sensors, 22(8), 2867. https://doi.org/10.3390/s22082867








