A Review of Fundamental Optimization Approaches and the Role of AI Enabling Technologies in Physical Layer Security
Abstract
:1. Introduction
2. Fundamental Concepts
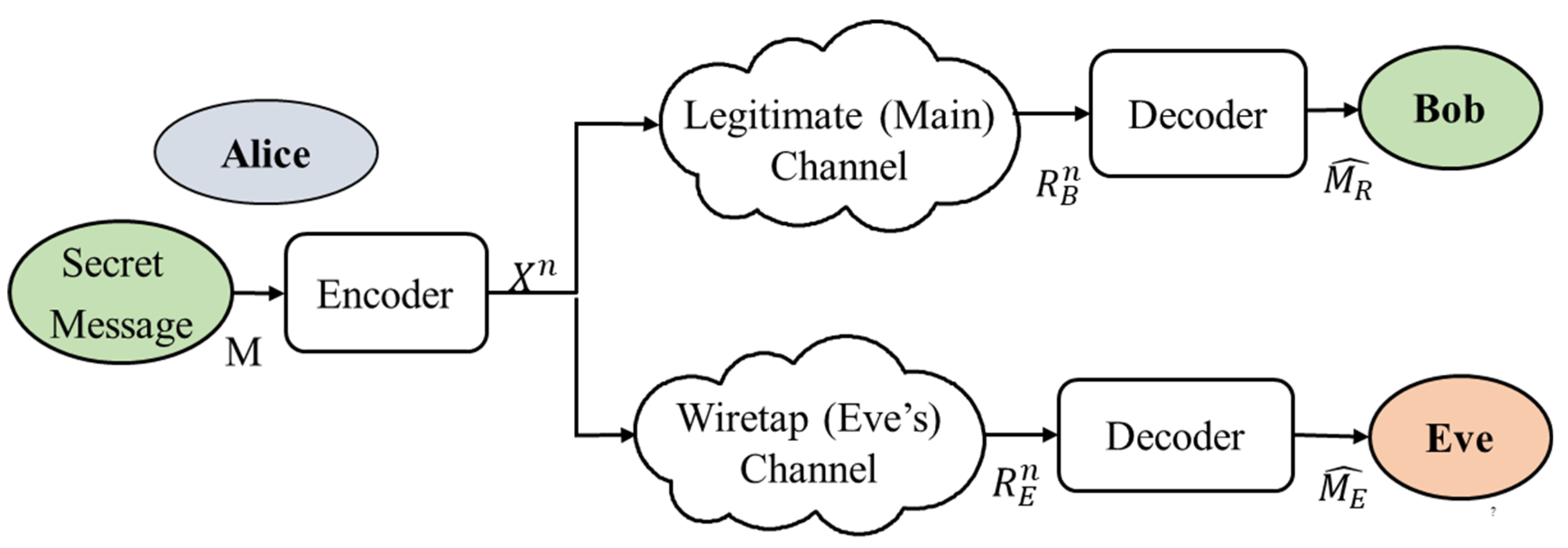
2.1. Generic System Model
2.2. Wireless Adversary Models
2.3. Wiretap Channel Models
2.3.1. MIMO Wiretap Channels
2.3.2. Broadcast Wiretap Channels
2.3.3. Multiple-Access Wiretap Channels
2.3.4. Interference Wiretap Channels
2.3.5. Relay Wiretap Channels
3. Performance Metrics and Application Scenarios in PLS
3.1. Secrecy Capacity Metrics
3.2. Secrecy Outage Probability (SOP)
3.3. Quality of Service (QoS)-Related Metrics
4. Research Directions for System Designs and Optimization Concepts
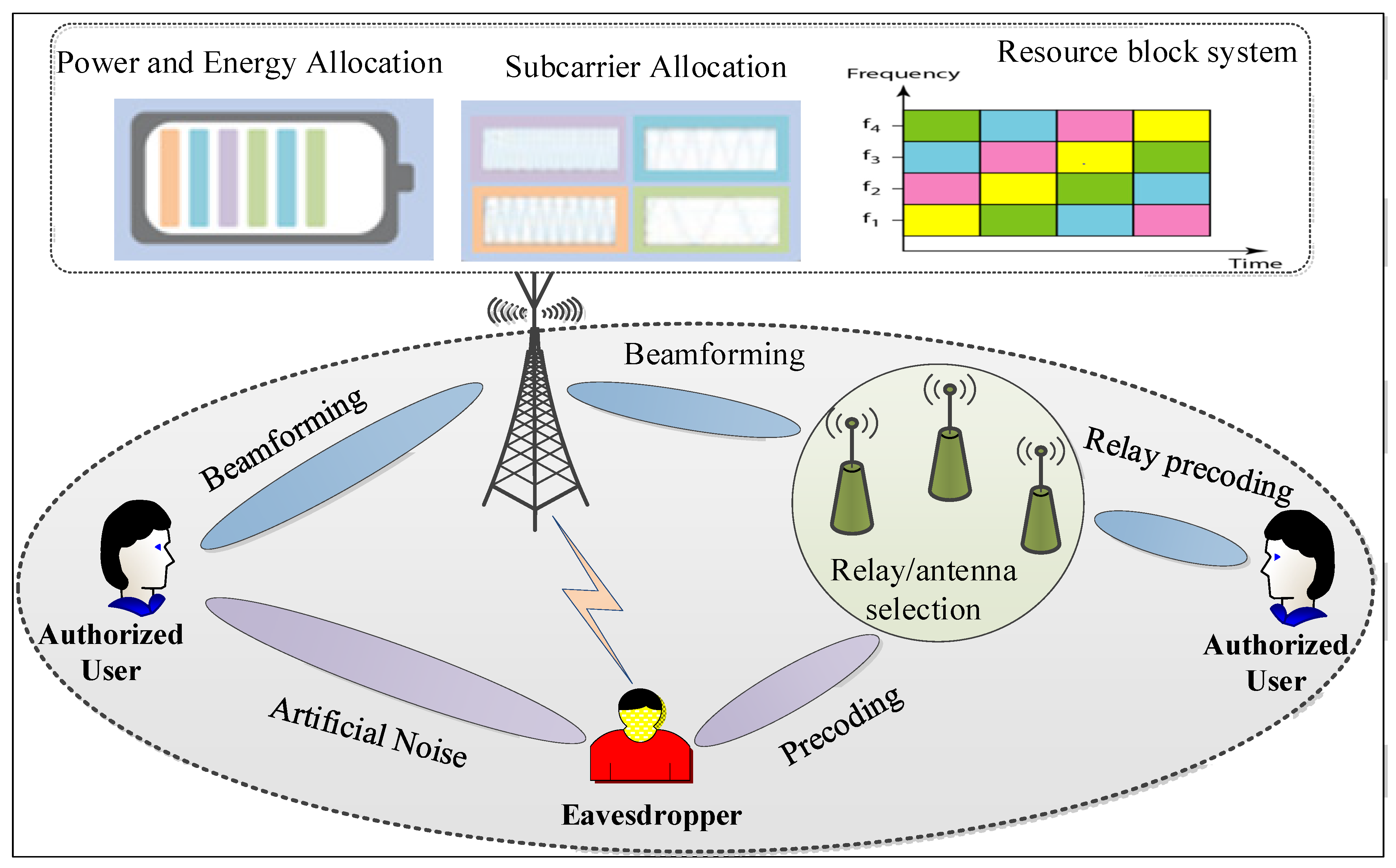
4.1. Main Technical Challenges in System Design
4.2. Optimization in PHY Security: Current Status and Main Issues
4.2.1. Convex Optimization Techniques
4.2.2. Secure Beamforming Techniques
4.2.3. Artificial Noise (AN) Techniques
4.2.4. Zero-Forcing (ZF) Precoding Techniques
5. Paradigms of AI for Physical Layer Optimization and System Design
5.1. Overview of AI and ML Enabling Technologies
5.2. AI for End-to-End Multi-Antenna Techniques
5.3. Applications of AI in Secure Resource Allocation
5.4. AI for Signal Processing Design
6. Discussions on Future Research Directions and Challenges
6.1. The Joint Optimization of Reliability, Security and Resource Allocation
6.2. The Joint Design of Classic Cryptographic and PHY Securities
6.3. The Impacts of ML on Channel Estimation
6.4. The Influences of AI and ML on B5G Security and Privacy
6.5. The Impacts of Adversarial Attack Models for Beamforming Systems
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Wang, C.X.; Haider, F.; Gao, X.; You, X.H.; Yang, Y.; Yuan, D.; Aggoune, H.M.; Haas, H.; Fletcher, S.; Hepsaydir, E. Cellular architecture and key technologies for 5G wireless communication networks. IEEE Commun. Mag. 2014, 52, 122–130. [Google Scholar] [CrossRef] [Green Version]
- Rawat, S.; Chaturvedi, P. A QoS Aware RA Algorithm for OFDM Network. J. Eng. Educ. Transform. 2015, 2349–2473. [Google Scholar] [CrossRef]
- Chou, S.F.; Pang, A.C.; Yu, Y.J. Energy-aware 3D unmanned aerial vehicle deployment for network throughput optimization. IEEE Trans. Wirel. Commun. 2019, 19, 563–578. [Google Scholar] [CrossRef]
- Hindumathi, V.; Reddy, K.R.L. A Proficient Fair Resource Allocation in the Channel of Multiuser Orthogonal Frequency Division Multiplexing using a Novel Hybrid Bat-Krill Herd Optimization. Wirel. Pers. Commun. 2021, 120, 1449–1473. [Google Scholar] [CrossRef]
- Zhou, L.; Wu, D.; Wei, X.; Dong, Z. Seeing Isn’t Believing: QoE Evaluation for Privacy-Aware Users. IEEE JSAC 2019, 37, 1656–1665. [Google Scholar] [CrossRef]
- Zorgui, M. Wireless Physical Layer Security: On the Performance Limits of Secret-Key Agreement. Masters’s Thesis, King Abdullah University of Science and Technology, Thuwal, Saudi Arabia, 2015. [Google Scholar]
- Campagna, M.; Chen, L.; Dagdelen, O.; Ding, J.; Fernick, J.; Gisin, N.; Hayford, D.; Jennewein, T.; Lütkenhaus, N.; Mosca, M.; et al. Quantum Safe Cryptography and Security: An Introduction, Benefits, Enablers and Challenges; European Telecommunications Standards Institute: Sophia Antipolis, France, 2015; Volume 8, pp. 1–64. [Google Scholar]
- Shiu, Y.S.; Chang, S.Y.; Wu, H.C.; Huang, S.C.H.; Chen, H.H. Physical layer security in wireless networks: A tutorial. IEEE Wireless Commun. 2011, 18, 66–74. [Google Scholar] [CrossRef]
- Mukherjee, A. Physical-layer security in the Internet of Things: Sensing and communication confidentiality under resource constraints. Proc. IEEE 2015, 103, 1747–1761. [Google Scholar] [CrossRef]
- Liu, Y.; Chen, H.H.; Wang, L. Secrecy Capacity Analysis of Artificial Noisy MIMO Channels—An Approach based on Ordered Eigenvalues of Wishart Matrices. IEEE Trans. Inf. Forensics Secur. 2016, 99, 1. [Google Scholar] [CrossRef]
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; Di Renzo, M. Safeguarding 5G wireless communication networks using physical layer security. IEEE Commun. Mag. 2015, 53, 20–27. [Google Scholar] [CrossRef]
- Wang, C.; Wang, H.M. Physical layer security in millimeter wave cellular networks. IEEE Trans. Wirel. Commun. 2016, 15, 5569–5585. [Google Scholar] [CrossRef] [Green Version]
- Zou, Y.; Zhu, J.; Wang, X.; Hanzo, L. A survey on wireless security: Technical challenges, recent advances, and future trends. Proc. IEEE 2016, 104, 1727–1765. [Google Scholar] [CrossRef] [Green Version]
- Barros, J.; Rodrigues, M.R. Secrecy capacity of wireless channels. In Proceedings of the 2006 IEEE International Symposium on Information Theory, Seattle, WA, USA, 9–16 July 2006; pp. 356–360. [Google Scholar]
- Jeon, H.; Kim, N.; Choi, J.; Lee, H.; Ha, J. Bounds on secrecy capacity over correlated ergodic fading channels at high SNR. IEEE Trans. Inf. Theory 2011, 57, 1975–1983. [Google Scholar] [CrossRef]
- Saad, W.; Zhou, X.; Han, Z.; Poor, H.V. On the physical layer security of backscatter wireless systems. IEEE Trans. Wirel. Commun. 2014, 13, 3442–3451. [Google Scholar] [CrossRef]
- Basciftci, Y.O.; Gungor, O.; Koksal, C.E.; Ozguner, F. On the secrecy capacity of block fading channels with a hybrid adversary. IEEE Trans. Inf. Theory 2015, 61, 1325–1343. [Google Scholar] [CrossRef] [Green Version]
- Zhang, N.; Cheng, N.; Lu, N.; Zhang, X.; Mark, J.W.; Shen, X. Partner selection and incentive mechanism for physical layer security. IEEE Trans. Wirel. Commun. 2015, 14, 4265–4276. [Google Scholar] [CrossRef]
- Bashar, S.; Ding, Z. Optimum power allocation against information leakage in wireless network. In Proceedings of the GLOBECOM 2009—2009 IEEE Global Telecommunications Conference, Honolulu, HI, USA, 30 November–4 December 2009; pp. 1–6. [Google Scholar]
- Wang, X.; Tao, M.; Mo, J.; Xu, Y. Power and subcarrier allocation for physical-layer security in OFDMA-based broadband wireless networks. IEEE Trans. Inf. Forensics Secur. 2011, 6, 693–702. [Google Scholar] [CrossRef] [Green Version]
- Du, Y.N.; Han, S.; Xu, S.; Li, C. Improving secrecy under high correlation via discriminatory channel estimation. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Hong, Y.W.P.; Lan, P.C.; Kuo, C.C.J. Signal Processing Approaches to Secure Physical Layer Communications in Multi-Antenna Wireless Systems; Springer: New York, NY, USA, 2014. [Google Scholar]
- Liu, R.; Trappe, W. Securing Wireless Communications at the Physical Layer; Springer: New York, NY, USA, 2010. [Google Scholar]
- Baldi, M.; Tomasin, S. (Eds.) Physical and Data-Link Security Techniques for Future Communication Systems; Springer International: Cham, Switzerland, 2016. [Google Scholar]
- Liu, Y.; Chen, H.H.; Wang, L. Physical layer security for next generation wireless networks: Theories, technologies, and challenges. IEEE Commun. Surv. Tutor. 2017, 19, 347–376. [Google Scholar] [CrossRef]
- Sharma, R.K.; Rawat, D.B. Advances on security threats and countermeasures for cognitive radio networks: A survey. IEEE Commun. Surv. Tutor. 2014, 17, 1023–1043. [Google Scholar] [CrossRef]
- Sanenga, A.; Mapunda, G.A.; Jacob, T.M.L.; Marata, L.; Basutli, B.; Chuma, J.M. An overview of key technologies in physical layer security. Entropy 2020, 22, 1261. [Google Scholar] [CrossRef]
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J.; Swindlehurst, A.L. Principles of physical layer security in multiuser wireless networks: A survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef] [Green Version]
- Chen, X.; Ng, D.W.; Gerstacker, W.H.; Chen, H.H. A Survey on Multiple-Antenna Techniques for Physical Layer Security. IEEE Commun. Surv. Tutor. 2017, 19, 1027–1053. [Google Scholar] [CrossRef]
- Wang, D.; Bai, B.; Zhao, W.; Han, Z. A Survey of Optimization Approaches for Wireless Physical Layer Security. IEEE Commun. Surv. Tutor. 2019, 21, 1878–1911. [Google Scholar] [CrossRef] [Green Version]
- Hamamreh, J.M.; Furqan, H.M.; Arslan, H. Classifications and applications of physical layer security techniques for confidentiality: A comprehensive survey. IEEE Commun. Surv. Tutor. 2018, 21, 1773–1828. [Google Scholar] [CrossRef]
- Trappe, W. The challenges facing physical layer security. IEEE Commun. Mag. 2015, 53, 16–20. [Google Scholar] [CrossRef]
- Mao, Q.; Hu, F.; Hao, Q. Deep Learning for Intelligent Wireless Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2018, 20, 2595–2621. [Google Scholar] [CrossRef]
- Zhao, L.; Zhang, X.; Chen, J.; Zhou, L. Physical layer security in the age of artificial intelligence and edge computing. IEEE Wirel. Commun. 2020, 27, 174–180. [Google Scholar] [CrossRef]
- Xiao, L.; Sheng, G.; Liu, S.; Dai, H.; Peng, M.; Song, J. Deep Reinforcement Learning-Enabled Secure Visible Light Communication against Eavesdropping. IEEE Trans. Commun. 2019, 67, 6994–7005. [Google Scholar] [CrossRef]
- Gui, L.; He, B.; Zhou, X.; Yu, C.; Shu, F.; Li, J. Learning-Based Wireless Powered Secure Transmission. IEEE Wirel. Commun. Lett. 2019, 8, 600–603. [Google Scholar]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Li, H.; Wang, X. Physical-Layer Security Enhancement in Wireless Communication Systems. Master’s Thesis, the University of Western Ontario London, Ontario, Canada, 2013. [Google Scholar]
- Zheng, G.; Choo, L.C.; Wong, K.K. Optimal cooperative jamming to enhance physical layer security using relays. IEEE Trans. Signal Process. 2011, 59, 1317–1322. [Google Scholar] [CrossRef]
- He, X.; Yener, A. On the Role of Feedback in Two-Way Secure Communication. In Proceedings of the 2008 42nd Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 26–29 October 2008; pp. 1093–1097. [Google Scholar]
- He, X.; Yener, A. Providing Secrecy When the Eavesdropper Channel is Arbitrarily Varying: A Case for Multiple Antennas. In Proceedings of the 2010 48th Annual Allerton Conference on Communication, Control, and Computing (Allerton), Monticello, IL, USA, 29 September–1 October 2010; pp. 1228–1235. [Google Scholar]
- Liao, W.C.; Chang, T.H.; Ma, W.K.; Chi, C.Y. QoS-based transmit beamforming in the presence of eavesdroppers: An optimized artificial-noise aided approach. IEEE Trans. Signal Process. 2011, 59, 1202–1216. [Google Scholar] [CrossRef]
- Reboredo, H.; Xavier, J.; Rodrigues, M.R.D. Filter design with secrecy constraints: The MIMO Gaussian wiretap channel. IEEE Trans. Signal Process. 2013, 61, 3799–3814. [Google Scholar] [CrossRef] [Green Version]
- Li, M.; Kundu, S.; Pados, D.A.; Batalama, S.N. Waveform design for secure SISO transmissions and multicasting. IEEE J. Sel. Areas Commun. 2013, 31, 1864–1874. [Google Scholar] [CrossRef]
- Mohaisen, M.; Wang, Y.; Chang, K. Multiple Antenna Technologies. Available online: https://arxiv.org/ftp/arxiv/papers/0909/0909.3342.pdf (accessed on 19 October 2021).
- Björnson, E.; Sanguinetti, L.; Wymeersch, H.; Hoydis, J.; Marzetta, T.L. Massive MIMO is a reality—What is next? Five promising research directions for antenna arrays. Digit. Signal Process. 2019, 94, 3–20. [Google Scholar] [CrossRef]
- Kapetanovic, D.; Zheng, G.; Rusek, F. Physical layer security for massive MIMO: An overview on passive eavesdropping and active attacks. IEEE Commun. Mag. 2015, 53, 21–27. [Google Scholar] [CrossRef] [Green Version]
- Liu, R.; Liu, T.; Poor, H.V.; Shamai, S. Multiple-input multiple-output Gaussian broadcast channels with common and confidential messages. IEEE Trans. Inf. Theory 2010, 56, 5477–5487. [Google Scholar]
- Liang, Y.; Poor, H.V.; Shamai, S. Information theoretic security. Found. Trends Commun. Inf. Theory 2009, 5, 355–580. [Google Scholar] [CrossRef]
- Ekrem, E.; Ulukus, S. Secure broadcasting using multiple antennas. J. Commun. Netw. 2010, 12, 411–432. [Google Scholar] [CrossRef]
- Lee, H.; Song, C.; Moon, J.; Lee, I. Precoder designs for MIMO Gaussian multiple access wiretap channels. IEEE Trans. Veh. Technol. 2017, 66, 8563–8568. [Google Scholar] [CrossRef]
- Fakoorian, S.A.A.; Swindlehurst, A.L. MIMO interference channel with confidential messages: Achievable secrecy rates and precoder design. IEEE Trans. Inf. Forensics Secur. 2011, 6, 640–649. [Google Scholar] [CrossRef]
- Ning, H.; Ling, C.; Leung, K.K. Feasibility condition for interference alignment with diversity. IEEE Trans. Inf. Theory 2011, 57, 2902–2912. [Google Scholar] [CrossRef]
- Chen, X.; Yuen, C. Performance analysis and optimization for interference alignment over MIMO interference channels with limited feedback. IEEE Trans. Signal Process. 2014, 62, 1785–1795. [Google Scholar] [CrossRef] [Green Version]
- Koyluoglu, O.O.; El Gamal, H.; Lai, L.; Poor, H.V. Interference alignment for secrecy. IEEE Trans. Inf. Theory 2011, 57, 3323–3332. [Google Scholar] [CrossRef] [Green Version]
- Yang, S.; Belfiore, J.C. Towards the optimal amplify-and-forward cooperative diversity scheme. IEEE Trans. Inf. Theory 2007, 53, 3114–3126. [Google Scholar] [CrossRef] [Green Version]
- Zhong, C.; Matthaiou, M.; Karagiannidis, G.K.; Huang, A.; Zhang, Z. Capacity bounds for AF dual-hop relaying in G fading channel. IEEE Trans. Veh. Technol. 2012, 61, 1730–1740. [Google Scholar] [CrossRef]
- Berger, S.; Kuhn, M.; Wittneben, A.; Unger, T.; Klein, A. Recent advances in amplify-and-forward two-hop relaying. IEEE Commun. Mag. 2009, 47, 50–56. [Google Scholar] [CrossRef]
- Wang, T.; Cano, A.; Giannakis, G.B.; Laneman, J.N. High performance cooperative demodulation with decode-and-forward relays. IEEE Trans. Commun. 2007, 55, 1427–1438. [Google Scholar] [CrossRef]
- Yi, Z.; Kim, I.M. Diversity order analysis of the decode-and forward cooperative networks with relay selection. IEEE Trans. Wireless Commun. 2008, 7, 1792–1799. [Google Scholar]
- Patel, C.S.; Stuber, G.L. Channel estimation for amplify and forward relay-based cooperation diversity systems. IEEE Trans. Wirel. Commun. 2007, 6, 2348–2356. [Google Scholar] [CrossRef]
- Huang, J.; Swindlehurst, A.L. Cooperative jamming for secure communications in MIMO relay networks. IEEE Trans. Signal Process. 2011, 59, 4871–4884. [Google Scholar] [CrossRef] [Green Version]
- Mo, J.; Tao, M.; Liu, Y.; Wang, R. Secure beamforming for MIMO two-way communications with an untrusted relay. IEEE Trans. Signal Process. 2014, 62, 2185–2199. [Google Scholar] [CrossRef] [Green Version]
- Li, Q.; Yang, Y.; Ma, W.K.; Lin, M.; Ge, J.; Lin, J. Robust cooperative beamforming and artificial noise design for physical-layer secrecy in AF multi-antenna multi-relay networks. IEEE Trans. Signal Process. 2015, 63, 206–220. [Google Scholar] [CrossRef]
- Zhou, X.S.; Song, L.; Zhang, Y. Physical Layer Security in Wireless Communications; CRC Press: Boca Raton, FL, USA, 2016; p. 295. [Google Scholar]
- Liang, Y.; Poor, H.V.; Shamai, S. Secure communication over fading channels. IEEE Trans. Inf. Theory 2008, 54, 2470–2492. [Google Scholar] [CrossRef] [Green Version]
- Bloch, M.R.; Barros, J. Physical-Layer Security: From Information Theory to Security Engineering, 1st ed.; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Bloch, M.R.; Laneman, J.N. Strong Secrecy from Channel Resolvability. IEEE Trans. Inf. Theory 2013, 59, 8077–8098. [Google Scholar] [CrossRef] [Green Version]
- Wang, H.M.; Xia, X.-G. Enhancing wireless secrecy via cooperation: Signal design and optimization. IEEE Commun. Mag. 2015, 53, 47–53. [Google Scholar] [CrossRef]
- Zhou, X.; Song, L.; Zhang, Y. Physical Layer Security in Wireless Communications, 1st ed.; CRC Press: Boca Raton, FL, USA, 2013. [Google Scholar] [CrossRef]
- Zhang, R.; Song, L.; Han, Z.; Jiao, B. Physical layer security for two-way untrusted relaying with friendly jammers. IEEE Trans. Veh. Technol. 2012, 61, 3693–3704. [Google Scholar] [CrossRef]
- Leung-Yan-Cheong, S.; Hellman, M. The Gaussian wiretap channel. IEEE Trans. Inf. Theory 1978, 24, 451–456. [Google Scholar] [CrossRef]
- Wang, H.M.; Zheng, T.X. Physical Layer Security in Random Cellular Networks; Springer Briefs in Computer Science; Springer: Singapore, 2016. [Google Scholar]
- Ryland, K.S.; Clancy, T.C.; Buehrer, R.M.; Dietrich, C.B. Software-Defined Radio Implementation of Two Physical Layer Security Techniques. Ph.D. Thesis, Virginia Tech, Blacksburg, VA, USA, 2018. Available online: https://vtechworks.lib.vt.edu/bitstream/handle/10919/82055/Ryland_KS_T_2018.pdf?sequence=1&isAllowed=y (accessed on 9 April 2022).
- Bloch, M.; Barros, J.; Rodrigues, M.R.; McLaughlin, S.W. Wireless information-theoretic security. IEEE Trans. Inf. Theory 2008, 54, 2515–2534. [Google Scholar] [CrossRef]
- Bassily, R.; Ekrem, E.; He, X.; Tekin, E.; Xie, J.; Bloch, M.R.; Ulukus, S.; Yener, A. Cooperative security at the physical layer: A summary of recent advances. IEEE Signal Process. Mag. 2013, 30, 16–28. [Google Scholar] [CrossRef]
- Park, K.H.; Wang, T.; Alouini, M.S. On the jamming power allocation for secure amplify-and-forward relaying via cooperative jamming. IEEE J. Sel. Areas Commun. 2013, 31, 1741–1750. [Google Scholar] [CrossRef]
- Bashar, S.; Ding, Z.; Li, G.Y. On secrecy of codebook-based transmission beamforming under receiver limited feedback. IEEE Trans. Wireless Commun. 2011, 10, 1212–1223. [Google Scholar] [CrossRef]
- Xiong, J.; Wong, K.K.; Ma, D.; Wei, J. A closed-form power allocation for minimizing secrecy outage probability for MISO wiretap channels via masked beamforming. IEEE Commun. Lett. 2012, 16, 1496–1499. [Google Scholar] [CrossRef]
- Gerbracht, S.; Scheunert, C.; Jorswieck, E.A. Secrecy outage in MISO systems with partial channel information. IEEE Trans. Inf. Forensics Secur. 2012, 7, 704–716. [Google Scholar] [CrossRef]
- Oggier, F.; Hassibi, B. The secrecy capacity of the MIMO wiretap channel. IEEE Trans. Inf. Theory 2011, 57, 4961–4972. [Google Scholar] [CrossRef] [Green Version]
- Gopala, P.K.; Lai, L.; El Gamal, H. On the secrecy capacity of fading channels. IEEE Trans. Inf. Theory 2008, 54, 4687–4698. [Google Scholar] [CrossRef] [Green Version]
- Zhou, X.; McKay, M.R.; Maham, B.; Hjørungnes, A. Rethinking the secrecy outage formulation: A secure transmission design perspective. IEEE Commun. Lett. 2011, 15, 302–304. [Google Scholar] [CrossRef] [Green Version]
- Hamamreh, J.M.; Yusuf, M.; Baykas, T.; Arslan, H. Cross MAC/PHY layer security design using ARQ with MRC and adaptive modulation. In Proceedings of the IEEE Wireless Communication Networks Conference (WCNC), Doha, Qatar, 3–6 April 2016; pp. 1–7. [Google Scholar]
- Liu, S.; Hong, Y.; Viterbo, E. Practical secrecy using artificial noise. IEEE Commun. Lett. 2013, 17, 1483–1486. [Google Scholar]
- Morrison, K.; Goeckel, D. Secrecy rate pair constraints for secure throughput. In Proceedings of the 2014 IEEE Military Communications Conference, Baltimore, MD, USA, 6–8 October 2014; pp. 479–484. [Google Scholar]
- Geraci, G.; Egan, M.; Yuan, J.; Razi, A.; Collings, I.B. Secrecy sumrates for multi-user MIMO regularized channel inversion precoding. IEEE Trans. Commun. 2012, 60, 3472–3482. [Google Scholar] [CrossRef] [Green Version]
- He, B.; Zhou, X.; Swindlehurst, A.L. On secrecy metrics for physical layer security over quasi-static fading channels. IEEE Trans. Wireless Commun. 2016, 15, 6913–6924. [Google Scholar] [CrossRef] [Green Version]
- He, X.; Khisti, A.; Yener, A. MIMO multiple access channel with an arbitrarily varying eavesdropper: Secrecy degrees of freedom. IEEE Trans. Inf. Theory 2013, 59, 4733–4745. [Google Scholar]
- Liu, Z.; Chen, C.; Bai, L.; Xiang, H.; Choi, J. Secure beamforming via amplify-and-forward relays in wireless networks with multiple eavesdroppers. In Proceedings of the IEEE International Conference on Communications (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 4698–4703. [Google Scholar]
- Dong, L.; Han, Z.; Petropulu, A.P.; Poor, H.V.L. Improving wireless physical layer security via cooperating relays. IEEE Trans. Signal Process. 2010, 58, 1875–1888. [Google Scholar] [CrossRef]
- Nomikos, N.; Nieto, A.; Makris, P.; Skoutas, D.N.; Vouyioukas, D.; Rizomiliotis, P.; Lopez, J.; Skianis, C. Relay selection for secure 5G green communications. Telecommun. Syst. 2015, 59, 169–187. [Google Scholar] [CrossRef]
- Li, J.; Petropulu, A.P.; Weber, S. On cooperative relaying schemes for wireless physical layer security. IEEE Trans. Signal Process. 2011, 59, 4985–4997. [Google Scholar] [CrossRef] [Green Version]
- Hong, Y.W.P.; Lan, P.C.; Kuo, C.C.J. Enhancing physical-layer secrecy in multiantenna wireless systems: An overview of signal processing approaches. IEEE Signal Process. Mag. 2013, 30, 29–40. [Google Scholar] [CrossRef]
- Yener, A.; Ulukus, S. Wireless physical-layer security: Lessons learned from information theory. Proc. IEEE 2015, 103, 1814–1825. [Google Scholar] [CrossRef] [Green Version]
- Boyd, S.; Boyd, S.P.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Bai, B.; Chen, W.; Cao, Z. Outage optimal subcarrier allocation for downlink secure OFDMA systems. In Proceedings of the IEEE Global Communications Conference (GLOBECOM) Workshops, Austin, TX, USA, 8–12 December 2014; pp. 1320–1325. [Google Scholar]
- Jindal, A.; Bose, R. Resource allocation for secure multicarrier AF relay system under total power constraint. IEEE Commun. Lett. 2014, 19, 231–234. [Google Scholar] [CrossRef]
- Chen, J.; Chen, X.; Gerstacker, W.H.; Ng, D.W.K. Resource allocation for a massive MIMO relay aided secure communication. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1700–1711. [Google Scholar] [CrossRef]
- Ng, D.W.K.; Lo, E.S.; Schober, R. Secure resource allocation and scheduling for OFDMA decode-and-forward relay networks. IEEE Trans. Wirel. Commun. 2011, 10, 3528–3540. [Google Scholar] [CrossRef]
- Huang, J.; Swindlehurst, A.L. Robust secure transmission in MISO channels based on worst-case optimization. IEEE Trans. Signal Process. 2012, 60, 1696–1707. [Google Scholar] [CrossRef] [Green Version]
- Jeong, C.; Kim, I.M. Optimal power allocation for secure multicarrier relay systems. IEEE Trans. Signal Process. 2011, 59, 5428–5442. [Google Scholar] [CrossRef]
- Tsai, S.H.; Poor, H.V. Power allocation for artificial-noise secure MIMO precoding systems. IEEE Trans. Signal Process. 2014, 62, 3479–3493. [Google Scholar] [CrossRef]
- Wang, L.; Elkashlan, M.; Huang, J.; Tran, N.H.; Duong, T.Q. Secure transmission with optimal power allocation in untrusted relay networks. IEEE Wireless Commun. Lett. 2014, 3, 289–292. [Google Scholar] [CrossRef]
- Benfarah, A.; Tomasin, S.; Laurenti, N. Power allocation in multiuser parallel Gaussian broadcast channels with common and confidential messages. IEEE Trans. Commun. 2016, 64, 2326–2339. [Google Scholar] [CrossRef]
- Zheng, T.X.; Wang, H.M. Optimal power allocation for artificial noise under imperfect CSI against spatially random eavesdroppers. IEEE Trans. Veh. Technol. 2016, 65, 8812–8817. [Google Scholar] [CrossRef] [Green Version]
- Khisti, A.; Wornell, G.W. Secure transmission with multiple antennas I: The MISOME wiretap channel. IEEE Trans. Inf. Theory 2010, 56, 3088–3104. [Google Scholar] [CrossRef] [Green Version]
- Khisti, A.; Wornell, G.W. Secure transmission with multiple antennas—Part II the MIMOME wiretap channel. IEEE Trans. Inf. Theory 2010, 56, 5515–5532. [Google Scholar] [CrossRef] [Green Version]
- Sheng, Z.; Tuan, H.D.; Sheng, Z.; Tuan, H.D.; Duong, T.Q.; Vincent Poor, H. Beamforming Optimization for Physical Layer Security in MISO Wireless Networks. IEEE Trans. Signal Process. 2018, 66, 3710–3723. [Google Scholar] [CrossRef] [Green Version]
- Palomar, D.P.; Chiang, M. A tutorial on decomposition methods for network utility maximization. IEEE J. Sel. Areas Commun. 2006, 24, 1439–1451. [Google Scholar] [CrossRef] [Green Version]
- Yaacoub, E.; Al-Husseini, M. Achieving physical layer security with massive MIMO beamforming. In Proceedings of the 2017 11th European Conference Antennas Propagation, EUCAP 2017, Paris, France, 19–24 March 2017; pp. 1753–1757. [Google Scholar]
- Shafiee, S.; Liu, N.; Ulukus, S. Towards the secrecy capacity of the Gaussian MIMO wire-tap channel: The 2-2-1 channel. IEEE Transactions on Information Theory 2009, 55, 4033–4039. [Google Scholar] [CrossRef] [Green Version]
- Björnson, E.; Bengtsson, M.; Ottersten, B. Optimal multiuser transmit beamforming: A difficult problem with a simple solution structure [lecture notes]. IEEE Signal Process. Mag. 2014, 31, 142–148. [Google Scholar] [CrossRef] [Green Version]
- Jeong, C.; Kim, I.M.; Kim, D.I. Joint secure beamforming design at the source and the relay for an amplify-and-forward MIMO untrusted relay system. IEEE Trans. Signal Process. 2012, 60, 310–325. [Google Scholar] [CrossRef]
- Zhao, P.; Zhang, M.; Yu, H.; Luo, H.; Chen, W. Robust beamforming design for sum secrecy rate optimization in MU-MISO networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1812–1823. [Google Scholar] [CrossRef] [Green Version]
- Shi, Q.; Xu, W.; Wu, J.; Song, E.; Wang, Y. Secure beamforming for MIMO broadcasting with wireless information and power transfer. IEEE Trans. Wirel. Commun. 2015, 14, 2841–2853. [Google Scholar] [CrossRef] [Green Version]
- Wang, X.; Wang, K.; Zhang, X.D. Secure relay beamforming with imperfect channel side information. IEEE Trans. Veh. Technol. 2013, 62, 2140–2155. [Google Scholar] [CrossRef]
- Zheng, G.; Arapoglou, P.D.; Ottersten, B. Physical layer security in multibeam satellite systems. IEEE Trans. Wirel. Commun. 2012, 11, 852–863. [Google Scholar] [CrossRef]
- Nghia, N.T.; Tuan, H.D.; Duong, T.Q.; Poor, H.V. MIMO beamforming for secure and energy-efficient wireless communication. IEEE Signal Process. Lett. 2017, 24, 236–239. [Google Scholar] [CrossRef] [Green Version]
- Nasir, A.A.; Tuan, H.D.; Duong, T.Q.; Poor, H.V. Secure and energy-efficient beamforming for simultaneous information and energy transfer. IEEE Trans. Wirel. Commun. 2017, 16, 7523–7537. [Google Scholar] [CrossRef] [Green Version]
- Zhao, N.; Yu, F.R.; Sun, H. Adaptive energy-efficient power allocation in green interference-alignment-based wireless networks. IEEE Trans. Veh. Technol. 2014, 64, 4268–4281. [Google Scholar] [CrossRef] [Green Version]
- Pu, W.; Xiao, J.; Zhang, T.; Luo, Z.Q. Overcoming dof limitation in robust beamforming: A penalized inequality-constrained approach. arXiv 2019, arXiv:1910.03365. [Google Scholar]
- Li, Q.; Ma, W.K. Spatially selective artificial-noise aided transmit optimization for MISO multi-eves secrecy rate maximization. IEEE Trans. Signal Process. 2013, 61, 2704–2717. [Google Scholar] [CrossRef] [Green Version]
- Lin, P.H.; Lai, S.H.; Lin, S.C.; Su, H.J. On secrecy rate of the generalized artificial-noise assisted secure beamforming for wiretap channels. IEEE J. Sel. Areas Commun. 2013, 31, 1728–1740. [Google Scholar] [CrossRef] [Green Version]
- Yang, N.; Yan, S.; Yuan, J.; Malaney, R.; Subramanian, R.; Land, I. Artificial noise: Transmission optimization in multi-input single-output wiretap channels. IEEE Trans. Commun. 2015, 63, 1771–1783. [Google Scholar] [CrossRef]
- Wang, B.; Mu, P.; Li, Z. Secrecy rate maximization with artificial noise-aided beamforming for MISO wiretap channels under secrecy outage constraint. IEEE Commun. Lett. 2015, 19, 18–21. [Google Scholar] [CrossRef]
- Tang, Y.; Xiong, J.; Ma, D.; Zhang, X. Robust artificial noise aided transmit design for MISO wiretap channels with channel uncertainty. IEEE Commun. Lett. 2013, 17, 2096–2099. [Google Scholar] [CrossRef]
- Reboredo, H.; Prabhu, V.; Rodrigues, M.R.; Xavier, J. Filter design with secrecy constraints: The multiple-input multiple-output Gaussian wiretap channel with zero forcing receive filters. In Proceedings of the 2011 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Prague, Czech Republic, 22–27 May 2011; pp. 3440–3443. [Google Scholar]
- Rezki, Z.; Alouini, M.S. On the finite-SNR diversity-multiplexing tradeoff of zero-forcing transmit scheme under secrecy constraint. In Proceedings of the IEEE International Conference Communication Workshops (ICC Workshops), Kyoto, Japan, 5–9 June 2011; pp. 1–5. [Google Scholar]
- Ahmed, E.; Yaqoob, I.; Hashem, I.A.T.; Shuja, J.; Imran, M.; Guizani, N.; Bakhsh, S.T. Recent advances and challenges in mobile big data. IEEE Commun. Mag. 2018, 56, 102–108. [Google Scholar] [CrossRef]
- Cayamcela, M.E.M.; Lim, W. Artificial intelligence in 5G technology: A survey. In Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 17–19 October 2018; pp. 860–865. [Google Scholar]
- Wang, T.; Wang, S.; Zhou, Z.H. Machine learning for 5G and beyond: From model-based to data-driven mobile wireless networks. China Commun. 2019, 16, 165–175. [Google Scholar]
- Challita, U.; Dong, L.; Saad, W. Proactive resource management for LTE in unlicensed spectrum: A deep learning perspective. IEEE Trans. Wirel. Commun. 2018, 17, 4674–4689. [Google Scholar] [CrossRef] [Green Version]
- Kilaru, S.; Harikishore, K.; Sravani, T.; Anvesh, C.L.; Balaji, T. Review and analysis of promising technologies with respect to Fifth generation networks. In Proceedings of the 2014 First International Conference on Networks & Soft Computing (ICNSC2014), Guntur, India, 19–20 August 2014; pp. 248–251. [Google Scholar]
- Wang, C.X.; Wu, S.; Bai, L.; You, X.; Wang, J.; Chih-Lin, I. Recent advances and future challenges for massive MIMO channel measurements and models. Sci. China Inf. Sci. 2016, 59, 021301. [Google Scholar] [CrossRef]
- Zhang, J.; Tang, P.; Tian, L.; Hu, Z.; Wang, T.; Wang, H. 6–100 GHz research progress and challenges from a channel perspective for fifth generation (5G) and future wireless communication. Sci. China Inf. Sci. 2017, 60, 080301. [Google Scholar] [CrossRef]
- Li, L.; Wang, D.; Niu, X.; Chai, Y.; Chen, L.; He, L.; Wu, X.; Zheng, F.; Cui, T.; You, X. mmWave communications for 5G: Implementation challenges and advances. Sci. China Inf. Sci. 2018, 61, 021301. [Google Scholar] [CrossRef] [Green Version]
- Zhang, C.; Xu, W. Neural networks: Efficient implementations and applications. In Proceedings of the 2017 IEEE 12th International Conference on ASIC (ASICON), Guiyang, China, 25–28 October2017; pp. 1029–1032. [Google Scholar]
- Xu, W.; Wu, Z.; Ueng, Y.L.; You, X.; Zhang, C. Improved polar decoder based on deep learning. In Proceedings of the 2017 IEEE International Workshop on Signal Processing Systems (SiPS), Lorient, France, 3–5 October 2017; pp. 1–6. [Google Scholar]
- Yang, C.; Xu, W.; Zhang, Z.; You, X.; Zhang, C. A channel-blind detection for SCMA based on image processing techniques. In Proceedings of the 2018 IEEE International Symposium on Circuits and Systems (ISCAS), Florence, Italy, 27–30 May 2018; pp. 1–5. [Google Scholar]
- Xu, W.; Zhong, Z.; Be’ery, Y.; You, X.; Zhang, C. Joint neural network equalizer and decoder. In Proceedings of the 2018 15th International Symposium on Wireless Communication Systems (ISWCS), Lisbon, Portugal, 28–31 August 2018; pp. 1–5. [Google Scholar]
- Xu, W.; Wang, Z.; You, X.; Zhang, C. Efficient fast convolution architectures for convolutional neural network. In Proceedings of the 2017 IEEE 12th International Conference on ASIC (ASICON), Guiyang, China, 25–28 October 2017; pp. 904–907. [Google Scholar]
- Xu, W.; You, X.; Zhang, C.; Be’ery, Y. Polar decoding on sparse graphs with deep learning. In Proceedings of the 2018 52nd Asilomar Conference on Signals, Systems, and Computers, Pacific Grove, CA, USA, 28–31 October 2018; pp. 599–603. [Google Scholar]
- Chih-Lin, I.; Sun, Q.; Liu, Z.; Zhang, S.; Han, S. The big-data-driven intelligent wireless network: Architecture, use cases, solutions, and future trends. IEEE Veh. Technol. Mag. 2017, 12, 20–29. [Google Scholar]
- Han, S.; Chih-Lin, I.; Li, G.; Wang, S.; Sun, Q. Big data enabled mobile network design for 5G and beyond. IEEE Commun. Mag. 2017, 55, 150–157. [Google Scholar] [CrossRef]
- Li, R.; Zhao, Z.; Zhou, X.; Ding, G.; Chen, Y.; Wang, Z.; Zhang, H. Intelligent 5G: When cellular networks meet artificial intelligence. IEEE Wirel. Commun. 2017, 24, 175–183. [Google Scholar] [CrossRef]
- Gao, X.; Jiang, B.; Li, X.; Gershman, A.B.; McKay, M.R. Statistical eigenmode transmission over jointly correlated MIMO channels. IEEE Trans. Inf. Theory 2009, 55, 3735–3750. [Google Scholar] [CrossRef]
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; Arcas, B.A. Communication-efficient learning of deep networks from decentralized data. arXiv, 2016; e-prints. [Google Scholar]
- Alkhateeb, A.; Alex, S.; Varkey, P.; Li, Y.; Qu, Q.; Tujkovic, D. Deep learning coordinated beamforming for highly-mobile millimeter wave systems. IEEE Access 2018, 6, 37328–37348. [Google Scholar] [CrossRef]
- Catak, E.; Catak, F.O.; Moldsvor, A. Adversarial machine learning security problems for 6G: MmWave beam prediction use-case. In Proceedings of the 2021 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom), Bucharest, Romania, 24–28 May 2021; pp. 1–6. [Google Scholar]
- Wu, Y.; Khisti, A.; Xiao, C.; Caire, G.; Wong, K.K.; Gao, X. A survey of physical layer security techniques for 5G wireless networks and challenges ahead. IEEE J. Sel. Areas Commun. 2018, 36, 679–695. [Google Scholar] [CrossRef] [Green Version]
- Qin, Z.; Ye, H.; Li, G.Y.; Juang, B.H.F. Deep learning in physical layer communications. IEEE Wirel. Commun. 2019, 26, 93–99. [Google Scholar] [CrossRef] [Green Version]
- You, X.; Zhang, C.; Tan, X.; Jin, S.; Wu, H. AI for 5G: Research directions and paradigms. Sci. China Inf. Sci. 2019, 62, 21301. [Google Scholar] [CrossRef] [Green Version]
- Samuel, N.; Diskin, T.; Wiesel, A. Deep MIMO detection. In Proceedings of the 2017 IEEE 18th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Sapporo, Japan, 3–6 July 2017; pp. 1–5. [Google Scholar]
- Ye, H.; Li, G.Y.; Juang, B.H. Power of deep learning for channel estimation and signal detection in OFDM systems. IEEE Wirel. Commun. Lett. 2018, 7, 114–117. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, S.; Zhang, C.; Chen, X.; Xu, S. A low-complexity belief propagation based decoding scheme for polar codes decodability detection and early stopping prediction. IEEE Access 2019, 7, 159808. [Google Scholar] [CrossRef]
- Xu, J.; Zhu, P.; Li, J.; You, X. Deep learning-based pilot design for multi-user distributed massive MIMO systems. IEEE Wirel. Commun. Lett. 2019, 8, 1016–1019. [Google Scholar] [CrossRef] [Green Version]
- Liang, F.; Shen, C.; Wu, F. An iterative BP-CNN architecture for channel decoding. IEEE J. Sel. Top. Signal Process. 2018, 12, 144–159. [Google Scholar] [CrossRef] [Green Version]
- Lv, X.Z.; Wei, P.; Xiao, X.C. Automatic identification of digital modulation signals using high order cumulants. Electron. Warf. 2004, 6, 1. [Google Scholar]
- Wang, T.; Wen, C.K.; Wang, H.; Gao, F.; Jiang, T.; Jin, S. Deep learning for wireless physical layer: Opportunities and challenges. China Commun. 2017, 14, 92–111. [Google Scholar] [CrossRef]
- O’shea, T.; Hoydis, J. An introduction to deep learning for the physical layer. IEEE Trans. Cogn. Commun. Netw. 2017, 3, 563–575. [Google Scholar] [CrossRef] [Green Version]
- O’Shea, T.J.; Erpek, T.; Clancy, T.C. Deep learning-based MIMO communications. arXiv 2017, arXiv:1707.07980. [Google Scholar]
- Tao, X.; Jiang, C.; Liu, J.; Xiao, A.; Qian, Y.; Lu, J. QoE Driven Resource Allocation in Next Generation Wireless Networks. IEEE Wirel. Commun. 2019, 26, 78–85. [Google Scholar] [CrossRef]
- Gesbert, D.; Hanly, S.; Huang, H.; Shitz, S.S.; Simeone, O.; Yu, W. Multi-cell MIMO cooperative networks: A new look at interference. IEEE J. Sel. Areas Commun. 2010, 28, 1380–1408. [Google Scholar] [CrossRef] [Green Version]
- Wang, D.; Zhang, Y.; Wei, H.; You, X.; Gao, X.; Wang, J. An overview of transmission theory and techniques of large-scale antenna systems for 5G wireless communications. Sci. China Inf. Sci. 2016, 59, 081301. [Google Scholar] [CrossRef] [Green Version]
- Kaelbling, L.P.; Littman, M.L.; Moore, A.W. Reinforcement learning: A survey. J. Artif. Intell. Res. 1996, 4, 237–285. [Google Scholar] [CrossRef] [Green Version]
- Wang, J.; Guan, W.; Huang, Y.; Schober, R.; You, X. Distributed optimization of hierarchical small cell networks: A GNEP framework. IEEE J. Sel. Areas Commun. 2017, 35, 249–264. [Google Scholar] [CrossRef] [Green Version]
- Bogale, T.E.; Wang, X.; Le, L.B. Machine intelligence techniques for next-generation context-aware wireless networks. arXiv 2018, arXiv:1801.04223. [Google Scholar]
- Li, R.; Zhao, Z.; Sun, Q.; Chih-Lin, I.; Yang, C.; Chen, X.; Zhao, M.; Zhang, H. Deep reinforcement learning for network slicing. IEEE Access 2018, 6, 74429–74441. [Google Scholar] [CrossRef]
- Long, H.; Xiang, W.; Zhang, Y.; Liu, Y.; Wang, W. Secrecy capacity enhancement with distributed precoding in multi-relay wiretap systems. IEEE Trans. Inf. Forensics Secur. 2012, 8, 229–238. [Google Scholar] [CrossRef]
- Fakoorian, S.A.A.; Swindlehurst, A.L. On the optimality of linear precoding for secrecy in the MIMO broadcast channel. IEEE J. Sel. Areas Commun. 2013, 31, 1701–1713. [Google Scholar] [CrossRef] [Green Version]
- Lin, C.H.; Tsai, S.H.; Lin, Y.P. Secure transmission using MIMO precoding. IEEE Trans. Inf. Forensics Secur. 2014, 9, 801–813. [Google Scholar]
- Hanif, M.F.; Tran, L.N.; Juntti, M.; Glisic, S. On linear precoding strategies for secrecy rate maximization in multiuser multiantenna wireless networks. IEEE Trans. Signal Process. 2014, 62, 3536–3551. [Google Scholar] [CrossRef]
- Zhang, H.; Huang, Y.; Li, S.; Yang, L. Energy-efficient precoder design for MIMO wiretap channels. IEEE Commun. Lett. 2014, 18, 1559–1562. [Google Scholar] [CrossRef]
- Wu, F.; Zhang, R.; Yang, L.L.; Wang, W. Transmitter precoding-aided spatial modulation for secrecy communications. IEEE Trans. Veh. Technol. 2015, 65, 467–471. [Google Scholar] [CrossRef]
- Weinand, A.; Karrenbauer, M.; Sattiraju, R.; Schotten, H. Application of machine learning for channel-based message authentication in mission critical machine type communication. In Proceedings of the European Wireless 2017 23th European Wireless Conference, Dresden, Germany, 17–19 May 2017; pp. 1–5. [Google Scholar]
- Jing, S.; Yu, A.; Liang, X.; You, X.; Zhang, C. Uniform belief propagation processor for massive MIMO detection and GF (2 n) LDPC decoding. In Proceedings of the 2017 IEEE 12th International Conference on ASIC (ASICON), Guiyang, China, 25–28 October 2017; pp. 961–964. [Google Scholar]
- Wen, C.K.; Jin, S.; Wong, K.K.; Chen, J.C.; Ting, P. Channel estimation for massive MIMO using Gaussian-mixture Bayesian learning. IEEE Trans. Wirel. Commun. 2014, 14, 1356–1368. [Google Scholar] [CrossRef]
- Sattiraju, R.; Kochems, J.; Schotten, H.D. Machine learning based obstacle detection for Automatic Train Pairing. In Proceedings of the 2017 IEEE 13th International Workshop on Factory Communication Systems (WFCS), Trondheim, Norway, 31 May–2 June 2017; pp. 1–4. [Google Scholar]
- Vieira, J.; Leitinger, E.; Sarajlic, M.; Li, X.; Tufvesson, F. Deep convolutional neural networks for massive MIMO fingerprint-based positioning. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–6. [Google Scholar]
- Ortuno, I.; Ortuno, M.; Delgado Penin, J.A. Error correcting neural networks for channels with Gaussian noise. In Proceedings of the Proceedings 1992—IJCNN International Joint Conference on Neural Networks, Baltimore, MD, USA, 7–11 June 1992; pp. 265–268. [Google Scholar]
- Sattiraju, R.; Weinand, A.; Schotten, H.D. Performance analysis of deep learning based on recurrent neural networks for channel coding. In Proceedings of the 2018 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Indore, India, 16–19 December 2018; pp. 1–6. [Google Scholar]
- Hornik, K.; Stinchcombe, M.; White, H. Multilayer feedforward networks are universal approximators. Neural Netw. 1989, 2, 359–366. [Google Scholar] [CrossRef]
- Zhang, X.; Kunz, A.; Schröder, S. Overview of 5G security in 3GPP. In Proceedings of the IEEE Conference Standards Communication Networks (CSCN), Helsinki, Finland, 18–20 September 2017; pp. 181–186. [Google Scholar]
- Ni, J.; Lin, X.; Shen, X.S. Efficient and secure service-oriented authentication supporting network slicing for 5G-enabled IoT. IEEE J. Sel. Areas Commun. 2018, 36, 644–657. [Google Scholar] [CrossRef]
- Mahmood, N.H.; Alves, H.; López, O.A.; Shehab, M.; Osorio, D.P.M.; Latva-aho, M. Six key enablers for machine type communication in 6G. arXiv 2019, arXiv:1903.05406. [Google Scholar]
- Yang, P.; Xiao, Y.; Xiao, M.; Li, S. 6G wireless communications: Vision and potential techniques. IEEE Netw. 2019, 33, 70–75. [Google Scholar] [CrossRef]
- Tariq, F.; Khandaker, M.R.; Wong, K.K.; Imran, M.A.; Bennis, M.; Debbah, M. A speculative study on 6G. IEEE Wirel. Commun. 2020, 27, 118–125. Available online: https://arxiv.org/pdf/1902.06700.pdf (accessed on 18 November 2021). [CrossRef]
- Jiang, C.; Zhang, H.; Ren, Y.; Han, Z.; Chen, K.C.; Hanzo, L. Machine Learning Paradigms for Next-Generation Wireless Networks. IEEE Wirel. Commun. 2017, 24, 98–105. [Google Scholar] [CrossRef] [Green Version]
- Huang, H.; Guo, S.; Gui, G.; Yang, Z.; Zhang, J.; Sari, H.; Adachi, H. Deep Learning for Physical-Layer 5G Wireless Techniques: Opportunities, Challenges and Solutions. IEEE Wirel. Commun. 2019, 27, 214–222. [Google Scholar] [CrossRef] [Green Version]
- Soltani, M.; Pourahmadi, V.; Mirzaei, A.; Sheikhzadeh, H. Deep Learning-Based Channel Estimation. IEEE Commun. Lett. 2019, 23, 652–655. [Google Scholar] [CrossRef] [Green Version]
- Mashhadi, B.; Gündüz, D. Deep Learning for Massive MIMO Channel State Acquisition and Feedback. J. Indian Inst. Sci. 2020, 100, 369–382. [Google Scholar] [CrossRef] [PubMed]
- Hu, S.; Rusek, F.; Edfors, O. Beyond massive MIMO: The potential of data transmission with large intelligent surfaces. IEEE Transactions on Signal Processing 2018, 66, 2746–2758. [Google Scholar] [CrossRef] [Green Version]
- He, H.; Wen, C.K.; Jin, S.; Li, G.Y. Deep learning-based channel estimation for beamspace mmWave massive MIMO systems. IEEE Wirel. Commun. Lett. 2018, 7, 852–855. [Google Scholar] [CrossRef] [Green Version]
- Wei, Z.; Yuan, W.; Li, S.; Yuan, J.; Ng, D.W.K. Off-grid Channel Estimation with Sparse Bayesian Learning for OTFS Systems. arXiv 2021, arXiv:2101.05629. [Google Scholar] [CrossRef]
- Ahmad, I.; Shahabuddin, S.; Kumar, T.; Okwuibe, J.; Gurtov, A.; Ylianttila, M. Security for 5G and beyond. IEEE Commun. Surv. Tutor. 2019, 21, 3682–3722. [Google Scholar] [CrossRef]
- Chen, K.C.; Zhang, T.; Gitlin, R.D.; Fettweis, G. Ultra-low latency mobile networking. IEEE Network 2018, 33, 181–187. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Zhang, Y. UAV communications for 5G and beyond: Recent advances and future trends. IEEE Internet Things J. 2018, 6, 2241–2263. [Google Scholar] [CrossRef] [Green Version]
- Challita, U.; Ferdowsi, A.; Chen, M.; Saad, W. Machine learning for wireless connectivity and security of cellular-connected UAVs. IEEE Wirel. Commun. 2019, 26, 28–35. [Google Scholar] [CrossRef] [Green Version]
- Wang, X.; Li, X.; Leung, V.C. Artificial intelligence-based techniques for emerging heterogeneous network: State of the arts, opportunities, and challenges. IEEE Access 2015, 3, 1379–1391. [Google Scholar] [CrossRef]
- Tang, F.; Kawamoto, Y.; Kato, N.; Liu, J. Future intelligent and secure vehicular network toward 6G: Machine-learning approaches. Proc. IEEE 2019, 108, 292–307. [Google Scholar] [CrossRef]
- Alhajri, R.; Zagrouba, R.; Al-Haidari, F. Survey for anomaly detection of IoT botnets using machine learning auto-encoders. Int. J. Appl. Eng. Res 2019, 14, 2417–2421. [Google Scholar]
- Shakiba-Herfeh, M.; Chorti, A.; Poor, H.V. Physical layer security: Authentication, integrity, and confidentiality. In Physical Layer Security; Springer: Cham, Switzerland, 2021; pp. 129–150. [Google Scholar]
- Liang, Y.C.; Niyato, D.; Larsson, E.G.; Popovski, P. 6G mobile networks: Emerging technologies and applications. China Commun. 2020, 17, 4. [Google Scholar] [CrossRef]
- Liang, Y.; Poor, H.V.; Ying, L. Secure communications over wireless broadcast networks: Stability and utility maximization. IEEE Trans. Inf. Forensics Secur. 2011, 6, 682–692. [Google Scholar] [CrossRef]
- Tang, X.; Ren, P.; Wang, Y.; Han, Z. Combating full-duplex active eavesdropper: A hierarchical game perspective. IEEE Trans. Commun. 2016, 65, 1379–1395. [Google Scholar] [CrossRef]
- Abedi, M.R.; Mokari, N.; Saeedi, H.; Yanikomeroglu, H. Robust resource allocation to enhance physical layer security in systems with full-duplex receivers: Active adversary. IEEE Trans. Wirel. Commun. 2016, 16, 885–899. [Google Scholar] [CrossRef]









| Existing Papers | Research Issues | Important Content |
|---|---|---|
| [12] | Examine the security threats and corresponding defense methods in PHY security. | Summary of the security requirements and threats in wireless networks considering the network protocols at various levels of data layers. Additionally, a comprehensive review of state-of-the-art PHY security and existing security protocols for 13 various wireless networks. |
| [25] | A comprehensive survey on the basic theories and key technologies of PHY security. | Discussion of the key technologies, limitations, and solutions of PHY security from the perspective of security coding, physical-layer authentication, secret key generation, and multi-antenna techniques. |
| [26] | Security threats and the corresponding countermeasure techniques. | Technologies, security attacks, and defense mechanisms in PHY security using game-theoretic approaches. |
| [27] | Overview of the key technologies of PHY security. | Recent technologies, optimization techniques, and limitations of PHY security from the perspective of information-theoretic security and wiretap channels. |
| [28] | A comprehensive investigation of multi-antenna techniques. | Survey of multi-antenna techniques in multi-user networks for improving the security performance of PHY security, but not considering CSI accuracy. |
| [29] | A brief survey on multi-antenna techniques. | Investigation on multi-antenna techniques in PHY security for improving secrecy performance considering the accuracy of CSI. |
| [30] | A comprehensive overview of the optimization and design strategies of PHY security. | Survey on security designs and optimization techniques from the viewpoints of information theory and security metrics in wireless PHY security. |
| [31] | Comprehensive overview of all existing PHY security techniques. | Classification of the existing PHY security techniques and brief discussion of the big picture they can be easily understood and applied in different communication systems. |
| [32] | Challenges of PHY security in real-world systems. | Identification of the existing assumptions and opportunities for applying PHY security in practical applications. |
| [34] | A comprehensive investigation of AI and edge computing (EC) for PLS. | Identification of the existing challenges in the design and optimization of PLS and design of an enhancement scheme for PLS application. |
| Acronyms | Full-Form Definition |
|---|---|
| 5G | Fifth-generation mobile networks |
| AI | Artificial intelligence |
| AF | Amplify-and-forward |
| ANN | Artificial neural networks |
| AWGN | Additive white Gaussian noise |
| B5G | Beyond fifth-generation networks |
| BER | Bit error rate |
| BLER | Block error rate |
| CNN | Convolutional neural network |
| CSI | Channel state information |
| DF | decode-and-forward |
| DL | Deep learning |
| DNN | Deep neural networks |
| FDD | Frequency division duplexing |
| IoT | Internet of Things |
| ILDP | Interactive learning design paradigm |
| LDPC | Low-density parity-check |
| LOS | Line of sight |
| MISO | Multiple-input single-output |
| MIMO | Multiple-input multiple-output |
| ML | Machine learning |
| mmWave | Millimeter wave |
| NOMA | Non-orthogonal multiple access |
| NDP | Non-deterministic polynomial |
| QoS | Quality of service |
| PLS | PHY security/Physical layer security |
| PER | Packet error rate |
| OFDM | Orthogonal frequency division multiplexing |
| SDP | Semi-definite programming |
| SOP | Secrecy outage probability |
| SIMO | Single-input multiple-output |
| SISO | Single-input single-output |
| SDP | Semi-definite programming |
| SNR | Signal-to-noise ratio |
| SIPNR | Signal-to-interference-plus-noise ratio |
| ReLU | Rectified linear units |
| ZF | Zero forcing |
| Metric Types | Definition | Optimization Problems |
|---|---|---|
| Secrecy capacity | The maximum (upper bound) of the secrecy rate [72]. | Transmission effectiveness of secure communication strategies. |
| Secrecy rate | The transmission rate that can be genuinely supported by the main transmission channel but not decoded on the eavesdropper channel [85]. | |
| Secrecy outage probability (SOP) | The probability that the actual or targeted transmission rate is greater than the instantaneous secrecy capacity [86,87,88]. | Reliability and security of communication systems. |
| Quality of service (QoS) | The performance improvement of secure transmission strategies, which includes the SINR-based, PER-based and BER-based metrics [27,31,89]. | QoS and security of transmission systems. |
| Power/energy consumption | The minimum power consumption that is needed to ensure secure QoS requirements for different services [90,91,92,93]. | Resource consumption costs for secrecy performance. |
| ML- and AI-Based Techniques | Focused Issues | Advantages | Limitations |
|---|---|---|---|
| AI and edge computing (EC) [34] | Investigation of the gap between PHY security and AI–EC. | Robust PHY layer key generation schemes and secure resource management frameworks. | Complexity of training models for various PLS issues. |
| Deep reinforcement learning [35] | Enabling of secured visible light communication (VLC). | Achievement of the optimal solution between secrecy rate and utility. | Avoidance of the quantization error. |
| Integrated AI [36] | Integration of wireless power transfers and cooperative jamming for secure transmission. | Achievement of the trade-off between security performance and energy consumption. | Limitations of optimal scheme for solving more complex problems. |
| Iterative water-filling algorithm [147] | A comprehensive investigation of MIMO eigenmode transmission. | Bridging of the gap between AI and 5G technologies. | Challenging integration of AI and 5G networks. |
| Distributed AI federated learning [148] | A brief survey on multi-antenna techniques. | Contribution of robust and fine-grained security metrics. | Security issues at the device level. |
| Feed-forward DL model [149] | RF beamforming codeword prediction. | Promising results for beamforming problems. | Lack of investigation into security issues. |
| Adversarial DL model [150] | Adversarial attacks for beamforming prediction. | Consideration of security issues. | Complexity of adversarial training approach. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tefera, M.K.; Jin, Z.; Zhang, S. A Review of Fundamental Optimization Approaches and the Role of AI Enabling Technologies in Physical Layer Security. Sensors 2022, 22, 3589. https://doi.org/10.3390/s22093589
Tefera MK, Jin Z, Zhang S. A Review of Fundamental Optimization Approaches and the Role of AI Enabling Technologies in Physical Layer Security. Sensors. 2022; 22(9):3589. https://doi.org/10.3390/s22093589
Chicago/Turabian StyleTefera, Mulugeta Kassaw, Zengwang Jin, and Shengbing Zhang. 2022. "A Review of Fundamental Optimization Approaches and the Role of AI Enabling Technologies in Physical Layer Security" Sensors 22, no. 9: 3589. https://doi.org/10.3390/s22093589
APA StyleTefera, M. K., Jin, Z., & Zhang, S. (2022). A Review of Fundamental Optimization Approaches and the Role of AI Enabling Technologies in Physical Layer Security. Sensors, 22(9), 3589. https://doi.org/10.3390/s22093589






