Customised Intrusion Detection for an Industrial IoT Heterogeneous Network Based on Machine Learning Algorithms Called FTL-CID
Abstract
:1. Introduction
- To the best of our knowledge, the FT-CID is the first model to apply FTL to a heterogeneous RPL-IIoT IDS security model. This approach aggregates the data from the IIoT application domain. It accomplishes a customised attack detection model with global knowledge for the IIoT network by transferring and federating learning knowledge between the server and edges.
- First, the FT-CID uses FL to accumulate the local learning models of different RPL-IIoT networks and generate a global shared parameter for edges to detect attack types of existing and unknown intrusions.
- Secondly, using relational knowledge transfer learning, the FT-CID achieves a personalised IDS by efficiently transferring distributed local and global parameters between the server and IIoT network or sensors with high security.
- Thirdly, the FT-CID detects and classifies intrusions under multiple classes using the customised IDS model and ensures a rich level of routing security for diverse IIoT scenarios without data leakage.
- Finally, the FT-CID reflects the security of a heterogeneous IIoT environment by conducting an experimental evaluation of the IIoT dataset: advanced metering infrastructure (AMI).
2. Related Work
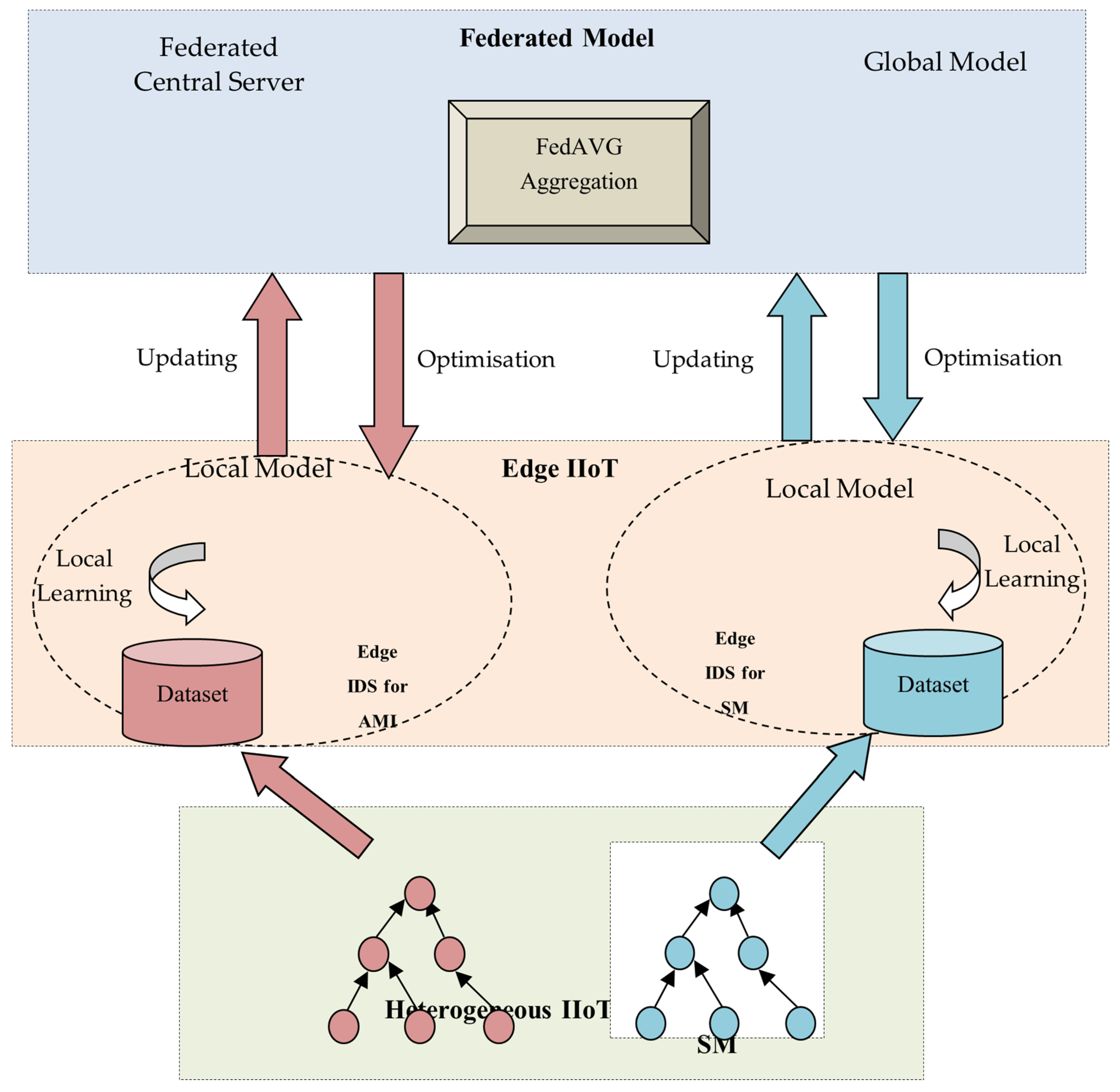
3. System Model
4. Proposed System Design Overview
4.1. Dataset Construction
4.2. Preprocessing and Feature Selection
4.3. Optimised FTL-assisted Edge IDS Learning
4.3.1. Distributed Local Model Training with Parameter Transfer
4.3.2. Global Model Generation with Relational Knowledge Transfer
4.3.3. SGD-TL-Based Local Model Optimisation
//FTL-assisted RPL IDS Learning Process//
5. Experimental Evaluation
5.1. Experimental Setup
5.2. Dataset Description
5.3. Performance Metrics
- True positive (TP) = number of samples correctly detected as intrusion samples;
- True negative (TN) = number of samples correctly detected as normal samples;
- False positive (FP) = number of samples incorrectly detected as intrusion samples;
- False negative (FN) = number of samples incorrectly detected as normal samples.
6. Results and Discussion
6.1. Training Data Size vs. Precision
6.2. Training Data Size vs. Recall
6.3. Number of Communication Rounds vs. F-Measure
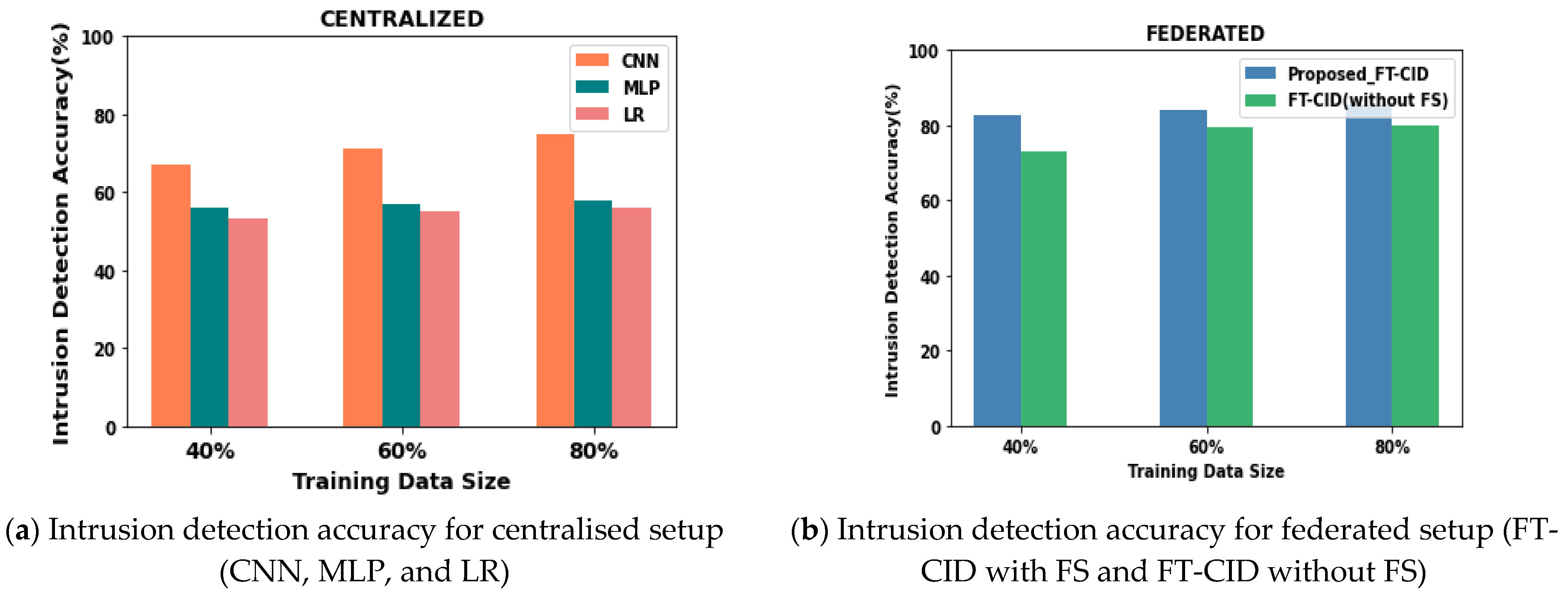
6.4. Intrusion Detection Accuracy
6.5. Training Data Size vs. False-Positive Rate
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Nižetić, S.; Šolić, P.; González-de-Artaza, D.L.-d.I.; Patrono, L. Internet of Things (IoT): Opportunities, issues and challenges towards a smart and sustainable future. J. Clean. Prod. 2020, 274, 122877. [Google Scholar] [CrossRef]
- Varga, P.; Peto, J.; Franko, A.; Balla, D.; Haja, D.; Janky, F.; Soos, G.; Ficzere, D.; Maliosz, M.; Toka, L. 5G support for Industrial IoT Applications—Challenges, Solutions, and Research gaps. Sensors 2020, 20, 828. [Google Scholar] [CrossRef] [Green Version]
- Thakkar, A.; Lohiya, R. A Review on Machine Learning and Deep Learning Perspectives of IDS for IoT: Recent Updates, Security Issues, and Challenges. Arch. Comput. Methods Eng. 2020, 28, 3211–3243. [Google Scholar] [CrossRef]
- Seyfollahi, A.; Ghaffari, A. A Review of Intrusion Detection Systems in RPL Routing Protocol Based on Machine Learning for Internet of Things Applications. Wirel. Commun. Mob. Comput. 2021, 2021, 8414503. [Google Scholar] [CrossRef]
- Simoglou, G.; Violettas, G.; Petridou, S.; Mamatas, L. Intrusion detection systems for RPL security: A comparative analysis. Comput. Secur. 2021, 104, 102219. [Google Scholar] [CrossRef]
- Imteaj, A.; Thakker, U.; Wang, S.; Li, J.; Amini, M.H. A Survey on Federated Learning for Resource-Constrained IoT Devices. IEEE Internet Things J. 2021, 9, 1–24. [Google Scholar] [CrossRef]
- Khan, L.U.; Saad, W.; Han, Z.; Hossain, E.; Hong, C.S. Federated Learning for Internet of Things: Recent Advances, Taxonomy, and Open Challenges. IEEE Commun. Surv. Tutorials 2021, 23, 1759–1799. [Google Scholar] [CrossRef]
- Wang, K.I.-K.; Zhou, X.; Liang, W.; Yan, Z.; She, J. Federated Transfer Learning Based Cross-Domain Prediction for Smart Manufacturing. IEEE Trans. Ind. Informatics 2021, 18, 4088–4096. [Google Scholar] [CrossRef]
- Verma, A.; Ranga, V. Machine Learning Based Intrusion Detection Systems for IoT Applications. Wirel. Pers. Commun. 2020, 111, 2287–2310. [Google Scholar] [CrossRef]
- Chakraborty, S.; Onuchowska, A.; Samtani, S.; Jank, W.; Wolfram, B. Machine Learning for Automated Industrial IoT Attack Detection: An Efficiency-Complexity Trade-off. ACM Trans. Manag. Inf. Syst. 2021, 12, 1–28. [Google Scholar] [CrossRef]
- Sharma, M.; Elmiligi, H.; Gebali, F. A Novel Intrusion Detection System for RPL-Based Cyber–Physical Systems. IEEE Can. J. Electr. Comput. Eng. 2021, 44, 246–252. [Google Scholar] [CrossRef]
- Foley, J.; Moradpoor, N.; Ochenyi, H. Employing a Machine Learning Approach to Detect Combined Internet of Things Attacks against Two Objective Functions Using a Novel Dataset. Secur. Commun. Networks 2020, 2020, 2804291. [Google Scholar] [CrossRef]
- Agiollo, A.; Conti, M.; Kaliyar, P.; Lin, T.-N.; Pajola, L. DETONAR: Detection of Routing Attacks in RPL-Based IoT. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1178–1190. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Ding, M.; Pathirana, P.N.; Seneviratne, A.; Li, J.; Poor, H.V. Federated learning for internet of things: A comprehensive survey. IEEE Commun. Surv. Tutor. 2021, 23, 1622–1658. [Google Scholar] [CrossRef]
- Tang, Z.; Hu, H.; Xu, C. A federated learning method for network intrusion detection. Concurr. Comput. Pract. Exp. 2022, 34, e6812. [Google Scholar] [CrossRef]
- Maurya, S.; Joseph, S.; Asokan, A.; Algethami, A.A.; Hamdi, M.; Rauf, H.T. Federated Transfer Learning for Authentication and Privacy Preservation Using Novel Supportive Twin Delayed DDPG (S-TD3) Algorithm for IIoT. Sensors 2021, 21, 7793. [Google Scholar] [CrossRef]
- Cui, L.; Qu, Y.; Xie, G.; Zeng, D.; Li, R.; Shen, S.; Yu, S. Security and Privacy-Enhanced Federated Learning for Anomaly Detection in IoT Infrastructures. IEEE Trans. Ind. Informatics 2021, 18, 3492–3500. [Google Scholar] [CrossRef]
- Rey, V.; Sánchez, P.M.S.; Celdrán, A.H.; Bovet, G. Federated learning for malware detection in IoT devices. Comput. Networks 2022, 204, 108693. [Google Scholar] [CrossRef]
- Nguyen, T.D.; Rieger, P.; Miettinen, M.; Sadeghi, A.-R. Poisoning Attacks on Federated Learning-based IoT Intrusion Detection System. In Proceedings of the 2020 Workshop on Decentralized IoT Systems and Security, San Diego, CA, USA, 23–26 February 2020; pp. 1–7. [Google Scholar] [CrossRef]
- Li, Y.; Li, Y.; Xu, H.; Ren, S. An Adaptive Communication-Efficient Federated Learning to Resist Gradient-Based Reconstruction Attacks. Secur. Commun. Networks 2021, 2021, 9919030. [Google Scholar] [CrossRef]
- Wu, Q.; He, K.; Chen, X. Personalized Federated Learning for Intelligent IoT Applications: A Cloud-Edge Based Framework. IEEE Open J. Comput. Soc. 2020, 1, 35–44. [Google Scholar] [CrossRef]
- Rahman, S.A.; Tout, H.; Talhi, C.; Mourad, A. Internet of Things Intrusion Detection: Centralized, On-Device, or Federated Learning? IEEE Netw. 2020, 34, 310–317. [Google Scholar] [CrossRef]
- Chen, Z.; Lv, N.; Liu, P.; Fang, Y.; Chen, K.; Pan, W. Intrusion Detection for Wireless Edge Networks Based on Federated Learning. IEEE Access 2020, 8, 217463–217472. [Google Scholar] [CrossRef]
- Man, D.; Zeng, F.; Yang, W.; Yu, M.; Lv, J.; Wang, Y. Intelligent Intrusion Detection Based on Federated Learning for Edge-Assisted Internet of Things. Secur. Commun. Networks 2021, 2021, 9361348. [Google Scholar] [CrossRef]
- Attota, D.C.; Mothukuri, V.; Parizi, R.M.; Pouriyeh, S. An Ensemble Multi-View Federated Learning Intrusion Detection for IoT. IEEE Access 2021, 9, 117734–117745. [Google Scholar] [CrossRef]
- Zhang, W.; Yang, D.; Wu, W.; Peng, H.; Zhang, N.; Zhang, H.; Shen, X. Optimizing Federated Learning in Distributed Industrial IoT: A Multi-Agent Approach. IEEE J. Sel. Areas Commun. 2021, 39, 3688–3703. [Google Scholar] [CrossRef]
- Yilmaz, S.; Aydogan, E.; Sen, S. A Transfer Learning Approach for Securing Resource-Constrained IoT Devices. IEEE Trans. Inf. Forensics Secur. 2021, 16, 4405–4418. [Google Scholar] [CrossRef]
- Zhang, P.; Sun, H.; Situ, J.; Jiang, C.; Xie, D. Federated Transfer Learning for IIoT Devices With Low Computing Power Based on Blockchain and Edge Computing. IEEE Access 2021, 9, 98630–98638. [Google Scholar] [CrossRef]
- Liu, X.; Yu, W.; Liang, F.; Griffith, D.; Golmie, N. Toward Deep Transfer Learning in Industrial Internet of Things. IEEE Internet Things J. 2021, 8, 12163–12175. [Google Scholar] [CrossRef]
- Guan, J.; Cai, J.; Bai, H.; You, I. Deep transfer learning-based network traffic classification for scarce dataset in 5G IoT systems. Int. J. Mach. Learn. Cybern. 2021, 12, 3351–3365. [Google Scholar] [CrossRef]
- Raza, A.; Tran, K.P.; Koehl, L.; Li, S. Designing ECG monitoring healthcare system with federated transfer learning and explainable AI. Knowledge-Based Syst. 2022, 236, 107763. [Google Scholar] [CrossRef]
- Otoum, Y.; Wan, Y.; Nayak, A. Federated Transfer Learning-Based IDS for the Internet of Medical Things (IoMT). In Proceedings of the 2021 IEEE Globecom Workshops, Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Al-Hadhrami, Y.; Hussain, F.K. Real time dataset generation framework for intrusion detection systems in IoT. Futur. Gener. Comput. Syst. 2020, 108, 414–423. [Google Scholar] [CrossRef]
- Ullah, I.; Mahmoud, Q.H. A Scheme for Generating a Dataset for Anomalous Activity Detection in IoT Networks. In Proceedings of the Canadian Conference on Artificial Intelligence, Ottawa, ON, Canada, 13–15 May 2020; Volume 12109, pp. 508–520. [Google Scholar] [CrossRef]
- Nadimi-Shahraki, M.H.; Taghian, S.; Mirjalili, S. An improved grey wolf optimizer for solving engineering problems. Expert Syst. Appl. 2020, 166, 113917. [Google Scholar] [CrossRef]
- McMahan, B.; Moore, E.; Ramage, D.; Hampson, S.; y Arcas, B.A. Communication-efficient learning of deep networks from decentralised data. In Artificial intelligence and statistics. In Proceedings of the 20th International Conference on Artificial Intelligence and Statistics, Lauderdale, FL, USA, 20–22 April 2017; pp. 1273–1282. [Google Scholar]






| Training Data Size (%) | Precision (%) | ||
|---|---|---|---|
| Proposed FT-CID | CNN | MLP | |
| 40 | 82.97 | 68.64 | 51.25 |
| 60 | 84.32 | 75.63 | 60.83 |
| 80 | 85.18 | 78.92 | 71.09 |
| Training Data Size (%) | Recall (%) | ||
|---|---|---|---|
| Proposed FT-CID | MLP | LR | |
| 40 | 82.12 | 52.95 | 50.62 |
| 60 | 83.08 | 59.38 | 55.99 |
| 80 | 84.94 | 65.36 | 57.91 |
| Number of Communication Rounds | F-Measure (%) | ||
|---|---|---|---|
| Centralised | Federated | ||
| AMI | |||
| Proposed FT-CID | CNN | Proposed FT-CID | |
| 5 | 79.23 | 67.23 | 78.97 |
| 10 | 80.16 | 68.98 | 80.12 |
| 15 | 83.296 | 72.15 | 82.72 |
| 20 | 85.91 | 69.15 | 85.75 |
| 25 | 79.56 | 67.16 | 79.98 |
| Training Data Size (%) | Intrusion Detection Accuracy (%) | ||||
|---|---|---|---|---|---|
| Centralised | Federated | ||||
| CNN | MLP | LR | Proposed FT-CID | Proposed FT-CID (without FS) | |
| 40 | 67.16 | 55.86 | 53.25 | 82.83 | 73.24 |
| 60 | 71.23 | 56.95 | 54.96 | 84.17 | 79.65 |
| 80 | 74.89 | 58.04 | 56.12 | 85.52 | 80.03 |
| Training Data Size (%) | False-Positive Rate (%) | ||
|---|---|---|---|
| Proposed FT-CID | CNN | MLP | |
| 40 | 16.57 | 31.251 | 43.74 |
| 60 | 15.01 | 27.36 | 42.17 |
| 80 | 13.29 | 24.98 | 41.76 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abosata, N.; Al-Rubaye, S.; Inalhan, G. Customised Intrusion Detection for an Industrial IoT Heterogeneous Network Based on Machine Learning Algorithms Called FTL-CID. Sensors 2023, 23, 321. https://doi.org/10.3390/s23010321
Abosata N, Al-Rubaye S, Inalhan G. Customised Intrusion Detection for an Industrial IoT Heterogeneous Network Based on Machine Learning Algorithms Called FTL-CID. Sensors. 2023; 23(1):321. https://doi.org/10.3390/s23010321
Chicago/Turabian StyleAbosata, Nasr, Saba Al-Rubaye, and Gokhan Inalhan. 2023. "Customised Intrusion Detection for an Industrial IoT Heterogeneous Network Based on Machine Learning Algorithms Called FTL-CID" Sensors 23, no. 1: 321. https://doi.org/10.3390/s23010321
APA StyleAbosata, N., Al-Rubaye, S., & Inalhan, G. (2023). Customised Intrusion Detection for an Industrial IoT Heterogeneous Network Based on Machine Learning Algorithms Called FTL-CID. Sensors, 23(1), 321. https://doi.org/10.3390/s23010321








