Robust Trajectory and Resource Optimization in UAV-Enabled IoT Networks under Probabilistic LoS Channel in Presence of Jammers
Abstract
:1. Introduction
- First, we model a more accurate probabilistic LoS channel model to adapt the real-time changing characteristics of the channel. Under such a setup, we design the UAV’s 3D trajectory, IoT devices’ transmit power, and scheduling in the presence of a jammer. In addition, we consider the practical scenario, that is, the jammer with imperfect location information operates the process of transmitting jamming signals. This model fully considers the variability and complexity of the external environment, which has good practical value and research significance.
- Second, a UAV-enabled optimization framework is proposed under a probabilistic LoS channel, where a jammer with imperfect location information transmits jamming to the UAV. Specifically, we aim to maximize all IoT devices’ throughput based on the probabilistic LoS channel model. Because of the coupling of the variables, the non-convexity and non-concavity of the constraint, and the non-convexity of the objective function, it is intractable to solve the optimization problem. To this end, we first use the block coordinate descent (BCD) method to solve the coupling problem, which iteratively optimizes the UAV’s trajectory, IoT devices’ scheduling, and transmit power. Then, we apply the difference of convex (D.C) programming approach to address the non-convexity and non-concavity, and we address the integer UAV scheduling constraints by continuous relaxing. Because the sub-problems of optimizing the UAV trajectory are still non-convex, we utilize the successive convex approximation (SCA) technology and -procedure to derive the local optimal solutions.
- Finally, we compare and verify different algorithms by simulation. Compared with the trajectory optimization based on the conventional simplified probabilistic LoS channel model, our proposed anti-jamming joint robust optimization algorithm based on the accurate probabilistic LoS model can vastly increase the system’s throughput by balancing the angle and distance trade-off. The performance is much better than the simplified probabilistic LoS channel model.
2. Problem Statement and Formulation
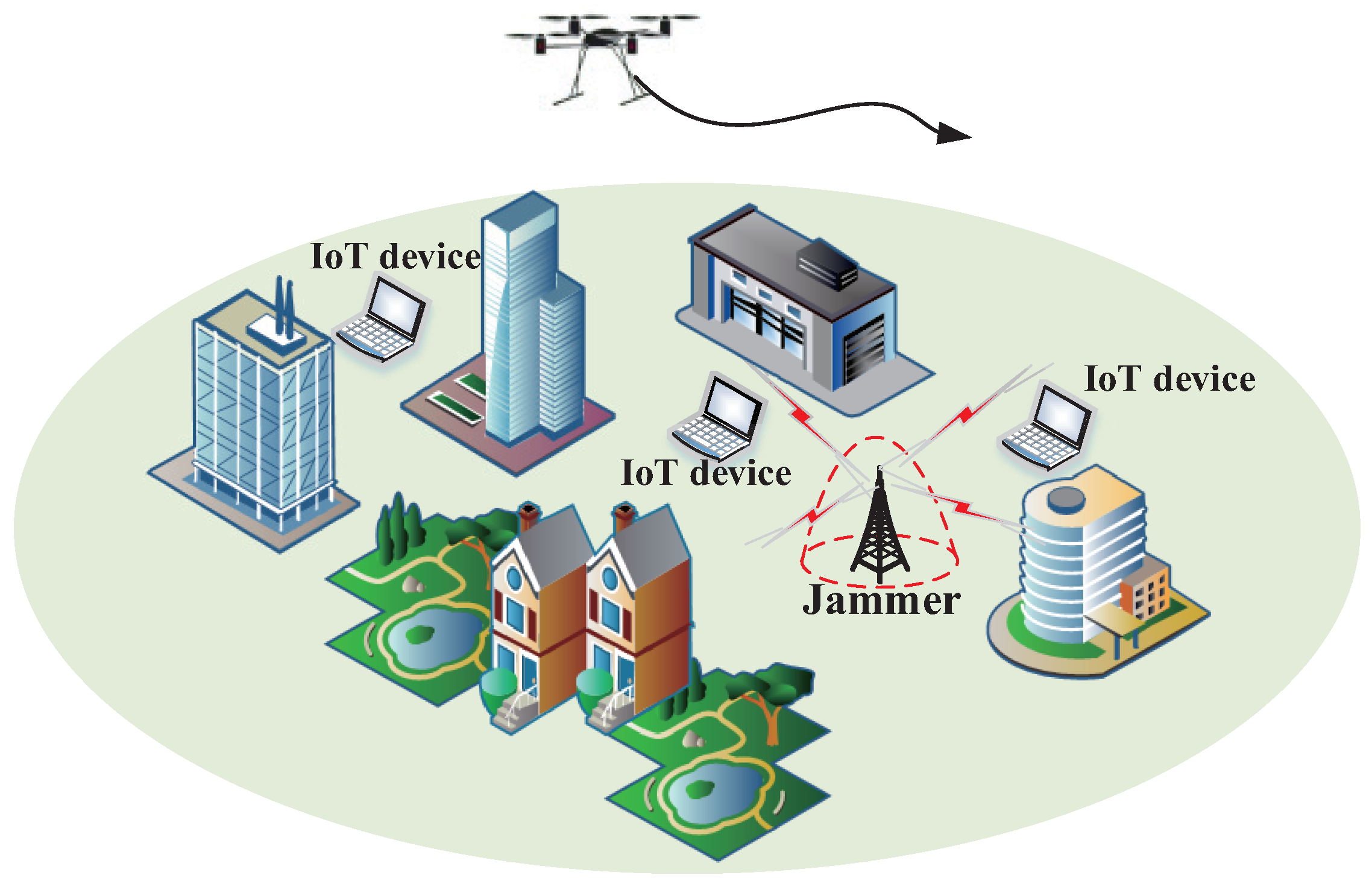
2.1. System Model
2.2. Channel Model
2.3. Problem Formulation for Throughput Maximization
3. Robust Iterative Algorithm for Throughput Maximization
3.1. Trajectory Optimization with Given Scheduling and Transmit Power
3.2. Scheduling Optimization with Given Transmit Power and Trajectory
3.3. Transmit Power Optimization with Given Trajectory and Scheduling
3.4. Overall Algorithm
| Algorithm 1 Robust iterative algorithm for Problem (21) |
|
4. Simulations and Discussion
4.1. Simulation Setup
4.2. Performance Comparison
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| UAV | unmanned aerial vehicle |
| IoT | Internet of Things |
| LoS | line-of-sight |
| BCD | block coordinate descent |
| SCA | successive convex approximation |
| D.C | difference of convex |
| 3D | three-dimensional |
| U2G | UAV to ground |
| NLoS | non-line-of-sight |
| PL | probabilistic LoS |
| AWGN | additive white Gaussian noise |
| LP | linear programming |
References
- Vo, V.N.; So-In, C.; Tran, H.; Tran, D.-D.; Huu, T.P. Performance Analysis of an Energy-Harvesting IoT System Using a UAV Friendly Jammer and NOMA Under Cooperative Attack. IEEE Access 2020, 8, 221986–222000. [Google Scholar] [CrossRef]
- Xiang, Z.; Yang, W.; Cai, Y.; Ding, Z.; Song, Y.; Zou, Y. NOMA-Assisted Secure Short-Packet Communications in IoT. IEEE Wirel. Commun. 2020, 27, 8–15. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, K.; Han, J.; Zhu, L.; Xiao, Z.; Xia, X.-G. Resource Allocation and 3-D Placement for UAV-Enabled Energy-Efficient IoT Communications. IEEE Internet Things J. 2021, 8, 1322–1333. [Google Scholar] [CrossRef]
- Qin, Z.; Li, F.Y.; Li, G.Y.; McCann, J.A.; Ni, Q. Low-Power Wide-Area Networks for Sustainable IoT. IEEE Wirel. Commun. 2019, 26, 140–145. [Google Scholar] [CrossRef] [Green Version]
- Qi, F.; Zhu, X.; Mang, G.; Kadoch, M.; Li, W. UAV Network and IoT in the Sky for Future Smart Cities. IEEE Netw. 2019, 33, 96–101. [Google Scholar] [CrossRef]
- Zeng, Y.; Wu, Q.; Zhang, R. Accessing From the Sky: A Tutorial on UAV Communications for 5G and Beyond. Proc. IEEE 2019, 107, 2327–2375. [Google Scholar] [CrossRef] [Green Version]
- Wang, H.; Wang, J.; Chen, J.; Gong, Y.; Ding, G. Network-connected UAV communications: Potentials and challenges. China Commun. 2018, 15, 111–121. [Google Scholar]
- Wang, H.; Ding, G.; Gao, F.; Chen, J.; Wang, J.; Wang, L. Power Control in UAV-Supported Ultra Dense Networks: Communications, Caching, and Energy Transfer. IEEE Commun. Mag. 2018, 56, 28–34. [Google Scholar] [CrossRef] [Green Version]
- Lei, H.; Wang, D.; Park, K.H.; Ansari, I.S.; Jiang, J.; Pan, G.; Alouini, M.S. Safeguarding UAV IoT Communication Systems Against Randomly Located Eavesdroppers. IEEE Internet Things J. 2020, 7, 1230–1244. [Google Scholar] [CrossRef]
- Wang, Z.; Liu, R.; Liu, Q.; Thompson, J.S.; Kadoch, M. Energy-Efficient Data Collection and Device Positioning in UAV-Assisted IoT. IEEE Internet Things J. 2020, 7, 1122–1139. [Google Scholar] [CrossRef]
- Wang, J.; Jiang, C.; Wei, Z.; Pan, C.; Zhang, H.; Ren, Y. Joint UAV Hovering Altitude and Power Control for Space-Air-Ground IoT Networks. IEEE Internet Things J. 2019, 6, 1741–1753. [Google Scholar] [CrossRef]
- Gu, J.; Wang, H.; Ding, G.; Xu, Y.; Xue, Z.; Zhou, H. Energy-Constrained Completion Time Minimization in UAV-Enabled Internet of Things. IEEE Internet Things J. 2020, 7, 5491–5503. [Google Scholar] [CrossRef]
- Almasoud, A.M.; Kamal, A.E. Data Dissemination in IoT Using a Cognitive UAV. IEEE Trans. Cogn. Commun. Netw. 2019, 5, 849–862. [Google Scholar] [CrossRef]
- Xue, Z.; Wang, J.; Ding, G.; Zhou, H.; Wu, Q. Maximization of Data Dissemination in UAV-Supported Internet of Things. IEEE Wireless Commun. Lett. 2019, 8, 185–188. [Google Scholar] [CrossRef]
- Jung, H.; Nguyen, B.V.; Song, I.; Kim, K. Design of Anti-Jamming Waveforms for Time-Hopping Spread Spectrum Systems in Tone Jamming Environments. IEEE Trans. Veh. Technol. 2020, 69, 728–737. [Google Scholar] [CrossRef] [Green Version]
- Duan, B.; Yin, D.; Cong, Y.; Zhou, H.; Xiang, X.; Shen, L. Anti-Jamming Path Planning for Unmanned Aerial Vehicles with Imperfect Jammer Information. In Proceedings of the 2018 IEEE International Conference on Robotics and Biomimetics (ROBIO), Kuala Lumpur, Malaysia, 12–15 December 2018; pp. 729–735. [Google Scholar]
- Wang, H.; Chen, J.; Ding, G.; Sun, J. Trajectory Planning in UAV Communication with Jamming. In Proceedings of the 2018 10th International Conference on Wireless Communications and Signal Processing (WCSP), Hangzhou, China, 18–20 October 2018; pp. 1–6. [Google Scholar]
- Pang, X.; Zhao, N.; Tang, J.; Wu, C.; Niyato, D.; Wong, K.-K. IRS-Assisted Secure UAV Transmission via Joint Trajectory and Beamforming Design. IEEE Trans. Commun. 2022, 70, 1140–1152. [Google Scholar] [CrossRef]
- Wang, X.; Wang, J.; Xu, Y.; Chen, J.; Jia, L.; Liu, X.; Yang, Y. Dynamic Spectrum Anti-Jamming Communications: Challenges and Opportunities. IEEE Commun. Mag. 2020, 58, 79–85. [Google Scholar] [CrossRef]
- Xu, Y.; Ren, G.; Chen, J.; Luo, Y.; Jia, L.; Liu, X.; Xu, Y. A One-Leader Multi-Follower Bayesian-Stackelberg Game for Anti-Jamming Transmission in UAV Communication Networks. IEEE Access 2018, 6, 21697–21709. [Google Scholar] [CrossRef]
- Wang, H.; Wang, J.; Ding, G.; Xue, Z.; Zhang, L.; Xu, Y. Robust Spectrum Sharing in Air-Ground Integrated Networks: Opportunities and Challenges. IEEE Wirel. Commun. 2020, 27, 148–155. [Google Scholar] [CrossRef]
- Zhou, Y.; Zhou, F.; Zhou, H.; Ng, D.W.K.; Hu, R.Q. Robust Trajectory and Transmit Power Optimization for Secure UAV-Enabled Cognitive Radio Networks. IEEE Trans. Commun. 2020, 68, 4022–4034. [Google Scholar] [CrossRef]
- Wu, Y.; Fan, W.; Yang, W.; Sun, X.; Guan, X. Robust Trajectory and Communication Design for Multi-UAV Enabled Wireless Networks in the Presence of Jammers. IEEE Access 2020, 8, 2893–2905. [Google Scholar] [CrossRef]
- Gao, Y.; Wu, Y.; Cui, Z.; Chen, H.; Yang, W. Robust Design for Turning and Climbing Angle-Constrained UAV Communication Under Malicious Jamming. IEEE Commun. Lett. 2021, 25, 584–588. [Google Scholar] [CrossRef]
- Cui, M.; Zhang, G.; Wu, Q.; Ng, D.W.K. Robust Trajectory and Transmit Power Design for Secure UAV Communications. IEEE Trans. Veh. Technol. 2018, 67, 9042–9046. [Google Scholar] [CrossRef] [Green Version]
- Wang, H.; Wang, J.; Ding, G.; Chen, J.; Gao, F.; Han, Z. Completion Time Minimization With Path Planning for Fixed-Wing UAV Communications. IEEE Trans. Wirel. Commun. 2019, 18, 3485–3499. [Google Scholar] [CrossRef]
- Zeng, Y.; Zhang, R. Energy-efficient UAV communication with trajectory optimization. IEEE Trans. Wirel. Commun. 2017, 16, 3747–3760. [Google Scholar] [CrossRef] [Green Version]
- Wang, H.; Wang, J.; Ding, G.; Chen, J.; Li, Y.; Han, Z. Spectrum sharing planning for full-duplex UAV relaying systems with underlaid D2D communications. IEEE J. Sel. Areas Commun. 2018, 36, 1986–1999. [Google Scholar] [CrossRef]
- Zhang, S.; Zhang, H.; He, Q.; Bian, K.; Song, L. Joint trajectory and power optimization for UAV relay networks. IEEE Commun. Lett. 2018, 22, 161–164. [Google Scholar] [CrossRef]
- Zeng, Y.; Zhang, R.; Lim, T.J. Throughput maximization for UAV-enabled mobile relaying systems. IEEE Trans. Commun. 2016, 64, 4983–4996. [Google Scholar] [CrossRef]
- Wu, Q.; Zeng, Y.; Zhang, R. Joint trajectory and communication design for multi-UA V enabled wireless networks. IEEE Trans. Wirel. Commun. 2018, 17, 2109–2121. [Google Scholar] [CrossRef] [Green Version]
- Khuwaja, A.A.; Chen, Y.; Zhao, N.; Alouini, M.-S.; Dobbins, P. A Survey of Channel Modeling for UAV Communications. IEEE Commun. Surv. Tutor. 2018, 20, 2804–2821. [Google Scholar] [CrossRef] [Green Version]
- You, C.; Zhang, R. 3D Trajectory Optimization in Rician Fading for UAV-Enabled Data Harvesting. IEEE Trans. Wirel. Commun. 2019, 18, 3192–3207. [Google Scholar] [CrossRef]
- You, C.; Zhang, R. Hybrid Offline-Online Design for UAV-Enabled Data Harvesting in Probabilistic LoS Channels. IEEE Trans. Wirel. Commun. 2020, 19, 3753–3768. [Google Scholar] [CrossRef] [Green Version]
- Duo, B.; Wu, Q.; Yuan, X.; Zhang, R. Anti-Jamming 3D Trajectory Design for UAV-Enabled Wireless Sensor Networks under Probabilistic LoS Channel. IEEE Trans. Veh. Technol. 2020, 69, 16288–16293. [Google Scholar] [CrossRef]
- Zhan, C.; Yao, G. Energy Efficient Estimation in Wireless Sensor Network with Unmanned Aerial Vehicle. IEEE Access 2019, 7, 63519–63530. [Google Scholar] [CrossRef]
- Boyd, S.; Boyd, S.P.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Zhang, S.; Zeng, Y.; Zhang, R. Cellular-Enabled UAV Communication: A Connectivity-Constrained Trajectory Optimization Perspective. IEEE Trans. Commun. 2019, 67, 2580–2604. [Google Scholar] [CrossRef]
- Grant, M.; Boyd, S. CVX: Matlab Software for Disciplined Convex Programming, Version 1.21. December 2010. Available online: http://cvxr.com/cvx (accessed on 13 October 2022).






| Notation | Physical Meaning | Value |
|---|---|---|
| UAV minimum flight altitude | 50 m | |
| UAV maximum flight altitude | 150 m | |
| UAV maximum flight speed | 50 m/s | |
| Time slot | s | |
| Radius of the hemisphere | 30 m | |
| Jammer’s transmit power | W | |
| The K’s average transmit power | ||
| The K’s maximum transmit power | ||
| The power of AWGN | dBm/Hz | |
| The path loss at m | dB | |
| The accuracy tolerance | ||
| The LoS path loss exponent | ||
| The NLoS path loss exponent | ||
| Additional signal attenuation factor | dB |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ji, Z.; Gao, Y.; Yang, W.; Rong, C. Robust Trajectory and Resource Optimization in UAV-Enabled IoT Networks under Probabilistic LoS Channel in Presence of Jammers. Sensors 2023, 23, 70. https://doi.org/10.3390/s23010070
Ji Z, Gao Y, Yang W, Rong C. Robust Trajectory and Resource Optimization in UAV-Enabled IoT Networks under Probabilistic LoS Channel in Presence of Jammers. Sensors. 2023; 23(1):70. https://doi.org/10.3390/s23010070
Chicago/Turabian StyleJi, Zhi, Yufang Gao, Wendong Yang, and Chuanzhen Rong. 2023. "Robust Trajectory and Resource Optimization in UAV-Enabled IoT Networks under Probabilistic LoS Channel in Presence of Jammers" Sensors 23, no. 1: 70. https://doi.org/10.3390/s23010070





