Plant and Salamander Inspired Network Attack Detection and Data Recovery Model
Abstract
:1. Introduction
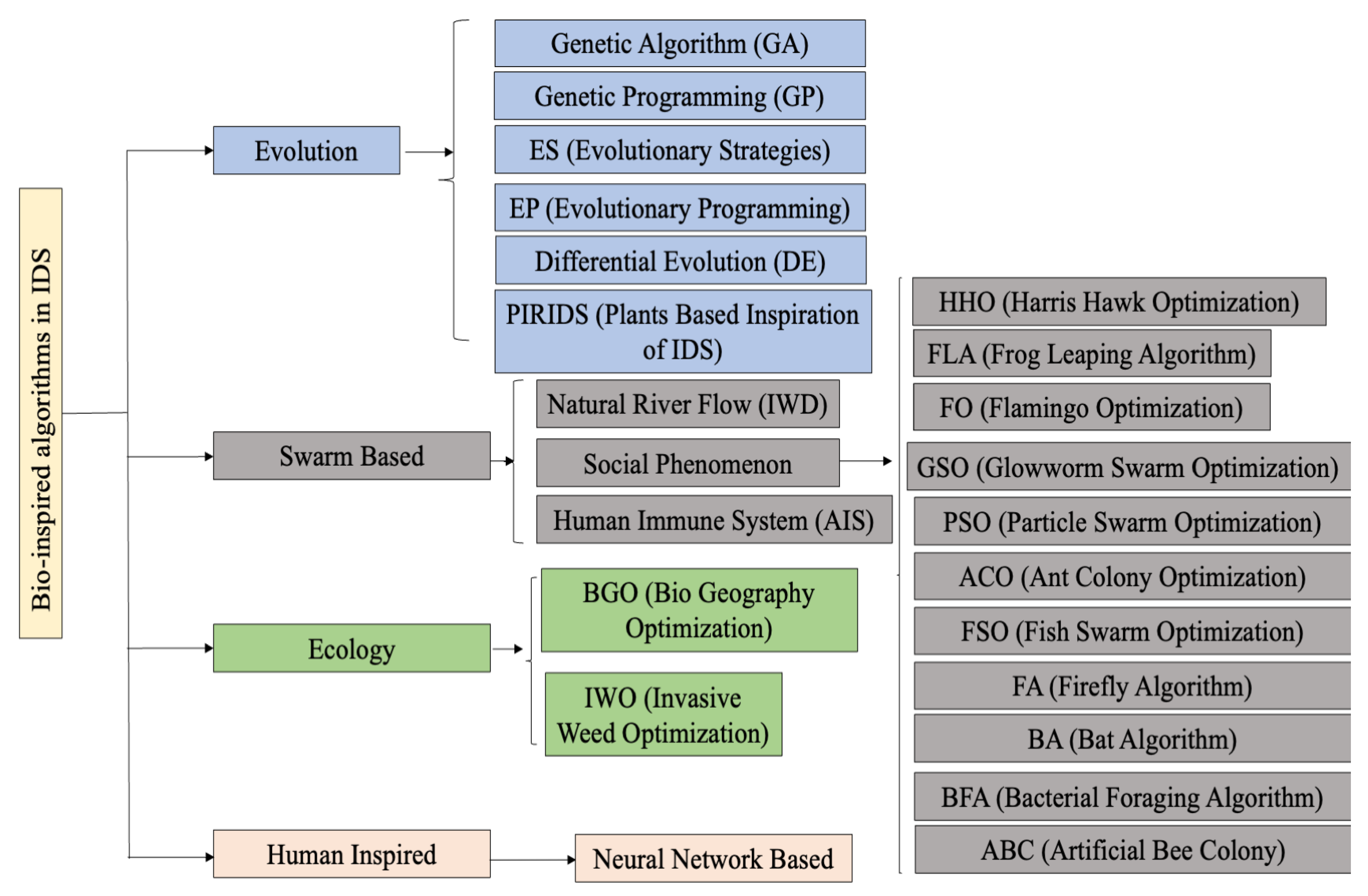
2. Related Work
2.1. Genetic Algorithm
2.2. Swarm-Based Algorithms
- Proximity Principle: This indicates the necessity and importance of the swarm agents to respond to even small variances in the environment and pass the information to other agents such that an overall response can be generated to the variance of the environment.
- Quality Principle: Consequence to responding to the variance in the environment, the members of the swarm should also ensure the quality of food, safety in location, proper path route towards the food source, etc.
- Principle of Diverse Response: Whenever there is an environmental change, the resources should be available to each swarm agent, and therefore, the resources should be distributed in such a manner prior.
- Principle of Stability: Each swarm agent should show deterrence to changes in its behavioral characteristics even when environmental conditions are fluctuating.
- Principle of Adaptability: When the mode of environment changes, the members of the swarm should be able to adapt to the new changes.
2.2.1. Ant Colony Optimization (ACO)
- Colony size (CS): This indicates the population of the ants within an ant colony.
- Indicates the number of iterations that occur until an optimal global tree is discovered.
- Indicates the factor by which pheromone evaporates for each entry in the pheromone matrix.
- J48—99.45%;
- Random Tree—99.83%;
- Random Forest—99.34%;
- JRIP—99.58%.
2.2.2. Particle Swarm Optimization (PSO)
2.2.3. Firefly Algorithm
- Unisex: One firefly is attracted to another, irrespective of sex.
- The attractiveness and the brightness are proportional. A less bright firefly always moves towards a brighter one.
- The objective function determines the brightness of a firefly.
2.3. Artificial Immune System Based IDS
3. Plant Defense Mechanism
Induced Systemic Resistance in Plants
4. Salamander Limb Regeneration
5. An Overview of IDS Taxonomy for Detection and Mitigation of Attacks in Network
6. Earlier Work and Motivation Forward
7. Proposed Model of Data Recovery Inspired from Salamander
7.1. Monitoring Agent
7.2. Backup Agent
7.3. Multicast Agent
| Algorithm 1: Proposed Method for Resources Recovery after Ransomware Attack |
 |
8. Understanding Data Recovery to a Ransomware-like Attack
9. Attack Detection Complexity of the Proposed Model
- is the threshold to consider a process malicious;
- is the point where the membership degree tends to rise significantly;
- .
10. Experimental Results and Analysis
- Linux systems with Ubuntu 16 OS.
- CPU Intel i5 processor.
- DLink Layer2 switch for the LAN network.
- 12 GB RAM.
- Python 2 and 3 for the program agents.
11. Data Recovery by the Proposed Model after Ransomware-like Attack
- HELLO message—used to multicast the node ID, this does not contain a recipient node ID.
- STORE message—used to notify a peer to be ready to receive backup files to store.
- GIVE message—used to fetch the critical resources backed up by the peers in the network.
12. Performance Comparison of the Recovery Model
Experiment Setup for Amanda and Burp
13. Time Complexity Analysis for PIRIDS Model
- Initialize all the receptor agents (SQL injection detector, Slowloris detector agent, syn flood detector agent, honeypot agent, ssh worm detector agent, Monitor agent).
- While all the agents are up and running, do:
- Receptor agents sniff incoming packets.
- The feature vector set of the sniffed packet is extracted.
- The fuzzy membership value of the extracted feature set is computed.
- The newly computed fuzzy value of the feature vector is added to its previous value.
- If the new fuzzy value exceeds a defined threshold, then action against the IP address corresponding to the feature vector set is taken and the fuzzy value of the feature vector is distributed to peers.
- If the threshold is not exceeded, then the fuzzy value of the feature vector is distributed to its peers so that their respective tables could be updated.
- Monitor agents monitor for the set of processes breaching receptor level detection and interacting with the CD.
- Fuzzy member of the process interacting with CD is computed and distributed to peers.
- The entropy of the files in CD is computed and if found a high file recovery process is initiated and the feature vector of the process is distributed to peers.
- If the number of files with high entropy is discovered, then the system is temporarily terminated from the network to stop further infection propagation.
- SQL injection detector: Here, every packet sniffed by the scapy-based sniffing agent is pushed to the parsing function as a parameter. Therefore, it is important to note that the processing is happening for every packet that goes inside the function independently. Inside the program, the HTTP header is extracted and split by the ‘referer’ tag. Once split and stored in a tuple, the tuple entries are searched for a host tag, and the corresponding host entry is parsed for SQL injection tags. The HTTP tag entry is also retrieved for verifying possible redirection to a malicious site. Once the full requested URL is retrieved, then it is searched for possible SQL injection patterns in the URL tag from the SQL injection set of patterns. The program, therefore, uses two iterative loops, one for iterating through the SQL injection set pattern and the other for iterating through the full URL of length ‘n’. The size of the URL pattern set is fixed as ‘k’. The time complexity is, therefore, or , where k is constant.
- Slowloris detector Agent: The Slowloris detector agent is responsible of detecting an incomplete HTTP header (i.e., non-terminating of HTTP header by \r \n \r \n). Here, the parsing of HTTP header data is done for every packet, and the number of fields in an HTTP header always remains fixed irrespective of the size of the HTTP packet. The Slowloris detector program has a time complexity of order , where ‘K’ is dependent on the number of a fixed amount of time instruction and is constant with respect to the input size.
- SYN flood detector Agent: The SYN flood detector agent is responsible for detecting the number of SYN requests arriving at the host in a given time window. The detector agent is programmed for every packet that has arrived to look for the TCP header and if present, it looks for the presence of SYN flag. This takes , where K is a constant. For ‘n’ number of packets arriving at the node at a given time window, the time complexity for processing TCP/UDP SYN flood is .
- Monitor Agent: The monitor agent is responsible for monitoring any malicious process breaching layer 1 defence and interacting with resources in the CD. Once identified the respective malicious program is terminated and if required file recovery is initiated. The input passed to the monitor agent is the file list of all the resources considered as critical. The fanotify of Linux is used to monitor any update on a file inside the CD. The monitor agent walks through the directories and sub-directories and then finally into the critical files of the directories. Therefore, this could have ‘n’ directories and ‘n’ files under each directory. The time complexity is therefore: .
14. Space Complexity Analysis for PIRIDS Model
15. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Demertzis, K.; Iliadis, L. A bio-inspired hybrid artificial intelligence framework for cybersecurity. In Computation, Cryptography, and Network Security; Springer: Berlin/Heidelberg, Germany, 2015; pp. 161–193. [Google Scholar]
- Thakkar, A.; Lohiya, R. Role of Swarm and evolutionary algorithms for intrusion detection system: A survey. In Swarm and Evolutionary Computation; Elseiver: Amsterdam, The Netherlands, 2019. [Google Scholar]
- Chen, Y.; Abraham, A.; Yang, B. Hybrid flexible neural- tree-based intrusion detection systems. Int. J. Intell. Syst. 2007, 22, 337–352. [Google Scholar] [CrossRef]
- Luo, J.; Bridges, S.M. Mining fuzzy association rules and fuzzy frequency episodes for intrusion detection. Int. Intell. Syst. 2000, 15, 687–703. [Google Scholar] [CrossRef]
- Neelima, D.; Karthik, J.; Aravind John, K.; Gowthami, S.; Nayak, J. Soft Computing-Based Intrusion Detection Approaches: An Analytical Study. In Soft Computing in Data Analytics; Springer: Singapore, 2019; pp. 635–651. [Google Scholar]
- Zhang, J.; Peng, S.; Gao, Y.; Zhang, Z.; Hong, Q. APMSA: Adversarial Perturbation Against Model Stealing Attacks. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1667–1679. [Google Scholar] [CrossRef]
- Wang, A.; Chang, W.; Chen, S.; Mohaisen, A. Delving into internet DDoS attacks by botnets: Characterization and analysis. IEEE/ACM Trans. Netw. 2018, 26, 2843–2855. [Google Scholar] [CrossRef]
- Abomhara, M.; Koien, G.M. Cyber security and the internet of things: Vulnerabilities, threats, intruders and attacks. J. Cyber Secur. Mobil. 2015, 4, 65–88. [Google Scholar] [CrossRef]
- Alqahtani, A.; Sheldon, F.T. A survey of crypto ransomware attack detection methodologies: An evolving outlook. Sensors 2022, 22, 1837. [Google Scholar] [CrossRef]
- Urooj, U.; Al-rimy, B.A.S.; Zainal, A.; Ghaleb, F.A.; Rassam, M.A. Ransomware detection using the dynamic analysis and machine learning: A survey and research directions. Appl. Sci. 2022, 12, 172. [Google Scholar] [CrossRef]
- Henry, C.; Grov, G.; Aspinall, D. Cbam: A contextual model for network anomaly detection. Computers 2021, 10, 79. [Google Scholar]
- Ferriyan, A.; Thamrin, A.H.; Takeda, K.; Murai, J. Generating network intrusion detection dataset based on real and encrypted synthetic attack traffic. Appl. Sci. 2021, 11, 7868. [Google Scholar] [CrossRef]
- Li, B.; Zhou, X.; Ning, Z.; Guan, X.; Yiu, K.F.C. Dynamic event-triggered security control for networked control systems with cyber-attacks: A model predictive control approach. Inf. Sci. 2022, 612, 384–398. [Google Scholar] [CrossRef]
- Zhang, X.; Wen, S.; Yan, L.; Feng, J.; Xia, Y. A Hybrid-Convolution Spatial—Temporal Recurrent Network For Traffic Flow Prediction. Comput. J. 2022. [Google Scholar] [CrossRef]
- Deeban, C.V.; Prakash, K.L.; Ramana, K.; Gadekallu, T.R. A Novel DDOS Attack Detection and Prevention Using DSA-DPI Method. In International Conference on Innovative Computing and Communications; Springer: Singapore, 2022; Volume 3, pp. 733–743. [Google Scholar]
- Shaikh, S.; Rupa, C.; Srivastava, G.; Gadekallu, T.R. Botnet Attack Intrusion Detection in IoT Enabled Automated Guided Vehicles. In Proceedings of the 2022 IEEE International Conference on Big Data (Big Data), Osaka, Japan, 17–20 December 2022; pp. 6332–6336. [Google Scholar]
- Yu, J.; Lu, L.; Chen, Y.; Zhu, Y.; Kong, L. An indirect eavesdropping attack of keystrokes on touch screen through acoustic sensing. IEEE Trans. Mob. Comput. 2019, 20, 337–351. [Google Scholar] [CrossRef]
- Cao, K.; Wang, B.; Ding, H.; Lv, L.; Tian, J.; Hu, H.; Gong, F. Achieving reliable and secure communications in wireless-powered NOMA systems. IEEE Trans. Veh. Technol. 2021, 70, 1978–1983. [Google Scholar] [CrossRef]
- Nejat, S.K.; Kabiri, P. An Adaptive and Cost-Based Intrusion Response System. Cybern. Syst. 2017, 48, 495–509. [Google Scholar] [CrossRef]
- Zonouz, S.A.; Khurana, H.; Sanders, W.H.; Yardley, T.M. RRE: A game-theoretic intrusion response and recovery engine. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 395–406. [Google Scholar] [CrossRef]
- Aslahi-Shahri, B.M.; Rahmani, R.; Chizari, M.; Maralani, A.; Eslami, M.; Golkar, M.J.; Ebrahimi, A. A hybrid method consisting of GA and SVM for intrusion detection system. Neural Comput. Appl. 2016, 27, 1669–1676. [Google Scholar] [CrossRef]
- Hashemi, V.M.; Muda, Z.; Yassin, W. Improving intrusion detection using genetic algorithm. Inf. Technol. J. 2013, 12, 2167–2173. [Google Scholar] [CrossRef] [Green Version]
- Chiba, Z.; Abghour, N.; Moussaid, K.; El Omri, A.; Rida, M. Intelligent approach to build a Deep Neural Network based IDS for cloud environment using combination of machine learning algorithms. Comput. Secur. 2019, 86, 291–317. [Google Scholar] [CrossRef]
- Badran, K.; Rohim, A. Genetic Programming Feature Extraction with Different Robust Classifiers for Network Intrusion Detection. Int. J. Comput. Appl. 2017, 168, 37–43. [Google Scholar] [CrossRef]
- Beni, G.; Wang, J. Swarm Intelligence in Cellular Robotic Systems. NATO Adv. Workshop Robot. Biol. Syst. 1989, 102, 703–712. [Google Scholar]
- Back, T.; Fogel, D.B.; Michalewicz, Z. Evolutionary Computation 1: Basic Algorithms and Operators; CRC Press: Boca Raton, FL, USA, 2018. [Google Scholar]
- Viegas, E.K.; Santin, A.O.; Oliveira, L.S. Toward a reliable anomaly-based intrusion detection in real-world environments. Comput. Netw. 2017, 127, 200–216. [Google Scholar] [CrossRef]
- Aghdam, M.H.; Kabiri, P. Feature Selection for Intrusion Detection System Using Ant Colony Optimization. Netw. Secur. 2016, 18, 420–432. [Google Scholar]
- Botes, F.H.; Leenen, L.; De La Harpe, R. Ant colony induced decision trees for intrusion detection. In Proceedings of the 16th European Conference on Cyber Warfare and Security, Dublin, Ireland, 29–30 June 2017. [Google Scholar]
- Varma, P.R.K.; Kumari, V.V.; Kumar, S.S. Feature selection using relative fuzzy entropy and ant colony optimization applied to real-time intrusion detection system. Procedia Comput. Sci. 2016, 85, 503–510. [Google Scholar] [CrossRef] [Green Version]
- Jones, J.D.G.; Dangl, J.L. The plant immune system. Nature 2006, 444, 323–329. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- El Bekri, M.; Diouri, O. Pso Based Intrusion Detection: A Pre-Implementation Discussion. Procedia Comput. Sci. 2019, 160, 837–842. [Google Scholar] [CrossRef]
- Ali, M.H.; Mohammed, B.A.D.A.; Ismail, A.; Zolkipli, M.F. A new intrusion detection system based on fast learning network and particle swarm optimization. IEEE Access 2018, 6, 20255–20261. [Google Scholar] [CrossRef]
- Aburomman, A.A.; Ibne Reaz, M.B. A novel SVM-kNN-PSO ensemble method for intrusion detection system. Appl. Soft Comput. 2016, 38, 360–372. [Google Scholar] [CrossRef]
- Yang, X.-S.; Karamanoglu, M. Swarm Intelligence and Bio-Inspired Computation: Theory and Applications; Elsevier: Amsterdam, The Netherlands, 2013. [Google Scholar]
- Selvakumar, B.; Muneeswaran, K. Firefly algorithm based feature selection for network intrusion detection. Comput. Secur. 2019, 81, 148–155. [Google Scholar]
- Al-Yaseen, W.L. Improving intrusion detection system by developing feature selection model based on firefly algorithm and support vector machine. IAENG Int. J. Comput. Sci. 2019, 46, 534–540. [Google Scholar]
- Arvinder, K.; Pal, S.K.; Singh, A.P. Hybridization of K-means and firefly algorithm for intrusion detection system. Int. J. Syst. Assur. Eng. Manag. 2018, 9, 901–910. [Google Scholar]
- Rana, N.F.; Dhannoon, B.N. A feature selection approach using binary firefly algorithm for network intrusion detection system. ARPN J. Eng. Appl. Sci. 2018, 13, 2347–2352. [Google Scholar]
- Saheed, Y.K. A Binary Firefly Algorithm Based Feature Selection Method on High Dimensional Intrusion Detection Data. In Illumination of Artificial Intelligence in Cybersecurity and Forensics; Springer: Cham, Switzerland, 2022; pp. 273–288. [Google Scholar]
- Bhattacharya, S.; S, S.R.K.; Maddikunta, P.K.R.; Kaluri, R.; Singh, S.; Gadekallu, T.R.; Alazab, M.; Tariq, U. A novel PCA-firefly based XGBoost classification model for intrusion detection in networks using GPU. Electronics 2020, 9, 219. [Google Scholar] [CrossRef] [Green Version]
- Almomani, O. A feature selection model for network intrusion detection system based on PSO, GWO, FFA and GA algorithms. Symmetry 2020, 12, 1046. [Google Scholar] [CrossRef]
- Shandilya, S.K.; Choi, B.J.; Kumar, A.; Upadhyay, S. Modified Firefly Optimization Algorithm-Based IDS for Nature-Inspired Cybersecurity. Processes 2023, 11, 715. [Google Scholar] [CrossRef]
- Phalguna, K.E.S.; Thangavelu, A. Attack detection in IoT devices using hybrid metaheuristic lion optimization algorithm and firefly optimization algorithm. Int. J. Syst. Assur. Eng. Manag. 2021. [Google Scholar] [CrossRef]
- Kim, J.; Bentley, P. The artificial immune model for network intrusion detection. In Proceedings of the 7th European Congress on Intelligent Techniques and Soft Computing (EUFIT’99), Aachen, Germany, 13–16 September 1999; Volume 158. [Google Scholar]
- Seresht, N.A.; Azmi, R. MAIS-IDS: A distributed intrusion detection system using multi-agent AIS approach. Eng. Appl. Artif. Intell. 2014, 35, 286–298. [Google Scholar] [CrossRef]
- Suliman, S.I.; Shukor, M.S.A.; Kassim, M.; Mohamad, R.; Shahbudin, S. Network intrusion detection system using artificial immune system (AIS). In Proceedings of the 3rd International Conference on Computer and Communication Systems (ICCCS), Nagoya, Japan, 27–30 April 2018. [Google Scholar]
- Maiti, S.; Basak, J.; Pal, A. Current understanding on plant r-genes/proteins and mechanisms of defence responses against biotic stresses. Rev. Plant Pathol. 2014, 6, 93–126. [Google Scholar]
- Sharma, R.K.; Issac, B.; Kalita, H.K. Intrusion detection and response system inspired by the defense mechanism of plants. IEEE Access 2019, 7, 52427–52439. [Google Scholar] [CrossRef]
- Spoel, S.H.; Dong, X. How do plants achieve immunity? defence without specialized immune cells. Nat. Rev. Immunol. 2012, 12, 89–100. [Google Scholar] [CrossRef]
- Parker, J.E. The quest for long-distance signals in plant systemic immunity. Sci. Signal. 2009, 2, 31. [Google Scholar] [CrossRef]
- Yokoyama, H. Initiation of limb regeneration: The critical steps for regenerative capacity. Dev. Growth Differ. 2007, 50, 13–22. [Google Scholar] [CrossRef] [PubMed]
- Verkerken, M.; D’hooge, L.; Wauters, T.; Volckaert, B.; Turck, F.D. Unsupervised Machine Learning Techniques for Network Intrusion Detection on Modern Data. In Proceedings of the 2020 4th Cyber Security in Networking Conference (CSNet), Lausanne, Switzerland, 21–23 October 2020; pp. 1–8. [Google Scholar] [CrossRef]
- Saheed, Y.K.; Abiodun, A.I.; Misra, S.; Holone, M.K.; Colomo-Palacios, R. A machine learning-based intrusion detection for detecting internet of things network attacks. Alex. Eng. J. 2022, 61, 9395–9409. [Google Scholar] [CrossRef]
- Ghosh, P.; Mitra, R. Proposed GA-BFSS and logistic regression based intrusion detection system. In Proceedings of the 2015 Third International Conference on Computer, Communication, Control and Information Technology (C3IT), Hooghly, India, 7–8 February 2015. [Google Scholar]
- Elham, B.; Naderan, M.; Namjoo, E. LR-HIDS: Logistic regression host-based intrusion detection system for cloud environments. J. Ambient. Intell. Humaniz. Comput. 2019, 10, 3669–3692. [Google Scholar]
- Amine, F.M.; Maglaras, L.; Ahmim, A.; Derdour, M.; Janicke, H. Rdtids: Rules and decision tree-based intrusion detection system for internet-of-things networks. Future Internet 2020, 12, 44. [Google Scholar]
- Kruegel, C.; Toth, T. Using decision trees to improve signature-based intrusion detection. In Proceedings of the Recent Advances in Intrusion Detection, Proceedings of the 6th International Symposium, RAID 2003, Pittsburgh, PA, USA, 8–10 September 2003; Proceedings 6. Springer: Berlin/Heidelberg, Germany, 2003. [Google Scholar]
- Li, W.; Yi, P.; Wu, Y.; Pan, L.; Li, J. A new intrusion detection system based on KNN classification algorithm in wireless sensor network. J. Electr. Comput. Eng. 2014, 2014, 240217. [Google Scholar] [CrossRef] [Green Version]
- Wazirali, R. An improved intrusion detection system based on KNN hyperparameter tuning and cross-validation. Arab. J. Sci. Eng. 2020, 45, 10859–10873. [Google Scholar] [CrossRef]
- Liao, Y.; Vemuri, V.R. Use of k-nearest neighbor classifier for intrusion detection. Comput. Secur. 2002, 21, 439–448. [Google Scholar] [CrossRef]
- Abu Al-Haija, Q.; Zein-Sabatto, S. An efficient deep-learning-based detection and classification system for cyber-attacks in IoT communication networks. Electronics 2020, 9, 2152. [Google Scholar] [CrossRef]
- Roy, B.; Cheung, H. A deep learning approach for intrusion detection in internet of things using bi-directional long short-term memory recurrent neural network. In Proceedings of the 2018 28th International Telecommunication Networks and Applications Conference (ITNAC), Sydney, Australia, 21–23 November 2018; pp. 1–6. [Google Scholar]
- Fioriti, V.; Chinnici, M. Node seniority ranking. arXiv 2014, arXiv:1402.6114. [Google Scholar]
- Brito, G.M. Molecular Mechanisms of Salamander Limb Regeneration. Ph.D. Thesis, Institutionen för Cell-Och Molekylärbiologi/Department of Cell and Molecular Biology, Stockholm, Sweden, 2018. [Google Scholar]
- Kok, S.; Abdullah†, A.; Jhanjhi, N.Z.; Supramaniam, M. Ransomware, Threat and Detection Techniques: A Review. Int. J. Comput. Sci. Netw. Secur. 2019, 19, 136–146. [Google Scholar]
- Grant, L.; Parkinson, S. Identifying File Interaction Patterns in Ransomware Behaviour. In Guide to Vulnerability Analysis for Computer Networks and Systems; Springer: Berlin/Heidelberg, Germany, 2018; pp. 317–335. [Google Scholar]
- Zurek, W.H. Complexity, Entropy and the Physics of Information; CRC Press: Boca Raton, FL, USA, 2018. [Google Scholar]
- Cui, W.; Kannan, J.; Wang, H.J. Discoverer: Automatic Protocol Reverse Engineering from Network Traces. In Proceedings of the USENIX Security Symposium, Boston, MA, USA, 6–10 August 2007; pp. 1–14. [Google Scholar]
- What Is WannaCry Ransomware? Available online: https://www.kaspersky.co.uk/resource-center/threats/ransomwarewannacry (accessed on 15 November 2022).
- Leyla, B.; Davide, B.; William, R.; Engin, K.; Christopher, K. Disclosure: Detecting botnet command and control servers through large-scale NetFlow analysis. In Proceedings of the 28th Annual Computer Security Applications Conference, Orlando, FL, USA, 3–7 December 2012; pp. 129–138. [Google Scholar]
- Abushwereb, M.; Mustafa, M.; Al-kasassbeh, M.; Qasaimeh, M. Attack based DoS attack detection using multiple classifier. arXiv 2020, arXiv:2001.05707. [Google Scholar]
- Gu, G.; Sharif, M.; Qin, X.; Dagon, D.; Lee, W.; Riley, G. Worm detection, early warning and response based on local victim information. In Proceedings of the 20th Annual Computer Security Applications Conference, Tucson, AZ, USA, 6–10 December 2004. [Google Scholar]
- Singh, S.; Estan, C.; Varghese, G.; Savage, S. Automated Worm Fingerprinting; University of California: San Diego, CA, USA, 2004. [Google Scholar]
- Valizadeh, S.; van Dijk, M. MalPro: A learning-based malware propagation and containment modeling. In Proceedings of the 2019 ACM SIGSAC Conference on Cloud Computing Security Workshop, London, UK, 11 November 2019. [Google Scholar]
- Singh, K.J.; De, T. An approach of ddos attack detection using classifiers. In Emerging Research in Computing, Information, Communication and Applications: ERCICA 2015; Springer: New Delhi, India, 2015; Volume 1. [Google Scholar]
- Xu, C.; Shen, J.; Du, X. Low-rate DoS attack detection method based on hybrid deep neural networks. J. Inf. Secur. Appl. 2021, 60, 102879. [Google Scholar] [CrossRef]
















| Criteria | ML and DL | Swarm and Evolutionary Algorithms |
|---|---|---|
| Working principle | Building a mapping between input and output | Finding an optimal solution from a set of population |
| Output | Trained Model | Optimal candidate solution |
| The goal of generalization | Aims at minimizing the computational cost of unseen data samples | Aims at minimizing the computational cost of known data samples |
| Applicability | Primarily used for classification, clustering, regression and feature extraction | Feature set and result optimization |
| Authors | Nature of Attack Detection | Response Time/Mechanism | Infection Spread/Accuracy of Detection |
|---|---|---|---|
| Abushwereb et al. [72] | Slowloris attack detection | Multiclass classification | 99.9% |
| Gu et al. [73] | Worm Spread | 15 min (average) | >1500 hosts |
| Singh et al. [74] | Worm Scan | 30 min | ∼1200 worm detection |
| Sharma et al. [49] | Worm Scan | 5 min (average) | <10 host |
| Valizadeh et al. [75] | Worm Scan | 15 min | <100 host |
| Singh et al. [76] | Slowloris attack detection | ML approach | 91.40% |
| Sharma et al. [49] | Slowloris attack detection | Time window based signature verification | 97% |
| Singh et al. [76] | Slowloris attack detection | Random Forest | 92% |
| Xu et al. [77] | Slowloris attack detection | Hybrid deep neural network | 93% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sharma, R.K.; Issac, B.; Xin, Q.; Gadekallu, T.R.; Nath, K. Plant and Salamander Inspired Network Attack Detection and Data Recovery Model. Sensors 2023, 23, 5562. https://doi.org/10.3390/s23125562
Sharma RK, Issac B, Xin Q, Gadekallu TR, Nath K. Plant and Salamander Inspired Network Attack Detection and Data Recovery Model. Sensors. 2023; 23(12):5562. https://doi.org/10.3390/s23125562
Chicago/Turabian StyleSharma, Rupam Kumar, Biju Issac, Qin Xin, Thippa Reddy Gadekallu, and Keshab Nath. 2023. "Plant and Salamander Inspired Network Attack Detection and Data Recovery Model" Sensors 23, no. 12: 5562. https://doi.org/10.3390/s23125562
APA StyleSharma, R. K., Issac, B., Xin, Q., Gadekallu, T. R., & Nath, K. (2023). Plant and Salamander Inspired Network Attack Detection and Data Recovery Model. Sensors, 23(12), 5562. https://doi.org/10.3390/s23125562









