Optimal ElGamal Encryption with Hybrid Deep-Learning-Based Classification on Secure Internet of Things Environment
Abstract
:1. Introduction
2. Literature Review
3. Materials and Methods
3.1. SMO Algorithm
3.2. Encryption Module
| Algorithm 1 Steps involved in SMO |
| Input: - Training dataset X with labels Y - Tolerance threshold tol - Regularization parameter C - Maximum number of iterations max_iter Initialize: - Lagrange multipliers alpha[i] = 0 for all i - Bias term b = 0 - Error cache E[i] = 0 for all i - Number of iterations iter = 0 while (iter < max_iter): num_changed_alphas = 0 for i in range(0, len(X)): E[i] = f(X[i]) − Y[i] // Calculate error for example i if ((Y[i] * E[i] < -tol and alpha[i] < C) or (Y[i] * E[i] > tol and alpha[i] > 0)): // Select the first Lagrange multiplier (alpha[i]) to optimize j = select_second_alpha(i, E) // Choose second Lagrange multiplier (alpha[j]) old_alpha_i = alpha[i] old_alpha_j = alpha[j] if (Y[i] != Y[j]): L = max(0, alpha[j] - alpha[i]) H = min(C, C + alpha[j] - alpha[i]) else: L = max(0, alpha[i] + alpha[j] - C) H = min(C, alpha[i] + alpha[j]) if (L == H): continue // Skip to next iteration eta = 2 * X[i].dot(X[j]) - X[i].dot(X[i]) - X[j].dot(X[j]) if (eta >= 0): continue // Skip to next iteration // Update Lagrange multipliers alpha[i] and alpha[j] alpha[j] = alpha[j] − (Y[j] * (E[i] − E[j])) / eta alpha[j] = clip_alpha(alpha[j], L, H) if (abs(alpha[j] − old_alpha_j) < 1 × 10−5): continue // Skip to next iteration alpha[i] = alpha[i] + Y[i] * Y[j] * (old_alpha_j − alpha[j]) // Update bias term b b1 = b - E[i] − Y[i] * (alpha[i] − old_alpha_i) * X[i].dot(X[i]) − Y[j] * (alpha[j] − old_alpha_j) * X[i].dot(X[j]) b2 = b − E[j] − Y[i] * (alpha[i] − old_alpha_i) * X[i].dot(X[j]) − Y[j] * (alpha[j] − old_alpha_j) * X[j].dot(X[j]) if (alpha[i] > 0 and alpha[i] < C): b = b1 elif (alpha[j] > 0 and alpha[j] < C): b = b2 else: b = (b1 + b2) / 2 E[i] = f(X[i]) − Y[i] // Update error cache E[i] E[j] = f(X[j]) − Y[j] // Update error cache E[j] num_changed_alphas = num_changed_alphas + 1 if (num_changed_alphas = = 0): iter = iter + 1 else: iter = 0 |
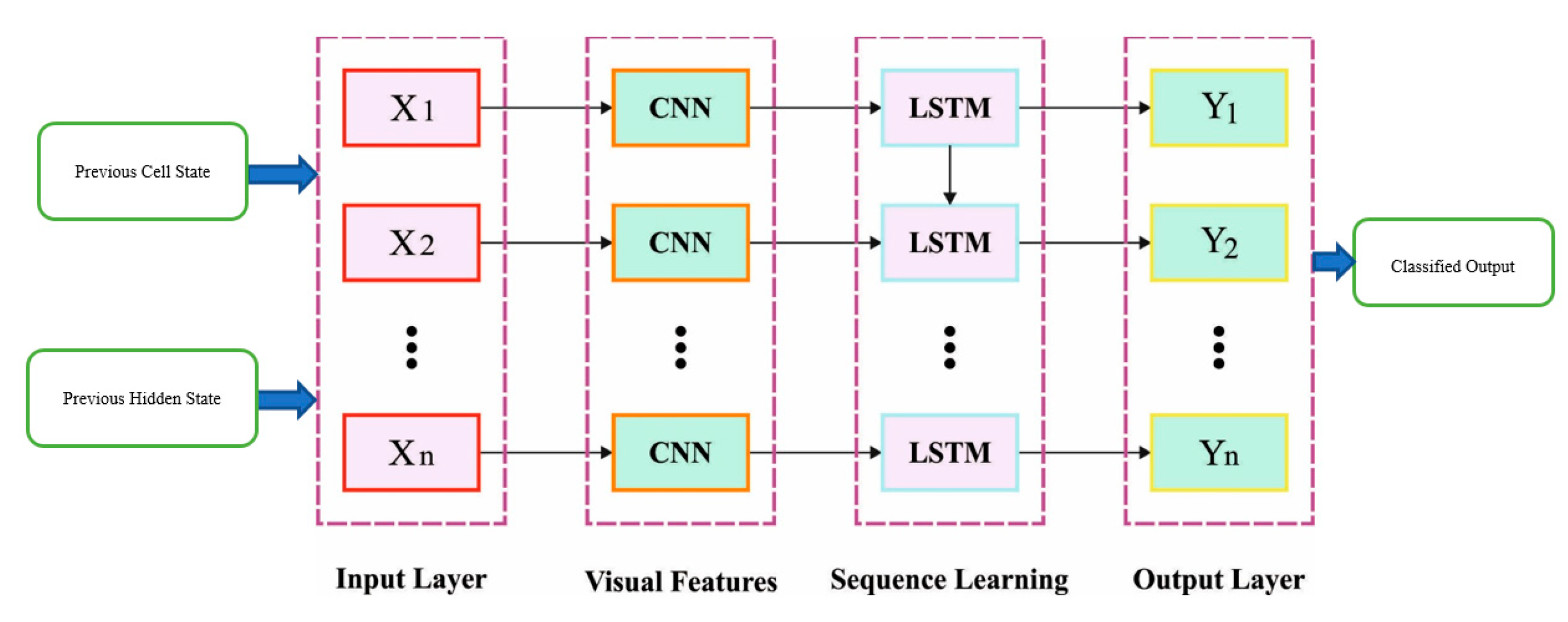
3.3. Data Classification Module
4. Results
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mehmood, M.S.; Shahid, M.R.; Jamil, A.; Ashraf, R.; Mahmood, T.; Mehmood, A. A comprehensive literature review of data encryption techniques in cloud computing and IoT environment. In Proceedings of the 8th International Conference on Information and Communication Technologies (ICICT), Karachi, Pakistan, 16–17 November 2019; pp. 54–59. [Google Scholar]
- Mann, P.; Tyagi, N.; Gautam, S.; Rana, A. Classification of Various Types of Attacks in IoT Environment. In Proceedings of the 2020 12th International Conference on Computational Intelligence and Communication Networks (CICN), Bhimtal, India, 25–26 September 2020; pp. 346–350. [Google Scholar]
- Shallal, Q.; Hussien, Z.; Abbood, A.A. Method to implement K-NN machine learning to classify data privacy in IoT environment. Indones. J. Electr. Eng. Comput. Sci. (IJEECS) 2020, 20, 985–990. [Google Scholar]
- Dar, Z.; Ahmad, A.; Khan, F.A.; Zeshan, F.; Iqbal, R.; Sherazi, H.H.R.; Bashir, A.K. A context-aware encryption protocol suite for edge computing-based IoT devices. J. Supercomput. 2020, 76, 2548–2567. [Google Scholar] [CrossRef]
- Li, D.; Cai, Z.; Deng, L.; Yao, X.; Wang, H.H. Information security model of block chain based on intrusion sensing in the IoT environment. Clust. Comput. 2019, 22, 451–468. [Google Scholar] [CrossRef]
- Li, X.; Li, J.; Yiu, S.; Gao, C.; Xiong, J. Privacy-preserving edge-assisted image retrieval and classification in IoT. Front. Comput. Sci. 2019, 13, 1136–1147. [Google Scholar] [CrossRef]
- Raj, J.S. A novel information processing in IoT based real time health care monitoring system. J. Electron. 2020, 2, 188–196. [Google Scholar]
- Ma, H.; Zhang, Z. A new private information encryption method in internet of things under cloud computing environment. Wirel. Commun. Mob. Comput. 2020, 2020, 8810987. [Google Scholar] [CrossRef]
- Savitha, V.; Karthikeyan, N.; Karthik, S.; Sabitha, R. A distributed key authentication and OKM-ANFIS scheme based breast cancer prediction system in the IoT environment. J. Ambient. Intell. Humaniz. Comput. 2020, 12, 1757–1769. [Google Scholar] [CrossRef]
- Elhoseny, M.; Shankar, K.; Lakshmanaprabu, S.K.; Maseleno, A.; Arunkumar, N. Hybrid optimization with cryptography encryption for medical image security in Internet of Things. Neural Comput. Appl. 2020, 32, 10979–10993. [Google Scholar] [CrossRef]
- Akhbarifar, S.; Javadi, H.H.S.; Rahmani, A.M.; Hosseinzadeh, M. A secure remote health monitoring model for early disease diagnosis in cloud-based IoT environment. Pers. Ubiquitous Comput. 2023, 27, 697–713. [Google Scholar] [CrossRef] [PubMed]
- Medileh, S.; Laouid, A.; Euler, R.; Bounceur, A.; Hammoudeh, M.; AlShaikh, M.; Eleyan, A.; Khashan, O.A. A flexible encryption technique for the internet of things environment. Ad. Hoc. Netw. 2020, 106, 102240. [Google Scholar] [CrossRef]
- Zhang, K.; Long, J.; Wang, X.; Dai, H.N.; Liang, K.; Imran, M. Lightweight searchable encryption protocol for industrial internet of things. IEEE Trans. Ind. Inform. 2020, 17, 4248–4259. [Google Scholar] [CrossRef]
- Kozik, R.; Pawlicki, M.; Choraś, M. A new method of hybrid time window embedding with transformer-based traffic data classification in IoT-networked environment. Pattern Anal. Appl. 2021, 24, 1441–1449. [Google Scholar] [CrossRef]
- Lee, G.Y.; Cha, K.J.; Kim, H.J. Designing the GDPR compliant consent procedure for personal information collection in the IoT environment. In Proceedings of the 2019 IEEE International Congress on Internet of Things (ICIOT), Milan, Italy, 8–13 July 2019; pp. 79–81. [Google Scholar]
- Fuchsbauer, G.; Plouviez, A.; Seurin, Y. Blind Schnorr signatures and signed ElGamal encryption in the algebraic group model. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Zagreb, Croatia, 10–14 May 2020; Springer: Cham, Switzerland, 2020; pp. 63–95. [Google Scholar]
- Zheng, R.; Jia, H.; Abualigah, L.; Liu, Q.; Wang, S. Deep ensemble of slime mold algorithm and arithmetic optimization algorithm for global optimization. Processes 2020, 9, 1774. [Google Scholar] [CrossRef]
- Yang, B.; Yin, K.; Lacasse, S.; Liu, Z. Time series analysis and long short-term memory neural network to predict landslide displacement. Landslides 2019, 16, 677–694. [Google Scholar] [CrossRef]
- Xiao, B.; Liu, Y.; Xiao, B. Accurate state-of-charge estimation approach for lithium-ion batteries by gated recurrent unit with ensemble optimizer. IEEE Access 2019, 7, 54192–54202. [Google Scholar] [CrossRef]
- Available online: http://archive.ics.uci.edu/ml/datasets/heart+disease (accessed on 1 April 2023).
- Kalyani, G.; Chaudhari, S. An efficient approach for enhancing security in Internet of Things using the optimum authentication key. Int. J. Comput. Appl. 2020, 42, 306–314. [Google Scholar] [CrossRef]
- Bhuvaneeswari, R.; Sudhakar, P.; Narmadha, R.P. Intelligent Heart Disease Diagnosis System Using Distance Based Outlier Detection with Gradient Tree Boosting Algorithm. Int. J. Sci. Technol. Res. 2019, 8, 2255–2274. [Google Scholar]
- LeCun, Y.; Bengio, Y.; Hinton, G. Deep learning. Nature 2015, 521, 436–444. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Al Nafea, R.; Almaiah, M.A. Cyber security threats in cloud: Literature review. In Proceedings of the 2021 International Conference on Information Technology (ICIT), Amman, Jordan, 14 July 2021; pp. 779–786. [Google Scholar]
- Kouicem, D.E.; Bouabdallah, A. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar]
- Roman, R.; Zhou, J.; Lopez, J. On the features and challenges of security and privacy in distributed Internet of Things. Comput. Netw. 2013, 57, 2266–2279. [Google Scholar] [CrossRef]
- Krishnaraj, N.; Elhoseny, M.; Thenmozhi, M.; Selim, M.M.; Shankar, K. Deep learning model for real-time image compression in Internet of Underwater Things (IoUT). J. Real-Time Image Process. 2020, 17, 2097–2111. [Google Scholar] [CrossRef]
- Krichen, M.; Mihoub, A.; Alzahrani, M.Y.; Adoni, W.Y.H.; Nahhal, T. Are Formal Methods Applicable to Machine Learning And Artificial Intelligence? In Proceedings of the 2022 2nd International Conference of Smart Systems and Emerging Technologies (SMARTTECH), Riyadh, Saudi Arabia, 9–11 May 2022; pp. 48–53. [Google Scholar]
- Raman, R.; Gupta, N.; Jeppu, Y. Framework for Formal Verification of Machine Learning Based Complex System-of-Systems. Insight 2023, 26, 91–102. [Google Scholar] [CrossRef]

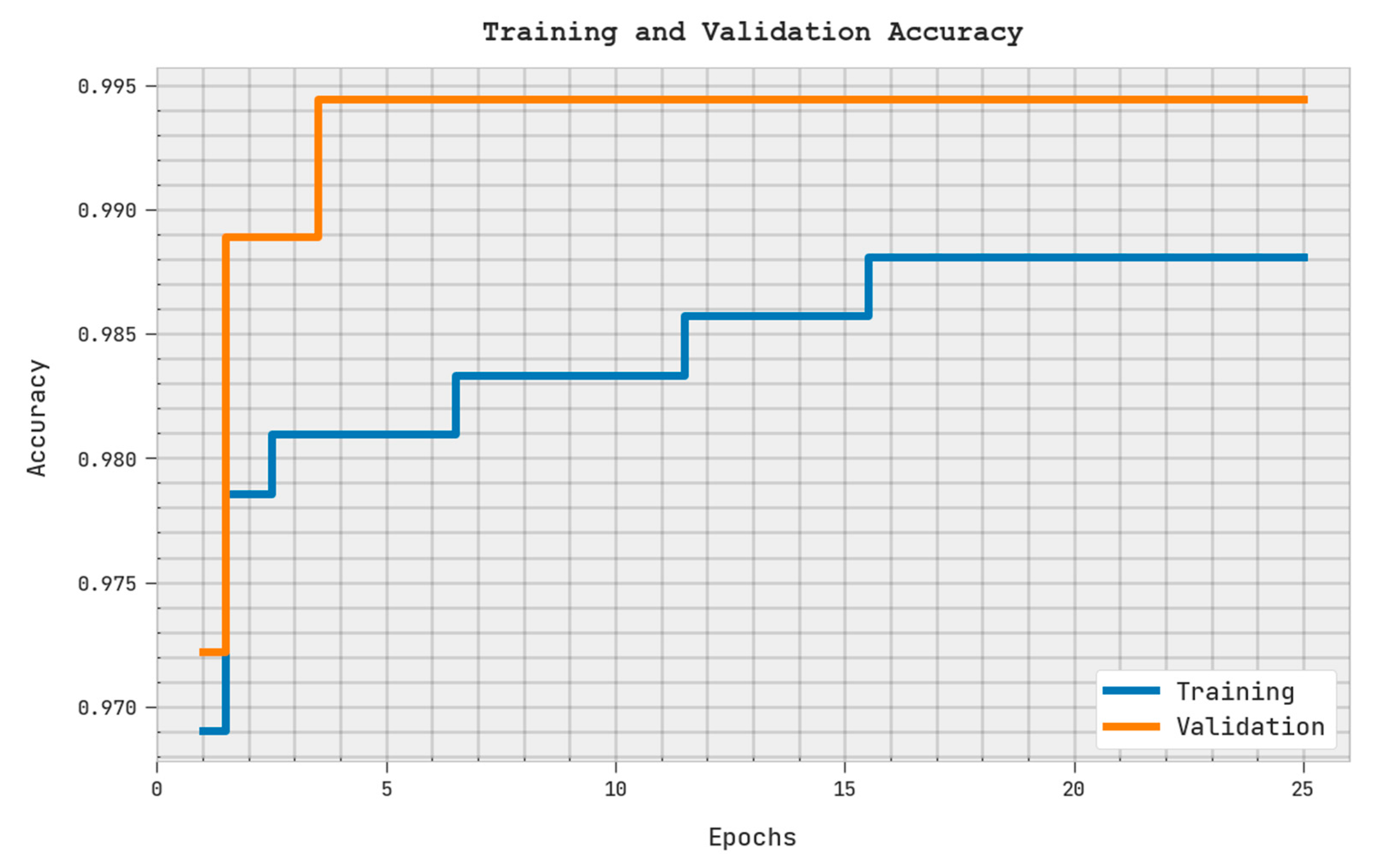
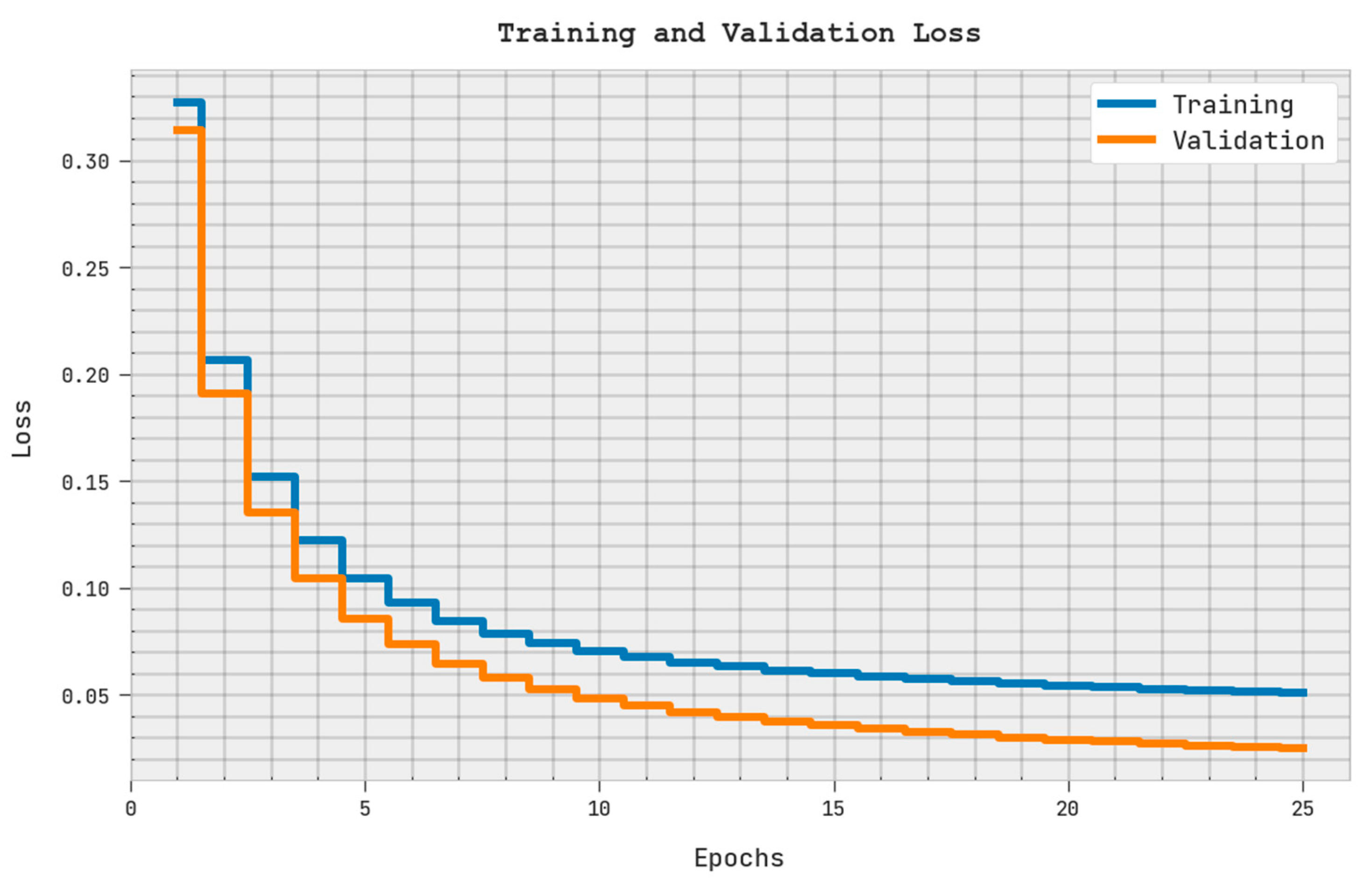
| File Size (kb) | Encryption Time (sec) | Encryption Memory (kb) | Key Size (kb) | Key Breaking Time (ms) | Decryption Time (sec) | Decryption Memory (kb) |
|---|---|---|---|---|---|---|
| 10 | 448.00 | 1110.00 | 44.00 | 116.00 | 72.00 | 645.00 |
| 20 | 490.00 | 1168.00 | 46.00 | 111.00 | 70.00 | 647.00 |
| 30 | 503.00 | 1126.00 | 60.00 | 114.00 | 73.00 | 641.00 |
| 40 | 494.00 | 1117.00 | 72.00 | 116.00 | 75.00 | 674.00 |
| 50 | 507.00 | 1188.00 | 77.00 | 110.00 | 85.00 | 679.00 |
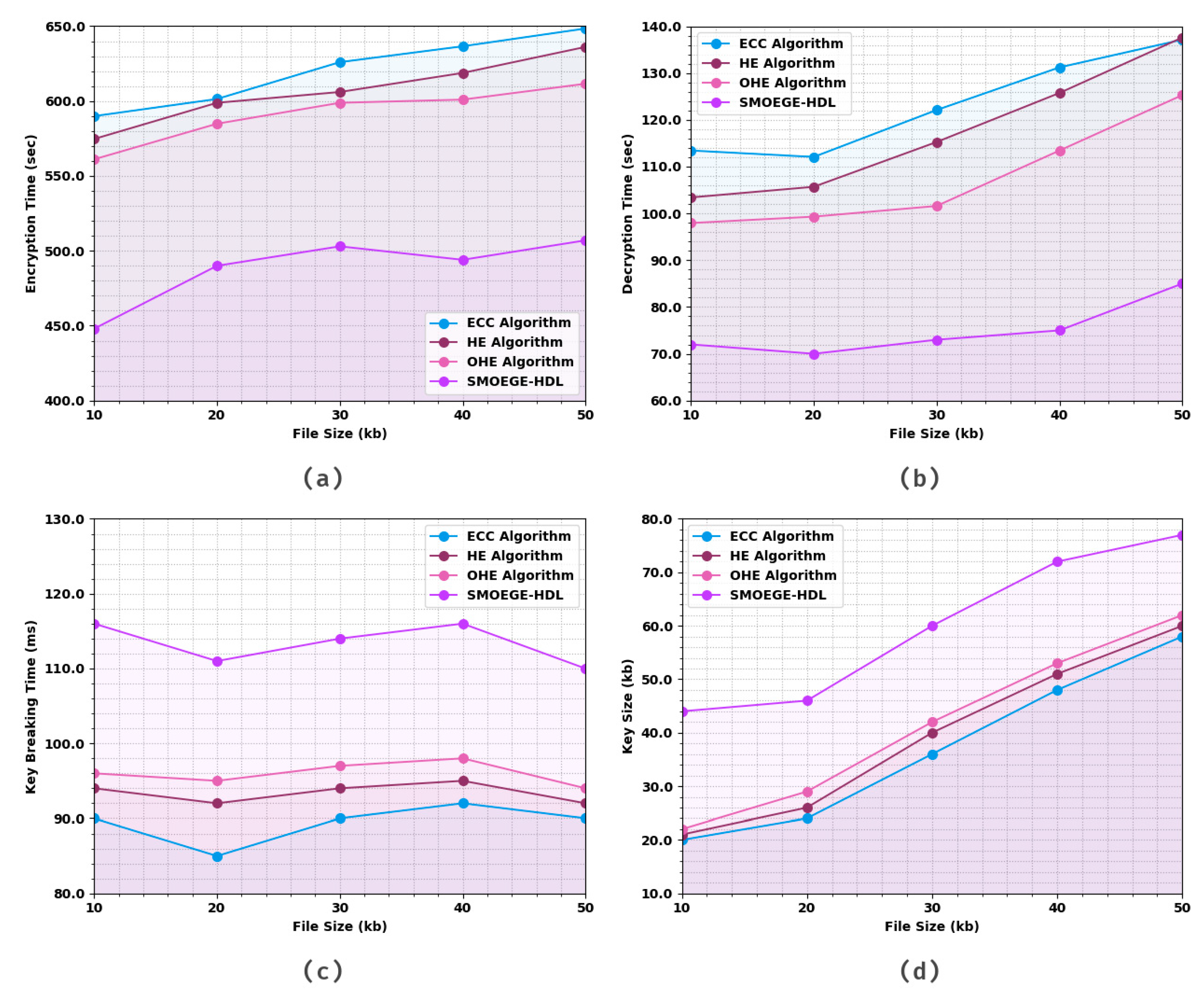
| Encryption Time (s) | ||||
|---|---|---|---|---|
| File Size (kb) | ECC Algorithm | HE Algorithm | OHE Algorithm | SMOEGE-HDL |
| 10 | 589.958 | 574.692 | 561.121 | 448.00 |
| 20 | 601.409 | 598.864 | 584.87 | 490.00 |
| 30 | 626.005 | 606.073 | 598.864 | 503.00 |
| 40 | 636.607 | 618.796 | 600.985 | 494.00 |
| 50 | 648.481 | 636.183 | 611.586 | 507.00 |
| Decryption Time (s) | ||||
| File Size (kb) | ECC Algorithm | HE Algorithm | OHE Algorithm | SMOEGE-HDL |
| 10 | 113.433 | 103.408 | 97.940 | 72.00 |
| 20 | 112.066 | 105.687 | 99.307 | 70.00 |
| 30 | 122.091 | 115.256 | 101.586 | 73.00 |
| 40 | 131.205 | 125.737 | 113.433 | 75.00 |
| 50 | 137.129 | 137.584 | 125.281 | 85.00 |
| Key Breaking Time (ms) | ||||
| File Size (kb) | ECC Algorithm | HE Algorithm | OHE Algorithm | SMOEGE-HDL |
| 10 | 90.00 | 94.00 | 96.00 | 116.00 |
| 20 | 85.00 | 92.00 | 95.00 | 111.00 |
| 30 | 90.00 | 94.00 | 97.00 | 114.00 |
| 40 | 92.00 | 95.00 | 98.00 | 116.00 |
| 50 | 90.00 | 92.00 | 94.00 | 110.00 |
| Key Size (kb) | ||||
| File Size (kb) | ECC Algorithm | HE Algorithm | OHE Algorithm | SMOEGE-HDL |
| 10 | 20.00 | 21.00 | 22.00 | 44.00 |
| 20 | 24.00 | 26.00 | 29.00 | 46.00 |
| 30 | 36.00 | 40.00 | 42.00 | 60.00 |
| 40 | 48.00 | 51.00 | 53.00 | 72.00 |
| 50 | 58.00 | 60.00 | 62.00 | 77.00 |
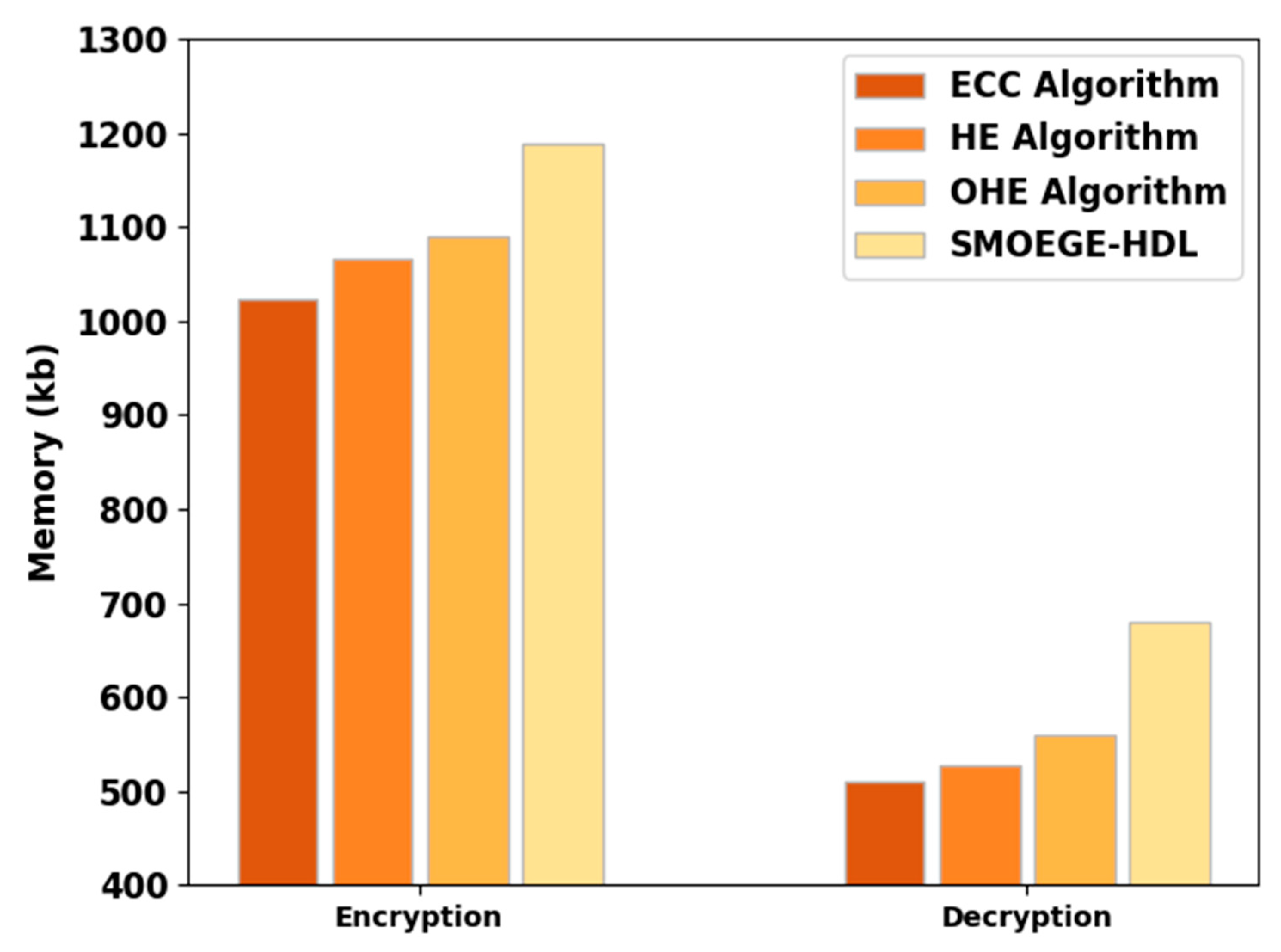
| Memory (kb) | ||
|---|---|---|
| Methods | Encryption | Decryption |
| ECC Algorithm | 1022.26 | 510.294 |
| HE Algorithm | 1066.54 | 526.898 |
| OHE Algorithm | 1088.68 | 560.106 |
| SMOEGE-HDL | 1188.00 | 679.000 |
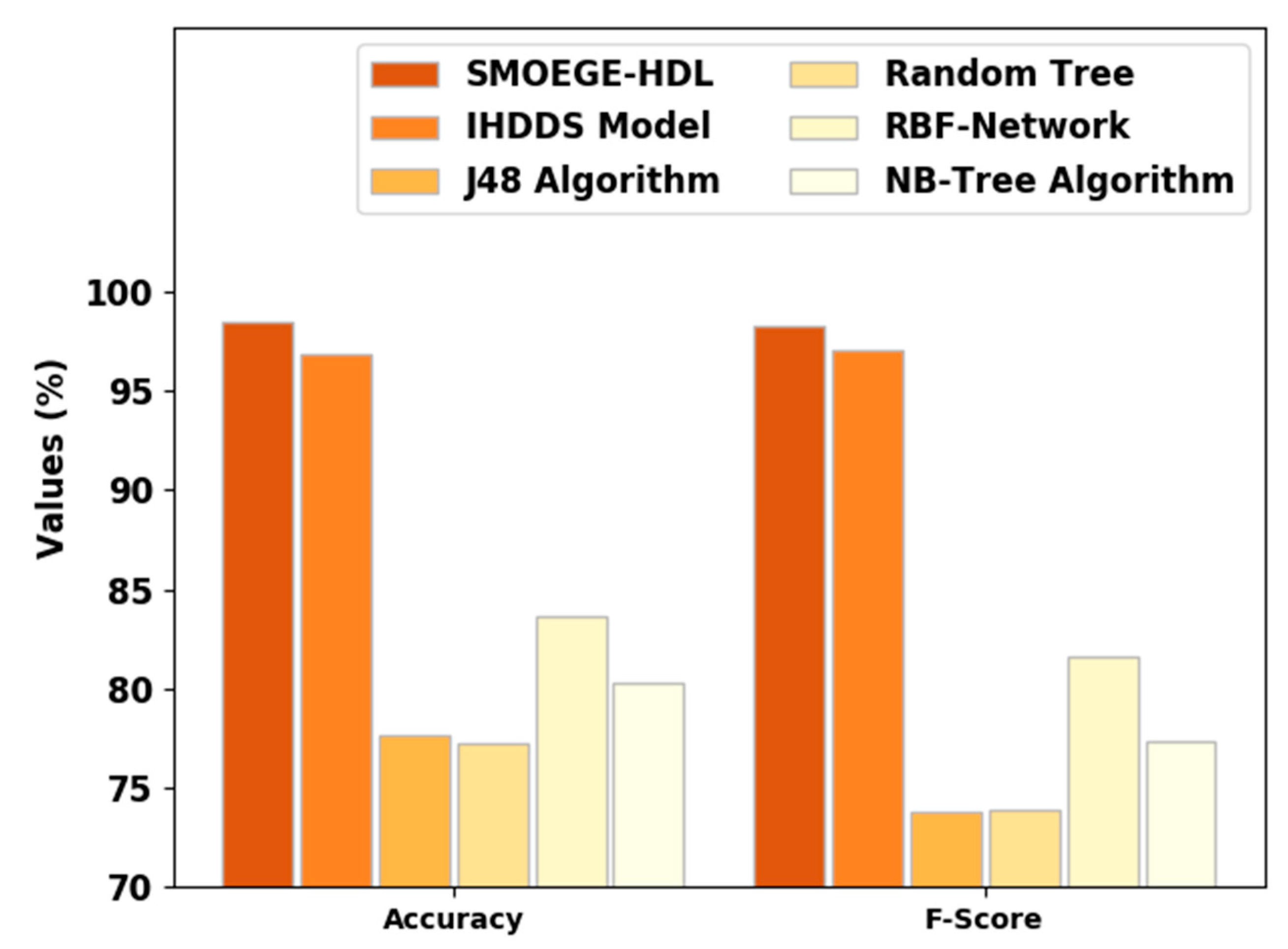
| Classifiers | Specificity | Precision | Recall | Accuracy | F-Score |
|---|---|---|---|---|---|
| SMOEGE-HDL | 98.50 | 98.75 | 98.30 | 98.50 | 98.25 |
| IHDDS Model | 95.23 | 95.78 | 97.03 | 96.81 | 97.06 |
| J48 Algorithm | 79.18 | 74.18 | 72.83 | 77.65 | 73.81 |
| Random Tree | 78.00 | 73.08 | 73.93 | 77.20 | 73.92 |
| RBF-Network | 85.01 | 81.80 | 82.48 | 83.62 | 81.58 |
| NB-Tree Algorithm | 79.72 | 75.77 | 79.38 | 80.28 | 77.31 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Annamalai, C.; Vijayakumaran, C.; Ponnusamy, V.; Kim, H. Optimal ElGamal Encryption with Hybrid Deep-Learning-Based Classification on Secure Internet of Things Environment. Sensors 2023, 23, 5596. https://doi.org/10.3390/s23125596
Annamalai C, Vijayakumaran C, Ponnusamy V, Kim H. Optimal ElGamal Encryption with Hybrid Deep-Learning-Based Classification on Secure Internet of Things Environment. Sensors. 2023; 23(12):5596. https://doi.org/10.3390/s23125596
Chicago/Turabian StyleAnnamalai, Chinnappa, Chellavelu Vijayakumaran, Vijayakumar Ponnusamy, and Hyunsung Kim. 2023. "Optimal ElGamal Encryption with Hybrid Deep-Learning-Based Classification on Secure Internet of Things Environment" Sensors 23, no. 12: 5596. https://doi.org/10.3390/s23125596






