Hash and Physical Unclonable Function (PUF)-Based Mutual Authentication Mechanism
Abstract
1. Introduction
2. Related Work
3. Kulseng’s Mutual Authentication Protocol
4. Proposed Mutual Authentication Mechanism
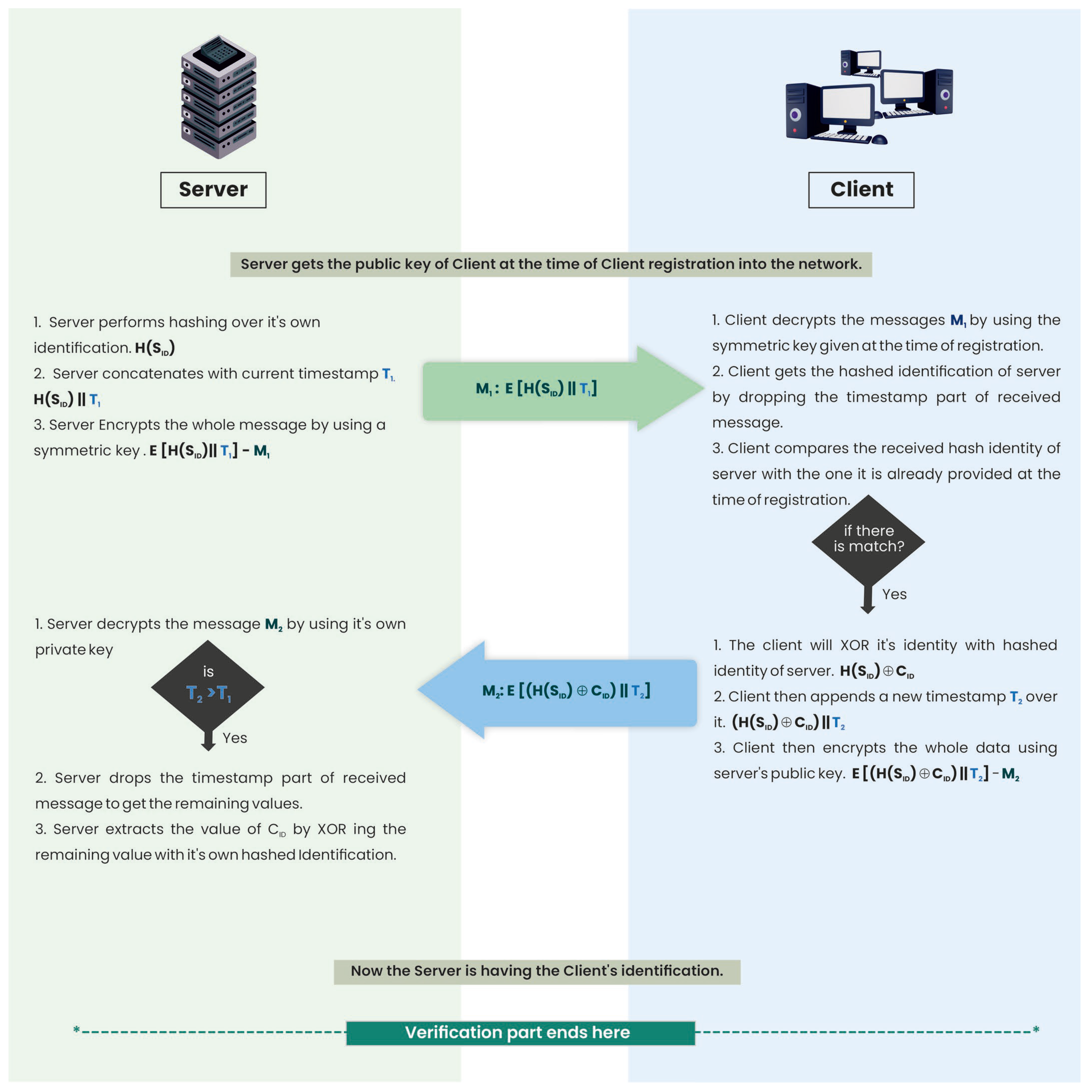
4.1. Server Verification
- The server performs hashing over its identity H(SID) and attaches the current timestamp, T1, to it. Then, it encrypts all the data with a symmetric key shared with the client at the time of registration.
- The server then sends the first message to the client: M1 = E[H(SID)||T1].
- The client then decrypts the whole message, M1, by using the symmetric key given to it at the time of registration. It gets the hashed identification of the server by dropping the timestamp part of the received message.
- The client compares the received H(SID) with the one it already has.
- If it is a match, the server is verified; otherwise, it is not verified.
4.2. Client Verification
- The client performs the XOR operation on its own identity, CID, along with the hashed identity of the server, H(SID). It then attaches a new timestamp, T2, to this message. The client encrypts the whole message with the server’s public key, which is broadcast to all the clients on a regular basis.
- The client then sends a second message to the server: M2 = E[(H(SID)⊕CID)||T2].
- At the server end, the first check is on the timestamp. It will check if the current timestamp is greater than the one the server sent to the client earlier: T2 > T1.
- The server then decrypts the whole message by using its private key.
- It drops the timestamp part of M2 to get the message part. The server then extracts the client identification, CID, from (CID⊕H(SID)) by XORing it with its own hashed identity, H(SID).
- The server asks the DB about CID. If there is a match, the client is verified; otherwise, it is not verified.
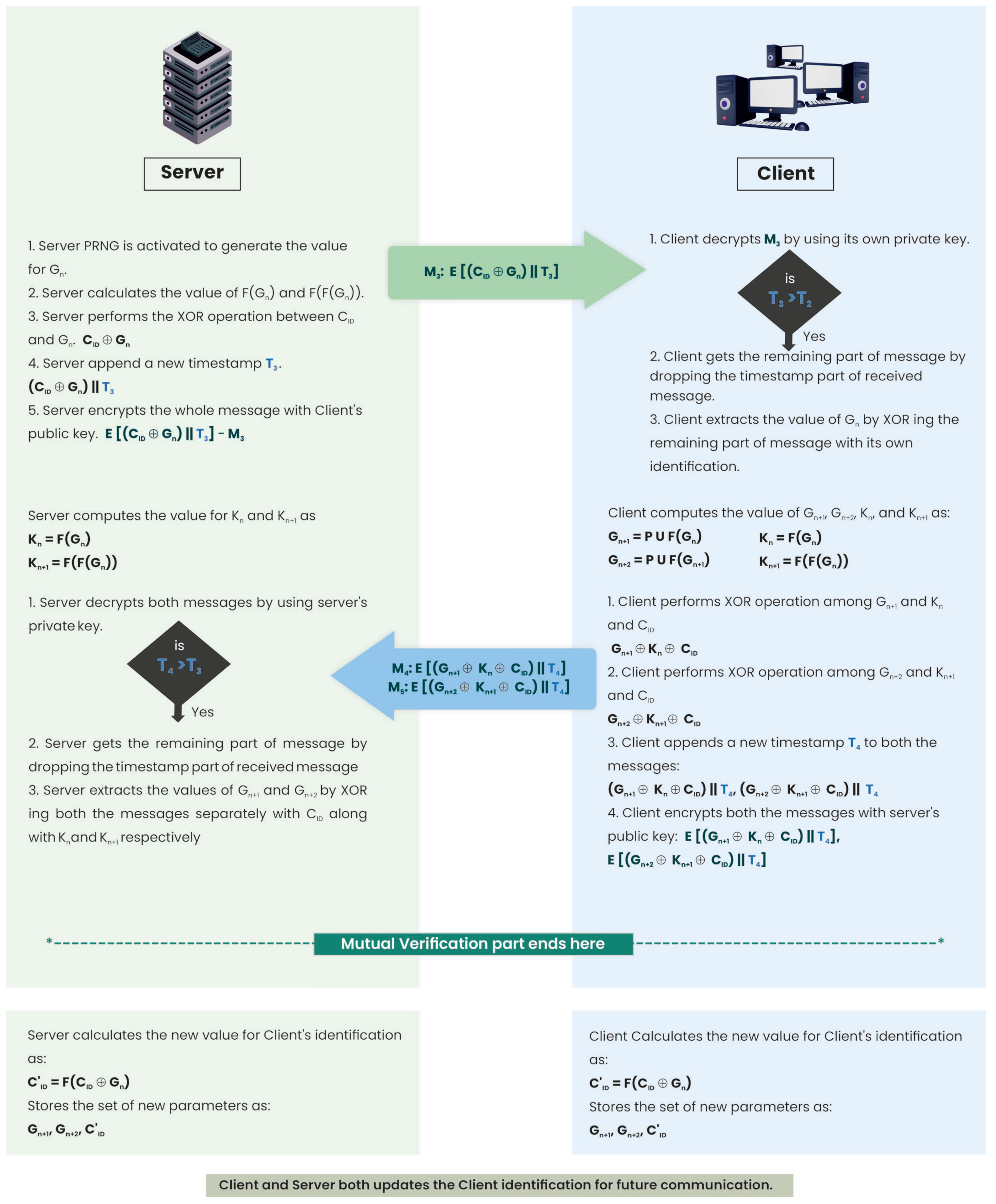
4.3. Mutual Authentication
- The server activates the PRNG unit to generate the value, Gn.
- The server performs an XOR between CID and Gn, then appends a new timestamp, T3, and encrypts the entire message with the client’s public key.
- It sends message M3 to the client: M3: E[(CID⊕Gn)||T3].
- The client first checks the timestamp. If T3 > T2 only then does it decrypt the entire message using its own private key.
- The client drops the timestamp field to get the original message. It then extracts the value of Gn by performing (CID⊕Gn)⊕CID.
- The server computes F(Gn) and F(F(Gn)), while the client simultaneously computes Gn+1 = PUF(Gn), Gn+2 = PUF(Gn+1), Kn = F(Gn), and Kn+1 = F(F(Gn)).
- The client performs the XOR operation between Gn+1 and Kn and CID: Gn+1⊕Kn⊕CID.
- The client performs a second XOR operation between Gn+2 and Kn+1 and CID: Gn+2⊕Kn+1⊕CID.
- The client then appends a new timestamp, T4, to both messages.
- It then encrypts them with the server’s public key: E[(Gn+1⊕Kn⊕CID)||T4], E[(Gn+2⊕Kn+1⊕CID)||T4].
- The client sends M4 and M5 to the server.
- The server first checks the new timestamp. If T4 > T3, only then will the server decrypt both messages. It then drops the timestamp part to get the original message. The server extracts the values of Gn+1 and Gn+2 by the following operations: (Gn+1⊕Kn⊕CID)⊕F(Gn⊕CID) and (Gn+2⊕Kn+1⊕CID)⊕F(F(Gn)⊕CID).
- The client and server simultaneously update the client identification, C′ID, by F(CID⊕Gn).
- They both store the set of new parameters as: Gn+1, Gn+2, and C′ID.
5. System Model
6. Security Evaluation of the Proposed Mechanism
6.1. Informal Analysis
6.1.1. Traceability Attack
6.1.2. Secret Disclosure Attack
6.1.3. Impersonation Attack
6.1.4. DDoS Attack
6.1.5. Desynchronization Attack
6.1.6. Forward/Backward Secrecy
6.2. Formal Analysis
7. Complexity Analysis
8. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
- hashfunction h;
- const xor:Function;
- const con:Function;
- const puf:Function;
- const enc:Function;
- secret ID;
- secret CID;
- secret SID;
- macro M1 = E[h(SID)||T1];
- macro M2 = E[(h(SID) xor CID)||T2];
- macro M3 = E[(CID xor Gn)||T3];
- macro M4 = E[(Gn + 1 xor Kn xor CID)||T4];
- macro M5 = E[(Gn + 2 xor Kn + 1 xor CID)T4];
- protocol improved(C,S){
- role S{
- secret Gn;
- secret CID;
- secret SID;
- secret ID;
- fresh Ti;
- send_1(M1: E[H(SID)||T1]);
- recv_2(M2: E[(H(SID) ⊕ CID)||T2]);
- send_3(M3: E[(CID ⊕ Gn)||T3]);
- recv_4(M4: E[(Gn + 1 ⊕ Kn ⊕ CID)||T4]);
- recv_5(M5: E[(Gn + 2 ⊕ Kn + 1 ⊕ CID)||T4]);
- claim(S,Secret,ID);
- claim(S,Tiagree);
- claim(S,Gnsynch);
- claim(S,Alive);
- claim(S,Weakagree);
- }
- role C{
- fresh Ti;
- secret Gn;
- secret CID;
- secret SID;
- secret ID;
- recv_1(M1: E[H(SID)||T1]);
- send_2(M2: E[(H(SID) ⊕ CID)||T2]);
- recv_3(M3: E[(CID ⊕ Gn)||T3]);
- send_4(M4: E[(Gn + 1 ⊕ Kn ⊕ CID)||T4]);
- send_5(M5: E[(Gn + 2 ⊕ Kn + 1 ⊕ CID)||T4]);
- claim(C,Secret,SID);
- claim(C,Tiagree);
- claim(C,Gnsynch);
- claim(C,Alive);
- claim(C,Weakagree);
- }
- }
References
- Shao, X.; Guo, Y.; Guo, Y. A PUF-based anonymous authentication protocol for wireless medical sensor networks. Wirel. Netw. 2022, 28, 3753–3770. [Google Scholar] [CrossRef]
- Zerrouki, F.; Ouchani, S.; Bouarfa, H. PUF-based mutual authentication and session key establishment protocol for IoT devices. J. Ambient Intell. Humaniz. Comput. 2022, 1–19. [Google Scholar] [CrossRef]
- OWASP Top 10 API Security Risks—2023. Available online: https://owasp.org/API-Security/editions/2023/en/0x11-t10/ (accessed on 18 June 2023).
- Abdolinezhad, S.; Sikora, A. A Lightweight Mutual Authentication Protocol Based on Physical Unclonable Functions. In Proceedings of the 2022 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 27–30 June 2022; pp. 161–164. [Google Scholar]
- Li, T.; Liu, Y.; Ning, J. SDRLAP: A secure lightweight RFID mutual authentication protocol based on PUF with strong desynchronization resistance. Peer-to-Peer Netw. Appl. 2023, 1–16. [Google Scholar] [CrossRef]
- API2:2023 Broken Authentication. Available online: https://owasp.org/API-Security/editions/2023/en/0xa2-broken-authentication/ (accessed on 18 June 2023).
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G. On the indifferentiability of the sponge construction. In Proceedings of the Advances in Cryptology–EUROCRYPT 2008: 27th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Istanbul, Turkey, 13–17 April 2008. [Google Scholar]
- Gupta, D.N.; Kumar, R. DeeR-Hash: A lightweight hash construction for Industry 4.0/IoT. J. Sci. Ind. Res. 2023, 82, 142–150. [Google Scholar]
- Ravikanth, P.S. Physical One-Way Functions. Ph.D. Thesis, Department Media Arts Sciences, Massachusetts Institute Technology, Cambridge, MA, USA, 2001. [Google Scholar]
- Suh, G.E.; Devadas, S. Physical unclonable functions for device authentication and secret key generation. In Proceedings of the 44th Annual Design Automation Conference (DAC), San Diego, CA, USA, 4–8 June 2007; pp. 9–14. [Google Scholar]
- Maes, R.; Verbauwhede, I. Physically unclonable functions: A study on the state of the art and future research directions. In Towards Hardware-Intrinsic Security; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]
- Gassend, B.; Clarke, D.; Van Dijk, M.; Devadas, S. Silicon physical random functions. In Proceedings of the 9th ACM Conference on Computer and Communications Security (CCS), Washington, DC, USA, 18–22 November 2002; pp. 148–160. [Google Scholar]
- Yin, C.-E.; Qu, G.; Zhou, Q. Design and implementation of a group based RO PUF. In Proceedings of the 2013 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 18–22 March 2013; pp. 416–421. [Google Scholar]
- Holcomb, D.E.; Burleson, W.P.; Fu, K. Power-up SRAM state as an identifying fingerprint and source of true random numbers. IEEE Trans. Comput. 2009, 58, 1198–1210. [Google Scholar] [CrossRef]
- Hein, D.; Wolkerstorfer, J.; Felber, N. ECC is ready for RFID—A proof in silicon. In Selected Areas in Cryptography (Lecture Notes in Computer Science); Springer: Berlin/Heidelberg, Germany, 2009; Volume 5381, pp. 401–413. [Google Scholar]
- Hutter, M.; Feldhofer, M.; Plos, T. An ECDSA processor for RFID authentication. In Radio Frequency Identification: Security and Privacy Issues (Lecture Notes in Computer Science); Springer: Berlin/Heidelberg, Germany, 2010; Volume 6370, pp. 189–202. [Google Scholar]
- Avoine, G.; Bingol, M.A.; Carpent, X.; Yalcin, S.B.O. Privacyfriendly authentication in RFID systems: On sublinear protocols based on symmetric-key cryptography. IEEE Trans. Mob. Comput. 2013, 12, 2037–2049. [Google Scholar] [CrossRef]
- Kinoshita, S.; Ohkubo, M.; Hoshino, F.; Morohashi, G.; Shionoiri, O.; Kanai, A. Privacy enhanced active RFID tag. In Proceedings of the Workshop Exploiting Context Histories Smart Environments, Munich, Germany, 11 May 2005; pp. 43–52. [Google Scholar]
- Ng, C.; Susilo, W.; Mu, Y.; Safavi-Naini, R. New privacy results on synchronized RFID authentication protocols against tag tracing. In Computer Security—ESORICS (Lecture Notes in Computer Science); Springer: Berlin/Heidelberg, Germany, 2009; Volume 5789, pp. 321–336. [Google Scholar]
- Lee, C.-I.; Chien, H.-Y. An elliptic curve cryptography-based RFID authentication securing e-health system. Int. J. Distrib. Sens. Netw. 2015, 11, 642425. [Google Scholar] [CrossRef]
- Liao, Y.-P.; Hsiao, C. A secure ECC-based RFID authentication scheme integrated with ID-verifier transfer protocol. Ad Hoc Netw. 2014, 18, 133–146. [Google Scholar] [CrossRef]
- Chien, H.-Y. De-synchronization attack on quadratic residues-based RFID ownership transfer. In Proceedings of the 2015 10th Asia Joint Conference on Information Security, Kaohsiung, Taiwan, 24–26 May 2015; pp. 42–47. [Google Scholar]
- Chien, H.-Y. Combining Rabin crypto-system and error correction codes to facilitate anonymous authentication with un-traceability for low-end devices. Comput. Netw. 2013, 57, 2705–2717. [Google Scholar] [CrossRef]
- Chen, Y.; Chou, J.S.; Sun, H.M. A novel mutual authentication scheme based on quadratic residues for RFID systems. Comput. Netw. 2008, 52, 2373–2380. [Google Scholar] [CrossRef]
- Doss, R.; Zhou, W.; Sundaresan, S.; Yu, S.; Gao, L. A minimum disclosure approach to authentication and privacy in RFID systems. Comput. Netw. 2012, 56, 3401–3416. [Google Scholar] [CrossRef]
- Tan, C.C.; Sheng, B.; Li, Q. Secure and server-less RFID authentication and search protocols. IEEE Trans. Wirel. Commun. 2008, 7, 1400–1407. [Google Scholar] [CrossRef]
- Yang, J.; Park, J.; Lee, H.; Ren, K.; Kim, K. Mutual authentication protocol for low-cost RFID. In Proceedings of the Workshop RFID Lightweight Cryptograp, Graz, Austria, 14–15 July 2005; pp. 17–24. [Google Scholar]
- Luo, Z.; Chan, T.; Li, J.S. A lightweight mutual authentication protocol for RFID networks. In Proceedings of the IEEE International Conference on e-Business Engineering (ICEBE’05), Beijing, China, 12–18 October 2005; pp. 620–625. [Google Scholar]
- Gope, P.; Hwang, T. A realistic lightweight authentication protocol preserving strong anonymity for securing RFID system. Comput. Secur. 2015, 55, 271–280. [Google Scholar] [CrossRef]
- Bringer, J.; Chabanne, H.; Icart, T. Improved privacy of the treebased hash protocols using physically unclonable function. In Proceedings of the 6th International Conference on Security and Cryptology for Networks (SCN), Amalfi, Italy, 10–12 September 2008; pp. 77–91. [Google Scholar]
- Sadeghi, A.-R.; Visconti, I.; Wachsmann, C. PUF-enhanced offline RFID security and privacy. In Proceedings of the Secure Component Systems Identification, Cologne, Germany, 15–16 June 2010; pp. 102–106. [Google Scholar]
- Akgun, M.; Caglayan, M.U. Puf based scalable private RFID authentication. In Proceedings of the 2011 Sixth International Conference on Availability, Reliability and Security, Vienna, Austria, 22–26 August 2011; pp. 473–478. [Google Scholar]
- Kardas, S.; Kiraz, M.S.; Bing, M.A.; Demirci, H. A novel RFID distance bounding protocol based on physically unclonable functions. In RFID. Security and Privacy, Proceedings of the 7th International Workshop, RFIDSec 2011, Amherst, MA, USA, 26–28 June 2011; Springer: Berlin/Heidelberg, Germany, 2012; pp. 78–93. [Google Scholar]
- Kardas, S.; Celik, S.; Yildiz, M.; Levi, A. Puf-enhanced offline RFID security and privacy. J. Netw. Comput. Appl. 2012, 35, 2059–2067. [Google Scholar] [CrossRef]
- Akgun, M.; Caglayan, M.U. Providing destructive privacy and scalability in RFID systems using PUFs. Ad. Hoc. Netw. 2015, 32, 32–42. [Google Scholar] [CrossRef]
- Bohm, C.; Hofer, M. Physical Unclonable Functions in Theory and Practice; Springer: New York, NY, USA, 2012. [Google Scholar]
- Pandey, S.; Deyati, S.; Singh, A.; Chatterjee, A. Noise-resilient SRAM physically unclonable function design for security. In Proceedings of the 2016 IEEE 25th Asian Test Symposium (ATS), Hiroshima, Japan, 21–24 November 2016; pp. 55–60. [Google Scholar]
- Bendavid, Y.; Bagheri, N.; Safkhani, M.; Rostampour, S. IoT Device Security: Challenging “A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function”. Sensors 2018, 18, 4444. [Google Scholar] [CrossRef]
- Xu, H.; Ding, J.; Li, P.; Zhu, F.; Wang, R. A Lightweight RFID Mutual Authentication Protocol Based on Physical Unclonable Function. Sensors 2018, 18, 760. [Google Scholar] [CrossRef] [PubMed]
- Kulseng, L.; Yu, Z.; Wei, Y.; Guan, Y. Lightweight Mutual Authentication and Ownership Transfer for RFID Systems. In Proceedings of the IEEE Infocom, San Diego, CA, USA, 14–19 March 2010; pp. 1–5. [Google Scholar]
- Cavusoglu, H.; Raghunathan, S.; Mishra, B. Optimal Design of Information Technology Security Architecture. In Proceedings of the International Conference on Information Systems, Barcelona, Spain, 15–18 December 2002; Volume 74. [Google Scholar]
- Bhattacharya, B.; Lu, Q.; Zhong, J. Reliability of redundant ductile structures with uncertain system failure criteria. Sadhana 2009, 34, 903–921. [Google Scholar] [CrossRef]
- Tyurin, S.F.; Grekov, A.V. Functionally Complete Tolerant Elements. Int. J. Appl. Eng. Res. 2015, 10, 34433–34442. [Google Scholar]
- Potapov, V.I.; Shafeeva, O.P.; Doroshenko, M.S.; Chervenchuk, I.V.; Gritsay, A.S. Numerically-analytical solution of problem gaming confrontation hardware-redundant dynamic system with the enemy operating in conditions of incomplete information about the behavior of participants in the game. J. Phys. Conf. Ser. 2018, 1050, 012062. [Google Scholar] [CrossRef]
- Gupta, D.N.; Kumar, R. DeeR-Gen: A pseudo random number generator for industry 4.0/IoT. J. Sci. Ind. Res. 2023, 82, 316–321. [Google Scholar]
- Aysu, A.; Gulcan, E.; Moriyama, D.; Schaumont, P.; Yung, M. End-to-end design of a PUF-based privacy preserving authentication protocol. In International Workshop on Cryptographic Hardware and Embedded Systems; Springer: Berlin/Heidelberg, Germany, 2015; pp. 556–576. [Google Scholar]
- Van Herrewege, A.; Katzenbeisser, S.; Maes, R.; Peeters, R.; Sadeghi, A.R.; Verbauwhede, I.; Wachsmann, C. Reverse fuzzy extractors: Enabling lightweight mutual authentication for PUF-enabled RFIDs. In Proceedings of the International Conference on Financial Cryptography and Data Security, Kralendijk, Bonaire, 27 Februray–2 March 2012; Springer: Berlin/Heidelberg, Germany, 2012; Volume 1, pp. 374–389. [Google Scholar]
| Symbol | Definition |
|---|---|
| CID | Identification of client |
| SID | Identification of server |
| H(SID) | Hashing over identification of server |
| ⊕ | XOR operation |
| E | Encryption function |
| T | Timestamp |
| Gn | Generator value |
| PUF | Physical unclonable function |
| F | Nonlinear-feedback shift register |
| Claim | Status | Comments | |||
|---|---|---|---|---|---|
| Improved | S | improved, S1 | Secret ID | OK | No attacks within bounds. |
| improved, S2 | Tiagree | OK | No attacks within bounds. | ||
| improved, S3 | Gnsynch | OK | No attacks within bounds. | ||
| improved, S4 | Alive | OK | No attacks within bounds. | ||
| improved, S5 | Weakagree | OK | No attacks within bounds. | ||
| C | improved, C1 | Secret SID | OK | No attacks within bounds. | |
| improved, C2 | Tiagree | OK | No attacks within bounds. | ||
| improved, C3 | Gnsynch | OK | No attacks within bounds. | ||
| improved, C4 | Alive | OK | No attacks within bounds. | ||
| improved, C5 | Weakagree | OK | No attacks within bounds. |
| Protocols | Impersonation | Traceability | Disclosure | Desynchronization | Forward/Backward Secrecy |
|---|---|---|---|---|---|
| Sadeghi et al. [31] | Non-resistant | Non-resistant | Resistant | Resistant | Non-resistant |
| Aysu et al. [46] | Resistant | Non-resistant | Non-resistant | Resistant | Non-resistant |
| Van Herrewege et al. [47] | Resistant | Resistant | Non-resistant | Resistant | Non-resistant |
| Kulseng et al. [40] | Resistant | Resistant | Non-resistant | Non-resistant | Non-resistant |
| Xu et al. [39] | Resistant | Resistant | Non-resistant | Non-resistant | Non-resistant |
| Bendavid et al. [38] | Resistant | Resistant | Resistant | Resistant | Non-resistant |
| Proposed | Resistant | Resistant | Resistant | Resistant | Resistant |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bhatia, K.; Pandey, S.K.; Singh, V.K.; Gupta, D.N. Hash and Physical Unclonable Function (PUF)-Based Mutual Authentication Mechanism. Sensors 2023, 23, 6307. https://doi.org/10.3390/s23146307
Bhatia K, Pandey SK, Singh VK, Gupta DN. Hash and Physical Unclonable Function (PUF)-Based Mutual Authentication Mechanism. Sensors. 2023; 23(14):6307. https://doi.org/10.3390/s23146307
Chicago/Turabian StyleBhatia, Kavita, Santosh K. Pandey, Vivek K. Singh, and Deena Nath Gupta. 2023. "Hash and Physical Unclonable Function (PUF)-Based Mutual Authentication Mechanism" Sensors 23, no. 14: 6307. https://doi.org/10.3390/s23146307
APA StyleBhatia, K., Pandey, S. K., Singh, V. K., & Gupta, D. N. (2023). Hash and Physical Unclonable Function (PUF)-Based Mutual Authentication Mechanism. Sensors, 23(14), 6307. https://doi.org/10.3390/s23146307







