Automatic Verification and Execution of Cyber Attack on IoT Devices
Abstract
1. Introduction
2. Background and Related Work
2.1. Internet of Things and Cybersecurity
2.1.1. Threats and Risks
2.1.2. Threat Actors
- Cyber-criminals is a term used for individuals that conduct illegal activities on the Web that does not involve hacking. This includes drug dealing, human trafficking, sharing or downloading child pornography, and conducting financial fraud. While they are not directly a cybersecurity threat, they are criminals within the cyber realm and are included in this list for the sake of completeness.
- Script kiddies and cyber-punks have limited knowledge and skills and use existing tools to exploit low hanging fruit. Fame among peers, small gains, or simply entertainment are usually their motives.
- Hacktivists are the digital equivalent to activists. They consist of anonymous groups that target private organizations and governments to publicize a political agenda.
- Cyber-terrorists are terrorists using the web to recruit new members and share information. They may also conduct attacks in the cyber domain with the same motives as terrorist attacks in the physical world.
- Black hat hackers are mostly individual hackers with knowledge and expertise in hacking and the tools used. Their targets may be specific companies or individuals or arbitrary devices found by means such as the search engine Shodan. Their motives are usually reputation or financial gains.
- Malware- and hacking tools coders are highly skilled adversaries that create tools and malware used to target different types of systems. They may work alone or in a criminal organization. The may sell the tools or use them in ransomware attacks or to create botnets. This is one of the most prevalent threats for IoT devices [13].
- State-sponsored attackers are groups with extensive expertise and resources. They target corporations or governments in order to reveal trade or state secrets, plans, or ideas, or in other ways harm the victim. Their attacks are sophisticated and may utilize zero-days, making them difficult to avert.
2.1.3. Attack Surface and Security Issues
- Perception LayerThe physical part of the device is represented by the perception layer. The layer gathers information from and interacts with the physical world around it. To achieve this, the device can use sensors, actuators, GPS, RFIDs, or other similar technologies. IoT devices may often have limited computing powers, storage, and battery capacity. This limits the complexity of its encryption schemes and key lengths [17]. Furthermore, the devices may need to be small and lightweight which limits the possible physical hardening options. The IoT devices may be situated in places where maintenance is difficult or neglected because they rarely receive human interaction. Such devices may be left untouched simply because they work, contributing to the growing concern of orphaned devices [18].
- Network LayerTo control the actuators or process the information gathered in the perception layer, data must be transmitted between the physical and the application layer. The network layer connects the end nodes to network devices, servers or other IoT objects, and handles the corresponding data flow. The connection is often wireless due of cost, coverage, and mobility. Examples of wireless technologies used within this layer include ZigBee, Bluetooth, WiFi, 4G, 5G, satellites, and combinations of them. The network layer is prone to jamming attacks, access point spoofing, data sniffing, MITM (Man-in-the-Middle) attacks, and more [17]. The devices may be used as an entry point into their connected networks, which makes their security increasingly important [16].
- Application LayerThe application layer provides user interaction and management of the service provided by the IoT device. This may be presented as a smart home hub, a Web or mobile application, or a machine-to-machine interface. Depending on the field, service, and user, there are numerous technologies and applications that can be used on this layer. Because the application layer often presents an interface to the Internet, it has the same security issues as most other computing devices with an Internet connection. While this layer can be harder to exploit, it will often be accessible from anywhere in the world, substantially increasing the potential threat actors. Examples of common attacks include credential guessing, SQL injection, buffer overflow, and social engineering attacks [19].
2.2. Penetration Testing
- Pre-Engagement InteractionsThis step involves and emphasises the importance of clearly defining the target, scope, and potential boundaries before interacting with a system.
- Intelligence GatheringBefore attacking the system, the tester must know how it functions, how it is structured, and how it can be interacted with. As mentioned above, automated software tools can often be used for this purpose.
- Threat ModellingTo properly analyze the security of a system, the tester should know who could attack it and why. Thus, PTES threat modelling focuses on the assets that can be targeted and the liable threat actors.
- Vulnerability AnalysisThis step is where potential vulnerabilities, from misconfigurations to faulty designs, are uncovered. Many software tools, as well as human interaction with the system, are important to properly examine it.
- ExploitationTo analyze the discovered vulnerabilities, the tester will attempt to exploit them. This should reveal their potential implications and may be used to uncover more vulnerabilities.
- PostexploitationIf a component of the system has been successfully compromised, the value of the component should be evaluated with regards to its usefulness in further exploitation of the system.
- ReportingThe value of the penetration test comes from reporting the discovered and exploited vulnerabilities. These should be evaluated according to their severity and risk.
2.2.1. Testing of IoT Devices
2.2.2. Autonomous Penetration Testing
2.3. Wi-Fi
2.3.1. Encryption Standards and WPA2 Personal
2.3.2. The 4-Way Handshake
2.3.3. Deauthentication Frames
2.3.4. Evil Twin Attack
2.4. The EP Model and Formal Specification
2.4.1. Formal Specification and Verification
- TLA+ is expressive: It allows users to describe complex systems and their behaviors in a clear and concise way.
- TLA+ is modular: It allows users to divide a system into smaller, easier-to-manage components, making it easier to understand and verify.
- TLA+ is reusable: Because it is a high-level language, TLA+ specifications can be reused and adapted to different systems, saving time and effort.
- TLA+ is supported by powerful tools: The TLA+ Toolbox is a suite of tools that support the development and verification of TLA+ specifications, including a model checker and an automatic theorem prover.
2.4.2. TLA+
2.5. Related Work
3. Case Study and Environment
3.1. Hardware
3.2. Software
3.2.1. The Aircrack-ng Suite
3.2.2. Airmon-ng
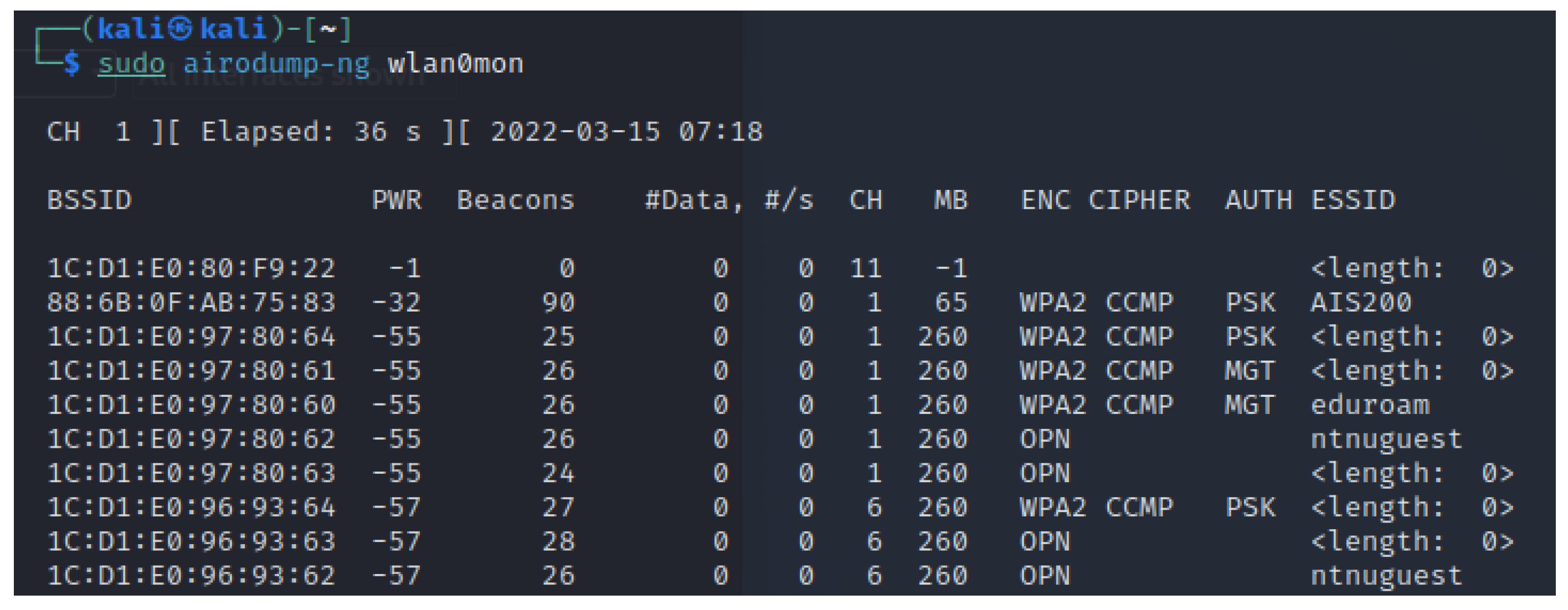
3.2.3. Airodump-ng
3.2.4. Aireplay-ng
3.2.5. Aircrack-ng
3.2.6. Hostapd
3.3. Target IoT Device
3.4. Physical Setup
4. Manual Attack Results
4.1. Attack 1: DoS
4.2. Attack 2: Evil Twin
5. System Design for Automated Attacks
5.1. The Attack Procedure
- Attack 1: DOS
- Capture APsFirst, the agent will capture all APs within range. This can be done within a couple of seconds using Airodump-ng but should be performed on a monitoring network interface. To change the mode of NIC, the agent will use Airmon-ng.
- Capture clientsIf the target AP is found in previous step, the agent will capture the clients connected to the AP using Airodump-ng. Depending on the traffic on the network, this may take few more seconds than capturing the APs.
- Launch attackProvided that there are clients on the network, the agent should perform the DOS attack. Each client will continuously receive deauthentication frames that appear to be from the AP, withholding them from the reconnecting.
- Attack 2: Evil Twin
- Capture handshakeThis step involves capturing the handshake process between a client and the AP. By deauthenticating the client using Aireplay-ng, the agent can capture the handshake upon reconnection using Airodump-ng.
- Find passwordThe password can be cracked using a dictionary attack if the nonces of the handshake was captured in the previous step. To perform the dictionary attack, Aircrack-ng will be used.
- Launch attackIf the password is cracked, the agent will spoof the network of the target AP using Hostapd. When deauthenticating the client again using Aireplay-ng, the client should automatically reconnect to the Evil Twin AP if its signal strength is stronger than that of the true AP.
5.2. EP Models of Attacks
6. System Implementation and Formal Verification
- <<“Launching attack…”>>
- <<“Not able to capture any clients”>>
- <<“Launching attack…”>>
6.1. Implementation
6.1.1. Tool Interface
| Algorithm 1. The function for capturing all APs within range. |
| def capture_aps(self, interface : str, proc_timeout=2) -> str: |
| “““Captures all access points within range |
| Parameters |
| ---------- |
| interface : str |
| Interface to capture packets on |
| proc_timeout : int, optional |
| Amount of seconds to run the capture, by default 2 |
| Returns |
| ------- |
| str |
| filepath to xml file containing AP data |
| “““ |
| self.logger.debug(’Capturing all APs...’) |
| fsuffix = [] |
| flags = { |
| ’--write-interval’: ’1’, |
| ’--output-format’: ’netxml’} |
| return self._capture(interface, fsuffix, flags, proc_timeout) |
| Algorithm 2. Part of the “run” function within the abstract ToolExecutor class. |
| self.logger.debug(f’Running command: <{command}>’) |
| if self.verbose: |
| self.logger.debug(f’\tkeywords: <{proc_flags}>’) |
| try: |
| output = subprocess.run(command, **proc_flags) |
| except subprocess.TimeoutExpired as e: |
| self.logger.debug(f’Process timout’) |
| return True |
| else: |
| if self.verbose: |
| self.logger.debug(f’Captured stdout: <{output.stdout[:-1]}>’) |
| self.logger.debug(f’Captured stderr: <{output.stderr}>’) |
| return output |
6.1.2. Agent Decision Making
7. Discussion
7.1. Network Interface Range
7.2. Time to Crack Network Password
7.3. Comparison with Similar Systems
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption Standard |
| AI | Artificial Intelligence |
| AIS | Automatic Identification System |
| AP | Access Point |
| APT | Advanced Persistent Threat |
| BDI | Belief–Desire–Intention |
| BSSID | Basic SSID |
| CCMP | Counter Mode with Cipher Block Chaining Message Authentication Code Protocol |
| DDoS | Distributed Denial of Service |
| DoS | Denial of Service |
| DSR | Design Science Research |
| EAPOL | Extensible Authentication Protocol over LAN |
| EP | Execution Plan |
| ESSID | Extended SSID |
| GPS | Global Positioning System |
| GTK | Group Temporal Key |
| IDS | Intrusion Detection Systems |
| IEEE | Institute of Electrical and Electronics Engineers |
| IGTK | Integrity Group Temporal Key |
| IIoT | Industrial Internet of Things |
| IoMT | Internet of Medical Things |
| IoT | Internet of Things |
| IPS | Intrusion Protection Systems |
| LAN | Local Area Network |
| MIC | Message Integrity Code |
| MitM | Man-in-the-Middle |
| NCR | Norwegian Cyber Range |
| NIC | Network Interface Card |
| NMEA | National Marine Electronics Association |
| PMK | Pairwise Master Key |
| PSK | Preshared Key |
| PTES | Penetration Testing Execution Standard |
| PTK | Pairwise Transient Key |
| RL | Reinforcement Learning |
| SSID | Service Set Identifier |
| VHF | Very High Frequency |
| VTS | Vessel Traffic Services |
| WEP | Wired Equivalent Privacy |
| WLAN | Wireless LAN |
| WPA | Wi-Fi Protected Access |
References
- Yamin, M.M.; Katt, B.; Gkioulos, V. Cyber ranges and security testbeds: Scenarios, functions, tools and architecture. Comput. Secur. 2020, 88, 101636. [Google Scholar] [CrossRef]
- Yamin, M.M.; Katt, B. Use of cyber attack and defense agents in cyber ranges: A case study. Comput. Secur. 2022, 122, 102892. [Google Scholar] [CrossRef]
- Samonas, S.; Coss, D. The CIA strikes back: Redefining confidentiality, integrity and availability in security. J. Inf. Syst. Secur. 2014, 10. [Google Scholar]
- Leavitt, N. Researchers fight to keep implanted medical devices safe from hackers. Computer 2010, 43, 11–14. [Google Scholar] [CrossRef]
- Hernandez, G.; Arias, O.; Buentello, D.; Jin, Y. Smart nest thermostat: A smart spy in your home. In Proceedings of the Black Hat Briefings USA 2015, Online, 5–6 August 2014. [Google Scholar]
- This Hacker Showed How a Smart Lightbulb Could Leak Your Wi-Fi Password. 2013. Available online: https://www.vice.com/en/article/kzdwp9/this-hacker-showed-how-a-smart-lightbulb-could-leak-your-wi-fi-password (accessed on 7 September 2022).
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the Mirai Botnet. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), USENIX Association, Vancouver, BC, Canada, 16–18 August 2017; pp. 1093–1110. [Google Scholar]
- Hack Forums Post. 2016. Available online: https://hackforums.net/showthread.php?tid=5420472 (accessed on 7 September 2022).
- Mirai GitHub Upload. 2016. Available online: https://github.com/jgamblin/Mirai-Source-Code (accessed on 7 September 2022).
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Cyber-Security Threats, Actors, and Dynamic Mitigation. 2013. Available online: https://books.google.no/books?hl=en&lr=&id=FXUhEAAAQBAJ&oi=fnd&pg=PP1&dq=iot+threat+actors&ots=nZm_msDCoq&sig=qkLTNyCLkKEr646Z2MTTfjRPxqU&redir_esc=y#v=onepage&q&f=false (accessed on 7 September 2022).
- Advanced Persistent Threat (APT). 2022. Available online: https://www.imperva.com/learn/application-security/apt-advanced-persistent-threat/ (accessed on 7 September 2022).
- Costin, A.; Zaddach, J. Iot malware: Comprehensive survey, analysis framework and case studies. BlackHat USA 2018, 1, 1–9. [Google Scholar]
- Jamali, J.; Bahrami, B.; Heidari, A.; Allahverdizadeh, P.; Norouzi, F. Towards the Internet of Things; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- IoT Architecture. 2020. Available online: https://www.zibtek.com/blog/iot-architecture/ (accessed on 7 September 2022).
- Chu, G.; Lisitsa, A. Penetration testing for internet of things and its automation. In Proceedings of the 2018 IEEE 20th International Conference on High Performance Computing and Communications; IEEE 16th International Conference on Smart City; IEEE 4th International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Exeter, UK, 28–30 June 2018; pp. 1479–1484. [Google Scholar]
- Hossain, M.M.; Fotouhi, M.; Hasan, R. Towards an analysis of security issues, challenges, and open problems in the internet of things. In Proceedings of the 2015 IEEE World Congress on Services, New York, NY, USA, 27 June–2 July 2015; pp. 21–28. [Google Scholar]
- Rose, C. The Security Implications of the Internet of Things. J. Cybersecur. Res. (JCR) 2017, 2, 1–4. [Google Scholar] [CrossRef]
- Bacudio, A.G.; Yuan, X.; Chu, B.T.B.; Jones, M. An overview of penetration testing. Int. J. Netw. Secur. Its Appl. 2011, 3, 19. [Google Scholar] [CrossRef]
- Office of Chief Information Officer, US Department of the Interior. 2022. Available online: https://www.doi.gov/ocio/customers/penetration-testing/ (accessed on 7 September 2022).
- Stiawan, D.; Idris, M.Y.; Abdullah, A.H.; Aljaber, F.; Budiarto, R. Cyber-Attack Penetration Test and Vulnerability Analysis. Int. J. Online Eng. 2017, 13. [Google Scholar] [CrossRef]
- Shanley, A.; Johnstone, M.N. Selection of Penetration Testing Methodologies: A Comparison and Evaluation. Ph.D Thesis, SRI Security Research Institute, Edith Cowan University, Perth, WA, Australia, 2015. [Google Scholar]
- Penetration Testing Execution Standard. 2009. Available online: http://www.pentest-standard.org/index.php/Main_Page (accessed on 7 September 2022).
- Chen, C.K.; Zhang, Z.K.; Lee, S.H.; Shieh, S. Penetration testing in the iot age. Computer 2018, 51, 82–85. [Google Scholar] [CrossRef]
- Johari, R.; Kaur, I.; Tripathi, R.; Gupta, K. Penetration Testing in IoT Network. In Proceedings of the 2020 5th International Conference on Computing, Communication and Security (ICCCS), Patna, India, 14–16 October 2020; pp. 1–7. [Google Scholar]
- Rak, M.; Salzillo, G.; Romeo, C. Systematic IoT Penetration Testing: Alexa Case Study. In Proceedings of the ITASEC, Ancona, Italy, 4–7 February 2020; pp. 190–200. [Google Scholar]
- Yadav, G.; Paul, K.; Allakany, A.; Okamura, K. IoT-PEN: An E2E penetration testing framework for IoT. J. Inf. Process. 2020, 28, 633–642. [Google Scholar] [CrossRef]
- Cisco. What is Wi-Fi. 2022. Available online: https://www.cisco.com/c/en/us/products/wireless/what-is-wi-fi-6.html (accessed on 7 September 2022).
- Understanding the Network Terms SSID, BSSID, and ESSID. 2018. Available online: https://www.juniper.net/documentation/en_US/junos-space-apps/network-director4.0/topics/concept/wireless-ssid-bssid-essid.html (accessed on 7 September 2022).
- Reddy, B.I.; Srikanth, V. Review on wireless security protocols (WEP, WPA, WPA2 & WPA3). Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2019, 28–35. [Google Scholar]
- Moissinac, K.; Ramos, D.; Rendon, G.; Elleithy, A. Wireless encryption and WPA2 weaknesses. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 27–30 January 2021; pp. 1007–1015. [Google Scholar]
- Tsitroulis, A.; Lampoudis, D.; Tsekleves, E. Exposing WPA2 security protocol vulnerabilities. Int. J. Inf. Comput. Secur. 2014, 6, 93–107. [Google Scholar] [CrossRef]
- Sofi, M.A. Bluetooth Protocol in Internet of Things (IoT), Security Challenges and a Comparison with Wi-Fi Protocol: A Review. Int. J. Eng. Tech. Res. 2016, 5, 461–467. [Google Scholar]
- Mathews, M.; Hunt, R. Evolution of wireless LAN security architecture to IEEE 802.11 i (WPA2). In Proceedings of the Fourth IASTED Asian Conference on Communication Systems and Networks, AsiaCSN, Phuket, Thailand, 2–4 April 2007; Volume 7, pp. 292–297. [Google Scholar]
- IEEE Computer Society LAN/MAN Standards Committee. IEEE Std 802.11i-2004; IEEE Standard for Information Technology-Telecommunications and Information Exchange between Systems-Local and Metropolitan Area Networks-Specific Requirements-Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications: Amendment 6: Medium Access Control (MAC) Security Enhancements. IEEE Computer Society LAN/MAN Standards Committee: New York, NY, USA, 2004; pp. 1–190. [CrossRef]
- Radivilova, T.; Hassan, H.A. Test for penetration in Wi-Fi network: Attacks on WPA2-PSK and WPA2-enterprise. In Proceedings of the 2017 International Conference on Information and Telecommunication Technologies and Radio Electronics (UkrMiCo), Odesa, Ukraine, 11–15 September 2017; pp. 1–4. [Google Scholar]
- Etta, V.O.; Sari, A.; Imoize, A.L.; Shukla, P.K.; Alhassan, M. Assessment and Test-case Study of Wi-Fi Security through the Wardriving Technique. Mob. Inf. Syst. 2022, 2022, 7936236. [Google Scholar] [CrossRef]
- Maráczi, M. Wardriving in Eger. In Proceedings of the 2019 IEEE 13th International Symposium on Applied Computational Intelligence and Informatics (SACI), Timisoara, Romania, 29–31 May 2019; pp. 000127–000130. [Google Scholar]
- Valchanov, H.; Edikyan, J.; Aleksieva, V. A study of Wi-Fi security in city environment. In Proceedings of the IOP Conference Series: Materials Science and Engineering; IOP Publishing: Bristol, UK, 2019; Volume 618, p. 012031. [Google Scholar]
- Kristiyanto, Y.; Ernastuti, E. Analysis of deauthentication attack on ieee 802.11 connectivity based on iot technology using external penetration test. CommIT (Commun. Inf. Technol.) J. 2020, 14, 45–51. [Google Scholar] [CrossRef]
- Bauer, K.; Gonzales, H.; McCoy, D. Mitigating evil twin attacks in 802.11. In Proceedings of the 2008 IEEE International Performance, Computing and Communications Conference, Austin, TX, USA, 7–9 December 2008; pp. 513–516. [Google Scholar]
- Yamin, M.M. Modelling and Analyzing Attack-Defense Scenarios for Cyber-Ranges. Ph.D. Thesis, Norwegian University of Science and Technology, Trondheim, Norway, 2022. [Google Scholar]
- Hierons, R.M.; Bogdanov, K.; Bowen, J.P.; Cleaveland, R.; Derrick, J.; Dick, J.; Gheorghe, M.; Harman, M.; Kapoor, K.; Krause, P.; et al. Using formal specifications to support testing. Acm Comput. Surv. (CSUR) 2009, 41, 1–76. [Google Scholar] [CrossRef]
- Bourgois, M. Advantages of Formal Specifications: A Case Study of Replication in Lotus Notes. In Formal Methods for Open Object-Based Distributed Systems; Najm, E., Stefani, J.B., Eds.; Springer: Boston, MA, USA, 1997; pp. 231–244. [Google Scholar] [CrossRef]
- A High-Level View of TLA+. 1997. Available online: http://lamport.azurewebsites.net/tla/high-level-view.html (accessed on 7 September 2022).
- Kulik, T.; Dongol, B.; Larsen, P.G.; Macedo, H.D.; Schneider, S.; Tran-Jørgensen, P.W.; Woodcock, J. A survey of practical formal methods for security. Form. Asp. Comput. 2022, 34, 1–39. [Google Scholar] [CrossRef]
- Krichen, M. Improving Formal Verification and Testing Techniques for Internet of Things and Smart Cities. In Mobile Networks and Applications; Springer: Berlin/Heidelberg, Germany, 2019; pp. 1–12. [Google Scholar]
- Nmap. 1997. Available online: https://nmap.org (accessed on 7 September 2022).
- SQLmap. 2006. Available online: https://sqlmap.org (accessed on 7 September 2022).
- Metasploit. 2003. Available online: https://www.metasploit.com/ (accessed on 7 September 2022).
- Nessus. 2005. Available online: https://www.tenable.com/products/nessus (accessed on 7 September 2022).
- Caldwell, S. Training an Autonomous Pentester with Deep RL. In Proceedings of the Strange Loop Conference 2021, Strange Loop, St. Louis, MO, USA, 1–2 October 2021. [Google Scholar]
- Schwartz, J.; Kurniawati, H. Autonomous penetration testing using reinforcement learning. arXiv 2019, arXiv:1905.05965. [Google Scholar]
- Zennaro, F.M.; Erdodi, L. Modeling penetration testing with reinforcement learning using capture-the-flag challenges: Trade-offs between model-free learning and a priori knowledge. arXiv 2020, arXiv:2005.12632. [Google Scholar]
- Hu, Z.; Beuran, R.; Tan, Y. Automated penetration testing using deep reinforcement learning. In Proceedings of the 2020 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Genoa, Italy, 7–11 September 2020; pp. 2–10. [Google Scholar]
- Tran, K.; Akella, A.; Standen, M.; Kim, J.; Bowman, D.; Richer, T.; Lin, C.T. Deep hierarchical reinforcement agents for automated penetration testing. arXiv 2021, arXiv:cs.AI/2109.06449. [Google Scholar]
- Krichen, M.; Alroobaea, R. A new model-based framework for testing security of iot systems in smart cities using attack trees and price timed automata. In Proceedings of the 14th International Conference on Evaluation Of Novel Approaches to Software Engineering, Crete, Greece, 4–5 May 2019; pp. 570–577. [Google Scholar]
- Wideł, W.; Audinot, M.; Fila, B.; Pinchinat, S. Beyond 2014: Formal Methods for Attack Tree–based Security Modeling. ACM Comput. Surv. (CSUR) 2019, 52, 1–36. [Google Scholar] [CrossRef]
- Saxena, S.; Bhushan, B.; Ahad, M.A. Blockchain based solutions to secure IoT: Background, integration trends and a way forward. J. Netw. Comput. Appl. 2021, 181, 103050. [Google Scholar] [CrossRef]
- Rathee, G.; Balasaraswathi, M.; Chandran, K.P.; Gupta, S.D.; Boopathi, C. A secure IoT sensors communication in industry 4.0 using blockchain technology. J. Ambient. Intell. Humaniz. Comput. 2021, 12, 533–545. [Google Scholar] [CrossRef]
- Verma, S.; Kawamoto, Y.; Kato, N. A network-aware Internet-wide scan for security maximization of IPV6-enabled WLAN IoT devices. IEEE Internet Things J. 2020, 8, 8411–8422. [Google Scholar] [CrossRef]
- Vanhoef, M.; Piessens, F. Key reinstallation attacks: Forcing nonce reuse in WPA2. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 1313–1328. [Google Scholar]
- Vanhoef, M. Fragment and Forge: Breaking Wi-Fi Through Frame Aggregation and Fragmentation. In Proceedings of the 30th USENIX Security Symposium, USENIX Association, Boston, MA, USA, 10–12 August 2021. [Google Scholar]
- D3Ext. WiFi Exploitation Framework. 2022. Available online: https://github.com/D3Ext/WEF (accessed on 7 September 2022).
- v1s1t0r. Airgeddon. 2022. Available online: https://github.com/v1s1t0r1sh3r3/airgeddon (accessed on 7 September 2022).
- Wifiphisher. 2017. Available online: https://wifiphisher.org/ (accessed on 7 September 2022).
- What is Kali Linux. 2022. Available online: https://www.kali.org/docs/introduction/what-is-kali-linux/ (accessed on 7 September 2022).
- Hostapd. 2022. Available online: https://man.openbsd.org/hostapd.8 (accessed on 7 September 2022).
- A200 AIS Class A. 2022. Available online: https://em-trak.com/products-a200/ (accessed on 7 September 2022).
- Automatic Identification System (AIS): Integrating and Identifying Marine Communication Channels. 2021. Available online: https://www.marineinsight.com/marine-navigation/automatic-identification-system-ais-integrating-and-identifying-marine-communication-channels/ (accessed on 7 September 2022).
- OpenCPN. 2022. Available online: https://www.opencpn.org/ (accessed on 7 September 2022).
- Ceri, S.; Gottlob, G.; Tanca, L. What you always wanted to know about Datalog(and never dared to ask). IEEE Trans. Knowl. Data Eng. 1989, 1, 146–166. [Google Scholar] [CrossRef]
- Subprocess Management. 2022. Available online: https://docs.python.org/3/library/subprocess.html (accessed on 7 September 2022).
- Pyrcrack Python Package. 2020. Available online: https://github.com/XayOn/pyrcrack (accessed on 7 September 2022).
- Bellardo, J.; Savage, S. 802.11 {Denial-of-Service} Attacks: Real Vulnerabilities and Practical Solutions. In Proceedings of the 12th USENIX Security Symposium (USENIX Security 03), Washington, DC, USA, 4–8 August 2003. [Google Scholar]
- What is Wi-Fi. 2017. Available online: https://hackingvision.com/2017/02/18/increasing-wifi-tx-power-signal-strength-in-linux/ (accessed on 7 September 2022).
- GPU Accelerated Password Cracking in the Cloud: Speed and Cost-Effectiveness. 2021. Available online: https://systemoverlord.com/2021/06/05/gpu-accelerated-password-cracking-in-the-cloud.html (accessed on 7 September 2022).
- Rak, M.; Salzillo, G.; Granata, D. ESSecA: An automated expert system for threat modelling and penetration testing for IoT ecosystems. Comput. Electr. Eng. 2022, 99, 107721. [Google Scholar] [CrossRef]






















| Aircrack-ng, Kali Machine | Aircrack-ng, Desktop | Hashcat | |
|---|---|---|---|
| Crack speed (k/s) | 2300 | 22,500 | 1.1 million |
| Dictionary attack on 1.4M key wordlist (s) | 10 m 6 s | 62 s | 1 s |
| Brute-force 8 integers | 13 h | 75 min | 2 min |
| Brute force 8 lowercase letters | 3 years | 4 months | 53 h |
| Brute force 8 integers and lowercase letters | 40 years | 5 years | 30 days |
| Brute force 12 integers and lowercase letters | 66,234,755 years | 6,770,664 years | 138,491 years |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Færøy, F.L.; Yamin, M.M.; Shukla, A.; Katt, B. Automatic Verification and Execution of Cyber Attack on IoT Devices. Sensors 2023, 23, 733. https://doi.org/10.3390/s23020733
Færøy FL, Yamin MM, Shukla A, Katt B. Automatic Verification and Execution of Cyber Attack on IoT Devices. Sensors. 2023; 23(2):733. https://doi.org/10.3390/s23020733
Chicago/Turabian StyleFærøy, Fartein Lemjan, Muhammad Mudassar Yamin, Ankur Shukla, and Basel Katt. 2023. "Automatic Verification and Execution of Cyber Attack on IoT Devices" Sensors 23, no. 2: 733. https://doi.org/10.3390/s23020733
APA StyleFærøy, F. L., Yamin, M. M., Shukla, A., & Katt, B. (2023). Automatic Verification and Execution of Cyber Attack on IoT Devices. Sensors, 23(2), 733. https://doi.org/10.3390/s23020733








