Leveraging Blockchain Technology for Ensuring Security and Privacy Aspects in Internet of Things: A Systematic Literature Review
Abstract
:1. Introduction
2. Overview
2.1. IoT
2.1.1. Architecture
2.1.2. Characteristics
2.1.3. Challenges
- When using WSN:
- –
- Physical/Link layer: Synchronization, selective forwarding, replay attacks.
- –
- Network/Transport layer: Sinkhole, false routing, eavesdropping attacks.
- –
- Application layer: Buffer overflow and injection attacks.
- When using RFID:
- –
- Physical/Link layer: Replay, sybil, passive interference attacks.
- –
- Network/Transport layer: Eavesdropping, impersonation, spoofing attacks.
- –
- Application layer: Tag modification, buffer overflow, injection attacks.
2.2. Blockchain
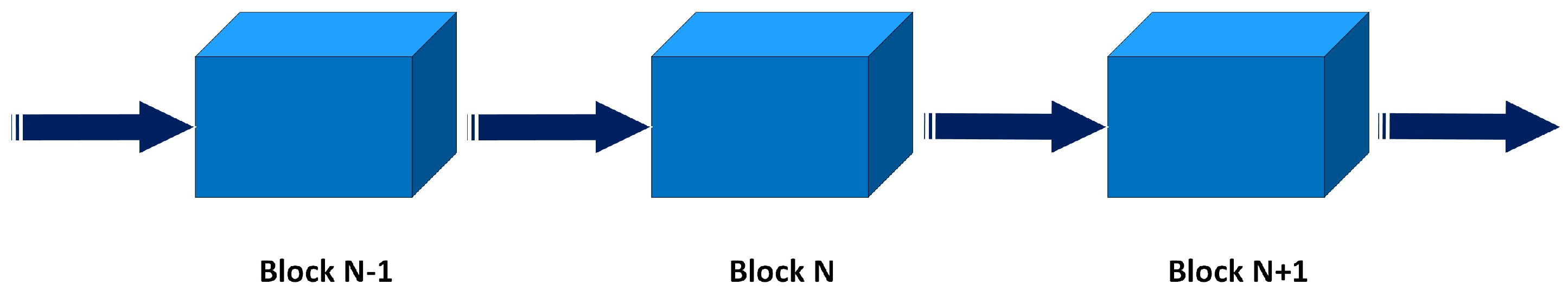
2.2.1. Architecture
2.2.2. Consensus Algorithms
2.2.3. Types of Blockchains
2.3. Challenges of Integrating Blockchain Technology and IoT
3. Review Methodology
- IEEE Explore Digital Library;
- ScienceDirect;
- SpringerLink;
- ACM Digital Library;
- MDPI;
- Wiley/Hindawi.
3.1. Search Strategy
3.2. Study Eligibility Criteria
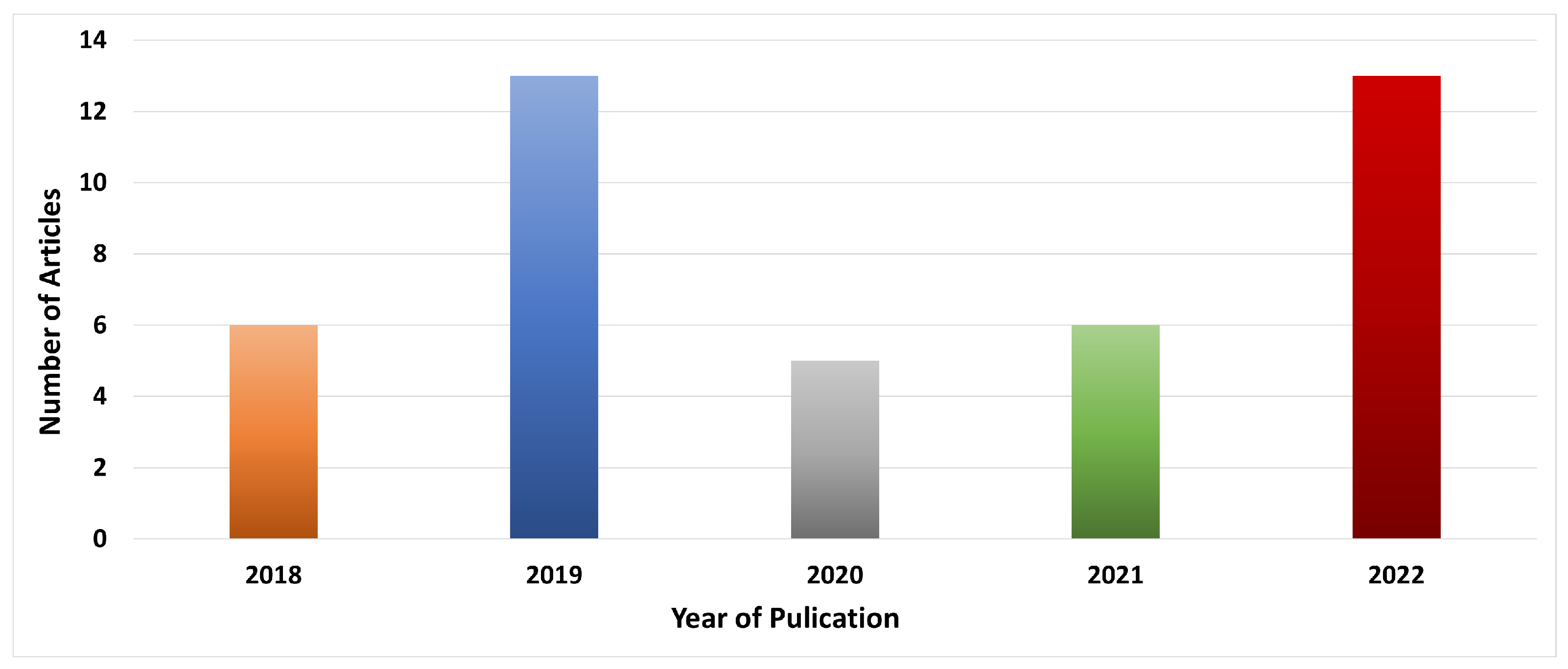
3.3. Selection Results
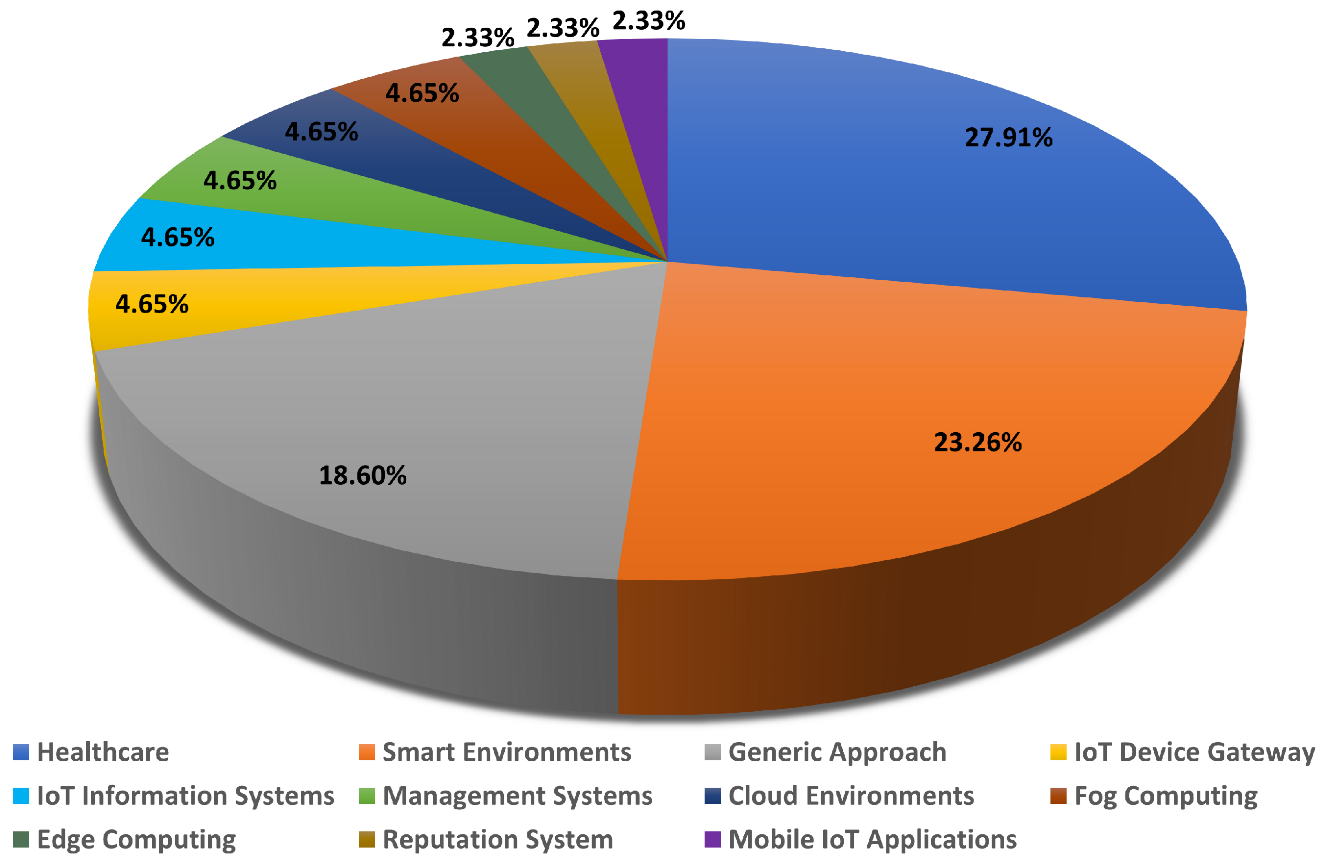
4. Findings
4.1. Generic Approaches
4.2. Healthcare
4.3. Smart Environments
4.3.1. Smart Home
4.3.2. Smart City
4.3.3. Smart Factory
4.3.4. Smart Traveling
4.3.5. Smart Agriculture
4.4. IoT Device Gateway
4.5. IoT Information Systems
4.6. Management Systems
4.7. Other Works
4.7.1. Cloud Environments
4.7.2. Fog Computing
4.7.3. Edge Computing
4.7.4. Reputation Systems
4.7.5. Mobile IoT Applications
- It is important to realize a mechanism to handle exchanging messages among network nodes to reduce the overhead.
- Eliminate using a centralized server that conflicts with the decentralization feature which blockchain technology offers.
- When designing a BIoT scheme, the scalability and confidentiality of data must be proven to consider the approach efficient.
- In several studies, the blockchain side is neglected, and there is insufficient information about the type of blockchain, platform, and consensus algorithm.
- It is crucial to evaluate and validate the proposed approach regarding security and resiliency against different attacks.
- The computation cost and communication overhead must be deeply investigated and studied.
- Although some studies enhance network privacy and security, it affects network performance metrics negatively, such as throughput and latency.
- A standardized evaluation manner needs to be followed; a public blockchain platform can be used to compare the performance of different proposed approaches.
5. Lessons Learned
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| IP | Internet Protocol |
| TCP | Transmission Control Protocol |
| UDP | User Datagram Protocol |
| P2P | Peer-to-Peer |
| SPI | Serial Peripheral Interface |
| IGMP | Internet Group Management Protocol |
| ICMP | Internet Control Message Protocol |
| REST | Representational State Transfer |
| DDP | Distributed Data Protocol |
| OSPF | Open Shortest Path First |
| IGP | Interior Gateway Protocol |
| AS | Autonomous System |
| WSN | Wireless Sensor Network |
| RFID | Radio Frequency Identification |
| PoW | Proof of Work |
| PoS | Proof of Stake |
| DPoS | Delegated Proof of Stake |
| TaPoS | Transactions as Proof of Stake |
| BFT | Byzantine Fault Tolerance |
| PBFT | Practical Byzantine Fault Tolerance |
| DBFT | Delegated BFT |
| PoA | Proof of Authority |
| PoSV | Proof-of-Stake-Velocity |
| PoP | Proof-of-Personhood |
| PoB | Proof of Bandwidth |
| PoET | Proof of Elapsed Time |
| SCP | Stellar Consensus Protocol |
| PKC | Public Key Cryptography |
| PKC | Public Key Cryptography |
| THS | Threshold signature |
| TPS | Transactions Per Second |
| PoV | Proof of Vote |
| PoT | Proof-of-Trust |
| LSB | Lightweight Scalable Blockchain |
| ELIB | Efficient Lightweight integrated Blockchain |
| SGD | Stochastic Gradient Descent |
| LSB | Least Significant Bit |
| IPFS | InterPlanetary File System |
| DTC | Distributed Time-based |
| ECC | Elliptic Curve Cryptography |
| PDA | Personal Digital Assistance |
| IHM | IoT Health Manager |
| DAG | Directed Acyclic Graph |
| CV | Cardinal Value |
| DV | Data Validity |
| CD | Contact Degree |
| ACC | Access Control Contract |
| JC | Judge Contract |
| DTM | Distributed Throughput Management |
| CH | Cluster Head |
| OBMs | Overlay Block Managers |
| DAC | Discretionary Access Control Models |
| MAC | Mandatory Access Control Model |
| MSP | Membership Service Provider |
| JCC | JointCloud Computing |
| JCCE | JointCloud Collaboration Environment |
| DO | Data Owner |
| KGC | Key Generate Center |
| ACL | Access Control List |
| ECIES | Elliptic Curve Integrated Encryption Scheme |
| MLNCML | Mixed Linear and Nonlinear Spatiotemporal Chaotic Systems |
| PEP | Policy Enforcement Point |
| CCBCM | Consortium Blockchain Manager |
| AEBCM | Aggregated Edge Blockchain Manager |
| EBCMs | Edge Blockchain Managers |
| PoEoI | Proof-of-Epidemiology-of-Interest |
| IHT | Information Hiding Techniques |
| SSI | Self-Sovereign Identity |
| VC | Verifiable Credential |
| DID | Decentralized ID |
| ABAC | Attribute-based Access Control |
| RBAC | Role-based Access Control |
| DSMAC | Decentralized Self-Management of data Access Control |
| ICN | Information-Centric Networking |
| IBE | Identity-Based Encryption |
| PRE | Proxy Re-encryption |
| ZK-SNARKs | Zero-Knowledge Succinct Non-Interactive Argument of Knowledge |
References
- Agiwal, M.; Saxena, N.; Roy, A. Towards connected living: 5G enabled Internet of Things (IoT). IETE Tech. Rev. 2019, 36, 190–202. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT security: Review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R. Blockchain in internet of things: Challenges and solutions. arXiv 2016, arXiv:1608.05187. [Google Scholar]
- Tseng, L.; Wong, L.; Otoum, S.; Aloqaily, M.; Othman, J.B. Blockchain for managing heterogeneous internet of things: A perspective architecture. IEEE Netw. 2020, 34, 16–23. [Google Scholar] [CrossRef]
- Mendez, D.M.; Papapanagiotou, I.; Yang, B. Internet of things: Survey on security and privacy. arXiv 2017, arXiv:1707.01879. [Google Scholar]
- Zhao, K.; Ge, L. A survey on the internet of things security. In Proceedings of the 2013 Ninth International Conference on Computational Intelligence and Security, Emeishan, China, 14–15 December 2013; pp. 663–667. [Google Scholar]
- Borgia, E. The Internet of Things vision: Key features, applications and open issues. Comput. Commun. 2014, 54, 1–31. [Google Scholar] [CrossRef]
- Plósz, S.; Schmittner, C.; Varga, P. Combining safety and security analysis for industrial collaborative automation systems. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Trento, Italy, 13–15 September 2017; Springer: Cham, Switzerland, 2017; pp. 187–198. [Google Scholar]
- Kozma, D.; Varga, P. Supporting digital supply chains by iot frameworks: Collaboration, control, combination. Infocommun. J. 2020, 12, 22–32. [Google Scholar] [CrossRef]
- Alfandi, O.; Khanji, S.; Ahmad, L.; Khattak, A. A survey on boosting IoT security and privacy through blockchain. Clust. Comput. 2020, 24, 37–55. [Google Scholar] [CrossRef]
- Subramanian, H. Decentralized blockchain-based electronic marketplaces. Commun. ACM 2017, 61, 78–84. [Google Scholar] [CrossRef]
- Wang, Q.; Zhu, X.; Ni, Y.; Gu, L.; Zhu, H. Blockchain for the IoT and industrial IoT: A review. Internet Things 2020, 10, 100081. [Google Scholar] [CrossRef]
- Panarello, A.; Tapas, N.; Merlino, G.; Longo, F.; Puliafito, A. Blockchain and iot integration: A systematic survey. Sensors 2018, 18, 2575. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Lo, S.K.; Liu, Y.; Chia, S.Y.; Xu, X.; Lu, Q.; Zhu, L.; Ning, H. Analysis of blockchain solutions for IoT: A systematic literature review. IEEE Access 2019, 7, 58822–58835. [Google Scholar] [CrossRef]
- Ye, C.; Cao, W.; Chen, S. Security challenges of blockchain in Internet of things: Systematic literature review. Trans. Emerg. Telecommun. Technol. 2020, 32, e4177. [Google Scholar] [CrossRef]
- El-Masri, M.; Hussain, E.M.A. Blockchain as a mean to secure Internet of Things ecosystems–a systematic literature review. J. Enterp. Inf. Manag. 2021, 34, 1371–1405. [Google Scholar] [CrossRef]
- Tsang, Y.P.; Wu, C.H.; Ip, W.; Shiau, W.L. Exploring the intellectual cores of the blockchain—Internet of Things (BIoT). J. Enterp. Inf. Manag. 2021, 24, 1287–1317. [Google Scholar] [CrossRef]
- Lu, Y. Implementing blockchain in information systems: A review. Enterp. Inf. Syst. 2022, 16, 2008513. [Google Scholar] [CrossRef]
- Varga, P.; Peto, J.; Franko, A.; Balla, D.; Haja, D.; Janky, F.; Soos, G.; Ficzere, D.; Maliosz, M.; Toka, L. 5G support for Industrial IoT Applications—Challenges, Solutions, and Research gaps. Sensors 2020, 20, 828. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Mistry, I.; Tanwar, S.; Tyagi, S.; Kumar, N. Blockchain for 5G-enabled IoT for industrial automation: A systematic review, solutions, and challenges. Mech. Syst. Signal Process. 2020, 135, 106382. [Google Scholar] [CrossRef]
- Jovović, I.; Husnjak, S.; Forenbacher, I.; Maček, S. Innovative application of 5G and blockchain technology in Industry 4.0. EAI Endorsed Trans. Ind. Netw. Intell. Syst. 2019, 6, e4. [Google Scholar] [CrossRef]
- Hewa, T.M.; Kalla, A.; Nag, A.; Ylianttila, M.E.; Liyanage, M. Blockchain for 5G and IoT: Opportunities and challenges. In Proceedings of the 2020 IEEE Eighth International Conference on Communications and Networking (ComNet), Hammamet, Tunisia, 27–30 October 2020; pp. 1–8. [Google Scholar]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Blockchain for 5G and beyond networks: A state of the art survey. J. Netw. Comput. Appl. 2020, 166, 102693. [Google Scholar] [CrossRef]
- Chaer, A.; Salah, K.; Lima, C.; Ray, P.P.; Sheltami, T. Blockchain for 5G: Opportunities and challenges. In Proceedings of the 2019 IEEE Globecom Workshops (GC Wkshps), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Jovović, I.; Husnjak, S.; Forenbacher, I.; Maček, S. 5G, blockchain and ipfs: A general survey with possible innovative applications in industry 4.0. In Proceedings of the MMS 2018: 3rd EAI International Conference on Management of Manufacturing Systems, Dubrovnik, Croatia, 6–8 November 2018; European Alliance for Innovation: Ghent, Belgium, 2018; Volume 2, p. 157. [Google Scholar]
- French, A.; Shim, J.; Risius, M.; Larsen, K.R.; Jain, H. The 4th Industrial Revolution Powered by the Integration of AI, Blockchain, and 5G. Commun. Assoc. Inf. Syst. 2021, 49, 6. [Google Scholar] [CrossRef]
- Vermesan, O.; Friess, P.; Guillemin, P.; Gusmeroli, S.; Sundmaeker, H.; Bassi, A.; Jubert, I.S.; Mazura, M.; Harrison, M.; Eisenhauer, M.; et al. Internet of things strategic research roadmap. In Internet of Things-Global Technological and Societal Trends from Smart Environments and Spaces to Green ICT; River Publishers: Roma, Italy, 2009. [Google Scholar]
- Noor, M.b.M.; Hassan, W.H. Current research on Internet of Things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar] [CrossRef]
- Jabraeil Jamali, M.; Bahrami, B.; Heidari, A.; Allahverdizadeh, P.; Norouzi, F. Towards the Internet of Things: Architectures, Security, and Applications; Springer Nature Switzerland AG: Cham, Switzerland, 2019. [Google Scholar]
- Darianian, M.; Michael, M.P. Smart home mobile RFID-based Internet-of-Things systems and services. In Proceedings of the 2008 International Conference on Advanced Computer Theory and Engineering, Phuket, Thailand, 20–22 December 2008; pp. 116–120. [Google Scholar]
- Varga, P.; Plosz, S.; Soos, G.; Hegedus, C. Security threats and issues in automation IoT. In Proceedings of the 2017 IEEE 13th International Workshop on Factory Communication Systems (WFCS), Trondheim, Norway, 31 May–2 June 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Sikder, A.K.; Petracca, G.; Aksu, H.; Jaeger, T.; Uluagac, A.S. A survey on sensor-based threats to internet-of-things (iot) devices and applications. arXiv 2018, arXiv:1802.02041. [Google Scholar]
- Al-Sarawi, S.; Anbar, M.; Alieyan, K.; Alzubaidi, M. Internet of Things (IoT) communication protocols: Review. In Proceedings of the 2017 8th International Conference on Information Technology (ICIT), Amman, Jordan, 17–18 May 2017; pp. 685–690. [Google Scholar]
- Patel, K.K.; Patel, S.M.; Scholar, P. Internet of things-IOT: Definition, characteristics, architecture, enabling technologies, application & future challenges. Int. J. Eng. Sci. Comput. 2016, 6, 6122–6131. [Google Scholar]
- Atlam, H.F.; Wills, G.B. Technical aspects of blockchain and IoT. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2019; Volume 115, pp. 1–39. [Google Scholar]
- Fortino, G.; Savaglio, C.; Palau, C.E.; de Puga, J.S.; Ganzha, M.; Paprzycki, M.; Montesinos, M.; Liotta, A.; Llop, M. Towards multi-layer interoperability of heterogeneous IoT platforms: The INTER-IoT approach. In Integration, Interconnection, and Interoperability of IoT Systems; Springer: Cham, Stwitzerland, 2018; pp. 199–232. [Google Scholar]
- Aloi, G.; Caliciuri, G.; Fortino, G.; Gravina, R.; Pace, P.; Russo, W.; Savaglio, C. Enabling IoT interoperability through opportunistic smartphone-based mobile gateways. J. Netw. Comput. Appl. 2017, 81, 74–84. [Google Scholar] [CrossRef]
- Blackstock, M.; Lea, R. IoT interoperability: A hub-based approach. In Proceedings of the 2014 International Conference on the Internet of Things (IOT), Cambridge, MA, USA, 6–8 October 2014; pp. 79–84. [Google Scholar]
- Bröring, A.; Schmid, S.; Schindhelm, C.K.; Khelil, A.; Käbisch, S.; Kramer, D.; Le Phuoc, D.; Mitic, J.; Anicic, D.; Teniente, E. Enabling IoT ecosystems through platform interoperability. IEEE Softw. 2017, 34, 54–61. [Google Scholar] [CrossRef] [Green Version]
- Xiao, G.; Guo, J.; Da Xu, L.; Gong, Z. User interoperability with heterogeneous IoT devices through transformation. IEEE Trans. Ind. Inform. 2014, 10, 1486–1496. [Google Scholar] [CrossRef]
- Biswas, S.; Sharif, K.; Li, F.; Nour, B.; Wang, Y. A scalable blockchain framework for secure transactions in IoT. IEEE Internet Things J. 2018, 6, 4650–4659. [Google Scholar] [CrossRef]
- Qiu, H.; Qiu, M.; Memmi, G.; Ming, Z.; Liu, M. A dynamic scalable blockchain based communication architecture for IoT. In Proceedings of the International Conference on Smart Blockchain, Tokyo, Japan, 10–12 December 2018; Springer: Cham, Swtizerland, 2018; pp. 159–166. [Google Scholar]
- Ruta, M.; Scioscia, F.; Ieva, S.; Capurso, G.; Di Sciascio, E. Semantic blockchain to improve scalability in the internet of things. Open J. Internet Things 2017, 3, 46–61. [Google Scholar]
- Dukkipati, C.; Zhang, Y.; Cheng, L.C. Decentralized, blockchain based access control framework for the heterogeneous internet of things. In Proceedings of the 3rd ACM Workshop on Attribute-Based Access Control, Tempe, AZ, USA, 3 March 2018; pp. 61–69. [Google Scholar]
- Alzubaidi, M.; Anbar, M.; Al-Saleem, S.; Al-Sarawi, S.; Alieyan, K. Review on mechanisms for detecting sinkhole attacks on RPLs. In Proceedings of the 2017 8th International Conference on Information Technology (ICIT), Amman, Jordan, 17–18 May 2017; pp. 369–374. [Google Scholar]
- Papp, D.; Tamás, K.; Buttyán, L. Iot hacking–a primer. Infocommun. J. 2019, 11, 2–13. [Google Scholar] [CrossRef]
- Alzubaidi, M.; Anbar, M.; Hanshi, S.M. Neighbor-passive monitoring technique for detecting sinkhole attacks in RPL networks. In Proceedings of the 2017 International Conference on Computer Science and Artificial Intelligence, Jakarta, Indonesiac, 5–7 December 2017; pp. 173–182. [Google Scholar]
- Plósz, S.; Hegedűs, C.; Varga, P. Advanced security considerations in the arrowhead framework. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Trondheim, Norway, 20–23 September 2016; Springer: Cham, Swtizerland, 2016; pp. 234–245. [Google Scholar]
- Maksuti, S.; Zsilak, M.; Tauber, M.; Delsing, J. Security and autonomic management in system of systems. Infocommun. J. 2021, 13, 66–75. [Google Scholar] [CrossRef]
- Meidan, Y.; Sachidananda, V.; Peng, H.; Sagron, R.; Elovici, Y.; Shabtai, A. A novel approach for detecting vulnerable IoT devices connected behind a home NAT. Comput. Secur. 2020, 97, 101968. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef] [Green Version]
- Mohanta, B.K.; Jena, D.; Satapathy, U.; Patnaik, S. Survey on IoT security: Challenges and solution using machine learning, artificial intelligence and blockchain technology. Internet Things 2020, 11, 100227. [Google Scholar] [CrossRef]
- Patil, P.; Sangeetha, M.; Bhaskar, V. Blockchain for IoT access control, security and privacy: A review. Wirel. Pers. Commun. 2021, 117, 1815–1834. [Google Scholar] [CrossRef]
- Reyna, A.; Martín, C.; Chen, J.; Soler, E.; Díaz, M. On blockchain and its integration with IoT. Challenges and opportunities. Future Gener. Comput. Syst. 2018, 88, 173–190. [Google Scholar] [CrossRef]
- Buterin, V. Ethereum white paper. GitHub Repos. 2013, 1, 22–23. [Google Scholar]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the 13th EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Roy, S.; Ashaduzzaman, M.; Hassan, M.; Chowdhury, A.R. Blockchain for IoT security and management: Current prospects, challenges and future directions. In Proceedings of the 2018 5th International Conference on Networking, Systems and Security (NSysS), Dhaka, Bangladesh, 18–20 December 2018; pp. 1–9. [Google Scholar]
- Cachin, C.; Vukolić, M. Blockchain consensus protocols in the wild. arXiv 2017, arXiv:1707.01873. [Google Scholar]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. Available online: https://www.debr.io/article/21260.pdf (accessed on 7 November 2021).
- Larimer, D. Transactions as Proof-of-Stake. 2013. Available online: https://cryptochainuni.com/wp-content/uploads/Invictus-Innovations-Transactions-As-Proof-Of-Stake.pdf (accessed on 12 November 2021).
- Larimer, D. Delegated proof-of-stake (dpos). Bitshare Whitepaper 2014, 81, 85. [Google Scholar]
- Larimer, D. Delegated Proof-of-Stake Consensus. 2018. Available online: https://how.bitshares.works/en/master/technology/dpos.html (accessed on 18 November 2021).
- Bentov, I.; Lee, C.; Mizrahi, A.; Rosenfeld, M. Proof of activity: Extending bitcoin’s proof of work via proof of stake [extended abstract] y. ACM SIGMETRICS Perform. Eval. Rev. 2014, 42, 34–37. [Google Scholar] [CrossRef]
- Vukolić, M. The quest for scalable blockchain fabric: Proof-of-work vs. BFT replication. In Proceedings of the International Workshop on Open Problems in Network Security, Zurich, Switzerland, 29 October 2015; Springer: Cham, Switzerland, 2015; pp. 112–125. [Google Scholar]
- Kotla, R.; Alvisi, L.; Dahlin, M.; Clement, A.; Wong, E. Zyzzyva: Speculative byzantine fault tolerance. In Proceedings of the 21st ACM SIGOPS Symposium on Operating Systems Principles, Stevenson, WA, USA, 14–17 October 2007; pp. 45–58. [Google Scholar]
- Kotla, R.; Alvisi, L.; Dahlin, M.; Clement, A.; Wong, E. Zyzzyva: Speculative byzantine fault tolerance. ACM Trans. Comput. Syst. 2010, 27, 1–39. [Google Scholar] [CrossRef]
- Copeland, C.; Zhong, H. Tangaroa: A Byzantine Fault Tolerant Raft. 2016. Available online: https://www.scs.stanford.edu/14au-cs244b/labs/projects/copeland_zhong.pdf (accessed on 13 November 2021).
- Ren, L. Proof of stake velocity: Building the social currency of the digital age. Self-Published White Paper. 2014. Available online: https://cryptochainuni.com/wp-content/uploads/Reddcoin-Proof-of-Stake-Velocity.pdf (accessed on 17 November 2021).
- P4Titan. Slimcoin: A Peer-To-Peer Crypto-Currency with Proof-of-Burn. Available online: http://www.doc.ic.ac.uk/~ids/realdotdot/crypto_papers_etc_worth_reading/proof_of_burn/slimcoin_whitepaper.pdf (accessed on 14 November 2021).
- Borge, M.; Kokoris-Kogias, E.; Jovanovic, P.; Gasser, L.; Gailly, N.; Ford, B. Proof-of-personhood: Redemocratizing permissionless cryptocurrencies. In Proceedings of the 2017 IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Paris, France, 26–28 April 2017; pp. 23–26. [Google Scholar]
- Ghosh, M.; Richardson, M.; Ford, B.; Jansen, R. A TorPath to TorCoin: Proof-of-Bandwidth Altcoins for Compensating Relays; Technical Report; Naval Research Lab: Washington, DC, USA, 2014. [Google Scholar]
- Intel. Proof of Elapsed Time (PoET). 2017. Available online: http://intelledger.github.io/ (accessed on 14 November 2021).
- Mazieres, D. The stellar consensus protocol: A federated model for internet-level consensus. Stellar Dev. Found. 2015, 32, 1–45. [Google Scholar]
- Eyal, I.; Gencer, A.E.; Sirer, E.G.; Van Renesse, R. Bitcoin-ng: A scalable blockchain protocol. In Proceedings of the 13th USENIX Symposium on Networked Systems Design and Implementation (NSDI 16), Santa Clara, CA, USA, 16–18 March 2016; pp. 45–59. [Google Scholar]
- Cachin, C.; Schubert, S.; Vukolić, M. Non-determinism in byzantine fault-tolerant replication. arXiv 2016, arXiv:1603.07351. [Google Scholar]
- Schwartz, D.; Youngs, N.; Britto, A. The ripple protocol consensus algorithm. Ripple Labs Inc White Pap. 2014, 5, 151. [Google Scholar]
- Kwon, J. Tendermint: Consensus without Mining. 2014. Available online: https://www.weusecoins.com/assets/pdf/library/Tendermint%20Consensus%20without%20Mining.pdf (accessed on 14 November 2021).
- Zubaydi, H.D.; Chong, Y.W.; Ko, K.; Hanshi, S.M.; Karuppayah, S. A review on the role of blockchain technology in the healthcare domain. Electronics 2019, 8, 679. [Google Scholar] [CrossRef] [Green Version]
- Wu, M.; Wang, K.; Cai, X.; Guo, S.; Guo, M.; Rong, C. A comprehensive survey of blockchain: From theory to IoT applications and beyond. IEEE Internet Things J. 2019, 6, 8114–8154. [Google Scholar] [CrossRef]
- Brotsis, S.; Limniotis, K.; Bendiab, G.; Kolokotronis, N.; Shiaeles, S. On the suitability of blockchain platforms for IoT applications: Architectures, security, privacy, and performance. Comput. Netw. 2021, 191, 108005. [Google Scholar] [CrossRef]
- Da Xu, L.; Lu, Y.; Li, L. Embedding blockchain technology into IoT for security: A survey. IEEE Internet Things J. 2021, 8, 10452–10473. [Google Scholar]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, X.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Bamakan, S.M.H.; Motavali, A.; Bondarti, A.B. A survey of blockchain consensus algorithms performance evaluation criteria. Expert Syst. Appl. 2020, 154, 113385. [Google Scholar] [CrossRef]
- Varga, P.; Janky, F. Blockchains for Industrial IoT—A Tutorial. RG Prepr. 2019. [Google Scholar] [CrossRef]
- Frankó, A.; Oláh, B.; Sass, Z.; Hegedüs, C.; Varga, P. Towards CBDC-supported Smart Contracts for Industrial Stakeholders. In Proceedings of the 2022 IEEE 5th International Conference on Industrial Cyber-Physical Systems (ICPS), Online, 24–26 May 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Bui, N.; Zorzi, M. Health care applications: A solution based on the internet of things. In Proceedings of the 4th International Symposium on Applied Sciences in Biomedical and Communication Technologies, Barcelona, Spain, 26–29 October 2011; pp. 1–5. [Google Scholar]
- Maroufi, M.; Abdolee, R.; Tazekand, B.M. On the convergence of blockchain and internet of things (iot) technologies. arXiv 2019, arXiv:1904.01936. [Google Scholar]
- Longchamp, Y.; Deshpande, S.; Mehra, U. The Blockchain Trilemma. 2020. Available online: https://theblockchaintest.com/uploads/resources/SEBA%20-%20The%20Blockchain%20Trilema%20-%202020%20-%20Oct.pdf (accessed on 3 January 2023).
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering. 2007. Available online: https://www.elsevier.com/__data/promis_misc/525444systematicreviewsguide.pdf (accessed on 7 December 2021).
- Jayasinghe, U.; Lee, G.M.; MacDermott, Á.; Rhee, W.S. Trustchain: A privacy preserving blockchain with edge computing. Wirel. Commun. Mob. Comput. 2019, 2019, 2014697. [Google Scholar] [CrossRef] [Green Version]
- Mohanta, B.K.; Jena, D.; Ramasubbareddy, S.; Daneshmand, M.; Gandomi, A.H. Addressing security and privacy issues of IoT using blockchain technology. IEEE Internet Things J. 2020, 8, 881–888. [Google Scholar] [CrossRef]
- Sun, S.; Chen, S.; Du, R.; Li, W.; Qi, D. Blockchain Based Fine-Grained and Scalable Access Control for IoT Security and Privacy. In Proceedings of the 2019 IEEE Fourth International Conference on Data Science in Cyberspace (DSC), Hangzhou, China, 23–25 June 2019; pp. 598–603. [Google Scholar]
- Nguyen, T.D.; Pham, H.A.; Thai, M.T. Leveraging blockchain to enhance data privacy in IoT-based applications. In Proceedings of the International Conference on Computational Social Networks, Shanghai, China, 18–20 December 2018; Springer: Cham, Switzerland, 2018; pp. 211–221. [Google Scholar]
- Jiang, W.; Li, H.; Xu, G.; Wen, M.; Dong, G.; Lin, X. PTAS: Privacy-preserving thin-client authentication scheme in blockchain-based PKI. Future Gener. Comput. Syst. 2019, 96, 185–195. [Google Scholar] [CrossRef]
- Fan, S.; Song, L.; Sang, C. Research on privacy protection in IoT system based on blockchain. In Proceedings of the International Conference on Smart Blockchain, Birmingham, UK, 11–13 October 2019; Springer: Cham, Switzerland, 2019; pp. 1–10. [Google Scholar]
- Du, M.; Wang, K.; Liu, Y.; Qian, K.; Sun, Y.; Xu, W.; Guo, S. Spacechain: A three-dimensional blockchain architecture for IoT security. IEEE Wirel. Commun. 2020, 27, 38–45. [Google Scholar] [CrossRef]
- Ye, J.; Kang, X.; Liang, Y.C.; Sun, S. A Trust-Centric Privacy-Preserving Blockchain for Dynamic Spectrum Management in IoT Networks. IEEE Internet Things J. 2022, 9, 13263–13278. [Google Scholar] [CrossRef]
- Abdi, A.I.; Eassa, F.E.; Jambi, K.; Almarhabi, K.; Khemakhem, M.; Basuhail, A.; Yamin, M. Hierarchical Blockchain-Based Multi-Chaincode Access Control for Securing IoT Systems. Electronics 2022, 11, 711. [Google Scholar] [CrossRef]
- Dwivedi, A.D.; Srivastava, G.; Dhar, S.; Singh, R. A decentralized privacy-preserving healthcare blockchain for IoT. Sensors 2019, 19, 326. [Google Scholar] [CrossRef] [Green Version]
- Ray, P.P.; Chowhan, B.; Kumar, N.; Almogren, A. BIoTHR: Electronic Health Record Servicing Scheme in IoT-Blockchain Ecosystem. IEEE Internet Things J. 2021, 8, 10857–10872. [Google Scholar] [CrossRef]
- Hossein, K.M.; Esmaeili, M.E.; Dargahi, T.; Khonsari, A. Blockchain-based privacy-preserving healthcare architecture. In Proceedings of the 2019 IEEE Canadian Conference of Electrical and Computer Engineering (CCECE), Edmonton, AB, Canada, 5–8 May 2019; pp. 1–4. [Google Scholar]
- Xu, J.; Xue, K.; Li, S.; Tian, H.; Hong, J.; Hong, P.; Yu, N. Healthchain: A blockchain-based privacy preserving scheme for large-scale health data. IEEE Internet Things J. 2019, 6, 8770–8781. [Google Scholar] [CrossRef]
- Badr, S.; Gomaa, I.; Abd-Elrahman, E. Multi-tier blockchain framework for IoT-EHRs systems. Procedia Comput. Sci. 2018, 141, 159–166. [Google Scholar] [CrossRef]
- Shen, M.; Deng, Y.; Zhu, L.; Du, X.; Guizani, N. Privacy-preserving image retrieval for medical IoT systems: A blockchain-based approach. IEEE Netw. 2019, 33, 27–33. [Google Scholar] [CrossRef]
- Jia, X.; Luo, M.; Wang, H.; Shen, J.; He, D. A Blockchain-Assisted Privacy-Aware Authentication Scheme for Internet of Medical Things. IEEE Internet Things J. 2022, 9, 21838–21850. [Google Scholar] [CrossRef]
- Azbeg, K.; Ouchetto, O.; Andaloussi, S.J. Access Control and Privacy-Preserving Blockchain-Based System for Diseases Management. IEEE Trans. Comput. Soc. Syst. 2022. [Google Scholar] [CrossRef]
- Samuel, O.; Omojo, A.B.; Mohsin, S.M.; Tiwari, P.; Gupta, D.; Band, S.S. An Anonymous IoT-Based E-Health Monitoring System Using Blockchain Technology. IEEE Syst. J. 2022. [Google Scholar] [CrossRef]
- Khan, A.A.; Wagan, A.A.; Laghari, A.A.; Gilal, A.R.; Aziz, I.A.; Talpur, B.A. BIoMT: A state-of-the-art consortium serverless network architecture for healthcare system using blockchain smart contracts. IEEE Access 2022, 10, 78887–78898. [Google Scholar] [CrossRef]
- El Azzaoui, A.; Chen, H.; Kim, S.H.; Pan, Y.; Park, J.H. Blockchain-Based Distributed Information Hiding Framework for Data Privacy Preserving in Medical Supply Chain Systems. Sensors 2022, 22, 1371. [Google Scholar] [CrossRef] [PubMed]
- Saidi, H.; Labraoui, N.; Ari, A.A.A.; Maglaras, L.A.; Emati, J.H.M. DSMAC: Privacy-aware Decentralized Self-Management of data Access Control based on blockchain for health data. IEEE Access 2022, 10, 101011–101028. [Google Scholar] [CrossRef]
- Cha, S.C.; Chen, J.F.; Su, C.; Yeh, K.H. A blockchain connected gateway for BLE-based devices in the internet of things. IEEE Access 2018, 6, 24639–24649. [Google Scholar] [CrossRef]
- Šarac, M.; Pavlović, N.; Bacanin, N.; Al-Turjman, F.; Adamović, S. Increasing privacy and security by integrating a Blockchain Secure Interface into an IoT Device Security Gateway Architecture. Energy Rep. 2021, 7, 8075–8082. [Google Scholar] [CrossRef]
- Zhao, Q.; Chen, S.; Liu, Z.; Baker, T.; Zhang, Y. Blockchain-based privacy-preserving remote data integrity checking scheme for IoT information systems. Inf. Process. Manag. 2020, 57, 102355. [Google Scholar] [CrossRef]
- Si, H.; Sun, C.; Li, Y.; Qiao, H.; Shi, L. IoT information sharing security mechanism based on blockchain technology. Future Gener. Comput. Syst. 2019, 101, 1028–1040. [Google Scholar] [CrossRef]
- Carvalho, K.; Granjal, J. Security and Privacy for Mobile IoT Applications Using Blockchain. Sensors 2021, 21, 5931. [Google Scholar] [CrossRef] [PubMed]
- Mora, O.B.; Rivera, R.; Larios, V.M.; Beltrán-Ramírez, J.R.; Maciel, R.; Ochoa, A. A Use Case in Cybersecurity based in Blockchain to deal with the security and privacy of citizens and Smart Cities Cyberinfrastructures. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MO, USA, 16–19 September 2018; pp. 1–4. [Google Scholar]
- Theodorou, S.; Sklavos, N. Blockchain-based security and privacy in smart cities. In Smart Cities Cybersecurity and Privacy; Elsevier: Amsterdam, The Netherlands, 2019; pp. 21–37. [Google Scholar]
- Makhdoom, I.; Zhou, I.; Abolhasan, M.; Lipman, J.; Ni, W. PrivySharing: A blockchain-based framework for privacy-preserving and secure data sharing in smart cities. Comput. Secur. 2020, 88, 101653. [Google Scholar] [CrossRef]
- Wan, J.; Li, J.; Imran, M.; Li, D.; Fazal-e-Amin. A blockchain-based solution for enhancing security and privacy in smart factory. IEEE Trans. Ind. Inform. 2019, 15, 3652–3660. [Google Scholar] [CrossRef]
- Dang, T.L.N.; Nguyen, M.S. An approach to data privacy in smart home using blockchain technology. In Proceedings of the 2018 International Conference on Advanced Computing and Applications (ACOMP), Ho Chi Minh City, Vietnam, 27–29 November 2018; pp. 58–64. [Google Scholar]
- Mohanty, S.N.; Ramya, K.; Rani, S.S.; Gupta, D.; Shankar, K.; Lakshmanaprabu, S.; Khanna, A. An efficient Lightweight integrated Blockchain (ELIB) model for IoT security and privacy. Future Gener. Comput. Syst. 2020, 102, 1027–1037. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. LSB: A Lightweight Scalable Blockchain for IoT security and anonymity. J. Parallel Distrib. Comput. 2019, 134, 180–197. [Google Scholar] [CrossRef]
- Qashlan, A.; Nanda, P.; He, X.; Mohanty, M. Privacy-Preserving Mechanism in Smart Home Using Blockchain. IEEE Access 2021, 9, 103651–103669. [Google Scholar] [CrossRef]
- Chen, W.; Ma, M.; Ye, Y.; Zheng, Z.; Zhou, Y. IoT service based on jointcloud blockchain: The case study of smart traveling. In Proceedings of the 2018 IEEE Symposium on Service-Oriented System Engineering (SOSE), Bamberg, Germany, 26–29 March 2018; pp. 216–221. [Google Scholar]
- Liu, Y.; Zhang, J.; Zhan, J. Privacy protection for fog computing and the internet of things data based on blockchain. Clust. Comput. 2021, 24, 1331–1345. [Google Scholar] [CrossRef]
- Rizzardi, A.; Sicari, S.; Miorandi, D.; Coen-Porisini, A. Securing the access control policies to the Internet of Things resources through permissioned blockchain. Concurr. Comput. Pract. Exp. 2022, 34, e6934. [Google Scholar] [CrossRef]
- Debe, M.; Salah, K.; Rehman, M.H.U.; Svetinovic, D. IoT public fog nodes reputation system: A decentralized solution using Ethereum blockchain. IEEE Access 2019, 7, 178082–178093. [Google Scholar] [CrossRef]
- Agyekum, K.O.B.O.; Xia, Q.; Sifah, E.B.; Cobblah, C.N.A.; Xia, H.; Gao, J. A proxy re-encryption approach to secure data sharing in the Internet of things based on blockchain. IEEE Syst. J. 2021, 16, 1685–1696. [Google Scholar] [CrossRef]
- Feng, T.; Yang, P.; Liu, C.; Fang, J.; Ma, R. Blockchain Data Privacy Protection and Sharing Scheme Based on Zero-Knowledge Proof. Wirel. Commun. Mob. Comput. 2022, 2022, 1040662. [Google Scholar] [CrossRef]
- Chaganti, R.; Varadarajan, V.; Gorantla, V.S.; Gadekallu, T.R.; Ravi, V. Blockchain-Based Cloud-Enabled Security Monitoring Using Internet of Things in Smart Agriculture. Future Internet 2022, 14, 250. [Google Scholar] [CrossRef]
- Venkatraman, S.; Parvin, S. Developing an IoT Identity Management System Using Blockchain. Systems 2022, 10, 39. [Google Scholar] [CrossRef]
- Yin, J.; Xiao, Y.; Pei, Q.; Ju, Y.; Liu, L.; Xiao, M.; Wu, C. SmartDID: A novel privacy-preserving identity based on blockchain for IoT. IEEE Internet Things J. 2022. [Google Scholar] [CrossRef]
- Hyperledger. Hyperledger Caliper. Available online: https://www.hyperledger.org/use/caliper (accessed on 12 December 2022).
- Banerjee, A.; Dutta, B.; Mandal, T.; Chakraborty, R.; Mondal, R. Blockchain in IoT and Beyond: Case Studies on Interoperability and Privacy. In Blockchain based Internet of Things; Springer: Singapore, 2022; pp. 113–138. [Google Scholar]
- Manoj, T.; Makkithaya, K.; Narendra, V. A Blockchain Based Decentralized Identifiers for Entity Authentication in Electronic Health Records. Cogent Eng. 2022, 9, 2035134. [Google Scholar]
- De Caro, A.; Iovino, V. jPBC: Java pairing based cryptography. In Proceedings of the 2011 IEEE Symposium on Computers and Communications (ISCC), Kerkyra, Greece, 28 June–1 July 2011; pp. 850–855. [Google Scholar]
- Kousaridas, A.; Falangitis, S.; Magdalinos, P.; Alonistioti, N.; Dillinger, M. SYSTAS: Density-based algorithm for clusters discovery in wireless networks. In Proceedings of the 2015 IEEE 26th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Hong Kong, China, 30 August–2 September 2015; pp. 2126–2131. [Google Scholar]
- Verma, S.K.; Ojha, D. A discussion on elliptic curve cryptography and its applications. Int. J. Comput. Sci. Issues 2012, 9, 74. [Google Scholar]


| Ref # | Year | Country | Publication Type | Publisher |
|---|---|---|---|---|
| [90] | 2019 | UK | Journal | Wiley–Hindawi Wireless Communications and Mobile Computing |
| [91] | 2020 | India | Journal | IEEE Internet of Things |
| [92] | 2019 | China | Conference | IEEE Fourth International Conference on Data Science in Cyberspace |
| [93] | 2018 | USA | Conference | Springer International Conference on Computational Social Networks |
| [94] | 2019 | China | Journal | Elsevier Future Generation Computer Systems |
| [95] | 2019 | China | Conference | Springer International Conference on Smart Blockchain |
| [96] | 2020 | China | Journal | IEEE Wireless Communications |
| [97] | 2022 | China | Journal | IEEE Internet of Things |
| [98] | 2022 | Saudi Arabia | Journal | MDPI Electronics |
| [99] | 2019 | Poland | Journal | MDPI Sensors |
| [100] | 2021 | India | Journal | IEEE Internet of Things |
| [101] | 2019 | Iran | Conference | IEEE Canadian Conference of Electrical and Computer Engineering |
| [102] | 2019 | China | Journal | IEEE Internet of Things |
| [103] | 2018 | Egypt | Conference | Elsevier The 9th International Conference on Emerging Ubiquitous Systems and Pervasive Networks (EUSPN) |
| [104] | 2019 | China | Journal | IEEE Network |
| [105] | 2022 | China | Journal | IEEE Internet of Things |
| [106] | 2022 | Morocco | Journal | IEEE Transactions on Computational Social Systems |
| [107] | 2022 | Nigeria | Journal | IEEE Systems Journal |
| [108] | 2022 | Pakistan | Journal | IEEE Access |
| [109] | 2022 | South Korea | Journal | MDPI Sensors |
| [110] | 2022 | Algeria | Journal | IEEE Access |
| [111] | 2018 | Taiwan | Journal | IEEE Access |
| [112] | 2021 | Serbia | Journal | Elsevier Energy Reports |
| [113] | 2020 | China | Journal | Elsevier Information Processing and Management |
| [114] | 2019 | China | Journal | Elsevier Future Generation Computer Systems |
| [115] | 2021 | Portugal | Journal | MDPI Sensors |
| [116] | 2018 | Mexico | Conference | IEEE International Smart Cities Conference (ISC2) |
| [117] | 2019 | Cyprus | Book | Elsevier Smart Cities Cybersecurity and Privacy |
| [118] | 2020 | Australia | Journal | Elsevier Computers and Security |
| [119] | 2019 | China | Journal | IEEE Transactions on Industrial Informatics |
| [120] | 2018 | Vietnam | Conference | IEEE International Conference on Advanced Computing and Applications |
| [121] | 2020 | India | Journal | Elsevier Future Generation Computer Systems |
| [122] | 2019 | Australia | Journal | Elsevier Journal of Parallel and Distributed Computing |
| [123] | 2021 | Australia | Journal | IEEE Access |
| [124] | 2018 | China | Symposium | IEEE Symposium on Service-Oriented System Engineering (SOSE) |
| [125] | 2021 | China | Journal | Springer Cluster Computing |
| [126] | 2022 | Italy | Journal | Wiley Concurrency and Computation: Practice and Experience |
| [127] | 2019 | UAE | Journal | IEEE Access |
| [128] | 2021 | China | Journal | IEEE Systems Journal |
| [129] | 2022 | China | Journal | Wiley / Hindawi Wireless Communications and Mobile Computing |
| [130] | 2022 | USA | Journal | MDPI Future Internet |
| [131] | 2022 | Australia | Journal | MDPI Systems |
| [132] | 2022 | China | Journal | IEEE Internet of Things |
| Ref # | Objective | TRL |
|---|---|---|
| [90] | TrustChain is an innovative privacy-protecting blockchain-based network to overcome the issues associated with existing IoT networks and investigates how to eliminate privacy and delay concerns while preserving IoT network resources | 2 |
| [91] | A detailed analysis is provided, including enabling technology and IoT technology integration. In a smart IoT system, a case study is implemented using an Ethereum-based blockchain technology | 5 |
| [92] | In this study, the authors presented a blockchain-based decentralized IoT system. They developed various access strategies and implement them using smart contracts | 5 |
| [93] | In order to ensure that users have full control over their data and can track how it is used by third-party services, a system model is developed. They also proposed a blockchain-based firmware update approach that helps prevent IoT device tampering from causing fraudulent data | 2 |
| [94] | Employing private information retrieval to present a Privacy-preserving Thin-client Authentication Scheme (PTAS) for IoT devices | 5 |
| [95] | Propose an efficient and secure authentication private protection scheme using blockchain technology and the AES algorithm to encrypt the original IoT information; this study provides an IoT information security protection strategy that may effectively address IoT data storage issues | 5 |
| [96] | Deal with the heterogeneity and scalability of IoT networks by proposing a three-dimensional architecture with unique data structures. In addition, they propose the 3D-GHOST consensus mechanism for spacechain | 5 |
| [97] | Propose a trust evaluation mechanism, PoT consensus algorithm, and privacy protection mechanism based on the commitment scheme and rign signature | 5 |
| [98] | This paper addresses the scalability, privacy, and security issues by introducing a multi-layer-blockchain-based solution. It eliminates the need of Trusting Third Parties (TTP) through multiple-chaincode-based access control | 5 |
| [99] | Propose a novel patient-centered electronic medical record access control framework based on modified blockchain models that take into account the IoT’s resource constraints | 2 |
| [100] | Propose a dual-layer blockchain-IoT privacy-preserving approach based on swarm exchange techniques to support the seamless and secure transmission of user data via secure swarm nodes of peer-to-peer communications | 5 |
| [101] | Propose a blockchain-based architecture for e-health applications that provides an efficient privacy-preserving access control mechanism | 2 |
| [102] | Healthchain is proposed which is a privacy-preserving scheme designed for the healthcare domain, this approach is large-scale and is used to conduct fine-grained access control for health data. Furthermore, introduce a distributed file system called InterPlanetary File System (IPFS) | 5 |
| [103] | Proposing a novel protocol named Pseudonym-Based Encryption with Different Authorities (PBE-DA), this paper aims to achieve perfect privacy-preserving EHRs in a multi-tier blockchain framework | 5 |
| [104] | This paper presents a privacy-protected blockchain-based system for medical image retrieval using layered architecture, a threat model, and a customized transaction structure | 5 |
| [105] | This work offers an architecture designed for IoMT and other possible applications. In addition, authentication schemes are introduced based on ECC and PUF to ensure the system’s privacy | 5 |
| [106] | A system that secures IoT devices in the healthcare domain using IPFS and blockchain technology. This system is designed to allow continuous monitoring for patients with chronic diseases | 5 |
| [107] | GaliMediChain is a healthcare system based on blockchain technology and garlic routing to enable secure sharing of health data (COVID-19). Furthermore, a new consensus mechanism (PoEoI) is proposed for blocks generation and miner selection processes | 5 |
| [108] | A medical Hyperledger Fabric-enabled blockchain-based architecture called BIoMT is proposed to increase the medical environemnt’s reliability while reducing the consumption of networking resources. Moreover, a customized consensus algorithm is designed to increase security and privacy | 5 |
| [109] | An implementation for critical systems to enhance privacy and security through combining Information Hiding Techniques (IHT), IoT, and blockchain technology | 5 |
| [110] | DSMAC is a decentralized system proposed to preserve the security and privacy of sharing medical records using Verifiable Credentials (VC), Decentralized Identifiers (DIDs), Attribute-Based Access Control (ABAC), Role-Based Access Control (RBAC), Self-Sovereign Identity (SSI), and blockchain | 5 |
| [111] | This approach aims to develop a blockchain-connected gateway for IoT devices that can adapt and securely retain the privacy preferences of users; security and privacy preferences can both be ensured by the proposed digital signature mechanism (PDSS) | 5 |
| [112] | This article discusses how the security gateway architecture of an IoT device can be provided with a basic interface using blockchain to allow decentralization and authentication. This offers IoT infrastructure with the required anonymity and versatility | 5 |
| [113] | By leveraging blockchain, bilinear pairing, and a lifted EC-ElGamal cryptosystem, this paper proposes a novel remote data integrity check approach for IoT information management systems that preserves privacy without requiring trusted third parties | 5 |
| [114] | This study presents a lightweight IoT data-sharing security framework based on a double-chain paradigm that combines data and transaction blockchains. To prevent malicious local dominance behavior, a dynamic game method of node cooperation is presented. This approach aims to improve privacy protection, data registration efficiency, and the PBFT consensus algorithm | 5 |
| [115] | The primary goal is to improve the privacy of users and their data by implementing user-controlled privacy using the anonymization characteristics of blockchain. This paper proposed an architecture to address privacy and security issues of IoT applications | 5 |
| [116] | A blockchain-based control access system integrated with IoT to improve smart cities services and performance | 2 |
| [117] | This research offered a smart city hybrid model that included five core features that the authors consider necessary to provide security and privacy | 2 |
| [118] | PrivySharing: a framework for secure, private IoT data sharing in smart cities via blockchain technology. By separating the blockchain network over multiple channels, data privacy is ensured | 5 |
| [119] | Transform the standard IoT architecture by introducing multi-center security and privacy blockchain architecture. Design the architecture’s data interaction and algorithmic processes. The specific solution is discussed using an automated manufacturing platform | 7 |
| [120] | A smart home-based IoT-Blockchain (SHIB) approach is proposed to address privacy, security, and authentication challenges | 5 |
| [121] | ELIB is a smart home model that is based on an overlay network that validates dedicated security and privacy by merging resources with high levels of capability into a public BC. This approach consists of three levels: DTM scheme, CC model, and consensus algorithm | 5 |
| [122] | This paper proposes a lightweight scalable blockchain (LSB) approach that focuses on achieving decentralization and optimizing the performance for IoT requirements through overlay networks. A time-based consensus algorithm is also proposed to reduce the delay and mining processing overhead | 5 |
| [123] | In order to develop a robust framework for smart home systems, they present an authentication model that integrates attribute-based access control with smart contracts and edge computing. In addition, they designed a Stochastic Gradient Descent (SGD) algorithm | 5 |
| [124] | In response to the need for data mining and analytic activities in IoT, a privacy-protected and inter-cloud data fusion platform based on JointCloud blockchain is proposed in this paper | 2 |
| [125] | Blockchain, fog computing, and the alliance chain concept are used in this research to provide a distributed access control solution for IoT data security that relies on LSB (Least Significant Bit) and MLNCML (mixed linear and nonlinear spatiotemporal chaotic systems) techniques | 5 |
| [126] | This works presents a cross-domain access control scheme that provides reliability and security. The distributed access control is achieved using blockchain and NetwOrked Smart object (NOS) middleware | 5 |
| [127] | A decentralized trust model is proposed in this research in order to maintain the reputation of publicly available fog nodes. The public fog nodes’ reputation is preserved by the opinions of previous users and their interactions with them | 5 |
| [128] | Secure the data sharing in cloud environments using a proxy re-encryption approach by combining PRE with blockchain technology, information-centric networking, and identity-based encryption | 5 |
| [129] | This article proposed a privacy protection scheme based on a combination of smart contracts and zero-knowledge proof in order to provide an effective use of data while maintaining data privacy and validity. Furthermore, in order to share the data safely and offer consistency between owners and cloud service providers, a proxy re-encryption technology is enclosed | 2 |
| [130] | A smart agriculture prototype is designed using cloud and blockchain to provide remote monitoring and alert mechanisms to farmers in real time | 5 |
| [131] | In order to overcome certain security and privacy issues in IoT ID management systems, this paper proposes a proof-of-concept blockchain-based modeling prototype | 5 |
| [132] | A distributed identity management system called SmartDID is proposed to address the lack of a systematic proof system and resource limitations for IoT devices | 5 |
| Ref # | Blockchain Platform | Type of Blockchain | Consensus Algorithm /Protocol | Evaluation Environment | Performance Evaluation Metrics |
|---|---|---|---|---|---|
| [91] | Generic Ethereum (Extension) | Public or Private | PoBT | Solidity platform, Ethereum’ web3.js, different types of sensors connected to Raspberry Pi | N/A |
| [92] | EOS | Private | DPoS | EOS system, desktop computers as gateways, gateways complied contract with C++ language | Max, min, and average time for contract deploy and execution, transaction package and validation |
| [93] | Ethereum or Hyperledger | Private (Hyperledger) | ✖ | N/A | N/A |
| [94] | Certcoin | Public | PoW | On a mobile phone with specific hardware parameters, these operations are tested and programmed using JAVA | Functionality, Computational overhead of thin-client and full node users, Communication overhead |
| [95] | Ethereum | Consortium | IPFS used in data storage module | Performance test on AES with a specific hardware specifications desktop, private IPFS network for information storage, Lena image, smart contracts are deployed on Ropsten Testnet test network | AES encryption and decryption rate, Delay of node joining the network |
| [96] | Spacechain | Private | 3D-GHOST Modified PoW | Python 3, simulator: Compiled automatic transaction generator, testbed: Multi-miner P2P network test consist of 50 cloud virtual machines | Defense effect of selfish mining and DDoS attack, Network performance, Network throughput (block creation rate and block size limitation), Scalability |
| [97] | Ethereum | Public | Proof of Trust (PoT) | Solidity platform, Ethereum virtual machine (EVM), Remix IDE, network with 20 nodes (four types of nodes) | Trust evaluation mechanism, Running time, Expected mining cost |
| [98] | Hyperledger Fabric | Permissioned (Consortium) | PBFT | Hyperledger Fabric (v1.4.4) as a blockchain platform, Docker engine (v19.03.8, build afacb8b7f0) for runtime, Docker-compose (1.25.0) for image configuration, Node (v10.24.0) to create clients, Golang language (go1.16.2) for smart contracts creation, Hyperledger Caliper [133] | Throughput, transaction latency |
| Ref # | Blockchain Platform | Type of Blockchain | Consensus Algorithm /Protocol | Evaluation Environment | Performance Evaluation Metrics |
|---|---|---|---|---|---|
| [99] | Generic | ✖ | ✖ | N/A | N/A |
| [100] | Swarm | Private | IPFS | GnuPG, IPFS, Golang, Five types of IoT-based health sensor nodes | Time of loading, exchange, listening, announcement, and availability, IoT elements activity |
| [101] | ✖ | Private | PBFT | N/A | N/A |
| [102] | Userchain Docchain | Public (Userchain) Consortium (Docchain) | PoW (Userchain) PBFT (Docchain) | Simulate the user node with a smart phone, The experiment is built on the platform Android 7.1.1, Java is used for IoT transaction and key transaction, OS Windows 7 is used to measure doctor nodes and mining nodes Python is used for programming Docchain and Userchain | Effectiveness and feasibility (computation and communication costs for user transactions generation |
| [103] | Multi-tier platform | Public (it can be also considered a consortium, since it contains constrained and unconstrained nodes) | PBE-DA | MIRACL Library (security tools ) Linux Ubuntu 12.10 on a computer machine | Processing time from different sources and destinations |
| [104] | Ethereum | ✖ | ✖ | Geth is used as the Ethereum client | Transaction generation time with varying transaction capacities and image retrieval time |
| [105] | Hyperledger Fabric | Consortium | ✖ | Edge server (Ali cloud platform), SD or EU simulators (smartphone), Fabric platform with multiple nodes is used to evaluate the performance of a smart contract | Computation cost, Communication cost, Time cost of smart contract |
| [106] | Ethereum | Private (in experiments) Consortium (in problem formulation) | Proof of Authority (PoA) | Private Ethereum Clique Blockchain (PC) Private IPFS network (PC), Raspberry Pi 3 Model B, Smartphone (DApp interfaces), JSON-RPC protocol | Processing time for different operations |
| [107] | ✖ | Consortium | Proof-of-Epidemiology-of-Interest (PoEoI) | The implementation environment is available online | Total cost (time) to evaluate the system’s efficiency, adaptability, and robustness. Elapsed time to request or respond, total utility, probability (availability attack), consensus protocol evaluation: computation cost and number of nonces. |
| [108] | Hyperledger Fabric | Consortium | Customized lightweight PoW | Docker (Hyperledger Fabric), Applying a resource limit mechanism on network nodes, Hybrid network topology, Experiment over P2P network | Frequency evaluation of CPU usage, Computational fluctuations (cost), Ratio between number of medical transactions and the total number of connected devices, Rate of throughput, duty cycle, delay, and response |
| [109] | Hyperledger Fabric | Private | Proposed PBFT | Smart city network models using network simulator-3 (ns-3), Network topology using Python, GO-Ethereum | Network throughput using PBFT compared with the classical algorithm, Latency of fault peers, General latency of execution over the network |
| [110] | Hyperledger Indy [134] Hyperledger Aries [135] | Permissioned (Consortium) | Zero-Knowledge Proof (ZKP) [38] | Hyperledger Indy for identity management, Hyperledger Aries for digital credentials, Solidity and Hyperledger Ethereum to run smart contracts, ACA-Py as cloud agent, VON-network as a ledger browser, Docker community edition | Transaction time (DSMAC evaluation), Transaction throughput, Transaction latency, Cryptographic computations, Scalability, Sustainability |
| Ref # | Blockchain Platform | Type of Blockchain | Consensus Algorithm /Protocol | Evaluation Environment | Performance Evaluation Metrics |
|---|---|---|---|---|---|
| [120] | Ethereum | Private | PoW | Ganache, Remix, web3.js | Smart contract, Data privacy, Usage of tokens, Updating the policies, Misbehavior Judging |
| [121] | Simulated platform on NS3 | Public | Time-dependent consensus algorithm | Cooja, Network Simulator 3 (NS3), C++ programming language | POW processing time, Time overhead, Energy consumption, Packet overhead |
| [122] | Simulated platform on NS3 | Public | DTC | NS3, MinerGate | POW processing time, Request/response delay, Impact of the number of OBMs on security and packet overhead, Impact of PTV on the ability to detect appending attacks, DTM in the overlay |
| [123] | Ethereum | Private | PoW | Two sensors (temperature and LED), Python in google colab environment | Resource usage for single transaction, K-fold cross-validation, Accuracy |
| [116] | Generic | Public | ✖ | N/A | N/A |
| [117] | Ethereum | Public | PoW, PoS, PoA, and Proof of Vote (PoV) were investigated | N/A | N/A |
| [118] | Hyperledger Fabric | Private | SOLO and Kafka | Oauth 2.0, ClientApp, REST API, Hyperledger Composer-Playground, Hyperledger Caliper | Validation of ACL rules, Performance efficiency, Average commit time, Average throughput, Average latency |
| [119] | ✖ | Private | PoW | Four industrial robots, 3B Raspberry Pis (two sensing layers), Intel I5 platform (management hubs) | Real-time performance testing |
| [124] | JointCloud | Private | ✖ | N/A | N/A |
| [130] | Ethereum | Public (on Rinkeby Etherscan) | PoW | Arduino Sensor Kit, ESP32, AWS cloud, Ethereum Rinkeby Test Network | Latency of: Device-to-Cloud, Cloud-to-Blockchain, Blockchain-to-Client-Console, Alert Total |
| Ref # | Blockchain Platform | Type of Blockchain | Consensus Algorithm/Protocol | Evaluation Environment | Performance Evaluation Metrics |
|---|---|---|---|---|---|
| IoT Device Gateway | |||||
| [111] | Ethereum | Private | Ethereum-like | PDSS: Raspberry PI III (Debian 8), Java 8 for ARM, Eclipse 3.8, BC gateway: Desktop (Ethereum network), NVIDIA Shield TV as gateway, LG Nexus 5X as client application, Smart contract management: Asus ZenBook, JDK 8u151, Java EE 7 | Computation cost for PDSS, Practical potential for BC gateway, Average time for smart contract management |
| [112] | ✖ | ✖ | ✖ | Node.js | AES, DES, and Triple DES are used to evaluate memory usage |
| IoT Information Systems | |||||
| [113] | Generic | ✖ | ✖ | Python 3.7.1, Key size = 32 bits, ECC encryption using ElGamal algorithm | Probability of the illegality behavior detection, Average time of key generation compared to the size of key, Average time of six other elements |
| [114] | ✖ | Combination of public, alliance, and private chains | Improved PBFT | CentOS 7, JDK version is 1.80, Threshold signature (THS) | Throughput, Latency, Determination time, Transactions per second (TPS), Node density, Routing protocol performance in blockchain IoT low-speed environment |
| Management Systems | |||||
| [131] | ✖ | Federated (Consortium) | ✖ | Solidity, Kaleido platform | Transaction monitoring, CPU time and utilization |
| [132] | FISCO BCOS | Consortium | PBFT | Java 1.8, Fisco Bcos platform, 28.5 Mbps /11.21 Mbps bandwidth, 10 ms average communication delay | Credentials generation, Proof generation, Proof time, Time per type of credential, Time for range credential, Block generation time, Credentials size, Average verification time, Time for credentials verification |
| Ref # | Blockchain Platform | Type of Blockchain | Consensus Algorithm/Protocol | Evaluation Environment | Performance Evaluation Metrics |
|---|---|---|---|---|---|
| Cloud Environments | |||||
| [128] | Hyperledger Fabric | Consortium | PBFT | jPBC library [136] for pairing, A super-singular curve, elliptic curve cryptography to implement group-based schemes, NIST P-256, web3.js to generate transactions | Computation cost, Encrypted data confidentiality, Data encryption computation time, Transaction latency |
| [129] | ✖ | ✖ | Combined RBFT and Raft | N/A | N/A |
| Fog Computing | |||||
| [125] | Hyperledger Fabric | Private | ✖ | Go language, JetBrains developer tools, MATLAB, Lena picture | Bit error rate with chaos coding parameter, Bit error rate with encrypted image pixels |
| [126] | ✖ | Permissioned (private or federated/consortium) | BFT replication | NOS architecture, 14 data sources, Data rate between 10 and 20 packets per second, Rate change policy, Block dimension and generation time, Raspberry Pi platforms, MQTT broker, Smart home testbed | Storage overhead, Computing effort (CPU load), Latency |
| Edge Computing | |||||
| [90] | TrustChain | Private | Proof of Trust (PoT), Trust+BFT | N/A | Object trust model, Data trust model, Privacy trust model, REK: Reputation, Experience, and Knowledge |
| Reputation Systems | |||||
| [127] | Ethereum | Public | PoW | MythX, Sercurify analyzer, SmartCheck, Oyente, Remix IDE using solidity | Cost (of transaction), Performance analysis, Security analysis |
| Mobile IoT Applications | |||||
| [115] | Ethereum | Private and Public | Private blockchain: PoA, Public blockchain: PoW | Python’s time library, NetHogs (version 0.8.6), psutil (version 5.8.0) python library | Time overhead, Bandwidth consumption, CPU and memory usage |
| Ref # | Future Works (Open Issues) | Notes |
|---|---|---|
| [90] | ✗ | ★ Efficient mining scheme ★ Significantly small mining delay compared to PoW ★ Enhanced scalability ★ Compatibility with IoT business models ★ Interoperability among several TrustChains ❖ Network overloading due to excessive exchange of messages between devices and server ❖ The centralized server is used for storage ❖ This approach is not implemented and evaluated yet |
| [91] | ✗ | ❖ It does not support dynamic access control |
| [92] | ✓ | ★ It supports the fast and secure insert of the device in the perception layer |
| [93] | ✓ | ★ Improved access tracking ★ Provided efficient access control and data transparency ❖ This approach is not implemented and evaluated yet |
| [94] | ✗ | ❖ (m-1)-private PTAS sacrifices little efficiency in exchange for safety improvement |
| [95] | ✓ | ★ Simple ★ Support parallel computing ★ Error not passing ★ Not easy to attack |
| [96] | ✓ | ❖ In order to achieve anonymity, public keys alone are not enough ❖ Zero-Knowledge Proofs |
| [97] | ✗ | ★ Robust against several types of attacks ★ Low expected computation cost ★ Moderate scaling ★ Transparency and verifiability ★ Good resiliency ❖ Does not include trust and reputation management |
| [98] | ✓ | ★ The proposed system includes auto-policy enforcement, on-chain policy management ★ It provides security, fee-less, trustworthy (without TTP), and scalability ❖ In order to eliminate network congestion and reduce the latency, machine learning algorithms can be integrated |
| [99] | ✓ | ★ Increased security due to the hybrid apporach that combined many lightweight cryptographic primitives with public and private keys ❖ This approach is not implemented and evaluated yet |
| [100] | ✓ | ★ Protection of EHR against fraud ★ Interoperability of EHR data formats ★ Simplification of current paradigms ★ Low cost ★ IoT data aggregator and sensor heterogeneity ❖ Not feasible for a large-scale network ❖ Block is mined instantaneously by the virtual nodes itself; thus, miners are needed |
| [101] | ✓ | ★ High resiliency against public blockchain modification and DoS, modification, appending, and 51% attacks ❖ This approach is not implemented and evaluated yet |
| [102] | ✗ | ★ This approach offers on-demand rescission, accountability, and improved privacy |
| [103] | ✓ | ★ Using file and data sharing, this approach improved intersectoral collaboration ❖ In terms of development and administration, it requires further accountability |
| [104] | ✓ | ★ Low latency ★ High feasibility ★ Enhanced image size ❖ Privacy concerns are still an issue when implementing in real-time environment |
| [105] | ✓ | ★ The proposed architecture is not limited to healthcare domain only ★ Efficient and pairing-free authentication scheme ★ Guaranteed user anonymity with satisfied security requirements ❖ Certain security properties and efficiency metrics can be improved |
| [106] | ✓ | ★ The proposed system offers confidentiality, integrity, privacy, and access control ❖ The authors suggests adding a fog layer between different system entities in order to process and filter the data |
| [107] | ✓ | ★ New consensus protocol is introduced while maintaining the system’s robustness, efficiency, and adaptability ★ The proposed consensus protocol requires less computational cost than PoW and PoA ❖ Overall computation cost is not considered when this approach is implemented |
| [108] | ✓ | ★ Reduces computational cost ★ Enhanced node transactions performance ★ This design offers provenance, transparency, security, and integrity |
| [109] | ✓ | ★ This work promises higher security levels and lower execution time ★ This approach achieves consistency, security, availability, integrity, and transparency ❖ Tested for medical supply chain-based scenario only ❖ No description of encryption and decryption of OTH |
| [110] | ✓ | ★ As compared to other models, DSMAC overcomes the others as it provides scalability, sustainability, data privacy, and emergency case ★ DSMAC includes access control methods such as identification, authentication, and authorization |
| [111] | ✓ | ★ Using such an access control approach provides a non-repudiation feature and allows users’ preferences and device policies to be preserved without tampering. |
| [112] | ✓ | ★ The authors included the advantages and several important remarks that can be added to the proposed approach to improve its performance ★ Flexibility to use all encryption algorithms ★ Intrusion prevention ★ Adding a new layer of security ❖ This approach will be considered useless if the database is corrupted in any form ❖ Scalability issue: the processing performance decreases as the number of smart devices increases |
| [113] | ✓ | ★ Supports dynamic auditing ★ Satisfies the public verification and correctness ★ The used storage method offers many advantages such as reducing cost |
| [114] | ✓ | ★ Anti-attack capability (10 types of attacks) ❖ When this system is implemented in certain industries, its performance must be improved, as well as the risk of privacy leaks must be addressed. |
| [115] | ✓ | ❖ Single points of failure (due to using smart contract proxy and MQTT) ❖ Reduced throughput ❖ Increased latency by the evaluation scenario |
| [116] | ✓ | ❖ This approach is not implemented and evaluated yet |
| [117] | ✓ | ❖ This approach is not implemented and evaluated yet |
| [118] | ✓ | ★ This approach offers better scaling than a single Ch blockchain system ❖ Massive resource requirement ❖ IoT device integrity mechanism is required |
| [119] | ✓ | ★ Enhanced scalability and flexibility ❖ It might introduce large communication overhead |
| [120] | ✗ | ★ High extension ability ★ Ability to handle misbehavior |
| [121] | ✓ | ★ Reduced processing time ★ Low energy consumption ❖ Requires extra cost due to cloud usage ❖ Low scalability |
| [122] | ✓ | ★ Decreases processing time and bandwidth compared to traditional blockchains ❖ Using DTC in small networks can make the network vulnerable to Sybil attack |
| [123] | ✓ | ★ Resilient against modification, linkage attacks, data mining, and DoS attacks ❖ Extra added noise (trade-off between accuracy and privacy) which might result in reduced data accuracy |
| [124] | ✗ | ❖ This approach is not implemented and evaluated yet |
| [125] | ✓ | ★ The proposed approach requires fewer start-up and running nodes ★ Less computing power is required ★ It does not need to pay remuneration ★ Offers effective management of the rights |
| [126] | ✓ | ★ This approach supports confidentiality, integrity, and resistance to attacks ❖ The proposed approach needs further testing with the common blockchain platforms such as Ethereum or Hyperledger Fabric with more complex environments in order to compare its performance with other approaches |
| [127] | ✗ | ❖ Further evaluations can be performed using throughput and power consumption |
| [128] | ✗ | ★ It offers confidentiality, decentralization, auditability, and low overhead for data owners ❖ High proxy overhead ❖ Does not include mutliple proxies ❖ Splitting re-encryption key scheme can be included |
| [129] | ✓ | ★ Offers content and identity privacy, data validity, verfiability, and traceability ❖ The proposed scheme relies on trusted third paties ❖ This approach is not implemented and evaluated yet |
| [130] | ✓ | ★ The proposed approach offers mininal network latency ❖ IoT gateway is not implemented ❖ This approach can work with Ethereum and PoW only |
| [131] | ✓ | ★ Authentication and secure identity are provided ★ This prototype is cost-effective ❖ Scalability issue, this prototype is not designed to handle large scale operation, adaptability and extendibility can be further investigated |
| [132] | ✓ | ★ The proposed system supports Credential Nested Verification ❖ PBFT caused communication overhead between nodes which leads to limited reliability due to increased latency and bottlenecks in network transmission |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zubaydi, H.D.; Varga, P.; Molnár, S. Leveraging Blockchain Technology for Ensuring Security and Privacy Aspects in Internet of Things: A Systematic Literature Review. Sensors 2023, 23, 788. https://doi.org/10.3390/s23020788
Zubaydi HD, Varga P, Molnár S. Leveraging Blockchain Technology for Ensuring Security and Privacy Aspects in Internet of Things: A Systematic Literature Review. Sensors. 2023; 23(2):788. https://doi.org/10.3390/s23020788
Chicago/Turabian StyleZubaydi, Haider Dhia, Pál Varga, and Sándor Molnár. 2023. "Leveraging Blockchain Technology for Ensuring Security and Privacy Aspects in Internet of Things: A Systematic Literature Review" Sensors 23, no. 2: 788. https://doi.org/10.3390/s23020788






