Post-Quantum Security: Opportunities and Challenges
Abstract
:1. Introduction
| Name | Pre-Quantum Security Level | Function | Post-Quantum Security Level | Impact |
|---|---|---|---|---|
| Symmetric cryptography | ||||
| AES-128 [15] | 128 | Block cipher | 64 | Cracked by Grover’s algorithm |
| AES-256 [15] | 256 | Block cipher | 128 | Cracked by Grover’s algorithm |
| Salsa20 [16] | 256 | Stream cipher | 128 | Cracked by Grover’s algorithm |
| GMAC [17] | 128 | MAC | 128 | No impact |
| Poly1305 [18] | 128 | MAC | 128 | No impact |
| SHA-256 [19] | 256 | Hash function | 128 | Cracked by Grover’s algorithm |
| SHA-3 [20] | 256 | Hash function | 128 | Cracked by Grover’s algorithm |
| Public-key cryptography | ||||
| RSA-3072 [21] | 128 | Encryption | Broken | Cracked by Shor’s algorithm |
| RSA-3072 [21] | 128 | Signature | Broken | Cracked by Shor’s algorithm |
| DH-3072 [22] | 128 | Key exchange | Broken | Cracked by Shor’s algorithm |
| DSA-3072 [23,24] | 128 | Signature | Broken | Cracked by Shor’s algorithm |
| 256-bit ECDH [25,26,27] | 128 | Key exchange | Broken | Cracked by Shor’s algorithm |
| 256-bit ECDSA [28,29] | 128 | Signature | Broken | Cracked by Shor’s algorithm |
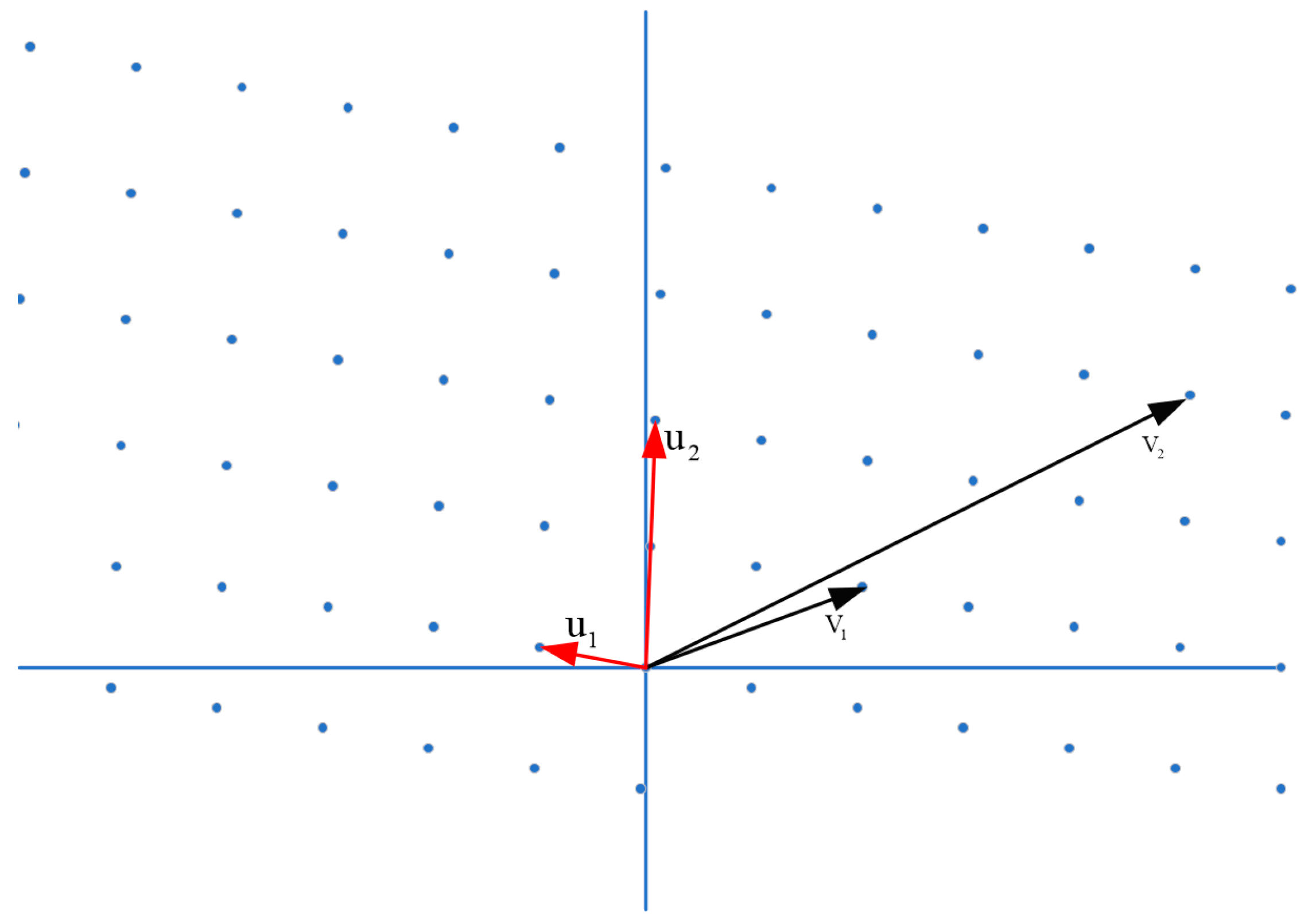
- Lattice-based algorithms are one of the most encouraging post-quantum cryptographic algorithms [33]. The algorithm has significantly improved computational speed and security intensity, and the channel overhead has only slightly increased [34]. The safety of lattice-based algorithms depends on the complexity of solving problems in the lattice and can achieve various existing cryptographic constructions, such as digital signature, key exchange, encryption, attribute encryption, function encryption, and all homomorphic encryptions. Two-dimensional lattices and two different sets of lattice bases are shown in Figure 1.
- 2.
- Code-based algorithms utilize error correction codes to correct and compute the randomness errors added; a famous code-based encryption algorithm is McEliece [35]. The core idea of McEliece’s scheme is to utilize the error-correcting ability of linear codes (or error-correcting codes) to construct encryption algorithms. According to different classification criteria, the specific classifications are shown in Table 2. This cryptography method relies on a public-key infrastructure, where the public key consists of a sparse random matrix and a matrix that generates a linear code. Meanwhile, the private key includes the matrix inverse of the one used for creating the linear code.
- 3.
- Algorithms based on multivariate polynomials utilize sets of quadratic polynomials with multiple variables over finite fields to construct encryption, signature, key exchange, and related methods [36]. The safety of multivariate cryptography relies on the difficulty of solving systems of nonlinear equations, specifically the challenge of addressing multivariate quadratic polynomial problems.
- 4.
- A hash-based signature algorithm was proposed by Ralph Merkel and is considered to be one of the feasible alternatives to traditional digital signatures (RSA, DSA, ECDSA, etc.) [37]. Due to the lack of effective quantum algorithms to quickly find collisions in hash functions, hash-based constructions (with sufficient output length) can resist quantum computer attacks. The Merkle tree is shown in Figure 2.
2. Background
- Symmetric encryption
- 2.
- Asymmetric encryption
- Two primes, P and Q, are chosen at random.
- Find the value M of the Euler function for N. The Euler function is given by the following formula, where , , ,…, is all unrepeated prime factors of n.
- 3.
- Find an integer E that is prime to M.
- 4.
- Find an integer D that satisfies the following relation:
3. CRYSTALS-KYBER Algorithm Construction Process
Kyber Build Specifics
| Algorithm 1. |
| 1. |
| 2. |
| 3. |
| 4. |
| 5: return |
| Algorithm 2. |
| 1. |
| 2. |
| 3. |
| 4. 5. |
| 6. 7: return |
| Algorithm 3. |
| 1. |
| 2. |
| 3: return |
| Algorithm 4. |
| 1: |
| 2: |
| 3: |
| 4: |
| 5: |
| 6: return |
| Algorithm 5. |
| 1. |
| 2. |
| 3. |
| 4: if then |
| 5: return |
| 6: else |
| 7: return |
| 8: end if |
- Increase the noise parameter of Kyber512.
- 2.
- Reduce the ciphertext compression rate of Kyber512.
- 3.
- Common matrix A adopts more effective uniform sampling.
- Updated specifications to match Round 3 parameters.
- Updated performance data.
- The performance analysis section includes data on ARM Coretex-M4 [78], and the submitted software package includes the corresponding software. Finally, a more detailed analysis was conducted on the latest technologies to solve the core Gaussian programming problem, and attacks that failed decryption were discussed. Significant updates were made in terms of security analysis.
4. Implementation
4.1. Software Implementation
4.2. Hardware Implementation
5. Discussion and Evolution
5.1. Opportunities and Challenges
- The development of post-quantum encryption algorithms effectively guards against quantum computer threats, providing a robust foundation for future information security. This is crucial for safeguarding information in various industries, including finance, telecommunications, healthcare, and more.
- Research in post-quantum encryption has also driven the establishment of encryption standards and international collaboration, with the potential to provide a consistent foundation for ensuring global information security.
- Developing sufficiently strong and efficient post-quantum encryption algorithms is a massive undertaking that requires in-depth mathematical and computer science research. Large-scale deployment and standardization will involve complex coordination and cooperation to ensure widespread adoption of new technologies.
- To maintain security, it is essential to continuously address potential new threats and attacks, which requires staying vigilant and updating encryption systems promptly.
5.2. Evolution
- Adoption and standardization of new encryption algorithms: With NIST establishing standardized post-quantum encryption algorithms, new opportunities are provided for data security and communications in various fields [95]. The anticipated future trends in post-quantum encryption algorithms are illustrated in Figure 8.
- Evolution of crypto: Post-quantum encryption is not just about responding to the threat of quantum computers but will drive the evolution of the entire field of encryption. This could include stronger authentication, more sophisticated key management, and more efficient encryption protocols. These evolutions will help improve the security of communications and data and adapt to evolving threats [96].
- Practicality and performance considerations: Post-quantum encryption algorithms need to be secure while also considering their practicality and performance. These algorithms need to be able to be used in real communications without significantly affecting the speed and efficiency of communications. Therefore, future research and development will focus not only on security but also on the practicality and deployability of the algorithms [97].
- Sensors typically transmit their collected data to other devices or storage servers. Consider employing post-quantum encryption algorithms to encrypt sensor data, ensuring data security during transmission.
- Sensors often require identity verification to ensure legitimacy. Post-quantum encryption algorithms can be used for sensor identity verification, ensuring data integrity and authenticity.
- Sensors may occasionally need firmware updates and configuration changes. Post-quantum encryption algorithms can be utilized to verify the integrity of sensor firmware and configuration files, ensuring the security of the sensors.
6. Summary and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
| Scheme | Sec.estim | Problem | Cycles | Bytes | Scheduled Shutdown |
|---|---|---|---|---|---|
| Passively secure KEMS | |||||
| BCNS [67] | 78a | Ring-LWE | K. ≈2,477,958 E. ≈3,395,977 D. ≈481,937 | sk: 4096 pk: 4096 c: 4224 | yes |
| NewHope [68] (AVXoptimize) | 255a | Ring-LWE | K: 88,920 E: 110,986 D: 19,422 | sk: 1792 pk: 1824 c: 2048 | yes |
| FRODO [77] (recommended parameters) | 130a | LWE | K. ≈2,938,000b E. ≈3,484,000b D. ≈338,000b | sk: 11,280 pk: 11,296 c: 11,288 | yes |
| CCA-secure KEMS | |||||
| NTRU Prime [104] | 129a | NTRUk | K. ?c E. >51,488c D. ?c | sk:1417 pk:1232 c:1141 | yes |
| spLWE-KEM [105] (128-bit PQ parameters) | 129i | spLWE | K. ≈2,938,000d E. ≈3,484,000d D. ≈78,200d | sk: ? pk: ? c: 804 | ? |
| Kyber (C reference) | 161i | Module-LWE | K: 276,720 E: 332,800 D: 376,104 | sk: 2368 pk: 1088 c: 1184 | yes |
| Kyber (AVX2 optimized) | 161i | Module-LWE | K: 77,892 E: 119,652 D: 125,736 | sk: 2400 pk: 1088 c: 1184 | yes |
| CCA-secure public-key encryption | |||||
| NTRYEncrpt ees743ep1 [60] | 158a | NTRU | K: 1,194,816 E: 57,440 D: 110,604 | sk: 1120 pk: 1027 c: 980 | no |
| Lizard. [61] (recommended parameters) | 128i | LWE + LWR | K. 97,573,000f E. ≈35,050f D. ≈80,840f | sk. 466,944g,h pk. 2,031,616h c: 1072 | no |
| Scenario Name | Scenario Run Cycle | The Scheme Stack Uses Bytes |
|---|---|---|
| Kyber-768 (v1) | Key generation: 946 k Encapsulation/encryption: 1167 k Decapsulation/decryption: 1117 k | Key generation: 3072 Encapsulation/encryption: 3120 Decapsulation/decryption: 3176 |
| Kyber-768 (v2) | Key generation: 947 k Encapsulation/encryption: 1113 k Decapsulation/decryption: 1059 k | Key generation: 3648 Encapsulation/encryption: 3232 Decapsulation/decryption: 3248 |
| Frodo-AES128 | Key generation: 41,681 k Encapsulation/encryption: 45,758 k Decapsulation/decryption: 46,720 k | Key generation: 31,116 Encapsulation/encryption: 51,444 Decapsulation/decryption: 61,280 |
| Frodo-cSHAKE128 | Key generation: 81,300 k Encapsulation/encryption: 86,255 k Decapsulation/decryption: 87,212 k | Key generation: 26,272 Encapsulation/encryption: 41,472 Decapsulation/decryption: 51,848 |
| Saber. | Key generation: 902 k Encapsulation/encryption: 1173 k Decapsulation/decryption:1217 k | Key generation: 13,248 Encapsulation/encryption: 15,528 Decapsulation/decryption: 16,624 |
| Key generation: 1165 k Encapsulation/encryption: 1530 k Decapsulation/decryption: 1635 k | Key generation: 6931 Encapsulation/encryption: 7019 Decapsulation/decryption: 8115 | |
| R5ND_3PKEb | Key generation: 1032 k Encapsulation/encryption: 1510 k Decapsulation/decryption: 1913 k | Key generation: 6796 Encapsulation/encryption: 8908 Decapsulation/decryption: 4296 |
| NewHope1024CCA | Key generation: 1221 k Encapsulation/encryption: 1902 k Decapsulation/decryption: 1926 k | Key generation: 11,152 Encapsulation/encryption: 17,448 Decapsulation/decryption: 19,648 |
| NTRU-HRSS-KEM | Key generation: 145,986 k Encapsulation/encryption: 406 k Decapsulation/decryption: 827 k | Key generation: 23,396 Encapsulation/encryption: 19,492 Decapsulation/decryption: 22,140 |
| NTRU-KEM-743 | Key generation: 5203 k Encapsulation/encryption: 1603 k Decapsulation/decryption: 1884 k | Key generation: 25,320 Encapsulation/encryption: 23,808 Decapsulation/decryption: 28,472 |
References
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.K.; Pan, J.W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Buchmann, J.A.; Butin, D.; Göpfert, F.; Petzoldt, A. Post-Quantum Cryptography: State of the Art. In The New Codebreakers; Ryan, P., Naccache, D., Quisquater, J.J., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2016; Volume 9100. [Google Scholar] [CrossRef]
- Cai, J.; Liang, W.; Li, X.; Li, K.; Gui, Z.; Khan, M.K. GTxChain: A Secure IoT Smart Blockchain Architecture Based on Graph Neural Network. IEEE Internet Things J. 2023. [Google Scholar] [CrossRef]
- Liu, S.; Wang, K.; Yang, X.; Ye, J.; Wang, X. Dataset distillation via factorization. Adv. Neural Inf. Process. Syst. 2022, 35, 1100–1113. [Google Scholar]
- Xiao, L.; Han, D.; Li, D.; Liang, W.; Yang, C.; Li, K.C.; Castiglione, A. CTDM: Cryptocurrency abnormal transaction detection method with spatio-temporal and global representation. Soft Comput. 2023, 27, 11647–11660. [Google Scholar] [CrossRef]
- Das, S.; Xiang, Z.; Kokoris-Kogias, L.; Ren, L. Practical asynchronous high-threshold distributed key generation and distributed polynomial sampling. In Proceedings of the 32nd USENIX Security Symposium (USENIX Security 23), Anaheim, CA, USA, 9–11 August 2023; pp. 5359–5376. [Google Scholar]
- Chen, Y.; Chen, S.; Li, K.C.; Liang, W.; Li, Z. DRJOA: Intelligent resource management optimization through deep reinforcement learning approach in edge computing. Clust. Comput. 2023, 26, 2897–2911. [Google Scholar] [CrossRef]
- Dutto, S.; Murru, N. On the cubic Pell equation over finite fields. Quaest. Math. 2023, 46, 1–20. [Google Scholar] [CrossRef]
- Hu, N.; Zhang, D.; Xie, K.; Liang, W.; Diao, C.; Li, K.C. Multi-range bidirectional mask graph convolution based GRU networks for traffic prediction. J. Syst. Archit. 2022, 133, 102775. [Google Scholar] [CrossRef]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar] [CrossRef]
- Grover, L.K. A fast quantum mechanical algorithm for database search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- Bernstein, D.J.; Lange, T. Post-quantum cryptography. Nature 2017, 549, 188–194. [Google Scholar] [CrossRef]
- Wikipedia: Timeline of Quantum Computing—Wikipedia, the Free Encyclopedia. 2014. Available online: http://en.wikipedia.org/w/index.php?title=Timeline_of_quantum_computing&oldid=613219069 (accessed on 25 September 2014).
- Borges, F.; Reis, P.R.; Pereira, D. A Comparison of Security and its Performance for Key Agreements in Post-Quantum Cryptography. IEEE Access 2020, 8, 142413–142422. [Google Scholar] [CrossRef]
- Daemen, J.; Rijmen, V. The Design of Rijndael: The Advanced Encryption Standard; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Bernstein, D.J. The Salsa20 Family of Stream Ciphers. New Stream Cipher Designs: The eSTREAM Finalists; Springer: Berlin/Heidelberg, Germany, 2008; pp. 84–97. [Google Scholar]
- McGrew, D.A.; Viega, J. The Security and Performance of the Galois/Counter Mode (GCM) of Operation; Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Bernstein, D.J. The Poly1305-AES Message-Authentication Code. In Proceedings of the International Workshop on Fast Software Encryption, Paris, France, 21–23 February 2005; Springer: Berlin/Heidelberg, Germany, 2005. [Google Scholar]
- Information Technology Laborator; National Institute of Standards and Technology. Secure Hash Standard. Federal Information Processing Standards Publication 180-4. 2012. Available online: http://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.180-4.pdf (accessed on 27 August 2023).
- Bertoni, G.; Daemen, J.; Peeters, M.; Van Assche, G. Keccak. In Annual International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2013; pp. 313–314. [Google Scholar]
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Hellman, M. New directions in cryptography. IEEE Trans. Inf. Theory 1976, 22, 644–654. [Google Scholar]
- ElGamal, T. A public key cryptosystem and a signature scheme based on discrete logarithms. IEEE Trans. Inf. Theory 1985, 31, 469–472. [Google Scholar] [CrossRef]
- Schnorr, C.P. Efficient Identification and Signatures for Smart Cards. In Advances in Cryptology—CRYPTO’ 89 Proceedings. CRYPTO 1989; Brassard, G., Ed.; Lecture Notes in Computer Science; Springer: New York, NY, USA, 1990; Volume 435. [Google Scholar] [CrossRef]
- Miller, V.S. Use of Elliptic Curves in Cryptography. In Advances in Cryptology—CRYPTO ’85 Proceedings. CRYPTO 1985; Williams, H.C., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1986; Volume 218. [Google Scholar] [CrossRef]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Bernstein, D.J. Curve25519: New Diffie-Hellman Speed Records. In Public Key Cryptography-PKC 2006. PKC 2006; Yung, M., Dodis, Y., Kiayias, A., Malkin, T., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2006; Volume 3958. [Google Scholar] [CrossRef]
- Johnson, D.; Menezes, A.; Vanstone, S. The Elliptic Curve Digital Signature Algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Duif, N.; Lange, T.; Schwabe, P.; Yang, B.Y. High-speed high-security signatures. J. Cryptogr. Eng. 2012, 2, 77–89. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Lange, T.; Peters, C. Attacking and defending the McEliece cryptosystem. In Proceedings of the Post-Quantum Cryptography:, Second International Workshop, PQCrypto 2008, Cincinnati, OH, USA, 17–19 October 2008; Springer: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Kumari, S.; Singh, M.; Singh, R.; Tewari, H. Signature based Merkle Hash Multiplication algorithm to secure the communication in IoT devices. Knowl.-Based Syst. 2022, 253, 109543. [Google Scholar] [CrossRef]
- Post-Quantum Cryptography. Available online: http://pqcrypto.org/conferences.html (accessed on 27 August 2023).
- Nejatollahi, H.; Dutt, N.; Ray, S.; Regazzoni, F.; Banerjee, I.; Cammarota, R. Post-quantum lattice-based cryptography implementations: A survey. ACM Comput. Surv. 2019, 51, 1–41. [Google Scholar] [CrossRef]
- Asif, R. Post-quantum cryptosystems for Internet-of-Things: A survey on lattice-based algorithms. IoT 2021, 2, 71–91. [Google Scholar] [CrossRef]
- McEliece, R.J. A public-key cryptosystem based on algebraic. Coding Thv 1978, 4244, 114–116. [Google Scholar]
- Kuang, R.; Perepechaenko, M.; Barbeau, M. A new post-quantum multivariate polynomial public key encapsulation algorithm. Quantum Inf. Process. 2022, 21, 360. [Google Scholar] [CrossRef]
- Yin, H.L.; Fu, Y.; Li, C.L.; Weng, C.X.; Li, B.H.; Gu, J.; Lu, Y.S.; Huang, S.; Chen, Z.B. Experimental quantum secure network with digital signatures and encryption. Natl. Sci. Rev. 2023, 10, nwac228. [Google Scholar] [CrossRef] [PubMed]
- Mitra, S.; Samanwita, D.; Malay, K. Prevention of the man-in-the-middle attack on Diffie–Hellman key exchange algorithm: A review. In Proceedings of International Conference on Frontiers in Computing and Systems: COMSYS 2020; Springer: Singapore, 2021. [Google Scholar]
- Harkanson, R.; Kim, Y. Applications of elliptic curve cryptography: A light introduction to elliptic curves and a survey of their applications. In Proceedings of the 12th Annual Conference on Cyber and Information Security Research, Oak Ridge, TN, USA, 4–6 April 2017; ACM: New York, NY, USA, 2017. [Google Scholar] [CrossRef]
- Jao, D.; De Feo, L. Towards quantum-resistant cryptosystems from supersingular elliptic curve isogenies. In Post-Quantum Cryptography, Proceedings of the 4th International Workshop, PQCrypto 2011, Taipei, Taiwan, 29 November–2 December 2011; Proceedings 4. Springer: Berlin/Heidelberg, Germany, 2011; pp. 19–34. [Google Scholar] [CrossRef]
- Alagic, G.; Apon, D.; Cooper, D.; Dang, Q.; Dang, T.; Kelsey, J.; Lichtinger, J.; Miller, C.; Moody, D.; Peralta, R.; et al. Status Report on the Third Round of the NIST Post-Quantum Cryptography Standardization Process; US Department of Commerce, NIST: Gaithersburg, MD, USA, 2022.
- Gong, Y.; Li, K.; Xiao, L.; Cai, J.; Xiao, J.; Liang, W.; Khan, M.K. VASERP: An adaptive, lightweight, secure, and efficient RFID-based authentication scheme for IoV. Sensors 2023, 23, 5198. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Q. An Overview and Analysis of Hybrid Encryption: The Combination of Symmetric Encryption and Asymmetric Encryption. In Proceedings of the 2021 2nd International Conference on Computing and Data Science (CDS), Stanford, CA, USA, 28–29 January 2021; pp. 616–622. [Google Scholar] [CrossRef]
- Rudnytskyi, V.; Korchenko, O.; Lada, N.; Ziubina, R.; Wieclaw, L.; Hamera, L. Cryptographic encoding in modern symmetric and asymmetric encryption. Procedia Comput. Sci. 2022, 207, 54–63. [Google Scholar] [CrossRef]
- Liang, W.; Xie, S.; Cai, J.; Wang, C.; Hong, Y.; Kui, X. Novel private data access control scheme suitable for mobile edge computing. China Commun. 2021, 18, 92–103. [Google Scholar] [CrossRef]
- Salim, S.; Msallam, M.; Olewi, H. Hide text in an image using Blowfish algorithm and development of least significant bit technique. Indones. J. Electr. Eng. Comput. Sci. 2023, 29, 339–347. [Google Scholar] [CrossRef]
- Christensen, C. Reviews of Two Post-Quantum Cryptography Books. In Post-Quantum Cryptography; Bernstein, D.J., Buchmann, J., Dahmen, E., Eds.; Springer: Berlin/Heidleberg, Germany, 2009; 245p. [Google Scholar]
- Chen, L.; Chen, L.; Jordan, S.; Liu, Y.K.; Moody, D.; Peralta, R.; Perlner, R.A.; Smith-Tone, D. Report on Post-Quantum Cryptography; US Department of Commerce, National Institute of Standards and Technology: Gaithersburg, MD, USA, 2016; Volume 12.
- Alagic, G.; Alagic, G.; Alperin-Sheriff, J.; Apon, D.; Cooper, D.; Dang, Q.; Liu, Y.K.; Miller, C.; Moody, D.; Peralta, R.; et al. Status Report on the First Round of the NIST Post-Quantum Cryptography Standardization Process; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2019.
- Alagic, G.; Alperin-Sheriff, J.; Apon, D.; Cooper, D.; Dang, Q.; Kelsey, J.; Liu, Y.K.; Miller, C.; Moody, D.; Peralta, R.; et al. Status Report on the Second Round of the NIST Post-Quantum Cryptography Standardization Process; US Department of Commerce, NIST, 2: Gaithersburg, MD, USA, 2020.
- Bos, J.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schanck, J.M.; Schwabe, P.; Seiler, G.; Stehlé, D. CRYSTALS-Kyber: A CCA-secure module-lattice-based KEM. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), London, UK, 24–26 April 2018; pp. 353–367. [Google Scholar] [CrossRef]
- Beckwith, L.; Nguyen, D.T.; Gaj, K. High-Performance Hardware Implementation of CRYSTALS-Dilithium. In Proceedings of the 2021 International Conference on Field-Programmable Technology (ICFPT), Auckland, New Zealand, 6–10 December 2021; pp. 1–10. [Google Scholar] [CrossRef]
- Soni, D.; Basu, K.; Nabeel, M.; Aaraj, N.; Manzano, M.; Karri, R. FALCON. In Hardware Architectures for Post-Quantum Digital Signature Schemes; Springer: Cham, Switzerland, 2021. [Google Scholar] [CrossRef]
- Liang, W.; Xie, S.; Cai, J.; Xu, J.; Hu, Y.; Xu, Y.; Qiu, M. Deep Neural Network Security Collaborative Filtering Scheme for Service Recommendation in Intelligent Cyber–Physical Systems. IEEE Internet Things J. 2022, 9, 22123–22132. [Google Scholar] [CrossRef]
- Nosouhi, M.R.; Shah, S.W.A.; Pan, L.; Doss, R. Bit Flipping Key Encapsulation for the Post-Quantum Era. IEEE Access 2023, 11, 56181–56195. [Google Scholar] [CrossRef]
- Lahr, N.; Niederhagen, R.; Petri, R.; Samardjiska, S. Side Channel Information Set Decoding Using Iterative Chunking. In Advances in Cryptology—ASIACRYPT 2020. ASIACRYPT 2020; Moriai, S., Wang, H., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2020; Volume 12491. [Google Scholar] [CrossRef]
- Guo, Q.; Johansson, T. A New Decryption Failure Attack Against HQC. In Advances in Cryptology—ASIACRYPT 2020. ASIACRYPT 2020; Moriai, S., Wang, H., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2020; Volume 12491. [Google Scholar] [CrossRef]
- Seo, H.; Anastasova, M.; Jalali, A.; Azarderakhsh, R. Supersingular Isogeny Key Encapsulation (SIKE) Round 2 on ARM Cortex-M4. IEEE Trans. Comput. 2021, 70, 1705–1718. [Google Scholar] [CrossRef]
- Cheon, J.H.; Han, K.; Kim, J.; Lee, C.; Son, Y. A Practical Post-Quantum Public-Key Cryptosystem Based on spLWE. In Information Security and Cryptolog—ICISC 2016. ICISC 2016; Hong, S., Park, J., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2017; Volume 10157. [Google Scholar] [CrossRef]
- Hoffstein, J.; Pipher, J.; Schanck, J.M.; Silverman, J.H.; Whyte, W.; Zhang, Z. Choosing Parameters for NTRUEncrypt. In Topics in Cryptology—CT-RSA 2017. CT-RSA 2017; Handschuh, H., Ed.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2017; Volume 10159. [Google Scholar] [CrossRef]
- Cheon, J.H.; Kim, D.; Lee, J.; Song, Y. Lizard: Cut off the tail! A practical post-quantum public-key encryption from LWE and LWR. In International Conference on Security and Cryptography for Networks; Springer International Publishing: Cham, Switzerland, 2018; pp. 160–177. [Google Scholar]
- Avanzi, R.; Bos, J.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schanck, J.M.; Schwabe, P.; Seiler, G.; Stehlé, D. CRYSTALS-Kyber algorithm specifications and supporting documentation. NIST PQC Round 2019, 2, 1–43. [Google Scholar]
- Langlois, A.; Stehlé, D. Worst-case to average-case reductions for module lattices. Des. Codes Cryptogr. 2015, 75, 565–599. [Google Scholar] [CrossRef]
- Rackoff, C.; Simon, D.R. Non-interactive zero-knowledge proof of knowledge and chosen ciphertext attack. In Proceeding of the Annual International Cryptology Conference; Santa Barbara, CA, USA, 11–15 August 1991, Springer: Berlin/Heidelberg, Germany, 1991; pp. 433–444. [Google Scholar]
- Bos, J.; Costello, C.; Ducas, L.; Mironov, I.; Naehrig, M.; Nikolaenko, V.; Raghunathan, A.; Stebila, D. Frodo: Take off the ring! practical, quantum-secure key exchange from LWE. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 1006–1018. [Google Scholar] [CrossRef]
- Targhi, E.E.; Unruh, D. Post-quantum security of the Fujisaki-Okamoto and OAEP transforms. In Proceedings of the Theory of Cryptography, 14th International Conference, TCC 2016-B, Beijing, China, 31 October–3 November 2016; Part II 14. Springer: Berlin/Heidelberg, Germany, 2016. [Google Scholar]
- Bos, J.W.; Costello, C.; Naehrig, M.; Stebila, D. Post-Quantum Key Exchange for the TLS Protocol from the Ring Learning with Errors Problem. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 17–21 May 2015; pp. 553–570. [Google Scholar] [CrossRef]
- Alkim, E.; Ducas, L.; Pöppelmann, T.; Schwabe, P. Post-quantum key Exchange—A new hope. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016; pp. 327–343. [Google Scholar]
- Bisheh-Niasar, M.; Azarderakhsh, R.; Mozaffari-Kermani, M. High-speed NTT-based polynomial multiplication accelerator for CRYSTALS-Kyber post-quantum cryptography. Cryptol. Eprint Arch. 2021. [Google Scholar] [CrossRef]
- Zhu, Y.; Zhu, M.; Yang, B.; Zhu, W.; Deng, C.; Chen, C.; Wei, S.; Liu, L. A High-Performance Hardware Implementation of Saber Based on Karatsuba Algorithm. Cryptology ePrint Archive. 2020. Available online: https://ia.cr/2020/1037 (accessed on 26 September 2023).
- Hao, Y.; Wang, W.; Dang, H.; Wang, G. Efficient Barrett Modular Multiplication Based on Toom-Cook Multiplication. IEEE Trans. Circuits Syst. II Express Briefs 2023. [Google Scholar] [CrossRef]
- Peikert, C. Public-key cryptosystems from the worst-case shortest vector problem. In Proceedings of the Forty-First Annual ACM Symposium on Theory of Computing, Bethesda, MD, USA, 31 May–2 June 2009; pp. 333–342. [Google Scholar] [CrossRef]
- Liang, W.; Li, Y.; Xu, J.; Qin, Z.; Zhang, D.; Li, K.-C. QoS Prediction and Adversarial Attack Protection for Distributed Services Under DLaaS. IEEE Trans. Comput. 2023. [Google Scholar] [CrossRef]
- Lyubashevsky, V.; Micciancio, D.; Peikert, C.; Rosen, A. SWIFFT: A Modest Proposal for FFT Hashing. In Fast Software Encryption. FSE 2008; Nyberg, K., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2008; Volume 5086. [Google Scholar] [CrossRef]
- He, S.; Malomed, B.A.; Mihalache, D.; Peng, X.; Yu, X.; He, Y.; Deng, D. Propagation dynamics of abruptly autofocusing circular Airy Gaussian vortex beams in the fractional Schrödinger equation. Chaos Solitons Fractals 2021, 142, 110470. [Google Scholar] [CrossRef]
- Canonne, C.L.; Kamath, G.; Steinke, T. The discrete gaussian for differential privacy. Adv. Neural Inf. Process. Syst. 2020, 33, 15676–15688. [Google Scholar] [CrossRef]
- Hofheinz, D.; Hövelmanns, K.; Kiltz, E. A modular analysis of the Fujisaki-Okamoto transformation. In Proceedings of the Theory of Cryptography Conference, Baltimore, MD, USA, 13–15 November 2017; Springer International Publishing: Cham, Switzerland, 2017. [Google Scholar]
- Chen, M.S.; Chou, T. Classic McEliece on the ARM cortex-M4. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2021, 2021, 125–148. [Google Scholar] [CrossRef]
- Zhang, W.; Zhu, S.; Tang, J.; Xiong, N. A novel trust management scheme based on Dempster–Shafer evidence theory for malicious nodes detection in wireless sensor networks. J. Supercomput. 2018, 74, 1779–1801. [Google Scholar] [CrossRef]
- Li, Y.; Liang, W.; Xie, K.; Zhang, D.; Xie, S.; Li, K. LightNestle: Quick and Accurate Neural Sequential Tensor Completion via Meta Learning. In Proceedings of the IEEE INFOCOM 2023-IEEE Conference on Computer Communications, New York, NY, USA, 17–20 May 2023; pp. 1–10. [Google Scholar] [CrossRef]
- Botros, L.; Kannwischer, M.J.; Schwabe, P. Memory-Efficient High-Speed Implementation of Kyber on Cortex-M4. In Progress in Cryptology–AFRICACRYPT 2019. AFRICACRYPT 2019; Buchmann, J., Nitaj, A., Rachidi, T., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2019; Volume 11627. [Google Scholar] [CrossRef]
- Bos, J.W.; Gourjon, M.O.; Renes, J.; Schneider, T.; Vredendaal, C.V. Masking kyber: First-and higher-order implementations. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2021, 2021, 173–214. [Google Scholar] [CrossRef]
- D’Anvers, J.-P.; Van Beirendonck, M.; Verbauwhede, I. Revisiting Higher-Order Masked Comparison for Lattice-Based Cryptography: Algorithms and Bit-Sliced Implementations. IEEE Trans. Comput. 2023, 72, 321–332. [Google Scholar] [CrossRef]
- Heinz, D.; Kannwischer, M.J.; Land, G.; Pöppelmann, T.; Schwabe, P.; Sprenkels, D. First-Order Masked Kyber on ARM Cortex-M4. Cryptology ePrint Archive. 2022. Available online: https://ia.cr/2022/058 (accessed on 26 September 2023).
- Nannipieri, P.; Di Matteo, S.; Zulberti, L.; Albicocchi, F.; Saponara, S.; Fanucci, L. A RISC-V Post Quantum Cryptography Instruction Set Extension for Number Theoretic Transform to Speed-Up CRYSTALS Algorithms. IEEE Access 2021, 9, 150798–150808. [Google Scholar] [CrossRef]
- Xing, Y.; Li, S. A Compact Hardware Implementation of CCA-Secure Key Exchange Mechanism CRYSTALS-KYBER on FPGA. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2021, 2021, 328–356. [Google Scholar] [CrossRef]
- Chen, J.; Liang, W.; Xiao, L.; Yang, C.; Zhang, R.; Gui, Z.; Poniszewska-Marańda, A. PrivBCS: A privacy-preserving and efficient crowdsourcing system with fine-grained worker selection based on blockchain. Connect. Sci. 2023, 35, 2202837. [Google Scholar] [CrossRef]
- Joseph, D.; Misoczki, R.; Manzano, M.; Tricot, J.; Pinuaga, F.D.; Lacombe, O.; Leichenauer, S.; Hidary, J.; Venables, P.; Hansen, R. Transitioning organizations to post-quantum cryptography. Nature 2022, 605, 237–243. [Google Scholar] [CrossRef]
- Xiong, N.; Han, W.; Vandenberg, A. Green cloud computing schemes based on networks: A survey. IET Commun. 2012, 6, 3294–3300. [Google Scholar] [CrossRef]
- Zhong, W.; Ce, Y.; Wei, L.; Cai, J.; Lin, C.; Jing, L.; Xiong, N. Byzantine Fault-Tolerant Consensus Algorithms: A Survey (2023-09-08). Electronics 2023, 12, 3801. [Google Scholar] [CrossRef]
- Wang, J.; Jin, C.; Tang, Q.; Xiong, N.N.; Srivastava, G. Intelligent Ubiquitous Network Accessibility for Wireless-Powered MEC in UAV-Assisted B5G. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2801–2813. [Google Scholar] [CrossRef]
- Wang, L.J.; Zhang, K.Y.; Wang, J.Y.; Cheng, J.; Yang, Y.H.; Tang, S.B.; Yan, D.; Tang, Y.L.; Liu, Z.; Yu, Y.; et al. Experimental authentication of quantum key distribution with post-quantum cryptography. NPJ Quantum Inf. 2021, 7, 67. [Google Scholar] [CrossRef]
- Kannwischer, M.J.; Rijneveld, J.; Schwabe, P. Faster Multiplication in Z2m[x] on Cortex-M4 to Speed up NIST PQC Candidates. In Applied Cryptography and Network Security. ACNS 2019; Deng, R., Gauthier-Umaña, V., Ochoa, M., Yung, M., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2019; Volume 11464. [Google Scholar] [CrossRef]
- Karmakar, A.; Mera JM, B.; Roy, S.S.; Verbauwhede, I. Saber on ARM CCA-secure module lattice-based key encapsulation on ARM. Cryptology ePrint Archive. 2018. Available online: https://ia.cr/2018/682 (accessed on 26 September 2023).
- Hu, W.J.; Fan, J.; Du, Y.X.; Li, B.S.; Xiong, N.; Bekkering, E. MDFC–ResNet: An agricultural IoT system to accurately recognize crop diseases. IEEE Access 2020, 8, 115287–115298. [Google Scholar] [CrossRef]
- Zhou, Y.; Zhang, Y.; Liu, H.; Xiong, N.; Vasilakos, A.V. A bare-metal and asymmetric partitioning approach to client virtualization. IEEE Trans. Serv. Comput. 2012, 7, 40–53. [Google Scholar] [CrossRef]
- Wang, Y.; Fang, W.; Ding, Y.; Xiong, N. Computation offloading optimization for UAV-assisted mobile edge computing: A deep deterministic policy gradient approach. Wirel. Netw. 2021, 27, 2991–3006. [Google Scholar] [CrossRef]
- Yu, J.; Liu, Z.; Liang, W.; Han, X.; Xiong, N. The Entropy-Based Hop Scheme for Influence Maximization in Dynamic Social Networks. Hum.-Centric Comput. Inf. Sci. 2023, 13, 40. [Google Scholar] [CrossRef]
- Zhao, J.; Huang, J.; Xiong, N. An effective exponential-based trust and reputation evaluation system in wireless sensor networks. IEEE Access 2019, 7, 33859–33869. [Google Scholar] [CrossRef]
- Shen, Y.; Fang, Z.; Gao, Y.; Xiong, N.; Zhong, C.; Tang, X. Coronary arteries segmentation based on 3D FCN with attention gate and level set function. IEEE Access 2019, 7, 42826–42835. [Google Scholar] [CrossRef]
- Zhang, S.; Hu, W.; Liang, W.; Lei, C.; Xiong, N. An Efficient Intelligent Control algorithm for Drying Rack System. IET Commun. 2023, 17, 1691–1705. [Google Scholar] [CrossRef]
- Kang, L.; Chen, R.-S.; Xiong, N.; Chen, Y.-C.; Hu, Y.-X.; Chen, C.-M. Selecting Hyper-Parameters of Gaussian Process Regression Based on Non-Inertial Particle Swarm Optimization in Internet of Things. IEEE Access 2019, 7, 59504–59513. [Google Scholar] [CrossRef]
- Huang, S.; Zeng, Z.; Ota, K.; Dong, M.; Wang, T.; Xiong, N.N. An Intelligent Collaboration Trust Interconnections System for Mobile Information Control in Ubiquitous 5G Networks. IEEE Trans. Netw. Sci. Eng. 2021, 8, 347–365. [Google Scholar] [CrossRef]
- Bernstein, D.J.; Chuengsatiansup, C.; Lange, T.; van Vredendaal, C. NTRU Prime: Reducing Attack Surface at Low Cost. In Selected Areas in Cryptography–SAC 2017. SAC 2017; Adams, C., Camenisch, J., Eds.; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2018; Volume 10719. [Google Scholar] [CrossRef]
- Lyubashevsky, V.; Peikert, C.; Regev, O. On ideal lattices and learning with errors over rings. Advances in Cryptology–EUROCRYPT 2010. In Proceedings of the 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar]







| Specific Classification | |
|---|---|
| Based on the relationship between the information element and the check factor | (1) Linear code (2) Nonlinear code |
| The type of correction based on the error code element | (1) Correct random error codes (2) Correct error codes (3) Correct synchronization error codes (4) It can correct both random errors and sudden error codes |
| Based on the processing of information elements | (1) Convolutional code (2) Block code |
| Based on the relationship between codewords | (1) Cyclic code (2) Acyclic code |
| Name | Advantages | Drawbacks |
|---|---|---|
| Lattice-based Cryptography | Based on lattice theory, security builds on number-theoretic puzzles; extensive research support and proven algorithms. | The computational intricacy of encryption and decryption is relatively high; the key and message lengths are long. |
| Code-based Cryptography | There has been a long history of research based on the difficult problem of error-correcting codes; relatively short key lengths. | Higher computational complexity for encryption and decryption; longer key and signature lengths. |
| Multivariate-based Cryptography | Difficult problems based on systems of polynomial equations that are mathematically rigorously defined and understood. This provides a solid theoretical foundation for security. | Encryption and decryption performance is relatively poor, requiring more computational resources and time. This may have an impact on the practical feasibility of certain application scenarios. |
| Hash-based Cryptography | Relatively mature schemes such as one-time signature schemes based on cryptographic hash functions (Merkle–Damgard constructs) are already available; shorter key and signature lengths. | The computational complexity of public-key exchange is high; it requires a long signature verification time. |
| Algorithm | Instance |
|---|---|
| symmetric encryption algorithm | AES, DES, 3DES |
| digital signature algorithm | RSA, DSA, ECDSA |
| key exchange algorithm | Diffie–Hellman, ECDH, MQV |
| hash function | SHA-1, SHA-2 Series, SHA-3 Series |
| message authentication code | HMAC, KMAC, CMAC |
| Random number generation | Hash_DRBG, CTR_DRBG, Dual_EC_DRBG, HMAC_DRBG |
| Category | Name | Overall |
|---|---|---|
| Lattice-based | CRYSTALS-DILITHIUM, DRS, FALCON, PqNTRUSign, qTESLA, Compact LWE, CRYSTALS-KYBER, Ding Key Exchange, EMBLEM and REMBLEM, FrodoKEM, HILA5, KCL, KINDI, LAC, LIMA, Lizard., LOTUS, NewHope, NTRU-HRSS-KEM, NTRU Prime, Odd Manhattan, Round2, SABER, Three Bears, Titanium | 26 |
| Code-based | PqsigRM, RaCoSS, BIG QUAKE, BIKE, Classic McEliece, DAGS, HQC, LAKE, LEDAkem, LEDApkc, Lepton, LOCKER, McNie, NTS-KEM, Quroboros-R, QC-MDPC KEM, RLCE-KEM, RQC | 18 |
| Multi-variate | DualModeMS, GeMSS, Gui, HiMQ-3, LUOV, MQDSS, Rainbow, CFPKM, DME | 9 |
| Symmetric/ Hash-based | Gravity-SPHINCS, Picnic, SPHINCS+ | 3 |
| Other | Post-quantum RSA-Signature, WainutDSA, Giophantus, Guess Again, Mersenne-756839, Post-quantum, RSA-Encryption, Ramstake SIKE | 8 |
| Total | 64 |
| n | t | i | |||||
|---|---|---|---|---|---|---|---|
| Kyber | 256 | 7681 | 3 | 4 | (11,3,11) | 161 |
| Work | Measure | Effect |
|---|---|---|
| Software Implementation | ||
| [81] | An improved optimization technology for NTT in Kyber is proposed. | Through experimental comparison, the improved software is 18% faster than the original author’s software. NTT in the improved software is more than twice as fast as the original software. |
| [82] | Kyber’s first complete masking was achieved by introducing two new technologies: Masked One-Bit Compression and Masked Decompressed Comparison. | The first masking scheme for complete Kyber decapsulation is proposed. Through experimental comparison, the improved software’s resistance to attacks has been improved. |
| [83] | Improve a technique to speed up OR operations at increased post-processing cost by replacing arithmetic multiplication with Galois field multiplication. | Through experimental comparison, the improved method is better than the original method. Implementation-specific improvements increase direct comparison implementation speed by 33%. |
| [84] | Kyber is optimized by combining different existing methods. Performance data were independently verified, and first-order resistance was confirmed using fixed and randomized TVLA methods. | A first-order shielded Kyber specifically for ARM CortexM4 is proposed and the first-order resistance is actually verified using ChipWhisperer Lite. It has been experimentally concluded that first-order masking is not sufficient to achieve practical side-channel immunity. |
| Hardware implementation | ||
| [85] | Embeds post-quantum ISA cryptographic extensions into the 64-bit CVA6 RISC-V processor and introduces new hardware features that map directly to assembly instructions. | Through experiments, we demonstrate that PQC algorithms can be significantly accelerated by leveraging the flexibility of RISC-V processors and integrating dedicated accelerators directly into the core pipeline. |
| [86] | Kyber’s independent hardware design is proposed through the FPGA platform. Through careful scheduling of sampling and Number Theoretic Transform (NTT)-related computations, good performance can be achieved with limited hardware resources. | Through careful scheduling and noise sampling of NTT-related procedures, the design achieves good performance and can be installed in the smallest devices in the Xilinx Artix-7 series FPGAs. Through experiments, the computational efficiency of the scheme based on structured lattice is verified. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, S.; Chen, Y.; Chen, L.; Liao, J.; Kuang, C.; Li, K.; Liang, W.; Xiong, N. Post-Quantum Security: Opportunities and Challenges. Sensors 2023, 23, 8744. https://doi.org/10.3390/s23218744
Li S, Chen Y, Chen L, Liao J, Kuang C, Li K, Liang W, Xiong N. Post-Quantum Security: Opportunities and Challenges. Sensors. 2023; 23(21):8744. https://doi.org/10.3390/s23218744
Chicago/Turabian StyleLi, Silong, Yuxiang Chen, Lin Chen, Jing Liao, Chanchan Kuang, Kuanching Li, Wei Liang, and Naixue Xiong. 2023. "Post-Quantum Security: Opportunities and Challenges" Sensors 23, no. 21: 8744. https://doi.org/10.3390/s23218744
APA StyleLi, S., Chen, Y., Chen, L., Liao, J., Kuang, C., Li, K., Liang, W., & Xiong, N. (2023). Post-Quantum Security: Opportunities and Challenges. Sensors, 23(21), 8744. https://doi.org/10.3390/s23218744







