An E2E Network Slicing Framework for Slice Creation and Deployment Using Machine Learning
Abstract
:1. Introduction
- To develop an effective method for slicing networks that makes use of the ML technique for the generation of slices and dynamic programming for the distribution of resources among the produced slices.
- Multi-layer perceptron (MLP) is adopted as the method to perform network slice classification. Also, MLP is investigated using a variety of weight optimization methods, and the most accurate classifier is that which has been selected.
- For slice creation, we conduct an exhaustive comparison of various ML algorithms including K-nearest neighbor (KNN), naive Bayes, support vector machine (SVM), random forest (RF), and MLP.
- We show that the present model is superior to the existing VNE approaches by providing empirical simulation results that are run under a variety of substrate network operating conditions.
2. Related Works
2.1. Slice Creation Using Machine Learning
2.2. Slice Deployment Using Virtual Network Embedding
3. Network Model
3.1. Substrate Network
3.2. Virtual Network Request
3.3. Slice Allocation
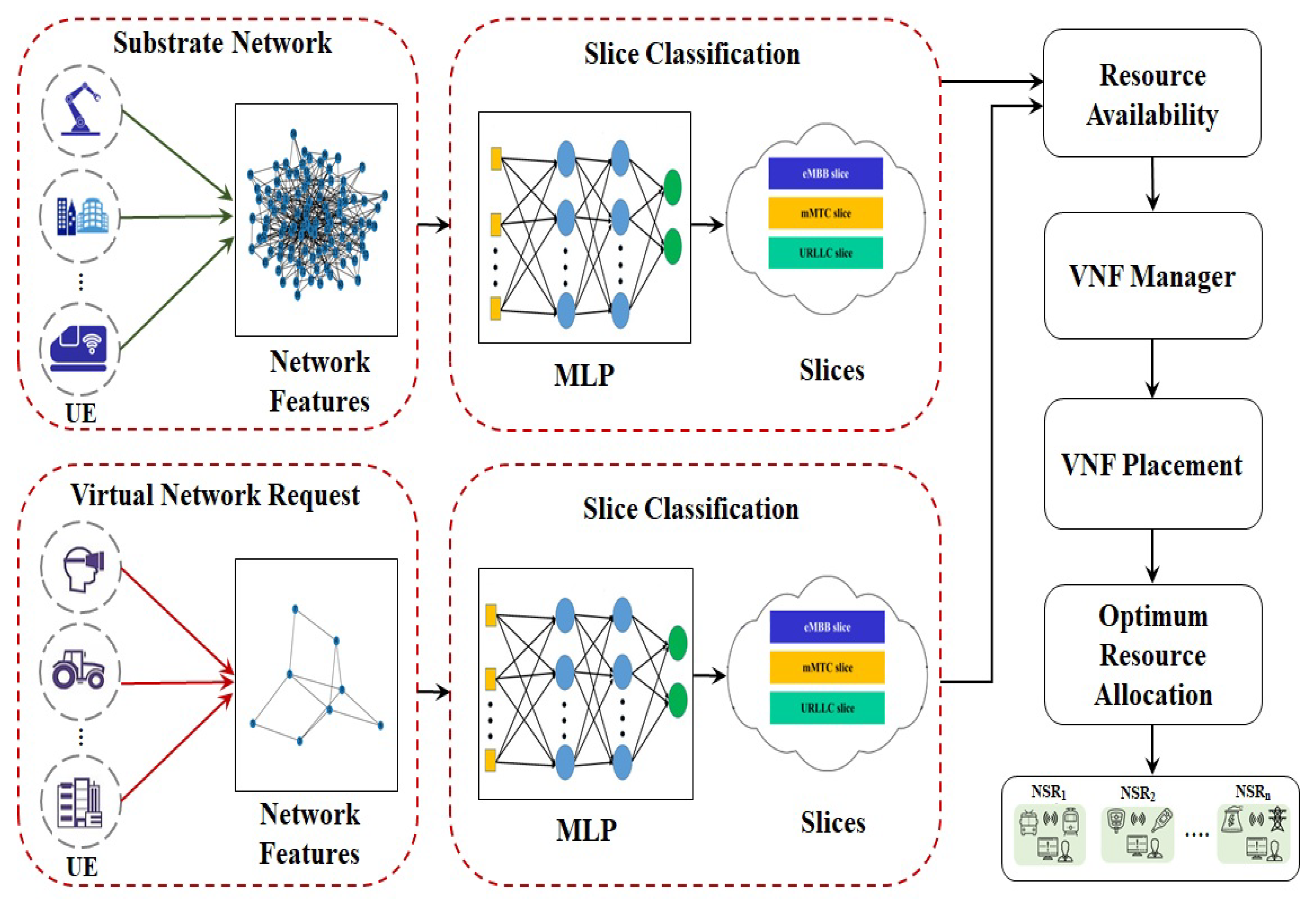
4. Design of E2E Network Slicing Using Machine Learning
4.1. Machine Learning-Based Slice Classification Model
| Algorithm 1 Slice classification using MLP |
Input: Substrate network Output: Node slice classification
|
4.1.1. K-Nearest Neighbor
4.1.2. Naive Bayes
4.1.3. Support Vector Machine
4.1.4. Random Forest
4.1.5. Multi-Layer Perceptron
4.2. Resource Allocation for E2E Network Slicing Using Dynamic Programming
4.2.1. Resource Provisioning Framework
| Algorithm 2 Resource allocation through dynamic programming |
Input: SN: , VNR: Output:
|
4.2.2. Performance Metrics for Optimal Resource Allocation
- (i)
- User access rate (UAR):where is the number of VNRs that are allocated into SN successfully and is the total number of requests received from time 0 to .
- (ii)
- Resource efficiency (RE):where shows the CPU load of the virtual node n, denotes the bandwidth of the virtual link L, and is the mapping length of the virtual link L. The revenue–cost ratio is used to calculate the efficiency of resources. A substrate network’s revenue from adopting a VNR is defined as the sum of the VNR’s capacity and link bandwidth requirements. The cost of a resource is determined by adding up the capacity of the nodes, the bandwidth resources of the link, and the path length of the link provided by the SN for the corresponding VNR nodes.
- (iii)
- Node utilization (NU) and link utilization (LU):where denotes total VNR, represents the total CPU capacity utilized for a VNR, and denotes the total bandwidth utilized for a VNR.
5. Experimental Results and Analysis
5.1. Simulation Testbed Settings
5.2. Performance Evaluation
5.2.1. Classification Reports
5.2.2. Performance of User Access Rate and Resource Efficiency
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Babbar, H.; Rani, S.; AlZubi, A.A.; Singh, A.; Nasser, N.; Ali, A. Role of Network Slicing in Software Defined Networking for 5G: Use Cases and Future Directions. IEEE Wirel. Commun. 2022, 29, 112–118. [Google Scholar] [CrossRef]
- Phyu, H.P.; Naboulsi, D.; Stanica, R. Machine Learning in Network Slicing—A Survey. IEEE Access 2023, 11, 39123–39153. [Google Scholar] [CrossRef]
- Zhang, S. An overview of network slicing for 5G. IEEE Wirel. Commun. 2019, 26, 111–117. [Google Scholar] [CrossRef]
- Ordonez-Lucena, J.; Ameigeiras, P.; Lopez, D.; Ramos-Munoz, J.J.; Lorca, J.; Folgueira, J. Network slicing for 5G with SDN/NFV: Concepts, architectures, and challenges. IEEE Commun. Mag. 2017, 55, 80–87. [Google Scholar] [CrossRef]
- Li, Q.; Wu, G.; Papathanassiou, A.; Mukherjee, U. An end-to-end network slicing framework for 5G wireless communication systems. arXiv 2016, arXiv:1608.00572. [Google Scholar]
- Irawan, D.; Syambas, N.R.; Ananda Kusuma, A.A.N.; Mulyana, E. Network Slicing Algorithms Case Study: Virtual Network Embedding. In Proceedings of the 2020 14th International Conference on Telecommunication Systems, Services, and Applications (TSSA), Bandung, Indonesia, 4–5 November 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Wang, G.; Feng, G.; Qin, S.; Wen, R.; Sun, S. Optimizing network slice dimensioning via resource pricing. IEEE Access 2019, 7, 30331–30343. [Google Scholar] [CrossRef]
- Yi, C.; Huang, S.; Cai, J. Joint resource allocation for device-to-device communication assisted fog computing. IEEE Trans. Mob. Comput. 2019, 20, 1076–1091. [Google Scholar] [CrossRef]
- Yi, C.; Cai, J.; Zhu, K.; Wang, R. A queueing game based management framework for fog computing with strategic computing speed control. IEEE Trans. Mob. Comput. 2020, 21, 1537–1551. [Google Scholar] [CrossRef]
- Yi, C.; Cai, J.; Su, Z. A multi-user mobile computation offloading and transmission scheduling mechanism for delay-sensitive applications. IEEE Trans. Mob. Comput. 2019, 19, 29–43. [Google Scholar] [CrossRef]
- Bega, D.; Gramaglia, M.; Banchs, A.; Sciancalepore, V.; Costa-Pérez, X. A machine learning approach to 5G infrastructure market optimization. IEEE Trans. Mob. Comput. 2019, 19, 498–512. [Google Scholar] [CrossRef]
- Preciado-Velasco, J.E.; Gonzalez-Franco, J.D.; Anias-Calderon, C.E.; Nieto-Hipolito, J.I.; Rivera-Rodriguez, R. 5G/B5G Service Classification Using Supervised Learning. Appl. Sci. 2021, 11, 4942. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Lee, J.H. Privacy-preserving data aggregation scheme against internal attackers in smart grids. Wirel. Netw. 2016, 22, 491–502. [Google Scholar] [CrossRef]
- Pham, Q.V.; Mirjalili, S.; Kumar, N.; Alazab, M.; Hwang, W.J. Whale Optimization Algorithm With Applications to Resource Allocation in Wireless Networks. IEEE Trans. Veh. Technol. 2020, 69, 4285–4297. [Google Scholar] [CrossRef]
- Gadekallu, T.R.; Khare, N.; Bhattacharya, S.; Singh, S.; Maddikunta, P.K.R.; Srivastava, G. Deep neural networks to predict diabetic retinopathy. J. Ambient. Intell. Humaniz. Comput. 2020. [Google Scholar] [CrossRef]
- He, D.; Ma, M.; Zeadally, S.; Kumar, N.; Liang, K. Certificateless Public Key Authenticated Encryption With Keyword Search for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3618–3627. [Google Scholar] [CrossRef]
- Chekired, D.A.; Togou, M.A.; Khoukhi, L.; Ksentini, A. 5G-Slicing-Enabled Scalable SDN Core Network: Toward an Ultra-Low Latency of Autonomous Driving Service. IEEE J. Sel. Areas Commun. 2019, 37, 1769–1782. [Google Scholar] [CrossRef]
- Abidi, M.H.; Alkhalefah, H.; Moiduddin, K.; Alazab, M.; Mohammed, M.K.; Ameen, W.; Gadekallu, T.R. Optimal 5G network slicing using machine learning and deep learning concepts. Comput. Stand. Interfaces 2021, 76, 103518. [Google Scholar] [CrossRef]
- Xiao, Y.; Zhang, Q.; Liu, F.; Wang, J.; Zhao, M.; Zhang, Z.; Zhang, J. NFVdeep: Adaptive Online Service Function Chain Deployment with Deep Reinforcement Learning. In Proceedings of the 2019 IEEE/ACM 27th International Symposium on Quality of Service (IWQoS), Phoenix, AZ, USA, 24–25 June 2019; pp. 1–10. [Google Scholar] [CrossRef]
- Wang, H.; Wu, Y.; Min, G.; Xu, J.; Tang, P. Data-driven dynamic resource scheduling for network slicing: A Deep reinforcement learning approach. Inf. Sci. 2019, 498, 106–116. [Google Scholar] [CrossRef]
- Gupta, R.K.; Misra, R. Machine Learning-based Slice allocation Algorithms in 5G Networks. In Proceedings of the 2019 International Conference on Advances in Computing, Communication and Control (ICAC3), Mumbai, India, 20–21 December 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Abbas, K.; Afaq, M.; Khan, T.A.; Mehmood, A.; Song, W.C. IBNSlicing: Intent-based network slicing framework for 5G networks using deep learning. In Proceedings of the 2020 21st Asia-Pacific Network Operations and Management Symposium (APNOMS), Daegu, Republic of Korea, 22–25 September 2020; pp. 19–24. [Google Scholar]
- Thantharate, A.; Paropkari, R.; Walunj, V.; Beard, C. Deepslice: A deep learning approach towards an efficient and reliable network slicing in 5G networks. In Proceedings of the 2019 IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 10–12 October 2019; pp. 762–767. [Google Scholar]
- Zhang, Q.; Liu, F.; Zeng, C. Online Adaptive Interference-Aware VNF Deployment and Migration for 5G Network Slice. IEEE/ACM Trans. Netw. 2021, 29, 2115–2128. [Google Scholar] [CrossRef]
- Chirivella-Perez, E.; Salva-Garcia, P.; Sanchez-Navarro, I.; Alcaraz-Calero, J.M.; Wang, Q. E2E network slice management framework for 5G multi-tenant networks. J. Commun. Netw. 2023, 25, 392–404. [Google Scholar] [CrossRef]
- Taleb, T.; Mada, B.; Corici, M.I.; Nakao, A.; Flinck, H. PERMIT: Network Slicing for Personalized 5G Mobile Telecommunications. IEEE Commun. Mag. 2017, 55, 88–93. [Google Scholar] [CrossRef]
- Mei, C.; Liu, J.; Li, J.; Zhang, L.; Shao, M. 5G network slices embedding with sharable virtual network functions. J. Commun. Netw. 2020, 22, 415–427. [Google Scholar] [CrossRef]
- Li, X.; Guo, C.; Gupta, L.; Jain, R. Efficient and secure 5G core network slice provisioning based on VIKOR approach. IEEE Access 2019, 7, 150517–150529. [Google Scholar] [CrossRef]
- Cheng, X.; Su, S.; Zhang, Z.; Wang, H.; Yang, F.; Luo, Y.; Wang, J. Virtual Network Embedding through Topology-Aware Node Ranking. ACM SIGCOMM Comput. Commun. Rev. 2011, 41, 38–47. [Google Scholar] [CrossRef]
- Guan, W.; Wen, X.; Wang, L.; Lu, Z.; Shen, Y. A Service-Oriented Deployment Policy of End-to-End Network Slicing Based on Complex Network Theory. IEEE Access 2018, 6, 19691–19701. [Google Scholar] [CrossRef]
- Raghavendra Prasad, J.; Senthil, M.; Yadav, A.; Gupta, P.; Anusha, K. A comparative study of machine learning algorithms for gas leak detection. In Inventive Communication and Computational Technologies: Proceedings of ICICCT 2020; Springer: Berlin/Heidelberg, Germany, 2021; pp. 81–90. [Google Scholar]
- Archanaa, R.; Athulya, V.; Rajasundari, T.; Kiran, M.V.K. A comparative performance analysis on network traffic classification using supervised learning algorithms. In Proceedings of the 2017 4th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, Tamil Nadu, India, 6–7 January 2017; pp. 1–5. [Google Scholar]
- Balachandran, A.; Amritha, P. Vpn network traffic classification using entropy estimation and time-related features. In IOT with Smart Systems: Proceedings of ICTIS 2021; Springer: Berlin/Heidelberg, Germany, 2022; Volume 2, pp. 509–520. [Google Scholar]
- Nair, M.R.; Ramya, G.; Sivakumar, P.B. Usage and analysis of Twitter during 2015 Chennai flood towards disaster management. Procedia Comput. Sci. 2017, 115, 350–358. [Google Scholar] [CrossRef]
- Landro, N.; Gallo, I.; La Grassa, R. Combining Optimization Methods Using an Adaptive Meta Optimizer. Algorithms 2021, 14, 186. [Google Scholar] [CrossRef]
- Barabasi, A.L.; Albert, R. Emergence of Scaling in Random Networks. Science 1999, 286, 509–512. [Google Scholar] [CrossRef]
- Thiruvenkadam, S.; Sujitha, V.; Jo, H.G.; Ra, I.H. A Heuristic Fuzzy Based 5G Network Orchestration Framework for Dynamic Virtual Network Embedding. Appl. Sci. 2022, 12, 6942. [Google Scholar] [CrossRef]
- Yu, M.; Yi, Y.; Rexford, J.; Chiang, M. Rethinking virtual network embedding: Substrate support for path splitting and migration. ACM SIGCOMM Comput. Commun. Rev. 2008, 38, 17–29. [Google Scholar] [CrossRef]
- Wang, Z.; Han, Y.; Lin, T.; Tang, H.; Ci, S. Virtual network embedding by exploiting topological information. In Proceedings of the 2012 IEEE Global Communications Conference (GLOBECOM), Anaheim, CA, USA, 3–7 December 2012; pp. 2603–2608. [Google Scholar] [CrossRef]











| Ref. No. | Methodology | Techniques | Objectives | Limitations |
|---|---|---|---|---|
| [21] | Supervised machine learning | K-nearest neighbors Random forest | - To meet QoS and SLA, allocates slices for services through ML | - Works better with the dataset used, but its performance measurement is not performed under high traffic |
| [22] | Deep learning | Generative adversarial neural network | - To automate slice creation and network settings | - Limited functionalities and need to add more features for network slicing life cycle management |
| [18] | Machine and deep learning | Deep neural network Glowworm swarm optimization and deer hunting optimization algorithm | - To provide accurate network slicing | - Used for small-scale problems, but has to be performed for real-time data and a huge amount of data in the cloud |
| [23] | Deep learning | Deep learning neural network | -To efficiently handle network load balancing and slice failures | - Due to the complexity of the dataset, training is incredibly expensive |
| [27] | Shareable VNF | Integer linear program Back-tracking coordinated virtual network mapping | - To minimize the resource consumption by integrating shareable VNF instances to increase acceptance rate and efficiency | - Assumed as all nodes of NSR requests for similar kinds of use cases. |
| [28] | VIKOR approach | Integer linear program Multi-criteria decision making | - To maximize slice acceptance and provide revenue-to-cost | - Performed better in slice traffic loads but need to improve performance in dynamic reprovisioning of slices |
| [30] | Complex network theory | Integer linear program Floyd algorithm | - To achieve higher resource efficiency and acceptance ratio with minimum execution time | - Assumed as all nodes of NSR requests for similar kinds of use cases |
| Substrate Network | |
|---|---|
| Terms | Specifications |
| Each node contains 20 to 50 CPU units | |
| Each node has a 20 to 50 unit link capacity | |
| The security level of a node from 0 to 1 | |
| Bandwidth of each link in the range of 20 to 50 units | |
| Each node’s delay time varies from 0 to 1 | |
| Virtual Network | |
| Terms | Specifications |
| CPU capacity of each VNR node in the range of 5 to 25 units | |
| Link capacity of each VNR node in the range of 5 to 25 units | |
| Available security level of a request in the range of 0 to 0.5 | |
| Bandwidth of each VNR link in the range of 0 to 25 units | |
| Delay time between each node is between 0 and 0.5 | |
| MLP | eMBB | mMTC | uRLLC | Accuracy | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| Precision | Recall | F1 Score | Precision | Recall | F1 Score | Precision | Recall | F1 Score | (%) | |
| LBFGS | 0.89 | 0.92 | 0.89 | 0.88 | 0.85 | 0.89 | 0.88 | 0.91 | 0.88 | 88 |
| SGD | 0.90 | 0.95 | 0.91 | 0.98 | 0.97 | 0.98 | 0.92 | 0.83 | 0.87 | 93 |
| ADAM | 0.98 | 0.98 | 0.98 | 0.98 | 0.97 | 0.98 | 0.97 | 0.98 | 0.97 | 98 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Venkatapathy, S.; Srinivasan, T.; Jo, H.-G.; Ra, I.-H. An E2E Network Slicing Framework for Slice Creation and Deployment Using Machine Learning. Sensors 2023, 23, 9608. https://doi.org/10.3390/s23239608
Venkatapathy S, Srinivasan T, Jo H-G, Ra I-H. An E2E Network Slicing Framework for Slice Creation and Deployment Using Machine Learning. Sensors. 2023; 23(23):9608. https://doi.org/10.3390/s23239608
Chicago/Turabian StyleVenkatapathy, Sujitha, Thiruvenkadam Srinivasan, Han-Gue Jo, and In-Ho Ra. 2023. "An E2E Network Slicing Framework for Slice Creation and Deployment Using Machine Learning" Sensors 23, no. 23: 9608. https://doi.org/10.3390/s23239608
APA StyleVenkatapathy, S., Srinivasan, T., Jo, H.-G., & Ra, I.-H. (2023). An E2E Network Slicing Framework for Slice Creation and Deployment Using Machine Learning. Sensors, 23(23), 9608. https://doi.org/10.3390/s23239608






