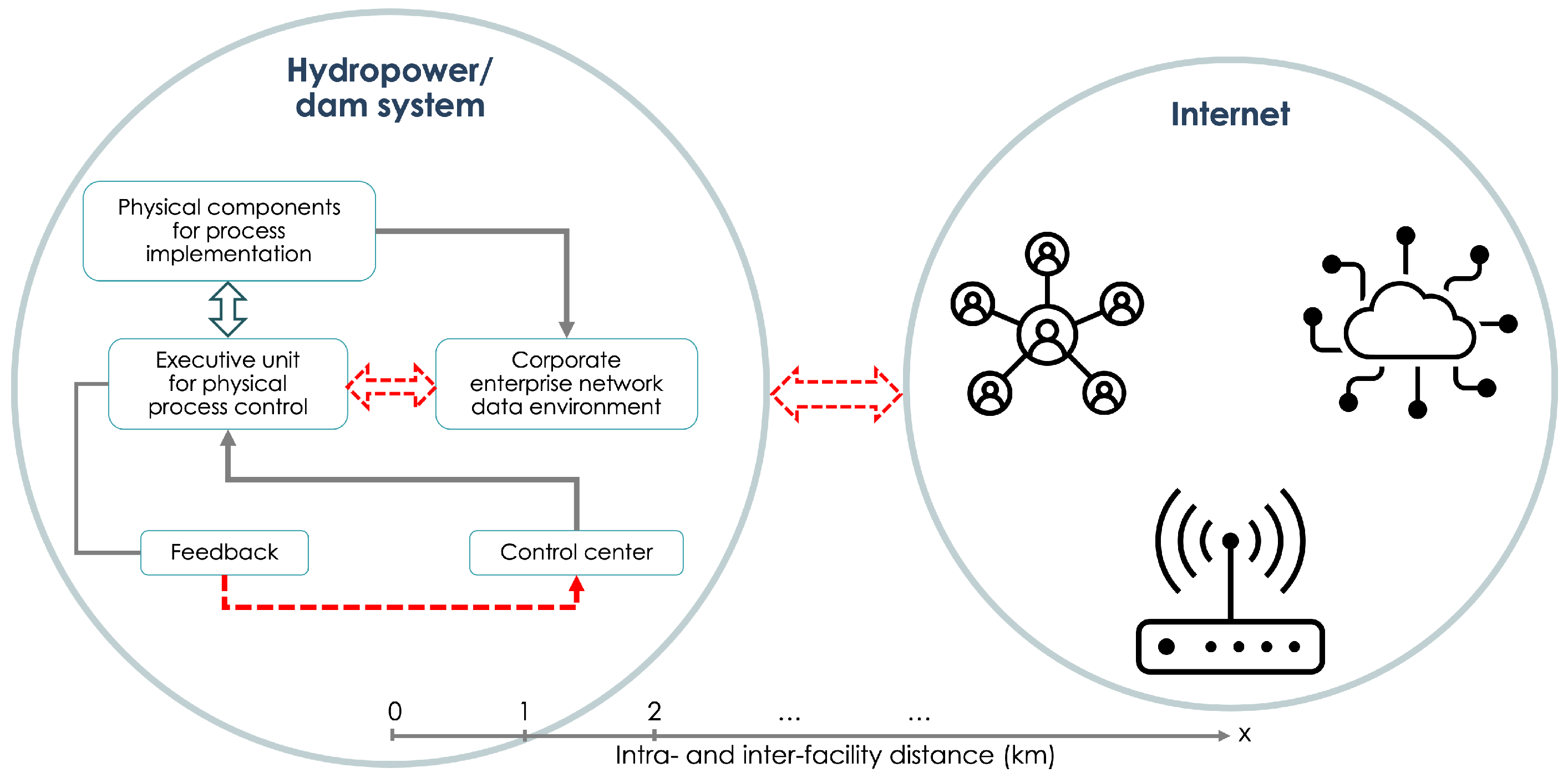
4.2. Integration of the QKD System with the Hydro Communications System
QKD is a novel quantum-based cybersecurity tool that allows for the generation and secure distribution of truly random number streams. Field demonstration of QKD has been reported in the case of a real-world electric utility optical fiber network [
13]. A “key” is simply a string of bits, that is, a sequence of 0 s and 1 s, and a “message” is in the form of a bit-string. The end goal here is the successful use of keys generated using QKD by the communicating parties. For example, when the two communicating parties share a private key, they can use that key to encrypt any messages they intend to send and decrypt any messages they receive. This encryption prevents eavesdropping from accessing any information in the messages. This could, for example, take the form of the complete set of communications needed for remote control of a dam, or communication for a SCADA system [
54]. This would ultimately entail generating random bits that are supplied to a computer hard drive or memory, at two (or more) locations. These bits are then to be used for the encryption of the messages between the two locations. Optical fiber-based QKD is highly versatile as fibers are immune to electromagnetic interference, and mechanically flexible so that they can penetrate confined areas, elaborate machines, and devices. The QKD process begins with a quantum transmitter (typically referred to as Alice, as indicated in
Figure 5). The sender will have to generate light and prepare it in a specific quantum state. These light pulses, representing bit-strings, are then sent into an optical fiber to travel to another location, where they can be detected by a quantum receiver (typically referred to as Bob, as indicated in
Figure 5), at the other end of the fiber. After concluding the quantum operations between the two communicating parties, to generate the final keys, the bit-streams must be post-processed. After processing the keys, as shown in
Figure 5, they can be used to protect the information between communicating entities (users, control systems, sensors, actuators, SCADAs, etc.).
The distributed keys are stored on a local computer where the encryption and authentication [
12] may be implemented. The most computationally efficient (and therefore lowest-latency) encryption method remains the one-time-pad (OTP) method, where a message and key are combined with the exclusive OR operation (XOR). OTP exhibits ITS (information-theoretical security), i.e., it is secure regardless of an adversary’s computational power, with the following requirements: (1) the keys must be truly random, be kept secret, be are used once only, and (2) the message length is less than or equal to the length of the key. The resulting communications are then sent out through a classical transceiver. An experimental demonstration of relaying keys between relevant hydro infrastructure locations could conclude after a QKD operation over a given period (e.g., ∼hours). Such an experiment could implement QKD over a metro area distance (typical of hydro facilities) using a commercial QKD system. The main metric governing QKD system performance is the secret key rate (SKR), i.e., the (average) number of secret bits generated and distributed securely between parties per second. SKR, while largely dependent on the type of system and QKD protocol employed, is ultimately determined by the optical loss on a given fiber link. This loss
, expressed in units of dB, is largely due to the fiber’s attenuation
a dB/km, which typically arises due to absorption and scattering mechanisms and can be written for a fiber of length
L km as
. It is crucial to minimize the losses, which also can be exacerbated by fiber-to-fiber connectors, sharp fiber bending, and splicing. High losses will reduce the throughput of the QKD process. The greater the optical loss, the lower the SKR, and vice versa. In situations where the optical link loss is significant, the SKR can be zero, indicating that no secret keys can be generated. From a practical standpoint, as noted above, optical losses receive contributions from two main factors: the physical distance along the fiber between two points (length attenuation) and splice, or connection losses. The former is indicative of intrinsic material losses in the optical fiber itself. Modern deployed optical fibers exhibit ≈ (0.2–0.5) dB/km for standard single mode fiber for telecommunications wavelengths around 1.3 to 1.6
m. Modern fibers could have slightly lower loss than 0.2 dB/km, around 1.54
m, but the inclusion of fiber-to-fiber connections, including in-field splices during deployment and patch cable connections within a communications facility or substation, can increase the average propagation loss. For this attenuation range, if, as simulated in
Figure 6, the fiber is 175 km long, the total loss in the fiber will be in the range of
(35–87.5) dB. Consequently, a viable QKD deployment must evaluate the optical link conditions between locations to see if it will allow for sufficient SKR for the desired operational requirements.
In QKD, the eventual length of the secure key is determined by several factors, including channel noise, error rates, and the specifics of the chosen protocol. While longer data collection times can yield larger secret keys, this could introduce delays before the key becomes available for encryption purposes. This is due to the need for post-processing steps like error correction, privacy amplification, and particularly the estimation of parameters such as the quantum bit error ratio (QBER) using a substantial portion of the sifted key. For real-world applications in hydropower plants, system optimization becomes vital. For instance, when several single-photon detectors in a command center are shared between remote links, the time each remote device utilizes a given detector should be optimized to reduce the total number of necessary detectors. This not only aids in efficient key generation but also in minimizing costs associated with hardware. The key rate or efficiency is not determined by a pre-selected length but rather emerges from the conditions of the quantum channel and post-processing. Practical QKD systems also need to address finite-size effects, where the security of the generated key can be influenced by statistical fluctuations. These effects become crucial in real-world applications such as hydropower plants, where reliable and timely key generation might be essential. An understanding of the communication frequency and topology between devices in such environments will be pivotal in tailoring QKD systems for optimal performance and cost-efficiency.
Figure 6 depicts how the SKR varies with distance for different key lengths, highlighting the impact of channel loss on the key rate. Similarly,
Figure 6 illustrates the SKR’s sensitivity to misalignment angles in the system. The secure key rate (SKR), as derived from the theoretical framework introduced by Lim et al. [
55], illustrates this dependency. In the protocol proposed by Lim et al., Alice sends Bob randomly polarized coherent states in two orthogonal bases: X and Z. While the X basis contributes to the secure key, the Z basis states are publicly disclosed to estimate the error rate in the X basis. The effective secure key length
is then described by:
where
and
represent the number of dark counts and single-photon counts at Bob’s detector, respectively. The term
denotes the error rate in the x basis. The binary entropy function
[
56] is given by:
which captures the maximum information Eve can deduce about the total key given the shared bits used to determine the error rate. As such, the term
must be subtracted from the total to yield a portion of the key that remains concealed from Eve.
encapsulates the information exposed during error correction, while the concluding terms address finite-size effects. A deeper analysis, especially of terms rooted in the X basis signals and shaped by the sacrificed Z basis signals, is detailed in [
55].
Figure 6 illustrates how the choice of key length, influenced by finite-size statistics, affects the secure key rate and associated generation time. Specifically, at a distance of 1 km, starting with the aim of distilling a 100-million-bit secure key yields a final key rate of approximately 98 kbps and takes 17 min to distill. In contrast, aiming for a 100-thousand-bit secure key results in a lower final key rate of about 25 kbps but only takes 4 s total to distill. Note that finite-size effects cause shorter key lengths to have higher uncertainty in the error and thus more bits are thrown away in post-processing, reducing key generation rates. In a continually operating secure communication system, these trade-offs highlight the importance of preemptive considerations. Factors such as communication frequency and average message size play a pivotal role in optimizing system performance and cost. Such metrics also influence choices regarding the QKD protocol, quantum encoding strategy, and equipment selection, ensuring that the system meets or exceeds the desired performance benchmarks.
Figure 6.
The final secure key rate as a function of the distance between communicating parties, derived from fiber-based loss and error models according to Equations (
2) and (
3). This representation assumes a decoy state BB84 variant of QKD, with parameters grounded in real-world and feasible experimental setups. As can be seen, for longer key lengths, the allowable communication distance before the SKR becomes impractical is reduced. An example of such a system, simulated at the University of Tennessee for a free-space deployment, is presented in [
57]. Conventional devices, including a 1550 nm continuous wave laser and single-photon avalanche detectors, were employed in their work. At the rates shown, 100-thousand-bit key takes 4 s to distill and the 100-million-bit key takes 17 min.
Figure 6.
The final secure key rate as a function of the distance between communicating parties, derived from fiber-based loss and error models according to Equations (
2) and (
3). This representation assumes a decoy state BB84 variant of QKD, with parameters grounded in real-world and feasible experimental setups. As can be seen, for longer key lengths, the allowable communication distance before the SKR becomes impractical is reduced. An example of such a system, simulated at the University of Tennessee for a free-space deployment, is presented in [
57]. Conventional devices, including a 1550 nm continuous wave laser and single-photon avalanche detectors, were employed in their work. At the rates shown, 100-thousand-bit key takes 4 s to distill and the 100-million-bit key takes 17 min.
The unique environment of a hydropower plant (see
Table 4) introduces specific imperfections crucial in the context of a QKD system. Predominantly, additional loss and noise from such a setting can elevate the QBER rates for the QKD system. For instance, vibrations and noises from turbine operations and machinery can induce phase fluctuations in the quantum states used in QKD, leading to increased QBER. Similarly, noises from waterfall/spill and flow turbulence could impact the alignment and synchronization of the QKD system. Given the finite-size effect in the context of secure encryption, variations in QBER invariably gravitate towards the maximum bound of error. Hence, fluctuations introduced by the dam environment can be quite influential. The channel error model used for QKD simulations is described by Equation (
4) [
55]:
where
is the error rate for a coherent pulse with intensity
k,
is the background noise rate of the detector (dark count rate),
is the after-pulse probability, and
is the detection rate.
represents the loss due to the fiber optic cables and is given by
, with
L being the fiber length in km. The term
stands for the probability of error due to polarization changes in the channel and can be influenced by environmental factors.
Given that turbine operations, with their frequencies typically around 1 Hz and 30 Hz (
Table 4), can introduce vibrations of typically less than 1 mm in amplitude and that generators, operating at either 50 Hz or 60 Hz, induce similar amplitudes of vibrations, the environment’s vibrational noise becomes crucial. Environmental factors, from seismic activities to localized events like machinery operations, can further introduce vibrational noise that influences the polarization states in fiber optics, which are sensitive to such changes [
58]. Understanding and mitigating these effects is pivotal for QKD. For instance, correlating the vibrational frequency and amplitude data with phase changes in the QKD system could enable real-time counteraction of potential misalignment errors. As observed in
Figure 7, by choosing longer final key lengths, we can generate secure bits at a higher misalignment, an important consideration in a noise-prone dam environment. To ensure high secure key rates, polarization-based hydro QKD systems should adopt polarization stabilization techniques [
59,
60]. Typically, stabilization is achieved through feedback loops that monitor changes in the final state, enabling the sender to effectuate corrections. Given that numerous dams employ fiber-based sensors [
61,
62], integrating such vibrational and noise data into the stabilization algorithm offers a promising avenue to maintain optical alignment, optimizing the QKD system’s performance.
It is also worth noting here that recent advancements in QKD technologies, such as the integration of advantage distillation technology with decoy state QKD systems, have shown significant improvements in both the maximal transmission distance and the maximal tolerable error rate. This enhancement is particularly crucial for the extensive and remote operations characteristic of hydropower facilities, ensuring robust and secure communications over longer distances with higher reliability (see Li et al. [
63]).
With measured SKR metrics in hand, the most appropriate cybersecurity strategy for QKD-secured hydro communications should be evaluated. This can be guided by the following principle. If the classical communication bandwidth needs for hydro are less than the SKR, then OTP may be employed (i.e., number of final key bits > number of classical bits requiring encryption). However, if the classical communication bandwidth needs exceed the link-specific SKR, then an alternative method must be employed, for example, where the same QKD key can be used to authenticate multiple messages, which can be accomplished as long as a QRNG supplies a new nonce [
12]. Finally, regardless of the cryptography option above (OTP or authentication), the interface required to supply QKD keys to the user/application must be developed. This is dependent on the type, vendor, model of the user/application, and methods by which the device allows ingestion of external (i.e., QKD) key material. This final experiment will demonstrate the encryption/decryption of realistic hydropower command/control communications using QKD-supplied keys. Performance challenges include SKR changes with variations in the environment in which the subsystems of QKD are to operate. Dealing with various sources of noise (including those in
Table 4) is of great importance in the successful generation of keys. For example, when both quantum and classical light are considered over the channel, a concern arises from “Raman noise”, which is unwanted light generated in the fiber material due to the scattering of stronger classical light. This effect is particularly pronounced when the wavelengths of the quantum and classical signals are closely multiplexed in wavelength. However, when they are in far-detuned bands, such as the quantum signal in the O band and the classical signal in the C band, the impact of Raman scattering is substantially mitigated [
64,
65]. Appropriate hardware choices can be made to better address the challenges and noise sources associated with the specific setting of the hydro facility. Although several QKD protocols exist, the well-established Bennet–Brassard protocol (BB84 protocol) makes for a suitable trial. Using the software, the dam communications can be interfaced with QKD keys. Similar experiments have been effectively performed to analyze and address implementation challenges facing the deployment of QKD systems in critical infrastructure, for example, as demonstrated in the recent field test of three QKD systems on a real-world electric utility optical fiber network [
13], where one endpoint was a hydro/dam.