Secure Data Transfer Based on a Multi-Level Blockchain for Internet of Vehicles
Abstract
:1. Introduction
2. Related Work
- (1)
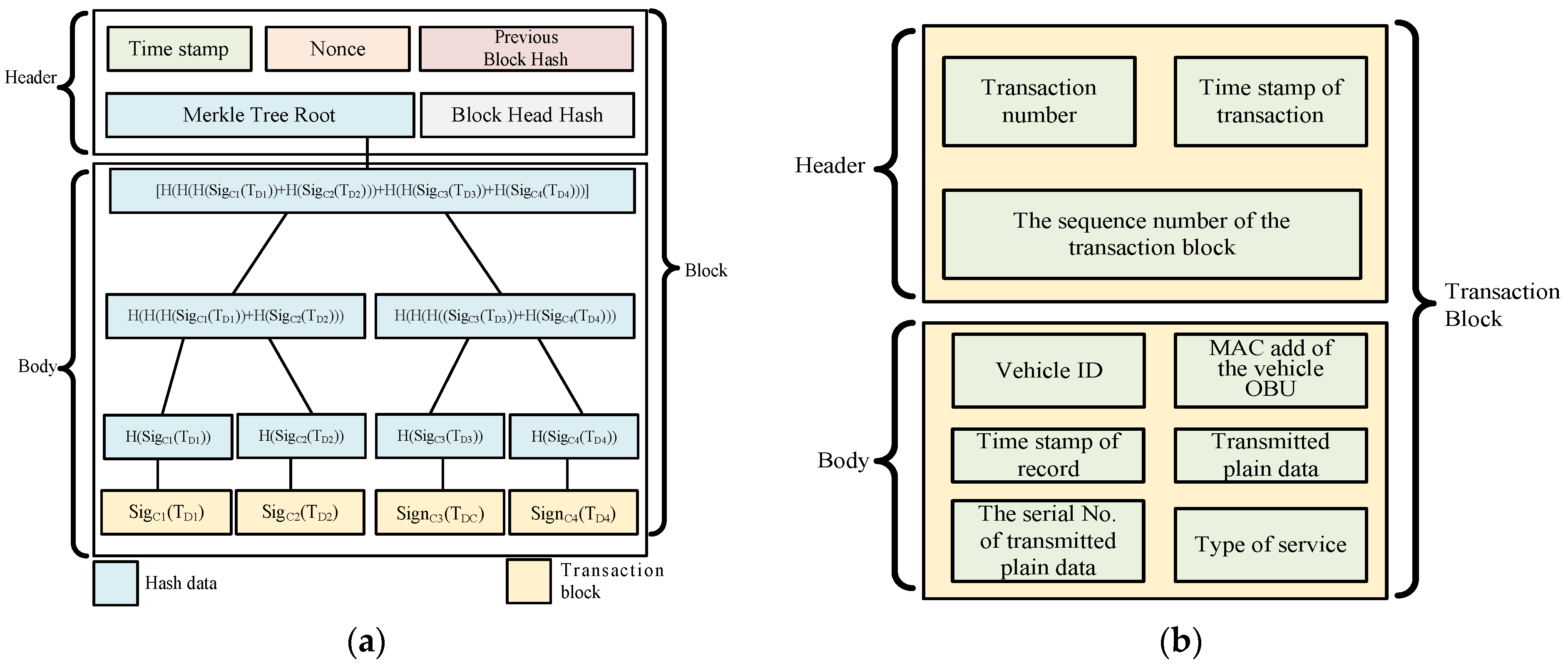
- Pervious block hash: The prev_hash value is the hash calculated from the block header of the preceding block.
- (2)
- Timestamp: Generate the timestamp of this block.
- (3)
- Nonce: This represents how many workload algorithms there are and how difficult these algorithms are.
- (4)
- Merkle tree root hash: This represents the value of the hash operation of the current block body and the hash value of the Merkle root node that is computed according to the algorithm of the Merkle tree.
- (1)
- Genesis block:
- (2)
- The blockchain is not able to be altered:
- (1)
- In 2019, Jiang et al. [7] divided the application of the blockchain in business transactions and management models into five categories, namely vehicle management blockchain, vehicle manufacturing blockchain, user privacy blockchain, vehicle insurance purchase blockchain and the common data blockchain. Shrestha et al. [8] proposed that a regional blockchain can achieve an attack success rate of 51% by controlling several control parameters, such as the number of vehicles, malicious vehicles, messaging and time and puzzle calculations under the premise of ensuring stability.
- (2)
- In 2019, Ma et al. [9] proposed a privacy-secure and decentralized vehicle network architecture. In the architecture, RSUs play the role of the main blockchain storage node. In addition, the cloud computing node is in charge of storing and backing up the data of the blockchain. Moreover, this architecture consists of two distinct sub-blockchains, called inter-blockchain and intra-blockchain. Interchain is in charge of communicating information between RSUs, vehicles and infrastructure. The intrachain supports sensors that allow drivers to communicate with passengers in the car.
- (3)
- In 2020, Dai et al. and Lu et al. [10,11], based on a ledger structure, set up a private blockchain to store transactions on a secure communication network with crowdsourcing tasks. Overcoming the traditional crowdsourcing single-point error problem, Liu et al. [12] incorporated blockchain mechanisms at the data layer, network layer, application layer, AI layer and business layer. Among them, the network layer contains the peer-to-peer network sublayer and the collaborative network module of the blockchain. Moreover, the AI layer consists of the consensus sublayer of the blockchain, the analysis services and vehicle-oriented computing, including the block consensus protocol executed at this layer.
- (4)
- Lu et al. [13] offered a blockchain-based VANETs (vehicular ad hoc networks) privacy protection authentication protocol in 2019 called the BPPA protocol. The authors developed a privacy-preserving authentication blockchain for VANETs. The proposed BPPA scheme uses a blockchain to remain immutable and store all credentials and transactions to achieve transparency and verifiability of TAs. In addition, this research provides a mechanism capable of distributed authentication but does not need a revocation list. To achieve indirect privacy, the study authorizes vehicles to deploy credentials that are encrypted and retained in the blockchain. If there is an inconsistency, it can be disclosed through a link.
- (5)
- In 2022, Cui et al. [14] designed an effective data-sharing method between vehicles named the consortium blockchain. In traditional vehicle systems, data sharing takes place between the vehicle and roadside equipment. However, the authors used a distributed technology consortium to enable the sharing of traceable information between anonymous vehicles. Furthermore, the combination of 5G and blockchain makes it possible to share data with no RSUs.
- (6)
- In 2021, Bagga and other scholars [15] proposed a batch authentication protocol for blockchain-based IoT. There are two types of authentication: (1) vehicle-to-vehicle authentication. In a cluster, this mode allows the authentication of a vehicle with adjacent vehicles. (2) Batch authentication enables the same group of vehicles to authenticate via their RSUs. Ultimately, cluster vehicles and RSUs can collaborate to establish a group key.
- (7)
- In 2021, Maria et al. [16] proposed an anonymous authentication mechanism, which can be applied to the security of the vehicular ad hoc networks during the switching process between the vehicles and the roadside device RSU that consumes fewer computing resources at reduced costs.
- (8)
- In 2022. Zheng et al. [17] offered a lightweight blockchain-based authentication and an IoT key agreement to improve the effectiveness of the authentication using a multi-TA model. The authors used the blockchain to save the vehicle’s authentication information and cross-region authentication to protect the user’s private information. At the same time, the proposed method adopts lightweight computing to shorten the certification time of the vehicles and complete the whole certification procedure.
3. A Secure Data Transfer Based on a Multi-Level Blockchain Framework for Internet of Vehicles
3.1. The Transaction Block and the ECDSA Digital Signature for IoVs
- (1)
- Transaction number: the serial number of the transaction.
- (2)
- Timestamp of the transaction: when the transaction block was produced.
- (3)
- The sequence number of the transaction block: the sequence of the transaction block that is generated.
- (1)
- Vehicle ID: Identification of the vehicle.
- (2)
- MAC add of the vehicle OBU: the vehicle hardware manufacturing number.
- (3)
- Timestamp of record: the time in which the transaction record is generated.
- (4)
- Transmitted plain data: textual information to be transmitted by vehicles.
- (5)
- The serial number of the transmitted plain data: the amount of data to be transmitted by the vehicles.
- (6)
- Type of service: The category of cloud service required for the vehicle.
- Phase 1.
- First, the registered OBU takes an elliptic curve EGF(p) (l, q) and owns an order d = |EGF(p) l, q)| + 1 and a generator R. Moreover, d indicates the number of points on this curve containing the distant point to infinity.
- Phase 2.
- Afterward, this vehicle OBU selects a private key S and a point R = (XR, YR); S is between 1 and d − 1, and d is the R order. In the meantime, the OBU computes the public key PK = S × R = S × (XR, YR) through the R generator. In this case, this system stands for the public key PK, as (l, q, p, d, R, PK).
- Phase 3.
- The OBU randomly selects an integer number e that is equally between 1 and d − 1. After that, it calculates a P point = (XP, YP) = e × R = e × (XR, YR).
- Phase 4.
- Next, the OBU uses the delivered transaction block TD coming from the point P and a coordinate value (X, Y) as inputs and calculates f = Hash (TD) using SHA256.
- Phase 5.
- H = XP mod d.
- Phase 6.
- DS = (S × H + f) × e−1 (mod d).
- Phase 7.
- (TD, H, DS) is the result of the signature; if H or DS is equal to 0, the system replicates Phase 3 to generate an arbitrary integer e until it is accomplished from Phase 1 to Phase 7.
- Phase 8.
- Once the recipient receives the transaction block TD and the result (TD, H, DS) of the signature, the recipient calculates f = Hash (TD), Z = DS−1 mod d, W1 = f × Z mode d, W2 = H × Z mode d. M = (XM, YM) = W1 × R + W2 × PK.
- Phase 9.
- Afterward, the recipient checks if H is equivalent to XM.
- Phase 10.
- If H = XM, the recipient agrees to this signature or otherwise refuses the incoming signature.
- Phase 1:
- First, the RSU is responsible for calculating the internal cluster blockchain named intra_clusterBC.
- Step 1.
- In this study, ECDSA digital signatures are used to digitally sign the transaction block. First, each vehicle C1~C4 performs an ECDSA signature on all of the transmitted transaction blocks TD1~TD4. Subsequently, we adopt SHA256 to calculate the hash value of each vehicle’s transaction block signature. Subsequently, H(SigCi(TDi)) is obtained, and the digital signature result is mapped to the Merkle tree leaf node MNi = [H(SigCi(TDi))||SigCi(TDi)], i = 1~4, as shown in Figure 5. For example, MN1 = [H(SigC1(TD1))||SigC1(TD1)], MN2 = [H(SigC2(TD2))||SigC2(TD2)], MN3 = [H(SigC3(TD3))||SigC3(TD3)], MN4 = [H(SigC4(TD4))||SigC4(TD4)].
- Step 2.
- Afterward, we combine two nearby Malekle nodes together and execute the hash operation to obtain the parent node at level 1 MNL1[(i+1)/2] = [H(H(SigCi(TDi))|H(SigCi+1(TDi+1)))||SigCi(TDi)|SigCi+1(TDi+1)], i = 1, 3, 5, 7,….
- Step 3.
- The above similar steps are repeated to combine two nearby parent nodes and execute the hash operation to obtain the ancestor node at level 2 MNL2[(j+1)/2] = [H(H(H(SigCi(TDi))|H(SigCi+1(TDi+1)))|H(H(SigCi+2(TDi+2))|H(SigCi+3(TDi+3))))]|| H(SigCi(TDi)|SigCi+1(TDi+1)|SigCi+2(TDi+2)|SigCi+3(TDi+3) ], i = 1, 5, 9,…, j = 1, 3, 5, 7,….
- Step 4.
- Repeat step 2 until the system obtains the Markle tree root node, as shown by the black dotted line in Figure 5.
- Phase 2:
- The base station BS connects the blockchains named intra_clusterBC, which are formed by the RSU, and there is a corresponding RSU responsible for the connected vehicles. Since each RSU is in charge of the management of the block within the cluster, this study assigns RSUix, respectively, where i represents the level, and x represents the number of the RSU and also the intra_clusterBCx.
- Phase 3:
- The cloud service platform PKI VMmaster combines each intra_clusterBCi coming from BSi to form inter_clusterBC, as shown in Figure 6.
3.2. Information Security Transmission Method between IoVs and Routers
3.3. The Secure Data Transmission Agreement for Map/Reduce
- (1)
- Initially, when the PKI VMmaster receives the request from the user, it then decides which mapper VMi can participate in the operation in the future and then transmits the task to VMi. With the purpose of confirming the validity of the PKI VMmaster identity of the request, the PKI VMmaster is required to sign the request information sent to the mapper VMi, the identity of the PKI VMmaster as IDVMmaster and the data to be transmitted as TDSigi, so the mapper VMi subsequently sends a request to verify the identity of the PKI VMmaster. Here, we represent the complete data TD = [H(H(H(SigC1(TD1))|H(SigC2(TD2)))|H(H(SigC3(TD3))|H(SigC4(TD4))))||(SigC1(TD1)|SigC2(TD2)|SigC3(TD3)|SigC4(TD4))], and divide TD into several segments, according to mapping/reduction operations.
- (2)
- Next, PKI VMmaster adopts the data segment of TDSigi as the input and computes its HMAC (TDSigi) value, accompanied by the mapper VMi’s identity IDVMi-mapper, the original data TDSigi, the timestamp and the results of the partial group signatures {Mi, TDSigi}. Finally, PKI VMmaster signs the entirety of the data through the secret sharing key of Si on the receiving end and transmits the signature result to the mapper VMi.
- (3)
- Once the reducer, VMx, accepts an appointed job from the VMmaster, for the purpose of ensuring that the sender is accurate, the PKI VMmaster must sign the requested information, the VMmaster identity IDVMmaster and the delivered data Infreq, and the reducer of VMx will then be able to verify the identity of the VMmaster.
- (4)
- Successively, the reducer, VMx, receives the data segments {Mi, TDSigi}~{Mn, TDSigm }, the timestamp, and the sequence number signed by the mappers VMi’s secret-sharing key Si from mappers VMi (i = 1~m).
- (5)
- After receiving the delivered data from the mapper, VM(1~m), the VMx reducer immediately requests the corresponding Pi public key to the VMi mapper from the PKI VMmaster.
- (6)
- Subsequently, the VMx reducer gains the public key corresponding to the Si from VMmaster, which participates in the operation mapper, VM(1~m).
4. The Analysis of Security Additionally, Performance
- (1)
- Merkle tree verification
- Step 1.
- Taking SigC1(TD1), SigC2(TD2), SigC3(TD3), SigC4(TD4) as the input, calculate the latest H* hash value for the MNL21 root node and confirm if the original value [H(H(H(SigC1(TD1))|H(SigC2(TD2)))|H(H(SigC3(TD3))|H(SigC4(TD4))))||(SigC1(TD1)|SigC2(TD2)|SigC3(TD3)|SigC4(TD4))] is equal to H*. When they are not equal, proceed to verify their child nodes, MNL11 and MNL12.
- Step 2.
- Similar hash jobs are performed repeatedly, and if MNL11 is the same and the node MNL12 is different, this study will examine the child nodes, MN3 and MN4, of the node MNL12.
- Step 3.
- Similar hash jobs are repeated, and if MN3 is equal but MN4 is not, this study will examine MN4 and finally realize the accurate collapsed node.
- (2)
- Group signature verification
- (3)
- Efficiency evaluation
- (4)
- The threshold cryptosystem with fault tolerance
- (5)
- Blockchain integrity
- (6)
- Comparison of the related research
5. Conclusions
Funding
Data Availability Statement
Conflicts of Interest
References
- Benkirane, B.; Benaziz, M. Performance evaluation of IEEE 802.11p and IEEE 802.16e for vehicular ad hoc networks using simulation tools. In Proceedings of the IEEE 5th International Congress on Information Science and Technology, Marrakech, Morocco, 21–27 October 2018. [Google Scholar]
- Zhu, P.; Zhu, K.; Zhang, L. Security analysis of LTE-V2X and a platooning case study. In Proceedings of the IEEE Conference on Computer Communications Workshops, Toronto, ON, Canada, 6–9 July 2020. [Google Scholar]
- Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on blockchain for Internet of things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
- Han, D.; Zhu, Y.; Li, D.; Liang, W.; Souri, A.; Li, K.C. A blockchain-based auditable access control system for private data in service-centric IoT environments. IEEE Trans. Ind. Inform. 2022, 18, 3530–3540. [Google Scholar] [CrossRef]
- Lin, H.Y. Secure cloud Internet of vehicles based on blockchain and data transmission scheme of map/reduce. Comput. Sci. Inf. Syst. 2023, 20, 137–156. [Google Scholar] [CrossRef]
- Wang, D.; Wang, H.; Fu, Y. Blockchain-based IoT device identification and management in 5G smart grid. EURASIP J. Wirel. Commun. Netw. 2021, 125. [Google Scholar] [CrossRef]
- Jiang, T.; Fang, H.; Wang, H. Blockchain-based internet of vehicles: Distributed network architecture and performance analysis. IEEE Internet Things J. 2019, 6, 4640–4649. [Google Scholar] [CrossRef]
- Shrestha, R.; Nam, S.Y. Regional blockchain for vehicular networks to prevent 51% attacks. IEEE Access 2019, 7, 95033–95045. [Google Scholar] [CrossRef]
- Ma, X.; Ge, C.; Liu, Z. Blockchain-enabled privacy preserving Internet of vehicles: Decentralized and reputation-based network architecture. Netw. Syst. Secur. 2019, 11928, 336–351. [Google Scholar]
- Dai, H.; Zheng, Z.; Zhang, Y. Blockchain for internet of things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef] [Green Version]
- Lu, Y.; Huang, X.; Zhang, K.; Maharjan, S.; Zhang, Y. Blockchain empowered asynchronous federated learning for secure data sharing in internet of vehicles. IEEE Trans. Veh. Technol. 2020, 69, 4298–4311. [Google Scholar] [CrossRef]
- Liu, K.; Chen, W.; Zheng, Z.; Li, Z.; Liang, W. A novel debt credit mechanism for blockchain-based data-trading in internet of vehicles. IEEE Internet Things J. 2019, 6, 9098–9111. [Google Scholar] [CrossRef]
- Lu, Z.; Wang, Q.; Qu, G.; Zhang, H.; Liu, Z. A blockchain-based privacy-preserving authentication scheme for VANETs. IEEE Trans. Very Large Scale Integr. Syst. 2019, 27, 2792–2801. [Google Scholar] [CrossRef]
- Cui, J.; Ouyang, F.; Ying, Z.; Wei, L.; Zhong, H. Secure and efficient data sharing among vehicles based on consortium blockchain. IEEE Trans. Intell. Transp. Syst. 2022, 23, 8857–8867. [Google Scholar] [CrossRef]
- Bagga, P.; Sutrala, A.K.; Das, A.K.; Vijayakumar, P. Blockchain-based batch authentication protocol for Internet of vehicles. J. Syst. Archit. 2021, 113, 101877. [Google Scholar] [CrossRef]
- Maria, A.; Rajasekaran, A.S.; Fadi, A.T.; Altrjman, C.; Mostarda, L. BAIV: An efficient blockchain-based anonymous authentication and integrity preservation scheme for secure communication in VANETs. Electronics 2022, 11, 488. [Google Scholar] [CrossRef]
- Zheng, J.; Wang, X.; Yang, Q.; Xiao, W.; Sun, Y.; Liang, W. A blockchain-based lightweight authentication and key agreement scheme for internet of vehicles. Connect. Sci. 2022, 34, 1430–1453. [Google Scholar] [CrossRef]
- Liang, W.; Yang, Y.; Yang, C.; Hu, Y.; Xie, S.; Li, K.C.; Cao, J. PDPChain: A consortium blockchain-based privacy protection scheme for personal data. IEEE Trans. Reliab. 2022, 1–13. [Google Scholar] [CrossRef]
- Stephen, S.M.; Jaekel, A. Blockchain based vehicle authentication scheme for vehicular ad-hoc networks. In Proceedings of the IEEE Intelligent Vehicles Symposium Workshops, Najoya, Japan, 11–17 July 2021. [Google Scholar]
- Genc, Y.; Afacan, E. Design and implementation of an efficient elliptic curve digital signature algorithm (ECDSA). In Proceedings of the IEEE International IoT, Electronics and Mechatronics Conference, Toronto, ON, Canada, 21–24 April 2021. [Google Scholar]
- Lin, H.Y.; Hsieh, M.Y. A dynamic key management and secure data transfer based on m-tree structure with multi-level security framework for Internet of vehicles. Connect. Sci. 2022, 34, 1089–1118. [Google Scholar] [CrossRef]
- Vijayakumar, P.; Azees, M.; Kozlov, S.A.; Rodrigues, J.J.P.C. An anonymous batch authentication and key exchange protocols for 6G enabled VANETs. IEEE Trans. Intell. Transp. Syst. 2022, 23, 1630–1638. [Google Scholar] [CrossRef]
- Moghadam, M.F.; Nikooghadam, M.; Jabban, M.A.B.A.; Alishahi, M.; Mortazavi, L.; Mohajerzadeh, A. An efficient authentication and key agreement scheme based on ECDH for wireless sensor network. IEEE Access 2020, 8, 73182–73192. [Google Scholar] [CrossRef]
- Abusukhon, A.; Mohammad, Z.; Al, A. Efficient and secure key exchange protocol based on elliptic curve and security models. In Proceedings of the IEEE Jordan International Joint Conference on Electrical Engineering and Information Technology, Amman, Jordan, 9–11 April 2019. [Google Scholar]
- Lin, H.Y.; Hsieh, M.Y.; Li, K.C. Secured map reduce computing based on virtual machine using threshold secret sharing and group signature mechanisms in cloud computing environments. Telecommun. Syst. 2015, 60, 303–313. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, J. Blockchain-based anonymous authentication for traffic reporting in VANETs. Connect. Sci. 2022, 34, 1038–1065. [Google Scholar] [CrossRef]
- Wu, Z.; Huang, H.; Zhou, Y.; Wu, C. A secure and efficient data deduplication framework for the internet of things via edge computing and blockchain. Connect. Sci. 2022, 34, 1999–2025. [Google Scholar] [CrossRef]
- Song, F.; Zhu, M.; Zhu, Y.; You, I.; Zhang, H. Smart collaborative tracking for ubiquitous power IoT in edge-cloud interplay domain. IEEE Internet Things J. 2020, 7, 6046–6055. [Google Scholar] [CrossRef]
- Liang, W.; Fan, Y.; Li, K.C.; Zhang, D.; Gaudiot, J.L. Secure data storage and recovery in industrial blockchain network environments. IEEE Trans. Ind. Inform. 2020, 16, 6543–6552. [Google Scholar] [CrossRef]
- Wang, Z.; Zhang, L.; Ding, X.; Choo, K.R.; Jin, H. A dynamic-efficient structure for secure and verifiable location-based skyline queries. IEEE Trans. Inf. Forensics Secur. 2022, 18, 920–935. [Google Scholar] [CrossRef]
- Yang, H.; Li, Y. A blockchain-based anonymous authentication scheme for Internet of vehicles. In Proceedings of the 13th International Conference on Ambient Systems, Networks and Technologies, Porto, Portugal, 22–25 March 2022. [Google Scholar]
- Lin, H.Y.; Hsieh, M.Y.; Li, K.C. A secure information transmission scheme for the cluster blockchain of the Internet of vehicles. In Proceedings of the Computing Conference, London, UK, 22–23 June 2023. [Google Scholar]







| Notations | Description |
|---|---|
| Ci | The vehicle C is numbered i. |
| TDx | Transaction block data TDx transmitted by the vehicle Cx. |
| SigCx(TDx) | The vehicles Cx performs an ECDSA digital signature on the transmitted transaction block data TDx. |
| Rx | The router R is numbered x. |
| H*(SigCx(TDx)) | Perform a SHA256 hash operation on the ECDSA digital signature of the delivered transaction block SigCx(TDx), * representing the value obtained after a new hash operation. |
| VMi | The virtual machine VM is numbered i. |
| TS | Timestamp. |
| IDVMx | The identity ID of the virtual machine VMx. |
| EKK | The data are encrypted using the key K. |
| || | Data concatenation operations. |
| MNLix | The vehicle node number x at the ith level of the Merkle tree. |
| BSx | The base station is numbered x. |
| MNx | The leaf node of the Merkle tree is numbered x |
| RSUxy | The road site equipment is located at level x, and the number is y. |
| Blockxy | The block is located at level x, and the number is y. |
| VMmaster | The master VM in map/reduce operation of the cloud. |
| intra_clusterBCx | The intra cluster blockchain is numbered x. |
| SKRx_Ry | The session key between devices Rx and Ry. |
| TDSigi | The signature of TD through VMi. |
| [ ]VMmaster_sig | The signature of [ ] through VMmaster. |
| S | The system key S. |
| P | The corresponding public key P. |
| Si | The shared secret Si. |
| Pi | The corresponding public key Pi. |
| Authors | Methods | Scalability | Communication Cost | Single-Point Failure |
|---|---|---|---|---|
| Our scheme | A Multi-level blockchain | V | Low | No |
| Jiang et al. [7] | Five categories of blockchain | X | High | Yes |
| Ma et al. [9] | A privacy-secure and decentralized VNets | V | Low | Yes |
| Dai et al. [10,11] | A private blockchain | X | High | No |
| Lu et al. [13] | A privacy protection authentication | X | Medium | Yes |
| Cui et al. [14] | A consortium blockchain | X | Medium | No |
| Bagga et al. [15] | A batch authentication protocol | V | Medium | No |
| Maria et al. [16] | An anonymous authentication | X | Medium | Yes |
| Zheng et al. [17] | A lightweight authentication | V | Medium | No |
| Song et al. [28] | An anonymous authentication | V | Medium | No |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lin, H.Y. Secure Data Transfer Based on a Multi-Level Blockchain for Internet of Vehicles. Sensors 2023, 23, 2664. https://doi.org/10.3390/s23052664
Lin HY. Secure Data Transfer Based on a Multi-Level Blockchain for Internet of Vehicles. Sensors. 2023; 23(5):2664. https://doi.org/10.3390/s23052664
Chicago/Turabian StyleLin, Hua Yi. 2023. "Secure Data Transfer Based on a Multi-Level Blockchain for Internet of Vehicles" Sensors 23, no. 5: 2664. https://doi.org/10.3390/s23052664
APA StyleLin, H. Y. (2023). Secure Data Transfer Based on a Multi-Level Blockchain for Internet of Vehicles. Sensors, 23(5), 2664. https://doi.org/10.3390/s23052664






