Efficient Authentication Scheme for 5G-Enabled Vehicular Networks Using Fog Computing
Abstract
:1. Introduction
2. Related Work
3. Preliminaries
3.1. System Model Design
- Trusted Authority (TA): It is assumed that the TA is a highly secure entity, which is reliable and independent. TA is responsible for initializing the system parameters for the 5G-enabled vehicular networks. Furthermore, it is in charge of registering each participating vehicle and fog server during the registration process.
- 5G-Base Stations (5G-BSs): The 5G-BSs are fixed infrastructure deployed on the roadside. It does not work with any computing and storage, only as an intermediate device between vehicles, fog servers, and TA. This is because it adapts to the wide range of D2D communication. Due to 5G-BSs being hardware, the attacker cannot compromise them.
- Fog Servers: This model assumes that the fog server has some verification computation and storage capabilities. The fog server has the private key of TA to validate vehicles during mutual authentication through 5G-BS. Furthermore, the fog server is responsible for issuing a group of public anonymous IDs and the corresponding group of signature keys to each participating vehicle.
- Vehicles: Each vehicle has a wireless device called an onboard unit (OBU) to communicate with other vehicles and fog servers. The OBU provides a tamper-proof device to save a group of public anonymous IDs and the corresponding group of signature keys that are obtained from the fog server. Meanwhile, the OBU offers a 5G protocol in order to exchange messages among 5G-BSs. When two mobile users can establish a connection directly, bypassing the base station (BS) and the core network, they are said to be engaging in device-to-device (D2D) transmission within the cellular network. Even if a node is within direct D2D communication range, all communications in a standard cellular network must first travel via the BS. With BS communication, traditional low data rate mobile services can thrive because users rarely contact directly with one another. However, users of today’s mobile networks make use of high-speed data services even when they are not in a direct line of sight to the network. This is why D2D communication has the potential to boost the spectral efficiency of networks. Spectrum efficiency, throughput, energy efficiency, latency, and fairness are all able to benefit from D2D communication [34,36].
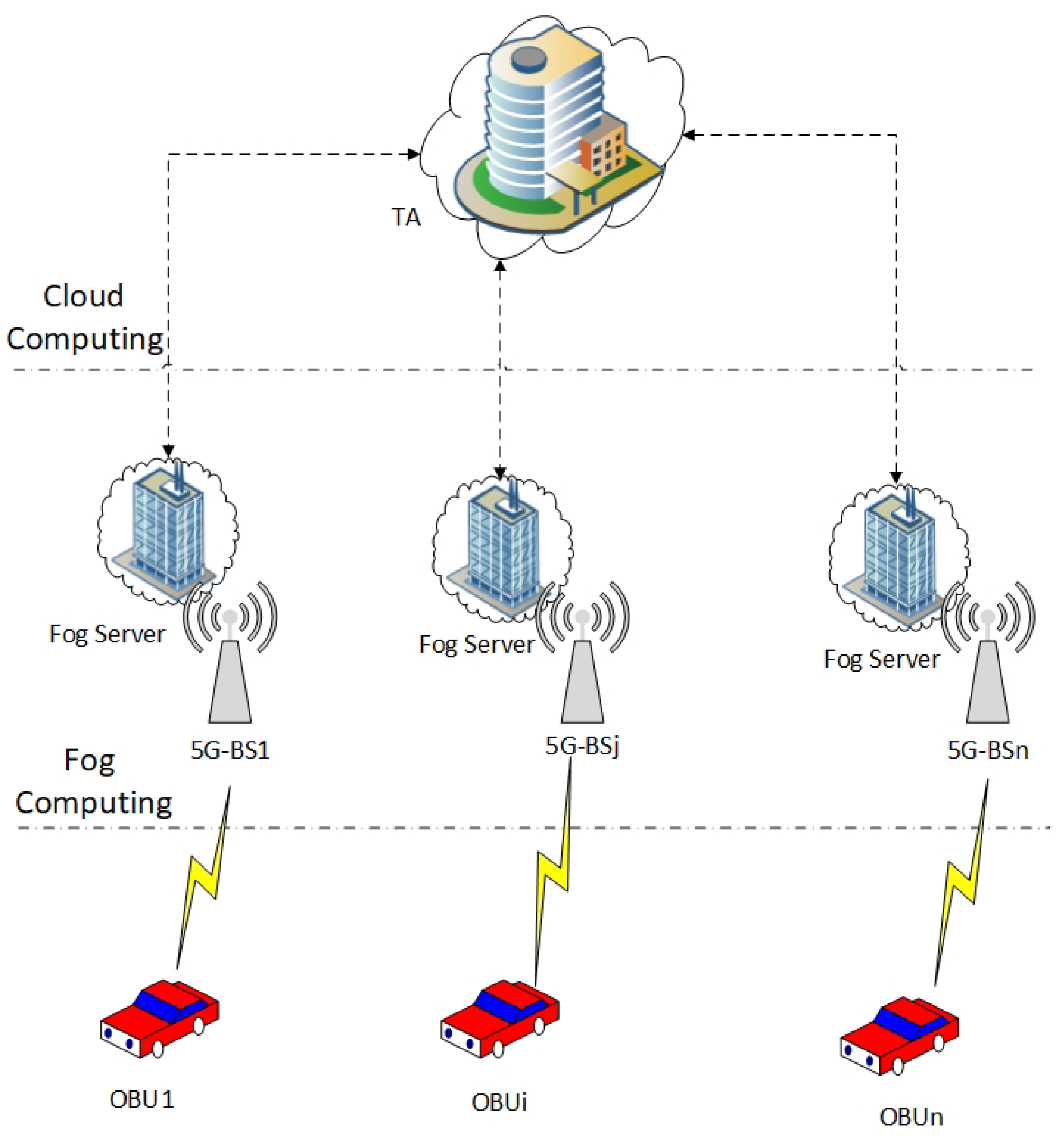
3.2. Fog Computing
3.3. Design Goals
- Authentication and Integrity: Ensures that an attacker is not able to modify or forge messages sent from participating vehicles.
- Anonymity- and Privacy-Preserving: Ensures that an attacker is not able to disclose the identity of the participating vehicle.
- Unlinkability: Ensures that an attacker is not able to link two or more messages sent from the same participating vehicle.
- Traceability: Ensures that TA is able to trace the harmful vehicle.
- Revocability: Ensures that TA is able to revoke the harmful vehicle.
- Resist Security Attacks: Ensures that the proposed FC-CPPA scheme is able to resist security attacks such as forgery, modification, replay, and Man-in-The-Middle attacks.
4. The Proposed FC-CPPA Scheme
4.1. Setup Phase
- Let be a large prime values, G be an additive group with the order q and a generator P, and E be a definition equation of an elliptic curve p, where .
- TA sets the randomly chosen number as the private key and computes the relevant public key .
- TA sets secure message authentication code (MAC) function and three the randomly chosen one-way hash functions as .
- TA publishes the system parameters SysPar =.
4.2. Registration Phase
4.2.1. Fog Server Registration
- Fog server submits the identity to TA through secure channel.
- After checking the validity of , TA computes as the public key of the fog server.
- TA preloads the system parameters SysPar = in each fog server.
- TA saves into the fog registration list (FRL).
- TA saves the private key x on the TPD of the fog server through a secure channel.
- Finally, the fog server publishes a public key through large-range communication of 5G-BSs.
4.2.2. Vehicle Registration
- Vehicles submits the identity to TA through secure channel.
- After checking the validity of , TA computes as inter anonymous-ID.
- TA saves the inter anonymous-ID on the TPD of the participating vehicle through a secure channel.
- TA saves into vehicle registration list (VRL).
- Finally, TA preloads the system parameters SysPar = in each OBU of participating vehicles.
4.3. Mutual Authentication Phase
- : Vehicle sets the randomly chosen number and computes its public anonymous-ID , where and . Next, vehicle sends to fog server , where is the current timestamp and as the signature of .
- : While receiving the from vehicle through a 5G-BS, fog server initially verifies the freshness of timestamp by checking whether Equation (2) holds or not for avoiding replay attacks. If (2) is verified, fog server continues the mutual authentication process. Otherwise, it is rejected.where is the received time of and is the predefined delay time.
- : Next, fog server computes inter anonymous-ID of vehicle as and verifies the signature of by checking whether Equation (3) holds or not. If (3) is correct, the fog server continues the mutual authentication process. Otherwise, it is rejected.Then fog server sends = , where = as the signature of .
- : While receiving the from fog server , TA checks the timestamp and the signature by using Equations (2) and (3), respectively. Then it computes Equation (4).Next, the TA checks the validity of participating vehicle and fog server by matching the existing value on VRL and FRL, respectively. If it is so, TA sends to fog server . Otherwise, TA sends to fog server .
- : While receiving the from TA, fog server picks n values , where . Then fog server computes a group of public anonymity-IDs as follows, where .Then fog server computes the corresponding a group of signature keys based on the a group of public anonymity-IDs as follows, where
- : Next, fog server sets the randomly chosen number and computes and . Then fog server computes as a symmetric secret key between the vehicle and fog server .
- : Next, fog server encrypts and sends = , where = .
- : While receiving the from fog server , vehicle verifies the freshness of timestamp by using Equation (2). Then vehicle computes , and decrypts to obtain .
- : Next, vehicle verifies the by checking whether Equation (7) holds or not.
4.4. Message Signing Phase
- Vehicle picks unused public anonymous-ID and the corresponding signature key from group of and , receptively.
- Vehicle signs messages as follows.
- Finally, vehicle broadcasts to others within the communication range of 5G-BS.
4.5. Single-Signature Verification Phase
4.6. Batch-Signature Verification Phase
5. Security Analysis
5.1. Formal Analysis
5.1.1. Authentication and Integrity
5.1.2. Identity Privacy-Preserving
5.2. Informal Analysis
- Authentication and Integrity: The format of the message shared by vehicle is to other vehicles, where is the signature message. Before message is accepted, the checker computes Equations (9) and (10) to detect any modification/impersonation of the message. Hence, the authentication and integrity requirements are achieved in our work.
- Anonymity- and Privacy-Preserving: During the vehicle registration phase, once the vehicle submits its identity to TA through a secure channel, the TA computes and preloads inter anonymous-ID to the vehicle. By using inter anonymous-ID , the fog server computes and preloads a group of public anonymous-ID to the vehicle during the mutual authentication process. The vehicle picks unused public anonymous-ID from group of that are received from the fog server, where at a time. Since the random numbers and x are not known by the attacker, it is possible to reveal the true identity of the vehicle. Hence, the anonymity privacy-preserving requirement is achieved in our work.
- Unlikability: When the vehicle wants to broadcast a message, it picks unused public anonymous-ID and the corresponding signature key from the group of and that is received from fog server, receptively, where . Since the random nonce is included for each public anonymous-ID , the attacker does not have the ability to link several messages sent from the same source. Hence, the unlikability requirement is achieved in our work.
- Traceability: The TA and the fog server work together to locate and revoke the harmful vehicle after receiving a report about a harmful vehicle. The TA discovers the vehicle’s inter anonymous-ID as follows:Hence, the traceability requirement is achieved in our work.
- Revocability: Once the traceability requirement is complete, the TA then updates the CRL by adding the inter anonymous-ID , and sends the new CRL to fog servers. As a result, the local CRLs are updated and broadcast by the fog servers involving the victim’s vehicle. Additionally, the authentication procedure fails in line with Equation (8) when the malicious actor joins the new fog server region, or the valid timestamp has expired. Hence, the revocability requirement is achieved in our work.
5.3. Attack Scenarios
- Resistance to Replay Attacks: The timestamp is included the message format in our proposal. Before the message is accepted, the checker verifies the freshness of timestamp by checking whether Equation (12) holds or not to avoid replay attacks. If (12) is verified, the checker continues the mutual authentication process. Otherwise, it is rejected.where is the received time of and is the predefined delay time. Hence, replay attacks are resisted in our work.
- Resistance to Man-In-The-Middle Attacks: According to the above analysis, no attacker is able to change/modify/replay/impersonate the communication between the sender and receiver. Hence, man-in-the-middle attacks are resisted in our work.
6. Performance Evaluation and Comparison
6.1. Experimental Environment
6.2. Computation Cost
6.3. Communication Cost
7. Conclusions
- The proposed novel architecture concept for 5G-enabled vehicle networks based on fog computing. The goal of this new layout is to boost the safety, confidentiality, and efficiency of existing vehicular networks.
- For 5G-enabled vehicle networks, this study offers a CPPA system based on fog computing; we term it the FC-CPPA scheme.
- We suggest using a fog server in conjunction with the FC-CPPA scheme to produce and preload a set of public anonymity identities and the related signature keys to each genuine vehicle.
- To meet the needs of privacy and security, we present a proof of the robustness of the proposed FC-CPPA method, noting the DDH problem’s hardness in the random oracle model.
- We present the performance of the proposed FC-CPPA scheme in terms of communication and computation costs, which are more efficient in message signing and single and batch signature verification as compared to related work.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Zhang, J.; Jiang, Y.; Cui, J.; He, D.; Bolodurina, I.; Zhong, H. DBCPA: Dual Blockchain-Assisted Conditional Privacy-Preserving Authentication Framework and Protocol for Vehicular Ad Hoc Networks. IEEE Trans. Mob. Comput. 2022, 1–15. [Google Scholar] [CrossRef]
- Hamdan, M.A.; Maklouf, A.M.; Mnif, H. Review of Authentication with Privacy-preserving Schemes for 5G-enabled Vehicular Networks. In Proceedings of the 15th IEEE International Conference on Security of Information and Networks (SIN), Sousse, Tunisia, 11–13 November 2022; pp. 1–6. [Google Scholar]
- Al-Mekhlafi, Z.G.; Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Qtaish, A. Lattice-Based Lightweight Quantum Resistant Scheme in 5G-Enabled Vehicular Networks. Mathematics 2023, 11, 399. [Google Scholar] [CrossRef]
- Zhong, H.; Yang, F.; Wei, L.; Zhang, J.; Gu, C.; Cui, J. Dataset for Evaluation of DDoS Attacks Detection in Vehicular Ad-Hoc Networks. In Proceedings of the International Conference on Wireless Algorithms, Systems, and Applications; Springer: Berlin/Heidelberg, Germany, 2022; pp. 249–260. [Google Scholar]
- Al-Shareeda, M.A.; Manickam, S. COVID-19 Vehicle Based on an Efficient Mutual Authentication Scheme for 5G-Enabled Vehicular Fog Computing. Int. J. Environ. Res. Public Health 2022, 19, 15618. [Google Scholar] [CrossRef]
- Wei, L.; Cui, J.; Zhong, H.; Xu, Y.; Liu, L. Proven secure tree-based authenticated key agreement for securing V2V and V2I communications in VANETs. IEEE Trans. Mob. Comput. 2021, 21, 3280–3297. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Manickam, S.; Laghari, S.A.; Jaisan, A. Replay-Attack Detection and Prevention Mechanism in Industry 4.0 Landscape for Secure SECS/GEM Communications. Sustainability 2022, 14, 15900. [Google Scholar] [CrossRef]
- Cui, J.; Ouyang, F.; Ying, Z.; Wei, L.; Zhong, H. Secure and efficient data sharing among vehicles based on consortium blockchain. IEEE Trans. Intell. Transp. Syst. 2021, 23, 8857–8867. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Manickam, S. Man-in-the-middle attacks in mobile ad hoc networks (MANETs): Analysis and evaluation. Symmetry 2022, 14, 1543. [Google Scholar] [CrossRef]
- Zhou, H.; Wu, T.; Chen, X.; He, S.; Guo, D.; Wu, J. Reverse auction-based computation offloading and resource allocation in mobile cloud-edge computing. IEEE Trans. Mob. Comput. 2022, 1–15. [Google Scholar] [CrossRef]
- Cui, J.; Wang, Y.; Zhang, J.; Xu, Y.; Zhong, H. Full Session Key Agreement Scheme Based on Chaotic Map in Vehicular Ad hoc Networks. IEEE Trans. Veh. Technol. 2020, 69, 8914–8924. [Google Scholar] [CrossRef]
- Mohammed, B.A.; Al-Shareeda, M.A.; Manickam, S.; Al-Mekhlafi, Z.G.; Alreshidi, A.; Alazmi, M.; Alshudukhi, J.S.; Alsaffar, M. FC-PA: Fog Computing-based Pseudonym Authentication Scheme in 5G-enabled Vehicular Networks. IEEE Access 2023, 11, 18571–18581. [Google Scholar] [CrossRef]
- Al-Mekhlafi, Z.G.; Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Alreshidi, A.; Alazmi, M.; Alshudukhi, J.S.; Alsaffar, M.; Alsewari, A. Chebyshev Polynomial-Based Fog Computing Scheme Supporting Pseudonym Revocation for 5G-Enabled Vehicular Networks. Electronics 2023, 12, 872. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. A Secure Pseudonym-Based Conditional Privacy-Preservation Authentication Scheme in Vehicular Ad Hoc Networks. Sensors 2022, 22, 1696. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Y.; Chang, G. Efficient privacy-preserving dual authentication and key agreement scheme for secure V2V communications in an IoV paradigm. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2740–2749. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. Password-Guessing Attack-Aware Authentication Scheme Based on Chinese Remainder Theorem for 5G-Enabled Vehicular Networks. Appl. Sci. 2022, 12, 1383. [Google Scholar] [CrossRef]
- Dua, A.; Kumar, N.; Das, A.K.; Susilo, W. Secure message communication protocol among vehicles in smart city. IEEE Trans. Veh. Technol. 2017, 67, 4359–4373. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Al-Mekhlafi, Z.G.; Qtaish, A.; Alzahrani, A.J.; Alshammari, G.; Sallam, A.A.; Almekhlafi, K. Chebyshev Polynomial-Based Scheme for Resisting Side-Channel Attacks in 5G-Enabled Vehicular Networks. Appl. Sci. 2022, 12, 5939. [Google Scholar] [CrossRef]
- Malhi, A.; Batra, S. Privacy-preserving authentication framework using bloom filter for secure vehicular communications. Int. J. Inf. Secur. 2016, 15, 433–453. [Google Scholar] [CrossRef]
- Jiang, S.; Zhu, X.; Wang, L. An efficient anonymous batch authentication scheme based on HMAC for VANETs. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2193–2204. [Google Scholar] [CrossRef]
- Azees, M.; Vijayakumar, P.; Deboarh, L.J. EAAP: Efficient anonymous authentication with conditional privacy-preserving scheme for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2467–2476. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Hasbullah, I.H. SE-CPPA: A Secure and Efficient Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-Hoc Networks. Sensors 2021, 21, 8206. [Google Scholar] [CrossRef]
- Wu, L.; Fan, J.; Xie, Y.; Wang, J.; Liu, Q. Efficient location-based conditional privacy-preserving authentication scheme for vehicle ad hoc networks. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717700899. [Google Scholar] [CrossRef]
- Asaar, M.R.; Salmasizadeh, M.; Susilo, W.; Majidi, A. A secure and efficient authentication technique for vehicular ad-hoc networks. IEEE Trans. Veh. Technol. 2018, 67, 5409–5423. [Google Scholar] [CrossRef]
- Li, J.; Choo, K.K.R.; Zhang, W.; Kumari, S.; Rodrigues, J.J.; Khan, M.K.; Hogrefe, D. EPA-CPPA: An efficient, provably-secure and anonymous conditional privacy-preserving authentication scheme for vehicular ad hoc networks. Veh. Commun. 2018, 13, 104–113. [Google Scholar] [CrossRef]
- Alshudukhi, J.S.; Al-Mekhlafi, Z.G.; Mohammed, B.A. A Lightweight Authentication With Privacy-Preserving Scheme for Vehicular Ad Hoc Networks Based on Elliptic Curve Cryptography. IEEE Access 2021, 9, 15633–15642. [Google Scholar] [CrossRef]
- Liu, L.; Antonopoulos, N.; Zheng, M.; Zhan, Y.; Ding, Z. A socioecological model for advanced service discovery in machine-to-machine communication networks. ACM Trans. Embed. Comput. Syst. (TECS) 2016, 15, 1–26. [Google Scholar] [CrossRef]
- Mumtaz, S.; Huq, K.M.S.; Ashraf, M.I.; Rodriguez, J.; Monteiro, V.; Politis, C. Cognitive vehicular communication for 5G. IEEE Commun. Mag. 2015, 53, 109–117. [Google Scholar] [CrossRef]
- Cheng, J.; Cheng, J.; Zhou, M.; Liu, F.; Gao, S.; Liu, C. Routing in internet of vehicles: A review. IEEE Trans. Intell. Transp. Syst. 2015, 16, 2339–2352. [Google Scholar] [CrossRef]
- Li, J.; Lu, H.; Guizani, M. ACPN: A novel authentication framework with conditional privacy-preservation and non-repudiation for VANETs. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 938–948. [Google Scholar] [CrossRef]
- Schneider, P.; Horn, G. Towards 5G security. In Proceedings of the 2015 IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20–22 August 2015; Volume 1, pp. 1165–1170. [Google Scholar]
- Kang, J.; Lin, D.; Jiang, W.; Bertino, E. Highly efficient randomized authentication in VANETs. Pervasive Mob. Comput. 2018, 44, 31–44. [Google Scholar] [CrossRef]
- Lu, H.; Li, J. Privacy-preserving authentication schemes for vehicular ad hoc networks: A survey. Wirel. Commun. Mob. Comput. 2016, 16, 643–655. [Google Scholar] [CrossRef]
- Zhang, J.; Zhong, H.; Cui, J.; Tian, M.; Xu, Y.; Liu, L. Edge computing-based privacy-preserving authentication framework and protocol for 5G-enabled vehicular networks. IEEE Trans. Veh. Technol. 2020, 69, 7940–7954. [Google Scholar] [CrossRef]
- Bayat, M.; Pournaghi, M.; Rahimi, M.; Barmshoory, M. NERA: A New and Efficient RSU based Authentication Scheme for VANETs. Wirel. Netw. 2019, 26, 3083–3098. [Google Scholar] [CrossRef]
- Tehrani, M.N.; Uysal, M.; Yanikomeroglu, H. Device-to-device communication in 5G cellular networks: Challenges, solutions, and future directions. IEEE Commun. Mag. 2014, 52, 86–92. [Google Scholar] [CrossRef]
- Horng, S.J.; Tzeng, S.F.; Pan, Y.; Fan, P.; Wang, X.; Li, T.; Khan, M.K. b-SPECS+: Batch verification for secure pseudonymous authentication in VANET. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1860–1875. [Google Scholar] [CrossRef]
- Jianhong, Z.; Min, X.; Liying, L. On the security of a secure batch verification with group testing for VANET. Int. J. Netw. Secur. 2014, 16, 351–358. [Google Scholar]
- Scott, M. Miracl-a Multiprecision Integer and Rational Arithmetic c/c++ Library. 2003. Available online: http://www.shamus.ie (accessed on 1 January 2023).


| Malhi and Batra [19] | Jiang et al. [20] | Azees et al. [21] | Wu et al. [23] | FC-CPPA Scheme | |
|---|---|---|---|---|---|
| Mutual Authentication | Yes | NO | NO | NO | Yes |
| Integrity | Yes | Yes | Yes | Yes | Yes |
| Anonymity Privacy-Preserving | Yes | Yes | Yes | Yes | Yes |
| Unlikability | Yes | Yes | Yes | Yes | Yes |
| Traceability | Yes | Yes | Yes | Yes | Yes |
| Revocability | Yes | Yes | Yes | Yes | Yes |
| Replaying Resistance | Yes | Yes | NO | Yes | Yes |
| NO RSU aided | NO | NO | NO | NO | Yes |
| Hardware | Features |
|---|---|
| Windows | Windows 11 professional |
| CPU | AMD Ryzen 7 5800H |
| RAM | 8.00 GB |
| Architecture | 64-bit CPU |
| Cryptography Operation | Notation | Running Time (ms) |
|---|---|---|
| The amount of time required to form a bilinear pair in | 5.811 | |
| The amount of time required to form a scalar multiplication operation in | 1.5654 | |
| The amount of time required to form a point addition operation in | 0.0106 | |
| The amount of time required to form a map-to-point hash function in | 4.1724 | |
| The amount of time required to form a scalar multiplication operation in G | 0.6718 | |
| The amount of time required to form a point addition operation in G | 0.0031 |
| Scheme | MsgSign Phase (ms) | SigVerify Phase (ms) | BSigVerify Phase (ms) |
|---|---|---|---|
| Azees et al. [21] | |||
| Al-Shareeda et al. [22] | |||
| Asaar et al. [24] | |||
| Li et al. [25] | |||
| Alshudukhi et al. [26] | |||
| FC-CPPA |
| Scheme | Message-Signature Tuple | Size (Bytes) | n Size (Bytes) |
|---|---|---|---|
| Azees et al. [21] | 128 × 6 + 20 × 3 + 20 = 848 | 848n | |
| Al-Shareeda et al. [22] | 128 + 2 × 20 + 2 × 4 = 216 | 216n | |
| Asaar et al. [24] | 40 × 3 + 20 × 3 + 4 = 184 | 184n | |
| Li et al. [25] | 40 × 3 + 20 + 4 = 144 | 144n | |
| Alshudukhi et al. [26] | 40 + 2 × 20 + 4 = 84 | 84n | |
| Our Proposed | 40 + 2 × 20 + 4 = 84 | 84n |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Mekhlafi, Z.G.; Al-Shareeda, M.A.; Manickam, S.; Mohammed, B.A.; Alreshidi, A.; Alazmi, M.; Alshudukhi, J.S.; Alsaffar, M.; Rassem, T.H. Efficient Authentication Scheme for 5G-Enabled Vehicular Networks Using Fog Computing. Sensors 2023, 23, 3543. https://doi.org/10.3390/s23073543
Al-Mekhlafi ZG, Al-Shareeda MA, Manickam S, Mohammed BA, Alreshidi A, Alazmi M, Alshudukhi JS, Alsaffar M, Rassem TH. Efficient Authentication Scheme for 5G-Enabled Vehicular Networks Using Fog Computing. Sensors. 2023; 23(7):3543. https://doi.org/10.3390/s23073543
Chicago/Turabian StyleAl-Mekhlafi, Zeyad Ghaleb, Mahmood A. Al-Shareeda, Selvakumar Manickam, Badiea Abdulkarem Mohammed, Abdulrahman Alreshidi, Meshari Alazmi, Jalawi Sulaiman Alshudukhi, Mohammad Alsaffar, and Taha H. Rassem. 2023. "Efficient Authentication Scheme for 5G-Enabled Vehicular Networks Using Fog Computing" Sensors 23, no. 7: 3543. https://doi.org/10.3390/s23073543
APA StyleAl-Mekhlafi, Z. G., Al-Shareeda, M. A., Manickam, S., Mohammed, B. A., Alreshidi, A., Alazmi, M., Alshudukhi, J. S., Alsaffar, M., & Rassem, T. H. (2023). Efficient Authentication Scheme for 5G-Enabled Vehicular Networks Using Fog Computing. Sensors, 23(7), 3543. https://doi.org/10.3390/s23073543












