Resource-Efficient Parallelized Random Access for Reliable Connection Establishment in Cellular IoT Networks
Abstract
:1. Introduction
- We provided meaningful insights regarding how the RA procedure should be evolved considering a scenario where multiple RAs in parallel are available.
- Especially, we newly proposed two redundancy elimination mechanisms to overcome shortcoming (i.e., waste of radio resources) in such a scenario, and, thus, we can achieve the improved radio resource efficiency as well as the improved connection establishment success probability.
- Through extensive simulations, we verified the validity of our proposed technique with various numerical results, and also verified the feasibility of our proposed technique for practical use with the advanced physical-layer techniques not that complicate to be implemented.
2. Brief Review on Random Access Parallelization Technique
- (Step 1) Multi-preamble transmissionsEach IoT device randomly selects multiple k different preambles (i.e., ) among a set of available RA preambles, and transmits them simultaneously on the physical RA channel (PRACH) to the BS. (Note that the preambles are a set of commonly shared signals, which are used for contending purpose in this step [13]. Each BS generally configures 64 preamble signatures (i.e., signals) using Zadoff-Chu sequence representing excellent auto/cross-correlation properties [28]).
- (Step 2) Random access responsesThe BS detects which preambles are active. Note that the BS can only detect the existence of signals during the detection phase (e.g., energy detection), and does not know which IoT devices sent those of signals. In response to the detected preambles, the BS broadcasts random access response (RAR) messages, each of which consists of the detected preamble index and an uplink grant (UG), where the actual message transmission occurs in the subsequent step. Each IoT device attempts to identify k RAR messages since it triggers the RA procedure with k different preambles in the previous step. Accordingly, each IoT device compares the preamble index contained each of RAR messages with k preamble indices used in Step 1 to identify the destination of each of RAR messages.
- (Step 3) Multiple scheduled message transmissionsIn this step, each IoT device generates multiple k copies of the scheduled message (i.e., k connection request messages), and transmits each message on each of the assigned uplink resources. Since the messages containing the identical information are sent k times redundantly, this can significantly mitigate the occurrence of the event that the entire messages experience the unexpected resource collisions at the same time.
- (Step 4) Contention resolutionThe BS echoes the identifiers of IoT devices, whose transmitted scheduled messages are successfully decoded without any collisions. If each IoT device receives the correct acknowledgement (ACK) message, then it regards the RA attempt as a success. This implies that the connection with the BS is successfully established. Otherwise, the device considers that the RA attempt fails and connection is not established yet. In this case, each IoT device reattempts the RA procedure at the next-available RA opportunity (i.e., PRACH) after performing a back-off.
3. System Model
4. Resource-Efficient Parallelized Random Access for Reliable Connection Establishment
4.1. Observations & New Opportunities
- All the signals (e.g., preambles in Step 1) sent by a certain IoT device experience the same wireless channel, and thus, the power delay profiles (PDPs) of those signals captured at the BS will show almost the same characteristic if they all are exclusively used by the corresponding device.
- When each IoT device redundantly transmits the identical messages (i.e., connection request messages) in parallel, the BS can cancel out redundant messages if there exists at least one successfully decoded message (The fundamental principle may be the same with the successive interference cancellation, but the duplicated message should be found somewhere in other radio resources [30]).
4.2. Preamble Redundancy Elimination
4.3. Message Redundancy Elimination
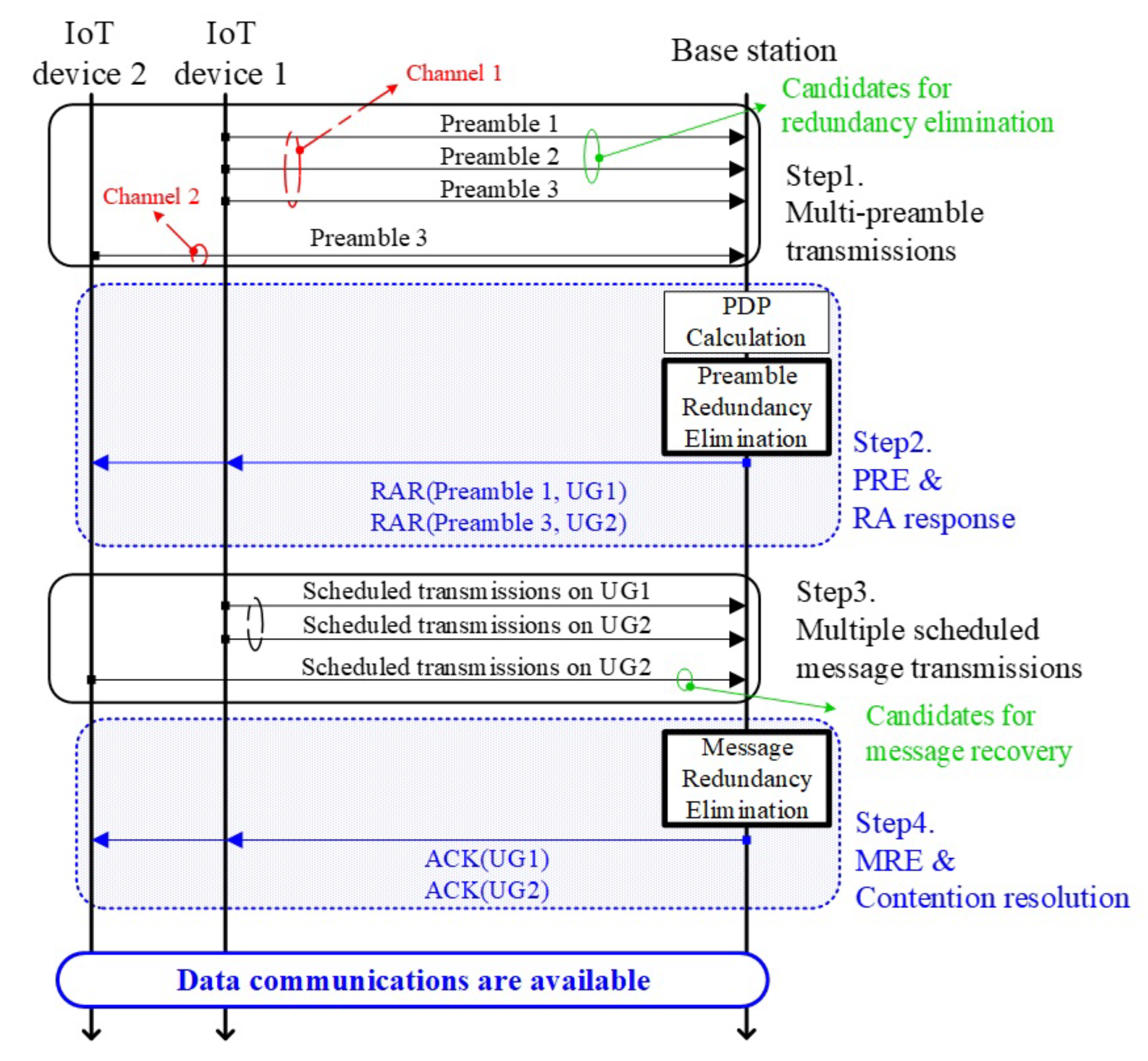
4.4. Overall Procedure
- (Step 1) Multi-preamble transmissionsEach IoT device triggers its RA procedure by simultaneously transmitting randomly selected multi-preambles to the BS via the PRACH. To be specific, each IoT device randomly selects k different preambles from the available preamble set, i.e., , and transmits them at the same time to the BS. Let denote a set of randomly selected preambles of the IoT device n, where and .
- (Step 2) Preamble redundancy elimination & random access responsesNote that the role of this step is to generate and send response messages in response to the preamble detection results, but our proposed technique further equips with the redundancy elimination functionality during the preamble detection phase. The BS determines which preambles are active during the preamble detection phase and performs the post-processing procedure, i.e., preamble redundancy elimination. Thereafter, the BS responses to the some of detected preambles by sending RA responses (RARs), each of which includes a detected preamble index and an uplink grant.First of all, the BS should obtain power delay profile (PDP) from the received signal via PRACH to detect preambles. To be specific, the PDP can be calculated as , where , y, and represent the cross-correlation between y and , the received signal via PRACH, and reference Zadoff-Chu sequence, respectively. The BS separates the PDP into M distinct preamble detection zones (PDZs) as , where . When a certain level of signal strength is observed in the , the m-th preamble (or, equivalently, preamble m) is regarded as active.Thereafter, the BS performs PRE mechanism. In detail, the BS compares the similarity between the preamble signals detected in each PDZ. If there exist multiple preambles showing similar PDP, the BS regards them as the preambles sent by an identical device, and avoids generating multiple RARs for them. In this case, instead, the BS generates a single representative RAR rather than generating multiple responses. This procedure enables to avoid redundant steps, and, thus the additional resource consumption in the subsequent steps can be efficiently avoided.
- (Step 3) Multiple scheduled message transmissionsEach IoT device makes replicas of its scheduled message (e.g., connection request message) where due to the PRE mechanism. Thereafter, it transmits each message on each of the assigned uplink resources, indicated by the UG value contained in each of RARs received in Step 2. This step enables the BS to achieve receive diversity by sending multiple replicas of the original scheduled message. Note that this degrades the resource efficiency in proportion to the level of duplication.
- (Step 4) Message redundancy elimination & contention resolutionThe BS attempts to decode messages received in Step 3 based on Algorithm 1. Particularly, the BS iteratively attempts the message redundancy elimination (MRE) with the successfully decoded messages until no messages are recovered or iteration round reaches R, where R represents the maximum number of iterations that the elimination procedure is performed. Thereafter, the BS transmits the ACK messages to the IoT devices whose packet is successfully decoded. If each IoT device receives one or more ACK messages, then its RA attempt is regarded as a success.
| Algorithm 1: Iterative message decoding algorithm |
| Notations |
| : Received signal via UGi |
| : Message decoding attempt with |
| : Set of the entire allocated UGs |
| : Set of UGs where the messages are successfully decoded |
| : Set of UGs where the replicas of are sent |
| Output: |
| 1: for do |
| 2: |
| 3: for do |
| 4: for do |
| 5: if then |
| 6: Try // MRE |
| 7: if then |
| 8 : end if |
| 9 : end for |
| 10: end for |
| 11: |
| 12: end for |
| 13: Broadcast the decoding results, |
5. Performance Evaluation
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| 5G | Fifth Generation |
| 6G | Sixth Generation |
| XR | Extended Reality |
| AI | Artificial Intelligence |
| IoT | Internet of Things |
| AMQP | Advanced Message Queuing Protocol |
| MQTT | Message Queuing Telemetry Transport |
| NB-IoT | Narrow Band Internet-of-Things |
| LTE | Long Term Evolution |
| NR | New Radio |
| BS | Base Station |
| RA | Random Access |
| RePRA | Resource-efficient Parallelized Random Access |
| PRACH | Physical Random Access Channel |
| RAP | Random Access Parallelization |
| PRE | Preamble Redundancy Elimination |
| MRE | Message Redundancy Elimination |
| RAR | Random Access Response |
| RAPID | Random Access Preamble Index |
| UG | Uplink Grant |
| PDP | Power Delay Profile |
| PDZ | Preamble Detection Zone |
References
- Shafi, M.; Molisch, A.F.; Smith, P.J.; Haustein, T.; Zhu, P.; De Silva, P.; Tufvesson, F.; Benjebbour, A.; Wunder, G. 5G: A tutorial overview of standards, trials, challenges, deployment, and practice. IEEE J. Sel. Areas Commun. 2017, 35, 1201–1221. [Google Scholar] [CrossRef]
- Vaezi, M.; Azari, A.; Khosravirad, S.R.; Shirvanimoghaddam, M.; Azari, M.M.; Chasaki, D.; Popovski, P. Cellular, Wide-Area, and Non-Terrestrial IoT: A Survey on 5G Advances and the Road Toward 6G. IEEE Commun. Surv. Tutor. 2022, 24, 1117–1174. [Google Scholar] [CrossRef]
- Letaief, K.B.; Chen, W.; Shi, Y.; Zhang, J.; Zhang, Y.J.A. The Roadmap to 6G: AI Empowered Wireless Networks. IEEE Commun. Mag. 2019, 57, 84–90. [Google Scholar] [CrossRef] [Green Version]
- Dong, L.; Liu, Z.; Jiang, F.; Wang, K. Joint Optimization of Deployment and Trajectory in UAV and IRS-Assisted IoT Data Collection System. IEEE Internet Things J. 2022, 9, 21583–21593. [Google Scholar] [CrossRef]
- Cisco. Cisco Edge-to-Enterprise IoT Analytics for Electric Utilities Solution Overview. Available online: https://www.cisco.com/c/en/us/solutions/data-center-virtualization/big-data/index.html (accessed on 1 January 2021).
- Srivastava, N.; Pandey, P. Internet of things (IoT): Applications, trends, issues and challenges. Mater. Today Proc. 2022, 69, 587–591. [Google Scholar] [CrossRef]
- Uroz, D.; Rodríguez, R.J. Characterization and Evaluation of IoT Protocols for Data Exfiltration. IEEE Internet Things J. 2022, 9, 19062–19072. [Google Scholar] [CrossRef]
- Mishra, B.; Kertesz, A. The Use of MQTT in M2M and IoT Systems: A Survey. IEEE Access 2020, 8, 201071–201086. [Google Scholar] [CrossRef]
- LoRa Alliance—Wide Area Networks for The Internet of Things. Available online: https://www.lora-alliance.org (accessed on 1 January 2021).
- SigFox—Global Cellular Connectivity for The Internet of Things. Available online: https://www.sigfox.com (accessed on 1 January 2021).
- Kim, T.; Kim, D.M.; Pratas, N.; Popovski, P.; Sung, D.K. An Enhanced Access Reservation Protocol with a Partial Preamble Transmission Mechanism in NB-IoT Systems. IEEE Commun. Lett. 2017, 21, 2270–2273. [Google Scholar] [CrossRef] [Green Version]
- Sesia, S.; Toufik, I.; Baker, M. LTE-the UMTS Long Term Evolution: From Theory to Practice, 2nd ed.; WILEY: Hoboken, NJ, USA, 2011. [Google Scholar]
- Dahlman, E.; Parkvall, S.; Skold, J. 5G NR: The Next Generation Wireless Access Technology, 1st ed.; Academic Press: Cambridge, MA, USA, 2018. [Google Scholar]
- 3GPP TS 36.321 V12.7.0; Evolved Universal Terrestrial Radio Access Network (E-UTRAN). Medium Access Control (MAC) Protocol Specification; 3GPP: Sophia Antipolis, France, 2015.
- 3GPP TS 38.321 V15.3.0; 5G NR. Medium Access Control (MAC) Protocol Specification. 3GPP: Sophia Antipolis, France, 2018.
- Laya, A.; Alonso, L.; Alonso-Zarate, J. Is the Random Access Channel of LTE and LTE-A Suitable for M2M Communications? A Survey of Alternatives. IEEE Commun. Surv. Tutorials 2014, 16, 4–16. [Google Scholar] [CrossRef] [Green Version]
- Kim, T.; Jung, B.C.; Sung, D.K. An Enhanced Random Access with Distributed Pilot Orthogonalization for Cellular IoT Networks. IEEE Trans. Veh. Technol. 2020, 69, 1152–1156. [Google Scholar] [CrossRef]
- Jang, H.S.; Jin, H.; Jung, B.C.; Quek, T.Q.S. Resource-Optimized Recursive Access Class Barring for Bursty Traffic in Cellular IoT Networks. IEEE Internet Things J. 2021, 8, 11640–11654. [Google Scholar] [CrossRef]
- Bui, A.T.H.; Pham, A.T. Deep Reinforcement Learning-Based Access Class Barring for Energy-Efficient mMTC Random Access in LTE Networks. IEEE Access 2020, 8, 227657–227666. [Google Scholar] [CrossRef]
- Jang, H.S.; Kim, S.M.; Ko, K.S.; Cha, J.; Sung, D.K. Spatial Group Based Random Access for M2M Communications. IEEE Commun. Lett. 2014, 18, 961–964. [Google Scholar] [CrossRef]
- Kim, T.; Jang, H.S.; Sung, D.K. An Enhanced Random Access Scheme with Spatial Group Based Reusable Preamble Allocation in Cellular M2M Networks. IEEE Commun. Lett. 2015, 19, 1714–1717. [Google Scholar] [CrossRef]
- Zhen, L.; Zhang, Y.; Yu, K.; Kumar, N.; Barnawi, A.; Xie, Y. Early Collision Detection for Massive Random Access in Satellite-Based Internet of Things. IEEE Trans. Veh. Technol. 2021, 70, 5184–5189. [Google Scholar] [CrossRef]
- Zhang, C.; Sun, X.; Xia, W.; Zhang, J.; Zhu, H.; Wang, X. Deep Learning Based Double-Contention Random Access for Massive Machine-Type Communication. IEEE Trans. Wirel. Commun. 2023, 22, 1794–1807. [Google Scholar] [CrossRef]
- Althumali, H.D.; Othman, M.; Noordin, N.K.; Hanapi, Z.M. Dynamic Backoff Collision Resolution for Massive M2M Random Access in Cellular IoT Networks. IEEE Access 2020, 8, 201345–201359. [Google Scholar] [CrossRef]
- Seo, J.B.; Jung, B.C.; Jin, H. Online Backoff Control for NOMA-Enabled Random Access Procedure for Cellular Networks. IEEE Wirel. Commun. Lett. 2021, 10, 1158–1162. [Google Scholar] [CrossRef]
- Kim, T.; Bang, I. Random Access Parallelization Based on Preamble Diversity for Cellular IoT Networks. IEEE Commun. Lett. 2020, 24, 188–192. [Google Scholar] [CrossRef]
- Kim, T.; Jang, H.S.; Bang, I.; Ko, K.S. Access Priority Provisioning Based on Random Access Parallelization for Prioritized Cellular IoT. IEEE Access 2021, 9, 111814–111822. [Google Scholar] [CrossRef]
- Chu, D. Polyphase codes with good periodic correlation properties (Corresp.). IEEE Trans. Inf. Theory 1972, 18, 531–532. [Google Scholar] [CrossRef]
- 3GPP TS 38.213 V16.2.0; 5G; NR; Physical Layer Procedures for Control. 3GPP: Sophia Antipolis, France, 2020.
- Kim, T.; Jung, B.C. An Enhanced Random Access with Inter-Frame Successive Interference Cancellation for Stationary Cellular IoT Networks. IEEE Wirel. Commun. Lett. 2020, 9, 606–610. [Google Scholar] [CrossRef]
- The MathWorks Inc.—MATLAB Version: 9.12.0 (R2022a). Available online: https://www.mathworks.com (accessed on 1 December 2022).







| Parameters | Values |
|---|---|
| Number of connection-requesting IoT devices per PRACH (n) | 2∼30 |
| Number of available preambles (M) | 32 |
| Number of preambles simultaneously transmitted at Step 1 (k) | 1∼3 |
| Maximum iteration rounds of the MRE process (R) | 1∼3 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, T.; Chae, S.; Lim, J.-T.; Bang, I. Resource-Efficient Parallelized Random Access for Reliable Connection Establishment in Cellular IoT Networks. Sensors 2023, 23, 3819. https://doi.org/10.3390/s23083819
Kim T, Chae S, Lim J-T, Bang I. Resource-Efficient Parallelized Random Access for Reliable Connection Establishment in Cellular IoT Networks. Sensors. 2023; 23(8):3819. https://doi.org/10.3390/s23083819
Chicago/Turabian StyleKim, Taehoon, Seongho Chae, Jin-Taek Lim, and Inkyu Bang. 2023. "Resource-Efficient Parallelized Random Access for Reliable Connection Establishment in Cellular IoT Networks" Sensors 23, no. 8: 3819. https://doi.org/10.3390/s23083819





