DNS for IoT: A Survey
Abstract
1. Introduction
2. Related Work
3. Survey Overview and Significance
- What are the main challenges facing the implementation and adoption of IoT on larger scales?
- How can the Domain Name System be used to address these challenges to facilitate the growth of IoT safely and cooperatively?
- What impact could the large-scale implementation of IoT have on DNS?
- We introduce IoT, its applications, and its main challenges.
- We explain the function of DNS, its security drawbacks, and the most important DNS security protocols and extensions.
- We perform a comprehensive literature review to investigate utilizing DNS to address the various challenges of IoT environments. To the best of our knowledge, a comprehensive survey of this nature has not been previously carried out. Hence, we perform a literature review about DNS usage in IoT environments to address the various challenges.
4. Method
- The concepts of IoT, its architecture, and applications.
- IoT’s challenges, including the constrained nature of IoT devices, IoT identification, interoperability between IoT technologies, and IoT security.
- DNS function, security and privacy drawbacks, and security and privacy extensions and protocols.
- The use of DNS in IoT environments to address at least one of the IoT challenges mentioned above.
- The effect IoT might have on DNS. Here we considered negative effects.
5. The Internet of Things (IoT)
5.1. Definition of IoT
- Data carriers: These are usually static, such as barcodes, and attached to physical things.
- Data-carrying devices: These devices might have the information stored in them altered by a data-capturing device, e.g., Radio-frequency identification (RFID).
- Data-capturing devices: These devices can read from or write to a physical thing. The physical thing could be a data carrier or a data-carrying device.
- Sensing and actuating devices: This category includes sensors that can interact with their environment, gather data and measurements, and send them over the network for processing. This category also includes actuators that can perform operations in their environment based on information received over the network or their measurement of the environment around them.
- General devices: These include industrial machinery, home appliances, personal computers, and mobile phones that have embedded processing and wired or wireless communication capabilities.
5.2. IoT Architecture
5.2.1. Three-Layer Architecture
- Perception Layer: This layer contains devices like sensors, actuators, barcodes, and RFID tags. It is mainly the layer that interacts with the environment to collect data to be sent to the upper layers.
- Network Layer: This layer receives data from the perception layer. It includes the network infrastructure that transfers data between the Perception and Application layers.
- Application Layer: This layer processes and analyzes data passed through the network layer.
5.2.2. Four-Layer (SOA) Architecture
- Sensing Layer: This layer is similar to the perception layer in the three-layer model. It contains sensing tools to perform the measurements in these devices’ environments.
- Network Layer: This layer is the network infrastructure (wired or wireless) that ensures connectivity between things among themselves and between things and their backend.
- Service Layer: This layer stores and processes information. Services required by users are created and managed here.
- Interface Layer: This layer defines interaction rules between users and devices. It also attempts to solve compatibility issues between devices from different vendors that follow different standards.
5.2.3. Five-Layer Architecture
- Perception Layer: This layer is similar to the Perception Layer in the three-layer architecture.
- Transport Layer: Also referred to as the network layer. This layer receives data from the perception layer and passes them to the processing layer.
- Processing Layer: This layer processes and analyzes data passed through the network layer.
- Application Layer: Data from the processing layer are used here for IoT applications.
- Business Layer: This layer contains the management of the IoT system.
5.3. Applications of IoT
6. Challenges in IoT
6.1. The Constrained IoT
- Limited ROM\Flash, leading to limitations on the maximum code complexity;
- Limited RAM, leading to constraints on the buffer sizes;
- Limited processing power;
- Batteries as sources of power;
- Constraints on user interface and accessibility in deployment.
6.2. Identification in IoT
6.2.1. Taxonomy of IoT Identifiers
6.2.2. Requirements for IoT Identifiers
6.2.3. IoT Identification Schemes
- IP Addresses: We start with the most common identifier, the Internet Protocol (IP) address. In the context of IoT, IP typically means IPv6 since the 32-bit IPv4 is already exhausted. On the other hand, the 128-bit IPv6 has a massive address space ( addresses) and could theoretically accommodate existing and future IoT devices. RFC 4919 [62] defines how IPv6 is used in Low-Power Wireless Personal Area Networks (LoWPANs). The devices in LoWPANs conform with our definition of constrained IoT devices. According to [62], these devices conform with the IEEE 802.15.4-2003 standard and are characterized by short-range, low bit rate, low power, and limited computational power and memory. IPv6 is used in such networks as a unique identifier for each device within the scope of the network. Other than its large address space, IP is preferential because it has been around for a long time. Therefore, its standards and regulations are readily and freely available and well-known in addition to its existing infrastructure that includes management, diagnostic, and commissioning tools [62].
- Digital Object Identifier: The Digital Object Identifier (DOI) is defined in the ISO 26324:2012 standard [63]. It was initially developed by the International DOI Foundation (IDF), which three publishing institutes formed [64], and later standardized by ISO 26324:2012 [63]. Later, the DOI system became the go-to tool for identifying objects digitally. The word Digital in Digital Object Identifier refers to the identifier. DOIs are meant to be unique, persistent, and permanent digital identifiers for objects. Information about an object identified by a DOI can be retrieved upon resolving the DOI. DOIs are formed of two parts, prefix and suffix, separated by a “/” and with no maximum length. The prefix identifies a unique naming authority that is responsible for assigning DOIs. The suffix is a unique identifier of objects which, for interoperability purposes, could be an existing identifier. A typical DOI, for example, is .The Handle System [65,66] does the resolution of DOI. The Handle System is a set of distributed servers that allow the storage of handles that refer to digital objects. The system can efficiently and securely resolve the handles into information to locate and access the intended object. Additional services could be added, such as data confidentiality, data integrity, and non-repudiation.
- The Electronic Product Code (EPC): The EPC is a universal identifier for physical objects operated by GS1 [67]. It is used whenever an object needs to be tracked or identified. EPC is predominantly known as the ID used in Radio Frequency Identification (RFID). RFIDs act as data carriers holding the object’s EPC to which they are attached. However, this is not always the case. EPC is not exclusively used in RFID; the latter does not always contain an EPC. When stored on computer systems, EPCs are in the form of a Universal Resource Identifier (URI), often referred to as Pure Identity EPC URI. A typical Pure Identity EPC URI in Uniform Resource Names (URN) notation, for example, isOn RIFD tags, and due to their memory limitations, EPCs are encoded in binary form. The resolution of EPC codes is accomplished using the Object Name Service (ONS) [11], which is based on the existing Domain Name System (DNS).
- Object Identifier: The Object Identifier (OID) [68] was developed jointly by ITU-T starting with ITU-T X.660 series [69], and ISO through ISO/IEC 9834-1:2012 [70]. The goal was to provide an unambiguous persistent name for objects. The OIDs are organized in a hierarchical tree structure. The top level is called the root; under it are nodes from which many arcs branch infinitely. An object’s name is the path from the root downwards until the node related to that object is reached. A typical OID in dot notation, for example, isand in URN notationFor resolution, the OID Resolution System (ORS) is a DNS-based system that accepts queries about OIDs and returns associated information. Various objects, big and small, could be identified using OIDs, such as countries, companies, X.509 certificates, standards, and Simple Network Management Protocol Management Information Bases (SNMP MIBs), to name a few.
6.3. IoT Security
- Perception Layer Attacks
- −
- Node capture attack: A physical attack against IoT nodes where the attacker captures the node and gains control over it. The attacker can then either impersonate the node, block incoming and outgoing traffic, or gain unauthorized access to the network associated with the node.
- −
- Replay attack: Replay attacks happen when the attacker captures a legitimate message destined for the device and saves it. The attacker later retransmits (replays) the same message to trick the devices about the sender’s identity. Replay attacks could allow attackers to access the network and control the devices.
- −
- Side-channel attack: Side-channel attacks occur due to unintentional device information leakage. This includes power consumption, acoustic emissions, or timing information. Using this information, an attacker might be able to, for example, guess the device’s key based on the power consumption during encryption or decryption.
- −
- False data injection attack: Occurs when attackers inject false data into devices. These attacks can be carried out manually on compromised devices, using Man-in-the-Middle or malware. False data injection attacks are particularly dangerous in critical applications such as healthcare.
- Network Layer Attacks
- −
- Spoofing attack: Occurs when an attacker impersonates legitimate devices or users on the network. This is achieved by altering data to make them look like they originated from other users or devices. Spoofing includes, for example, MAC spoofing, IP spoofing, or DNS spoofing.
- −
- Man in The Middle attack: Such attacks happen while data is transmitted between devices or between a device and its backend servers. The attacker intercepts the data and could sniff, alter, or block the communication.
- −
- Sinkhole attack: Occurs when attackers redirect IoT traffic to a compromised device or malicious server instead of the legitimate destination. This is accomplished by controlling the DNS or routing infrastructure.
- −
- DoS attack: Denial of Service (DoS) attacks occur when a large number of compromised devices are used to overwhelm a target server by sending a large number of requests. The target could be a DNS server or a regular web server.
- Application Layer Attacks
- −
- Phishing attack: Occurs when an attacker sends a malicious file or link to users of IoT devices posing as a legitimate entity such as a service provider or a manufacturer. Malware is installed upon clicking the link or opening the file, which might grant the attacker access to the network and control over its devices.
- −
- Stolen Verifier attack: Occurs when an attacker obtains a password or an authentication token that grants them access to the network and the devices connected to it. The attacker can then impersonate the users or devices of the network, leading to possible information theft or data corruption.
- −
- Cross-site scripting (XSS) attack: An injection attack where the attacker injects malicious code into a webpage or web application. This could be, for example, the web interface for managing IoT devices. As a result, the attacker can control the devices, steal sensitive information, or corrupt data.
- −
- Cross-site request forgery (CSRF) attack: Occurs when an attacker tricks a user into performing a malicious action on the webpage the user is already authenticated to. The attacker can then gain access to the network, steal or corrupt data, or control the devices connected to that network.
- −
- SQL injection attack: Occurs when an attacker inserts malicious SQL statements into an application’s input field. As a result, the attacker can corrupt, steal, or modify data. In the context of IoT, an IoT device with a web interface that accepts user input, such as a security camera with a login page, may be vulnerable to SQL injection attacks.
6.4. IoT Interoperability
- The Web of Things: The Web of Things (WoT) [92,93], created by the World Wide Web Consortium (W3C), is a concept that aims to enable interoperability between existing IoT technologies by connecting things in these networks to the web. WoT aims to preserve and complement existing IoT technologies rather than implement new ones. The main building blocks of the WoT are:
- Thing Description (TD): The TD is a central building block of WoT. It contains metadata describing the thing, a set of Interaction Affordances indicating how the thing can be used, schemas for the data exchanged with the thing for machine understandability, and web links to express the thing’s relation with other things or documents.
- Binding templates: These consist of reusable vocabulary and extensions to the TD format that enables a client to interact with diverse things exposing different protocols.
- Scripting API: An optional block that enables implementing the application logic of a thing using a common JavaScript API similar to web browser APIs.
- Security and Privacy Guidelines: Guidelines for secure implementation and configuration of things.
- OneM2M: OneM2M [95] was established in 2012 as a partnership project between eight standardization bodies. The goal was to address the interoperability problem in IoT and machine-to-machine communications by promoting a global IoT standard. OneM2M does not propose a new standard but builds on the existing standards and aims to facilitate interoperability. This is achieved by defining a common middleware between IoT devices, communication networks, and IoT applications. This middleware service layer contains a suite of common service functions (CSFs) exposed to IoT devices and applications via RESTful APIs. CSFs are general-purpose services unrelated to specific IoT domains or technologies. They can be looked at as generic operating system tools that various IoT devices and applications could use. The claim is that OneM2M allows any IoT application to connect to any IoT device, facilitating interoperability between IoT silos.
7. The Domain Name System
7.1. Function of DNS
7.2. DNS Security Drawbacks
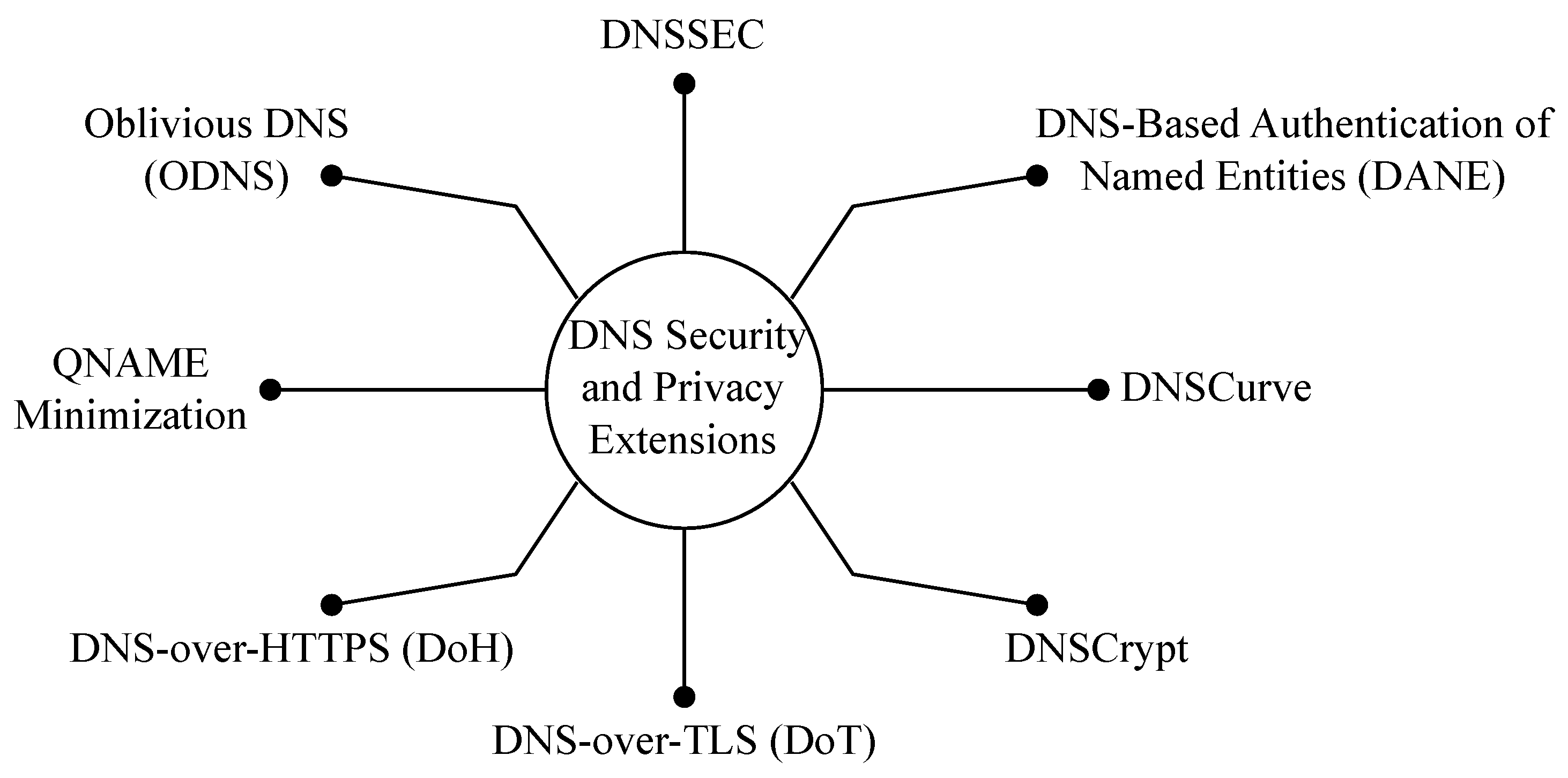
7.3. DNS Security Standards
- DNS-Based Authentication of Named Entities (DANE): DNS-Based Authentication of Named Entities (DANE), which was introduced in RFC 6698 [108], is a security protocol that allows domain name owners to associate digital certificates with their domain names to provide a way to authenticate and secure Internet communications. DANE uses DNSSEC to guarantee the integrity of certificates and associated domains.
- DNSCurve: DNSCurve [109] was designed in 2009 to add link-level security to DNS using elliptic-curve cryptography. In particular, DNSCurve preserves confidentiality by encrypting DNS packets, protects the integrity of DNS responses by cryptographically authenticating them, and ensures availability by protecting against Denial of Service (DoS) attacks. DNSCurve uses 256-bit public and secret keys, 192-bit nonces, and 128-bit authenticators. DNS servers that use DNSCurve distribute their public keys by encoding them in regular nameserver (NS) records, ensuring that the public key distribution system is compatible with registries and name server software. On the other hand, clients share their public keys in the queries they send.
- DNSCrypt: DNSCrypt [110] acts between DNS clients and DNS recursive resolvers. It uses cryptographic signatures to verify that responses from the resolvers are authentic and have not been tampered with on the way. Anonymized DNSCrypt [111] was proposed in 2019 as an extension to further secure DNS traffic by not allowing the server to see the client’s IP address.
- DNS-over-TLS: DNS-over-TLS (DoT) [9,112] is one the few IETF-standardized DNS-securing protocols (the other notable one being DNS-over-HTTPS)). Instead of the traditional UDP, DoT uses TCP and provides packet authentication and confidentiality for DNS traffic between clients and resolvers. This is achieved using TLS. A TLS session is established on TCP port 853, and DNS data are exchanged over the secure channel.
- DNS-over-HTTPS: DNS-over-HTTPS (DoH) [9,113] is the other IETF-standardized DNS-securing protocol. Its goal is also to preserve the integrity and confidentiality of DNS data. Moreover, as the name indicates, DoH uses HTTPS instead of benefiting only from the TLS handshake, as with DoT. The use of HTTPS allows a web application to use DNS securely. In DoH, any DNS query with its response is an HTTPS exchange. A client encodes the DNS request into an HTTP request using an HTTP GET or POST method.
7.4. DNS Privacy Extensions
- QNAME Minimization: One of the shortcomings of DNS is that the full QNAME and query type (QTYPE) are always sent during recursive DNS resolving, regardless of the stage of the resolving. Meanwhile, the full QNAME and QTYPE are only needed when the request reaches the authoritative name server of the domain requested. For example, when resolving “www.afnic.fr (accessed on 24 April 2023)”, the root name server receives a query with QNAME ‘www.afnic.fr’ even though it only needs to know .fr and does not need to know QTYPE. QNAME minimization [114,115] aims to allow resolvers to send minimum information at every stage of the resolution since the principle is “the less data you send out, the fewer privacy problems you have” [116]. Therefore, when sending queries to servers not authoritative for the requested domains, resolvers implementing QNAME minimization send a different QNAME to obscure the original one. Instead of the full QNAME, they send one level longer than what the name server is known to be authoritative for.
- Oblivious DNS (ODNS): ODNS [117] addresses the fact that in any privacy setup, there should always exist a party that is trusted by default. The trusted party could be any entity from the ISP to large public DNS resolver companies. When a client sends DNS requests to their designated recursive DNS resolver, the resolver has complete access to the domains requested by the client and the client’s IP. Mostly, this recursive resolver is trusted not to abuse or share this data with third parties. The trust is almost baseless since one has no solid reason to trust their recursive resolver. ODNS aims to eliminate the need for that trust by preventing the recursive resolvers from associating between client identities and requested domains. ODNS uses the existing DNS infrastructure, which facilitates its deployment.
8. DNS and IoT
8.1. DNS for Constrained IoT
8.2. DNS for IoT Name Resolution
8.3. DNS for IoT Security
8.4. DNS for IoT Interoperability
8.5. Impact of IoT on DNS
- Security: Security is the main enabler of IoT, and although DNS security is enhanced, it remains too costly for constrained IoT devices.
- Mobility: An IoT naming service should support mobility and automatic name update. DNS is ready to provide the automatic name update, but since mobility was not accounted for when designing DNS, it lacks this feature for now.
- Infrastructure Independence: Name resolution should generally be independent of the underlying infrastructure. DNS could provide that with local link extensions and technologies such as cloud computing.
- Localization: All devices must be localizable and reachable. The authors argue that DNS is evolving to account for service deployment and name format localization.
- Efficiency: Efficiency is crucial for latency-sensitive IoT services. Efficiency remains a significant challenge for DNS because the DNS name resolution mechanism incurs delays due to the hierarchical delegation and unpredictable cache hits.
- DDoS attacks: The large number of IoT devices, coupled with their security vulnerabilities, allows for DDoS attacks of increased size and complexity against Internet infrastructure, which includes the DNS [14,15]. The Mirai botnet DDoS attack against the DYN DNS service provider had an unprecedented strength at the time, reaching 1.2 Tbps [12,13]. Such attacks are launched from several hundred thousand IoT devices that the attackers control. Having many devices under the attackers’ control makes countering the attack harder with traditional filtering based on IP addresses. This allows such DDoS attacks to last for extended durations.
- DDoS amplification: These attacks, also known as reflection attacks, depend on open resolvers’ response to a query which is usually larger than the original query. Adversaries might abuse this by sending several DNS queries but using the victim’s spoofed IP address as a source for these queries. The servers then respond and send responses to the victim’s machine. The massive load received by the victim could overload its memory and CPU and put it out of service [15].
- Recent DNS vulnerability: A vulnerability in several popular TCP/IP stacks used in some IT and IoT firmware was discovered in 2021. It was referred to as ‘Name: Wreck’, and it allows the devices to be used for remote code execution and denial of service attacks [15].
9. Discussion
10. Conclusions and Future Outlook
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Bulashenko, A.; Piltyay, S.; Polishchuk, A.; Bulashenko, O. New Traffic Model of M2M Technology in 5G Wireless Sensor Networks. In Proceedings of the 2020 IEEE 2nd International Conference on Advanced Trends in Information Theory (ATIT), Kyiv, Ukraine, 25–27 November 2020; pp. 125–131. [Google Scholar] [CrossRef]
- Piltyay, S.; Bulashenko, A.; Demchenko, I. Wireless Sensor Network Connectivity in Heterogeneous 5G Mobile Systems. In Proceedings of the 2020 IEEE International Conference on Problems of Infocommunications, Science and Technology (PIC S&T), Kharkiv, Ukraine, 6–9 October 2020; pp. 625–630. [Google Scholar] [CrossRef]
- Report: Connected Devices Have More Than Doubled Since. 2019. Available online: https://www.telecompetitor.com/report-connected-devices-have-more-than-doubled-since-2019/ (accessed on 24 April 2023).
- Number of Internet of Things (IoT) Connected Devices Worldwide from 2019 to 2030. Available online: https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide/ (accessed on 24 April 2023).
- Number of Connected IoT Devices Will Surge to 125 Billion by 2030. Available online: https://sst.semiconductor-digest.com/2017/10/number-of-connected-iot-devices-will-surge-to-125-billion-by-2030/ (accessed on 24 April 2023).
- Internet of Things (IoT) Total Annual Revenue Worldwide from 2019 to 2030. Available online: https://www.statista.com/statistics/1194709/iot-revenue-worldwide/ (accessed on 24 April 2023).
- Global IoT Market to Grow to $1.5trn Annual Revenue by 2030. Available online: https://www.iot-now.com/2020/05/20/102937-global-iot-market-to-grow-to-1-5trn-annual-revenue-by-2030/ (accessed on 24 April 2023).
- Domain Names—Concepts and Facilities; RFC 1034; Internet Society: Reston, VA, USA, 1987. [CrossRef]
- Schmid, G. Thirty Years of DNS Insecurity: Current Issues and Perspectives. IEEE Commun. Surv. Tutorials 2021, 23, 2429–2459. [Google Scholar] [CrossRef]
- Saidi, S.J.; Matic, S.; Gasser, O.; Smaragdakis, G.; Feldmann, A. Deep Dive into the IoT Backend Ecosystem. In Proceedings of the Proceedings of the 22nd ACM Internet Measurement Conference, IMC ′22, Nice, France, 25–27 October 2022; Association for Computing Machinery: New York, NY, USA, 2022; pp. 488–503. [Google Scholar] [CrossRef]
- Object Name Service (ONS). Available online: https://www.gs1.org/standards/epcis/epcis-ons/2-0-1 (accessed on 24 April 2023).
- DDoS Attack That Disrupted Internet Was Largest of Its Kind in History, Experts Say. Available online: https://www.theguardian.com/technology/2016/oct/26/ddos-attack-dyn-mirai-botnet (accessed on 24 April 2023).
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the Mirai Botnet. In Proceedings of the 26th USENIX Security Symposium (USENIX Security 17), Berkeley, CA, USA, 16–18 August 2017; USENIX Association: Vancouver, BC, Canada, 2017; pp. 1093–1110. [Google Scholar]
- Hesselman, C.; Kaeo, M.; Chapin, L.; Claffy, K.; Seiden, M.; McPherson, D.; Piscitello, D.; McConachie, A.; April, T.; Latour, J.; et al. The DNS in IoT: Opportunities, Risks, and Challenges. IEEE Internet Comput. 2020, 24, 23–32. [Google Scholar] [CrossRef]
- Aucklah, K.; Mungur, A.; Armoogum, S.; Pudaruth, S. The Impact of Internet of Things on the Domain Name System. In Proceedings of the 2021 5th International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 6–8 May 2021; pp. 449–454. [Google Scholar] [CrossRef]
- HaddadPajouh, H.; Dehghantanha, A.; Parizi, R.M.; Aledhari, M.; Karimipour, H. A survey on internet of things security: Requirements, challenges, and solutions. Internet Things 2021, 14, 100129. [Google Scholar] [CrossRef]
- Ali, R.; Muneer, A.; Panneer Selvam, D.D.D.; Mohd Taib, S.; Ghaleb, E. Internet of Things (IoT) Security Challenges and Solutions: A Systematic Literature Review; Springer: Singapore, 2021; pp. 128–154. [Google Scholar] [CrossRef]
- Sadhu, P.K.; Yanambaka, V.P.; Abdelgawad, A. Internet of Things: Security and Solutions Survey. Sensors 2022, 22, 7433. [Google Scholar] [CrossRef]
- Jmila, H.; Blanc, G.; Shahid, M.R.; Lazrag, M. A Survey of Smart Home IoT Device Classification Using Machine Learning-Based Network Traffic Analysis. IEEE Access 2022, 10, 97117–97141. [Google Scholar] [CrossRef]
- Ashraf, I.; Park, Y.; Hur, S.; Kim, S.W.; Alroobaea, R.; Zikria, Y.B.; Nosheen, S. A Survey on Cyber Security Threats in IoT-Enabled Maritime Industry. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2677–2690. [Google Scholar] [CrossRef]
- Bhuiyan, M.N.; Rahman, M.M.; Billah, M.M.; Saha, D. Internet of Things (IoT): A Review of Its Enabling Technologies in Healthcare Applications, Standards Protocols, Security, and Market Opportunities. IEEE Internet Things J. 2021, 8, 10474–10498. [Google Scholar] [CrossRef]
- Ren, Y.; Xie, R.; Yu, F.R.; Huang, T.; Liu, Y. Potential Identity Resolution Systems for the Industrial Internet of Things: A Survey. IEEE Commun. Surv. Tutor. 2021, 23, 391–430. [Google Scholar] [CrossRef]
- Mazhar, N.; Salleh, R.; Zeeshan, M.; Hameed, M.M. Role of Device Identification and Manufacturer Usage Description in IoT Security: A Survey. IEEE Access 2021, 9, 41757–41786. [Google Scholar] [CrossRef]
- Guo, H.; Heidemann, J. Detecting IoT Devices in the Internet. ACM/IEEE Trans. Netw. 2020, 28, 2323–2336. [Google Scholar] [CrossRef]
- Ashton, K. That ‘Internet of Things’ Thing. Available online: https://www.itrco.jp/libraries/RFIDjournal-That%20Internet%20of%20Things%20Thing.pdf (accessed on 24 April 2023).
- Standardization of NB-IOT Completed. Available online: https://www.3gpp.org/news-events/1785-nb_iot_complete (accessed on 24 April 2023).
- Kanj, M.; Savaux, V.; Le Guen, M. A Tutorial on NB-IoT Physical Layer Design. IEEE Commun. Surv. Tutor. 2020, 22, 2408–2446. [Google Scholar] [CrossRef]
- Bluetooth® Low Energy (LE). Available online: https://www.bluetooth.com/learn-about-bluetooth/tech-overview/ (accessed on 24 April 2023).
- Sigfox. Available online: https://www.sigfox.com/en (accessed on 24 April 2023).
- Zigbee The Full-Stack Solution for All Smart Devices. Available online: https://csa-iot.org/all-solutions/zigbee/ (accessed on 24 April 2023).
- LoRa Alliance®. Available online: https://lora-alliance.org/ (accessed on 24 April 2023).
- Overview of the Internet of Things, 2012. ITU-T Recommendation Y.4000. Available online: https://www.itu.int/rec/T-REC-Y.2060-201206-I/en (accessed on 24 April 2023).
- Al-Qaseemi, S.A.; Almulhim, H.A.; Almulhim, M.F.; Chaudhry, S.R. IoT architecture challenges and issues: Lack of standardization. In Proceedings of the 2016 Future Technologies Conference (FTC), San Francisco, CA, USA, 6–7 December 2016; pp. 731–738. [Google Scholar] [CrossRef]
- Kakkar, L.; Deepali, G.; Saxena, S.; Tanwar, S. IoT Architectures and Its Security: A Review; Springer: Singapore, 2021; pp. 87–94. [Google Scholar] [CrossRef]
- Gokhale, P.; Bhat, O.; Bhat, S. Introduction to IOT. Int. Adv. Res. J. Sci. Eng. Technol. 2018, 5, 41–44. [Google Scholar]
- Elkin, D.; Vyatkin, V. IoT in Traffic Management: Review of Existing Methods of Road Traffic Regulation; Springer: Cham, Switzerland, 2020; pp. 536–551. [Google Scholar] [CrossRef]
- Dhingra, S.; Madda, R.B.; Gandomi, A.H.; Patan, R.; Daneshmand, M. Internet of Things Mobile–Air Pollution Monitoring System (IoT-Mobair). IEEE Internet Things J. 2019, 6, 5577–5584. [Google Scholar] [CrossRef]
- Cai, Z.; Zhou, Y.; Qi, Y.; Zhuang, W.; Deng, L. A Millimeter Wave Dual-Lens Antenna for IoT-Based Smart Parking Radar System. IEEE Internet Things J. 2021, 8, 418–427. [Google Scholar] [CrossRef]
- Deese, A.S.; Jesson, J.; Brennan, T.; Hollain, S.; Stefanacci, P.; Driscoll, E.; Dick, C.; Garcia, K.; Mosher, R.; Rentsch, B.; et al. Long-Term Monitoring of Smart City Assets via Internet of Things and Low-Power Wide-Area Networks. IEEE Internet Things J. 2021, 8, 222–231. [Google Scholar] [CrossRef]
- Han, H.; Ma, W.; Zhou, M.; Guo, Q.; Abusorrah, A. A Novel Semi-Supervised Learning Approach to Pedestrian Reidentification. IEEE Internet Things J. 2021, 8, 3042–3052. [Google Scholar] [CrossRef]
- Han, J.; Lin, N.; Ruan, J.; Wang, X.; Wei, W.; Lu, H. A Model for Joint Planning of Production and Distribution of Fresh Produce in Agricultural Internet of Things. IEEE Internet Things J. 2021, 8, 9683–9696. [Google Scholar] [CrossRef]
- Ben-Daya, M.; Hassini, E.; Bahroun, Z. Internet of things and supply chain management: A literature review. Int. J. Prod. Res. 2017, 57, 1–24. [Google Scholar] [CrossRef][Green Version]
- Ayaz, M.; Ammad-Uddin, M.; Sharif, Z.; Mansour, A.; Aggoune, E.H.M. Internet-of-Things (IoT)-Based Smart Agriculture: Toward Making the Fields Talk. IEEE Access 2019, 7, 129551–129583. [Google Scholar] [CrossRef]
- Tun, S.; Madanian, S.; Mirza, F. Internet of things (IoT) applications for elderly care: A reflective review. Aging Clin. Exp. Res. 2021, 33, 855–867. [Google Scholar] [CrossRef]
- Aloi, G.; Fortino, G.; Gravina, R.; Pace, P.; Savaglio, C. Simulation-Driven Platform for Edge-Based AAL Systems. IEEE J. Sel. Areas Commun. 2021, 39, 446–462. [Google Scholar] [CrossRef]
- Nouman, M.; Khoo, S.Y.; Mahmud, M.A.P.; Kouzani, A.Z. Recent Advances in Contactless Sensing Technologies for Mental Health Monitoring. IEEE Internet Things J. 2022, 9, 274–297. [Google Scholar] [CrossRef]
- Huynh-The, T.; Hua, C.H.; Tu, N.A.; Kim, D.S. Physical Activity Recognition with Statistical-Deep Fusion Model Using Multiple Sensory Data for Smart Health. IEEE Internet Things J. 2021, 8, 1533–1543. [Google Scholar] [CrossRef]
- Rashid, N.; Dautta, M.; Tseng, P.; Al Faruque, M.A. HEAR: Fog-Enabled Energy-Aware Online Human Eating Activity Recognition. IEEE Internet Things J. 2021, 8, 860–868. [Google Scholar] [CrossRef]
- Pivoto, D.G.; de Almeida, L.F.; da Rosa Righi, R.; Rodrigues, J.J.; Lugli, A.B.; Alberti, A.M. Cyber-physical systems architectures for industrial internet of things applications in Industry 4.0: A literature review. J. Manuf. Syst. 2021, 58, 176–192. [Google Scholar] [CrossRef]
- Mei, G.; Xu, N.; Qin, J.; Wang, B.; Qi, P. A Survey of Internet of Things (IoT) for Geohazard Prevention: Applications, Technologies, and Challenges. IEEE Internet Things J. 2020, 7, 4371–4386. [Google Scholar] [CrossRef]
- Kumar, N.; Acharya, D.; Lohani, D. An IoT-Based Vehicle Accident Detection and Classification System Using Sensor Fusion. IEEE Internet Things J. 2021, 8, 869–880. [Google Scholar] [CrossRef]
- Zhang, G.; Lu, D.; Liu, H. IoT-Based Positive Emotional Contagion for Crowd Evacuation. IEEE Internet Things J. 2021, 8, 1057–1070. [Google Scholar] [CrossRef]
- Bianco, G.M.; Giuliano, R.; Marrocco, G.; Mazzenga, F.; Mejia-Aguilar, A. LoRa System for Search and Rescue: Path-Loss Models and Procedures in Mountain Scenarios. IEEE Internet Things J. 2021, 8, 1985–1999. [Google Scholar] [CrossRef]
- Singh, R.P.; Javaid, M.; Haleem, A.; Suman, R. Internet of things (IoT) applications to fight against COVID-19 pandemic. Diabetes Metab. Syndr. Clin. Res. Rev. 2020, 14, 521–524. [Google Scholar] [CrossRef]
- Ndiaye, M.; Oyewobi, S.S.; Abu-Mahfouz, A.M.; Hancke, G.P.; Kurien, A.M.; Djouani, K. IoT in the Wake of COVID-19: A Survey on Contributions, Challenges and Evolution. IEEE Access 2020, 8, 186821–186839. [Google Scholar] [CrossRef] [PubMed]
- Bormann, C.; Ersue, M.; Keränen, A. Terminology for Constrained-Node Networks; RFC 7228; Internet Society: Reston, VA, USA, 2014. [Google Scholar] [CrossRef]
- Shelby, Z.; Hartke, K.; Bormann, C. The Constrained Application Protocol (CoAP); RFC 7252; Internet Society: Reston, VA, USA, 2014. [Google Scholar] [CrossRef][Green Version]
- Domain Names—Implementation and Specification; RFC 1035; Internet Society: Reston, VA, USA, 1987. [CrossRef]
- China Academy of Telecommunication Research (CATR) and Research Cluster on the Internet-of-Things (IERC). EU-China Joint White Paper on Internet-of-Things Identification. Available online: https://www.napier.ac.uk/research-and-innovation/research-search/outputs/eu-china-joint-white-paper-on-the-internet-of-things#downloads (accessed on 24 April 2023).
- Alliance for Internet of Things Innovation. Identifiers in Internet of Things (IoT). Available online: https://aioti.eu/wp-content/uploads/2018/03/AIOTI-Identifiers_in_IoT-1_0.pdf.pdf (accessed on 24 April 2023).
- Requirements and Common Characteristics of the IoT identifier for the IoT Service. 2014. ITU-T Recommendation Y.4801. Available online: https://www.itu.int/rec/T-REC-F.748.1-201410-I/en (accessed on 24 April 2023).
- Montenegro, G.; Schumacher, C.; Kushalnagar, N. IPv6 over Low-Power Wireless Personal Area Networks (6LoWPANs): Overview, Assumptions, Problem Statement, and Goals; RFC 4919; Internet Society: Reston, VA, USA, 2007. [Google Scholar] [CrossRef]
- ISO 26324:2012; Information and Documentation—Digital Object Identifier System. The International DOI Foundation: Westwood, MA, USA, 2012.
- DOI Handbook. Available online: https://www.doi.org/hb.html (accessed on 24 April 2023).
- Lannom, L.; Boesch, L.C.B.P.; Sun, S. Handle System Overview; RFC 3650; Internet Society: Reston, VA, USA, 2003. [Google Scholar] [CrossRef]
- Handle.Net Registry. Available online: https://www.handle.net/ (accessed on 24 April 2023).
- Gs1 EPC Tag Data Standard. Available online: https://www.gs1.org/standards/rfid/tds (accessed on 24 April 2023).
- Object Identifier (OID) Repository. Available online: http://oid-info.com/ (accessed on 24 April 2023).
- Information Technology—Procedures for the Operation of Object Identifier Registration Authorities: General Procedures and Top Arcs of the International Object Identifier Tree. ITU-T Recommendation X.660. 2011. Available online: https://www.itu.int/rec/T-REC-X.660-201107-I/en (accessed on 24 April 2023).
- ISO/IEC 9834-1:2012; Information Technology—Procedures for the Operation of Object Identifier Registration Authorities: General Procedures and Top Arcs of the International Object Identifier Tree—Part 1. ISO/IEC JTC 1/SC 6 Telecommunications and Information Exchange between Systems. Seoul, Republic of Korea. 2012. Available online: https://www.iso.org/obp/ui/#iso:std:iso-iec:9834:-1:ed-4:v1:en (accessed on 24 April 2023).
- Garcia-Morchon, O.; Kumar, S.; Sethi, M. Internet of Things (IoT) Security: State of the Art and Challenges; RFC 8576; Internet Society: Reston, VA, USA, 2019. [Google Scholar] [CrossRef]
- Zandberg, K.; Schleiser, K.; Acosta, F.; Tschofenig, H.; Baccelli, E. Secure Firmware Updates for Constrained IoT Devices Using Open Standards: A Reality Check. IEEE Access 2019, 7, 71907–71920. [Google Scholar] [CrossRef]
- Ghubaish, A.; Salman, T.; Zolanvari, M.; Unal, D.; Al-Ali, A.; Jain, R. Recent Advances in the Internet-of-Medical-Things (IoMT) Systems Security. IEEE Internet Things J. 2021, 8, 8707–8718. [Google Scholar] [CrossRef]
- Ding, Y.; Wu, G.; Chen, D.; Zhang, N.; Gong, L.; Cao, M.; Qin, Z. DeepEDN: A Deep-Learning-Based Image Encryption and Decryption Network for Internet of Medical Things. IEEE Internet Things J. 2021, 8, 1504–1518. [Google Scholar] [CrossRef]
- Rahman, A.; Hossain, M.S.; Alrajeh, N.A.; Alsolami, F. Adversarial Examples—Security Threats to COVID-19 Deep Learning Systems in Medical IoT Devices. IEEE Internet Things J. 2021, 8, 9603–9610. [Google Scholar] [CrossRef]
- Mohanta, B.K.; Jena, D.; Ramasubbareddy, S.; Daneshmand, M.; Gandomi, A.H. Addressing Security and Privacy Issues of IoT Using Blockchain Technology. IEEE Internet Things J. 2021, 8, 881–888. [Google Scholar] [CrossRef]
- Schiller, E.; Aidoo, A.; Fuhrer, J.; Stahl, J.; Ziörjen, M.; Stiller, B. Landscape of IoT security. Comput. Sci. Rev. 2022, 44, 100467. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Jurcut, A.; Ranaweera, P.; Xu, L. Introduction to IoT Security; John Wiley & Sons Ltd.: Hoboken, NJ, USA, 2019; pp. 1–39. [Google Scholar] [CrossRef]
- Mishra, N.; Pandya, S. Internet of Things Applications, Security Challenges, Attacks, Intrusion Detection, and Future Visions: A Systematic Review. IEEE Access 2021, 9, 59353–59377. [Google Scholar] [CrossRef]
- Minoli, D.; Occhiogrosso, B. Blockchain mechanisms for IoT security. Internet Things 2018, 1–2, 1–13. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A Survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef][Green Version]
- Uprety, A.; Rawat, D.B. Reinforcement Learning for IoT Security: A Comprehensive Survey. IEEE Internet Things J. 2020, 2020, 3040957. [Google Scholar] [CrossRef]
- Lv, Z.; Qiao, L.; Li, J.; Song, H. Deep-Learning-Enabled Security Issues in the Internet of Things. IEEE Internet Things J. 2021, 8, 9531–9538. [Google Scholar] [CrossRef]
- Atiquzzaman, M.; Noura, M.; Gaedke, M. Interoperability in Internet of Things: Taxonomies and Open Challenges. Mob. Netw. Appl. 2018, 24, 769–809. [Google Scholar] [CrossRef][Green Version]
- Jimenez, J.; Tschofenig, H.; Thaler, D. Report from the Internet of Things (IoT) Semantic Interoperability (IOTSI) Workshop 2016; RFC 8477; Internet Society: Reston, VA, USA, 2018. [Google Scholar] [CrossRef]
- Lee, E.; Seo, Y.D.; Oh, S.R.; Kim, Y.G. A Survey on Standards for Interoperability and Security in the Internet of Things. IEEE Commun. Surv. Tutor. 2021, 23, 1020–1047. [Google Scholar] [CrossRef]
- Rahman, H.; Hussain, M.I. A comprehensive survey on semantic interoperability for Internet of Things: State-of-the-art and research challenges. Trans. Emerg. Telecommun. Technol. 2020, 31, e3902. [Google Scholar] [CrossRef]
- Nagowah, S.D.; Ben Sta, H.; Gobin-Rahimbux, B.A. An Overview of Semantic Interoperability Ontologies and Frameworks for IoT. In Proceedings of the 2018 Sixth International Conference on Enterprise Systems (ES), Limassol, Cyprus, 1–2 October 2018; pp. 82–89. [Google Scholar] [CrossRef]
- Ganzha, M.; Paprzycki, M.; Pawlowski, W.; Szmeja, P.; Wasielewska, K. Towards Semantic Interoperability Between Internet of Things Platforms. Integr. Interconnect. Interoperabil. Iot Syst. 2018, 103–127. [Google Scholar] [CrossRef]
- Gyrard, A.; Datta, S.K.; Bonnet, C. A survey and analysis of ontology-based software tools for semantic interoperability in IoT and WoT landscapes. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 86–91. [Google Scholar] [CrossRef]
- Web of Things (WoT) Architecture. Available online: https://www.w3.org/TR/wot-architecture/ (accessed on 24 April 2023).
- Datta, S.K.; Bonnet, C. Advances in Web of Things for IoT Interoperability. In Proceedings of the 2018 IEEE International Conference on Consumer Electronics-Taiwan (ICCE-TW), Yilan, Taiwan, 20–22 May 2019; pp. 1–2. [Google Scholar] [CrossRef]
- Novo, O.; Francesco, M. Semantic Interoperability in the IoT: Extending the Web of Things Architecture. ACM Trans. Internet Things 2020, 1, 1–25. [Google Scholar] [CrossRef][Green Version]
- OneM2M. Available online: https://www.onem2m.org/ (accessed on 24 April 2023).
- The Domain Naming Convention for Internet User Applications; RFC 819; Internet Society: Reston, VA, USA, 1982. [CrossRef][Green Version]
- Domain Requirements; RFC 920; Internet Society: Reston, VA, USA, 1984. [CrossRef][Green Version]
- Wicinski, T. DNS Privacy Considerations; RFC 9076; Internet Society: Reston, VA, USA, 2021. [Google Scholar] [CrossRef]
- Google Public DNS. Available online: https://developers.google.com/speed/public-dns (accessed on 24 April 2023).
- Cloudflare Public DNS. Available online: https://www.cloudflare.com/dns/ (accessed on 24 April 2023).
- Huitema, C.; Rescorla, E. Issues and Requirements for Server Name Identification (SNI) Encryption in TLS; RFC 8744; Internet Society: Reston, VA, USA, 2020. [Google Scholar] [CrossRef]
- Rose, S.; Larson, M.; Massey, D.; Austein, R.; Arends, R. DNS Security Introduction and Requirements; RFC 4033; Internet Society: Reston, VA, USA, 2005. [Google Scholar] [CrossRef]
- Rose, S.; Larson, M.; Massey, D.; Austein, R.; Arends, R. Resource Records for the DNS Security Extensions; RFC 4034; Internet Society: Reston, VA, USA, 2005. [Google Scholar] [CrossRef][Green Version]
- Rose, S.; Larson, M.; Massey, D.; Austein, R.; Arends, R. Protocol Modifications for the DNS Security Extensions; RFC 4035; Internet Society: Reston, VA, USA, 2005. [Google Scholar] [CrossRef][Green Version]
- Josefsson, S. Storing Certificates in the Domain Name System (DNS); RFC 4398; Internet Society: Reston, VA, USA, 2006. [Google Scholar] [CrossRef][Green Version]
- Arends, R.; Sisson, G.; Blacka, D.; Laurie, B. DNS Security (DNSSEC) Hashed Authenticated Denial of Existence; RFC 5155; Internet Society: Reston, VA, USA, 2008. [Google Scholar] [CrossRef][Green Version]
- Hoffman, P.E. Cryptographic Algorithm Identifier Allocation for DNSSEC; RFC 6014; Internet Society: Reston, VA, USA, 2010. [Google Scholar] [CrossRef]
- Hoffman, P.E.; Schlyter, J. The DNS-Based Authentication of Named Entities (DANE) Transport Layer Security (TLS) Protocol: TLSA; RFC 6698; Internet Society: Reston, VA, USA, 2012. [Google Scholar] [CrossRef][Green Version]
- DNSCurve: Usable Security for DNS. Available online: https://dnscurve.org/ (accessed on 24 April 2023).
- DNSCrypt. Available online: https://www.dnscrypt.org/ (accessed on 24 April 2023).
- Anonymized DNSCrypt. Available online: https://github.com/DNSCrypt/dnscrypt-protocol/blob/master/ANONYMIZED-DNSCRYPT.txt (accessed on 24 April 2023).
- Hu, Z.; Zhu, L.; Heidemann, J.; Mankin, A.; Wessels, D.; Hoffman, P.E. Specification for DNS over Transport Layer Security (TLS); RFC 7858; Internet Society: Reston, VA, USA, 2016. [Google Scholar] [CrossRef][Green Version]
- Hoffman, P.E.; McManus, P. DNS Queries over HTTPS (DoH); RFC 8484; Internet Society: Reston, VA, USA, 2018. [Google Scholar] [CrossRef]
- Bortzmeyer, S.; Dolmans, R.; Hoffman, P.E. DNS Query Name Minimisation to Improve Privacy; RFC 9156; Internet Society: Reston, VA, USA, 2021. [Google Scholar] [CrossRef]
- de Vries, W.; Scheitle, Q.; Müller, M.; Toorop, W.; Dolmans, R.; Rijswijk-Deij, R. A First Look at QNAME Minimization in the Domain Name System; Springer: Cham, Switzerland, 2019; pp. 147–160. [Google Scholar] [CrossRef]
- Cooper, A.; Tschofenig, H.; Aboba, D.B.D.; Peterson, J.; Morris, J.; Hansen, M.; Smith, R. Privacy Considerations for Internet Protocols; RFC 6973; Internet Society: Reston, VA, USA, 2013. [Google Scholar] [CrossRef][Green Version]
- Schmitt, P.; Edmundson, A.; Mankin, A.; Feamster, N. Oblivious DNS: Practical Privacy for DNS Queries. Proc. Priv. Enhancing Technol. 2019, 2019, 228–244. [Google Scholar] [CrossRef][Green Version]
- Ayoub, I.; Berthaud-Müller, G.; Balakrichenan, S.; Khawam, K.; Ampeau, B. The DNS to Reinforce the PKIX for IoT Backend Servers: Implementation and Evaluation. In Proceedings of the 2022 14th IFIP Wireless and Mobile Networking Conference (WMNC), Sousse, Tunisia, 17–19 October 2022; pp. 80–84. [Google Scholar] [CrossRef]
- Igoe, K.; McGrew, D.; Salter, M. Fundamental Elliptic Curve Cryptography Algorithms; RFC 6090; Internet Society: Reston, VA, USA, 2011. [Google Scholar] [CrossRef][Green Version]
- Lenders, M.S.; Amsüss, C.; Gündogan, C.; Schmidt, T.C.; Wählisch, M. Securing Name Resolution in the IoT: DNS over CoAP. In Proceedings of the CoNEXT Student Workshop, CoNEXT-SW ′21, Virtual, 7 December 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 11–12. [Google Scholar] [CrossRef]
- Reddy, K.T.; Wing, D.; Patil, P. DNS over Datagram Transport Layer Security (DTLS); RFC 8094; Internet Society: Reston, VA, USA, 2017. [Google Scholar] [CrossRef]
- Yan, Z.; Kong, N.; Tian, Y.; Park, Y.J. A Universal Object Name Resolution Scheme for IoT. In Proceedings of the 2013 IEEE International Conference on Green Computing and Communications and IEEE Internet of Things and IEEE Cyber, Physical and Social Computing, Beijing, China, 20–23 August 2013; pp. 1120–1124. [Google Scholar] [CrossRef]
- Karakostas, B. A DNS Architecture for the Internet of Things: A Case Study in Transport Logistics. Procedia Comput. Sci. 2013, 19, 594–601. [Google Scholar] [CrossRef][Green Version]
- Kamilaris, A.; Papakonstantinou, K.; Pitsillides, A. Exploring the use of DNS as a search engine for the Web of Things. In Proceedings of the 2014 IEEE World Forum on Internet of Things (WF-IoT), Seoul, Republic of Korea, 6–8 March 2014. [Google Scholar] [CrossRef]
- Fernandez, S.; Amoretti, M.; Restori, F.; Korczynski, M.; Duda, A. Semantic Identifiers and DNS Names for IoT. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN), IEEE, Athens, Greece, 19–22 July 2021. [Google Scholar] [CrossRef]
- Lee, S.; Jeong, J.; Park, J. DNS Name Autoconfiguration for IoT Home Devices. In Proceedings of the 2015 IEEE 29th International Conference on Advanced Information Networking and Applications Workshops, Gwangju, Republic of Korea, 24–27 March 2015; pp. 131–134. [Google Scholar] [CrossRef]
- Lee, S.; Jeong, J.P.; Park, J.S. DNSNA: DNS name autoconfiguration for Internet of Things devices. In Proceedings of the 2016 18th International Conference on Advanced Communication Technology (ICACT), Pyeongchang, Republic of Korea, 31 January–3 February 2016; pp. 410–416. [Google Scholar] [CrossRef]
- Lee, K.; Kim, S.; Jeong, J.P. DNSNAv4: DNS Name Autoconfiguration for Internet-of-Things Devices in IPv4 Networks. In Proceedings of the 2017 31st International Conference on Advanced Information Networking and Applications Workshops (WAINA), Taipei, Taiwan, 27–29 March 2017; pp. 347–351. [Google Scholar] [CrossRef]
- Perdisci, R.; Papastergiou, T.; Alrawi, O.; Antonakakis, M. IoTFinder: Efficient Large-Scale Identification of IoT Devices via Passive DNS Traffic Analysis. In Proceedings of the 2020 IEEE European Symposium on Security and Privacy (EuroS P), Genoa, Italy, 7–11 September 2020; pp. 474–489. [Google Scholar] [CrossRef]
- Balakrichenan, S.; Bernard, A.; Marot, M.; Ampeau, B. IoTRoam: Design and implementation of an open LoRaWAN roaming architecture. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021. [Google Scholar]
- Lee, K.; Kang, H.; Jeong, J.P.; Kim, H.; Park, J.S. Secure DNS name autoconfiguration for IPv6 internet-of-things devices. In Proceedings of the 2016 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Republic of Korea, 19–21 October 2016; pp. 564–569. [Google Scholar] [CrossRef]
- Kim, T.H.; Reeves, D.; Dutta, R. Advanced Secure DNS Name Autoconfiguration with Authentication for Enterprise IoT Network. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar] [CrossRef]
- von Sperling, T.L.; de Caldas Filho, F.L.; de Sousa, R.T.; e Martins, L.M.C.; Rocha, R.L. Tracking intruders in IoT networks by means of DNS traffic analysis. In Proceedings of the 2017 Workshop on Communication Networks and Power Systems (WCNPS), Brasília, Brazil, 16–17 November 2017; pp. 1–4. [Google Scholar] [CrossRef]
- Spaulding, J.; Mohaisen, D. Defending Internet of Things against Malicious Domain Names Using D-FENS. In Proceedings of the 2018 IEEE/ACM Symposium on Edge Computing (SEC), Seattle, WA, USA, 25–27 October 2018; pp. 387–392. [Google Scholar] [CrossRef]
- Ding, D.; Li, M.; Zhu, Z. Object Naming Service Supporting Heterogeneous Object Code Identification for IoT System. In Proceedings of the 2018 IEEE 42nd Annual Computer Software and Applications Conference (COMPSAC), Tokyo, Japan, 23–27 July 2018; Volume 1, pp. 545–554. [Google Scholar] [CrossRef]
- Djamaa, B.; Richardson, M. Towards Scalable DNS-Based Service Discovery for the Internet of Things; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2014; pp. 432–435. [Google Scholar] [CrossRef]
- Stolikj, M.; Verhoeven, R.; Cuijpers, P.J.L.; Lukkien, J.J. Proxy support for service discovery using mDNS/DNS-SD in low power networks. In Proceedings of the IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks 2014, Sydney, Australia, 19 June 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Stolikj, M.; Cuijpers, P.J.L.; Lukkien, J.J.; Buchina, N. Context based service discovery in unmanaged networks using mDNS/DNS-SD. In Proceedings of the 2016 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 7–11 January 2016; pp. 163–165. [Google Scholar] [CrossRef]
- DNS 2XL. Available online: https://labs.apnic.net/?p=1386 (accessed on 24 April 2023).
- Ager, B.; Dreger, H.; Feldmann, A. Predicting the DNSSEC overhead using DNS traces. In Proceedings of the 2006 40th Annual Conference on Information Sciences and Systems, Princeton, NJ, USA, 22–24 March 2006; pp. 1484–1489. [Google Scholar] [CrossRef]
- Hoeneisen, B.; Mayrhofer, A. ENUM Validation Architecture; RFC 4725; Internet Society: Reston, VA, USA, 2006. [Google Scholar] [CrossRef][Green Version]
- Li, W.; Jin, J.; Lee, J.H. Analysis of Botnet Domain Names for IoT Cybersecurity. IEEE Access 2019, 7, 94658–94665. [Google Scholar] [CrossRef]
- Dietrich, C.J.; Rossow, C.; Freiling, F.C.; Bos, H.; Steen, M.v.; Pohlmann, N. On Botnets That Use DNS for Command and Control. In Proceedings of the 2011 Seventh European Conference on Computer Network Defense, EC2ND ′11, Gothenburg, Sweden, 6–7 September 2011; pp. 9–16. [Google Scholar] [CrossRef][Green Version]
- Cheshire, S.; Krochmal, M. DNS-Based Service Discovery; RFC 6763; Internet Society: Reston, VA, USA, 2013. [Google Scholar] [CrossRef][Green Version]
- Cheshire, S.; Krochmal, M. Multicast DNS; RFC 6762; Internet Society: Reston, VA, USA, 2013. [Google Scholar] [CrossRef][Green Version]
- Hamzic, A.; Olofsson, I. DNS and the Internet of Things: Outlining the Challenges Faced by DNS in the Internet of Things. Master’s Thesis, KTH Royal Institute of Technology, Stockholm, Sweden, 2016. [Google Scholar]
- Yan, Z.; Li, H.; Zeadally, S.; Zeng, Y.; Geng, G. Is DNS Ready for Ubiquitous Internet of Things? IEEE Access 2019, 7, 28835–28846. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G.; Nitti, M. The Social Internet of Things (SIoT)—When social networks meet the Internet of Things: Concept, architecture and network characterization. Comput. Netw. 2012, 56, 3594–3608. [Google Scholar] [CrossRef]
- Xia, P.; Wang, H.; Yu, Z.; Liu, X.; Luo, X.; Xu, G.; Tyson, G. Challenges in Decentralized Name Management: The Case of ENS. In Proceedings of the 22nd ACM Internet Measurement Conference, IMC ′22, Nice, France, 25–27 October 2022; Association for Computing Machinery: New York, NY, USA, 2022; pp. 65–82. [Google Scholar] [CrossRef]
- Rajendran, B.; Palaniappan, G.; Dijesh, R.; Bindhumadhava Bapu, S.; Sudarsan, S.D. A Universal Domain Name Resolution Service—Need and Challenges—Study on Blockchain Based Naming Services. In Proceedings of the 2022 IEEE Region 10 Symposium (TENSYMP), Mumbai, India, 1–3 July 2022; pp. 1–6. [Google Scholar] [CrossRef]







| Abbreviation | Definition | Abbreviation | Definition |
|---|---|---|---|
| IoT | Internet of Things | DNS | Domain Name System |
| IP | Internet Protocol | TCP | Transmission Control Protocol |
| RFID | Radio-Frequency Identification | IoMT | Internet of Medical Things |
| IIoT | Industrial Internet of Things | RFC | Request for Comments |
| CoAP | Constrained Application Protocol | UDP | User Datagram Protocol |
| DOI | Digital Object Identifier | EPC | Electronic Product Code |
| URL | Uniform Resource Locator | URI | Universal Resource Identifier |
| ONS | Object Name Service | URN | Uniform Resource Names |
| MAC | Media Access Control | OID | Object Identifier |
| IETF | Internet Engineering Task Force | ORS | OID Resolution System |
| TLD | Top Level Domain | RR | Resource Record |
| DANE | DNS-Based Authentication of Named Entities | QNAME | Query Name |
| DDoS | Distributed Denial of Service | DNSSEC | DNS Security Extensions |
| DoH | DNS-over-HTTPS | DoT | DNS-over-TLS |
| Name | Data Size (e.g., RAM) | Code Size (e.g., Flash) |
|---|---|---|
| Class 0, C0 | ≪10 KiB | ≪100 KiB |
| Class 1, C1 | ∼10 KiB | ∼100 KiB |
| Class 2, C2 | ∼50 KiB | ∼250 KiB |
| Identifier Category | Function | Use Case |
|---|---|---|
| Objects/Things Identifiers [59,60] | Used to identify the entity of interest, which could be physical or virtual | Sensors, machines, humans, merchandise (physical). Data, files, metadata (virtual) |
| Communication Identifiers [59,60] | Used to identify Things in the scope of communicating with other devices, including Internet-based communications. | IP address, MAC address, E.164 |
| Application and Service Identifiers [59,60] | Used to identify applications/services used in the scope of IoT applications. | URL, URI, identifiers for different services on a single platform |
| User Identifier [60] | Used to identify physical or virtual objects that interact with IoT devices on the Internet. | ID for humans/animals (physical). ID for software applications interacting with IoT devices (virtual) |
| Data Identifier [60] | Used to identify data instances and datatypes | Digital Twin, stored sensor measurements |
| Location Identifier [60] | Used to specify a location within a geographical region | Coordinates, postal codes |
| Protocol Identifier [60] | Used to identify protocols so that, for example, layers within a communication stack can identify what protocols are being used by other layers | Ethertype |
| Requirement | Definition |
|---|---|
| Identify anything physical or virtual [61] | The identifier should be able to identify any physical or virtual thing as it is required that any physical or virtual thing can be connected to network infrastructure, which implies the necessity of having an identifier. |
| Communication between things [61] | Connection between things using identifiers, regardless if a particular thing needs to communicate or not, should be guaranteed. |
| Networking technology independence [61] | Identifiers should be independent of the underlying network technology used by the thing they identify. |
| Uniqueness [60] | Uniqueness is required within the specific application context. If a larger scope is needed where identifiers are no longer unique, a replacement or an extension of the identification scheme is always necessary to guarantee the identifier’s uniqueness. |
| Security and Privacy [60] | Identifiers used should be privacy- and personal-information-preserving. Ideally, identifiers should not leak information about the entity they define. The identifier by itself should not reveal, based on its structure, information about the identified thing. |
| Scalability [60] | The identification scheme should be able to accommodate the increasing number of identification-needing things in the future. |
| Interoperability [60] | Even if a single identification scheme does not exist, the existing and any newly proposed ones should account for interoperability between different schemes. |
| DNS for Constrained IoT | DNS for IoT Name Resolution |
|---|---|
| |
| DNS for IoT Security | DNS for IoT Interoperability |
|
|
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ayoub, I.; Balakrichenan, S.; Khawam, K.; Ampeau, B. DNS for IoT: A Survey. Sensors 2023, 23, 4473. https://doi.org/10.3390/s23094473
Ayoub I, Balakrichenan S, Khawam K, Ampeau B. DNS for IoT: A Survey. Sensors. 2023; 23(9):4473. https://doi.org/10.3390/s23094473
Chicago/Turabian StyleAyoub, Ibrahim, Sandoche Balakrichenan, Kinda Khawam, and Benoît Ampeau. 2023. "DNS for IoT: A Survey" Sensors 23, no. 9: 4473. https://doi.org/10.3390/s23094473
APA StyleAyoub, I., Balakrichenan, S., Khawam, K., & Ampeau, B. (2023). DNS for IoT: A Survey. Sensors, 23(9), 4473. https://doi.org/10.3390/s23094473






