Distributed Consensus Estimation for Networked Multi-Sensor Systems under Hybrid Attacks and Missing Measurements
Abstract
:1. Introduction
- Governed by multi-random variables with Bernoulli distribution, a unified hybrid attack model considering the joint impact of random FDI and DoS attacks is proposed. Different from cyber attacks on the sensor-to-estimator communication channel in [13,18], the proposed hybrid attack disrupts the data transmission between neighboring estimators in the distributed consensus estimation.
- This paper is the first attempt to provide a modified distributed consensus estimation algorithm for networked multi-sensor systems subject to hybrid attacks and missing measurements. A suboptimal distributed estimation algorithm, simplified by an approximation method, is devised to circumvent the computation of the cross-covariance matrix, thereby reducing the computational complexity.
- A co-design scheme of consensus gain coefficients, hybrid attack parameters, missing measurement probabilities and model parameters based on Lyapunov stability analysis is proposed. It is theoretically proved that the stability of the proposed distributed consensus estimator can be guaranteed by constructing a sufficient condition.
2. Problem Statement
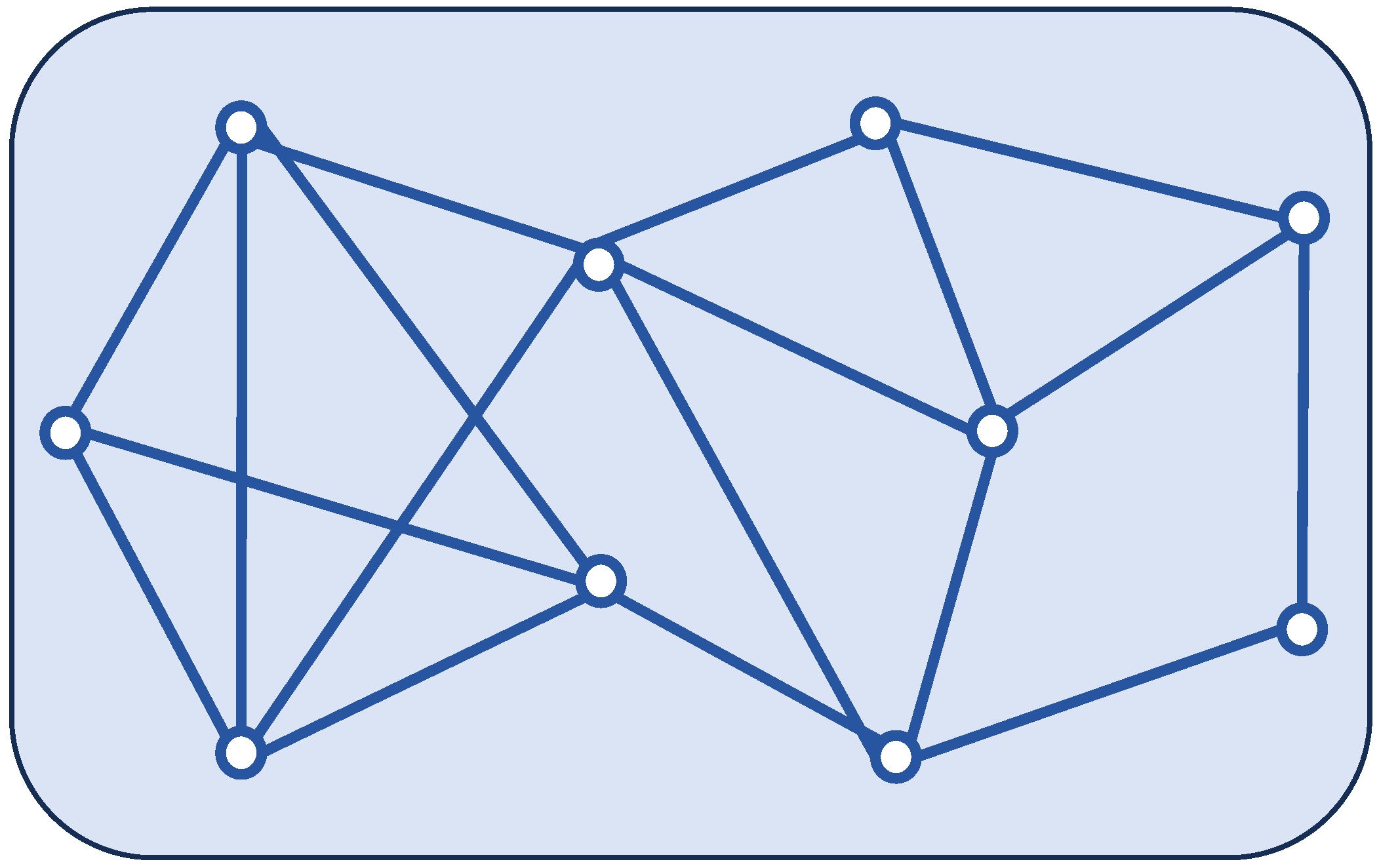
2.1. System Description
2.2. Hybrid Attack Model
2.3. Problem Statement
3. Distributed Consensus Estimator
4. A Scalable Estimation Algorithm and Stability Analysis
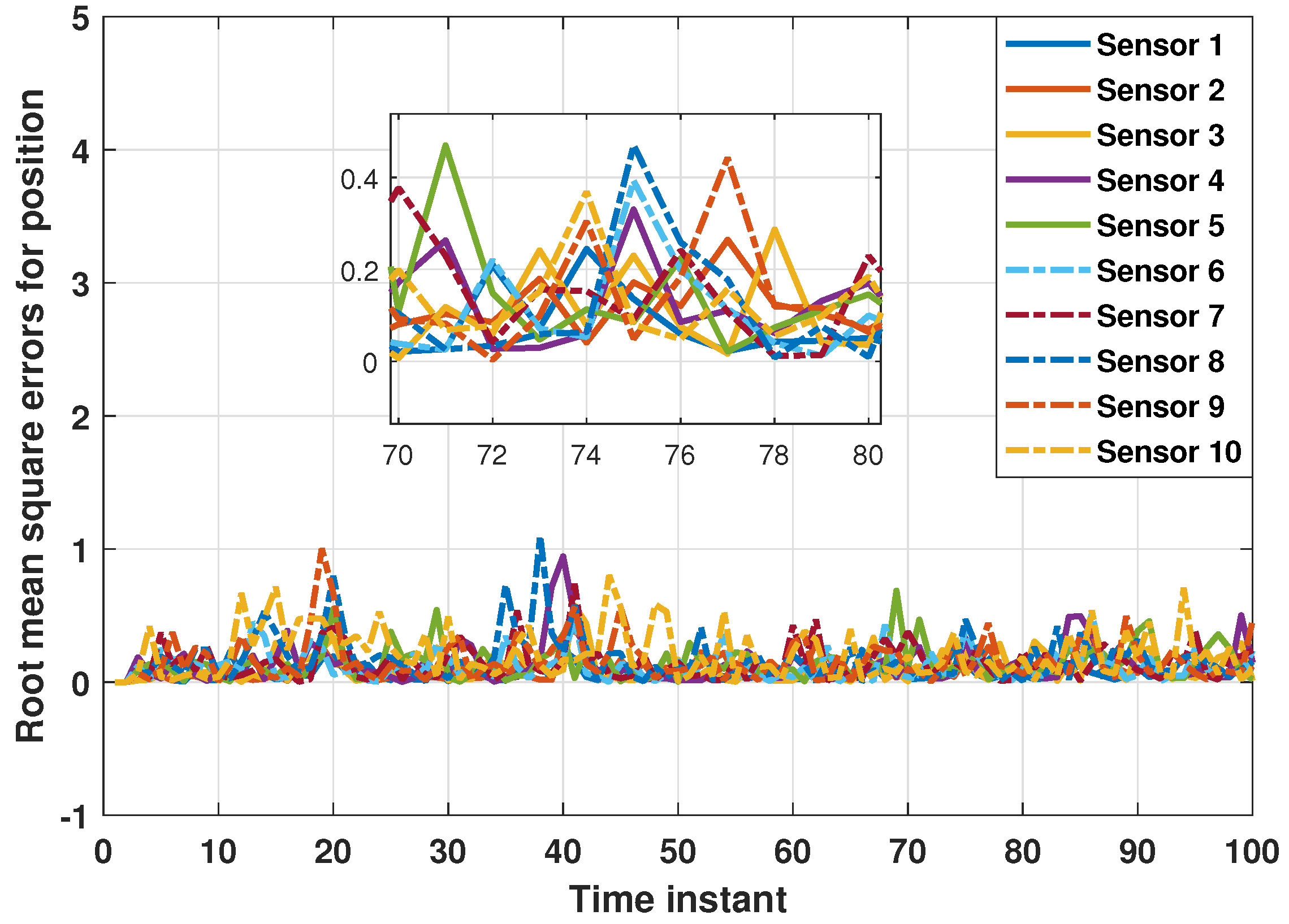
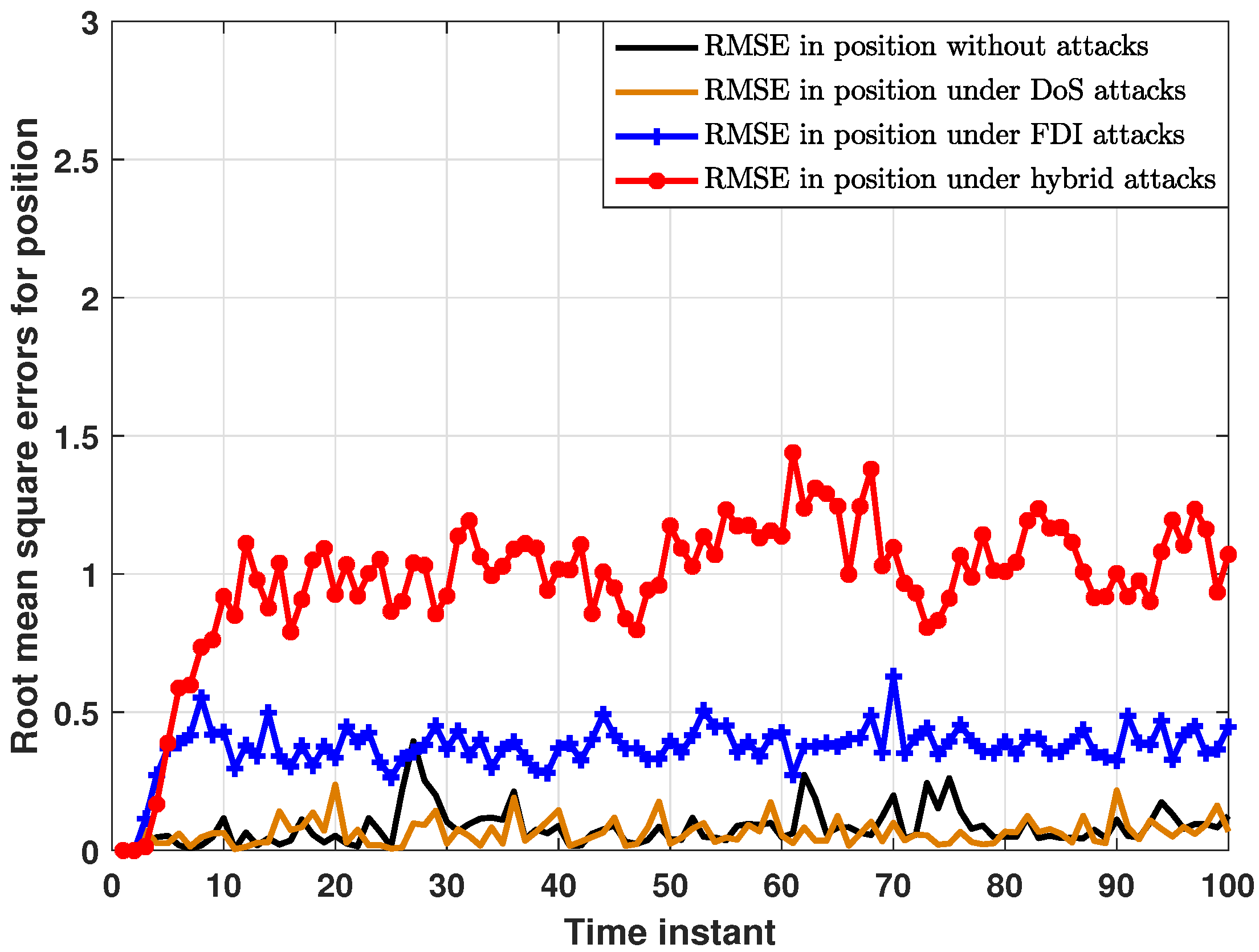
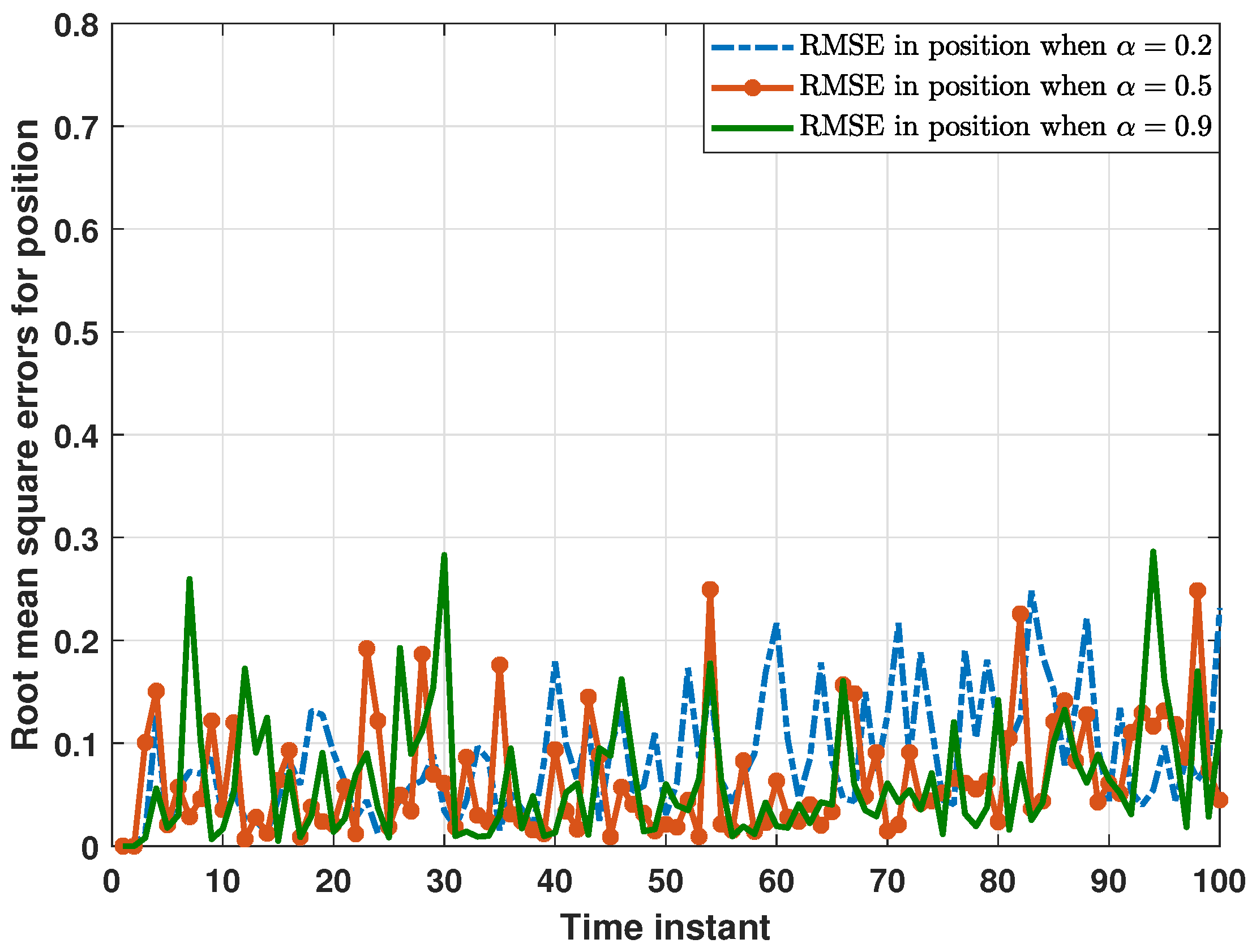
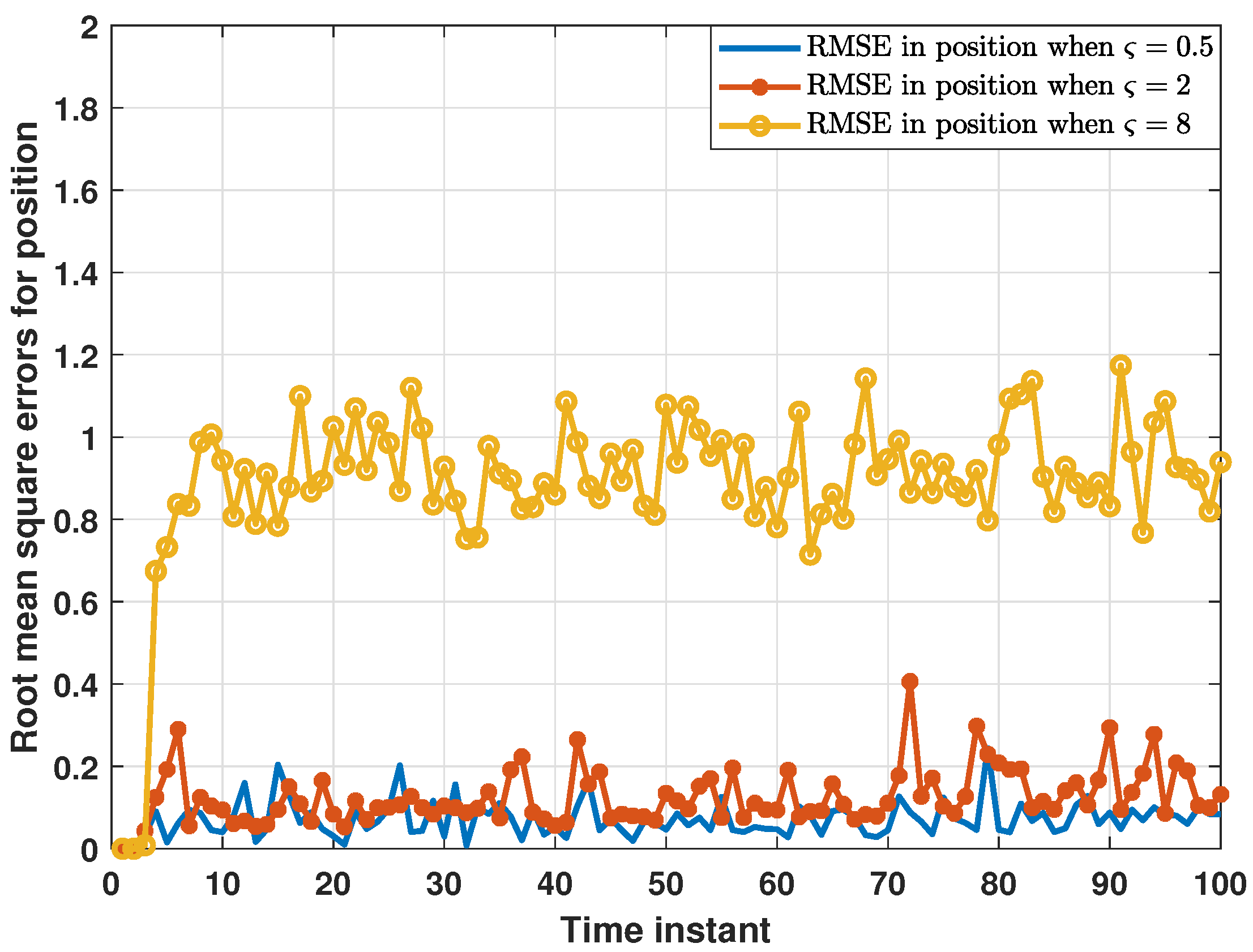
5. Simulation Results
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| FDI | false data injection |
| DoS | denial of service |
| RMSEs | root-mean-square errors |
References
- Zhou, H.; Sun, S. Distributed filtering for multi-sensor networked systems with stochastic communication protocol and correlated noises. Inf. Fusion 2024, 104, 102121. [Google Scholar] [CrossRef]
- Zhou, J.; Yang, W.; Zhang, H.; Zheng, W.X.; Xu, Y.; Tang, Y. Security analysis and defense strategy of distributed filtering under false data injection attacks. Automatica 2022, 138, 110151. [Google Scholar] [CrossRef]
- Zha, L.; Guo, Y.; Liu, J.; Xie, X.; Tian, E. Protocol-based distributed security fusion estimation for time-varying uncertain systems over sensor networks: Tackling DoS attacks. IEEE Trans. Signal Inf. Process. Over Netw. 2024, 10, 119–130. [Google Scholar] [CrossRef]
- Ren, H.; Ma, H.; Li, H.; Wang, Z. Adaptive fixed-time control of nonlinear MASs with actuator faults. IEEE/CAA J. Autom. Sin. 2023, 10, 1252–1262. [Google Scholar] [CrossRef]
- Ren, H.; Liu, Z.; Liang, H.; Li, H. Pinning-based neural control for multiagent systems with self-regulation intermediate event-triggered method. IEEE Trans. Neural Netw. Learn. Syst. 2024. [Google Scholar] [CrossRef] [PubMed]
- Xu, S.; Ye, D.; Li, G.; Yang, D. Globally stealthy attacks against distributed state estimation in smart grid. IEEE Trans. Autom. Sci. Eng. 2024. [Google Scholar] [CrossRef]
- Wang, J.; Liu, J.; Kato, N. Networking and communications in autonomous driving: A survey. IEEE Commun. Surv. Tutor. 2018, 21, 1243–1274. [Google Scholar] [CrossRef]
- Lee, J.H.; Hashimoto, H. Controlling mobile robots in distributed intelligent sensor network. IEEE Trans. Ind. Electron. 2003, 50, 890–902. [Google Scholar] [CrossRef]
- Huang, J.; Tang, Y.; Yang, W.; Li, F. Resilient consensus-based distributed filtering: Convergence analysis under stealthy attacks. IEEE Trans. Ind. Inform. 2020, 16, 4878–4888. [Google Scholar] [CrossRef]
- Niu, M.; Wen, G.; Lv, Y.; Chen, G. Innovation-based stealthy attack against distributed state estimation over sensor networks. Automatica 2023, 152, 110962. [Google Scholar] [CrossRef]
- Chen, Y.; Kar, S.; Moura, J.M. Resilient distributed estimation: Sensor attacks. IEEE Trans. Autom. Control 2019, 64, 3772–3779. [Google Scholar] [CrossRef]
- Han, F.; Wang, Z.; Dong, H.; Alsaadi, F.E.; Alharbi, K.H. A local approach to distributed H∞-consensus state estimation over sensor networks under hybrid attacks: Dynamic event-triggered scheme. IEEE Trans. Signal Inf. Process. Over Netw. 2022, 8, 556–570. [Google Scholar] [CrossRef]
- Chen, Y.; Meng, X.; Wang, Z.; Dong, H. Event-triggered recursive state estimation for stochastic complex dynamical networks under hybrid attacks. IEEE Trans. Neural Netw. Learn. Syst. 2023, 34, 1465–1477. [Google Scholar] [CrossRef] [PubMed]
- Cheng, Z.; Ren, H.; Qin, J.; Lu, R. Security analysis for dynamic state estimation of power systems with measurement delays. IEEE Trans. Cybern. 2023, 53, 2087–2096. [Google Scholar] [CrossRef]
- Li, T.; Chen, B.; Yu, L.; Zhang, W.A. Active security control approach against DoS attacks in cyber-physical systems. IEEE Trans. Autom. Control 2021, 66, 4303–4310. [Google Scholar] [CrossRef]
- Sun, Y.C.; Yang, G.H. Event-triggered remote state estimation for cyber-physical systems under malicious DoS attacks. Inf. Sci. 2022, 602, 43–56. [Google Scholar] [CrossRef]
- Liu, J.; Wang, Y.; Cao, J.; Yue, D.; Xie, X. Secure adaptive-event-triggered filter design with input constraint and hybrid cyber attack. IEEE Trans. Cybern. 2021, 51, 4000–4010. [Google Scholar] [CrossRef]
- Lv, Y.; Lu, J.; Liu, Y.; Lou, J. Resilient distributed state estimation under stealthy attack. IEEE Trans. Inf. Forensics Secur. 2022, 17, 3254–3263. [Google Scholar] [CrossRef]
- Zhou, J.; Yang, W.; Ding, W.; Zheng, W.X.; Xu, Y. Watermarking-based protection strategy against stealthy integrity attack on distributed state estimation. IEEE Trans. Autom. Control 2023, 68, 628–635. [Google Scholar] [CrossRef]
- Li, X.M.; Yao, D.; Li, P.; Meng, W.; Li, H.; Lu, R. Secure finite-horizon consensus control of multiagent systems against cyber attacks. IEEE Trans. Cybern. 2022, 52, 9230–9239. [Google Scholar] [CrossRef]
- An, D.; Zhang, F.; Cui, F.; Yang, Q. Toward data integrity attacks against distributed dynamic state estimation in smart grid. IEEE Trans. Autom. Sci. Eng. 2024, 21, 881–894. [Google Scholar] [CrossRef]
- Lei, X.; Wen, G.; Zheng, W.X.; Fu, J. Security strategy against location-varying sparse attack on distributed state monitoring. IEEE Trans. Autom. Control 2024, 69, 2514–2521. [Google Scholar] [CrossRef]
- Zhang, T.Y.; Ye, D.; Shi, Y. Decentralized false-data injection attacks against state omniscience: Existence and security analysis. IEEE Trans. Autom. Control 2023, 68, 4634–4649. [Google Scholar] [CrossRef]
- Li, W.; Jia, Y.; Du, J. Distributed Kalman consensus filter with intermittent observations. J. Frankl. Inst. 2015, 352, 3764–3781. [Google Scholar] [CrossRef]
- Hu, J.; Wang, Z.; Liu, G.P.; Zhang, H.; Navaratne, R. A prediction-based approach to distributed filtering with missing measurements and communication delays through sensor networks. IEEE Trans. Syst. Man Cybern. Syst. 2021, 51, 7063–7074. [Google Scholar] [CrossRef]
- Jin, H.; Sun, S. Distributed filtering for multi-sensor systems with missing data. Inf. Fusion 2022, 86, 116–135. [Google Scholar] [CrossRef]
- Liang, J.; Wang, Z.; Liu, X. State estimation for coupled uncertain stochastic networks with missing measurements and time-varying delays: The discrete-time case. IEEE Trans. Neural Netw. 2009, 20, 781–793. [Google Scholar] [CrossRef]
- Ren, H.; Cheng, Z.; Qin, J.; Lu, R. Deception attacks on event-triggered distributed consensus estimation for nonlinear systems. Automatica 2023, 154, 111100. [Google Scholar] [CrossRef]
- Yang, W.; Yang, C.; Shi, H.; Shi, L.; Chen, G. Stochastic link activation for distributed filtering under sensor power constraint. Automatica 2017, 75, 109–118. [Google Scholar] [CrossRef]
- Yang, W.; Zhang, Y.; Chen, G.; Yang, C.; Shi, L. Distributed filtering under false data injection attacks. Automatica 2019, 102, 34–44. [Google Scholar] [CrossRef]
- Du, D.; Li, X.; Li, W.; Chen, R.; Fei, M.; Wu, L. ADMM-based distributed state estimation of smart grid under data deception and denial of service attacks. IEEE Trans. Syst. Man Cybern. Syst. 2019, 49, 1698–1711. [Google Scholar] [CrossRef]
- Qin, J.; Li, M.; Shi, L.; Yu, X. Optimal denial-of-service attack scheduling with energy constraint over packet-dropping networks. IEEE Trans. Autom. Control 2018, 63, 1648–1663. [Google Scholar] [CrossRef]
- Cheng, Z.; Ren, H.; Zhang, B.; Lu, R. Distributed Kalman filter for large-scale power systems with state inequality constraints. IEEE Trans. Ind. Electron. 2021, 68, 6238–6247. [Google Scholar] [CrossRef]
- Reif, K.; Gunther, S.; Yaz, E.; Unbehauen, R. Stochastic stability of the discrete-time extended Kalman filter. IEEE Trans. Autom. Control 1999, 44, 714–728. [Google Scholar] [CrossRef]
- Li, W.; Wang, Z.; Ho, D.W.; Wei, G. On boundedness of error covariances for Kalman consensus filtering problems. IEEE Trans. Autom. Control 2019, 65, 2654–2661. [Google Scholar] [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cheng, Z.; Yang, L.; Yuan, Q.; Long, Y.; Ren, H. Distributed Consensus Estimation for Networked Multi-Sensor Systems under Hybrid Attacks and Missing Measurements. Sensors 2024, 24, 4071. https://doi.org/10.3390/s24134071
Cheng Z, Yang L, Yuan Q, Long Y, Ren H. Distributed Consensus Estimation for Networked Multi-Sensor Systems under Hybrid Attacks and Missing Measurements. Sensors. 2024; 24(13):4071. https://doi.org/10.3390/s24134071
Chicago/Turabian StyleCheng, Zhijian, Lan Yang, Qunyao Yuan, Yinren Long, and Hongru Ren. 2024. "Distributed Consensus Estimation for Networked Multi-Sensor Systems under Hybrid Attacks and Missing Measurements" Sensors 24, no. 13: 4071. https://doi.org/10.3390/s24134071




