Non-Intrusive Continuous Monitoring of Leaks for an In-Service Penstock
Abstract
:1. Introduction
2. Materials and Methods
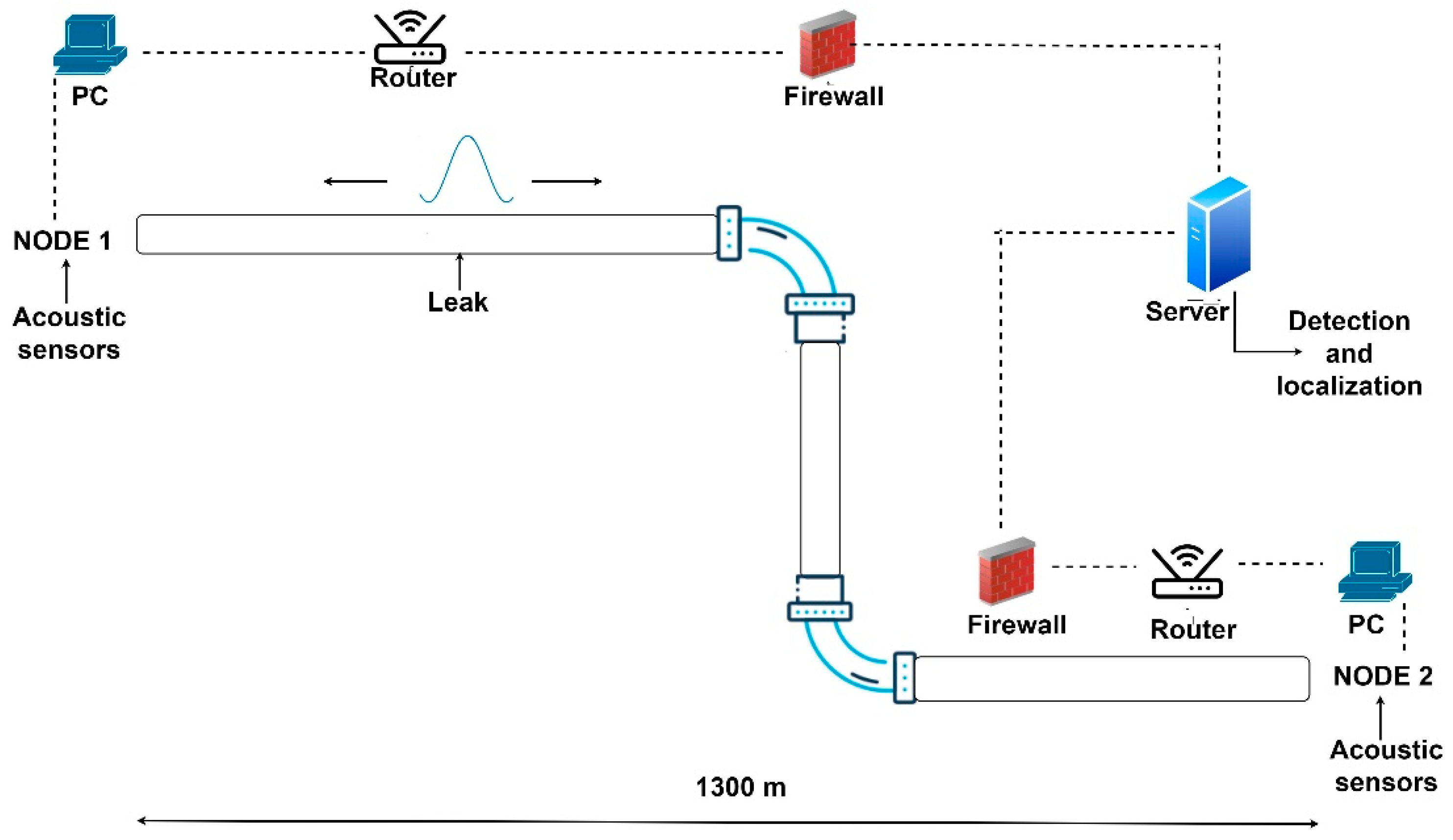
2.1. System Presentation
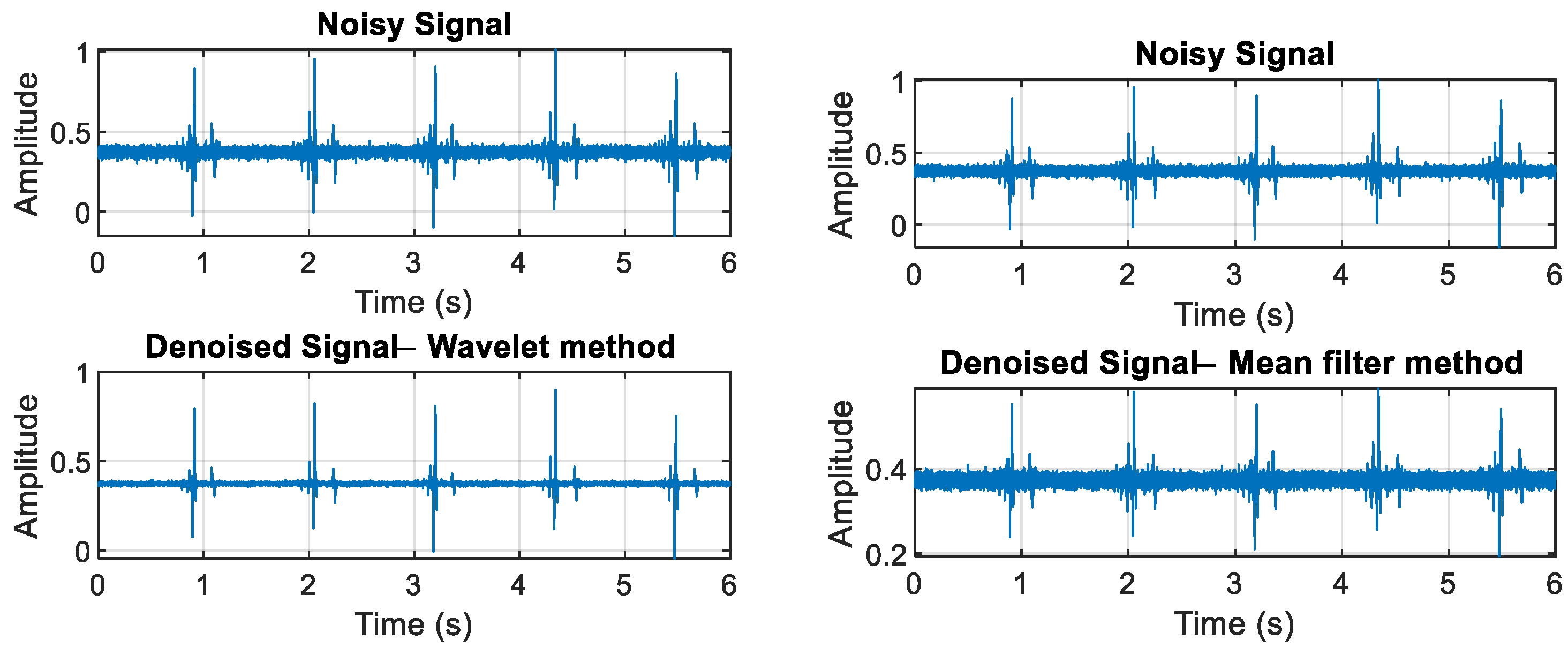
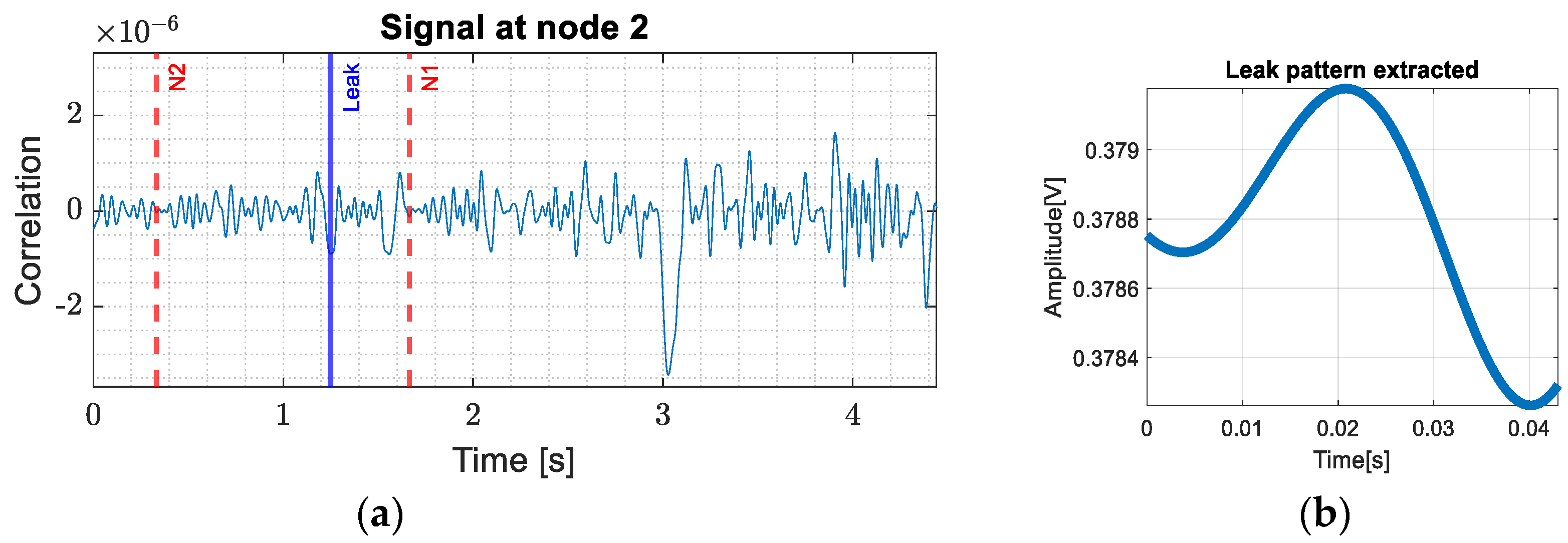
2.2. Leak Detection
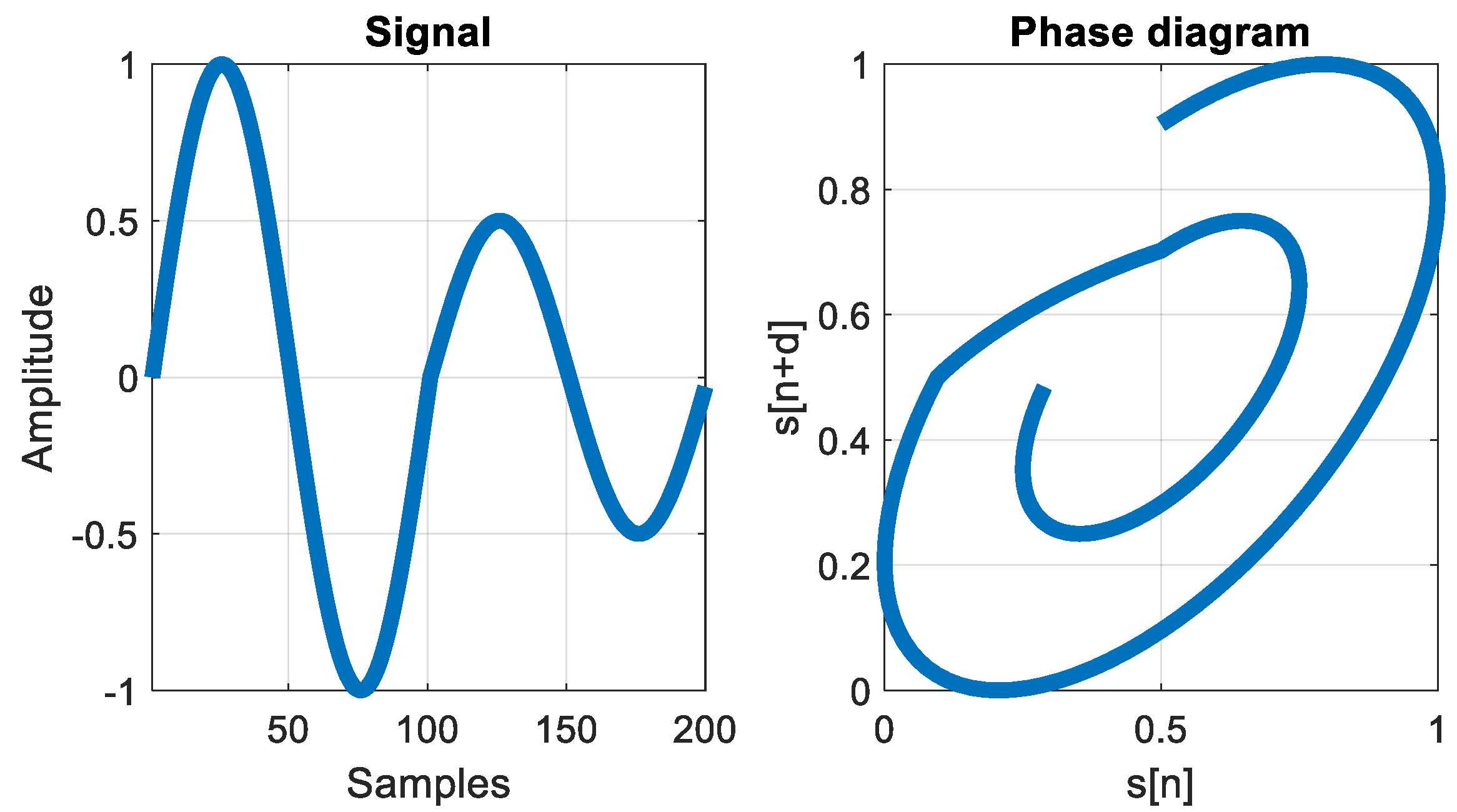
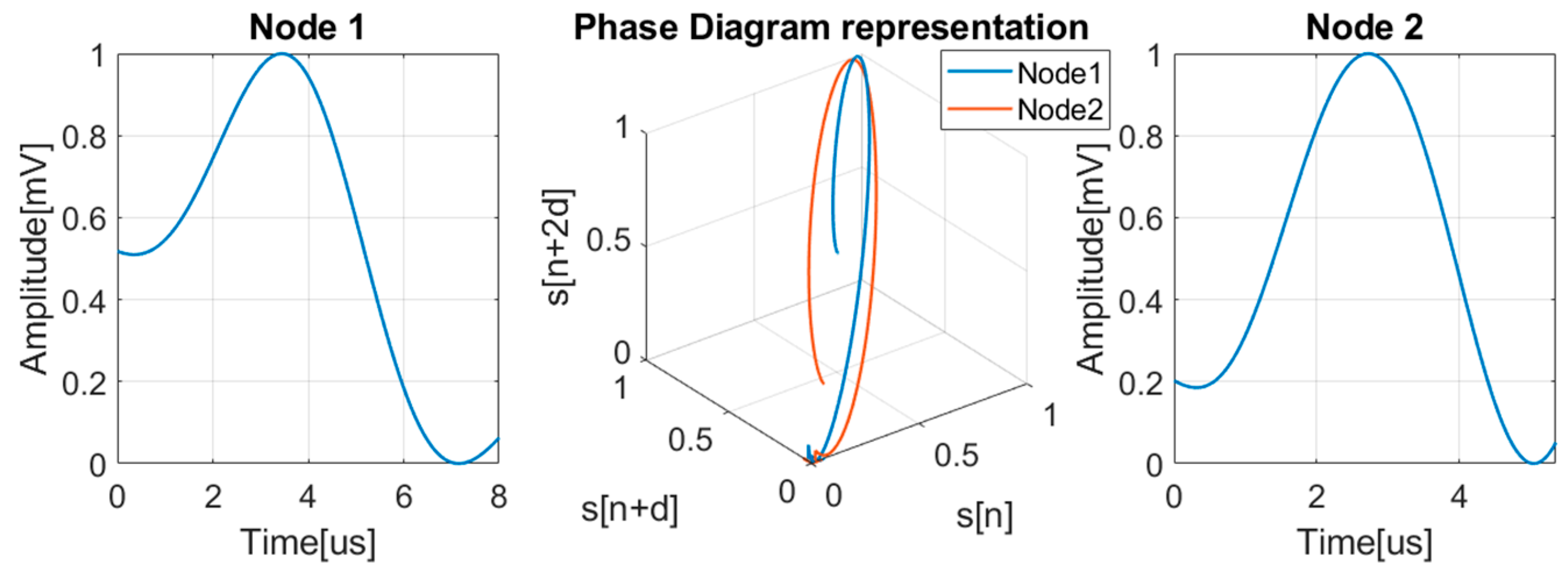
2.3. Localization Principle
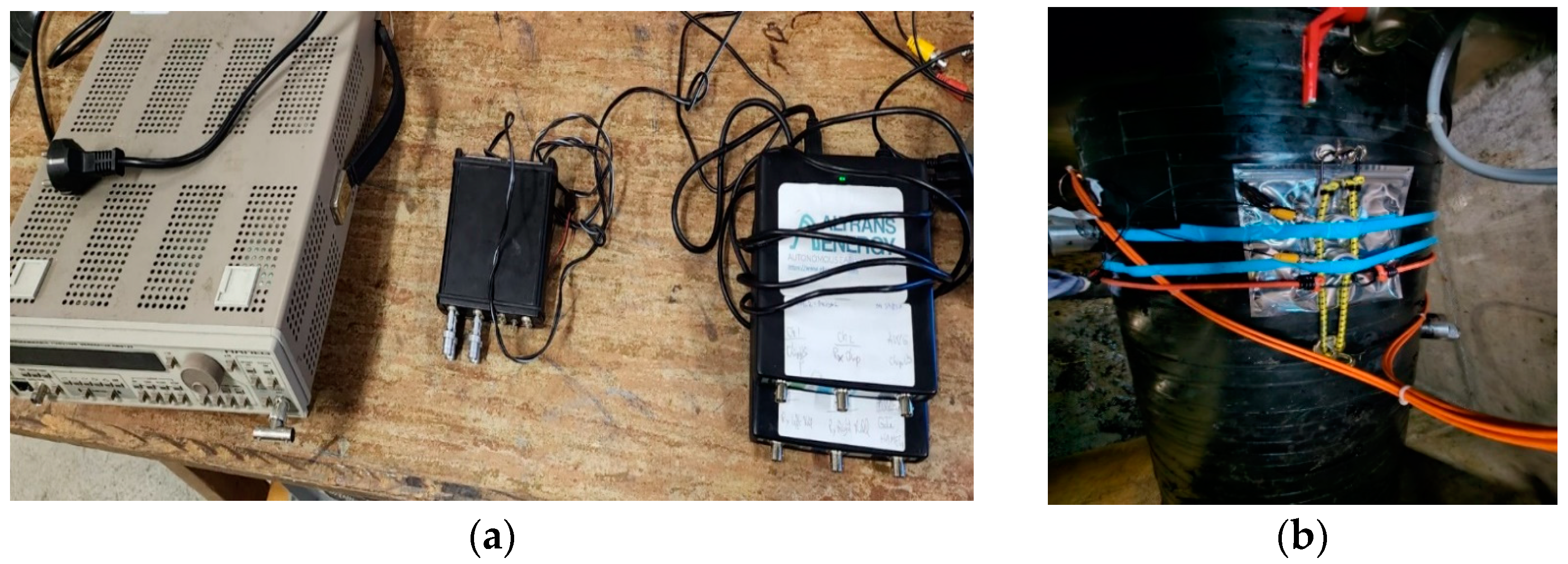
3. Experimental Results
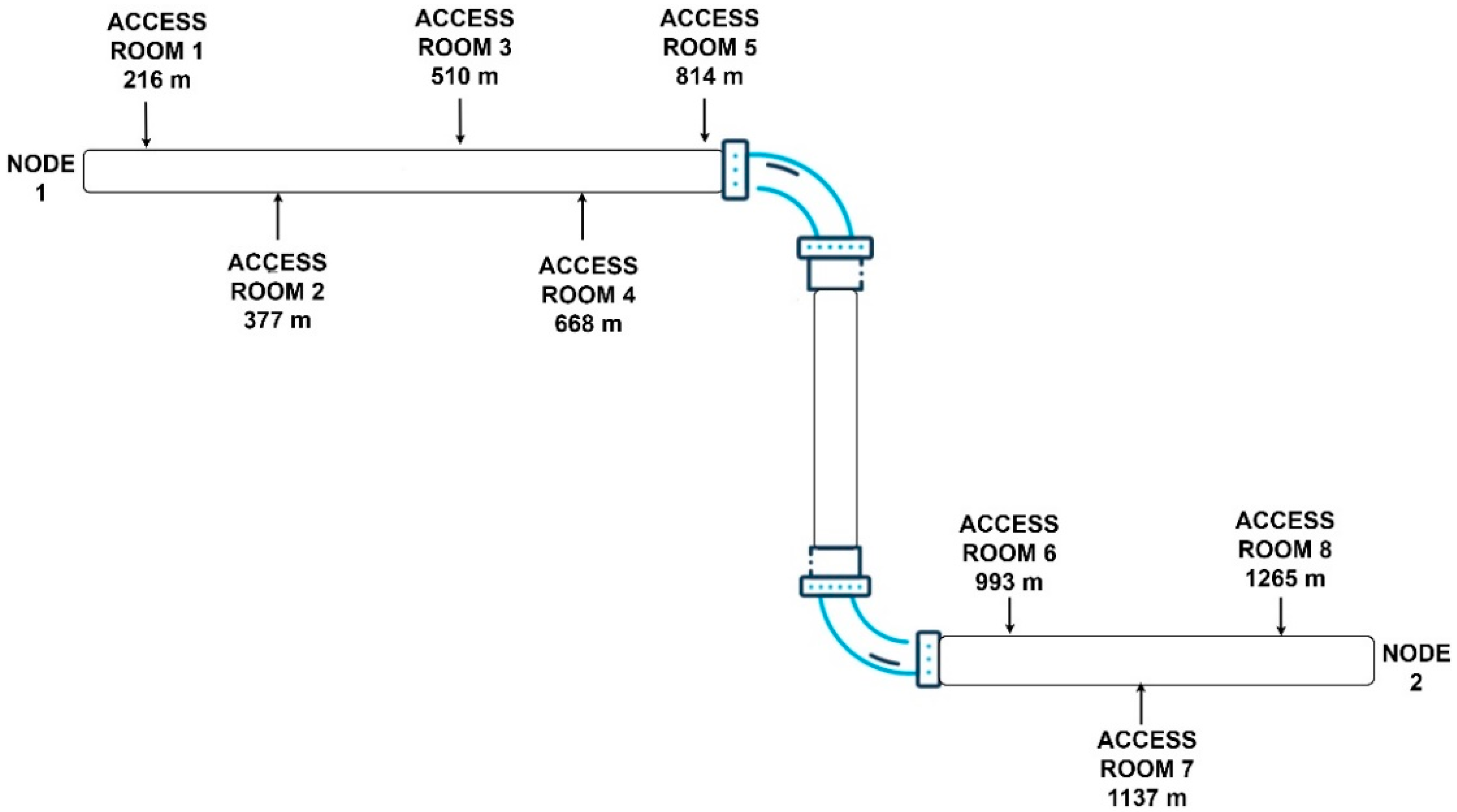
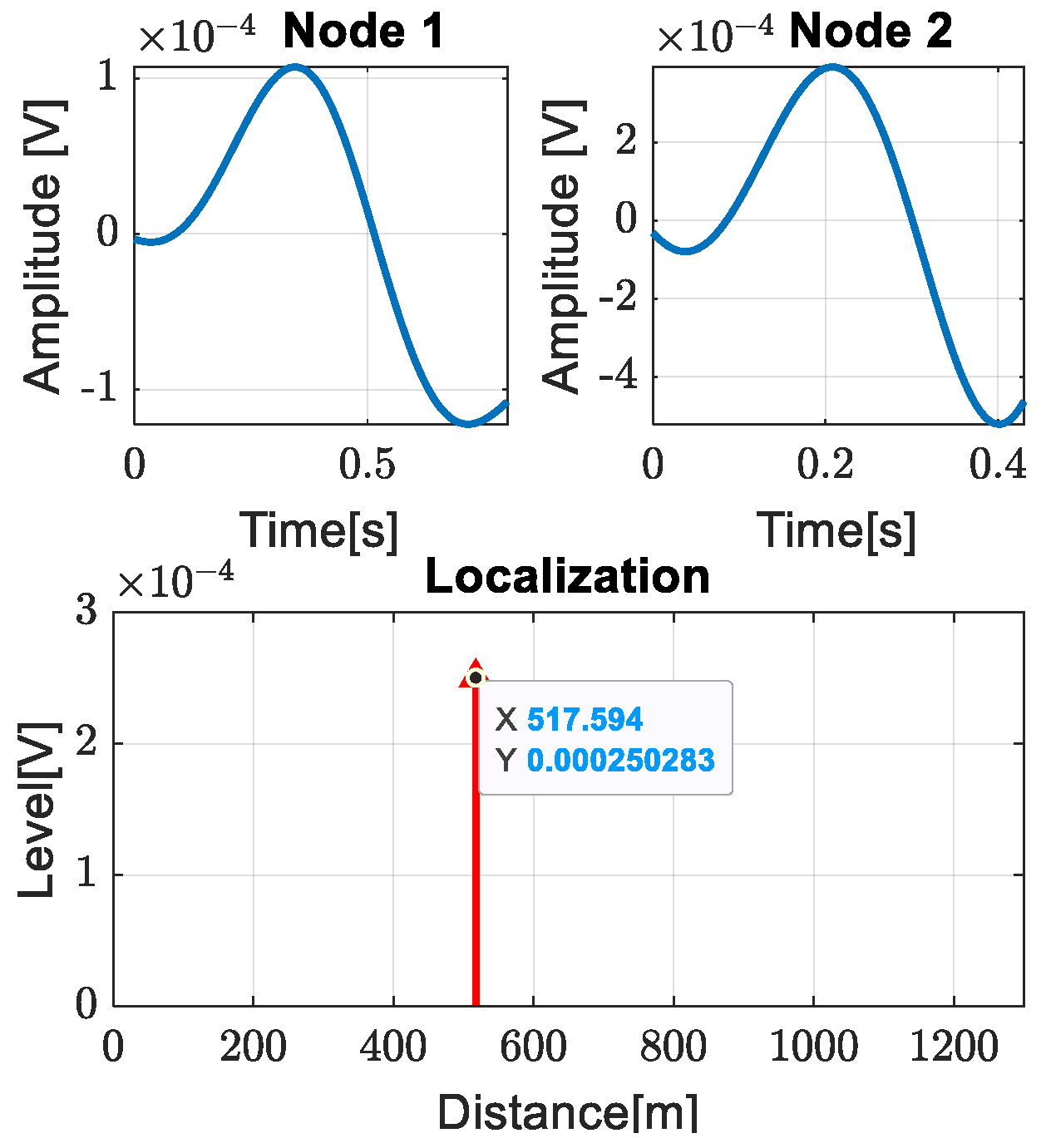
3.1. Experimental Results
3.2. Continuous Monitoring Results
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Ong, C.; Tortajada, C.; Arora, O. Water Losses. In Urban Water Demand Management: A Guidebook for ASEAN; Springer Nature: Singapore, 2023. [Google Scholar]
- Alzarooni, E.; Ali, T.; Atabay, S.; Yilmaz, A.G.; Mortula, M.M.; Fattah, K.P.; Khan, Z. GIS-Based Identification of Locations in Water Distribution Networks Vulnerable to Leakage. Appl. Sci. 2023, 13, 4692. [Google Scholar] [CrossRef]
- Almeida, F.; Brennan, M.; Joseph, P.; Whitfield, S.; Dray, S.; Paschoalini, A. On the Acoustic Filtering of the Pipe and Sensor in a Buried Plastic Water Pipe and Its Effect on Leak Detection: An Experimental Investigation. Sensors 2014, 14, 5595. [Google Scholar] [CrossRef] [PubMed]
- European Union. Directive (EU) 2020/2184 of the European Parliament and of the Council of 16 December 2020 on the Quality of Water Intended for Human Consumption (Recast). Off. J. Eur. Union 2020, 435, 1–62. [Google Scholar]
- Datta, S.; Sarkar, S. A Review on Different Pipeline Fault Detection Methods. J. Loss Prev. Process Ind. 2016, 41, 97–106. [Google Scholar] [CrossRef]
- Zaman, D.; Tiwari, M.K.; Gupta, A.K.; Sen, D. A Review of Leakage Detection Strategies for Pressurised Pipeline in Steady-State. Eng. Fail. Anal. 2020, 109, 104264. [Google Scholar] [CrossRef]
- Kim, Y.; Lee, S.J.; Park, T.; Lee, G.; Suh, J.C.; Lee, J.M. Robust Leakage Detection and Interval Estimation of Location in Water Distribution Network. IFAC-PapersOnLine 2015, 48, 1264–1269. [Google Scholar] [CrossRef]
- Aamo, O.M. Leak Detection, Size Estimation and Localization in Pipe Flows. IEEE Trans. Autom. Contr 2016, 61, 246–251. [Google Scholar] [CrossRef]
- Gamal, M.; Di, Q.; Zhang, J.; Fu, C.; Ebrahim, S.; El-Raouf, A.A. Utilizing Ground-Penetrating Radar for Water Leak Detection and Pipe Material Characterization in Environmental Studies: A Case Study. Remote Sens. 2023, 15, 4924. [Google Scholar] [CrossRef]
- Murvay, P.S.; Silea, I. A Survey on Gas Leak Detection and Localization Techniques. J. Loss Prev. Process Ind. 2012, 25, 966–973. [Google Scholar] [CrossRef]
- Ress, E.; Roberson, J.A. The Financial and Policy Implications of Water Loss. J. Am. Water Works Assoc. 2016, 108, E77–E86. [Google Scholar] [CrossRef]
- Brunone, B. Transient Test-Based Technique for Leak Detection in Outfall Pipes. J. Water Resour. Plan. Manag. 1999, 125, 302–306. [Google Scholar] [CrossRef]
- Brunone, B.; Maietta, F.; Capponi, C.; Keramat, A.; Meniconi, S. A Review of Physical Experiments for Leak Detection in Water Pipes through Transient Tests for Addressing Future Research. J. Hydraul. Res. 2022, 60, 894–906. [Google Scholar] [CrossRef]
- Meniconi, S.; Capponi, C.; Frisinghelli, M.; Brunone, B. Leak Detection in a Real Transmission Main Through Transient Tests: Deeds and Misdeeds. Water Resour. Res. 2021, 57, e2020WR027838. [Google Scholar] [CrossRef]
- Meniconi, S.; Brunone, B.; Tirello, L.; Rubin, A.; Cifrodelli, M.; Capponi, C. Transient Tests for Checking the Trieste Subsea Pipeline: Diving into Fault Detection. J. Mar. Sci. Eng. 2024, 12, 391. [Google Scholar] [CrossRef]
- Li, S.; Wen, Y.; Li, P.; Yang, J.; Yang, L. Leak Detection and Location for Gas Pipelines Using Acoustic Emission Sensors. In Proceedings of the IEEE International Ultrasonics Symposium, IUS, Dresden, Germany, 7–10 October 2012. [Google Scholar]
- Nguyen, D.T.; Nguyen, T.K.; Ahmad, Z.; Kim, J.M. A Reliable Pipeline Leak Detection Method Using Acoustic Emission with Time Difference of Arrival and Kolmogorov–Smirnov Test. Sensors 2023, 23, 9296. [Google Scholar] [CrossRef] [PubMed]
- Wu, Q.; Lee, C.M. A Modified Leakage Localization Method Using Multilayer Perceptron Neural Networks in a Pressurized Gas Pipe. Appl. Sci. 2019, 9, 1954. [Google Scholar] [CrossRef]
- Montenegro, D.; Gonzalez, J. Average Filtering: Theory, Design and Implementation. In Digital Signal Processing (DSP): Fundamentals, Techniques and Applications; Nova: Hauppauge, NY, USA, 2016. [Google Scholar]
- Agrawal, N.; Kumar, A.; Bajaj, V.; Singh, G.K. Design of Digital IIR Filter: A Research Survey. Appl. Acoust. 2021, 172, 107669. [Google Scholar] [CrossRef]
- Bakshi, S.; Javid, I.; Rajoriya, M.; Naz, S.; Gupta, P.; Sahni, M.; Singh, M. Designand Comparison between IIR Butterwoth and Chebyshev Digital Filters Using Matlab. In Proceedings of the 2019 International Conference on Computing, Communication, and Intelligent Systems, ICCCIS 2019, Greater Noida, India, 18–19 October 2019; Volume 2019. [Google Scholar]
- Lang, X.; Yuan, L.; Li, S.; Liu, M. Pipeline Multipoint Leakage Detection Method Based on KKL-MSCNN. IEEE Sens. J. 2024, 24, 11438–11449. [Google Scholar] [CrossRef]
- Xing, T.; Wang, X.; Ni, K.; Zhou, Q. A Novel Joint Denoising Method for Hydrophone Signal Based on Improved SGMD and WT. Sensors 2024, 24, 1340. [Google Scholar] [CrossRef]
- Turin, G.L. An Introduction to Matched Filters. IRE Trans. Inf. Theory 1960, 6, 311–329. [Google Scholar] [CrossRef]
- Nastasiu, D.; Bernier, M.; Ioana, C.; Tréhoult, C.; Lyannaz, L.; Garet, F. Phase Diagram Method for Efficient THz Images Reconstructing. In Proceedings of the International Conference on Infrared, Millimeter, and Terahertz Waves, IRMMW-THz, Chengdu, China, 29 August–3 September 2021; Volume 2021. [Google Scholar]
- Stanescu, D.; Digulescu, A.; Ioana, C.; Serbanescu, A. A Novel Approach for Characterization of Transient Signals Using the Phase Diagram Features. In Proceedings of the 2021 IEEE International Conference on Microwaves, Antennas, Communications and Electronic Systems, COMCAS 2021, Tel Aviv, Israel, 1–3 November 2021. [Google Scholar]
- Bordeianu, C.C.; Landau, R.H.; Paez, M.J. Wavelet Analyses and Applications. Eur. J. Phys. 2009, 30, 1049–1062. [Google Scholar] [CrossRef]
- Srirangarajan, S.; Allen, M.; Preis, A.; Iqbal, M.; Lim, H.B.; Whittle, A.J. Wavelet-Based Burst Event Detection and Localization in Water Distribution Systems. J. Signal Process Syst. 2013, 72, 1–16. [Google Scholar] [CrossRef]
- Stanescu, D.; Digulescu, A.; Ioana, C.; Serbanescu, A. Entropy-Based Characterization of the Transient Phenomena—Systemic Approach. Mathematics 2021, 9, 648. [Google Scholar] [CrossRef]
- Marwan, N.; Carmen Romano, M.; Thiel, M.; Kurths, J. Recurrence Plots for the Analysis of Complex Systems. Phys. Rep. 2007, 438, 237–329. [Google Scholar] [CrossRef]
- Stanescu, D.; Digulescu, A.; Ioana, C.; Candel, I. Early-Warning Indicators of Power Cable Weaknesses for Offshore Wind Farms. In Proceedings of the Oceans Conference Record (IEEE), Biloxi, MS, USA, 25–28 September 2023. [Google Scholar]




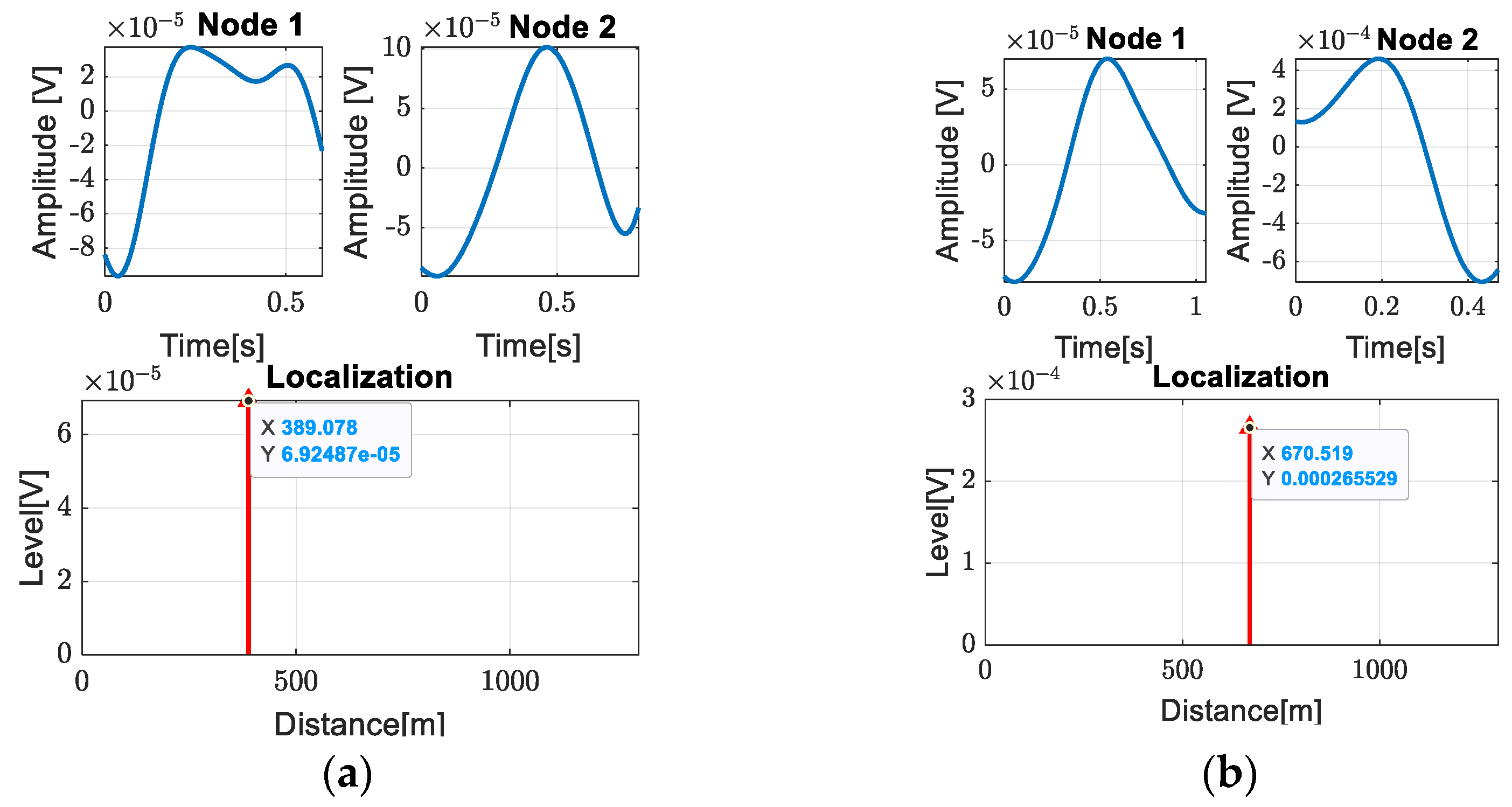
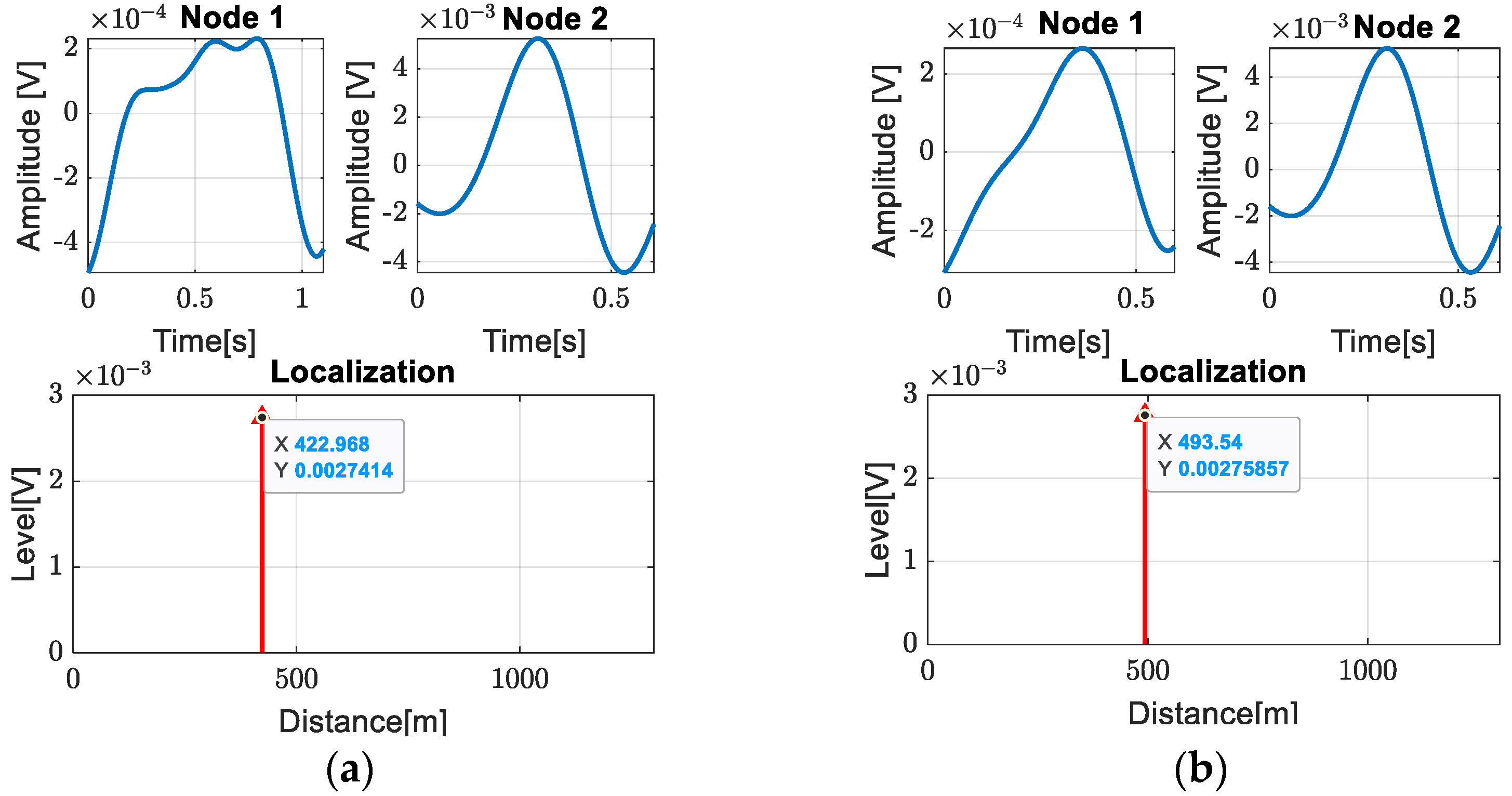
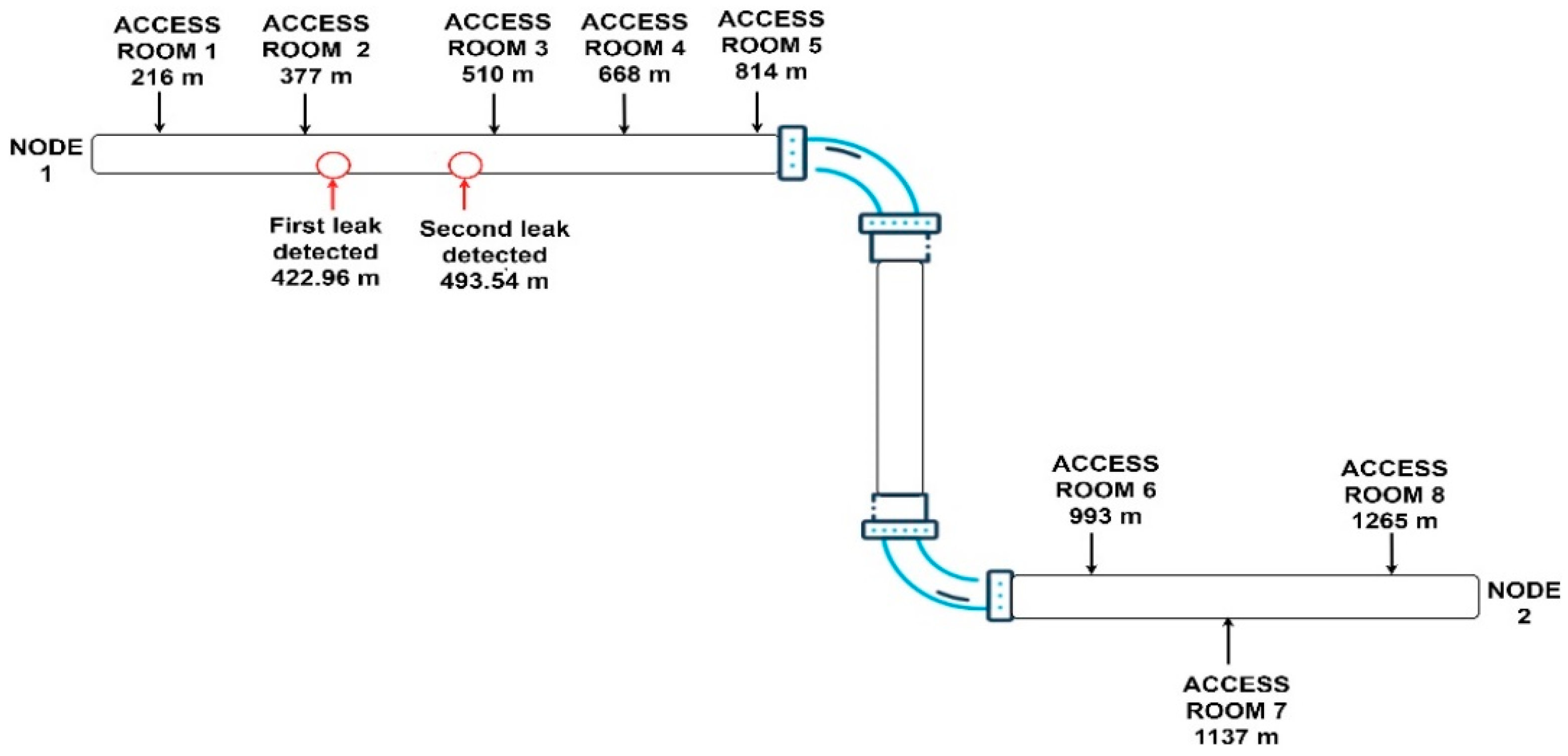


| Leak | Our Proposed Method | Position of Access Rooms | Relative Error |
|---|---|---|---|
| Leak at access room 2 | 398.078 m | 377 m | 0.928% |
| Leak at access room 3 | 517.594 m | 510 m | 0.583% |
| Leak at access room 4 | 670.519 m | 668 m | 0.193% |
| Leak | Our Proposed Method | Video Surveillance Results | Relative Error |
|---|---|---|---|
| Leak 1 | 422.96 m | 417.75 m | 0.4% |
| Leak 2 | 493.54 m | 482.78 m | 0.82% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Nati, M.; Despina-Stoian, C.; Nastasiu, D.; Stanescu, D.; Digulescu, A.; Ioana, C.; Nanchen, V. Non-Intrusive Continuous Monitoring of Leaks for an In-Service Penstock. Sensors 2024, 24, 5182. https://doi.org/10.3390/s24165182
Nati M, Despina-Stoian C, Nastasiu D, Stanescu D, Digulescu A, Ioana C, Nanchen V. Non-Intrusive Continuous Monitoring of Leaks for an In-Service Penstock. Sensors. 2024; 24(16):5182. https://doi.org/10.3390/s24165182
Chicago/Turabian StyleNati, Marius, Cristina Despina-Stoian, Dragos Nastasiu, Denis Stanescu, Angela Digulescu, Cornel Ioana, and Vincent Nanchen. 2024. "Non-Intrusive Continuous Monitoring of Leaks for an In-Service Penstock" Sensors 24, no. 16: 5182. https://doi.org/10.3390/s24165182







