Prototyping a Secure and Usable User Authentication Mechanism for Mobile Passenger ID Devices for Land/Sea Border Control
Abstract
1. Introduction
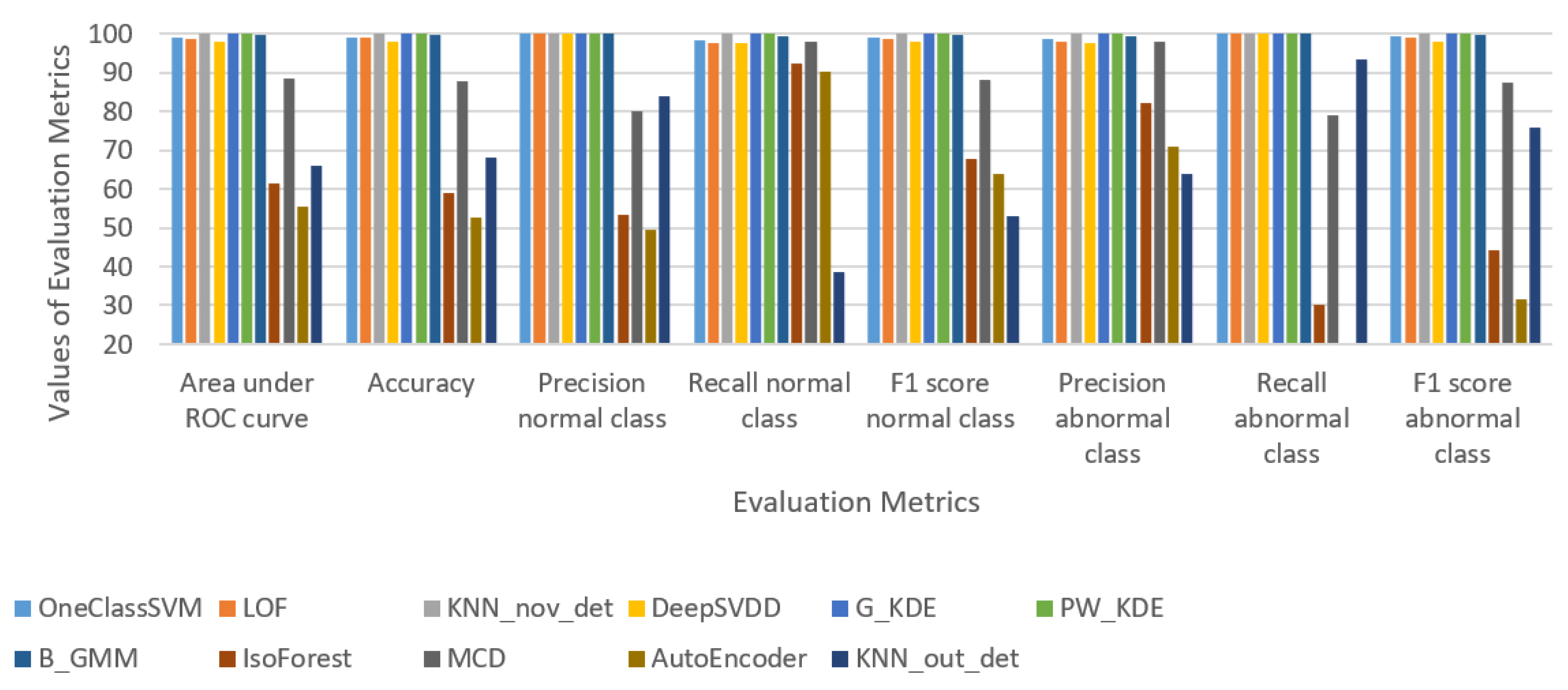
- Initially, a comprehensive overall assessment across all novelty and outlier detection algorithms, presented in [6,26,27], is conducted, using the HuMIdb dataset [28,29] to identify the most effective ones for integration into the proposed risk-based adaptive user authentication mechanism. According to our findings, the three novelty detection algorithms, namely OneClassSVM, LOF, and B_GMM, demonstrated a balance of high performance and likely generalizability to new data, outperforming the rest of the novelty detection and outlier detection algorithms.
- Additionally, as a second extension of our previous works, we developed the proposed mechanism as an application on a Raspberry Pi 4 Model B device (i.e., playing the role of the mobile device for passenger identification for land and sea border control).
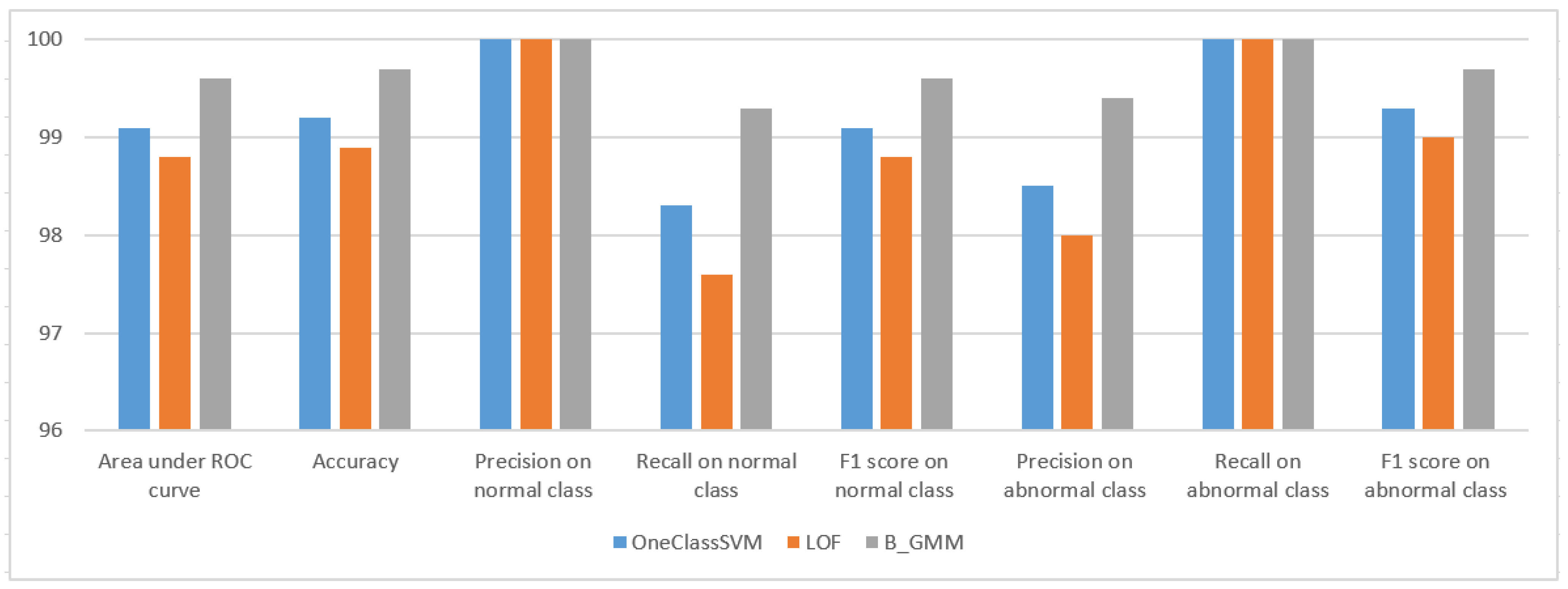
- In addition, as third extension, we developed the three best performing novelty detection algorithms (i.e., OneClassSVM, LOF, and B_GMM), integrated them into the risk-based adaptive user authentication mechanism, and evaluated their detection performance. The evaluation results demonstrated that B_GMM surpasses the others (i.e., OneClassSVM, LOF) in performance when deployed on the Raspberry Pi 4 device.
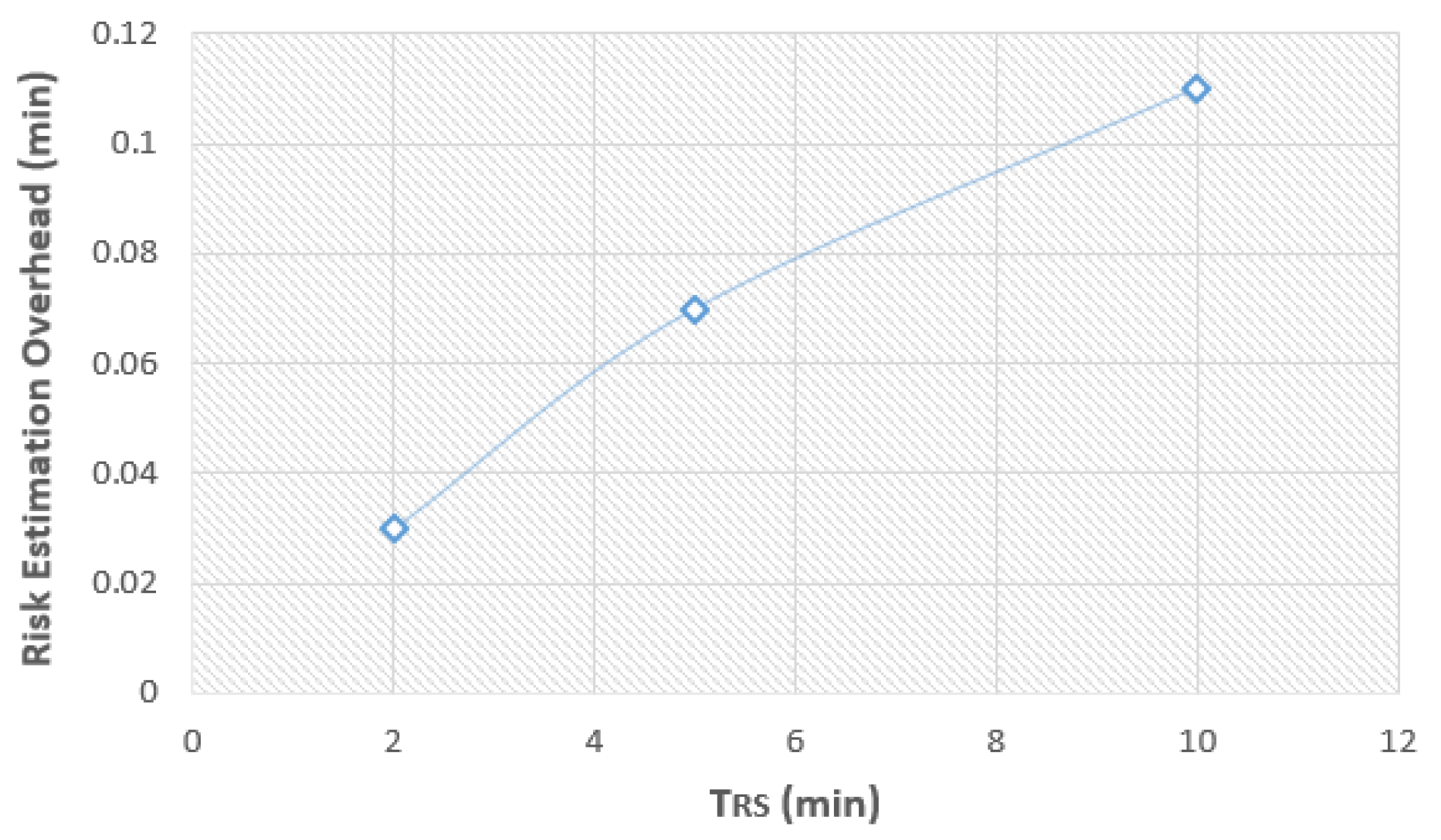
- Finally, as a fourth extension of our previous works, we evaluated the risk estimation overhead of the developed mechanism, when the best performing B_GMM novelty detection algorithm was used for risk estimation, indicating efficient operation with minimal additional latency.
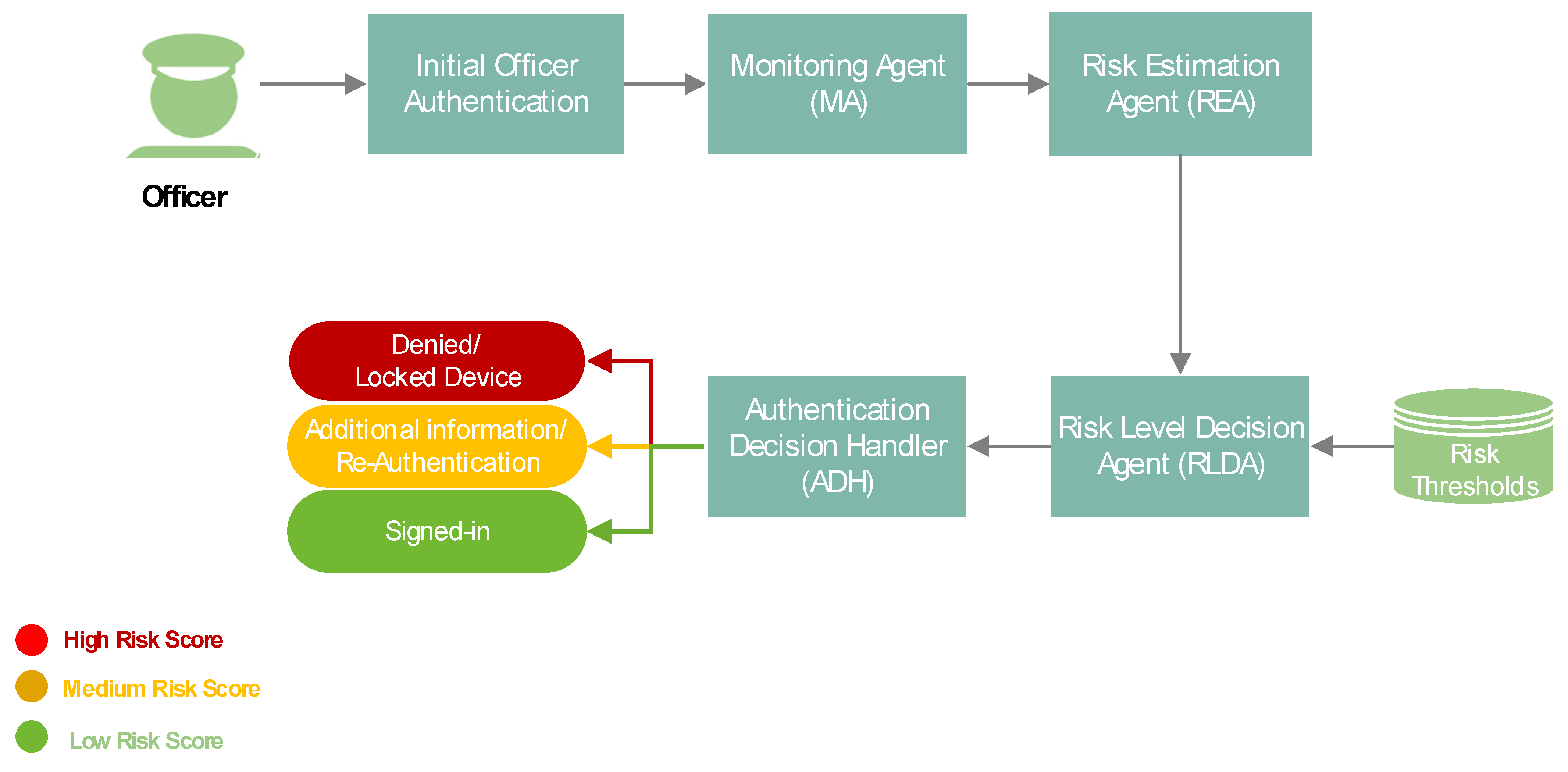
2. Overview of the Proposed Risk-Based Adaptive User Authentication Mechanism
2.1. Mechanism Components
2.1.1. Initial Officer Authentication
2.1.2. Monitoring Agent (MA)
2.1.3. Risk Estimation Agent (REA)
2.1.4. Risk Level Decision Agent (RLDA)
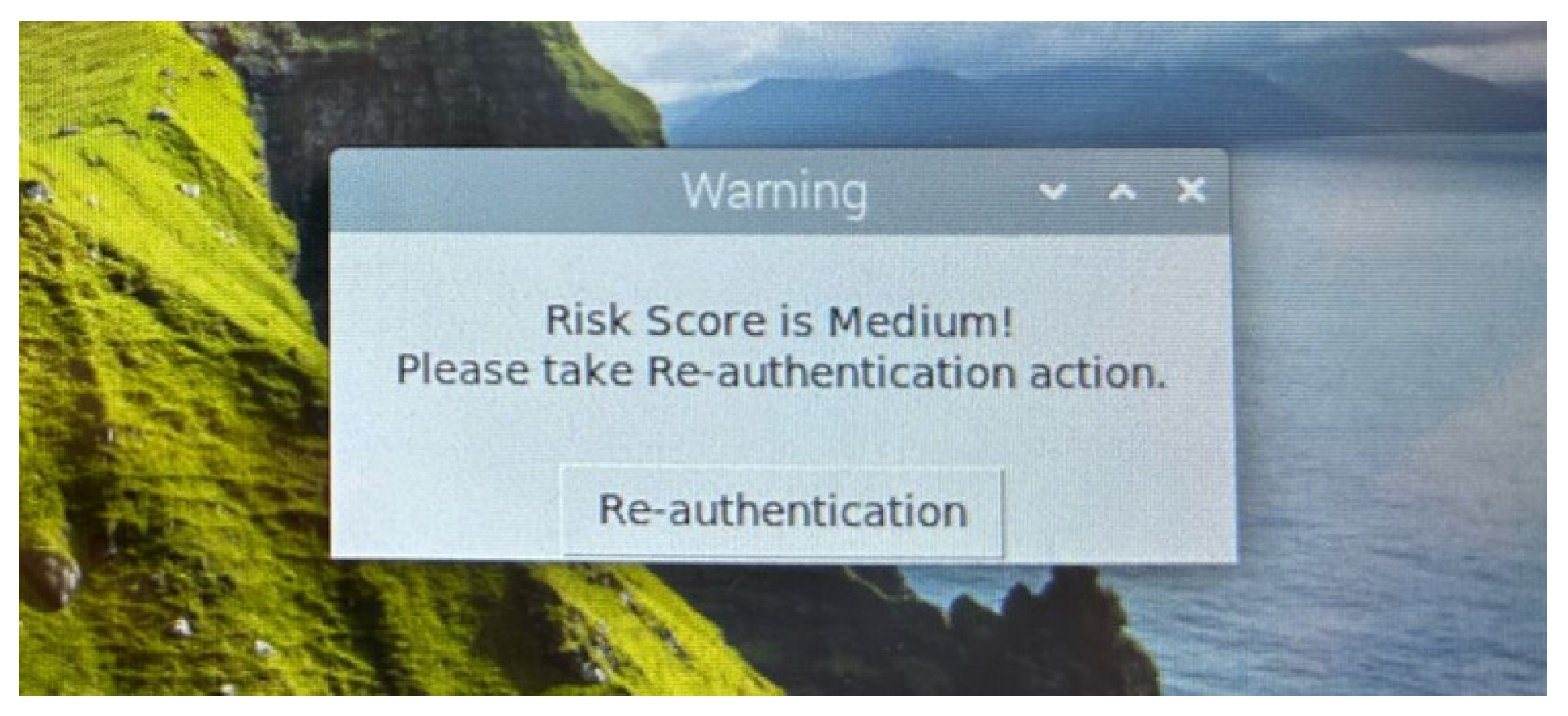
2.1.5. Authentication Decision Handler (ADH)
3. Novelty vs. Outlier Detection for Risk Estimation in the Proposed Mechanism
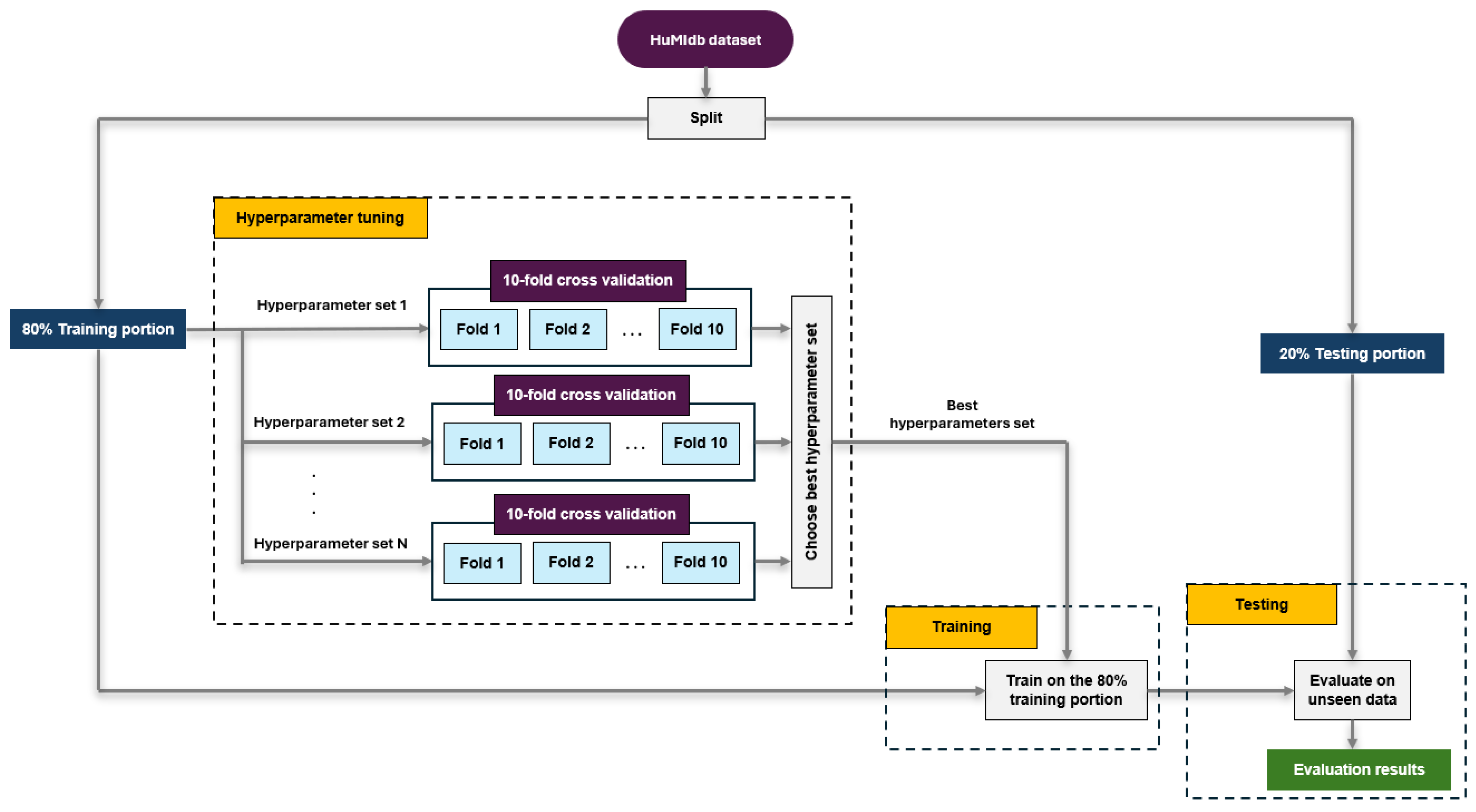
3.1. Data Pre-Processing and Normalization
3.2. Hyperparameter Tuning, Training and Testing Processes
3.3. Detection Algorithms Performance Evaluation
- B_GMM: demonstrates the highest performance with an Area under ROC curve of 99.6 and accuracy of 99.7, alongside perfect scores in other metrics.
- OneClassSVM: exhibits robust performance with high scores in Area under ROC curve (99.1) and accuracy (99.2), as well as excellent precision, recall, and F1 scores.
- LOF: delivers strong results with a slightly lower Area under ROC curve than OneClassSVM (98.8) but maintains high accuracy (98.9) and exceptional precision, recall, and F1 scores.
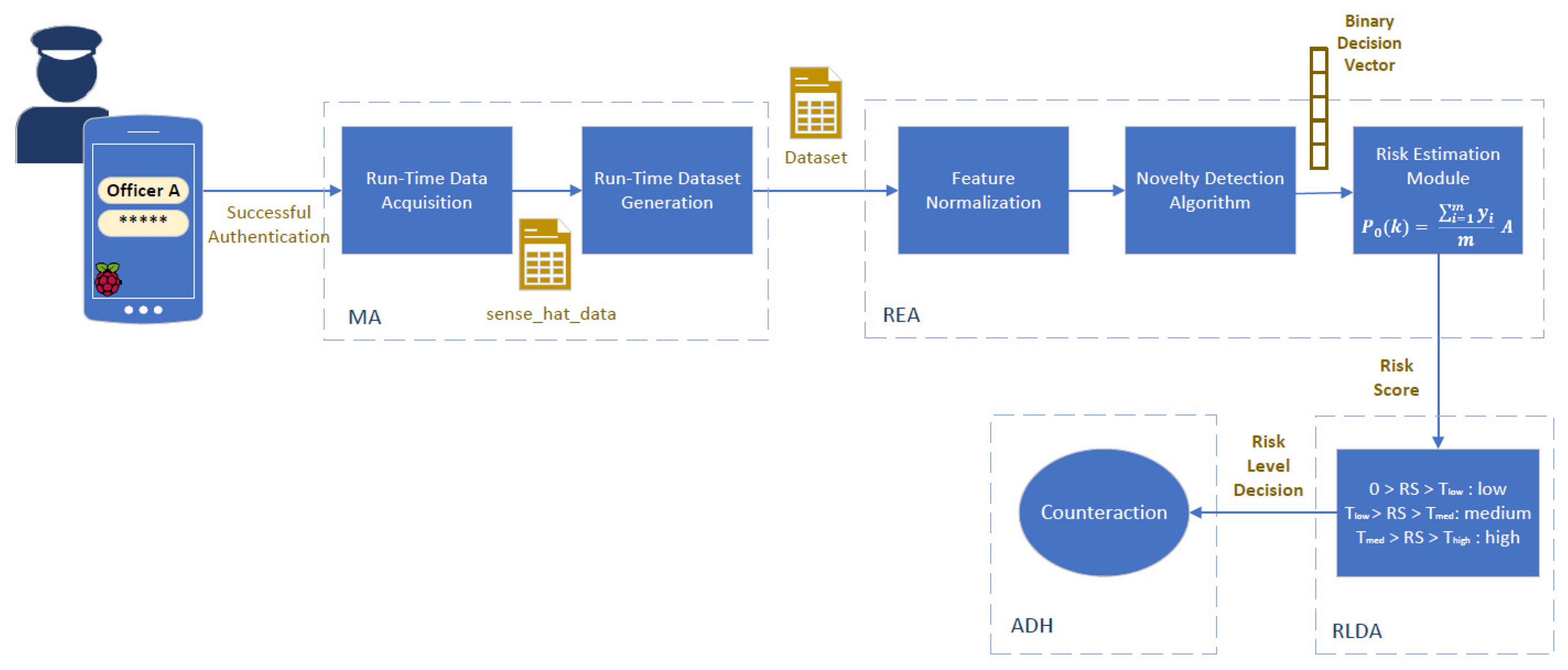
4. Functional Description of the Proposed Risk-Based Adaptive User Authentication Mechanism
- TP (True Positive) represents the count of correctly identified suspicious users.
- TN (True Negative) signifies the count of correctly identified normal users.
- FP (False Positive) indicates the count of normal users incorrectly labeled as suspicious.
- FN (False Negative) represents the count of suspicious users incorrectly labeled as normal.
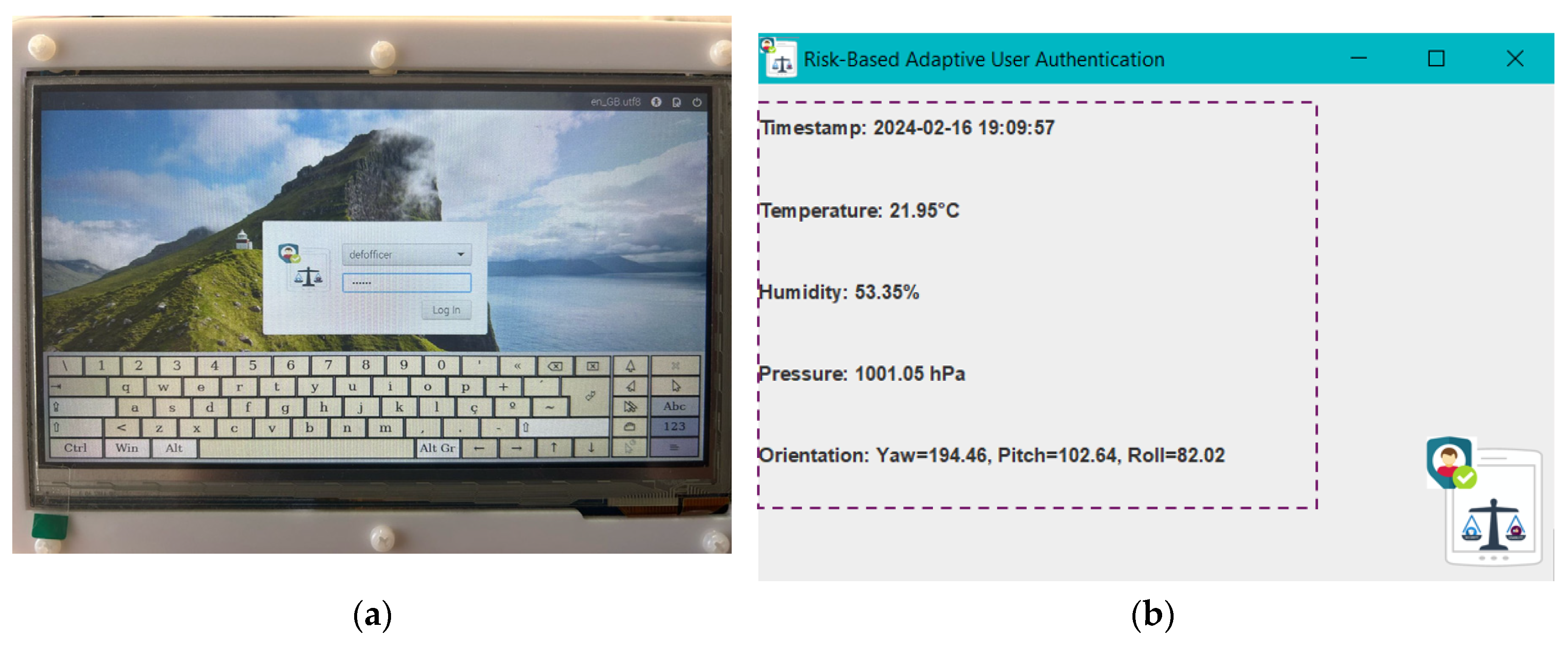
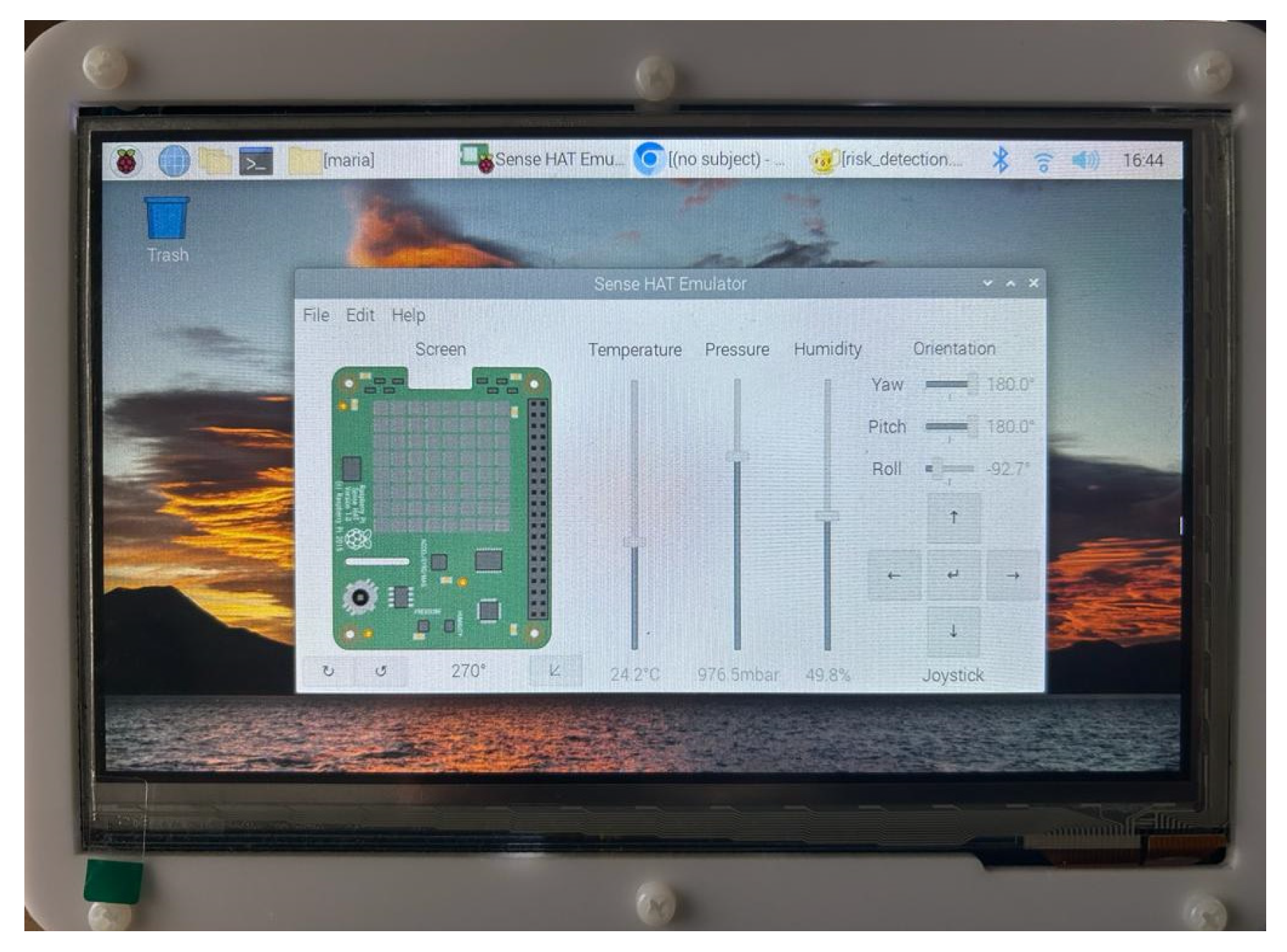
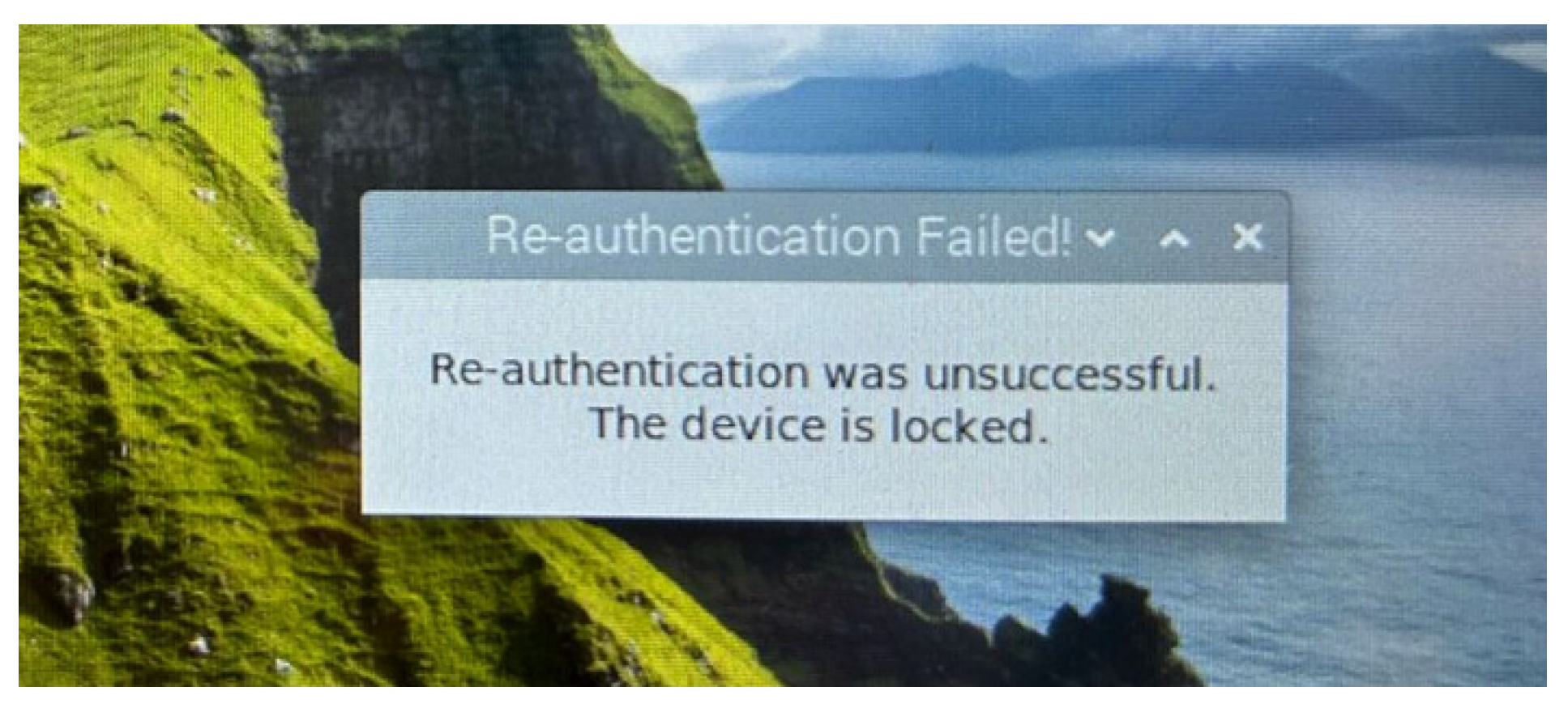
5. Prototype Implementation of the Proposed Risk-Based Adaptive User Authentication Mechanism
Implementation Overview
6. Performance Evaluation
6.1. Experimental Setup
6.2. Detection Performance
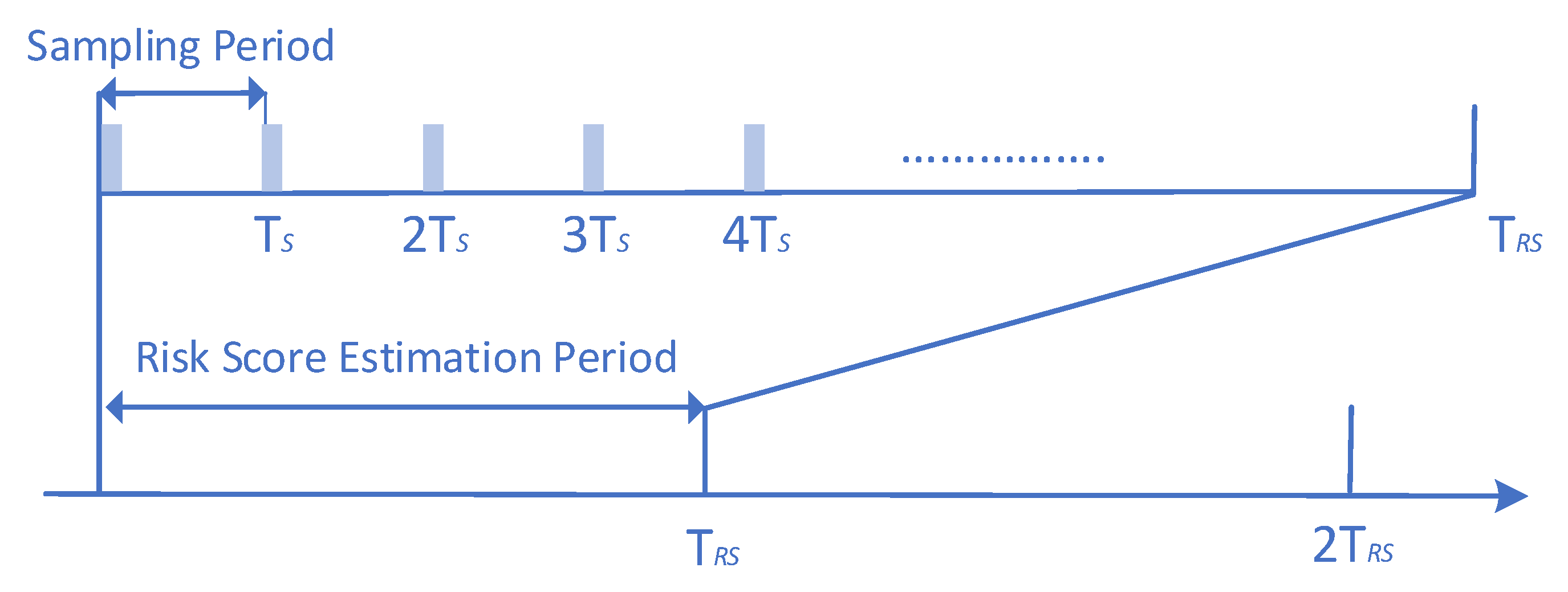
6.3. Risk Estimation Overhead
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Papaioannou, M.; Mantas, G.; Lymberopoulos, D.; Rodriguez, J. User authentication and authorization for next generation mobile passenger ID devices for land and sea border control. In Proceedings of the 12th International Symposium on Communication Systems, Networks and Digital Signal Processing, CSNDSP 2020, Porto, Portugal, 20–22 July 2020; pp. 8–13. [Google Scholar]
- European Commission. Mobility and Transport; European Commission: Brussels, Belgium, 2018; p. 144. [Google Scholar]
- McLaughlin, P. Cross-border data flows and increased enforcement. IEEE Secur. Priv. 2008, 6, 58–61. [Google Scholar] [CrossRef]
- Bustard, J. The impact of EU privacy legislation on biometric system deployment: Protecting citizens but constraining applications. IEEE Signal Process. Mag. 2015, 32, 101–108. [Google Scholar] [CrossRef]
- Papaioannou, M.; Pelekoudas-oikonomou, F.; Mantas, G.; Serrelis, E.; Rodriguez, J.; Fengou, M. A Survey on Quantitative Risk Estimation Approaches for Secure and Usable User Authentication on Smartphones. Sensors 2023, 23, 2979. [Google Scholar] [CrossRef] [PubMed]
- Papaioannou, M.; Zachos, G.; Essop, I.; Mantas, G.; Rodriguez, J. Towards a Secure and Usable User Authentication for Mobile Passenger ID Devices for Land/Sea Border Control. IEEE Access 2022, 10, 38832–38849. [Google Scholar] [CrossRef]
- Choong, Y.-Y.; Franklin, J.M.; Greene, K.K. Usability and Security Considerations for Public Safety Mobile Authentication; Report 8080; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2016. [Google Scholar] [CrossRef]
- Papaioannou, M.; Mantas, G.; Panaousis, E.M.; Essop, A.; Rodriguez, J.; Sucasas, V. Behavioral Biometrics for Mobile User Authentication: Benefits and Limitations. In Proceedings of the 2023 IFIP Networking Conference (IFIP Networking), Barcelona, Spain, 12–15 June 2023. [Google Scholar] [CrossRef]
- Picard, C.; Pierre, S. RLAuth: A Risk-Based Authentication System Using Reinforcement Learning. IEEE Access 2023, 11, 61129–61143. [Google Scholar] [CrossRef]
- Shankar, V.; Singh, K. An Intelligent Scheme for Continuous Authentication of Smartphone Using Deep Auto Encoder and Softmax Regression Model Easy for User Brain. IEEE Access 2019, 7, 48645–48654. [Google Scholar] [CrossRef]
- Di Nocera, F.; Tempestini, G.; Orsini, M. Usable Security: A Systematic Literature Review. Information 2023, 14, 641. [Google Scholar] [CrossRef]
- Baig, A.F.; Eskeland, S. Security, privacy, and usability in continuous authentication: A survey. Sensors 2021, 21, 5967. [Google Scholar] [CrossRef] [PubMed]
- Johnston, J.; Eloff, J.H.P.; Labuschagne, L. Security and human computer interfaces. Comput. Secur. 2003, 22, 675–684. [Google Scholar] [CrossRef]
- Theofanos, M. Is Usable Security an Oxymoron? Computer 2020, 53, 71–74. [Google Scholar] [CrossRef]
- Gupta, S.; Buriro, A.; Crispo, B. Demystifying authentication concepts in smartphones: Ways and types to secure access. Mob. Inf. Syst. 2018, 2018, 2649598. [Google Scholar] [CrossRef]
- ClearLogin Risk-Based Authentication. 2017. Available online: http://www.clearlogin.com/glossary/risk-based-authentication/ (accessed on 10 March 2024).
- Wiefling, S.; Jørgensen, P.R.; Thunem, S.; Iacono, L. Lo Pump Up Password Security! Evaluating and Enhancing Risk-Based Authentication on a Real-World Large-Scale Online Service. ACM Trans. Priv. Secur. 2022, 1, 1–35. [Google Scholar] [CrossRef]
- Wiefling, S.; Dürmuth, M.; Lo Iacono, L. What’s in Score for Website Users: A Data-Driven Long-Term Study on Risk-Based Authentication Characteristics. In Financial Cryptography and Data Security: 25th International Conference, FC 2021, Virtual Event, 1–5 March 2021; Springer: Berlin/Heidelberg, Germany, 2021; Volume 12675 LNCS, pp. 361–381. [Google Scholar] [CrossRef]
- Jansen, W.A.; Winograd, T.; Scarfone, K. Guidelines on Active Content and Mobile Code. Available online: https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-28ver2.pdf (accessed on 12 March 2024).
- Hubbard, D.W.; Seiersen, R. How to Measure Anything in Cybersecurity Risk; Wiley: Hoboken, NJ, USA, 2016; ISBN 978-1-119-22460-0. [Google Scholar]
- Ghazouani, M.; Faris, S.; Medromi, H.; Sayouti, A. Information Security Risk Assessment A Practical Approach with a Mathematical Formulation of Risk. Int. J. Comput. Appl. 2014, 103, 36–42. [Google Scholar] [CrossRef]
- Quinn, S.; Ivy, N.; Barrett, M.; Witte, G.; Gardner, R.K. Identifying and Estimating Cybersecurity Risk for Enterprise Risk Management; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2021; pp. 1–52. [Google Scholar]
- Lamb, P.; Millar, A.; Fuentes, R. Swipe dynamics as a means of authentication: Results from a bayesian unsupervised approach. In Proceedings of the 2020 IEEE International Joint Conference on Biometrics (IJCB), Houston, TX, USA, 28 September–1 October 2020. [Google Scholar] [CrossRef]
- Rzecki, K.; Baran, M. Application of Elastic Shape Analysis to User Authentication and Identification. IEEE Trans. Emerg. Top. Comput. 2022, 10, 1157–1165. [Google Scholar] [CrossRef]
- Cheung, W.; Vhaduri, S. Continuous Authentication of Wearable Device Users from Heart Rate, Gait, and Breathing Data. In Proceedings of the 2020 8th IEEE RAS/EMBS International Conference for Biomedical Robotics and Biomechatronics (BioRob), New York, NY, USA, 29 November–1 December 2020; pp. 587–592. [Google Scholar] [CrossRef]
- Papaioannou, M.; Zachos, G.; Mantas, G.; Rodriguez, J. Novelty Detection for Risk-based User Authentication on Mobile Devices. In Proceedings of the 2022 IEEE Global Communications Conference, GLOBECOM 2022-Proceedings, Rio de Janeiro, Brazil, 4–8 December 2022; IEEE: Piscateville, NJ, USA, 2022; pp. 837–842. [Google Scholar]
- Papaioannou, M.; Zachos, G.; Mantas, G.; Essop, I.; Saghezchi, F.; Rodriguez, J. Outlier Detection for Risk-based User Authentication on Mobile Devices. In Proceedings of the 2023 IEEE Global Communications Conference, GLOBECOM 2023-Proceedings, Kuala Lumpur, Malaysia, 4–8 December 2023; pp. 2778–2783. [Google Scholar]
- Acien, A.; Morales, A.; Fierrez, J.; Vera-Rodriguez, R.; Delgado-Mohatar, O. BeCAPTCHA: Bot detection in smartphone interaction using touchscreen biometrics and mobile sensors. arXiv 2020, arXiv:2005.13655. [Google Scholar]
- Acien, A.; Morales, A.; Fierrez, J.; Vera-Rodriguez, R.; Bartolome, I. BeCAPTCHA: Detecting human behavior in smartphone interaction using multiple inbuilt sensors. arXiv 2020, arXiv:2002.00918. [Google Scholar]
- Hu, M.; Zhang, K.; You, R.; Tu, B. Multisensor-Based Continuous Authentication of Smartphone Users With Two-Stage Feature Extraction. IEEE Internet Things J. 2023, 10, 4708–4724. [Google Scholar] [CrossRef]
- Shen, Z.; Li, S.; Zhao, X.; Zou, J. MMAuth: A Continuous Authentication Framework on Smartphones Using Multiple Modalities. IEEE Trans. Inf. Forensics Secur. 2022, 17, 1450–1465. [Google Scholar] [CrossRef]
- Kim, J.; Kim, H.; Kang, P. Keystroke dynamics-based user authentication using freely typed text based on user-adaptive feature extraction and novelty detection. Appl. Soft Comput. J. 2018, 62, 1077–1087. [Google Scholar] [CrossRef]
- Qiu, X.; Jiang, T.; Wu, S.; Jiang, C.; Yao, H.; Hayes, M.H.; Benslimane, A. Wireless User Authentication Based on KLT and Gaussian Mixture Model. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Gupta, S.; Kumar, R.; Kacimi, M.; Crispo, B. IDeAuth: A novel behavioral biometric-based implicit deauthentication scheme for smartphones. Pattern Recognit. Lett. 2022, 157, 8–15. [Google Scholar] [CrossRef]
- Kumar, R.; Kundu, P.P.; Phoha, V.V. Continuous authentication using one-class classifiers and their fusion. In Proceedings of the 2018 IEEE 4th International Conference on Identity, Security, and Behavior Analysis (ISBA), Singapore, 11–12 January 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Antal, M.; Szabó, L.Z. Biometric Authentication Based on Touchscreen Swipe Patterns. Procedia Technol. 2016, 22, 862–869. [Google Scholar] [CrossRef]
- Antal, M.; Szabo, L.Z. An evaluation of one-class and two-class classification algorithms for keystroke dynamics authentication on mobile devices. In Proceedings of the 2015 20th International Conference on Control Systems and Computer Science, Bucharest, Romania, 27–29 May 2015; pp. 343–350. [Google Scholar] [CrossRef]
- Shen, C.; Cai, Z.; Guan, X.; Du, Y.; Maxion, R.A. User authentication through mouse dynamics. IEEE Trans. Inf. Forensics Secur. 2013, 8, 16–30. [Google Scholar] [CrossRef]
- Scikit-Learn Developers Novelty and Outlier Detection. Available online: https://scikit-learn.org/stable/modules/outlier_detection.html (accessed on 4 July 2024).
- Wu, C.; He, K.; Chen, J.; Du, R.; Xiang, Y. CaIAuth: Context-Aware Implicit Authentication When the Screen Is Awake. IEEE Internet Things J. 2020, 7, 11420–11430. [Google Scholar] [CrossRef]
- Papaioannou, M.; Zachos, G.; Mantas, G.; Essop, A.; Karasuwa, A.; Rodriguez, J. Generating Datasets Based on the HuMIdb Dataset for Risk-based User Authentication on Smartphones. In Proceedings of the 2022 IEEE 27th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Paris, France, 2–3 November 2022; pp. 134–139. [Google Scholar] [CrossRef]
- Lantz, B. Machine Learning with R: Learn Techniques for Building and Improving Machine Learning Models, from Data Preparation to Model Tuning, Evaluation, and Working with Big Data; Packt Publishing: Birmingham, UK, 2023. [Google Scholar]
- Friedman, L.; Komogortsev, O.V. Assessment of the Effectiveness of Seven Biometric Feature Normalization Techniques. IEEE Trans. Inf. Forensics Secur. 2019, 14, 2528–2536. [Google Scholar] [CrossRef]
- Kabir, W.; Ahmad, M.O.; Swamy, M.N.S. Normalization and weighting techniques based on genuine-impostor score fusion in multi-biometric systems. IEEE Trans. Inf. Forensics Secur. 2018, 13, 1989–2000. [Google Scholar] [CrossRef]
- Géron, A. Hands-on Machine Learning with Scikit-Learn, Keras, and TensorFlow: Concepts, Tools, and Techniques to Build Intelligent Systems; O’Reilly Media: Sevastopol, CA, USA, 2019. [Google Scholar]
- Géron, A. Hands-on Machine Learning with Scikit-Learn and TensorFlow; O’Reilly Media: Sevastopol, CA, USA, 2017; ISBN 9781491962299. [Google Scholar]
- Papaioannou, M.; Mantas, G.; Essop, A.; Sucasas, V.; Aaraj, N.; Rodriguez, J. Risk Estimation for a Secure & Usable User Authentication Mechanism for Mobile Passenger ID Devices. In Proceedings of the 2022 IEEE 27th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Paris, France, 2–3 November 2022; IEEE: Piscateville, NJ, USA, 2022; pp. 173–178. [Google Scholar]
- Ribeiro, J.; Saghezchi, F.B.; Mantas, G.; Rodriguez, J.; Abd-Alhameed, R.A. HIDROID: Prototyping a behavioral host-based intrusion detection and prevention system for android. IEEE Access 2020, 8, 23154–23168. [Google Scholar] [CrossRef]
- Ribeiro, J.; Saghezchi, F.B.; Mantas, G.; Rodriguez, J.; Shepherd, S.J.; Abd-Alhameed, R.A. An Autonomous Host-Based Intrusion Detection System for Android Mobile Devices. Mob. Netw. Appl. 2020, 25, 164–172. [Google Scholar] [CrossRef]
- Borges, P.; Sousa, B.; Ferreira, L.; Saghezchi, F.; Mantas, G.; Ribeiro, J.; Rodriguez, J.; Cordeiro, L.; Simoes, P. Towards a Hybrid Intrusion Detection System for Android-based PPDR Terminals. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM): Workshop on Security for Emerging Distributed Network Technologies (DISSECT 2017), Lisbon, Portugal, 8–12 May 2017; pp. 1034–1039. [Google Scholar]
- Raspberry Pi Ltd. Raspberry Pi Documentation-Sense HAT. Available online: https://www.raspberrypi.com/documentation/accessories/sense-hat.html (accessed on 4 July 2024).
- Shin, M.; Cornelius, C.; Peebles, D.; Kapadia, A.; Kotz, D.; Triandopoulos, N. AnonySense: A system for anonymous opportunistic sensing. Pervasive Mob. Comput. 2011, 7, 16–30. [Google Scholar] [CrossRef]
- Ra, M.R.; Liu, B.; La Porta, T.F.; Govindan, R. Medusa: A programming framework for crowd-sensing applications. In Proceedings of the 10th International Conference on Mobile Systems, Applications, and Service, Ambleside, UK, 25–29 June 2012; pp. 337–350. [Google Scholar] [CrossRef]
- De Cristofaro, E.; Soriente, C. Extended capabilities for a privacy-enhanced participatory sensing infrastructure (PEPSI). IEEE Trans. Inf. Forensics Secur. 2013, 8, 2021–2033. [Google Scholar] [CrossRef]


| Algorithm | Best Hyperparameters | |
|---|---|---|
| Novelty Detection | OneClassSVM | nu = 0.01, gamma = 0.07, kernel = rbf |
| LOF | algorithm = kd_tree, contamination = auto, metric = chebyshev, n_neighbors = 20, novelty = True | |
| KNN_nov_det | algorithm = ball_tree, contamination = 0.00001, method = largest, metric = chebyshev, n_neighbors = 5 | |
| DeepSVDD | contamination = 0.00001, hidden_neurons = [8,4] | |
| G_KDE | bandwidth = 0.1, kernel = gaussian, metric = chebyshev | |
| PW_KDE | bandwidth = 0.4, kernel = tophat, metric = chebyshev | |
| B_GMM | components = 4, covariance = full | |
| Outlier Detection | IsoForest | behaviour = new, contamination = 0.1, n_estimators = 90 |
| MCD | contamination = 0.1, assume_centered = false | |
| AutoEncoder | contamination = 0.1, hidden_neurons = [16,8,8,16] | |
| KNN_out_det | algorithm = ball_tree, contamination = 0.1, method = median, metric = manhattan, n_neighbors = 20 |
| Algorithm | Area under ROC Curve | Accuracy | Precision on Normal Class | Recall on Normal Class | F1 Score on Normal Class | Precision on Abnormal Class | Recall on Abnormal Class | F1 Score on Abnormal Class | |
|---|---|---|---|---|---|---|---|---|---|
| Novelty Detection | OneClassSVM | 99.14 | 99.20 | 100 | 98.28 | 99.13 | 98.53 | 100 | 99.26 |
| LOF | 98.78 | 98.87 | 100 | 97.56 | 98.77 | 97.93 | 100 | 98.96 | |
| KNN_nov_det | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | |
| DeepSVDD | 97.86 | 97.87 | 100 | 97.71 | 97.86 | 97.75 | 100 | 97.88 | |
| G_KDE | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | |
| PW_KDE | 100 | 100 | 100 | 100 | 100 | 100 | 100 | 100 | |
| B_GMM | 99.64 | 99.67 | 100 | 99.28 | 99.64 | 99.38 | 100 | 99.70 | |
| Outlier Detection | IsoForest | 61.33 | 59.08 | 53.4 | 92.40 | 67.68 | 82.16 | 30.27 | 44.24 |
| MCD | 88.58 | 87.89 | 80.19 | 98.14 | 88.26 | 98 | 79.03 | 87.5 | |
| AutoEncoder | 55.37 | 52.83 | 49.53 | 90.39 | 63.99 | 71.00 | 20.35 | 31.63 | |
| KNN_out_det | 66.14 | 68.13 | 83.85 | 38.74 | 52.99 | 63.84 | 93.55 | 75.89 |
| Algorithm | Hyperparameters |
|---|---|
| OneClassSVM | nu = 0.01, gamma = 0.07, kernel = rbf |
| LOF | algorithm = kd_tree, contamination = auto, metric = chebyshev, n_neighbors = 20, novelty = True |
| B_GMM | components = 4, covariance = full |
| Algorithm | Area under ROC Curve | Accuracy | Precision on Normal Class | Recall on Normal Class | F1 Score on Normal Class | Precision on Abnormal Class | Recall on Abnormal Class | F1 Score on Abnormal Class |
|---|---|---|---|---|---|---|---|---|
| OneClassSVM | 99.2 | 99.2 | 100 | 98.3 | 99.1 | 98.6 | 100 | 99.4 |
| LOF | 98.8 | 98.9 | 100 | 97.6 | 98.8 | 98 | 100 | 99 |
| B_GMM | 99.8 | 99.7 | 100 | 99.3 | 99.6 | 99.5 | 100 | 99.7 |
| TRS (min) | Risk Estimation Overhead (min) | Risk Estimation Overhead (sec) |
|---|---|---|
| 2 | 0.03 | 1.8 |
| 5 | 0.07 | 4.2 |
| 10 | 0.11 | 6.6 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Papaioannou, M.; Zachos, G.; Mantas, G.; Panaousis, E.; Rodriguez, J. Prototyping a Secure and Usable User Authentication Mechanism for Mobile Passenger ID Devices for Land/Sea Border Control. Sensors 2024, 24, 5193. https://doi.org/10.3390/s24165193
Papaioannou M, Zachos G, Mantas G, Panaousis E, Rodriguez J. Prototyping a Secure and Usable User Authentication Mechanism for Mobile Passenger ID Devices for Land/Sea Border Control. Sensors. 2024; 24(16):5193. https://doi.org/10.3390/s24165193
Chicago/Turabian StylePapaioannou, Maria, Georgios Zachos, Georgios Mantas, Emmanouil Panaousis, and Jonathan Rodriguez. 2024. "Prototyping a Secure and Usable User Authentication Mechanism for Mobile Passenger ID Devices for Land/Sea Border Control" Sensors 24, no. 16: 5193. https://doi.org/10.3390/s24165193
APA StylePapaioannou, M., Zachos, G., Mantas, G., Panaousis, E., & Rodriguez, J. (2024). Prototyping a Secure and Usable User Authentication Mechanism for Mobile Passenger ID Devices for Land/Sea Border Control. Sensors, 24(16), 5193. https://doi.org/10.3390/s24165193








