The Intersection of Machine Learning and Wireless Sensor Network Security for Cyber-Attack Detection: A Detailed Analysis
Abstract
:1. Introduction
- Conventional sensors are frequently limited to places far from the direct source of the phenomenon they aim to detect, relying on complicated procedures to separate the intended signal from the cacophony of ambient noise that surrounds it. To accomplish its discerning purpose, this strategy needs the deployment of considerably bigger sensors endowed with complicated signal processing capabilities.
- An alternate technique is the deployment of many sensors that are primarily concerned with perceiving the physical environment but lack comprehensive signal processing capabilities. To arrange both the physical location of these sensors and the extensive web of communication topologies that connects them in this situation, rigorous engineering is necessary. This complex interplay culminates in the transfer of time series data containing detected events to central nodes, where computational alchemy occurs and data fusion transforms raw data into useful insights. This contrast between the old sensor paradigm and the transformational sensor network ethos emphasises the latter’s seismic shift in strategy and technical innovation.
Research Gap
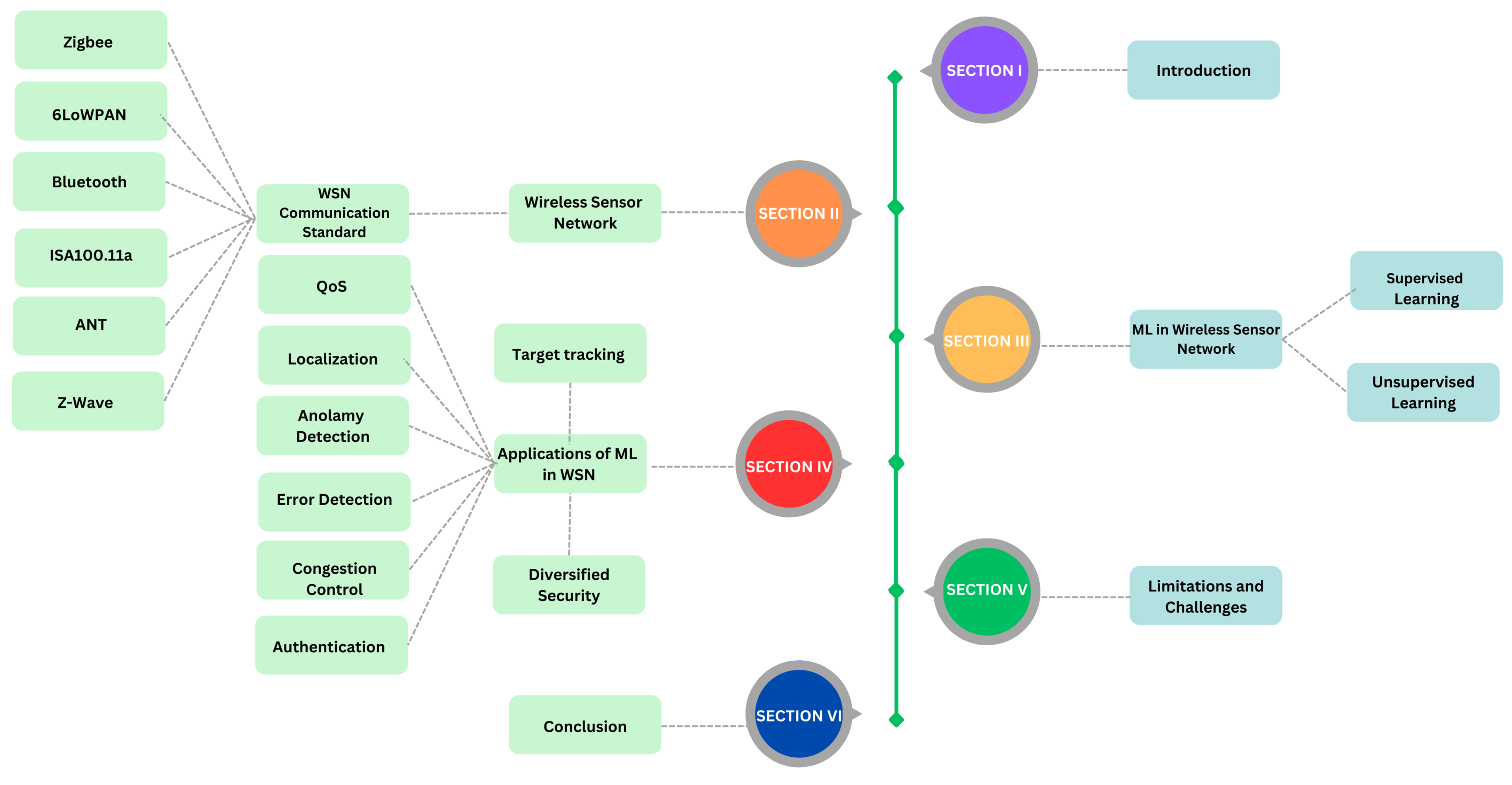
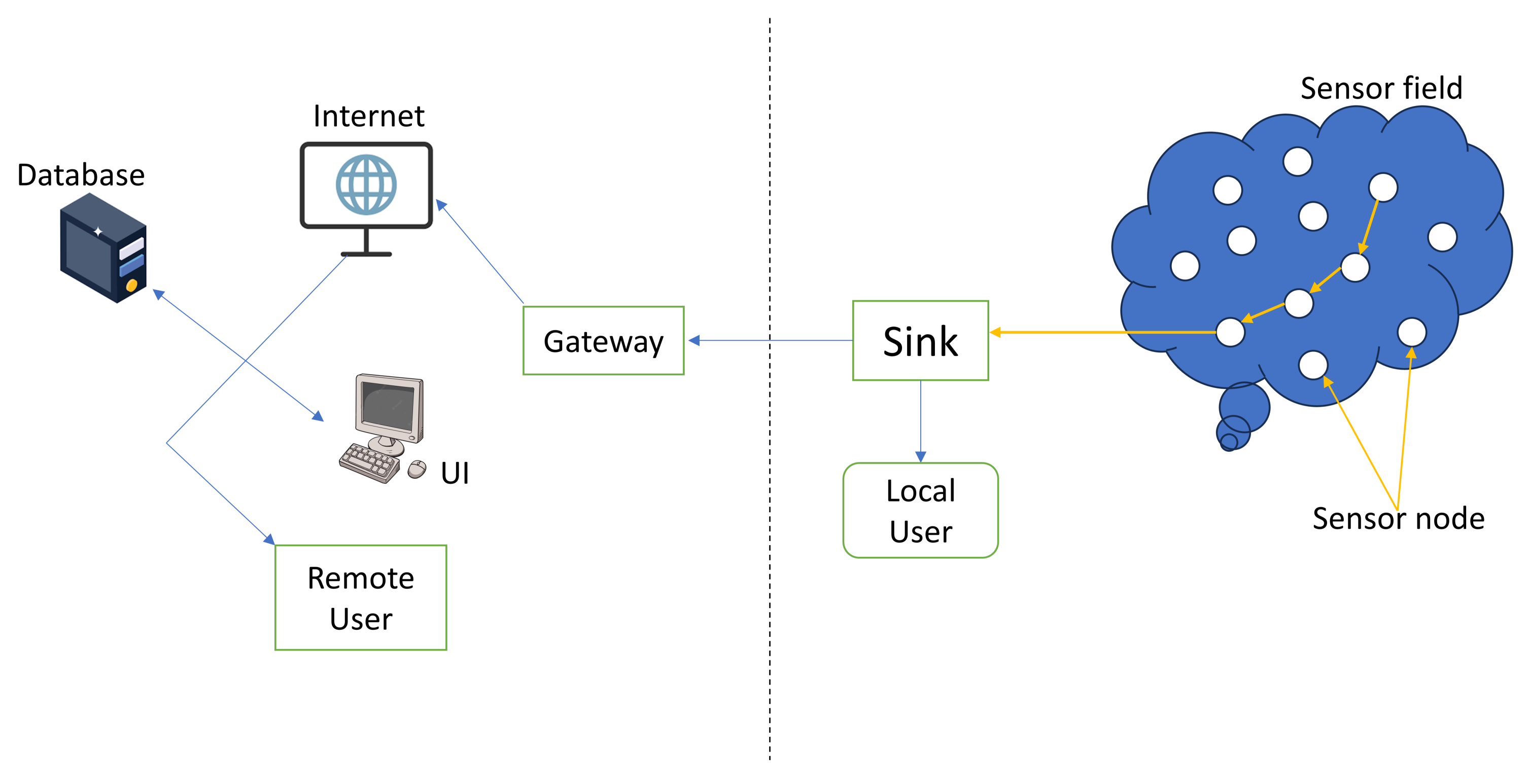
2. Wireless Sensor Networks
- Decentralisation: WSN nodes function autonomously without the governance of a central controller.
- Stationarity and mobility: These nodes can operate as either stationary fixtures or mobile entities, bringing dynamism to the network’s composition.
- Restricted transmission range: The propagation distance of WSN nodes is intrinsically restricted, which contributes to the complicated structure of their communication.
- Dynamic network topology: The network topology of the WSN is constantly changing, necessitating adaptive communication solutions.
- Multi-hop connectivity: Data transmission frequently involves multiple-hop connections, adding to the complexity of network communication.
- Bandwidth limitations: As bandwidth resources are limited, careful data management and transmission are required.
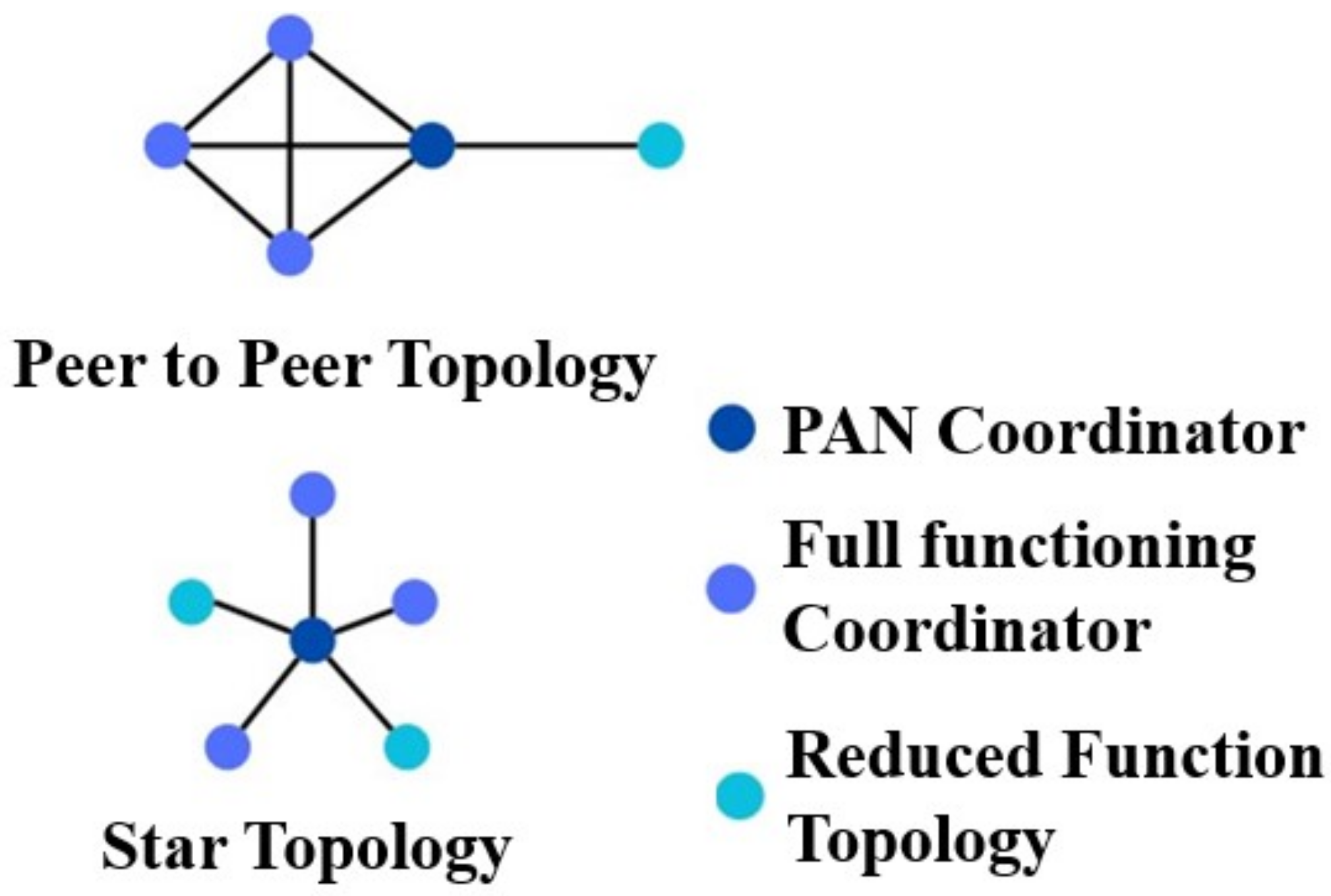
2.1. WSNs Communication Standard
2.1.1. ZigBee
2.1.2. 6LoWPAN
2.1.3. Bluetooth
2.1.4. ISA100.11a
2.1.5. ANT
2.1.6. Z-Wave
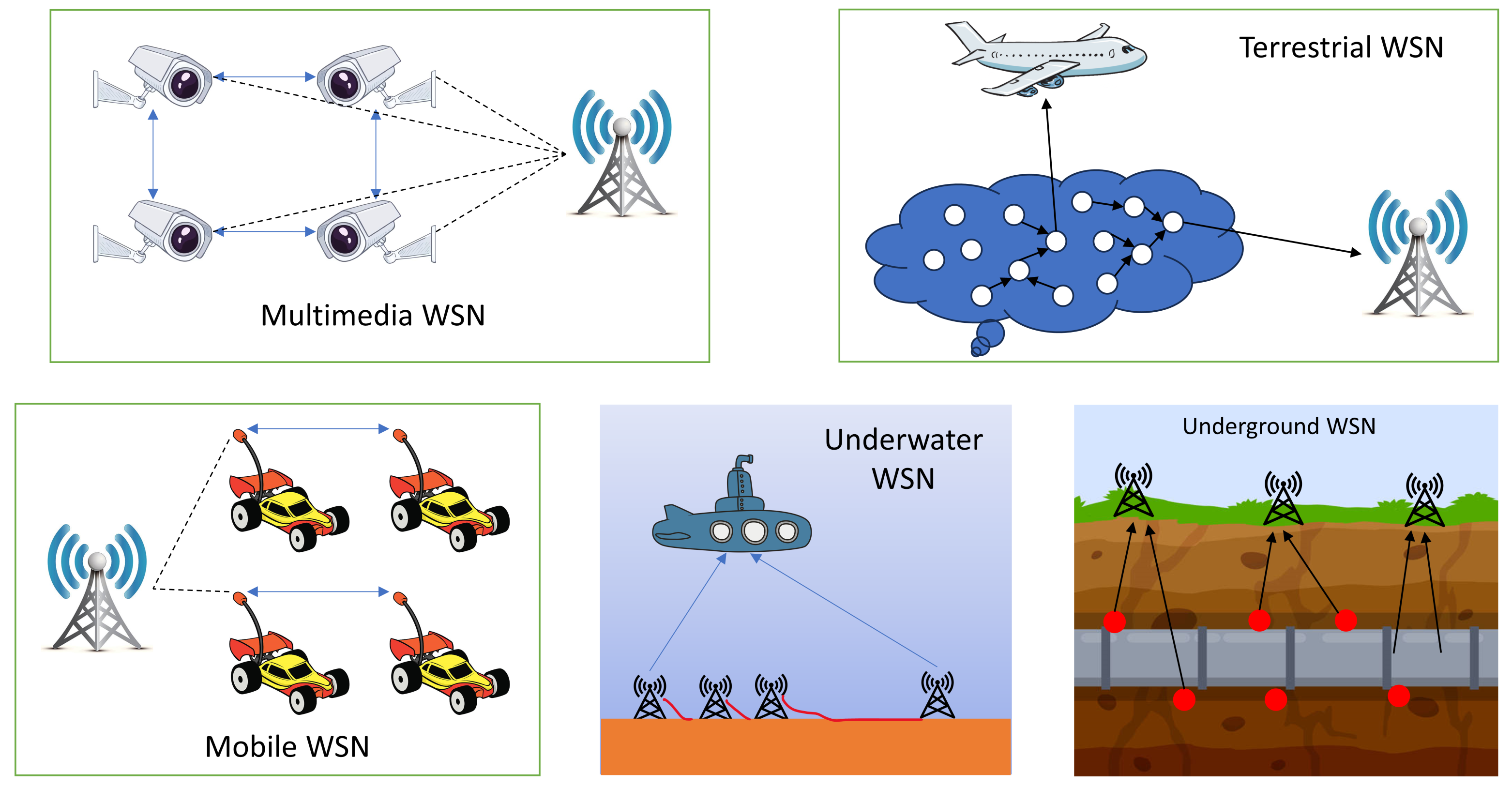
2.2. Types of WSNs
- Terrestrial WSNs are systems of dozens to thousands of inexpensive nodes that are placed strategically all over the world’s surface. These nodes are generally deployed haphazardly, using means like aerial drops from aeroplanes. The challenge with terrestrial WSNs [31] is to provide smooth data connection back to the central base station in the midst of a densely populated area.Because of the inherent limitations of finite, non-rechargeable battery power, terrestrial sensor nodes usually include supplemental power sources like solar cells. Effective multihop routing, constrained transmission range, in-network data aggregation, and the utilisation of low-duty-cycle operations all contribute to energy savings. Environmental sensing, industrial monitoring, and terrestrial exploration are just a few of the uses for terrestrial WSNs.
- Underground Wireless Sensor Networks (UGWSNs) are network configurations in which sensor nodes are deliberately placed in underground settings such as caverns, mines, or beneath the Earth’s surface [32]. To help with data transmission from underwater sensor nodes to the top layer, additional sink nodes are positioned above the surface. These networks are often more expensive than terrestrial versions, owing to the need for specialised equipment to provide reliable communication through liquid, stone, and impurities.Given these conditions, signal attenuation and loss make wireless communication problematic. The subterranean placement of nodes makes replenishing or charging their batteries difficult, necessitating the development of energy-efficient Communication Protocols for extended operational life. UGWSNs applications include agricultural monitoring, landscape management, subsurface soil, water, and mineral monitoring, and military border surveillance.
- Underwater Wireless Sensor Networks (UWWSNs) comprise a set of sensors positioned below the water’s surface, notably in marine environments [33]. Only a small number of nodes are installed because of the high node costs, and autonomous submersibles are used for exploration and data collection. Acoustic signals, serving as the fundamental medium for underwater wireless communication, face a variety of challenges, including constrained capacity, extended propagation delays, increased latency, and signal loss issues. To survive in the severe circumstances of the maritime world, these nodes must be capable of self-configuration and adaptation. Energy-efficient underwater interaction and collaboration strategies are essential since underwater nodes have finite, non-rechargeable battery lives. Technologies of UWWSNs include equipment surveillance, disaster prevention and tracking, tracking of seismic activity, underwater robotics, and the monitoring of pollution.
- Multimedia Wireless Sensor Networks (MUWSNs) are made up of low-cost sensor nodes that are armed with a variety of sensors, including cameras and microphones, and are strategically placed in advance to provide complete coverage [34]. Video, audio, and picture data types may all be stored, processed, and retrieved using multimedia sensor devices. They deal with a number of challenges, such as increasing bandwidth needs, greater use of energy, provisioning for Quality of Service (QoS), data processing, and approaches to compression as well as cross-layer design. The transmission methods designed for multimedia WSNs must strike a compromise between meeting high bandwidth needs and consuming little energy, especially when delivering multimedia material such as video streams. Although attaining constant QoS in multimedia WSNs remains difficult owing to changing connection capacity and latency, achieving a certain degree of QoS is critical for dependable content delivery. These networks supplement existing WSN applications, notably in the tracking and monitoring domains.
- Mobile Wireless Sensor Networks (MOWSNs) have sensor nodes that are mobile, allowing them to travel and interact with their actual environment [15]. These mobile nodes may move across the network and self-organise, integrating sensing, computing, and communication capabilities. Mobile WSNs, as opposed to static WSNs that rely on fixed routing, require dynamic routing methods. Mobility poses a variety of challenges, including those related to deployment strategies, managing mobile nodes, real-time positioning, guiding and supervising moving elements, ensuring adequate sensing coverage, consuming less energy while moving, maintaining network connectivity, and optimising data dissemination. Mobile WSNs’ primary uses include environmental monitoring, habitat surveillance, undersea exploration, military reconnaissance, target tracking, and search-and-rescue operations. When compared to static networks, these networks have the ability to provide better coverage and connection.
2.3. Applications of WSNs
2.3.1. Military Applications
- Supervising Allied Personnel, Gear, and Munitions: Military leaders and commanders can oversee the activities of friendly troops, equipment, and ammunition in real time on the battlefield. Small sensors mounted to soldiers, vehicles, and essential supplies continually communicate their status to sink nodes, which send this information to the command. The data can also move up the command structure, where they is combined with data from other units at each level.
- Battlefield Surveillance: Sensor networks cover crucial terrains, approach approaches, and straits quickly and provide attentive observation of opposing forces’ actions. New sensor networks may be quickly established to increase surveillance coverage as operating plans alter.
- Reconnaissance of Opposing Forces and Terrain: Deploying sensor networks in critical terrains allows for the collection of crucial intelligence about opposing troops and the battlefield’s geography in minutes, reducing the chance of enemy interception.
- Targeting: Sensor networks may be linked into intelligent munitions guiding systems to improve precise aiming.
- Battle Damage Assessment: Sensor networks can be carefully put in target locations before or after an assault to capture important data for analysing the level of damage caused.
- Detection and Reconnaissance of Nuclear, Biological, and Chemical (NBC) Attacks: Sensor networks are implemented in friendly regions as warning systems to identify NBC agents in a timely and accurate manner. This prior notice allows for critical reaction time, which reduces casualties. Furthermore, sensor networks may undertake thorough post-attack surveillance, such as nuclear radiations, without exposing reconnaissance crews to potentially dangerous conditions.
2.3.2. Environmental Applications
- Forest Fire Detection: Sensor nodes may be carefully placed across woods to create a dense network. In the case of a fire, these nodes can quickly determine the source, allowing for faster response efforts. This approach’s scalability allows for the deployment of millions of nodes connected through radio frequencies or optical networks. Furthermore, to ensure long-term, unattended functioning, these nodes can contain power scavenging technologies like solar cells.
- Biocomplexity Mapping: Mapping environmental biocomplexity needs sophisticated data integration approaches across several temporal and geographical domains. While aerial and satellite sensors are effective for seeing vast amounts of biodiversity, they lack the granularity needed for studying smaller biodiversity aspects. The placement of wireless sensor nodes on the ground bridges this gap, allowing for thorough studies of small-scale biodiversity. These nodes are Internet-connected, allowing for remote monitoring and management of ambient biocomplexity.
- Flood Detection: To identify and monitor floods, systems like ALERT in the United States use a variety of sensors, involving precipitation, water depth, and meteorological sensors. These sensors provide data to a centralised database system, guaranteeing that flood information is prompt and reliable. Decentralised techniques for communicating with sensor nodes in the field are being investigated in research, allowing for both immediate and delayed queries.
- Advanced Farming Techniques: Sensor networks are critical in precision agriculture because they monitor pesticide levels in drinking water, soil erosion rates, and air pollution levels in real time. These qualities improve agricultural practises’ efficiency and sustainability.
2.3.3. Healthcare Applications
- Assistive Interfaces: Sensor networks play an important role in developing interfaces for people with impairments. These interfaces increase the accessibility and quality of life for impaired people.
- Integrated Patient Monitoring: They are critical components of complete patient monitoring, providing healthcare personnel with real-time access to key patient data such as physiological parameters and vital signs.
- Diagnostics: Sensor networks aid in diagnostic procedures by gathering and analysing data that are critical for illness detection and monitoring. This assists in the discovery and treatment of medical disorders at an early stage.
- Hospital Drug Administration: Sensor networks provide a barrier against drug mistakes in hospital settings. They assist in matching patients with the proper prescriptions by tagging pharmaceuticals with sensor nodes, lowering the likelihood of adverse drug effects.
- Insect and Small Animal Studies: These networks’ scope includes the study of insect and small animal behaviour and physiology. Sensor nodes contribute to scientific studies by allowing for the tracking of these organisms’ motions and internal functions.
- Telemonitoring of Human Physiology: Sensor networks allow for the telemonitoring of human physiological data, which may be retained for extended periods of time and used for medical research. They can also identify and inform healthcare practitioners of major incidents, such as falls among the elderly.
- Tracking and Monitoring Within Hospitals: Sensor nodes linked to patients and medical personnel provide exact tracking and monitoring within hospital grounds. Physicians can quickly identify one another, improving teamwork and efficiency.
2.3.4. Home Automation
- Home Automation: Smart sensor nodes and actuators may now be integrated into home appliances such as vacuum cleaners, microwave ovens, refrigerators and Video Cassette Recorders (VCRs) thanks to technological advancements. These integrated sensor nodes enable smooth communication inside devices as well as with external networks through the Internet or satellite connections. This interconnection enables users to manage and control their home gadgets effortlessly, whether they are on-site or remotely [40].
- Smart Environments: Human-focused and technology-centric approaches can be employed to approach the idea of intelligent settings. The human-centred approach focuses on adapting the environment to its residents’ individual requirements and preferences, enabling intuitive input and output capabilities. To construct intelligent environments, the technology-centred viewpoint requires the development of cutting-edge hardware technologies, networking solutions, and middleware services [41].
2.3.5. Commercial Applications
- Monitoring Material Fatigue: Sensor networks are critical in monitoring material wear and tear and guaranteeing the prompt replacement or repair of fatigue-prone components.
- Virtual Keyboards: Sensor networks are used to build innovative virtual keyboards that provide users with intuitive and responsive input techniques.
- Inventory Management: Sensor-enabled inventory management systems help businesses optimise stock levels and streamline operations by enabling real-time tracking.
- Product Quality Monitoring: By continually monitoring product quality parameters during production operations, sensor networks guarantee stringent quality control.
- Smart Office Spaces: Sensor networks govern ambient variables to increase comfort and efficiency in offices, transforming them into intelligent workspaces.
- Robot Control in Manufacturing: In automated production environments, sensor networks guide and control robots, improving precision and productivity.
- Interactive Toys and Museums: Sensor networks are used by interactive toys and museums to engage people with responsive items, enabling learning and amusement.
- Factory Process Control: Sensor networks are used in industries for real-time process control and automation, guaranteeing efficient and error-free manufacturing.
- Disaster Area Monitoring: In disaster-stricken areas, sensor networks are used to monitor conditions, aid in rescue attempts, and send important data to responders.
- Smart Structures: Sensor nodes are embedded in building infrastructure, allowing for the continuous monitoring of structural health and safety.
- Machine Diagnosis: Sensor networks aid in the detection and diagnosis of equipment problems, hence avoiding costly breakdowns.
- Transportation Solutions: In transportation, sensor networks are used to track and optimise vehicle movements and logistics.
- Vehicle Theft Detection: Sensor nodes are strategically placed throughout a geographic region to detect and identify hazards, instantly reporting instances for study.
- Inventory Control: Sensor nodes may be installed in each warehouse item, allowing for exact tracking and inventory control while minimising mistakes and increasing efficiency.
- Vehicle Tracking: For vehicle tracking, sensor networks provide two options: local determination of vehicle bearing inside clusters and data forwarding to a base station for exact vehicle location determination.
3. Machine Learning in WSNs
3.1. Supervised Learning
- Linear Regression is a fundamental supervised learning method that predicts a value (Y) based on input data (X). It is a reliable and accurate technique that minimises mistakes, making it a popular machine learning approach. The linear regression model [50] can be represented mathematically as Equation (1). It is useful for addressing various issues, including localisation, connection concerns, data aggregation, and energy harvesting.
- Decision Tree (DT): The Decision Tree (DT) is based on the approach of observation-to-value paradigm, in which observations regarding a specific object lead to the assessment of its worth at the tree’s leaves. In the disciplines of statistics, data mining, and machine learning, this technique of predictive modelling is commonly used. Similar to classification trees, decision trees are built using variables that have a set of values and contain leaves that reflect several categories that are represented by branches. Notably, regression trees, a version used for regression analysis, accommodate numeric variables with real values. When dealing with data-driven decision-making, decision trees come to the fore and are useful in data management activities. They are relatively simple to understand in comparison to other classification methods, emphasising their usability [28].
- Support Vector Machine (SVM): The Support Vector Machine (SVM) method is a strong supervised machine learning tool that excels at both classification and regression issues. SVM works by assigning a point in an n-dimensional space to each data piece, with attribute values acting as coordinates. SVM creates a hyperplane in this multidimensional space that successfully divides two unique groups [51].
- Artificial Neural Network (ANN): Data classification using a synthetic neural network (ANN) is a powerful method that is inspired by the complexities of human neuron models. ANNs, which are made up of many neurons or functional units, systematically process data to produce exact results. Levels are widely used in these networks, with linked nodes covering many levels, each with a distinct purpose [52]. An ANN has the structure of three fundamental layers, a layer that provides inputs, one or more hidden layers, and one or more output layers. ANNs excel in classifying complex and non-linear datasets, distinguishing them from traditional classification algorithms due to their absence of input constraints.
3.2. Unsupervised Learning
- K-Means Clustering: Uniting Data into Cohesive Clusters The K-means clustering technique is a key component of unsupervised learning. It is an efficient approach for clustering nearby data points into clusters. This method avoids the creation of learning models. Instead, it evaluates each new data point’s closeness to existing clusters, frequently depending on criteria such as distance from the cluster centre or arithmetic mean. The data point is allocated to the bunch to which it is nearest according to these metrics. Consider grouping three distinct clusters from a collection of data points; this entails determining the proximity of each data point to a given cluster by taking criteria such as the Euclidean distance between data points into account [54].
- Fuzzy Logic: Bridging Real Numbers with Degrees of Truth Fuzzy logic is a revolutionary way of introducing degrees between real values. The fuzzy set, under this paradigm, assigns a degree of membership to items inside a universe, commonly stated as a real integer between [0, 1]. This degree of membership is a crucial concept in fuzzy logic that allows statements to have varying degrees of truth. In the classical truth value spectrum, where 0 represents “completely false” and 1 represents “absolutely true”, fuzzy logic provides intermediate values representing partial truth. As a result, fuzzy logic emerges as a potent instrument for dealing with problems marked by imprecision, ambiguity, estimate, qualitative uncertainty, and partial truth [55].
- Hierarchical Clustering: Structured Data Organisation Hierarchical clustering is an unsupervised learning technique that excels in grouping related items into clusters, with top-down and bottom-up approaches available. Top-down hierarchical clustering, sometimes referred to as disagreeable clustering, starts with one major split and recursively divides the data into smaller and smaller clusters until every discovery is given its own cluster. On the other hand, bottom-up hierarchical clustering, sometimes referred to as agglomerative aggregation, assigns each record to a cluster based on a weight per cubic function. Surprisingly, hierarchical clustering is incredibly adaptable and straightforward to use since it does not need previous knowledge of the number of clusters. Data aggregation, synchronisation, mobile sink management, and gathering energy in WSNs are only a few of its many uses [56].
4. Applications of ML in WSNs
4.1. Localisation
4.2. Anomaly Detection
4.3. Error Detection
4.4. Target Tracking
- Computational Overhead Reduction: ML approaches, whether used with fixed or mobile sensor nodes, reduce the compute needs for monitoring mobile objects.
- Adaptability to Dynamic Targets: Given the changing nature of targets in sensor networks, ML techniques optimise target tracking efficiency.
4.5. Authentication
4.6. Congestion Control
- Enhanced Traffic Estimation: Machine learning approaches excel at assessing traffic loads and establishing effective pathways to minimise end-to-end delays between nodes and the base station.
- Dynamic Transmission Range: ML enables the dynamic modification of transmission ranges in response to changing network dynamics.
4.7. Diversified Security
4.8. QoS
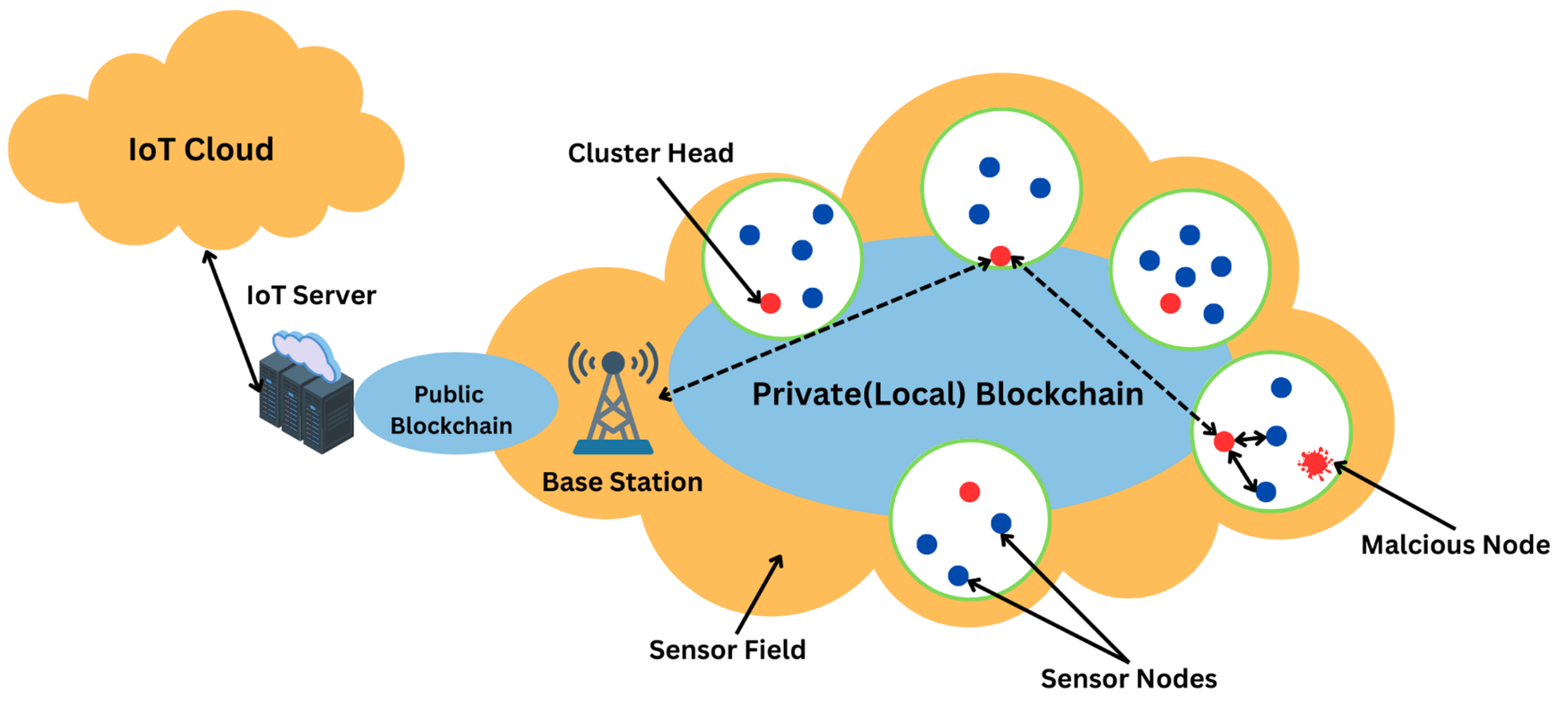
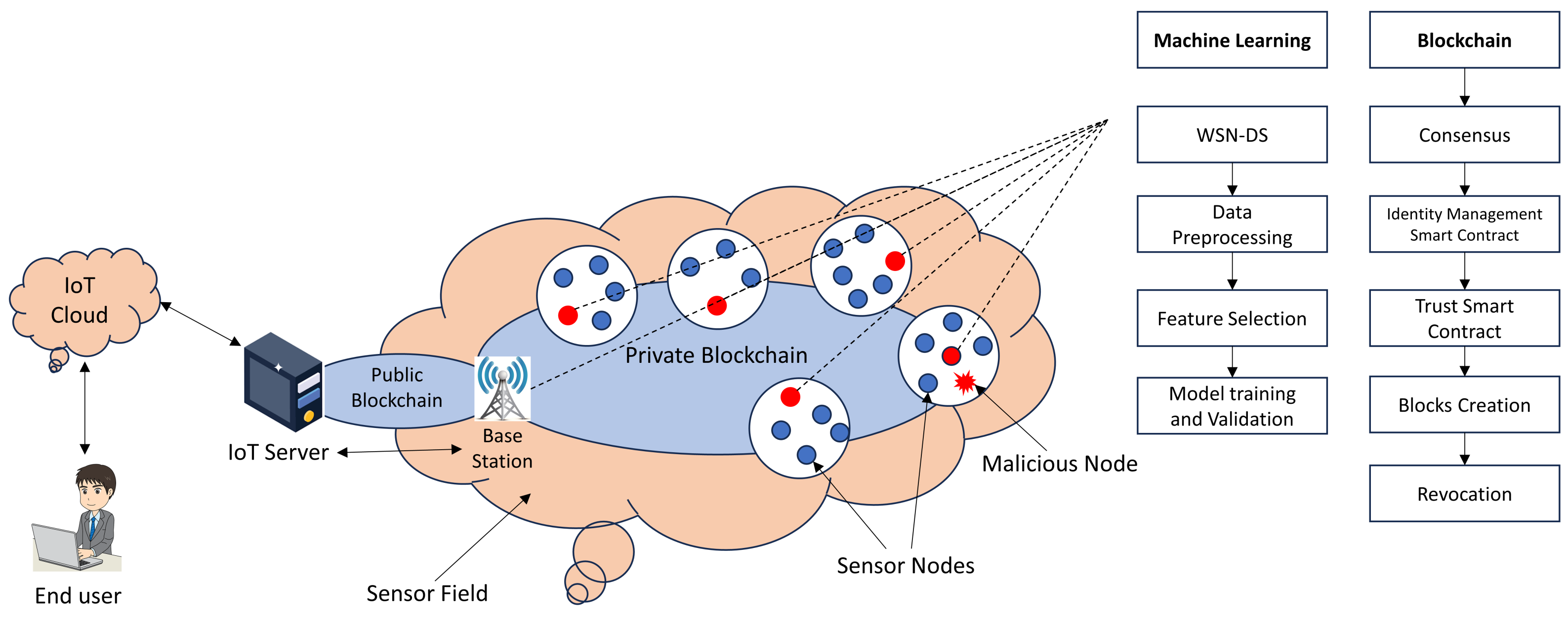
5. Cyber Attacks Prevention Using Machine Learning (ML) and Blockchain (BC) in WSN
5.1. Machine Learning (ML) and Cyberattacks
5.2. BC Introduction
5.3. Securing WSN
6. Limitations and Challenges
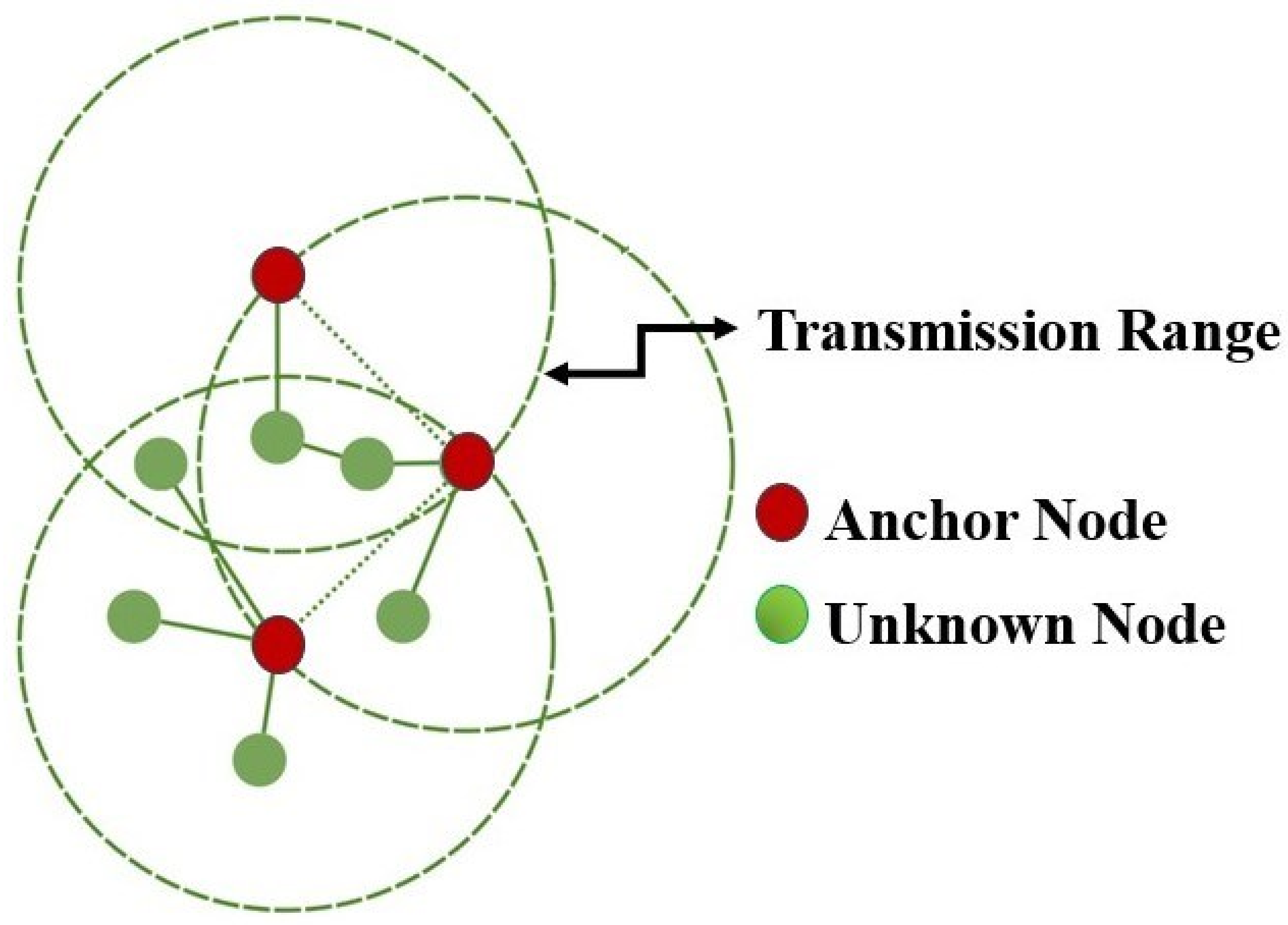
- Localisation Challenges: In the world of WSNs, effective Path Planning for mobile sensor nodes, particularly beacon nodes, is critical. Surprisingly, there are no well-defined Path Planning algorithms targeted to movable anchor nodes. In this context, the use of machine learning (ML) appears to be a viable route, with the ability to give optimised Path Planning for individual anchor nodes in sensor networks. This holds the prospect of improving localisation accuracy while reducing energy usage, which is crucial in resource-constrained WSNs. It is important to note that numerous live applications extend their data collection points into the space of three dimensions. However, the bulk of known localisation techniques have been studied primarily in two-dimensional space. The development of localisation algorithms that are specifically tailored to three-dimensional environments, including both static and mobile WSNs, is thus urgently needed [134].
- Coverage and Connectivity Challenges: Recent efforts have made significant progress in tackling coverage and connection difficulties inside WSNs. Nonetheless, a variety of unexplored problems and difficulties remain, awaiting research. Among these difficulties is anticipating the minimal number of sensor nodes required to efficiently cover a particular region or goal, as well as finding the appropriate placement of these sensor nodes [135]. Furthermore, random Sensor Node Deployment, which is typical in real-time WSN applications, poses the possibility of coverage gaps, commonly known as “coverage holes”. Detecting and correcting such coverage gaps is a hard job, made more difficult by the dynamic nature of networks, where coverage gaps can occur spontaneously. Importantly, whereas two-dimensional coverage algorithms have made great progress, the area of three-dimensional coverage, characterised by maximum computing efficiency, remains completely unexplored.
- Anomaly Detection Challenges: The identification of anomalies is one of the most significant research challenges in WSNs. In recent years, academics have worked hard to develop a variety of strategies for detecting abnormalities. Anomalies in WSNs have far-reaching consequences, affecting communication overhead, transmission delays, and possibly sensor node data. While anomaly detection has received a lot of attention, it is only one aspect of the problem. When an abnormality is discovered, further research efforts must focus on determining the best course of action. This entails defining the necessary actions to reduce harm and maintain network integrity. It is critical to recognise that anomaly detection algorithms are intrinsically application-specific, demanding a careful selection procedure, particularly in diverse WSNs. To fit with the different needs and operating dynamics of such networks, the selected detection algorithm must strike a compromise between precision and speed [136].
- Congestion Control and Avoidance Challenges: Congestion control and avoidance are fundamental concerns in the ever-changing WSN ecosystem. When considering the multifarious nature of WSN operations, which are prone to internal disturbances and external stimuli that may result in data loss, the necessity for strong and durable congestion management systems becomes clear. The intrinsic limits of WSNs, which include limited energy and memory resources, highlight the significance of simplified congestion control at the node level, in conjunction with prudent regulation of transmission rates between nodes. Efficient congestion control necessitates an adaptive, self-learning solution capable of dynamically responding to network disturbances. This flexibility should include the ability to add or remove nodes when congestion patterns emerge throughout the network. Furthermore, there is a pressing need for novel traffic prediction techniques capable of detecting and mitigating dynamic route modifications in order to avoid congestion problems. Furthermore, further research into effective mobile agent-based data gathering systems as an alternative to traditional inter-node data transfer is warranted [137].
- Quality of Service (QoS) Challenges: A multidimensional problem occurs in the quest for Quality of Service (QoS) in WSNs. The varying needs of users and applications need the development of customised QoS standards that account for differences in sensor types, data rates, traffic management strategies, and data formats. The customizable nature of QoS standards offers a significant issue since it involves the creation of efficient cross-layer protocols capable of upgrading QoS to satisfy a wide range of requirements. The issue of developing and adhering to QoS standards appears as a complicated difficulty within the context of large-scale, heterogeneous mobile sensor networks, necessitating thorough thought and novel solutions [138].
- Integration Performance: The successful integration of Blockchain (BC) with machine learnng (ML) depends on the enhancement of each technology’s unique capabilities. For instance, data manipulation may cause ML models to perform worse, which BC can help to prevent. In order to prevent manipulation, BC guarantees [139] the integrity of the transactions used to train ML models and the recorded judgements in attack classification. Authorised nodes have access to these records for auditing and review, which helps to improve subsequent ML detection judgements. Due to this synergy, incremental ML models can more effectively identify new assaults and evolve over time to accommodate dynamically changing networks.
- Scalability: In the context of WSNs, scalability refers to network capacity, including the quantity of nodes and transactions. Scalability is highly impacted by the consensus technique and the BC type chosen. For instance, compared to Proof-of-Work (PoW), consensus algorithms like Practical Byzantine Fault Tolerance (PBFT) and Proof-of-Authentication (PoA) might increase transaction throughput. Scalability becomes difficult as data and network size grow. For better scalability, solutions include hybrid BCs with public and private BCs, as well as limiting transaction volume and ledger size. For private BCs and cooperative WSNs, voting [140] or multiparty consensus are appropriate. PoAh is a possible option for networks with limited resources.
- Lightweight Schemes: Lightweight schemes are necessary for effective BC-ML [141] integration because they maintain security while having the least amount of overhead. The storage, processing, and communication requirements for components like trust, authentication, access control, smart contracts, and consensus processes should be met. For instance, IPFS can lower data storage costs in WSNs, but communication overhead must be taken into account. The preferable consensus mechanisms requiring less computation and latency are PBFT and PoA.
- Vulnerability: While combining [142] ML and BC improves security, not all attacks are completely eliminated. Even when data are protected by BC, it is possible for them to be altered before being securely recorded in the ledger.
- Managing Network Resources: Limited-resource sensor nodes present technical difficulties, particularly in the areas of encryption, trust, authentication, and transaction validation. Due to the exponential expansion of the ledger, memory space may become limited. Solutions [143] include reducing the complexity of BC encryption, calculating hash functions more efficiently, using nodes specifically designed to store ledgers (such as CHs and BS nodes), and transferring old data to external storage or the IoT cloud. These methods seek to solve storage and processing problems while consuming less power.
7. Conclusions and Future Research
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Eljakani, Y.; Boulouz, A.; Ben Salah, M.; El Hachemy, S. Performances prediction in Wireless Sensor Networks: A survey on Deep learning based-approaches. In ITM Web of Conferences; EDP Sciences: Les Ulis, France, 2022; Volume 43, p. 01010. [Google Scholar]
- Intanagonwiwat, C.; Govindan, R.; Estrin, D. Directed diffusion: A scalable and robust communication paradigm for sensor networks. In Proceedings of the ACM Mobi-Com’00, Boston, MA, USA, 6–11 August 2000; pp. 56–67. [Google Scholar]
- Akyildiz, I.F.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless Sensor Networks: A survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Rawat, P.; Singh, K.D.; Chaouchi, H.; Bonnin, J.M. Wireless Sensor Networks: A survey on recent developments and potential synergies. J. Supercomput. 2014, 68, 1–48. [Google Scholar] [CrossRef]
- Mitchell, T.M. Machine Learning, 1st ed.; McGraw-Hill, Inc.: New York, NY, USA, 1997. [Google Scholar]
- Alsheikh, M.A.; Lin, S.; Niyato, D.; Tan, H.-P. Machine Learning in Wireless Sensor Networks: Algorithms, Strategies, and Applications. IEEE Commun. Surv. Tutor. 2014, 16, 1996–2018. [Google Scholar] [CrossRef]
- Fu, S.; Zhang, Y.; Jiang, Y.; Hu, C.; Shih, C.-Y.; Marron, P.J. Experimental study for multi-layer parameter configuration of wsn links. In Proceedings of the 2015 IEEE 35th International Conference on Distributed Computing Systems, Columbus, OH, USA, 29 June–2 July 2015; pp. 369–378. [Google Scholar]
- Vinayakumar, R.; Alazab, M.; Soman, K.P.; Poornachandran, P.; Al-Nemrat, A.; Venkatraman, S. Deep Learning Approach for Intelligent Intrusion Detection System. IEEE Access 2019, 7, 41525–41550. [Google Scholar] [CrossRef]
- Ma, X.; Yao, T.; Hu, M.; Dong, Y.; Liu, W.; Wang, F.; Liu, J. A Survey on Deep Learning Empowered IoT Applications. IEEE Access 2019, 7, 181721–181732. [Google Scholar] [CrossRef]
- Ahmad, R.; Wazirali, R.; Abu-Ain, T. Machine Learning for Wireless Sensor Networks Security: An Overview of Challenges and Issues. Sensors 2022, 22, 4730. [Google Scholar] [CrossRef]
- Khashan, O.A.; Ahmad, R.; Khafajah, N.M. An automated lightweight encryption scheme for secure and energy-efficient communication in Wireless Sensor Networks. Ad Hoc Netw. 2021, 115, 102448. [Google Scholar] [CrossRef]
- Mohan, K.; Madan, S.; Bagavathi, C. A Power Efficient Mac Protocol for Quality of Service Evaluation in Wireless Sensor Networks. Int. J. Innov. Res. Electr. Electron. Instrum. Control Eng. 2014, 2, 2154–2159. [Google Scholar]
- IEEE 802.15.4-2006; Standard for Information Technology Part 15.4: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Low Rate Wireless Personal Area Networks (LRWPANs). IEEE: Piscataway Township, NJ, USA, 2006.
- Zhang, Y.; Cai, W. The Key Technology of Wireless Sensor Network and Its Application in the Internet of Things. J. Sens. 2022, 3, 1817781. [Google Scholar] [CrossRef]
- Ramasamy, V. Mobile Wireless Sensor Networks: An overview. In Wireless Sensor Networks—Insights and Innovations; IntechOpen: London, UK, 2017; pp. 1–197. [Google Scholar]
- Ali, A.; Ming, Y.; Chakraborty, S.; Iram, S. A Comprehensive Survey on Real-Time Applications of WSN. Futur. Internet 2017, 9, 77. [Google Scholar] [CrossRef]
- Phoemphon, S.; So-In, C.; Niyato, D. A hybrid model using fuzzy logic and an extreme learning machine with vector particle swarm optimization for Wireless Sensor Network localization. Appl. Soft Comput. 2018, 65, 101–120. [Google Scholar] [CrossRef]
- Yoneki, E.; Bacon, J. A Survey of Wireless Sensor Network Technologies: Research Trends and Middleware’s Role; University of Cambridge: Cambridge, UK, 2005. [Google Scholar]
- Ullah, S.; Higgins, H.; Braem, B.; Latre, B.; Blondia, C.; Moerman, I.; Saleem, S.; Rahman, Z.; Kwak, K.S. A Comprehensive Survey of Wireless Body Area Networks. J. Med. Syst. 2012, 36, 1065–1094. [Google Scholar] [CrossRef]
- Celandroni, N.; Ferro, E.; Gotta, A.; Oligeri, G.; Roseti, C.; Luglio, M.; Bisio, I.; Cello, M.; Davoli, F.; Panagopoulos, A.D.; et al. A survey of architectures and scenarios in satellite-based Wireless Sensor Networks: System design aspects. Int. J. Satell. Commun. Netw. 2013, 31, 1019. [Google Scholar] [CrossRef]
- Rodrigues, J.J.P.C.; Neves, P.A.C.S. A survey on IP-based Wireless Sensor Network solutions. Int. J. Commun. Syst. 2010, 23, 963–981. [Google Scholar] [CrossRef]
- Losilla, F.; Garcia-Sanchez, A.-J.; Garcia-Sanchez, F.; Garcia-Haro, J.; Haas, Z.J. A Comprehensive Approach to WSN-Based ITS Applications: A Survey. Sensors 2011, 11, 10220–10265. [Google Scholar] [CrossRef] [PubMed]
- Đurišić, M.P.; Tafa, Z.; Dimić, G.; Milutinović, V. A survey of military applications of Wireless Sensor Networks. In Proceedings of the 2012 Mediterranean Conference on Embedded Computing (MECO), Bar, Montenegro, 19–21 June 2012; pp. 196–199. [Google Scholar]
- Montenegro, G.; Kushalnagar, N.; Hui, J.; Culler, D. Transmission of IPv6 Packets over IEEE 802.15.4 Networks. Internet Proposed Standard RFC 4944; RFC Editor: Marina del Rey, CA, USA, 2007. [Google Scholar]
- Javeri, O.; Jeyakumar, A. Wireless Sensor Network Using Bluetooth. In Advances in Computing, Communication and Control; Unnikrishnan, S., Surve, S., Bhoir, D., Eds.; ICAC3 2011 Communications in Computer and Information Science; Springer: Berlin/Heidelberg, Germany, 2011; Volume 125. [Google Scholar]
- Hall, J.L. A Practical Wireless Exploitation Framework for Z-Wave Networks. Doctoral Thesis, Air Force Institute of Technology, Dayton, OH, USA, 2016. [Google Scholar]
- Patel, N.; Kathiriya, H.; Bavarva, A. Wireless Sensor Network using ZigBee. Int. J. Res. Eng. Technol. 2013, 2, 1038–1042. [Google Scholar]
- Sarker, I.H.; Colman, A.; Han, J.; Khan, A.I.; Abushark, Y.B.; Salah, K. BehavDT: A Behavioral Decision Tree Learning to Build User-Centric Context-Aware Predictive Model. Mob. Netw. Appl. 2020, 25, 1151–1161. [Google Scholar] [CrossRef]
- ISA-100.11 a-2009; Wireless Systems for Industrial Automation: Process Control and Related Applications. International Society of Automation: Pittsburgh, PA, USA, 2009.
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless Sensor Network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Akyildiz, I.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. A survey on sensor networks. IEEE Commun. Mag. 2002, 40, 102–114. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Stuntebeck, E.P. Wireless underground sensor networks: Research challenges. Ad Hoc Netw. 2006, 4, 669–686. [Google Scholar] [CrossRef]
- Heidemann, J.; Li, Y.; Syed, A.; Wills, J.; Ye, W. Underwater sensor networking: Research challenges and potential applications. In Proceedings of the IEEE Wireless Communications and Networking Conference, Las Vegas, NV, USA, 3–6 April 2006. [Google Scholar]
- Akyildiz, I.F.; Melodia, T.; Chowdhury, K.R. A survey on wireless multimedia sensor networks. Comput. Netw. 2007, 51, 921–960. [Google Scholar] [CrossRef]
- Nelli, A.; Mangasuli, S. Wireless Sensor Networks: An Overview on Security Issues and Challenges. Int. J. Adv. Eng. Manag. Sci. 2017, 3, 209–214. [Google Scholar] [CrossRef]
- Winkler, M.; Street, M.; Tuchs, K.-D.; Wrona, K. Wireless Sensor Networks for Military Purposes. In Autonomous Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2012; pp. 365–394. [Google Scholar]
- Cerpa, A.; Elson, J.; Hamilton, M.; Zhao, J. Habitat monitoring: Application driver for wireless communications technology. ACM SIGCOMM Comput. Commun. Rev. 2001, 31, 20–41. [Google Scholar] [CrossRef]
- Celler, B.; Hesketh, T.; Earnshaw, W.; Ilsar, E. An instrumentation system for the remote monitoring of changes in functional health status of the elderly at home. In Proceedings of the 16th Annual International Conference of the IEEE Engineering in Medicine and Biology Society, Baltimore, MD, USA, 3–6 November 1994; pp. 908–909. [Google Scholar]
- Dishongh, T.J.; McGrath, M. Wireless Sensor Networks for Healthcare Applications; Artech House: London, UK, 2010. [Google Scholar]
- Petriu, E.M.; Georganas, N.D.; Petriu, D.C.; Makrakis, D.; Groza, V.Z. Sensor-based information appliances. IEEE Instrum. Meas. Mag. 2000, 3, 31–35. [Google Scholar]
- Herring, C.; Kaplan, S. Component-based software systems for smart environments. IEEE Wirel. Commun. 2000, 7, 60–61. [Google Scholar] [CrossRef]
- Pottie, G.J.; Kaiser, W.J. Wireless integrated network sensors. Commun. ACM 2000, 43, 551–558. [Google Scholar] [CrossRef]
- Wheeler, A. Commercial Applications of Wireless Sensor Networks Using ZigBee. IEEE Commun. Mag. 2007, 45, 70–77. [Google Scholar] [CrossRef]
- Flammini, A.; Ferrari, P.; Marioli, D.; Sisinni, E.; Taroni, A. Wired and Wireless Sensor Networks for industrial applications. Microelectron. J. 2009, 40, 1322–1336. [Google Scholar] [CrossRef]
- Kumar, D.P.; Amgoth, T.; Annavarapu, C.S.R. Machine learning algorithms for Wireless Sensor Networks: A survey. Inf. Fusion 2019, 49, 1–25. [Google Scholar] [CrossRef]
- Modares, H.; Salleh, R.; Moravejosharieh, A. Overview of security issues in Wireless Sensor Networks. In Proceedings of the 2011 Third International Conference on Computational Intelligence, Modelling & Simulation, Langkawi, Malaysia, 20–22 September 2011; pp. 308–311. [Google Scholar]
- Kumar, A.; Lim, T.J. EDIMA: Early Detection of IoT Malware Network Activity Using Machine Learning Techniques. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT’19), Limerick, Ireland, 15–18 April 2019; pp. 289–294. [Google Scholar]
- Shen, M.; Tang, X.; Zhu, L.; Du, X.; Guizani, M. Privacy-Preserving Support Vector Machine Training Over Blockchain-Based Encrypted IoT Data in Smart Cities. IEEE Internet Things J. 2019, 6, 7702–7712. [Google Scholar] [CrossRef]
- Modak, S.; Sehgal, D.; Valadi, J. Applications of artificial intelligence and machine learning in viral biology. Glob. Virol. III Virol. 21st Century 2019, 154, 1–39. [Google Scholar]
- Ali, M.; Jung, L.T.; Abdel-Aty, A.-H.; Abubakar, M.Y.; Elhoseny, M.; Ali, I. Semantic-k-NN algorithm: An enhanced version of traditional k-NN algorithm. Expert Syst. Appl. 2020, 151, 113374. [Google Scholar] [CrossRef]
- Pisner, D.A.; Schnyer, D.M. Support vector machine. In Machine Learning; Elsevier: Amsterdam, The Netherlands, 2020; pp. 101–121. ISBN 9780128157398. [Google Scholar]
- Yaghini, M.; Khoshraftar, M.M.; Fallahi, M. A hybrid algorithm for artificial neural network training. Eng. Appl. Artif. Intell. 2013, 26, 293–301. [Google Scholar] [CrossRef]
- Ghahramani, Z. Unsupervised Learning. In Summer School on Machine Learning; Springer: Berlin/Heidelberg, Germany, 2004; pp. 72–112. [Google Scholar]
- Sinaga, K.P.; Yang, M.-S. Unsupervised K-Means Clustering Algorithm. IEEE Access 2020, 8, 80716–80727. [Google Scholar] [CrossRef]
- Kambalimath, S.; Deka, P.C. A basic review of fuzzy logic applications in hydrology and water resources. Appl. Water Sci. 2020, 10, 191. [Google Scholar] [CrossRef]
- Xu, X.; Ansari, R.; Khokhar, A.; Vasilakos, A.V. Hierarchical Data Aggregation Using Compressive Sensing (HDACS) in WSNs. ACM Trans. Sens. Netw. 2015, 11, 45. [Google Scholar] [CrossRef]
- Gharghan, S.K.; Nordin, R.; Ismail, M.; Ali, J.A. Accurate Wireless Sensor Localization Technique Based on Hybrid PSO-ANN Algorithm for Indoor and Outdoor Track Cycling. IEEE Sens. J. 2016, 16, 529–541. [Google Scholar] [CrossRef]
- Bernas, M.; Płaczek, B. Fully connected neural networks ensemble with signal strength clustering for indoor localization in Wireless Sensor Networks. Int. J. Distrib. Sens. Netw. 2015, 11, 12. [Google Scholar] [CrossRef]
- Banihashemian, S.S.; Adibnia, F.; Sarram, M.A. A New Range-Free and Storage-Efficient Localization Algorithm Using Neural Networks in Wireless Sensor Networks. Wirel. Pers. Commun. 2018, 98, 1547–1568. [Google Scholar] [CrossRef]
- El Assaf, A.; Zaidi, S.; Affes, S.; Kandil, N. Robust ANNs-Based WSN Localization in the Presence of Anisotropic Signal At-tenuation. IEEE Wirel. Commun. Lett. 2016, 5, 504–507. [Google Scholar] [CrossRef]
- Xie, M.; Hu, J.; Han, S.; Chen, H.-H. Scalable Hypergrid k-NN-Based Online Anomaly Detection in Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 1661–1670. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K. An Efficient Hybrid Anomaly Detection Scheme Using K-Means Clustering for Wireless Sensor Networks. Wirel. Pers. Commun. 2016, 90, 1971–2000. [Google Scholar] [CrossRef]
- Javaid, A.; Javaid, N.; Wadud, Z.; Saba, T.; Sheta, O.E.; Saleem, M.Q.; Alzahrani, M.E. Machine Learning Algorithms and Fault Detection for Improved Belief Function Based Decision Fusion in Wireless Sensor Networks. Sensors 2019, 19, 1334. [Google Scholar] [CrossRef] [PubMed]
- Emperuman, M.; Chandrasekaran, S. Hybrid Continuous Density Hmm-Based Ensemble Neural Networks for Sensor Fault Detection and Classification in Wireless Sensor Network. Sensors 2020, 20, 745. [Google Scholar] [CrossRef]
- Sun, Q.-Y.; Sun, Y.-M.; Liu, X.-J.; Xie, Y.-X.; Chen, X.-G. Study on fault diagnosis algorithm in WSN nodes based on RPCA model and SVDD for multi-class classification. Clust. Comput. 2019, 22, 6043–6057. [Google Scholar] [CrossRef]
- Vasuhi, S.; Vaidehi, V. Target tracking using Interactive Multiple Model for Wireless Sensor Network. Inf. Fusion 2016, 27, 41–53. [Google Scholar] [CrossRef]
- Zhou, B.; Chen, Q.; Li, T.J.; Xiao, P. Online Variational Bayesian Filtering-Based Mobile Target Tracking in Wireless Sensor Networks. Sensors 2014, 14, 21281–21315. [Google Scholar] [CrossRef]
- Xue, B.; Zhang, L.; Zhu, W.; Yu, Y. A new sensor selection scheme for Bayesian learning based sparse signal recovery in WSNs. J. Frankl. Inst. 2017, 355, 1798–1818. [Google Scholar] [CrossRef]
- Das, R.; Gadre, A.; Zhang, S.; Kumar, S.; Moura, J.M.F. A Deep Learning approach to IoT authentication. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018. [Google Scholar]
- Liao, R.-F.; Wen, H.; Wu, J.; Pan, F.; Xu, A.; Jiang, Y.; Xie, F.; Cao, M. Deep learning-Based physical-layer authentication for Industrial Wireless Sensor Networks. Sensors 2019, 19, 2440. [Google Scholar] [CrossRef]
- Ashibani, Y.; Mahmoud, Q.H. A Machine Learning-Based User Authentication Model Using Mobile App Data; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Rezaee, A.A.; Pasandideh, F. A Fuzzy Congestion Control Protocol Based on Active Queue Management in Wireless Sensor Networks with Medical Applications. Wirel. Pers. Commun. 2017, 98, 815–842. [Google Scholar] [CrossRef]
- O’Mahony, G.D.; Harris, P.J.; Murphy, C.C. Investigating Supervised Machine Learning Techniques for Channel Identification in Wireless Sensor Networks. In Proceedings of the 2020 31st Irish Signals and Systems Conference (ISSC), Letterkenny, Ireland, 11–12 June 2020. [Google Scholar]
- Abu Alsheikh, M.; Lin, S.; Niyato, D.; Tan, H.-P. Rate-Distortion Balanced Data Compression for Wireless Sensor Networks. IEEE Sens. J. 2016, 16, 5072–5083. [Google Scholar] [CrossRef]
- Gholipour, M.; Haghighat, A.T.; Meybodi, M.R. Hop-by-Hop Congestion Avoidance in Wireless Sensor Networks based on genetic support vector machine. Neurocomputing 2017, 223, 63–76. [Google Scholar] [CrossRef]
- Sun, W.; Lu, W.; Li, Q.; Chen, L.; Mu, D.; Yuan, X. WNN-LQE: Wavelet-Neural-Network-Based Link Quality Estimation for Smart Grid WSNs. IEEE Access 2017, 5, 12788–12797. [Google Scholar] [CrossRef]
- Lee, E.K.; Viswanathan, H.; Pompili, D. RescueNet: Reinforcement-learning-based communication framework for emergency networking. Comput. Netw. 2016, 98, 14–28. [Google Scholar] [CrossRef]
- Renold, A.P.; Chandrakala, S. MRL-SCSO: Multi-agent Reinforcement Learning-Based Self-Configuration and Self-Optimization Protocol for Unattended Wireless Sensor Networks. Wirel. Pers. Commun. 2017, 96, 5061–5079. [Google Scholar] [CrossRef]
- Revanesh, M.; Sridhar, V. A trusted distributed routing scheme for Wireless Sensor Networks using Blockchain and meta-heuristics-based deep learning technique. Trans. Emerg. Telecommun. Technol. 2021, 32, e4259. [Google Scholar] [CrossRef]
- Zhao, J.; Shetty, S.; Pan, J.W.; Kamhoua, C.; Kwiat, K. Transfer learning for detecting unknown network attacks. EURASIP J. Inf. Secur. 2019, 2019, 1. [Google Scholar] [CrossRef]
- Kuriakose, J.; Joshi, S.; Raju, R.V.; Kilaru, A. A review on localization in Wireless Sensor Networks. In Advances in Signal Processing and Intelligent Recognition Systems; Springer: Berlin/Heidelberg, Germany, 2014; pp. 599–610. [Google Scholar]
- Baccar, N.; Bouallegue, R. Interval type 2 fuzzy localization for Wireless Sensor Networks. EURASIP J. Adv. Signal Process. 2016, 2016, 42. [Google Scholar] [CrossRef]
- He, W.; Lu, F.; Chen, J.; Ruan, Y.; Lu, T.; Zhang, Y. A Kernel-Based Node Localization in Anisotropic Wireless Sensor Network. Sci. Program. 2021, 2021, 9944358. [Google Scholar] [CrossRef]
- Wang, Z.; Zhang, H.; Lu, T.; Sun, Y.; Liu, X. A new range-free localisation in Wireless Sensor Networks using support vector machine. Int. J. Electron. 2018, 105, 244–261. [Google Scholar] [CrossRef]
- Hashim, H.A.; Ayinde, B.; Abido, M. Optimal placement of relay nodes in Wireless Sensor Network using artificial bee colony algorithm. J. Netw. Comput. Appl. 2016, 64, 239–248. [Google Scholar] [CrossRef]
- Kumar, S.; Tiwari, S.N.; Hegde, R.M. Sensor node tracking using semi-supervised Hidden Markov Models. Ad Hoc Netw. 2015, 33, 55–70. [Google Scholar] [CrossRef]
- Sudhir, K.; Rajesh, H. A Review of Localization and Tracking Algorithms in Wireless Sensor Networks. arXiv 2017, arXiv:1701.02080. [Google Scholar]
- Wang, Y.; Liu, Z.; Wang, D.; Li, Y.; Yan, J. Anomaly detection and visual perception for landslide monitoring based on a heterogeneous sensor network. IEEE Sens. J. 2017, 17, 4248–4257. [Google Scholar] [CrossRef]
- Garofalo, A.; Di Sarno, C.; Formicola, V. Enhancing intrusion detection in Wireless Sensor Networks through decision trees. In Dependable Computing; Springer: Berlin/Heidelberg, Germany, 2013; pp. 1–15. [Google Scholar]
- Gil, P.; Martins, H.; Januário, F. Outliers detection methods in Wireless Sensor Networks. Artif. Intell. Rev. 2018, 52, 2411–2436. [Google Scholar] [CrossRef]
- Feng, Z.; Fu, J.; Du, D.; Li, F.; Sun, S. A new approach of anomaly detection in Wireless Sensor Networks using support vector data description. Int. J. Distrib. Sens. Netw. 2017, 13, 1. [Google Scholar] [CrossRef]
- Shahid, N.; Naqvi, I.H.; Bin Qaisar, S. One-class support vector machines: Analysis of outlier detection for Wireless Sensor Networks in harsh environments. Artif. Intell. Rev. 2015, 43, 515–563. [Google Scholar] [CrossRef]
- Tran, D.A.; Nguyen, T. Localization in Wireless Sensor Networks Based on Support Vector Machines. IEEE Trans. Parallel Distrib. Syst. 2008, 19, 981–994. [Google Scholar] [CrossRef]
- Zhang, H.; Liu, J.; Kato, N. Threshold Tuning-BasedWearable Sensor Fault Detection for Reliable Medical Monitoring Using Bayesian Network Model. IEEE Syst. J. 2018, 12, 1886–1896. [Google Scholar] [CrossRef]
- Titouna, C.; Aliouat, M.; Gueroui, M. FDS: Fault Detection Scheme for Wireless Sensor Networks. Wirel. Pers. Commun. 2016, 86, 549–562. [Google Scholar] [CrossRef]
- Chanak, P.; Banerjee, I. Fuzzy rule-based faulty node classification and management scheme for large scale Wireless Sensor Networks. Expert Syst. Appl. 2016, 45, 307–321. [Google Scholar] [CrossRef]
- Zidi, S.; Moulahi, T.; Alaya, B. Fault Detection in Wireless Sensor Networks through SVM Classifier. IEEE Sens. J. 2018, 18, 340–347. [Google Scholar] [CrossRef]
- Ez-Zaidi, A.; Rakrak, S. A Comparative Study of Target Tracking Approaches in Wireless Sensor Networks. J. Sens. 2016, 2016, 3270659. [Google Scholar] [CrossRef]
- Braca, P.; Willett, P.; LePage, K.; Marano, S.; Matta, V. Bayesian Tracking in Underwater Wireless Sensor Networks with Port-Starboard Ambiguity. IEEE Trans. Signal Process. 2014, 62, 1864–1878. [Google Scholar] [CrossRef]
- Chen, H.; Wang, R.; Cui, L.; Zhang, L. EasiDSlT: A Two-Layer Data Association Method for Multitarget Tracking in Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2015, 62, 434–443. [Google Scholar] [CrossRef]
- Das, S.N.; Misra, S.; Wolfinger, B.E.; Obaidat, M.S. Temporal-Correlation-Aware Dynamic Self-Management of Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2016, 12, 2127–2138. [Google Scholar] [CrossRef]
- Oikonomou, P.; Botsialas, A.; Olziersky, A.; Kazas, I.; Stratakos, I.; Katsikas, S.; Dimas, D.; Mermikli, K.; Sotiropoulos, G.; Goustouridis, D.; et al. A wireless sensing system for monitoring the workplace environment of an industrial installation. Sens. Actuators B 2016, 224, 266–274. [Google Scholar] [CrossRef]
- Wei, Z.; Zhang, Y.; Xu, X.; Shi, L.; Feng, L. A task scheduling algorithm based on Q-learning and shared value function for WSNs. Comput. Netw. 2017, 126, 141–149. [Google Scholar] [CrossRef]
- Chen, C.-P.; Mukhopadhyay, S.C.; Chuang, C.-L.; Lin, T.-S.; Liao, M.-S.; Wang, Y.-C.; Jiang, J.-A. A Hybrid Memetic Framework for Coverage Optimization in Wireless Sensor Networks. IEEE Trans. Cybern. 2015, 45, 2309–2322. [Google Scholar] [CrossRef]
- Dener, M.; Al, S.; Orman, A. STLGBM-DDS: An Efficient Data Balanced DoS Detection System for Wireless Sensor Networks on Big Data Environment. IEEE Access 2022, 10, 92931–92945. [Google Scholar] [CrossRef]
- Alshrif, F.F.; Sundararajan, E.A.; Ahmad, R.; Alkhatib, Y. New Framework for Authentication and key Establishment to Secure 6LoWPAN Networks. In Proceedings of the 2021 International Conference on Electrical Engineering and Informatics (ICEEI), Kuala Terengganu, Malaysia, 12–13 October 2021; pp. 1–6. [Google Scholar]
- Pan, F.; Wen, H.; Liao, R.; Jiang, Y.; Xu, A.; Ouyang, K.; Zhu, X. physical-layer authentication based on channel information and machine learning. In Proceedings of the 2017 IEEE Conference on Communications and Network Security (CNS), Las Vegas, NV, USA, 9–11 October 2017; pp. 364–365. [Google Scholar]
- Fang, H.; Wang, X.; Hanzo, L. Learning-Aided physical-layer authentication as an Intelligent Process. IEEE Trans. Commun. 2019, 67, 2260–2273. [Google Scholar] [CrossRef]
- Ashibani, Y.; Mahmoud, Q.H. User authentication for smart home networks based on mobile apps usage. In Proceedings of the 2019 28th International Conference on Computer Communication and Networks (ICCCN), Valencia, Spain, 29 July–1 August 2019; pp. 1–6. [Google Scholar]
- Sergiou, C.; Antoniou, P.; Vassiliou, V. A Comprehensive Survey of Congestion Control Protocols in Wireless Sensor Net-works. IEEE Commun. Surv. Tutor. 2014, 16, 1839–1859. [Google Scholar] [CrossRef]
- Kafi, M.A.; Ben-Othman, J.; Ouadjaout, A.; Bagaa, M.; Badache, N. REFIACC: Reliable, efficient, fair and interference-aware congestion control protocol for Wireless Sensor Networks. Comput. Commun. 2017, 101, 1–11. [Google Scholar] [CrossRef]
- Moon, S.-H.; Park, S.; Han, S.-J. Energy efficient data collection in sink-centric Wireless Sensor Networks: A cluster-ring ap-proach. Comput. Commun. 2017, 101, 12–25. [Google Scholar] [CrossRef]
- Canedo, J.; Skjellum, A. Using machine learning to secure IoT systems. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 219–222. [Google Scholar]
- Miettinen, M.; Marchal, S.; Hafeez, I.; Asokan, N.; Sadeghi, A.R.; Tarkoma, S. IoT SENTINEL: Automated Device-Type Identi-fication for Security Enforcement in IoT. In Proceedings of the 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), Atlanta, GA, USA, 5–8 June 2017; pp. 2177–2184. [Google Scholar]
- Meidan, Y.; Bohadana, M.; Shabtai, A.; Guarnizo, J.D.; Ochoa, M.; Tippenhauer, N.O.; Elovici, Y. ProfilIoT: A machine learning approach for IoT device identification based on network traffic analysis. In Proceedings of the Symposium on Applied Computing, Marrakech, Morocco, 3–7 April 2017. [Google Scholar]
- O’MAhony, G.D.; Harris, P.J.; Murphy, C.C. Detecting Interference in Wireless Sensor Network Received Samples: A Machine Learning Approach. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; pp. 1–6. [Google Scholar]
- Rathore, H.; Badarla, V.; Jha, S.; Gupta, A. Novel approach for security in Wireless Sensor Network using bio-inspirations. In Proceedings of the 2014 Sixth International Conference on Communication Systems and Networks (COMSNETS), Bangalore, India, 6–10 January 2014. [Google Scholar]
- Asif, M.; Khan, S.; Ahmad, R.; Sohail, M.; Singh, D. Quality of Service of Routing Protocols in Wireless Sensor Networks: A Review. IEEE Access 2017, 5, 1846–1871. [Google Scholar] [CrossRef]
- Collotta, M.; Pau, G.; Bobovich, A.V. A Fuzzy Data Fusion Solution to Enhance the QoS and the Energy Consumption in Wireless Sensor Networks. Wirel. Commun. Mob. Comput. 2017, 2017, 3418284. [Google Scholar] [CrossRef]
- Ren, L.; Wang, W.; Xu, H. A Reinforcement Learning Method for Constraint-Satisfied Services Composition. IEEE Trans. Serv. Comput. 2017, 13, 786–800. [Google Scholar] [CrossRef]
- Razzaque, A.; Ahmed, M.H.U.; Hong, C.S.; Lee, S. QoS-aware distributed adaptive cooperative routing in Wireless Sensor Networks. Ad Hoc Netw. 2014, 19, 28–42. [Google Scholar] [CrossRef]
- Haber, S.; Stornetta, W.S. How to Time-Stamp a Digital Document. J. Cryptol. 1991, 3, 99–111. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. SSRN 2008. [Google Scholar] [CrossRef]
- Gagneja, K.; Gagneja, K.; Kiefer, R. Security Protocol for Internet of Things (IoT): Blockchain-based Implementation and Analysis. In Proceedings of the 2020 Sixth International Conference on Mobile and Secure Services (MobiSecServ), Miami Beach, FL, USA, 22–23 February 2020; pp. 1027–1034. [Google Scholar]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. Blendcac: A blockchain-enabled decentralized capability-based access control for iots. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 207–212. [Google Scholar]
- Khalil, A.A.; Franco, J.; Parvez, I.; Uluagac, S.; Shahriar, H.; Rahman, M.A. A Literature Review on Blockchain-enabled Security and Operation of Cyber-Physical Systems. In Proceedings of the 2022 IEEE 46th Annual Computers, Software and Applications Conference (COMPSAC), Los Alamitos, CA, USA, 27 June 2022–1 July 2022; pp. 1774–1779. [Google Scholar]
- Ismail, S.; Dawoud, D.; Reza, H. Towards a light weight Identity Management and Secure Authentication for IoT Using Blockchain. In Proceedings of the 2022 IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 6–9 June 2022; pp. 77–83. [Google Scholar]
- Miraz, M.H. Blockchain of things (BCoT): The fusion of Blockchain and IoT technologies. In Advanced Applications of Blockchain Technology; Springer: Berlin/Heidelberg, Germany, 2020; pp. 141–159. [Google Scholar]
- Pundir, S.; Wazid, M.; Singh, D.P.; Das, A.K.; Rodrigues, J.J.P.C.; Park, Y. Intrusion Detection Protocols in Wireless Sensor Networks Integrated to Internet of Things Deployment: Survey and Future Challenges. IEEE Access 2019, 8, 3343–3363. [Google Scholar] [CrossRef]
- Omar, S.; Ngadi, A.; Jebur, H.H. Machine Learning Techniques for Anomaly Detection: An Overview. Int. J. Comput. Appl. 2013, 79, 33–41. [Google Scholar] [CrossRef]
- Faiz, M.; Sandhu, R.; Akbar, M.; Shaikh, A.A.; Bhasin, C.; Fatima, N. Machine Learning Techniques inWireless Sensor Networks: Algorithms, Strategies, and Applications. Int. J. Intell. Syst. Appl. Eng. 2023, 11, 685–694. [Google Scholar]
- Indu, S.D. Wireless Sensor Networks: Issues & challenges. Int. J. Comput. Sci. Mob. Comput. 2014, 3, 681–685. [Google Scholar]
- Joshi, G.P.; Nam, S.Y.; Kim, S.W. Cognitive radio Wireless Sensor Networks: Applications, challenges and research trends. Sensors 2013, 13, 11196–11228. [Google Scholar] [CrossRef]
- Javed, B.; Hanan, A.; Abdul, K. Issues and Challenges in Localization of Wireless Sensor Networks. Sci. Int. 2014, 26, 595–603. [Google Scholar]
- Abhishek, T.; Hari, G.; Tanima, D.; Rahul, M.; Kaushal, S.; Somporn, J. Coverage and Connectivity in WSNs: A Survey, Research Issues and Challenges. IEEE Access 2018, 6, 26971–26992. [Google Scholar]
- Satish, B.; Chetan, B.; Vishal, D. Anomaly Detection Techniques for Wireless Sensor Networks—A Survey. Int. J. Emerg. Trends Technol. Comput. Sci. 2013, 2, 3852. [Google Scholar]
- Charalambos, S.; Vasos, V.; Aristodemos, P. Congestion control in Wireless Sensor Networks through dynamic alternative path selection. Comput. Netw. 2014, 75, 226–238. [Google Scholar]
- Bhuyan, B.; Sarma, H.K.D.; Sarma, N.; Kar, A.; Mall, R. Quality of Service (QoS) Provisions in Wireless Sensor Networks and Related Challenges. Wirel. Sens. Netw. 2010, 2, 861–868. [Google Scholar] [CrossRef]
- Ifzarne, S.; Tabbaa, H.; Hafidi, I.; Lamghari, N. Anomaly Detection using Machine Learning Techniques in Wireless Sensor Networks. J. Phys. Conf. Ser. 2021, 1743, 012021. [Google Scholar] [CrossRef]
- Puthal, D.; Mohanty, S.P.; Nanda, P.; Kougianos, E.; Das, G. Proof-of-Authentication for Scalable Blockchain in Re-source-Constrained Distributed Systems. In Proceedings of the 2019 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 11–13 January 2019; pp. 1–5. [Google Scholar]
- Nouman, M.; Qasim, U.; Nasir, H.; Almasoud, A.; Imran, M.; Javaid, N. Malicious Node Detection Using Machine Learning and Distributed Data Storage Using Blockchain in WSNs. IEEE Access 2023, 11, 6106–6121. [Google Scholar] [CrossRef]
- Du, M.; Ma, X.; Zhang, Z.; Wang, X.; Chen, Q. A review on consensus algorithm of blockchain. In Proceedings of the 2017 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Banff, AB, Canada, 5–8 October 2017; pp. 2567–2572. [Google Scholar]
- Wang, S.-Y.; Hsu, Y.-J.; Hsiao, S.-J. Integrating Blockchain Technology for Data Collection and Analysis in Wireless Sensor Networks with an Innovative Implementation. In Proceedings of the 2018 International Symposium on Computer, Consumer and Control (IS3C), Taichung, Taiwan, 6–8 December 2018; pp. 149–152. [Google Scholar]









| Reference | Approach | Contributions/Findings |
|---|---|---|
| Eljakani et al., 2022 [1] | • Deep learning approaches for WSN performance prediction • CNN-based MAC protocol identification MLP for PDR and SNR prediction | • Survey of recent DL methods for WSN performance prediction • Application of DL in multiple WSN layers • Exploration of cross-layer approaches • Identification of challenges in data availability and multi-parameter prediction |
| Rawat et al., 2014 [4] | • Overview of WSN technologies • Challenges in WSN applications • Collaborative nature of WSNs • Highlights infrastructure challenges • Importance of intelligent collaboration among nodes • No explicit discussion of limitations • Acknowledgment of resource constraints and communication reliability challenges | • Comprehensive overview of recent WSN developments • Identification of challenges and potential applications • Emphasis on intelligent collaboration and energy efficiency • Discussion of sensor node limitations • Importance of intelligent collaboration among nodes • No explicit discussion of limitations • Acknowledgment of resource constraints and communication reliability challenges • Limited focus on machine learning or DL techniques |
| Alsheikh et al., 2014 [6] | • Literature review of ML methods in WSNs • Text representation methods for system calls • Performance evaluation and comparison | • Identification of best algorithm for detection • Insights into ML performance in intrusion detection • Evaluation of classical ML classifiers • Benchmarking DNNs for intrusion detection |
| Vinayakumar et al., 2019 [8] | • Intrusion detection using DNNs • Evaluation of classical classifiers • Text representation methods for system calls • Need for systematic dataset updates • No discussion of scalability in real-world implementation | • Evaluation of DNNs and classical classifiers for intrusion detection • Proposal of Scale-Hybrid-IDS-Alert Net (SHIA) • Identification of best algorithm for detection • Insights into ML techniques for intrusion detection • Performance evaluation and benchmarking |
| Ahmad et al., 2022 [10] | • Survey of ML algorithms for WSN security • Discussion of security requirements in WSNs | • Identification of security requirements and challenges • Statistical analysis of security implementations • Highlighting open issues in ML adaptation to sensor capabilities • Specific ML algorithm analysis lacking • Performance evaluation not discussed |
| Khashan et al., 2021 [11] | • Introduction of FlexCrypt scheme for secure and efficient WSNs • Dynamic clustering for mobility support • Performance evaluation in simulation | • Introduction of FlexCrypt scheme for secure and efficient WSNs • Flexible lightweight cryptographic method • Security analysis and performance evaluation • Highlighting advantages over other ciphers |
| Mohan et al., 2014 [12] | • Cross-layer framework based on IEEE 802.15.4 [13]/ZigBee standards • Simulation using GloMoSim • Beacon-enabled peer-to-peer topology • LEACH routing protocol • Superframe structure utilisation • Sleep and ACK modes | • Improved energy efficiency, network lifetime, latency • Higher packet delivery ratio, lower delay, increased throughput • Reduced energy consumption |
| Zhang et al., 2022 [14] | • QoS model based on routing, clustering, and data fusion • Evaluation of an optimal fertilisation system | • Better energy balance and cluster head distribution • Improved energy consumption and flexibility • Insight into sensor node diagnostics • Effective fertilisation support system • Comparison of diagnostic models • Assessment of node consumption |
| Ramasamy et al., 2017 [15] | • Categorisation of factors for energy efficient MWSNs • Discussion of mobile sensor node architecture • Exploration of various aspects of MWSNs | • Insights into mobile sensor node architecture • Exploration of MWSN aspects |
| Ali et al., 2017 [16] | • Survey of real-time WSN applications • Mention of sensor technology advancements | • Highlighting sensor technology advancements • Lack of specific quantitative results • No exploration of scalability, interoperability, security, or cost-effectiveness |
| Phoemphon et al., 2018 [17] | • Hybrid model: Fuzzy Logic + ELM + PSO • Centroid method with weight (wi) | • Improved WSN localisation accuracy • Integration of soft computing techniques • Lack of discussion on scalability and energy efficiency • No analysis of network topology impact • Fuzzy logic limitations not addressed • Limited comparison with other localisation techniques |
| Protocol Characteristics | Wi-Fi (IEEE 801.11n [12]) | ZigBee (IEEE 802.15.4 [13]) | 6LoWPAN (IETF RFC-6282 [24]) | Bluetooth (IEEE 802.15.1 [25]) | BLE (IEEE 802.15.1 [25]) | Z-Wave (ISO/IEC 14543 [26]) |
|---|---|---|---|---|---|---|
| Frequency Range | 2.4–5 GHz, 120 kHz | 2.4 GHz, 868/915 MHz | 868/921 Hz, 2.4–5 GHz | 2.402–2.482 GHz | 2.402–2.482 GHz | 2.4 GHz, 868/915 MHz |
| Max Data Rate | 11–54 Mbps | 20/40 kbps; 250 kbps | 10–40 kbps, 250 kbps | 0.7–2.1 Mbps | 0.27 Mbps | 9.6–40 kbps |
| Effective Range | 10–100 m | 10–1000 m | 10–100 m | 15–20 m | 10–15 m | 30–50 m |
| Modulation Schemes | BPSK, QPSK, OFDM, M-QAM | D-BPSK, OQPSK, QPSK | BPSK, O-QPSK, ASK | GFSK, CPFSK, 8-DPSK | GFSK | FSK, GFSK, Narrowband |
| Network Topology | Star, Tree, Point-to-Point | Star, Mesh, Cluster Tree | Star, Mesh, Point-to-Point | Star | Star, Mesh, Point-to-Point | Mesh |
| Network Size | Up to 32 devices | Up to 65536 nodes | Up to 100 nodes | Up to 8 devices | Not Applicable | Up to 232 nodes |
| Encryption | RC4 Stream, AES Block Cipher | 128-bit AES | 128-bit AES | AES-CCM | 128-bit AES | 128-bit AES |
| Coding Techniques | MC-DSSS, CCK, OFDM | DSSS (1–15), DSSS (4–32) | Header Compression, DSSS | FSK, GFSK, RISS | Adaptive CCK | Manchester, NRZ |
| Channel Bandwidth | 20–25 MHz, 0.3/0.6 MHz | 0 MHz (fixed), 2–5 MHz | Not Applicable | 8 MHz | 2–5 MHz | Fixed (1 MHz) |
| Reference | WSN Category | Approach | Evaluation Parameter | Inference |
|---|---|---|---|---|
| Phoemphon et al., 2018 [17] | Localisation, Determining the relationships between anchor nodes and their locations using Received Signal Strength Indicators (RSSIs) | Fuzzy Logic and Extreme Learning Machine (ELM) with Vector Particle Swarm Optimisation (PSO), SVM-RBF | Location estimation precision, node density, sensing coverage | Enhances the location approximation in WSNs, and the ELM-based technique is found to be superior to other techniques such as Fuzzy Logic, Genetic Algorithms (GAs), Neural Networks (NNs), and SVMs |
| Gharghan et al., 2016 [57] | Localisation, distance estimation between mobile sensor node and anchor node in outdoor and indoor environments | PSO-ANN, Levenberg–Marquardt (LM) training algorithm | Mean absolute error | The hybrid PSO-ANN algorithm significantly improved the distance estimation accuracy compared to the traditional LNSM method |
| Bernas et al., 2015 [58] | Localisation | FCNNs | Arithmetic mean of error | Use of FCNNs and signal strength clustering helps in reducing the memory required to store the received signal strength map |
| Banihashemian et al., 2018 [59] | Localisation | Neural networks | Localisation accuracy and storage overhead | Lower localisation error rate and requires less storage compared to analogous methods in different environmental conditions |
| El Assaf et al., 2016 [60] | Localisation, Distance estimation and power-efficient correction mechanisms | ANNs | Accuracy and robustness against anisotropic signal attenuation | Proposed algorithm significantly outperforms most representative range-free localisation algorithms in terms of accuracy and robustness against anisotropic attenuation |
| Xie et al., 2013 [61] | Anomaly Detection | K-Nearest Neighbour (k-NN) | Accuracy | Proposed scheme is effective and robust for online anomaly detection in WSNs |
| Wazid et al., 2016 [62] | Anomaly Detection, detect two types of malicious nodes: blackhole and misdirection nodes | K-Means Clustering | Detection Rate | Proposed technique using K-means clustering achieves significantly better results compared to existing related schemes for detecting malicious nodes in WSNs |
| Javaid et al., 2019 [63] | Error Detection | Enhanced K-Nearest Neighbour (Ek-NN), Enhanced Extreme Learning Machine (EELM), Enhanced Support Vector Machine (ESVM), and Enhanced Recurrent Extreme Learning Machine (ERELM) | Detection Accuracy (DA), True Positive Rate (TPR), and Error Rate (ER) | Proposed methods outperform existing techniques and provide better results for belief function fusion and fault detection in WSNs |
| Emperuman et al., 2020 [64] | Error Detection | Continuous Density Hidden Markov Model (CDHMM) and various neural networks (NNs) | Detection accuracy, false positive rate, F1-score, and the Matthews correlation coefficient | Learning vector quantisation NN classifier outperforms the other classifiers in terms of detection accuracy rate |
| Sun et al., 2019 [65] | Error Detection | Recursive Principal Component Analysis (RPCA) model and Support Vector Data Description (SVDD) | Sample evaluation criterion rF(i) | Proposed algorithm in the research paper can satisfy the real-time needs of data stream processing and track data changes well. It improves the safety factor of monitoring sites and allows for timely repair or replacement of faulty nodes. |
| Vasuhi et al., 2016 [66] | Target Tracking | Interactive Target Tracking in Wireless Sensor Networks (ITTWSN) | Accuracy | Proposed ITTWSN scheme using Interactive Multiple Model (IMM) is more accurate in target tracking compared to the existing Kalman Filter (KF) based approach in a WSNs environment |
| Zhou et al., 2014 [67] | Target Tracking | Variational Bayesian Filtering (VBF) | Accuracy | Focuses on the convergence properties of the proposed VBF scheme for target position estimation in WSNs |
| Xue et al., 2017 [68] | Target Tracking, sparse signal recovery in WSNs for the detection of sparse events and localisation purposes | Sparse Bayesian Learning (SBL) | Accuracy | Proposed approaches in the research paper lead to superior performance compared to reference methods in terms of sparse signal recovery in WSNs |
| Das et al., 2018 [69] | Authentication | Long short-term memory (LSTM) | Classification accuracy | Deep learning classifier shows high resilience to advanced software radio adversaries |
| Liao et al., 2019 [70] | Authentication | Counter Propagation Neural Network (CPNN), Deep Neural Network (DNN) | Accuracy | Proposed DL-based PHY-layer authentication method can implement lightweight authentication for the sensor nodes under the edge computing (EC) system in Industrial WSNs |
| Ashibani et al., 2020 [71] | Authentication | Random Forest, K-Nearest Neighbours, Gradient Boosting Classifier, and Multi-Layer Perceptron | F-Measure | Presented model authenticates users based on application access events with high F-measure |
| Rezaee et al., 2018 [72] | Congestion Control | Fuzzy Proportional-Integral-Derivative (PID) | Data loss rate and end-to-end delay | Proposed protocol outperformed other approaches in terms of data loss rate and end-to-end delay, based on simulation results using the OPNET simulator and MATLAB |
| O’Mahony et al., 2020 [73] | Congestion Control, Safety-critical applications | Support Vector Machine (SVM) and Random Forest | Classification accuracy | Investigates supervised machine learning techniques for channel identification in WSNs using SVM and Random Forest algorithms |
| Alsheikh et al., 2016 [74] | Congestion Control | Autoencoder networks | Evaluated using real-world datasets and compared with conventional methods for temporal and spatial data compression | Proposed algorithm outperforms several existing WSN data compression methods in terms of compression efficiency and signal reconstruction |
| Gholipour et al., 2019 [75] | Congestion Control | Support Vector Machines (SVM) | Energy consumption, packet loss, end-to-end delay, throughput, and network lifetime | Proposed method using SVM and genetic algorithm tuning improves network throughput, decreases energy consumption, packet loss, and end-to-end delay in WSNs. It also significantly improves network lifetime under different traffic conditions, especially in heavy-traffic areas |
| Sun et al., 2017 [76] | QoS, monitoring and control in smart grids | Wavelet-Neural-Network-based Link Quality Estimation (WNN-LQE) | Accuracy | Presents comparative experimental results to demonstrate the validity of the proposed LQE algorithm |
| Lee et al., 2016 [77] | QoS | RescueNet | Accuracy | Introduces a self-adaptation framework for the network called RescueNet to enhance QoS in disaster scenarios |
| Renold et al., 2017 [78] | QoS | Multi-Robot Learning (MRL) | Packet delivery ratio, end-to-end delay, path stability, throughput | Proposed MRL algorithm achieves stabilised performance in terms of packet delivery ratio, end-to-end delay, path stability, and throughput in underwater sensor networks (UWSNs) |
| Revanesh et al., 2021 [79] | Malicious Attacks | Deep Convolutional Neural Networks (DCNN), Simulated Annealing-based Search Optimisation (SSO) | Latency, Energy, Computational cost, and Accuracy | Proposed method shows a 97% improvement in energy efficiency and a 90.5% improvement in computational cost, with better accuracy and latency compared to existing systems |
| Zhao et al., 2019 [80] | Cyber Attacks | Decision trees, Random forests, Gradient boosting, and XGBoost with Hierarchical Ensemble Transfer Learning (HeTL) and Centralised Ensemble Hierarchical Transfer Learning (CeHTL) | Accuracy | Proposed hierarchical ensemble transfer learning methods significantly improve the performance of individual base learners and the overall system in terms of accuracy |
| ML Approach | Relevant Research | Computational Complexity | Targeted Goals |
|---|---|---|---|
| Artificial Neural Network (ANN) | [76] | Minimal | Assessment of Link Quality |
| [96] | Moderate | Detection of Faulty Nodes | |
| [119] | Reasonable | Fusion of Data and Energy Efficiency | |
| Reinforcement Learning | [77] | Moderate | Cross-Layer Communication Framework |
| [78] | Minimal | Control of Network Topology and Data Distribution Protocol | |
| [120] | Substantial | Composition of Services with Fulfillment of Constraints | |
| [121] | Moderate | Adaptive Cooperative Routing in a Distributed Manner |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Delwar, T.S.; Aras, U.; Mukhopadhyay, S.; Kumar, A.; Kshirsagar, U.; Lee, Y.; Singh, M.; Ryu, J.-Y. The Intersection of Machine Learning and Wireless Sensor Network Security for Cyber-Attack Detection: A Detailed Analysis. Sensors 2024, 24, 6377. https://doi.org/10.3390/s24196377
Delwar TS, Aras U, Mukhopadhyay S, Kumar A, Kshirsagar U, Lee Y, Singh M, Ryu J-Y. The Intersection of Machine Learning and Wireless Sensor Network Security for Cyber-Attack Detection: A Detailed Analysis. Sensors. 2024; 24(19):6377. https://doi.org/10.3390/s24196377
Chicago/Turabian StyleDelwar, Tahesin Samira, Unal Aras, Sayak Mukhopadhyay, Akshay Kumar, Ujwala Kshirsagar, Yangwon Lee, Mangal Singh, and Jee-Youl Ryu. 2024. "The Intersection of Machine Learning and Wireless Sensor Network Security for Cyber-Attack Detection: A Detailed Analysis" Sensors 24, no. 19: 6377. https://doi.org/10.3390/s24196377







