A Conditional Privacy Preserving Generalized Ring Signcryption Scheme for Micro Aerial Vehicles
Abstract
:1. Introduction
- We propose a conditional privacy-preserving generalized ring signcryption scheme for MAVs using the ECC operation.
- The proposed scheme is conditional privacy-preserving, meaning each entity encrypts its real identity using a common secret key between entity and PKG in the key generation process.
- The proposed scheme enables encryption and digital signature simultaneously as well as independently using generalized signcryption. In ring configurations mode, this scheme guarantees anonymity, spontaneity, flexibility, and equal membership.
- We conducted a formal security study using the Random Oracle Model (ROM) and found that the proposed scheme is secure against a wide range of cyber-attacks.
- Finally, the proposed scheme’s efficiency is compared to its counterparts, validating its low computation cost, communication cost and memory overhead.
2. Preliminaries, Network Model and Syntax of the Proposed Scheme
2.1. Preliminaries
2.1.1. Elliptic Curve Cryptography (ECC)
2.1.2. Elliptic Curve Decisional Diffie-Hellman Problem (ECDDHP)
2.1.3. Elliptic Curve Discrete Logarithm Problem (ECDLP)
2.2. Syntax
- Initialization: The ground core network (GCN) can play the role private key generator (PKG), in which he/she can sets as his/her secret key, as his/her public key, and generates a public parameter set .
- Key Generation: The device that participates in a network as a legal user will send () to GCN by using open channel. Based on (), GCN first compute and recover the real identity . Then, GCN computes and send () to the legitimate user by using secure channel.
- Generalized Ring Signcryption: This algorithm will run by Micro Aerial Vehicle (MAV), in which the MAV take input that are () and produce the tuple ().
- Generalized Ring Signcryption Verifications: Given the tuple (), a user can verify ().
2.3. Network Model
3. Proposed Scheme Construction
- MDN choose and compute .
- Compute and
- Compute and .
- MAV send () to everything (X).
- Compare if is holds, where .
- Compute and .
Correctness Analysis
4. Security Analysis
- Query: send a request for Query with identity check for a tuple in the list , if is found, returns to . Otherwise, choose the value for randomly and returns it to .
- Query: send a request for Query with identity check for a tuple in the list , if is found, returns to . Otherwise, choose the value for randomly and returns it to .
- Query: send a request for Query with identity check for a tuple in the list , if is found, returns to . Otherwise, choose the value for randomly and returns it to .
- At query, if , set .
- Else, compute , where it selects randomly.
- At the end, returns to
- If , It choose and compute .
- Compute and
- Compute and , where is randomly selected now here.
- send () to .
- It computes .
- Compute and
- Compute and , where is randomly selected now here.
- returns ().
- 1.
- succeeded in User Private Key Query.
- 2.
- succeeded in Generalized Ring Signcryption Verification Query.
- 3.
- succeeded in in challenge phase.
- choose and compute .
- Compute and
- Compute and .
- Returns ().
- 4.
- succeeded in User Private Key Query.
- 5.
- succeeded in Generalized Ring Signcryption Verification Query.
- 6.
- succeeded in in challenge phase.
- INT first struggle to access from to made .
- Secondly INT can access from to made .
- INT first struggle to access from to made .
- Secondly INT can access from to made .
5. Performance Comparison
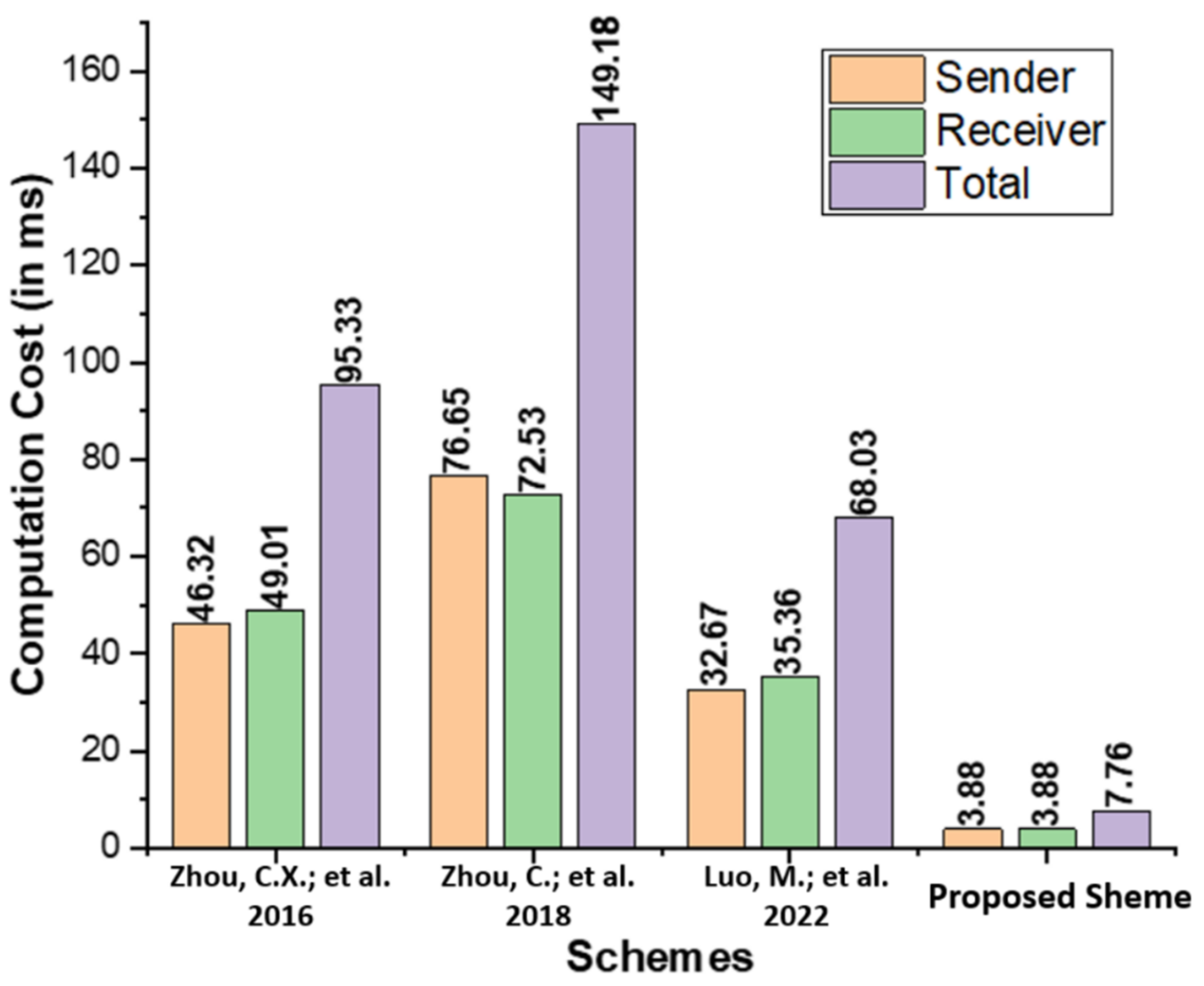
5.1. Computation Cost
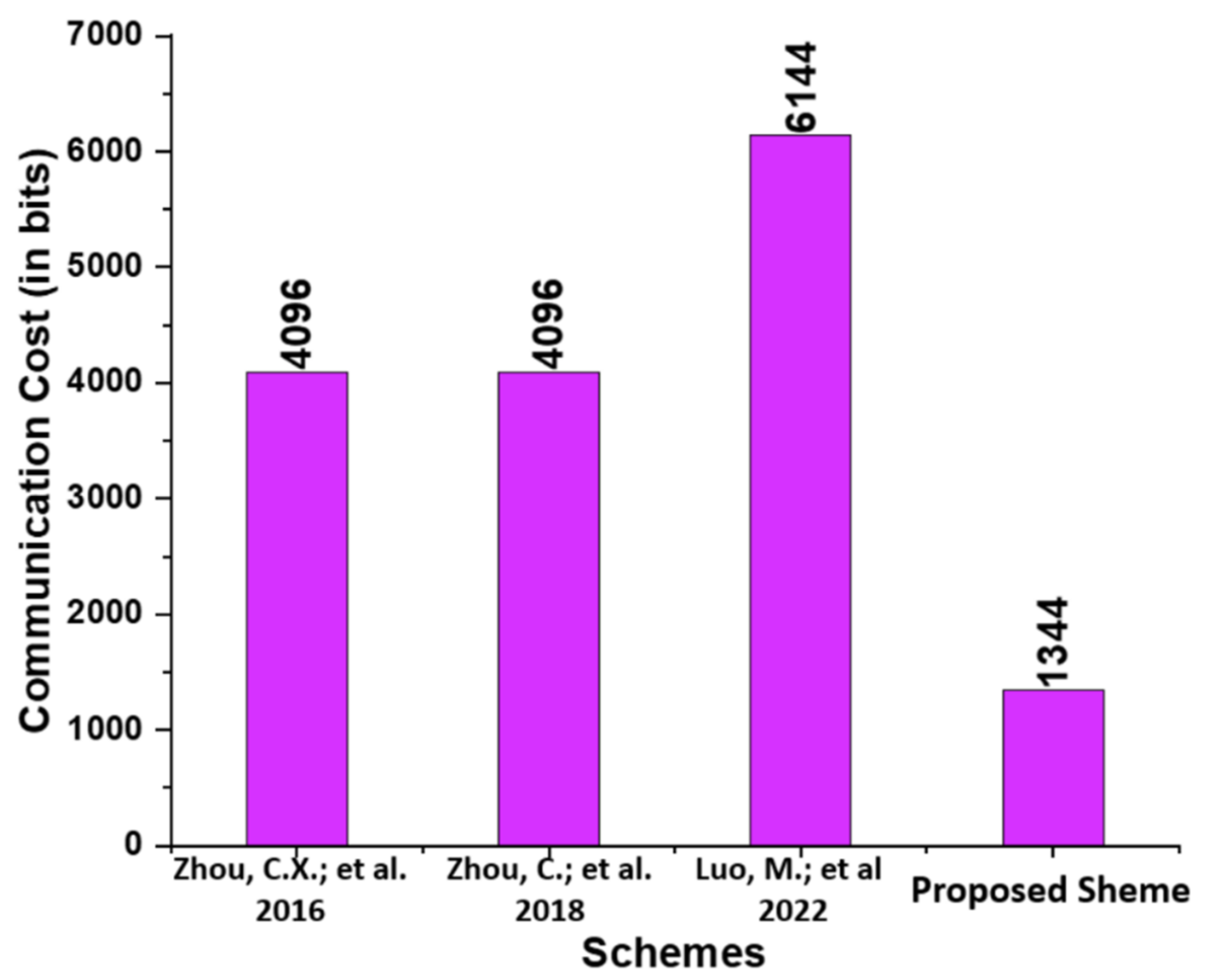
5.2. Communication Cost
5.3. Memory Overhead
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Mohsan, S.A.H.; Othman, N.Q.H.; Khan, M.A.; Amjad, H.; Żywiołek, J. A Comprehensive Review of Micro UAV Charging Techniques. Micromachines 2022, 13, 977. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.; Chen, S.W.; Nardari, G.V.; Qu, C.; Ojeda, F.C.; Taylor, C.J.; Kumar, V. Challenges and Opportunities for Autonomous Micro-UAVs in Precision Agriculture. IEEE Micro 2022, 42, 61–68. [Google Scholar] [CrossRef]
- Ahmed, F.; Mohanta, J.C.; Keshari, A.; Yadav, P.S. Recent Advances in Unmanned Aerial Vehicles: A Review. Arab. J. Sci. Eng. 2022, 47, 7963–7984. [Google Scholar] [CrossRef] [PubMed]
- Noor, F.; Khan, M.A.; Al-Zahrani, A.; Ullah, I.; Al-Dhlan, K.A. A Review on Communications Perspective of Flying Ad-Hoc Networks: Key Enabling Wireless Technologies, Applications, Challenges and Open Research Topics. Drones 2020, 4, 65. [Google Scholar] [CrossRef]
- Khan, M.A.; Kumar, N.; Mohsan, S.A.H.; Khan, W.U.; Nasralla, M.M.; Alsharif, M.H.; Zywiolek, J.; Ullah, I. Swarm of UAVs for Network Management in 6G: A Technical Review. IEEE Trans. Netw. Serv. Manag. 2022. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Alkhalifah, A.; Rehman, S.U.; Shah, J.A.; Uddin, I.I.; Alsharif, M.H.; Algarni, F. A Provable and Privacy-Preserving Authentication Scheme for UAV-Enabled Intelligent Transportation Systems. IEEE Trans. Ind. Inform. 2021, 18, 3416–3425. [Google Scholar] [CrossRef]
- Krishna, C.G.L.; Murphy, R.R. A review on cybersecurity vulnerabilities for unmanned aerial vehicles. In Proceedings of the 2017 IEEE International Symposium on Safety, Security and Rescue Robotics (SSRR), Shanghai, China, 11–13 October 2017; pp. 194–199. [Google Scholar]
- Guo, Y.; Wu, M.; Tang, K.; Tie, J.; Li, X. Covert Spoofing Algorithm of UAV Based on GPS/INS-Integrated Navigation. IEEE Trans. Veh. Technol. 2019, 68, 6557–6564. [Google Scholar] [CrossRef]
- Eldosouky, A.R.; Ferdowsi, A.; Saad, W. Drones in Distress: A Game-Theoretic Countermeasure for Protecting UAVs Against GPS Spoofing. IEEE Internet Things J. 2019, 7, 2840–2854. [Google Scholar] [CrossRef] [Green Version]
- Arteaga, S.P.; Hernandez, L.A.M.; Perez, G.S.; Orozco, A.L.S.; Villalba, L.J.G. Analysis of the GPS Spoofing Vulnerability in the Drone 3DR Solo. IEEE Access 2019, 7, 51782–51789. [Google Scholar] [CrossRef]
- Zheng, Y. Digital signcryption or how to achieve cost (signature & encryption) << cost (signature) + cost (encryption). In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 17–21 August 1997; Springer: Berlin/Heidelberg, Germany, 1997; pp. 165–179. [Google Scholar]
- Han, Y.; Yang, X.; Wei, P.; Wang, Y.; Hu, Y. ECGSC: Elliptic curve based generalized signcryption. In Proceedings of the Third International Conference Ubiquitous Intelligence and Computing of Lecture Notes in Computer Science, Wuhan, China, 3–6 September 2006; Springer: Berlin/Heidelberg, Germany, 2006; Volume 4159, pp. 956–965. [Google Scholar]
- Wang, L.; Zhang, G.; Ma, C. A Secure Ring Signcryption Scheme for Private and Anonymous Communication. In Proceedings of the 2007 IFIP International Conference on Network and Parallel Computing Workshops (NPC 2007), Dalian, China, 18–21 September 2007; Springer: Berlin/Heidelberg, Germany, 1997; pp. 107–111. [Google Scholar]
- Zhou, C.X.; Cui, Z.M.; Gao, G.Y. Efficient identity-based generalized ring signcryption scheme. KSII Trans. Internet Inf. Syst. 2016, 10, 5553–5571. [Google Scholar]
- Zhou, C.; Gao, G.; Cui, Z.; Zhao, Z. Certificate-based generalized ring signcryption scheme. Int. J. Found. Comput. Sci. 2018, 29, 1063–1088. [Google Scholar] [CrossRef]
- Luo, M.; Zhou, Y. An Efficient Conditional Privacy-preserving Authentication Protocol Based on Generalized Ring Signcryption for VANETs. IEEE Trans. Veh. Technol. 2022, 71, 10001–10015. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Nisar, S.; Noor, F.; Qureshi, I.M.; Khanzada, F.; Khattak, H.; Aziz, M.A. Multi-access Edge Computing (MEC) Enabled Flying Ad-hoc Networks with Secure Deployment Using Identity Based Generalized Signcryption. Mob. Inf. Syst. 2020, 2020, 8861947. [Google Scholar]
- Din, N.; Waheed, A.; Zareei, M.; Alanazi, F. An Improved Identity-Based Generalized Signcryption Scheme for Secure Multi-Access Edge Computing Empowered Flying Ad Hoc Networks. IEEE Access 2021, 9, 120704–120714. [Google Scholar] [CrossRef]
- Khan, M.A.; Ullah, I.; Alsharif, M.H.; Alghtani, A.H.; Aly, A.A.; Chen, C.M. An Efficient Certificate-Based Aggregate Signature Scheme for Internet of Drones. Secur. Commun. Netw. 2022, 2022, 9718580. [Google Scholar] [CrossRef]
- Shamus Sofware Ltd. Miracl Library. Available online: http://github.com/miracl/MIRACL (accessed on 2 August 2022).
- Zhou, C.; Zhao, Z.; Zhou, W.; Mei, Y. Certificateless Key-Insulated Generalized Signcryption Scheme without Bilinear Pairings. Secur. Commun. Netw. 2017, 2017, 8405879. [Google Scholar] [CrossRef]


| S. No | Notation | Descriptions |
|---|---|---|
| 1 | GCN | Ground core network |
| 2 | PKG | Private key generator |
| 3 | Public parameter param | |
| 4 | , | Irreversible and collision resistant hash functions |
| 5 | Master secret key of ground core network | |
| 6 | Master public key of ground core network | |
| 7 | Generator of group | |
| 8 | Finite cyclic group on the elliptic curve | |
| 9 | The elliptic curve defined on | |
| 10 | Encrypted identity of | |
| 11 | It represents a Micro Aerial Vehicle () | |
| 12 | Encrypted identity of everything () | |
| 13 | Real identity of | |
| 14 | Real identity of everything () | |
| 15 | Finite field on the elliptic curve of order | |
| 16 | Private key of | |
| 17 | Private key of everything () | |
| 18 | Public key of everything () | |
| 19 | Public key of | |
| 20 | Identities of ring group , | |
| 21 | Encryption and decryption key for real identity of | |
| 22 | Encryption and decryption key for real identity of everything () | |
| 23 | Encryption and decryption key for message and everything () | |
| 24 | Used for Encryption and decryption |
| Schemes | Sender | Receiver | Total |
|---|---|---|---|
| Zhou et al. [14] | |||
| Zhou et al. [15] | |||
| Luo and Zhou [16] | |||
| Proposed Scheme |
| Schemes | Sender | Receiver | Total |
|---|---|---|---|
| Zhou et al. [14] | |||
| Zhou et al. [15] | |||
| Luo and Zhou [16] | |||
| Proposed Scheme |
| Schemes | Communication Cost | Communication Cost in Bits |
|---|---|---|
| Zhou et al. [14] | ||
| Zhou et al. [15] | ||
| Luo and Zhou [16] | ||
| Proposed Scheme |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ullah, I.; Khan, M.A.; Abdullah, A.M.; Mohsan, S.A.H.; Noor, F.; Algarni, F.; Innab, N. A Conditional Privacy Preserving Generalized Ring Signcryption Scheme for Micro Aerial Vehicles. Micromachines 2022, 13, 1926. https://doi.org/10.3390/mi13111926
Ullah I, Khan MA, Abdullah AM, Mohsan SAH, Noor F, Algarni F, Innab N. A Conditional Privacy Preserving Generalized Ring Signcryption Scheme for Micro Aerial Vehicles. Micromachines. 2022; 13(11):1926. https://doi.org/10.3390/mi13111926
Chicago/Turabian StyleUllah, Insaf, Muhammad Asghar Khan, Ako Muhammad Abdullah, Syed Agha Hassnain Mohsan, Fazal Noor, Fahad Algarni, and Nisreen Innab. 2022. "A Conditional Privacy Preserving Generalized Ring Signcryption Scheme for Micro Aerial Vehicles" Micromachines 13, no. 11: 1926. https://doi.org/10.3390/mi13111926
APA StyleUllah, I., Khan, M. A., Abdullah, A. M., Mohsan, S. A. H., Noor, F., Algarni, F., & Innab, N. (2022). A Conditional Privacy Preserving Generalized Ring Signcryption Scheme for Micro Aerial Vehicles. Micromachines, 13(11), 1926. https://doi.org/10.3390/mi13111926