Exponential Stability of a Wave Equation with Boundary Delay Control
Abstract
:1. Introduction
2. Equivalence Between Systems (4) and (5)
2.1. The Transformation Between Systems (4) and (5)
2.2. The Solvability of Kernel Function Equations (8) and (10)
2.3. The Boundedness of Transformations (7) and (9)
3. Equivalence Between Systems (5) and (6)
3.1. The Transformation Between Systems (5) and (6)
3.2. The Solvability of Kernel Function Equations (14) and (17)
3.3. The Boundedness of Transformations (13) and (16)
4. The Stability of Systems (4) and (6)
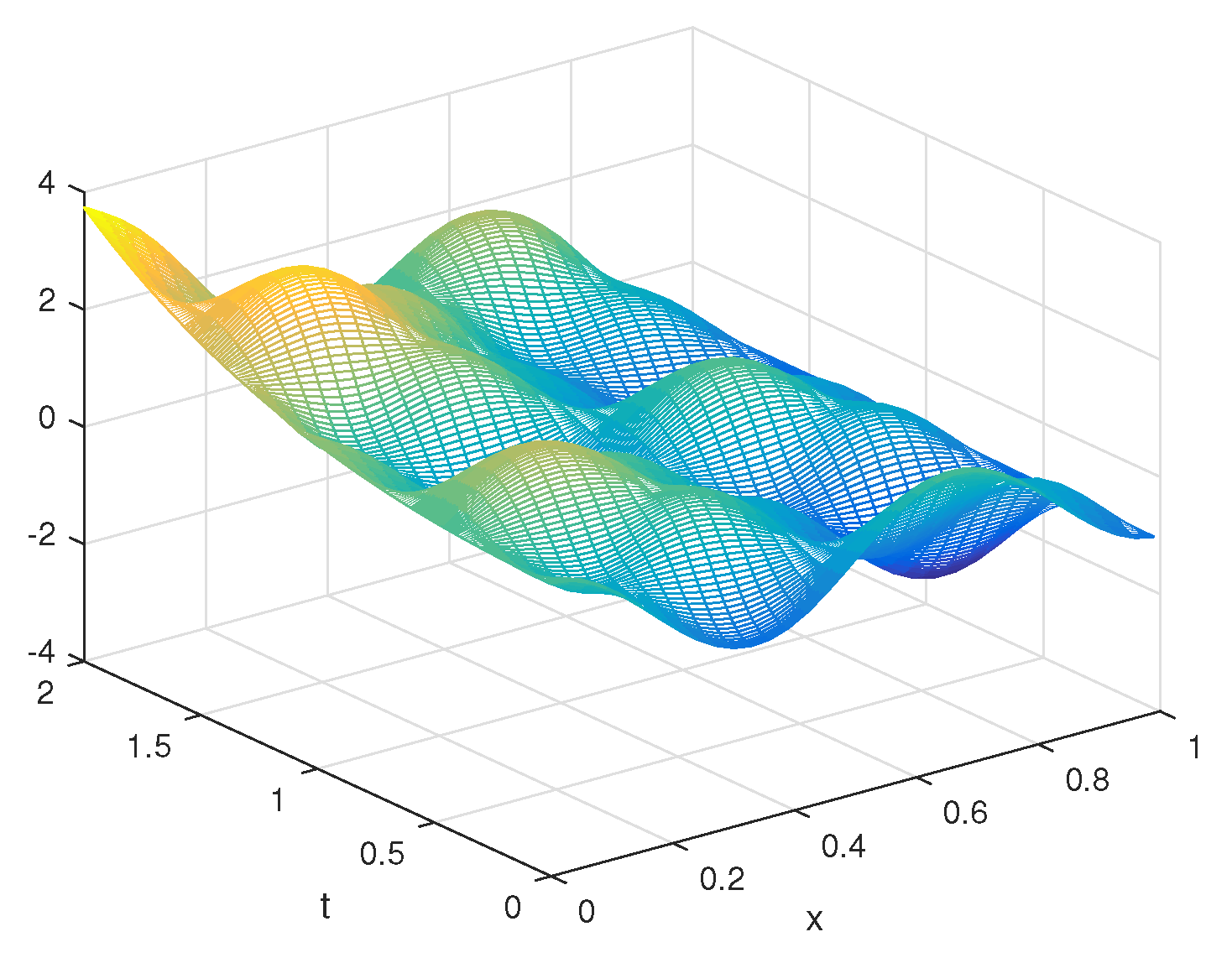
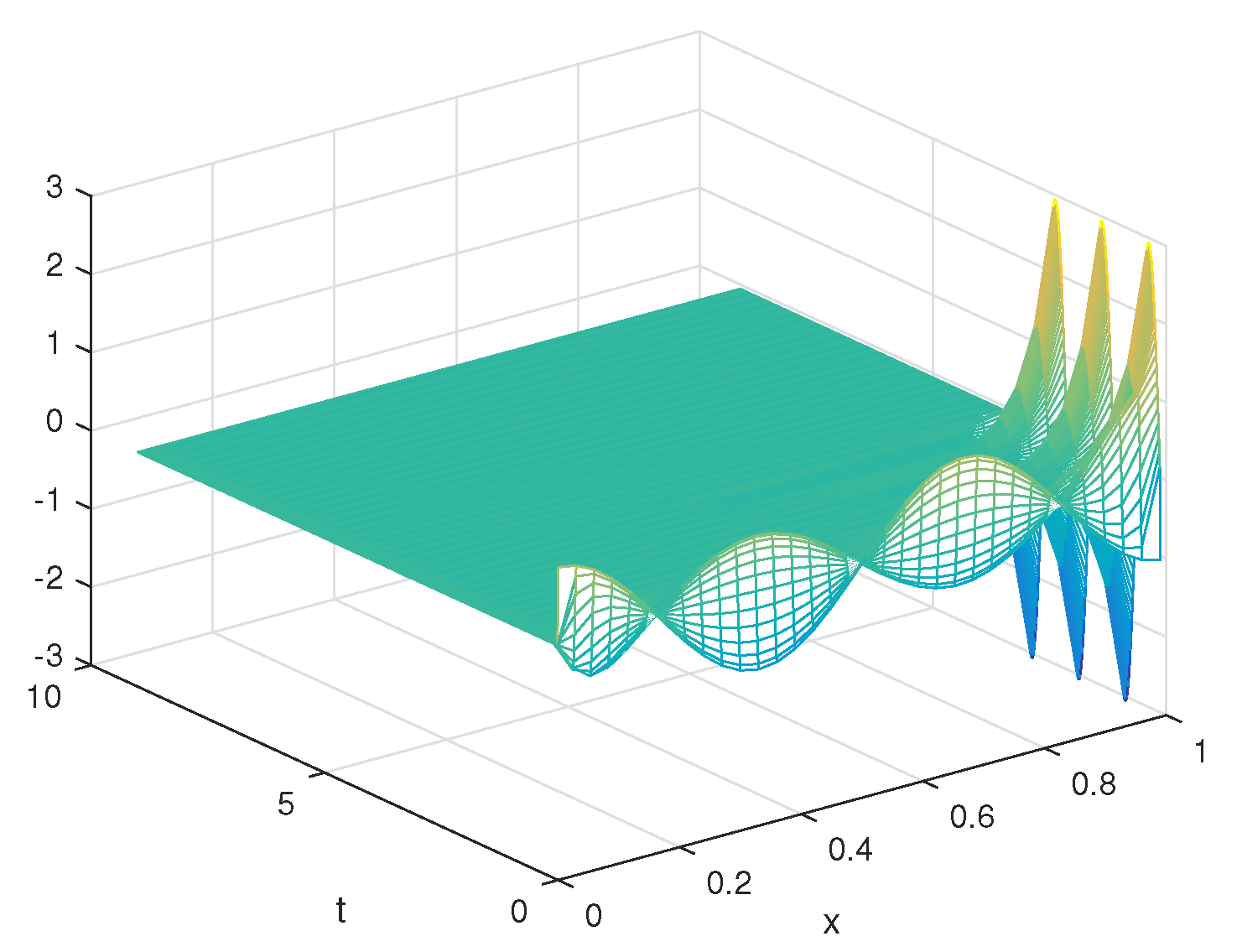
5. Numerical Results
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Russell, D.L. Mathematical models for the elastic beam and their control-theoretic implications. Semigroups. Theory Appl. 1986, 2, 177–216. [Google Scholar]
- Lions, J.L. Exact controllability, stabilization and perturbations for distributed systems. SIAM Rev. 1988, 30, 1–68. [Google Scholar]
- Malek-Zavarei, M.; Jamshidi, M. Time-Delay Systems: Analysis, Optimization and Applications; Elsevier Science Inc.: Amsterdam, The Netherlands, 1987. [Google Scholar]
- Michiels, W.; Niculescu, S.I. Stability and Stabilization of Time-Delay Systems: An Eigenvalue-Based Approach; SIAM: Bangkok, Thailand, 2007. [Google Scholar]
- Datko, R.; Lagnese, J.; Polis, M. An example on the effect of time delays in boundary feedback stabilization of wave equations. SIAM J. Control Optim. 1986, 24, 152–156. [Google Scholar]
- Datko, R. Two examples of ill-posedness with respect to small time delays in stabilized elastic systems. IEEE Trans. Autom. Control 1993, 38, 163–166. [Google Scholar]
- Logemann, H.; Rebarber, R.; Weiss, G. Conditions for robustness and nonrobustness of the stability of feedback systems with respect to small delays in the feedback loop. SIAM J. Control Optim. 1996, 34, 572–600. [Google Scholar]
- Brahmi, B.; Driscoll, M.; Laraki, M.H.; Brahmi, A. Adaptive high-order sliding mode control based on quasi-time delay estimation for uncertain robot manipulator. Control Theory Technol. 2020, 18, 279–292. [Google Scholar]
- Sheng, Z.; Guo, Y.; Xue, A.; Han, W. Multi-sensor multi-target bearing-only tracking with signal time delay. Signal, Image Video Process. 2023, 17, 4495–4502. [Google Scholar] [CrossRef]
- Xia, Y.; Zhang, X.; Xia, S.; Wu, M.; Feng, Y. Pathological basal ganglia oscillations with time delays: A memoryless feedback control strategy. Control Theory Technol. 2024, 22, 1–13. [Google Scholar]
- Komornik, V. On the Nonlinear Boundary Stabilization of the Wave-Equation. Chin. Ann. Math. Ser. 1993, 14, 153–164. [Google Scholar]
- Komornik, V. Rapid boundary stabilization of linear distributed systems. SIAM J. Control Optim. 1997, 35, 1591–1613. [Google Scholar]
- Lasiecka, I.; Triggiani, R. Control Theory for Partial Differential Equations: Continuous and Approximation Theories. Encyclopedia of Mathematics and its Applications; Cambridge University Press: Cambridge, UK, 2000. [Google Scholar]
- Kobayashi, T. Stabilization of infinite-dimensional undamped second order systems by using a parallel compensator. Ima J. Math. Control Inf. 2004, 1, 85–94. [Google Scholar]
- Xu, G.Q. Stabilization of string system with linear boundary feedback. Nonlinear Anal. Hybrid Syst. 2007, 1, 383–397. [Google Scholar]
- Rebarber, R.; Townley, S. Robustness with respect to delays for exponential stability of distributed parameter systems. SIAM J. Control Optim. 1998, 37, 230–244. [Google Scholar]
- Dastan, Z.; Tavakoli-Kakhki, M. Suppression of high order disturbances and tracking for nonchaotic systems: A time-delayed state feedback approach. Control Theory Technol. 2022, 20, 54–68. [Google Scholar]
- Guo, B.Z.; Xu, C.Z.; Hammouri, H. Output feedback stabilization of a one-dimensional wave equation with an arbitrary time delay in boundary observation. ESAIM Control Optim. Calc. Var. 2022, 18, 22–35. [Google Scholar]
- Lhachemi, H.; Prieur, C. Boundary output feedback stabilisation of a class of reaction–diffusion PDEs with delayed boundary measurement. Int. J. Control 2023, 96, 2285–2295. [Google Scholar]
- Xu, G.Q.; Yung, S.P.; Li, L.K. Stabilization of wave systems with input delay in the boundary control. ESAIM Control Optim. Calc. Var. 2006, 12, 770–785. [Google Scholar]
- Nicaise, S.; Pignotti, C. Stability and instability results of the wave equation with a delay term in the boundary or internal feedbacks. SIAM J. Control Optim. 2006, 45, 1561–1585. [Google Scholar]
- Shang, Y.F.; Xu, G.Q. Stabilization of an Euler–Bernoulli beam with input delay in the boundary control. Syst. Control Lett. 2012, 61, 1069–1078. [Google Scholar]
- Wang, H.; Xu, G.Q. Exponential stabilization of 1-d wave equation with input delay. WSEAS Trans. Math. 2013, 12, 1001–1013. [Google Scholar]
- Liu, X.F.; Xu, G.Q. Exponential stabilization for Timoshenko beam with distributed delay in the boundary control. Abstr. Appl. Anal. 2013, 2013, 726794. [Google Scholar] [CrossRef]
- Han, Z.J.; Xu, G.Q. Output-based stabilization of Euler–Bernoulli beam with time-delay in boundary input. IMA J. Math. Control Inf. 2014, 31, 533–550. [Google Scholar] [CrossRef]
- Shang, Y.F.; Xu, G.Q. Dynamic feedback control and exponential stabilization of a compound system. J. Math. Anal. Appl. 2015, 422, 858–879. [Google Scholar] [CrossRef]
- Guo, Y.; Xu, G.; Guo, Y. Stabilization of the wave equation with interior input delay and mixed Neumann-Dirichlet boundary. Discret. Contin. Dyn. Syst.-B 2016, 21, 2491–2507. [Google Scholar] [CrossRef]
- Liu, X.P.; Xu, G.Q. Integral-Type Feedback Controller and Application to the Stabilization of Heat Equation with Boundary Input Delay. WSEAS Trans 2018, 17, 311–318. [Google Scholar]
- Feng, X.; Xu, G.; Chen, Y. Rapid stabilisation of an Euler–Bernoulli beam with the internal delay control. Int. J. Control 2019, 92, 42–55. [Google Scholar]
- Chen, H.; Xie, Y.; Genqi, X. Rapid stabilisation of multi-dimensional Schrödinger equation with the internal delay control. Int. J. Control 2019, 92, 2521–2531. [Google Scholar]
- Liu, X.P.; Xu, G.Q. Solvability of the nonlocal initial value problem and application to design of controller for heat-equation with delay. J. Math. Study 2019, 52, 127–159. [Google Scholar]
- Zhang, L.; Xu, G.Q.; Chen, H. Uniform stabilization of 1-d wave equation with anti-damping and delayed control. J. Frankl. Inst. 2020, 357, 12473–12494. [Google Scholar] [CrossRef]
- Xu, G.Q.; Zhang, L. Uniform stabilization of 1-D coupled wave equations with anti-dampings and joint delayed control. SIAM J. Control Optim. 2020, 58, 3161–3184. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, G.Q.; Mastorakis, N.E. A new approach for stabilization of Heat-ODE cascaded systems with boundary delayed control. IMA J. Math. Control Inf. 2022, 39, 112–131. [Google Scholar]
- Xie, Y.; Chen, Y. Rapid Stabilization of Timoshenko Beam System with the Internal Delay Control. Acta Appl. Math. 2023, 186, 7. [Google Scholar] [CrossRef]
- Pazy, A. Semigroups of Linear Operators and Applications to Partial Differential Equations; Springer-Verlag: Berlin/Heidelberg, Germany, 1983. [Google Scholar]
- Smyshlyaev, A.; Cerpa, E.; Krstic, M. Boundary Stabilization of a 1-D Wave Equation with In-Domain Antidamping. SIAM J. Control Optim. 2010, 48, 4014–4031. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xie, Y.; Tian, C.; Li, Y. Exponential Stability of a Wave Equation with Boundary Delay Control. Axioms 2025, 14, 280. https://doi.org/10.3390/axioms14040280
Xie Y, Tian C, Li Y. Exponential Stability of a Wave Equation with Boundary Delay Control. Axioms. 2025; 14(4):280. https://doi.org/10.3390/axioms14040280
Chicago/Turabian StyleXie, Yaru, Congyue Tian, and Yanfang Li. 2025. "Exponential Stability of a Wave Equation with Boundary Delay Control" Axioms 14, no. 4: 280. https://doi.org/10.3390/axioms14040280
APA StyleXie, Y., Tian, C., & Li, Y. (2025). Exponential Stability of a Wave Equation with Boundary Delay Control. Axioms, 14(4), 280. https://doi.org/10.3390/axioms14040280





