A Trust-Influenced Smart Grid: A Survey and a Proposal
Abstract
:1. Introduction
- We present a mathematical formalization of trust within the context of Smart Grid devices.
- We categorize the existing trust-based literature within the Smart Grid under the NIST conceptual domains and priority areas, multi-agent systems, and the derived trust formalization.
- We present a proposed novel substation-based trust model and implement a Modbus variation to detect final-phase attacks. We believe other protocol variants of the trust model can be created and developing these will be addressed in future work.
- The variation is tested against two publicly available Modbus datasets (EPM and ATENA H2020) under three kinds of tests, namely external, internal, and internal with IP-MAC blocking.
- The tests were performed from a Modbus server’s point of view and a Modbus client’s point of view.
- All attacks were detected and the behaviour of attacks was revealed based on their impact on the trust model’s components.
2. NIST Priority Areas on Smart Grid
2.1. Energy Storage
2.2. Wide-Area Situational Awareness (WASA)
2.3. Advanced Metering Infrastructure (AMI)
2.4. Distributed Energy Resources (DERs)
2.5. Distribution Grid Management
2.6. Network Communications
2.7. Demand Response and Consumer Energy Efficiency
2.8. Electric Transportation
2.9. Cybersecurity
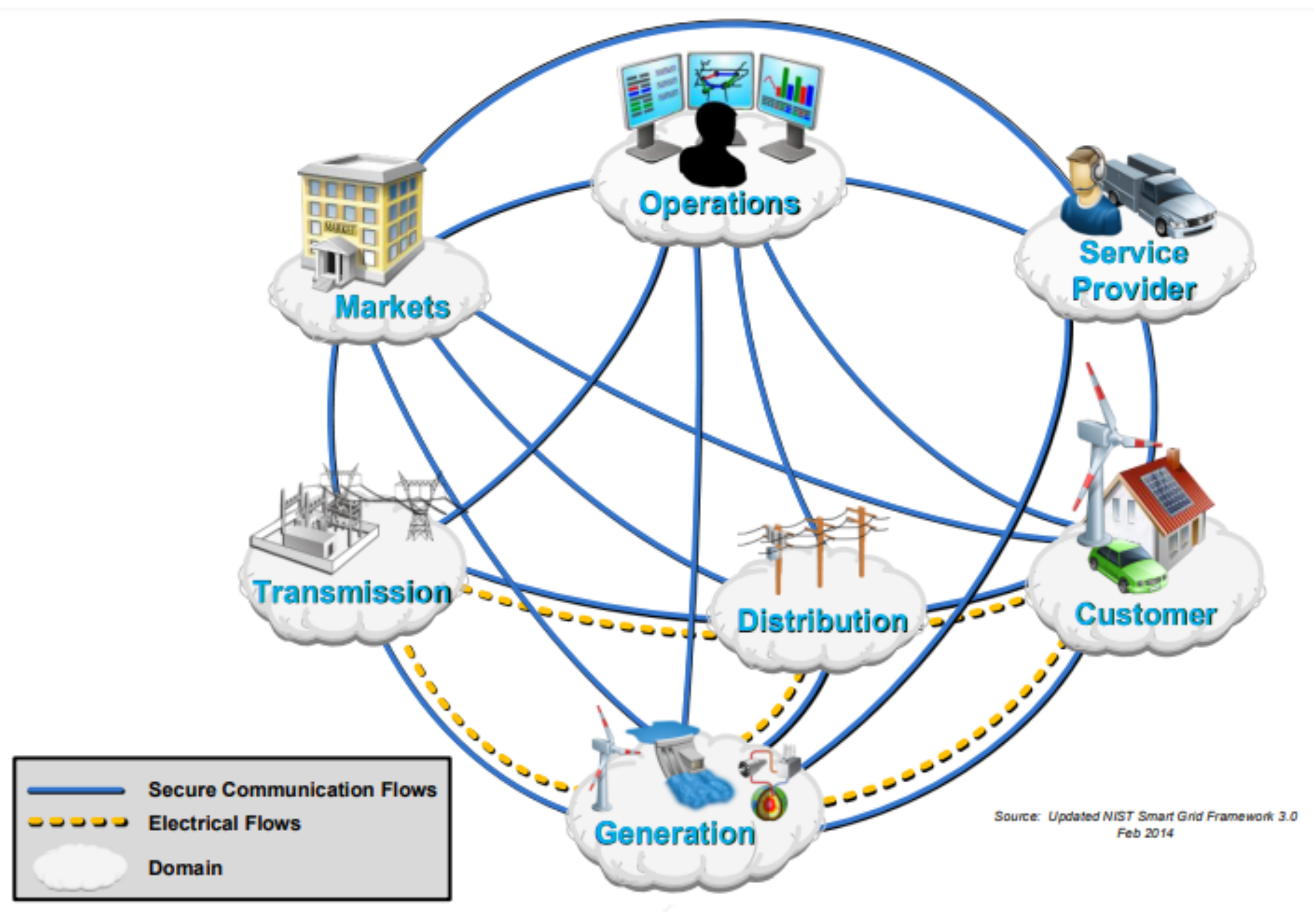
3. NIST Conceptual Domain Model
3.1. Generation Domain
3.2. Transmission Domain
3.3. Distribution Domain
3.4. Operations Domain
3.5. Service Provider Domain
3.6. Markets Domain
3.7. Customer Domain
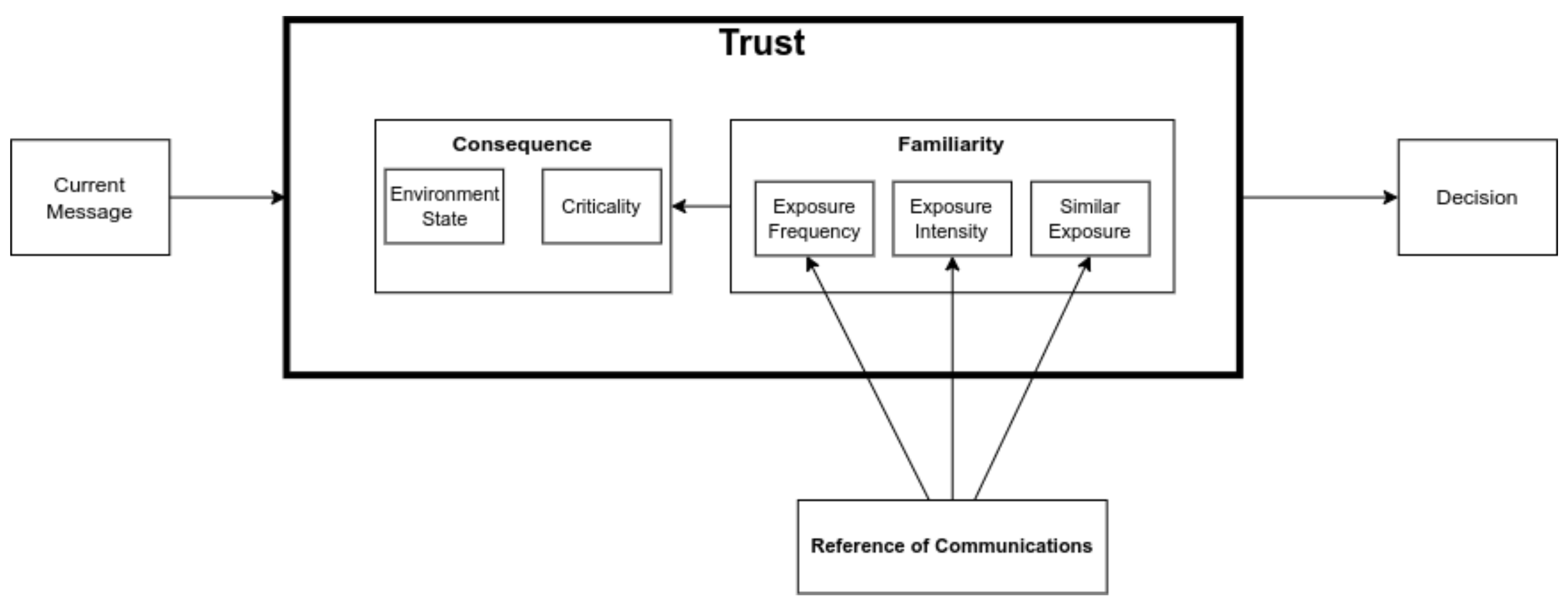
4. Trust
4.1. Trust Definition and Formalization
4.2. Trust-Based Attacks
- Misleading feedback attack: In this attack, a compromised agent feeds bad reports or recommendations to other nodes to denigrate agents with good reputations. It is also known as bad-mouthing attack or betrayal attack.
- Sybil attack: This attack involves a malicious agent within the system creating fake identities to create a larger influence over other agents using false rankings.
- Newcomer attack: This attack involves the malicious agent reintroducing itself as a new agent within the system in an attempt to erase its history of bad scores.
- Ballot-stuffing attack: In this attack, malicious agents collude by providing inaccurate recommendations or reports in an attempt to take over the system. It is also known as collusion attack.
- On–off attack: This attack involves a malicious agent repeatedly switching between being honest and dishonest in an attempt to be undetected. It is also known as inconsistency attack.
5. Trust: State of the Art in Smart Grid
5.1. Research Areas
5.2. Discussion
6. Trust: State of the Art in Substations
6.1. Research Areas
6.2. Discussion
7. Multi-Agent Systems (MASs)
7.1. MAS Tools
7.1.1. JADE
7.1.2. ZEUS
7.1.3. VOLTTRON
7.1.4. Aglets
7.1.5. JACK
8. MASs with Trust in the Smart Grid
8.1. Research Areas
8.2. Discussion
9. Motivation
| Algorithm 1 Pseudo-algorithm for trust computation for agent device. |
|
10. Criticality
11. Models and Scenario
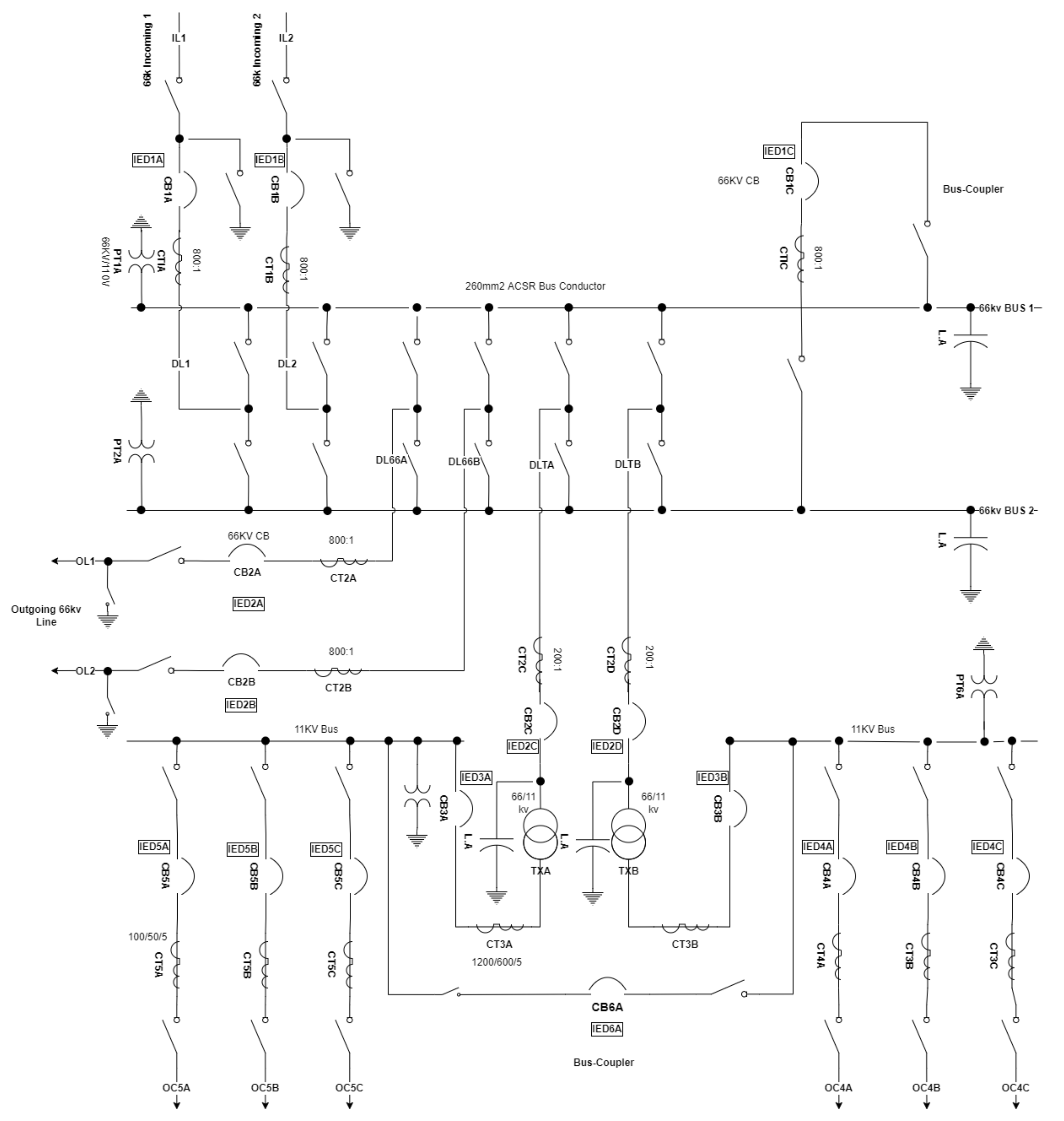
11.1. Substation Model
11.2. Attack Scenarios
11.2.1. Compromised Network,
- Man-in-the-middle (MitM) attack: (or ) impersonates a device to send or ;
- Maliciously crafting packets: (or ) sends maliciously crafted (or ) to drop a payload or trigger a buffer overflow;
- Query flooding: (or ) exhausts a device’s resources with a bombardment of or .
11.2.2. Compromised Client
- Reconnaissance: For , transmits to to all existing Modbus addresses.
- Loading Malicious Firmware: makes inaccessible by loading a malicious firmware. This can be performed by utilizing a device-specific software within SCADA or embedding malicious bytes in . The former option is not within the scope of this paper.
- Baseline Replay Attack: (or ) replays Q or R to a device after profiling the substation to avoid detection.
- Write attack: Without reconnaissance and for , is sent to to all existing Modbus addresses. Another scenario requires a completed reconnaissance attack. , where , is sent to target an address of a specific . It can be also executed after a baseline replay attack.
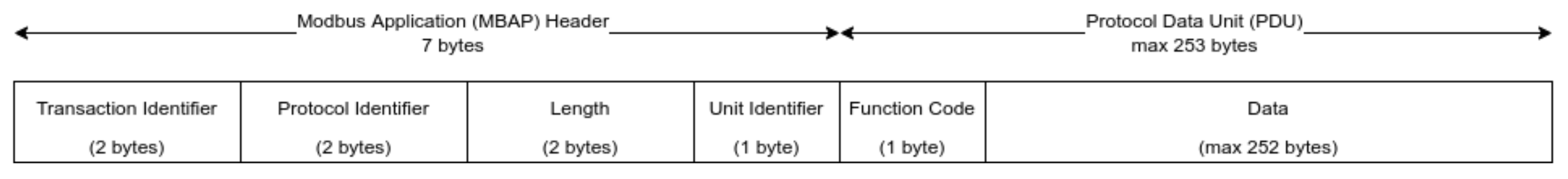
11.3. Modbus TCP
11.4. Familiarity-Based Definitions
11.4.1. Exposure Intensity
11.4.2. Similar Exposure
- defined in Equation (31) represents a set of states where each state represents or where is the initial state. Accept states are not required due endless transmissions of or .
- , defined in Equation (32), is a set of input alphabets extracted from or .
- is the transition function defined in Equation (33).
- A set of features, , is an output of (Equation (36)).
11.4.3. Exposure Frequency
- For , , .
- For , , .
- For , , .
- For , , .
- For , , , , .
- For , , , , .
- For , , , , .
- For , , , , .
- For , , ,
- For , , ,
- For , , ,
- For , , ,
- For , , , , .
- For , , , , .
- For , , .
- For , , .
11.4.4. Familiarity
11.5. Consequence-Based Definitions
11.5.1. Environment Status Attack Value
11.5.2. Replay Attack Value
11.5.3. Reconnaissance Attack Value
11.5.4. Query Flooding Attack Value
11.5.5. Packet Manipulation Attack Value
11.5.6. Consequence
11.6. Trust
12. Implementation
- The network communication of this substation is predictable because Q is pre-set by engineers.
- The pristineness of this substation; therefore, queries will be considered as malicious.
- The existence of a determinate number of devices inside the network of the substation for the Modbus communication; hence, H, is additionally bounded. These pairs can be categorised into two: the client group, , and the server group, . Additionally, is restricted from sending arbitrary responses. IP–MAC pairs outside this group are considered malicious and grouped as .
- Attacks that are neither Modbus nor IT-related are publicly disclosed by numerous CVE and CWE mitigation techniques; accordingly, they are considered outside of the sphere of the undertaking in this paper.
- The networking port utilized for Modbus communication by a device is restricted to the port number stated in the Modbus specification document.
- The attacker has penetrated the substation, achieved persistence, and has successfully evaded detection.
- The reference features (Equations (23), (36) and (44)) for the exposures in Section 11.4 were generated using the benign traffic captures of the two datasets.
- Based on established documentation of the datasets and careful analysis of every network capture file (pcap file) using Wireshark, , , and could be identified.
- From and , members that were compromised were grouped as . The rest of the members were the target devices, .
- Per each dataset, we concentrated on communications that were concerned with and generated sub-capture files containing their communication with the other groups.
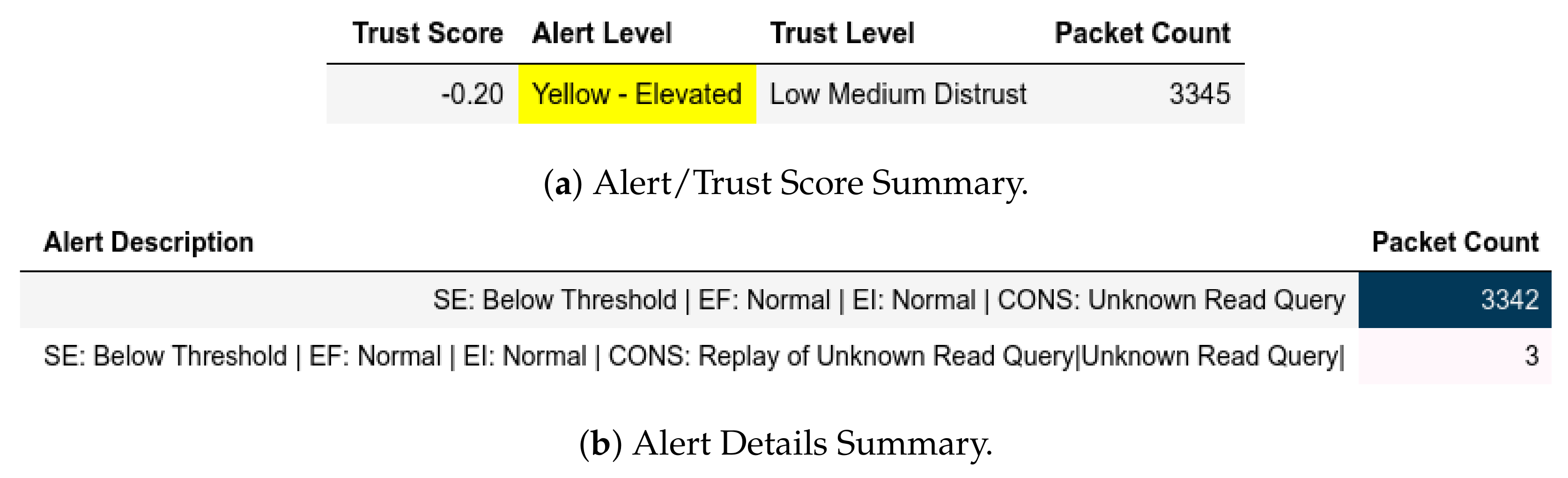
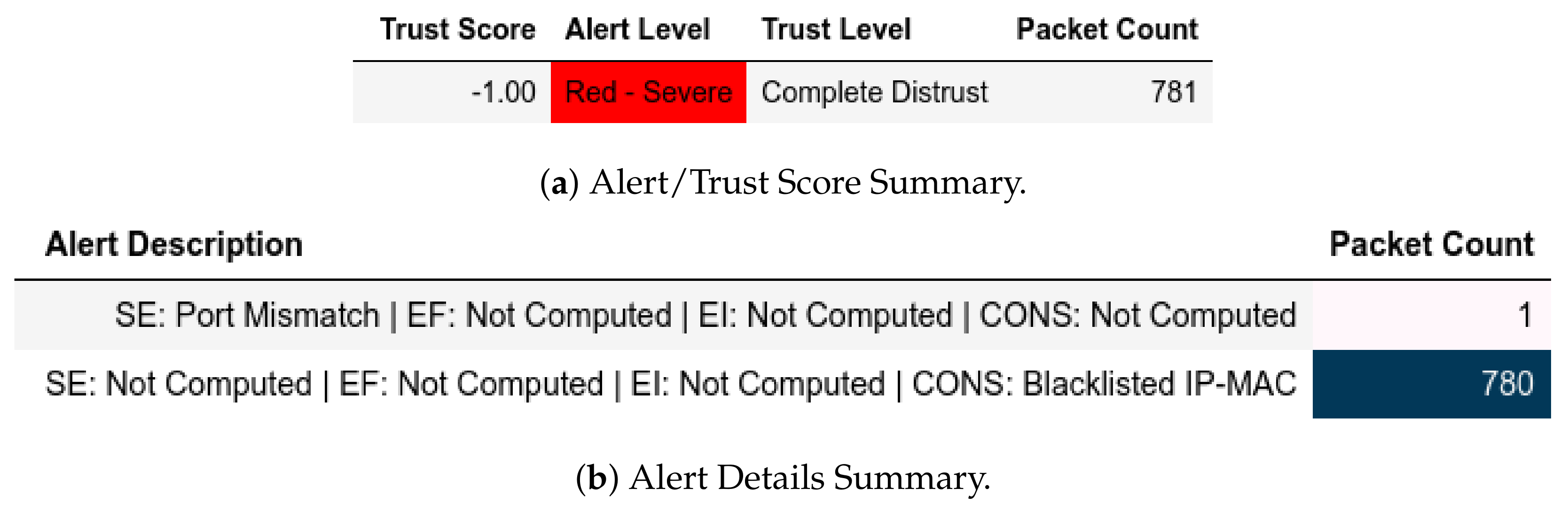
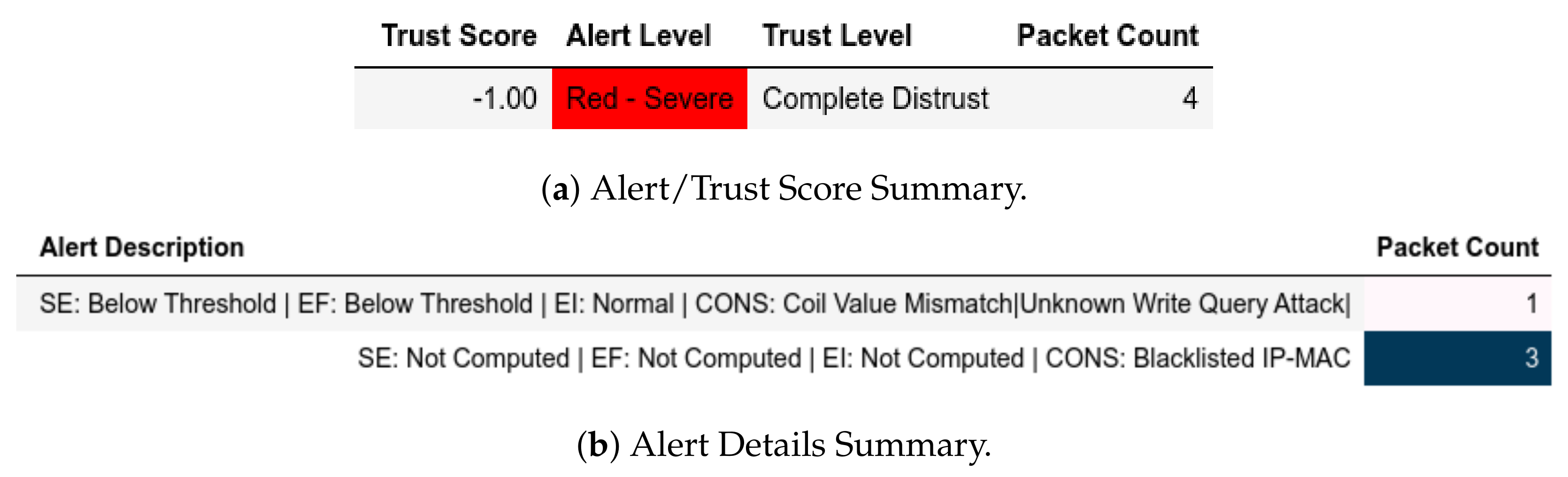
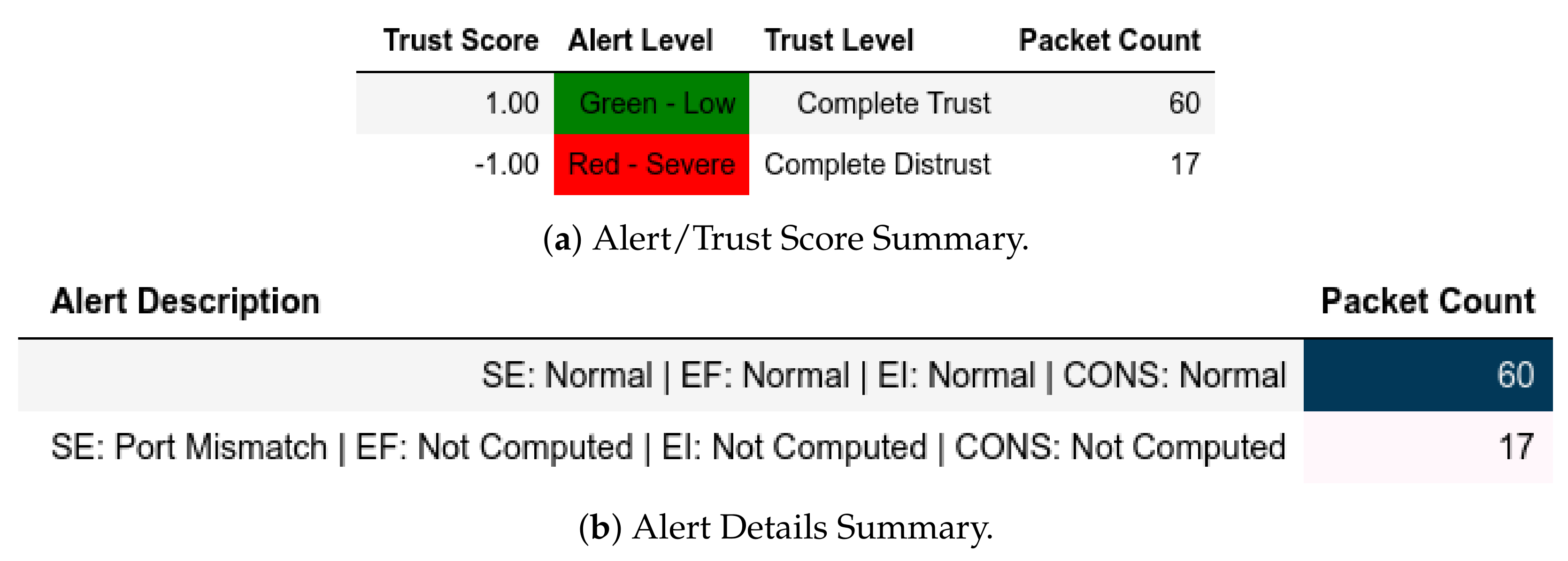
- External Attack Test: Here, the existing condition is maintained as , , and ; hence, complies with the attack scenario mentioned in Section 11.2.1. Evidently, the outcome is that or sent from will be flagged as expected without probing into the Modbus frame (see the first definition of Equation (43)).
- Internal Attack Test: For this test, we have (Equation (56)) and (Equation (57)) to depict as described in Section 11.2.2. Any or sent from these groups be flagged accordingly.
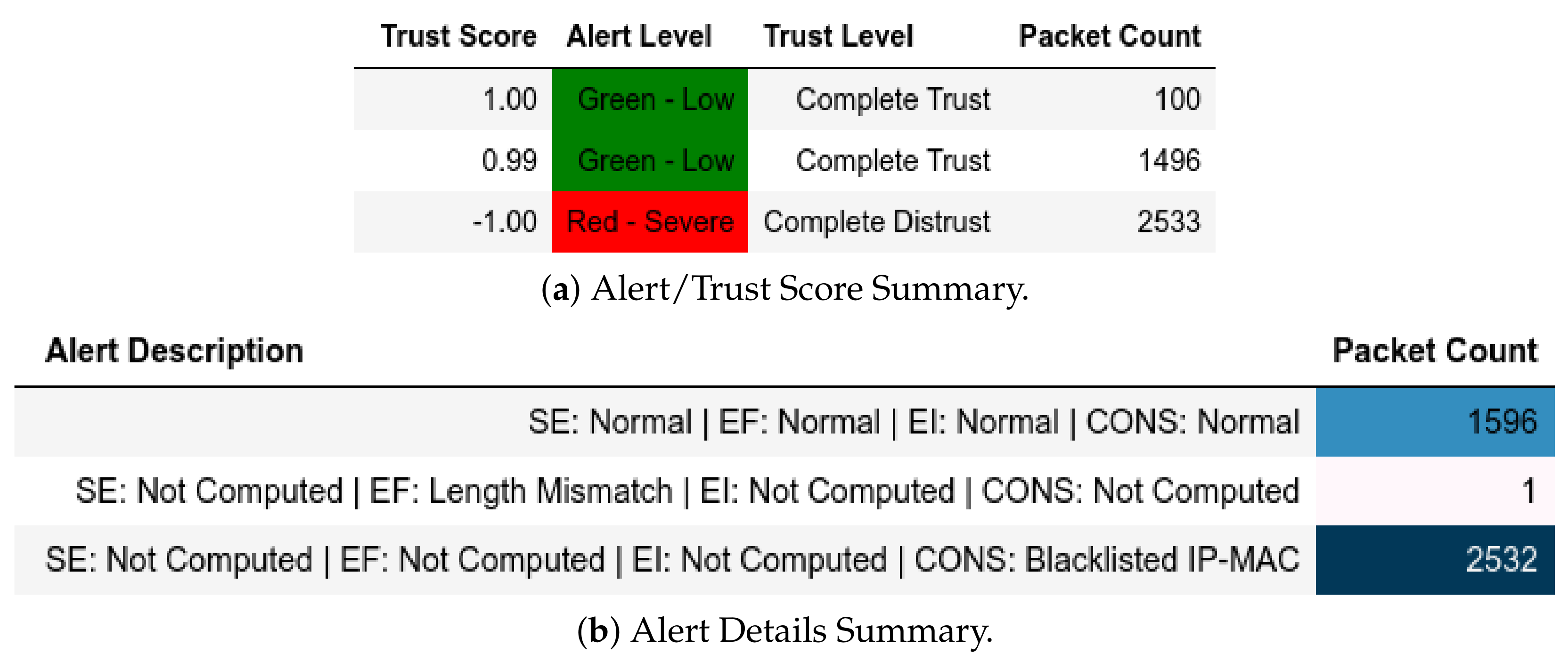
- Internal Attack Test with IP-MAC Blacklisting: The test and groups are the same as the internal test with the exception that any device that has is added to a group of blacklisted MAC-IP pairs, ; and is closed from further communication.
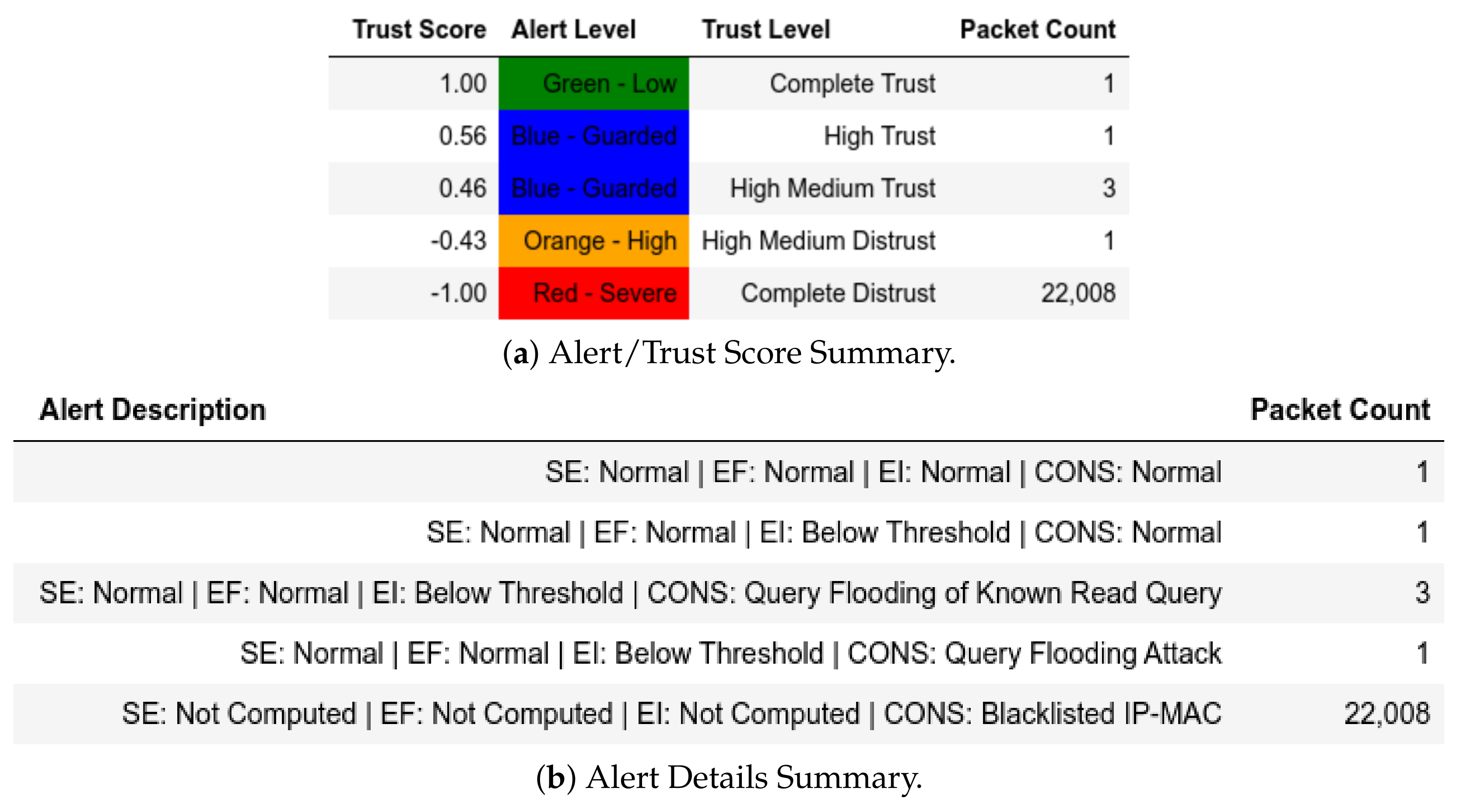
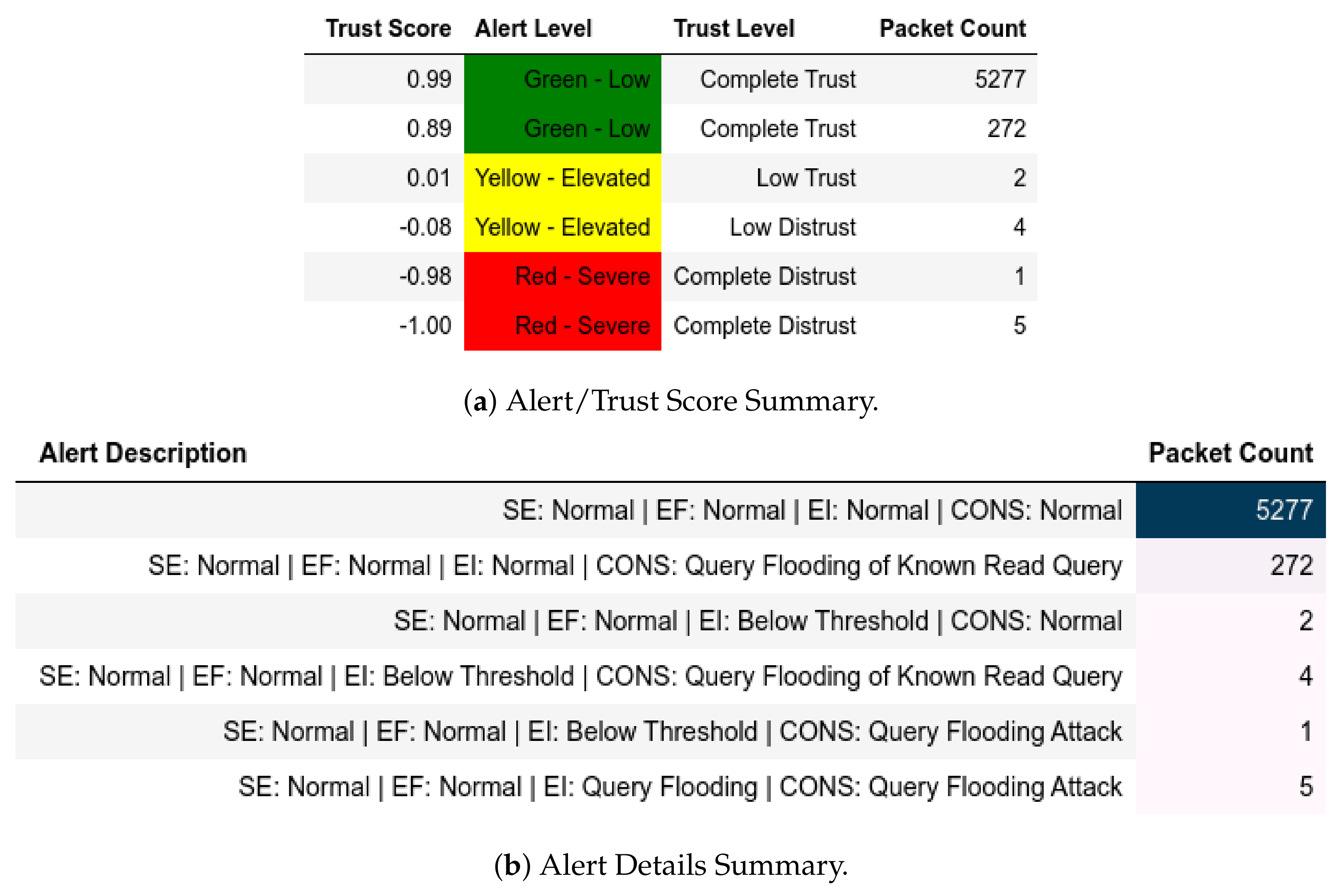
13. Evaluation
13.1. EPM Dataset
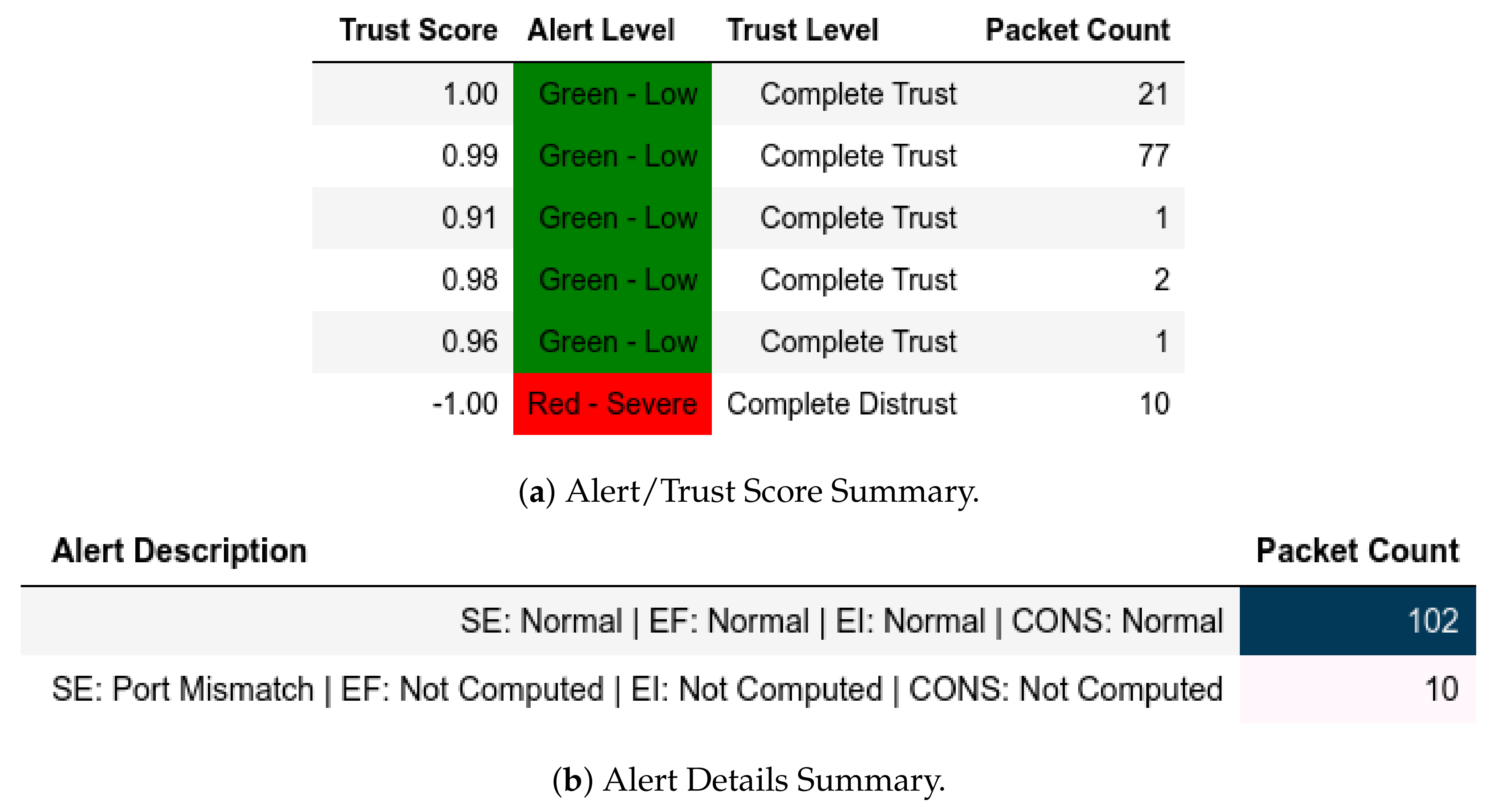
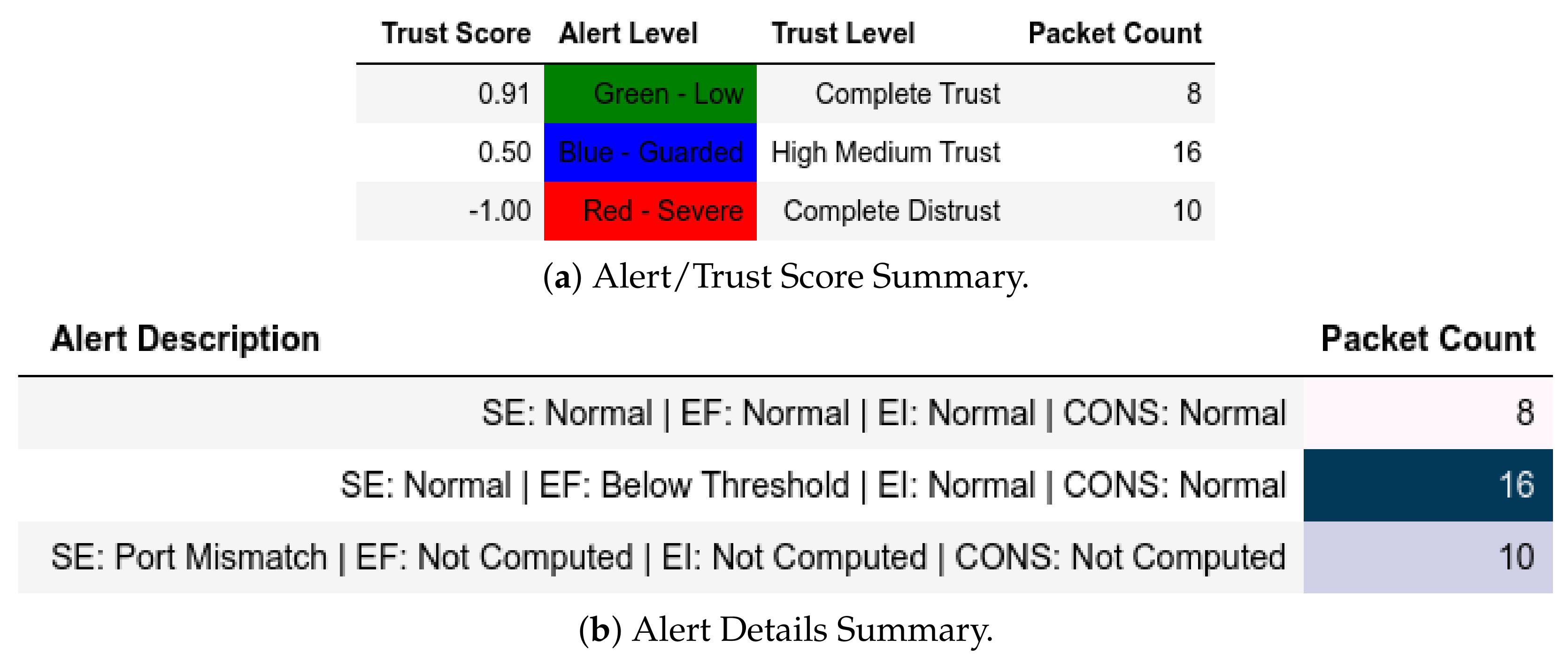
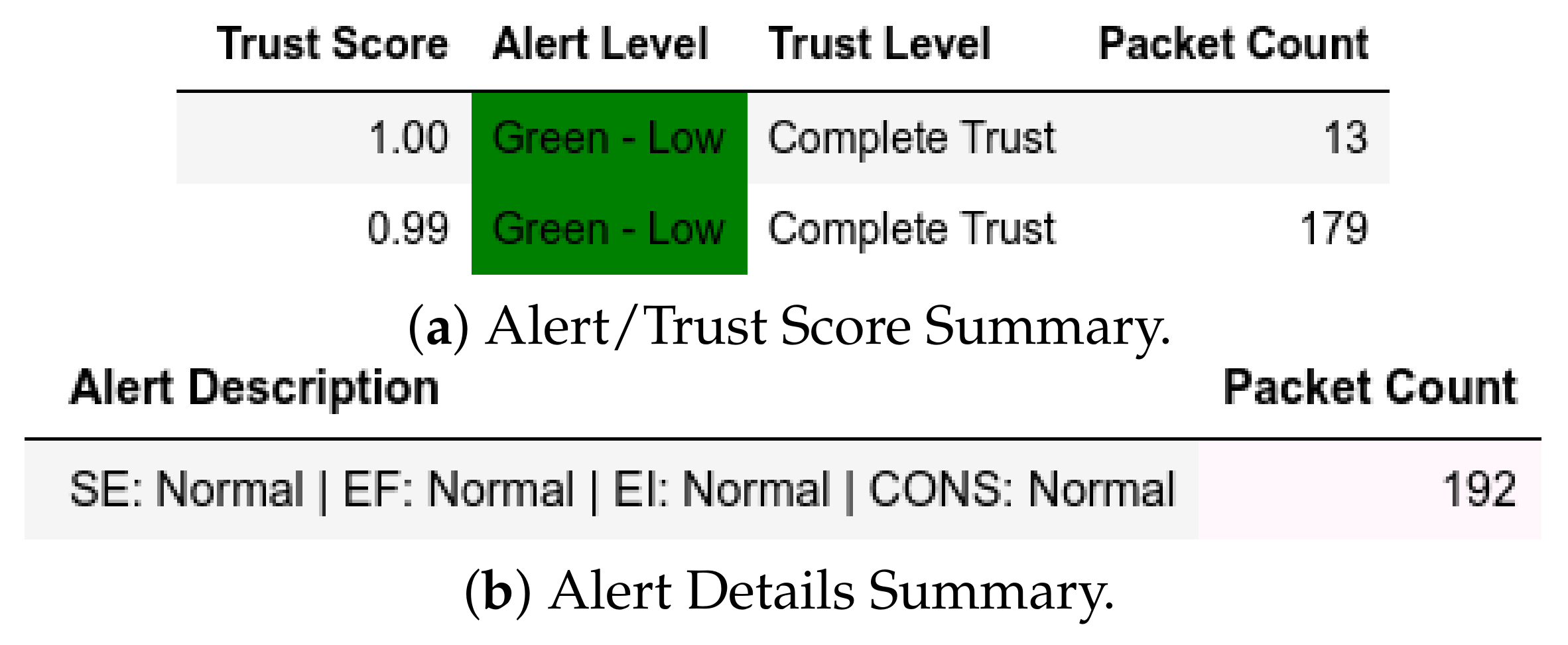
13.1.1. External Attack Test towards Server
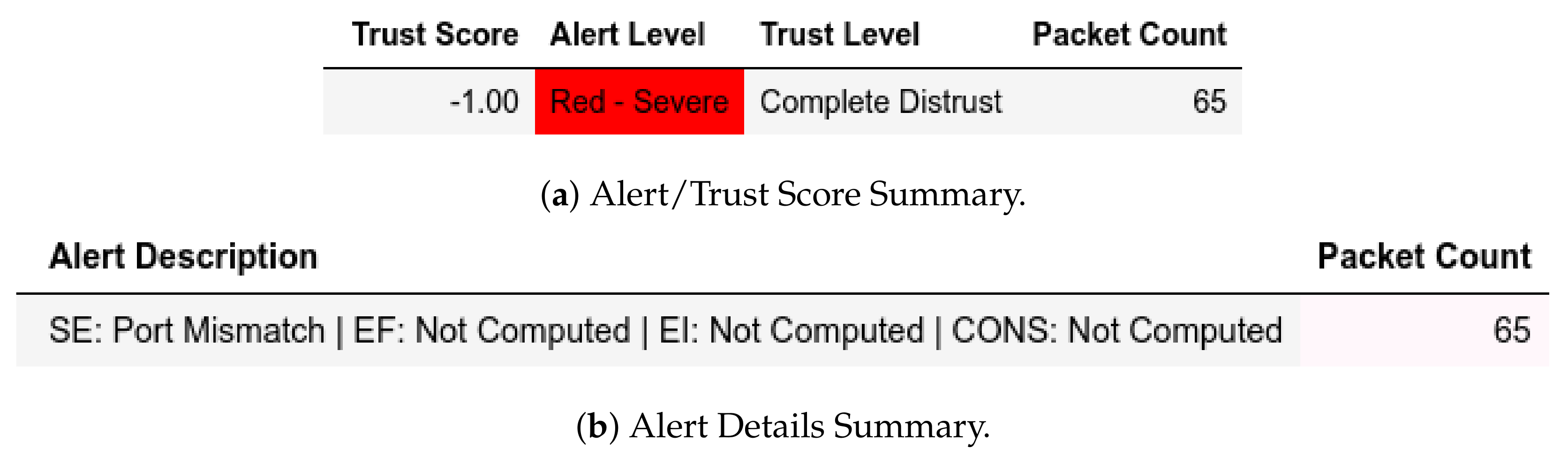
13.1.2. Internal Attack Test towards Server
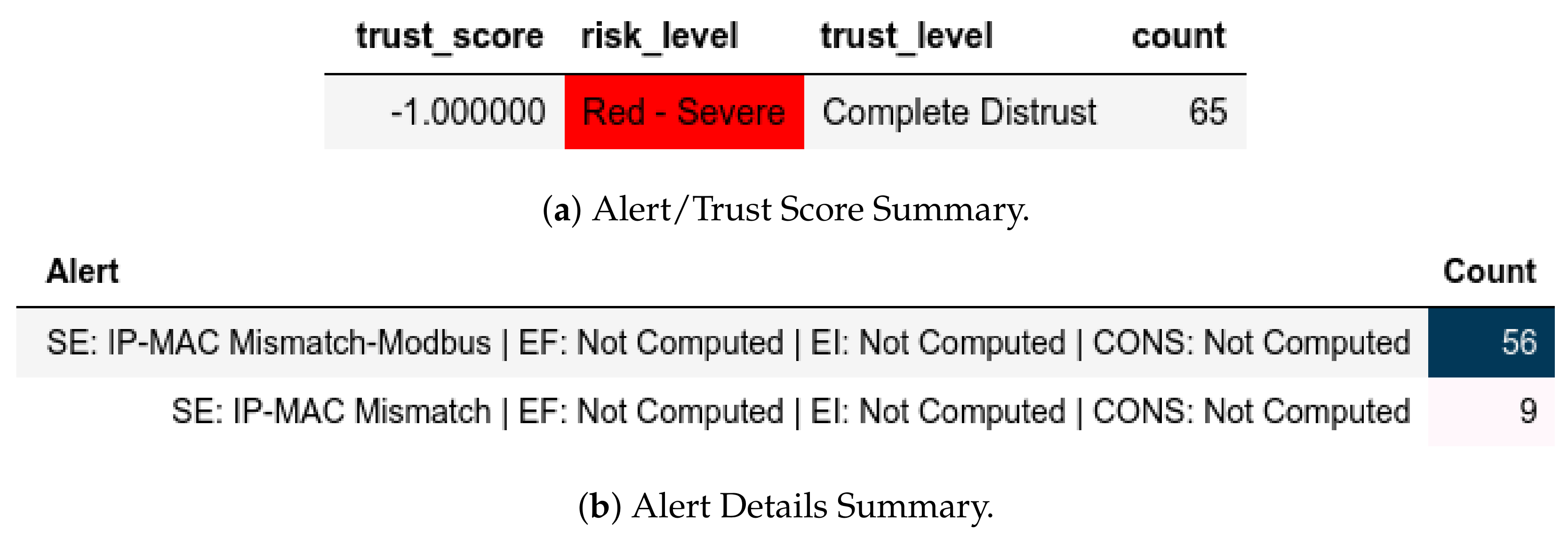
13.1.3. Internal Attack Test with IP-MAC Blacklisting towards Server
13.1.4. Internal Attack Test towards Client
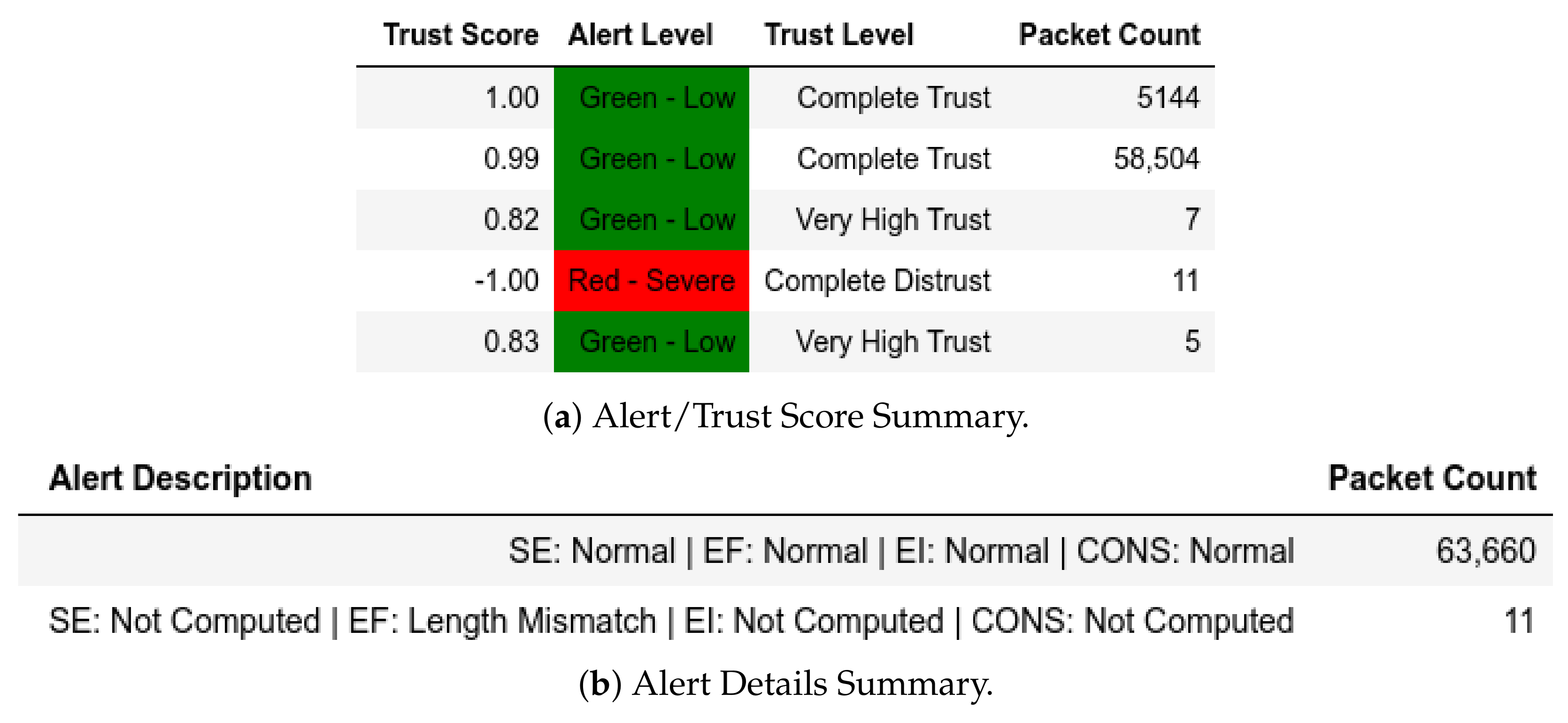
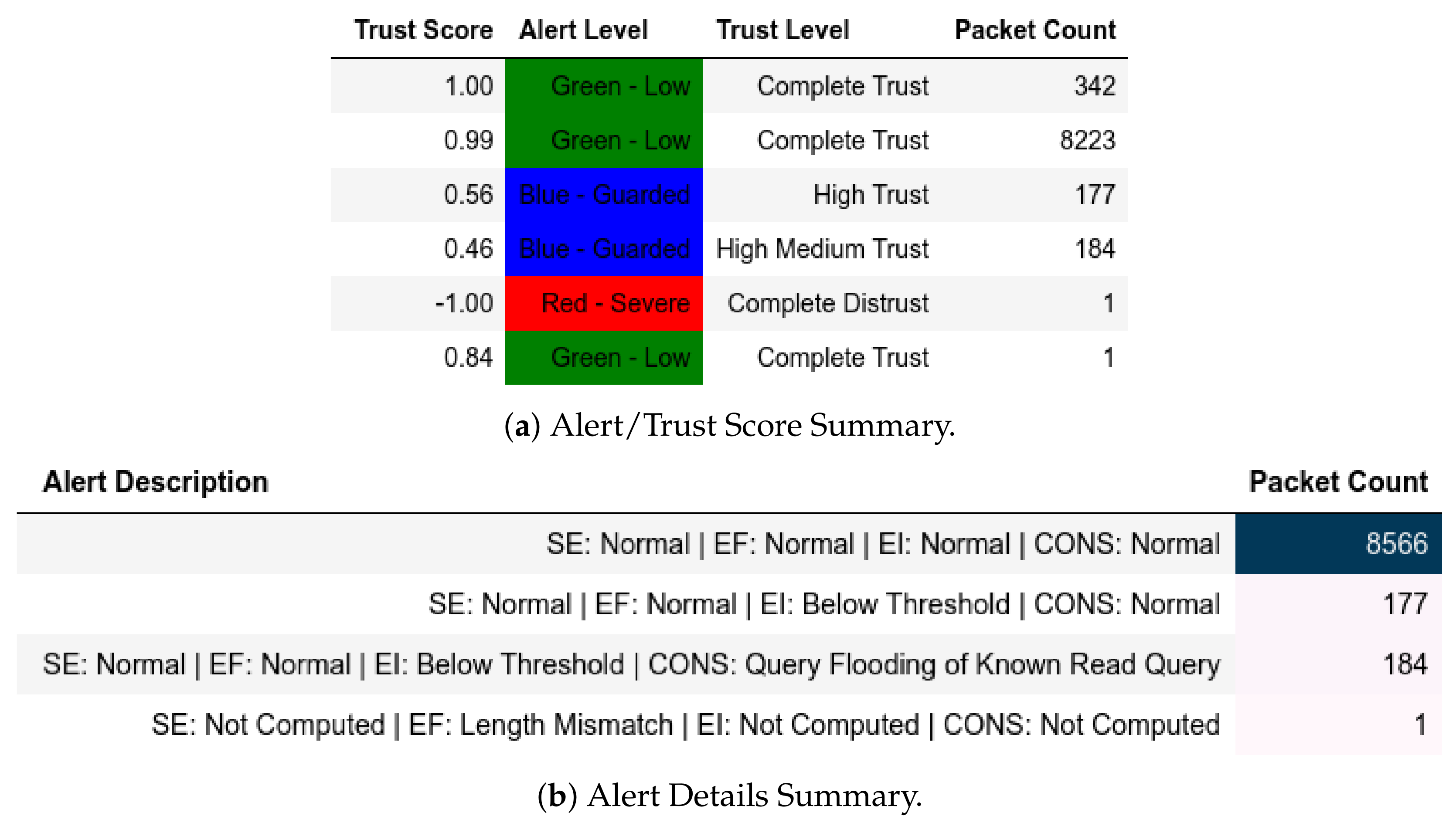
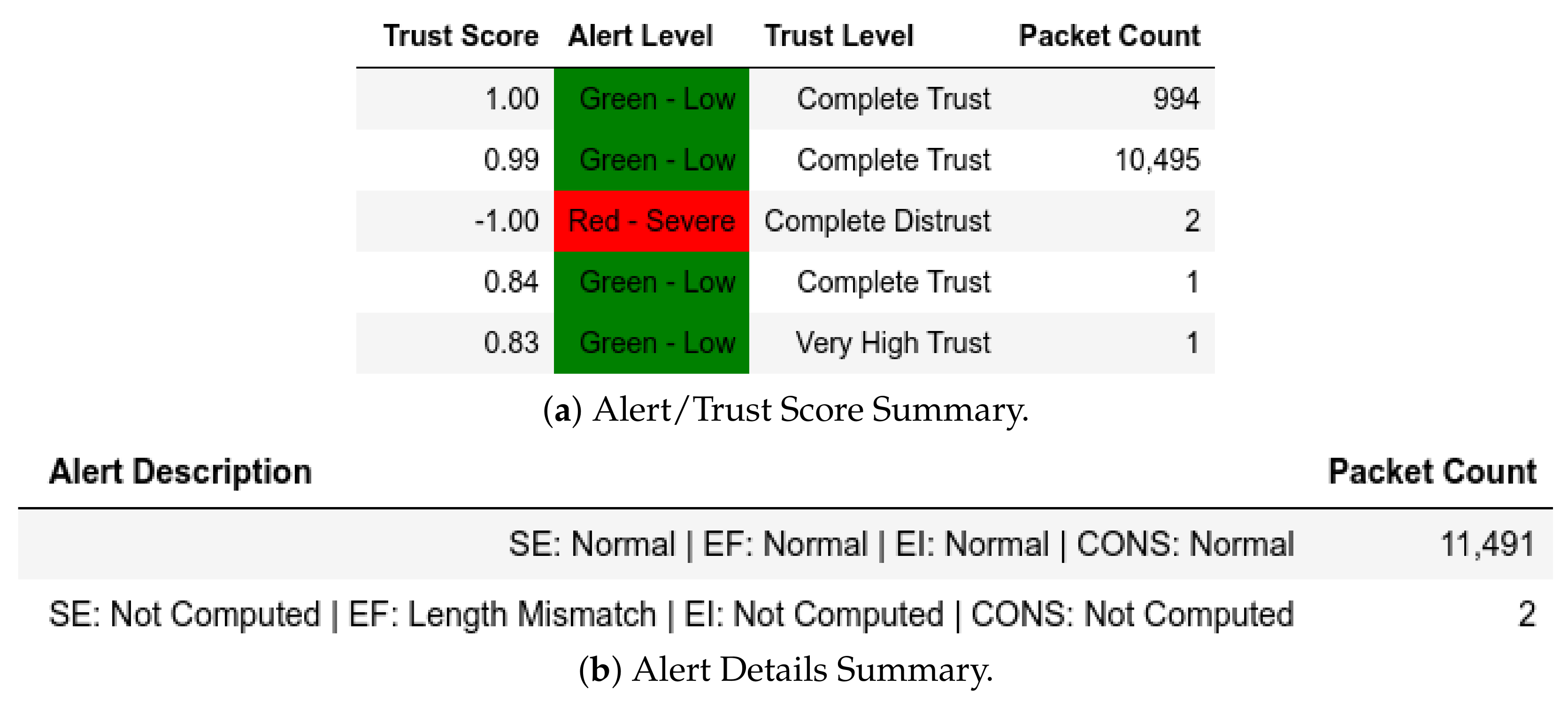
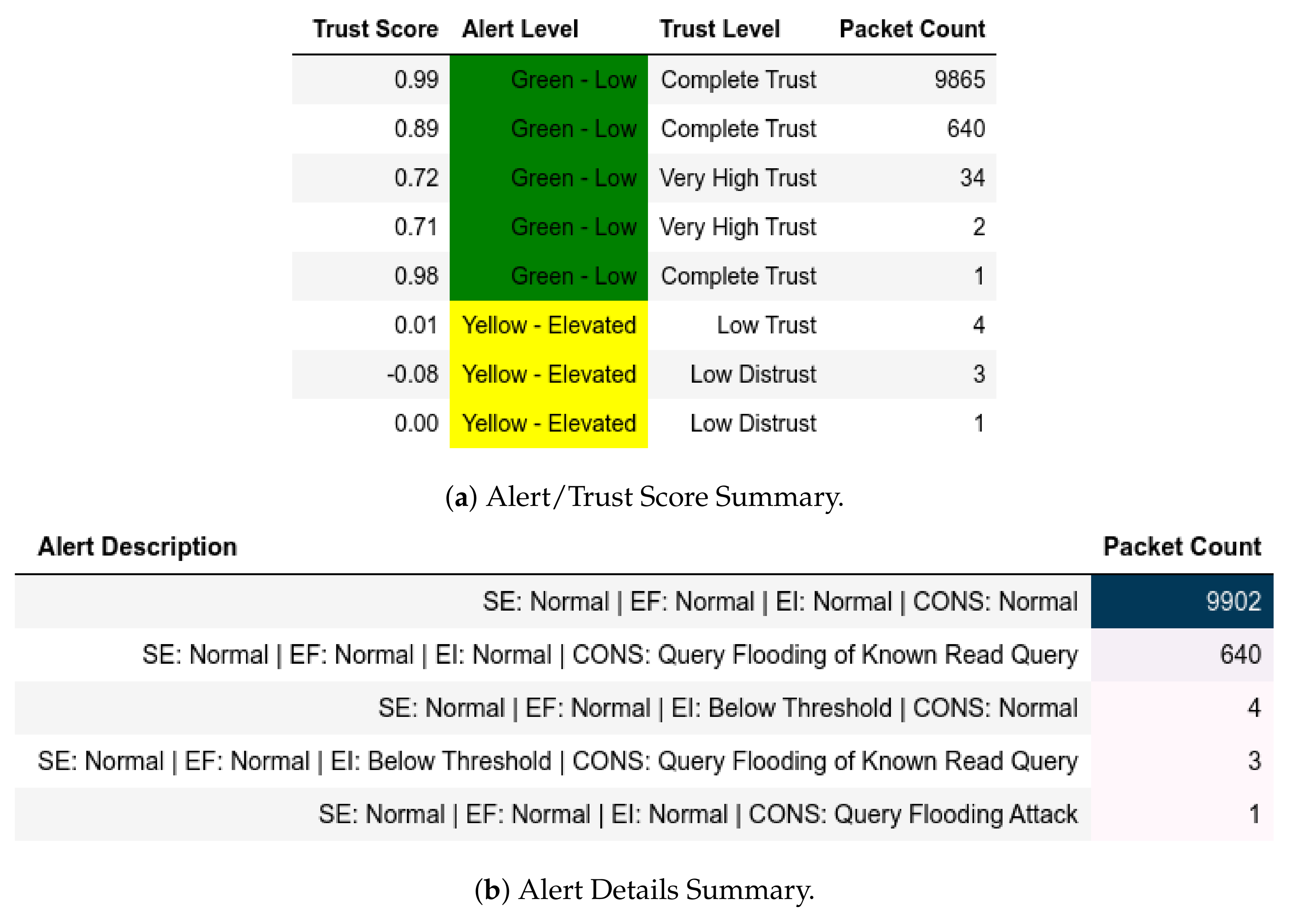
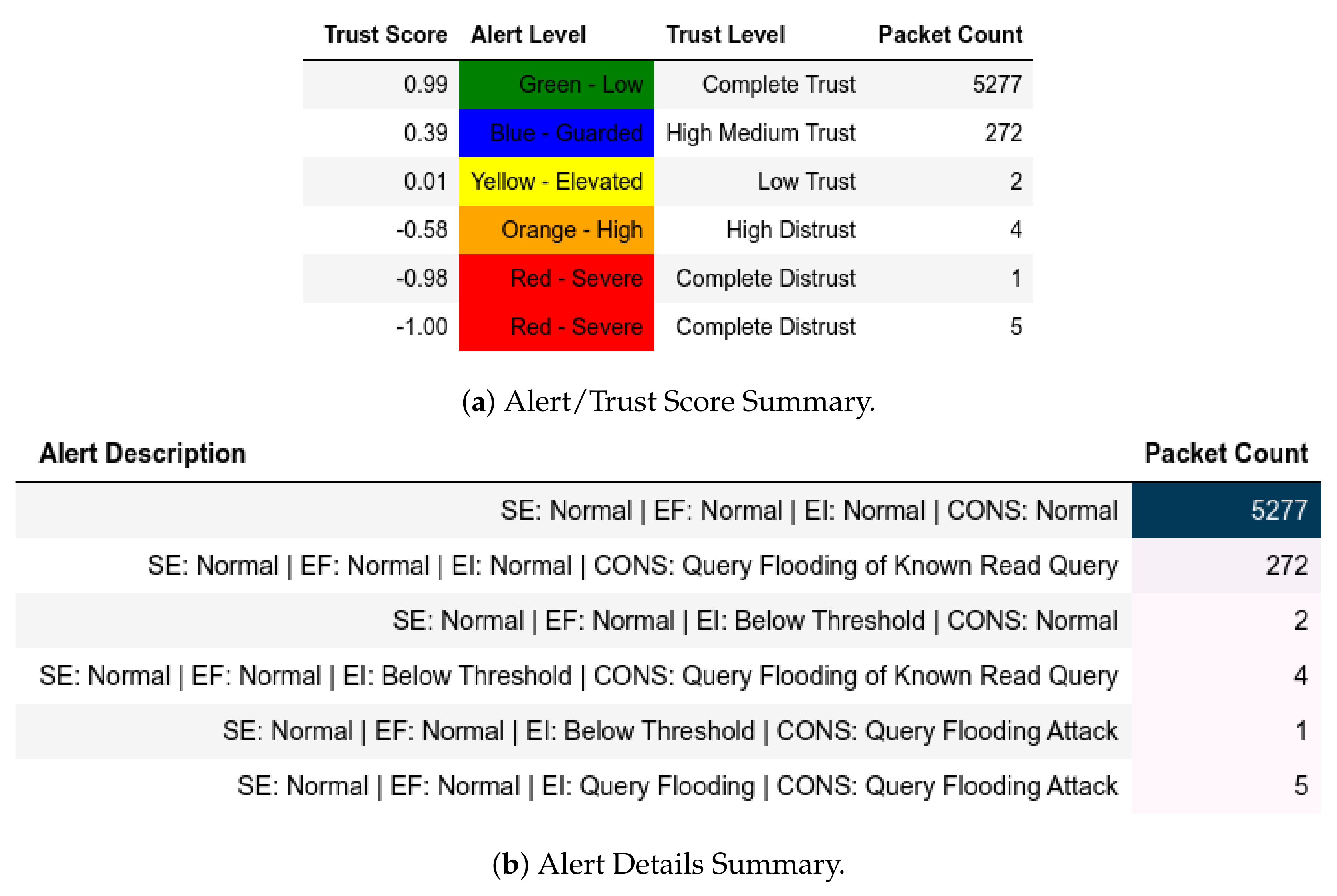
13.2. ATENA H2020 Dataset
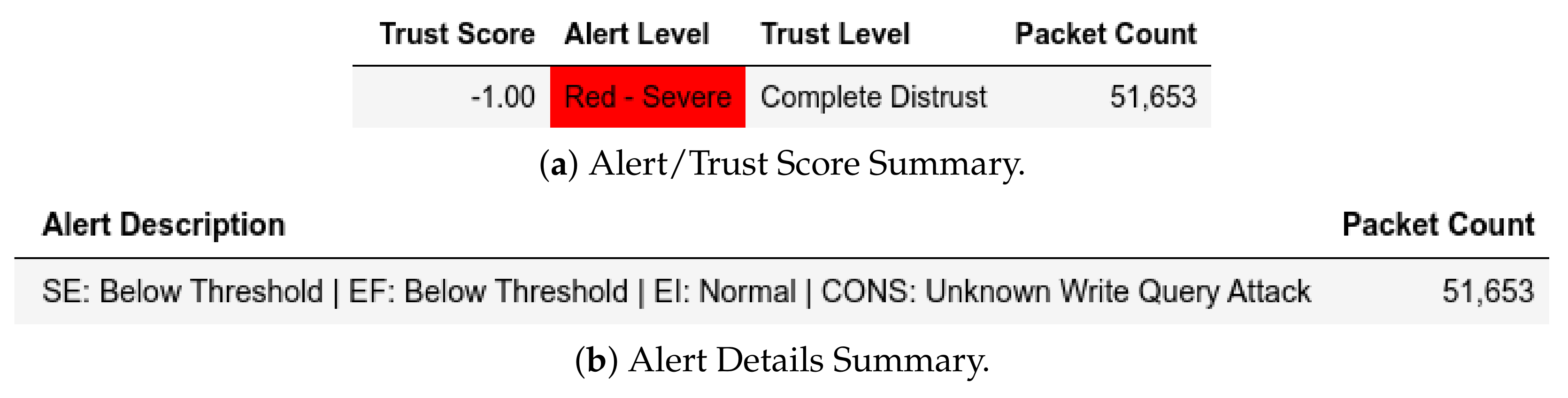
13.2.1. External Attack Test towards Server
13.2.2. Internal Attack Test towards Server
13.2.3. Internal Attack Test with IP-MAC Blacklisting towards Server
13.2.4. Internal Attack Test towards Client
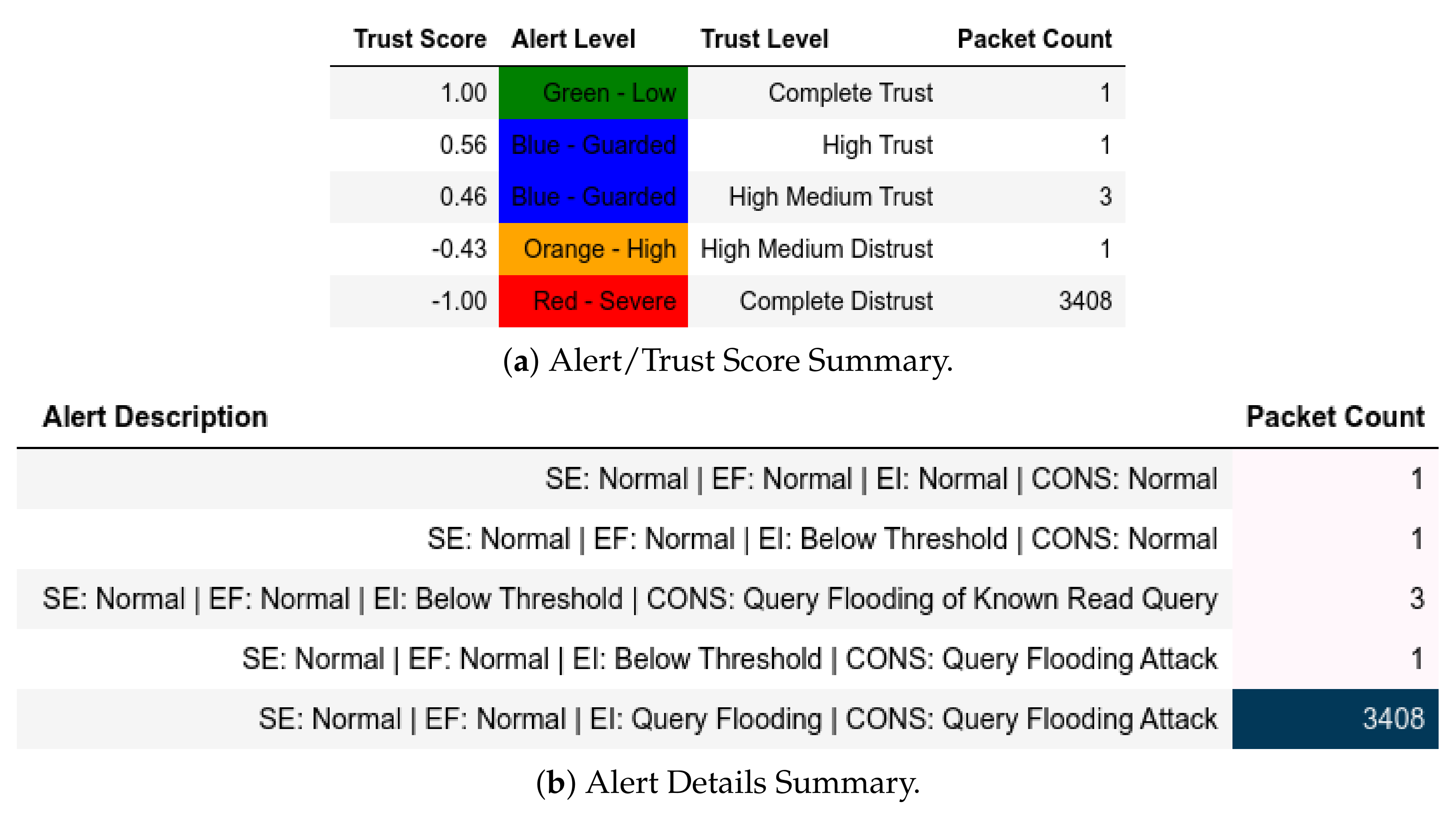
13.2.5. Testing with Criticality Variation
13.3. Discussion
14. Conclusions
15. Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ACM | Association for Computing Machinery |
| AMI | Advanced Metering Infrastructure |
| APT | Advanced Persistent Threat |
| ATENA | Advanced Tools to Assess and Mitigate the Criticality of ICT Components and |
| their Dependencies over Critical Infrastructures | |
| CB | Circuit Breaker |
| CHP | Combined Heat and Power |
| CnC | Command and Control |
| CNP | Contract Net Protocol |
| CONS | Consequence |
| CT | Current Transformer |
| CVE | Common Vulnerabilities and Exposures |
| CWE | Common Weakness Enumeration |
| DER | Distributed Energy Resources |
| DL | Direct Line |
| DOS | Denial of Service |
| EF | Exposure Frequency |
| EI | Exposure Intensity |
| EPM | École Polytechnique de Montréal |
| FIPA | Foundation for Intelligent Physical Agents |
| GOOSE | Generic Object-Oriented Substation Event |
| HMI | Human–Machine Interface |
| IBM | International Business Machines Company |
| IDS | Intrusion Detection Systems |
| IED | Intelligent Electronic Device |
| IEEE | Institute of Electrical and Electronics Engineers |
| IL | Incoming Line |
| IP | Internet Protocol |
| IP | Internet Protocol |
| JADE | Java Agent Development Framework |
| KQML | Knowledge Query and Manipulation Language |
| LMP | Local Marginal Price |
| MAC | Media Access Control |
| MAS | Multi-Agent System |
| MiTM | Man in the Middle |
| MS-ISAC | Multi-State Information Sharing and Analysis Center |
| NIST | National Institute of Standards and Technology |
| OC | Outgoing Circuit |
| OL | Outgoing Line |
| OT | Operational Technology |
| PEV | Plug-in Electric Vehicles |
| PNNL | Pacific Northwest National Laboratory |
| PT | Potential Transformer |
| SAS | Substation Automation System |
| SCADA | Supervisory Control and Data Acquisition |
| SE | Similar Exposure |
| SPS | Special Protection System |
| TCP | Transmission Control Protocol |
| TTL | Time to Live |
| TX | Transformer |
| WASA | Wide-Area Situational Awareness |
| WCA | Water Cycle Algorithm |
| WSN | Wireless Sensor Network |
Appendix A
| Notation | Meaning |
|---|---|
| Agent | |
| Subject | |
| Risk between and | |
| A transaction between and | |
| Knowledge about | |
| Knowledge of previous transactions between and | |
| Knowledge of | |
| t | Time |
| Trust between and | |
| Previous trust between and | |
| Agent device | |
| Subject device | |
| Message between and | |
| History of communication between and | |
| D | A list of n devices |
| List of devices functionally dependent on | |
| List of devices that functionally influence | |
| Intersection of and | |
| l | Criticality rank of devices |
| Substation | |
| M | A set of clients |
| S | A set of servers |
| N | A set of network devices |
| Q | A set of queries |
| R | A set of responses associated with Q |
| ype of query or response being either read or write | |
| A malicious Q | |
| Exposure intensity | |
| Exposure frequency | |
| Similar exposure | |
| An exposure’s threshold | |
| An alarm associated with a particular exposure factor of familiarity | |
| Z | A set of features associated with |
| A reference set of features associated with | |
| Pre-time feature | |
| Inter-query time feature | |
| Inter-response time feature | |
| Query-response time feature | |
| Transaction time feature | |
| Timeout feature | |
| Inter-query time threshold | |
| Inter-response time threshold | |
| Query-response time threshold | |
| Timeout threshold | |
| Moore machine used to generate -based features | |
| Finite set of states | |
| Read discrete input state | |
| Read coil state | |
| Write coil state | |
| Write multiple coils state | |
| Read holding registers state | |
| Write single register state | |
| Write multiple registers state | |
| Read input registers state | |
| Unknown state | |
| Modbus function code of or | |
| a | Modbus address |
| Modbus data value of a | |
| Modbus byte count of the value found at a | |
| Modbus length of data frame | |
| Length of entire Modbus packet | |
| Modbus coil/discrete input/input register/holding register quantity | |
| Modbus header length | |
| A set of input alphabets of | |
| A transition function of | |
| A set of features associated with | |
| A reference set of features associated with | |
| State traversed feature | |
| IP-MAC mismatch feature | |
| Port mismatch feature | |
| Unknown state feature | |
| Address match feature | |
| Address size match feature | |
| Function code match feature | |
| Discrete input reference match feature | |
| Discrete input quantity match feature | |
| Coil reference match feature | |
| Coil quantity match feature | |
| Holding register reference match feature | |
| Holding register quantity feature | |
| Input register reference match | |
| Input register quantity match | |
| Output function of | |
| A set of features associated | |
| A reference set of features associated | |
| Count for read coil function code | |
| Coil quantity | |
| Count for read discrete input function code | |
| Discrete input quantity | |
| Count for read holding register function code | |
| Holding register quantity | |
| Count for read input register function code | |
| Input register quantity | |
| Count for write single coil function code | |
| Coil value | |
| Coil data byte count | |
| Discrete input data byte count | |
| Holding register data byte count | |
| Input register data byte count | |
| Count for write single register function code | |
| Holding register value | |
| Count for write multiple coils function code | |
| Set of coil values | |
| Count for Write Multiple Registers function code | |
| Set of holding register values | |
| Input register value | |
| Set of input register values | |
| Frame size feature | |
| F | Familiarity |
| Replay sensitivity weight | |
| Replay sensitivity weight for unknown states | |
| Reconnaissance sensitivity weight | |
| Query flooding sensitivity weight | |
| Query flooding sensitivity weight for unknown states | |
| Criticality rank ratio | |
| Environment status attack value | |
| Replay attack value | |
| Reconnaissance attack value | |
| Query flooding attack value | |
| Packet manipulation attack value | |
| C | Consequence |
| Trust score | |
| Initial state of device | |
| Previous trust score | |
| Trust score threshold | |
| Forgiveness weight | |
| Forgiveness state of device | |
| Client group | |
| Server group | |
| Attack group | |
| Targeted group | |
| Compromised group | |
| Compromised client group | |
| Blacklisted group |
References
- Gupta, B.; Akhtar, T. A survey on smart power grid: Frameworks, tools, security issues, and solutions. Ann. Telecommun. 2017, 72, 517–549. [Google Scholar] [CrossRef]
- Knirsch, F.; Unterweger, A.; Unterrainer, M.; Engel, D. Comparison of the Paillier and ElGamal Cryptosystems for Smart Grid Aggregation Protocols. In Proceedings of the ICISSP, Valletta, Malta, 25–27 February 2020; pp. 232–239. [Google Scholar]
- Abbasinezhad-Mood, D.; Nikooghadam, M. Design and extensive hardware performance analysis of an efficient pairwise key generation scheme for smart grid. Int. J. Commun. Syst. 2018, 31, e3507. [Google Scholar] [CrossRef]
- Yu, S.; Park, K.; Lee, J.; Park, Y.; Park, Y.; Lee, S.; Chung, B. Privacy-preserving lightweight authentication protocol for demand response management in smart grid environment. Appl. Sci. 2020, 10, 1758. [Google Scholar] [CrossRef] [Green Version]
- Gunduz, M.Z.; Das, R. Cyber-security on smart grid: Threats and potential solutions. Comput. Netw. 2020, 169, 107094. [Google Scholar] [CrossRef]
- Langner, R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar] [CrossRef]
- Greer, C.; Wollman, D.; Prochaska, D.; Boynton, P.; Mazer, J.; Nguyen, C.; FitzPatrick, G.; Nelson, T.; Koepke., G.; Hefner, A., Jr.; et al. NIST Framework and Roadmap for Smart Grid Interoperability Standards, Release 3.0. Available online: https://tsapps.nist.gov/publication/get_pdf.cfm?pub_id=916755 (accessed on 21 October 2020).
- Sommerville, P.B. Distributed Energy Resources: The Role of Regional Planning, New Benefit-Cost Methodologies and the Competitive Landscape; Mowat Centre for Policy Innovation: Toronto, ON, Canada, 2019. [Google Scholar]
- Kent Hedrick. What New Capabilities Mean for Distribution Grid Management. Available online: https://www.landisgyr.com/webfoo/wp-content/uploads/2014/07/LAN-14009_GridMgmtWP_140728.pdf (accessed on 17 November 2020).
- Xia, J.; Wang, Y. Secure key distribution for the smart grid. IEEE Trans. Smart Grid 2012, 3, 1437–1443. [Google Scholar] [CrossRef]
- Bartoli, A.; Hernandez-Serrano, J.; Soriano, M.; Dohler, M.; Kountouris, A.; Barthel, D. Secure lossless aggregation for smart grid M2M networks. In Proceedings of the 2010 First IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 333–338. [Google Scholar]
- Maharjan, S.; Zhu, Q.; Zhang, Y.; Gjessing, S.; Basar, T. Dependable demand response management in the smart grid: A Stackelberg game approach. IEEE Trans. Smart Grid 2013, 4, 120–132. [Google Scholar] [CrossRef]
- Parvania, M.; Fotuhi-Firuzabad, M. Demand response scheduling by stochastic SCUC. IEEE Trans. Smart Grid 2010, 1, 89–98. [Google Scholar] [CrossRef]
- Deilami, S.; Masoum, A.S.; Moses, P.S.; Masoum, M.A. Real-time coordination of plug-in electric vehicle charging in smart grids to minimize power losses and improve voltage profile. IEEE Trans. Smart Grid 2011, 2, 456–467. [Google Scholar] [CrossRef]
- Carryl, C.; Ilyas, M.; Mahgoub, I.; Rathod, M. The PEV security challenges to the smart grid: Analysis of threats and mitigation strategies. In Proceedings of the 2013 International Conference on Connected Vehicles and Expo (ICCVE), Las Vegas, NV, USA, 2–6 December 2013; pp. 300–305. [Google Scholar]
- Liu, J.; Xiao, Y.; Li, S.; Liang, W.; Chen, C.P. Cyber security and privacy issues in smart grids. IEEE Commun. Surv. Tutor. 2012, 14, 981–997. [Google Scholar] [CrossRef]
- Liu, N.; Chen, J.; Zhu, L.; Zhang, J.; He, Y. A key management scheme for secure communications of advanced metering infrastructure in smart grid. IEEE Trans. Ind. Electron. 2012, 60, 4746–4756. [Google Scholar] [CrossRef]
- Qi, J.; Hahn, A.; Lu, X.; Wang, J.; Liu, C.C. Cybersecurity for distributed energy resources and smart inverters. IET Cyber-Phys. Syst. Theory Appl. 2016, 1, 28–39. [Google Scholar] [CrossRef] [Green Version]
- Srikantha, P.; Kundur, D. A DER attack-mitigation differential game for smart grid security analysis. IEEE Trans. Smart Grid 2015, 7, 1476–1485. [Google Scholar] [CrossRef]
- Lu, R.; Liang, X.; Li, X.; Lin, X.; Shen, X. EPPA: An efficient and privacy-preserving aggregation scheme for secure smart grid communications. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 1621–1631. [Google Scholar]
- Radoglou–Grammatikis, P.I.; Sarigiannidis, P.G. Securing the smart grid: A comprehensive compilation of intrusion detection and prevention systems. IEEE Access 2019, 7, 46595–46620. [Google Scholar] [CrossRef]
- Goodman, S. Alliance Commission on National Energy Efficiency Policy. Available online: https://www.ase.org/history-energy-efficiency-alliance-commission-national-energy-efficiency-policy (accessed on 17 May 2020).
- Cook, K. Trust in Society. In Russell Sage Foundation Series on Trust, New York; Publisher is Russell Sage: New York, NY, USA, 2003; Volume 2, p. 432. [Google Scholar]
- Gambetta, D. Can we trust trust. Trust. Mak. Break. Coop. Relat. 2000, 13, 213–237. [Google Scholar]
- Marsh, S.P. Formalising trust as a computational concept. In STORRE: Stirling Online Research Repository; University of Stirling: Stirling, UK, 1994. [Google Scholar]
- Joint Task Force Transformation Initiative. SP 800-39. Managing Information Security Risk: Organization, Mission, and Information System View; NIST: Scotts Valley, CA, USA, 2011.
- Altaf, A.; Abbas, H.; Iqbal, F.; Derhab, A. Trust models of internet of smart things: A survey, open issues, and future directions. J. Netw. Comput. Appl. 2019, 137, 93–111. [Google Scholar] [CrossRef]
- Fung, C.J.; Zhang, J.; Aib, I.; Boutaba, R. Dirichlet-based trust management for effective collaborative intrusion detection networks. IEEE Trans. Netw. Serv. Manag. 2011, 8, 79–91. [Google Scholar] [CrossRef]
- Cheng, X.; Li, T. A credibility measurement method of smart grid data. In Proceedings of the 2016 IEEE Advanced Information Management, Communicates, Electronic and Automation Control Conference (IMCEC), Xi’an, China, 3–5 October 2016; pp. 1231–1235. [Google Scholar]
- Velusamy, D.; Pugalendhi, G.; Ramasamy, K. A Cross-Layer Trust Evaluation Protocol for Secured Routing in Communication Network of Smart Grid. IEEE J. Sel. Areas Commun. 2019, 38, 193–204. [Google Scholar] [CrossRef]
- Velusamy, D.; Pugalendhi, G. Water Cycle Algorithm Tuned Fuzzy Expert System for Trusted Routing in Smart Grid Communication Network. IEEE Trans. Fuzzy Syst. 2020, 28, 1167–1177. [Google Scholar] [CrossRef]
- Alnasser, A.; Sun, H. A fuzzy logic trust model for secure routing in smart grid networks. IEEE Access 2017, 5, 17896–17903. [Google Scholar] [CrossRef] [Green Version]
- Xiang, M.; Bai, Q.; Liu, W. Self-adjustable trust-based energy efficient routing for smart grid systems. In Proceedings of the 2012 IEEE/WIC/ACM International Conferences on Web Intelligence and Intelligent Agent Technology, Macau, China, 4–7 December 2012; Volume 3, pp. 378–382. [Google Scholar]
- Xiang, M.; Liu, W.; Bai, Q. Trust-based geographical routing for smart grid communication networks. In Proceedings of the 2012 IEEE Third International Conference on Smart Grid Communications (SmartGridComm), Tainan, Taiwan, 5–8 November 2012; pp. 704–709. [Google Scholar]
- Xiang, M.; Liu, W.; Bai, Q. TIGER: A trust-based intelligent geographical energy-aware routing for smart grid communication networks. In Proceedings of the 2013 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, Australia, 16–18 July 2013; pp. 65–72. [Google Scholar]
- Bello, A.; Liu, W.; Bai, Q.; Narayanan, A. Revealing the role of topological transitivity in efficient trust and reputation system in smart metering network. In Proceedings of the 2015 IEEE International Conference on Data Science and Data Intensive Systems, Sydney, Australia, 11–13 December 2015; pp. 337–342. [Google Scholar]
- Bello, A.; Liu, W.; Bai, Q.; Narayanan, A. Exploring the role of structural similarity in securing smart metering infrastructure. In Proceedings of the 2015 IEEE International Conference on Data Science and Data Intensive Systems, Sydney, Australia, 11–13 December 2015; pp. 343–349. [Google Scholar]
- Reza, S.S.; Mahbub, T.N.; Islam, M.M.; Arifeen, M.M.; Remu, S.R.H.; Hossain, D.A. Assuring Cyber Security in Smart Grid Networks by Fuzzy-logic based Trust Management Model. In Proceedings of the 2019 IEEE International Conference on Robotics, Automation, Artificial-intelligence and Internet-of-Things (RAAICON), Dhaka, Bangladesh, 29 November–1 December 2019; pp. 1–4. [Google Scholar]
- Pliatsios, D.; Sarigiannidis, P.; Efstathopoulos, G.; Sarigiannidis, A.; Tsiakalos, A. Trust Management in Smart Grid: A Markov Trust Model. In Proceedings of the 2020 9th International Conference on Modern Circuits and Systems Technologies (MOCAST), Bremen, Germany, 7–9 September 2020; pp. 1–4. [Google Scholar]
- Pradhan, O.; Awan, M.; Newman, K.; Barnes, F. Trust and reputation approach to smart grid security. In Proceedings of the 2011 4th IEEE International Symposium on Resilient Control Systems, Boise, ID, USA, 9–11 August 2011; pp. 101–104. [Google Scholar]
- Fadul, J.; Hopkinson, K.; Andel, T.; Kurkowski, S.; Moore, J. Simple trust protocol for wired and wireless SCADA networks. In Proceedings of the International Conference on Cyber Warfare and Security, Dayton, OH, USA, 8–9 April 2010; Academic Conferences International Limited: Reading, UK, 2010; p. 89. [Google Scholar]
- Fadul, J.E.; Hopkinson, K.M.; Andel, T.R.; Sheffield, C.A. A trust-management toolkit for smart-grid protection systems. IEEE Trans. Power Deliv. 2013, 29, 1768–1779. [Google Scholar] [CrossRef]
- Shipman, C.M.; Hopkinson, K.M.; Lopez, J. Con-resistant trust for improved reliability in a smart-grid special protection system. IEEE Trans. Power Deliv. 2014, 30, 455–462. [Google Scholar] [CrossRef]
- Zhang, Y.; Sun, W.; Wang, L. Location and communication routing optimization of trust nodes in smart grid network infrastructure. In Proceedings of the 2012 IEEE Power and Energy Society General Meeting, San Diego, CA, USA, 22–26 July 2012; pp. 1–8. [Google Scholar]
- Zhang, Y.; Sun, W.; Wang, L. Efficient trust node aware routing in ZigBee communication network of smart grid. In Proceedings of the 2012 10th International Power & Energy Conference (IPEC), Ho Chi Minh City, Vietnam, 12–14 December 2012; pp. 321–326. [Google Scholar]
- Zhang, Y.; Sun, W.; Wang, L. Placement of primary-secondary trust nodes in smart grid communication network. In Proceedings of the 2013 IEEE Power & Energy Society General Meeting, Vancouver, BC, Canada, 21–25 July 2013; pp. 1–5. [Google Scholar]
- Zhang, Y.; Sun, W.; Wang, L. Fault-tolerant optimal routing of trust nodes in smart grid communications. In Proceedings of the 2012 IEEE International Conference on Cyber Technology in Automation, Control, and Intelligent Systems (CYBER), Bangkok, Thailand, 27–31 May 2012; pp. 281–286. [Google Scholar]
- Zhang, Y.; Wang, L.; Sun, W. Trust system design optimization in smart grid network infrastructure. IEEE Trans. Smart Grid 2013, 4, 184–195. [Google Scholar] [CrossRef]
- Hasan, M.M.; Mouftah, H.T. Optimization of trust node assignment for securing routes in smart grid SCADA networks. IEEE Syst. J. 2018, 13, 1505–1513. [Google Scholar] [CrossRef]
- McDonald, J.D. Electric Power Substations Engineering; CRC Press: Boca Raton, FL, USA, 2016. [Google Scholar]
- Hauser, C.H.; Bakken, D.E.; Dionysiou, I.; Gjermundrod, K.H.; Irava, V.; Helkey, J.; Bose, A. Security, trust, and QoS in next-generation control and communication for large power systems. Int. J. Crit. Infrastruct. 2008, 4, 3–16. [Google Scholar] [CrossRef]
- Singh, N.K.; Mahajan, V. Cyber Attack Detection In Smart Grid Substation Using Virtual Range Increment Furthermore, Trust Weight. In Proceedings of the 2019 8th International Conference on Power Systems (ICPS), Jaipur, India, 20–22 December 2019; pp. 1–6. [Google Scholar]
- Singh, N.K.; Mahajan, V. Detection of cyber cascade failure in smart grid substation using advance grey wolf optimization. J. Interdiscip. Math. 2020, 23, 69–79. [Google Scholar] [CrossRef]
- Obert, J.; Chavez, A.; Johnson, J. Behavioral based trust metrics and the smart grid. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 1490–1493. [Google Scholar]
- Obert, J.; Chavez, A. Graph-Based Event Classification in Grid Security Gateways. In Proceedings of the 2019 Second International Conference on Artificial Intelligence for Industries (AI4I), Laguna Hills, CA, USA, 25–27 September 2019; pp. 63–66. [Google Scholar]
- Nasr, P.M.; Yazdian-Varjani, A. Toward operator access management in SCADA system: Deontological threat mitigation. IEEE Trans. Ind. Inform. 2017, 14, 3314–3324. [Google Scholar] [CrossRef]
- Rashid, M.T.A.; Yussof, S.; Yusoff, Y. Trust system architecture for securing GOOSE communication in IEC 61850 substation network. Int. J. Secur. Its Appl. 2016, 10, 289–302. [Google Scholar] [CrossRef]
- Bellifemine, F.L.; Caire, G.; Greenwood, D. Developing Multi-Agent Systems with JADE; John Wiley & Sons: Hoboken, NJ, USA, 2007; Volume 7. [Google Scholar]
- Kuzin, A.Y.; Demidova, G.L.; Lukichev, D.V. An Approach of the JADE and Simulink Interaction to Control Smart Grid Based on the Multi Agent System. In Proceedings of the 2019 IEEE Conference of Russian Young Researchers in Electrical and Electronic Engineering (EIConRus), Saint Petersburg and Moscow, Russia, 28–31 January 2019; pp. 574–577. [Google Scholar]
- Maaroufi, M.; Ouassaid, M. Demand side management in smart grid by multi-agent systems technology. In Proceedings of the 2014 International Conference on Multimedia Computing and Systems (ICMCS), Marrakesh, Morocco, 14–16 April 2014; pp. 1042–1045. [Google Scholar]
- Garrab, A.; Bouallegue, A.; Bouallegue, R. Multi-Agent modeling of a meters network used in Smart Grid. In Proceedings of the 2014 World Congress on Computer Applications and Information Systems (WCCAIS), Hammamet, Tunisia, 17–19 January 2014; pp. 1–5. [Google Scholar]
- Kim, B.; Lavrova, O. Optimal power flow and energy-sharing among multi-agent smart buildings in the smart grid. In Proceedings of the 2013 IEEE Energytech, Cleveland, OH, USA, 21–23 May 2013; pp. 1–5. [Google Scholar]
- Dong, L.; Li, Y.; Liu, K.; Pu, T.; Liu, G. Research on smart grid simulation framework based on distributed intelligent system. In Proceedings of the 2014 International Conference on Power System Technology, Chengdu, China, 20–22 October 2014; pp. 1969–1974. [Google Scholar]
- JAVA Agent DEvelopment Framework. Available online: https://jade.tilab.com/ (accessed on 23 March 2020).
- Kantamneni, A.; Brown, L.E.; Parker, G.; Weaver, W.W. Survey of multi-agent systems for microgrid control. Eng. Appl. Artif. Intell. 2015, 45, 192–203. [Google Scholar] [CrossRef]
- Bellifemine, F.; Caire, G.; Poggi, A.; Rimassa, G. JADE: A software framework for developing multi-agent applications. Lessons learned. Inf. Softw. Technol. 2008, 50, 10–21. [Google Scholar] [CrossRef]
- Volttron|Devices|Data|Decisions. Available online: https://volttron.org/ (accessed on 4 March 2021).
- Welcome to the Aglets Web Site. Available online: http://aglets.sourceforge.net/ (accessed on 4 March 2021).
- AOS Group: Products. Available online: https://aosgrp.com/products/jack/ (accessed on 2 March 2021).
- Shakshuki, E.; Jun, Y. Multi-agent development toolkits: An evaluation. In Proceedings of the International Conference on Industrial, Engineering and Other Applications of Applied Intelligent Systems, Ottawa, ON, Canada, 17–20 May 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 209–218. [Google Scholar]
- Zhao, X.; Hu, G.; Wu, Z. The Smart grid scheduling based on contract net protocol with trust model. In Proceedings of the 2014 IEEE/ACIS 13th International Conference on Computer and Information Science (ICIS), Taiyuan, China, 4–6 June 2014; pp. 419–424. [Google Scholar]
- Smith, R.G. The contract net protocol: High-level communication and control in a distributed problem solver. IEEE Trans. Comput. 1980, 29, 1104–1113. [Google Scholar] [CrossRef]
- Alavikia, Z.; Mozayani, N.; Shahbazi, J.; Alavikia, F. Utilizing an Agent Based Negotiation Mechanism to Defend Against Jamming Attack in Smart Grid Power Market. In Proceedings of the 2018 9th International Symposium on Telecommunications (IST), Tehran, Iran, 17–19 December 2018; pp. 45–52. [Google Scholar]
- Conejo, A.J.; Castillo, E.; Mínguez, R.; Milano, F. Locational marginal price sensitivities. IEEE Trans. Power Syst. 2005, 20, 2026–2033. [Google Scholar] [CrossRef]
- Li, F.; Bo, R. Small test systems for power system economic studies. In Proceedings of the IEEE PES General Meeting, Minneapolis, MN, USA, 25–29 July 2010; pp. 1–4. [Google Scholar]
- Pereira, A.; Rodrigues, N.; Barbosa, J.; Leitão, P. Trust and risk management towards resilient large-scale cyber-physical systems. In Proceedings of the 2013 IEEE International Symposium on Industrial Electronics, Taipei, Taiwan, 28–31 May 2013; pp. 1–6. [Google Scholar]
- Chassin, D.P.; Schneider, K.; Gerkensmeyer, C. GridLAB-D: An open-source power systems modeling and simulation environment. In Proceedings of the 2008 IEEE/PES Transmission and Distribution Conference and Exposition, Chicago, IL, USA, 21–24 April 2008; pp. 1–5. [Google Scholar]
- Cintuglu, M.H.; Ishchenko, D. Secure Distributed State Estimation for Networked Microgrids. IEEE Internet Things J. 2019, 6, 8046–8055. [Google Scholar] [CrossRef]
- Matei, I.; Baras, J.S.; Srinivasan, V. Trust-based multi-agent filtering for increased smart grid security. In Proceedings of the 2012 20th Mediterranean Conference on Control & Automation (MED), Barcelona, Spain, 3–6 July 2012; pp. 716–721. [Google Scholar]
- Cunningham, C.; Roque, A. Adapting an agent-based model of socio-technical systems to analyze security failures. In Proceedings of the 2017 IEEE International Symposium on Technologies for Homeland Security (HST), Waltham, MA, USA, 25–26 April 2017; pp. 1–7. [Google Scholar]
- Minkel, J. The 2003 Northeast Blackout–Five Years Later. Sci. Am. 2008, 13, 1–3. [Google Scholar]
- Hussain, S.; Honeth, N.; Gustavsson, R.; Sandels, C.; Saleem, A. Trustworthy injection/curtailment of DER in distribution network maintaining quality of service. In Proceedings of the 2011 16th International Conference on Intelligent System Applications to Power Systems, Hersonissos, Greece, 25–28 September 2011; pp. 1–6. [Google Scholar]
- AOS Group|Products. Available online: https://www.aosgrp.com/products/jack/ (accessed on 2 March 2021).
- Borowski, J.F.; Hopkinson, K.M.; Humphries, J.W.; Borghetti, B.J. Reputation-based trust for a cooperative agent-based backup protection scheme. IEEE Trans. Smart Grid 2011, 2, 287–301. [Google Scholar] [CrossRef]
- Chen, Q.; Schmidt-Eisenlohr, F.; Jiang, D.; Torrent-Moreno, M.; Delgrossi, L.; Hartenstein, H. Overhaul of IEEE 802.11 modeling and simulation in ns-2. In Proceedings of the 10th ACM Symposium on Modeling, Analysis, and Simulation of Wireless and Mobile Systems, Chania Crete Island, Greece, 22–26 October 2007; pp. 159–168. [Google Scholar]
- Hopkinson, K.; Wang, X.; Giovanini, R.; Thorp, J.; Birman, K.; Coury, D. EPOCHS: A platform for agent-based electric power and communication simulation built from commercial off-the-shelf components. IEEE Trans. Power Syst. 2006, 21, 548–558. [Google Scholar] [CrossRef]
- Anaya-Lara, O.; Acha, E. Modeling and analysis of custom power systems by PSCAD/EMTDC. IEEE Trans. Power Deliv. 2002, 17, 266–272. [Google Scholar] [CrossRef]
- Blangenois, J.; Guemkam, G.; Feltus, C.; Khadraoui, D. Organizational security architecture for critical infrastructure. In Proceedings of the 2013 International Conference on Availability, Reliability and Security, Regensburg, Germany, 2–6 September 2013; pp. 316–323. [Google Scholar]
- Guemkam, G.; Blangenois, J.; Feltus, C.; Khadraoui, D. Metamodel for reputation based agents system: Case study for electrical distribution SCADA design. In Proceedings of the 6th International Conference on Security of Information and Networks, Aksaray, Turkey, 26–28 November 2013; pp. 251–255. [Google Scholar]
- Cho, J.H.; Chan, K.; Adali, S. A survey on trust modeling. ACM Comput. Surv. (CSUR) 2015, 48, 1–40. [Google Scholar] [CrossRef]
- Yonelinas, A.P. The nature of recollection and familiarity: A review of 30 years of research. J. Mem. Lang. 2002, 46, 441–517. [Google Scholar] [CrossRef] [Green Version]
- Zhan, C.; Li, W.; Ogunbona, P. Measuring the degree of face familiarity based on extended NMF. ACM Trans. Appl. Percept. (TAP) 2013, 10, 1–22. [Google Scholar] [CrossRef]
- Tonkoski, R.; Lopes, L.A.C.; El-Fouly, T.H.M. Coordinated Active Power Curtailment of Grid Connected PV Inverters for Overvoltage Prevention. IEEE Trans. Sustain. Energy 2011, 2, 139–147. [Google Scholar] [CrossRef]
- Boakye-Boateng, K.; Ghorbani, A.A.; Lashkari, A.H. RiskISM: A Risk Assessment Tool for Substations. In Proceedings of the 2021 IEEE 9th International Conference on Smart City and Informatization (iSCI), Shenyang, China, 20–22 October 2021; pp. 23–30. [Google Scholar] [CrossRef]
- Single Line Diagrams Of Substations 66/11 kV and 11/0.4 kV: EEP. Available online: https://electrical-engineering-portal.com/single-line-diagrams-substations (accessed on 12 January 2021).
- Kim, B.K.; Kang, Y. Abnormal traffic detection mechanism for protecting IIoT environments. In Proceedings of the 2018 International Conference on Information and Communication Technology Convergence (ICTC), Jeju Island, Korea, 17–19 October 2018; pp. 943–945. [Google Scholar]
- Case, D.U. Analysis of the cyber attack on the Ukrainian power grid. Electr. Inf. Shar. Anal. Cent. (E-ISAC) 2016, 388, 1–29. [Google Scholar]
- Nelson, N. The Impact of Dragonfly Malware on inDustrial Control Systems. SANS Institute: Rockville, MD, USA, 2016. [Google Scholar]
- North American Protective Relay Marketplace. Available online: http://www.newton-evans.com/north-american-protective-relay-marketplace-new-report-now-available/ (accessed on 13 January 2021).
- Modbus Organization. MODBUS Messaging on TCP/IP Implementation Guide: V1.0b. Available online: https://www.modbus.org/docs/Modbus_Messaging_Implementation_Guide_V1_0b.pdf (accessed on 23 June 2021).
- Modbus Organization. Modbus Application Protocol Specification V1.1b. Available online: https://modbus.org/docs/Modbus_Application_Protocol_V1_1b3.pdf (accessed on 25 June 2021).
- Tidrea, A.; Korodi, A.; Silea, I. Cryptographic Considerations for Automation and SCADA Systems Using Trusted Platform Modules. Sensors 2019, 19, 4191. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Lai, Y.; Gao, H.; Liu, J. Vulnerability Mining Method for the Modbus TCP Using an Anti-Sample Fuzzer. Sensors 2020, 20, 2040. [Google Scholar] [CrossRef] [Green Version]
- Siniosoglou, I.; Radoglou–Grammatikis, P.; Efstathopoulos, G.; Fouliras, P.; Sarigiannidis, P. A unified deep learning anomaly detection and classification approach for smart grid environments. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1137–1151. [Google Scholar] [CrossRef]
- Nyasore, O.N.; Zavarsky, P.; Swar, B.; Naiyeju, R.; Dabra, S. Deep packet inspection in industrial automation control system to mitigate attacks exploiting modbus/TCP vulnerabilities. In Proceedings of the 2020 IEEE 6th Intl Conference on Big Data Security on Cloud (BigDataSecurity), IEEE Intl Conference on High Performance and Smart Computing,(HPSC) and IEEE Intl Conference on Intelligent Data and Security (IDS), Baltimore, MD, USA, 25–27 May 2020; pp. 241–245. [Google Scholar]
- Si, Y.; Korada, N.; Ayyanar, R.; Lei, Q. A high performance communication architecture for a smart micro-grid testbed using customized edge intelligent devices (eids) with spi and modbus tcp/ip communication protocols. IEEE Open J. Power Electron. 2021, 2, 2–17. [Google Scholar] [CrossRef]
- González, I.; Calderón, A.J.; Portalo, J.M. Innovative Multi-Layered Architecture for Heterogeneous Automation and Monitoring Systems: Application Case of a Photovoltaic Smart Microgrid. Sustainability 2021, 13, 2234. [Google Scholar] [CrossRef]
- Lemay, A.; Fernandez, J.M. Providing {SCADA} network data sets for intrusion detection research. In Proceedings of the 9th Workshop on Cyber Security Experimentation and Test ({CSET} 16), Austin, TX, USA, 8 August 2016. [Google Scholar]
- Frazão, I.; Abreu, P.H.; Cruz, T.; Araújo, H.; Simões, P. Denial of service attacks: Detecting the frailties of machine learning algorithms in the classification process. In Proceedings of the International Conference on Critical Information Infrastructures Security, Kaunas, Lithuania, 24–26 September 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 230–235. [Google Scholar]
- Pcap4J: A Java Library for Capturing, Crafting, and Sending Packets. Available online: Https://github.com/kaitoy/pcap4j (accessed on 31 May 2021).
- Infrastructure, C. Threat Information Sharing Framework. A Reference Guide for the Critical Infrastructure Community. USA Homeland Security. Available online: https://www.cisa.gov/sites/default/files/publications/ci-threat-information-sharing-framework-508.pdf (accessed on 10 January 2022).
- Saharkhizan, M.; Azmoodeh, A.; Dehghantanha, A.; Choo, K.K.R.; Parizi, R.M. An ensemble of deep recurrent neural networks for detecting iot cyber attacks using network traffic. IEEE Internet Things J. 2020, 7, 8852–8859. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Rhode, M.; Burnap, P.; Wedgbury, A. Adversarial attacks on machine learning cybersecurity defences in Industrial Control Systems. J. Inf. Secur. Appl. 2021, 58, 102717. [Google Scholar] [CrossRef]
- Ayodeji, A.; Liu, Y.k.; Chao, N.; Yang, L.q. A new perspective towards the development of robust data-driven intrusion detection for industrial control systems. Nucl. Eng. Technol. 2020, 52, 2687–2698. [Google Scholar] [CrossRef]
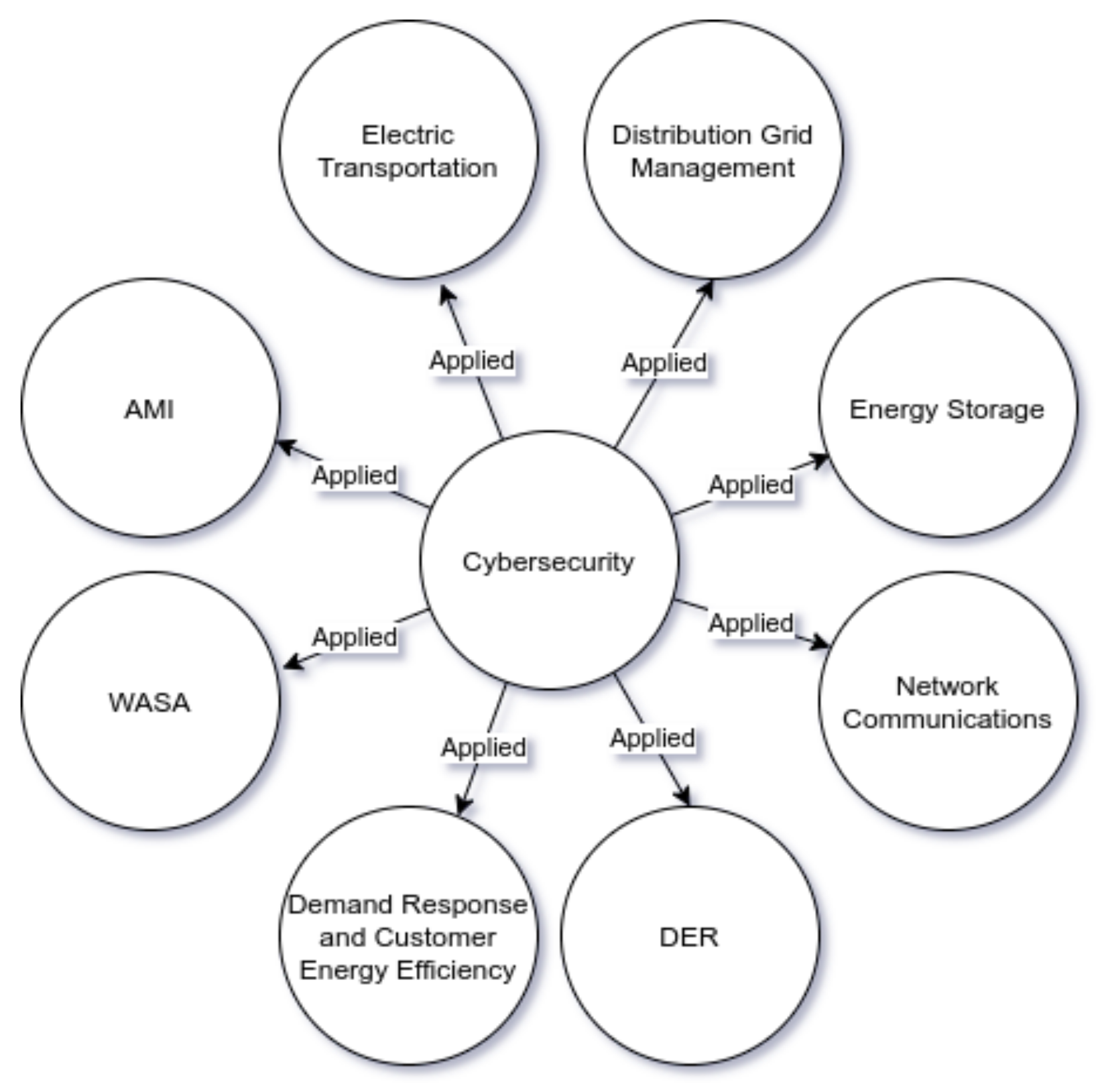












| NIST Priority Areas | |||||||
|---|---|---|---|---|---|---|---|
| Distribution Grid Management | Energy Storage | AMI | Electric Transportation | Network Communications | Demand Response and Consumer Energy Efficiency | WASA | DER |
| [29,42,43,49] | [29] | [29,30,31,39] [33,34,35,38] [32,36,37,40] [44,45,46,47] [48,49] | [29] | [29,30,31,38] [33,34,35,36] [32,37,44,45] [46,47,48,49] | [29] | [29] | [29] |
| NIST Conceptual Domains | ||||||
|---|---|---|---|---|---|---|
| Transmission | Generation | Distribution | Markets | Customer | Service Provider | Operations |
| [29,42,43] | [29,42,43] | [29,42,43] | [29] | [29,30,31,39] [33,34,35,38] [32,36,37,40] [44,45,46,47] [48] | [29,30,31,39] [33,34,35,38] [32,36,37,40] [44,45,46,47] [48] | [29,42,43,49] |
| Trust Components | ||||
|---|---|---|---|---|
| Direct Trust | Indirect Trust | Tested Against Trust Attacks | Risk Component | Knowledge Component |
| [29,30,31,39] [33,34,35,38] [36,37,42,43] [32,40] | [29,30,31,33] [34,35,42,43] [32,36,37,40] | [32,37] | - | [29,30,31,39] [36,38,42,43] [32,37,40] |
| Trust Components | ||||
|---|---|---|---|---|
| Direct Trust | Indirect Trust | Tested Against Trust Attacks | Risk Component | Knowledge Component |
| [52,53,54,55] [56,57] | [52,53] | - | - | [52,53,54,55] [56,57] |
| NIST Priority Areas | |||||||
|---|---|---|---|---|---|---|---|
| Distribution Grid Managemen | Energy Storage | AMI | Electric Transportation | Network Communication | Demand Response and Consumer Energy Efficiency | WASA | DER |
| [79,80,84] | - | - | - | - | [71,76] | - | [73,78,82] |
| NIST Conceptual Domains | ||||||
|---|---|---|---|---|---|---|
| Transmission | Generation | Distribution | Markets | Customer | Service Provider | Operations |
| [79,80,84] | - | [78,79,80,82,84] | [73,76] | - | - | [71,79,80,84] |
| Trust Components | ||||
|---|---|---|---|---|
| Direct Trust | Indirect Trust | Tested Against Trust Attacks | Risk Component | Knowledge Component |
| [71,73,76,78] [79,80,82,84] | [71,73,76,79,84,88] | - | [76] | [71,73,76,78] [78,79,80,82] |
| Paper | MAS Architecture | Type of Testing | Tool Used |
|---|---|---|---|
| Zhao et al. [71] | Decentralized | Simulation | JADE |
| Cintuglu et al. [78] | Decentralized | Simulation | - |
| Cunningham et al. [80] | Centralized | Simulation | JADE |
| Alavikia et al. [73] | Decentralized | Simulation | PJM 5-bus system |
| Matei et al. [79] | Decentralized | Simulation | - |
| Guemkam et al. [89] | Centralized | Simulation | Utopia, MOISE |
| Hussain et al. [82] | Centralized | Simulation | Jack-AOS |
| Borowski et al. [84] | Decentralized | Simulation | JADE, EPOCHS, PPSCAD/EMTDC |
| Pereira et al. [76] | Decentralized | Simulation | JADE, GridLab-D |
| Level | Devices |
|---|---|
| Level 9 | CB1A, IED1A, CB1B, IED1B |
| Level 8 | IL2, IL1 |
| Level 7 | CB1C, DLI1, IED1C, DLI2 |
| Level 6 | CB2D, CB2C, IED2D, IED2C, BUS2, BUS1 |
| Level 5 | CB3B, CB3A, IED3B, IED3A, DLTB, DLTA |
| Level 4 | CB4B, CB4A, CB4C, CB5B, CB5A, CB6A, CB5C, IED4B, IED4A, IED4C, IED5C, IED5A, IED5B, TXA, TXB |
| Level 3 | CB2B, CB2A, IED2B, IED2A, BUS4, BUS3 |
| Level 2 | DL66B, DL66A, OC4C, OC4A, OC4B, OC5B, OC5A, OC5C |
| Level 1 | CT1C, CT1A, CT1B, CT2C, CT2A, CT2D, CT2B, CT3B, CT3A, CT4C, CT4A, CT4B, CT5B, CT5C, CT5A, PT2A, PT2B, PT6A, PT3A, OL2, OL1 |
| Address Type | Access Type | Address Size | Function/Query | Function Code (Hex) |
|---|---|---|---|---|
| Read Coil | 0x01 | |||
| Coil | Write/Read | 1 bit | Write Multiple Coils | 0x0F |
| Write Single Coil | 0x05 | |||
| Read Holding Register | 0x03 | |||
| Holding Register | Write/Read | 2 bytes | Write Multiple Registers | 0x10 |
| Write Single Register | 0x06 | |||
| Discrete Input | Read | 1 bit | Read Discrete Input | 0x02 |
| Input Register | Read | 2 bytes | Read Input Register | 0x04 |
| Server | |||||
|---|---|---|---|---|---|
| Attack | Labelled Packets | External | Percentage (External) | Internal | Percentage (Internal) |
| CNC | 76 | 76 | 100% | 76 | 100% |
| Exploit | 780 | 780 | 100% | 780 | 100% |
| Moving Files | 39 | 39 | 100% | 39 | 100% |
| Send Fake Command | 6 | 6 | 100% | 6 | 100% |
| Client | |||||
|---|---|---|---|---|---|
| Attack | Labelled Packets | External | Percentage (External) | Internal | Percentage (Internal) |
| CNC | 11 | 11 | 100% | 11 | 100% |
| Moving Files | 17 | 17 | 100% | 17 | 100% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Boakye-Boateng, K.; Ghorbani, A.A.; Lashkari, A.H. A Trust-Influenced Smart Grid: A Survey and a Proposal. J. Sens. Actuator Netw. 2022, 11, 34. https://doi.org/10.3390/jsan11030034
Boakye-Boateng K, Ghorbani AA, Lashkari AH. A Trust-Influenced Smart Grid: A Survey and a Proposal. Journal of Sensor and Actuator Networks. 2022; 11(3):34. https://doi.org/10.3390/jsan11030034
Chicago/Turabian StyleBoakye-Boateng, Kwasi, Ali A. Ghorbani, and Arash Habibi Lashkari. 2022. "A Trust-Influenced Smart Grid: A Survey and a Proposal" Journal of Sensor and Actuator Networks 11, no. 3: 34. https://doi.org/10.3390/jsan11030034
APA StyleBoakye-Boateng, K., Ghorbani, A. A., & Lashkari, A. H. (2022). A Trust-Influenced Smart Grid: A Survey and a Proposal. Journal of Sensor and Actuator Networks, 11(3), 34. https://doi.org/10.3390/jsan11030034








