Edge Intelligence in Smart Grids: A Survey on Architectures, Offloading Models, Cyber Security Measures, and Challenges
Abstract
:1. Introduction
- We have provided a synthesis of the most recent studies on the application of EI in SGs. It was discovered that the literature lacked a survey of this nature, and the purpose of the current article is to address this gap, particularly for the benefit of researchers who may interested in developing some knowledge about the subject.
- We conducted a detailed overview of edge computing architectures and those based on EI for deployment in SGs. Due to the paucity of comprehensive EI-based designs for SG latency-sensitive applications in the existing literature, we also discussed a deployment-friendly architecture for the integration of EI in SGs.
- We highlighted and emphasized a number of critical cybersecurity issues linked with edge computing, as well as discussed some available solutions to these challenges in SG applications. We provided additional details on how machine learning algorithms and blockchain technologies were used to solve these problems.
- We discussed the current challenges that are associated with SGs and EI, which have surfaced as a result of the confluence of these two ideas. These challenges include communication at the edge, big data processing, resource management, and effective big data offloading, to mention a few of them. These difficulties and possible paths for the future are presented with an intention to aid the development of potential solutions regarding the adoption of EI in SGs.
2. Related Surveys
- The keywords that characterize our area of interest were noted, namely “architectures”, “computation offloading”, “edge intelligence”, “smart grids”, “security”, and these were used to search within the Scopus and Google Scholar database among others that were taken into consideration.
- The search process returned more than 16,700 hits, which were then narrowed down based on the period covered within the last decade. In addition, these hits were improved based on the following important categories: “architectures”, “offloading procedures”, and “security”. These keywords were used to manually narrow down our selection to around 250 articles, of which 234 were included in this article. The articles omitted were those that did not contribute directly to our area of interest.
- Furthermore, all survey articles found within this narrowed list were then culled and analyzed to establish the originality of the current article, for which we will now discuss these related survey articles.
3. Overview of Edge Intelligence and Smart Grid
3.1. Edge Intelligence
3.1.1. Edge Computing
Concepts Closely Related to Edge Computing
- (i)
- Mobile Ad hoc: Originally, a mobile ad hoc cloud was proposed as a potentially transformative solution to the issues inherent in the traditional cloud model. This concept consists of many mobile cloudlets (nearby mobile servers) that are utilized by mobile end users (i.e., smart phones, tablets, etc.) to offload intensive computational workloads in an ad hoc manner [47]. Additionally, it promises to accelerate the execution of computationally intensive operations and minimize the energy consumed by devices. Due to its self-configuration and self-maintenance characteristics, this paradigm has attracted significant interest in the frontiers of communication technologies over the last decades.However, despite its advantages, mobile ad hoc networking has some significant issues, including the lack of an open network architecture, shared wireless medium, resource constraints, and a highly dynamic network topology [48]. Furthermore, due to the shared nature of the mobile ad hoc architecture, security is one of the most crucial challenges in this concept. Various articles have attempted to address these issues in a variety of ways. For example, the authors in [49] have proposed an enforced cooperative bait detection scheme (CBDS).
- (ii)
- Cloudlet: Cloudlet, like other post-cloud computing concepts, may be viewed as an extension of the standard cloud. This paradigm is comprised of relatively small-scale mobility support clouds located near mobile end-users. It was created primarily to reduce the computation offloading latency across wide area networks (WANs). Existing work from around 2009 is included among the early work on cloudlet [50]. They have also established the cloudlet concept as a typical intermediate layer in a three-tier architecture. The architecture, as the name implies, is composed of three tiers: end-device, an edge cloud platform, and a centralized data center [51]. Fundamentally, cloudlet is used to alleviate pressure on the remote Internet cloud by shifting computation resources to mobile devices with minimal latency.The key benefit of cloudlets is their capacity to support mobility. A typical cloudlet consists of a server and wireless access points that are linked together through a local area network (LAN) [52]. Given the distributed nature of these cloudlets, managing large numbers of cloudlets in an efficient and effective manner remains a significant difficulty. Furthermore, cloudlets suffer from a number of challenges, including network capacity and backhaul linkages, as a result of the rapid growth in the demand for multimedia services [53]. The authors in [54] provided a thorough survey of existing works entirely focused on cloudlet-based mobile computing. Whereas, in a separate article, a secured cloudlet-based recommendation system for EVs was presented [55].
- (iii)
- Fog Computing: In comparison to other existing post-cloud computing paradigms, fog computing appears to be the most popular, along with edge computing. The authors of [16] conducted a thorough study on these emerging paradigms with focus on performance metrics. The ability of these two paradigms to support the introduction of new IoT applications such as smart cities, SGs, EVs, and wireless sensor and actuator networks is the primary reason for their increased popularity. Furthermore, they are both known for their essential feature of shifting from a centralized to a decentralized architecture in which computation services are performed close to end-users rather than in the cloud. For these reasons, most researchers have been using these paradigms interchangeably, despite the fact that they are not identical [24,56]. As with Zhang and Tao [57], we also distinguish these concepts for the sake of clarity. According to the OpenFog Consortium [58], these paradigms can be distinguished based on where the intelligence and computing power are executed.For example, fog computing can enable computing, networking, storage, control, and acceleration anywhere from the cloud to end-devices (on the network side), whereas edge computing may only be capable of performing these functions at the edge (end node side). In general, fog computing has been recognized as a form of edge computing. Cisco defines fog computing as a highly virtualized platform that provides computing, storage, and networking services between end devices and traditional cloud computing data centers, which are typically but not exclusively located at the network’s edge [59]. The term “fog computing” is distinct due to the fact that, literally, we consider fog in the natural geological environment as being closer to people than clouds [53].According to the literature, fog computing has been integrated into various business domains with the goal of addressing a variety of challenges. For example, the authors in [60] have provided a detailed classification of fog computing applications such as smart cities, augmented reality (AR), and virtual reality (VR) from a machine learning (ML) perspective, with the goal of facilitating decision-making. An investigation into how to deal with security and privacy issues was conducted in [61,62]. The authors of [63] proposed a fog computing-based framework for SG applications (microgrid to be specific). Hussain and Beg highlighted the importance of integrating fog computing as a supporting technology for real-time SG data analytics [64]. In summary, the devices used in the fog computing-based architecture are not programmed to conduct any computation functions, but instead to serve as the network’s data acquisition component while the analysis of data is performed in the gateway. As a result, fog computing experiences significant challenges such as latency and inefficient bandwidth utilization [65].
- (iv)
- Mist Computing: Mist computing can be thought of as a lightweight version of fog computing that is located very close to the network edge [66]. This paradigm serves as a bridge between the fog and IoT tiers, with the goal of bringing fog computing functions even closer to end users. As a result, the traditional fog computing architecture experiences less data transmission delay. Mist computing, such as fog computing, is often referred to as edge computing, which is not the case [66]. Mist computing occurs at the network’s extreme edge, which is comprised of microcontrollers and sensors. In this instance, mist computing involves the use of microcomputers and microcontrollers to offer processed data as input to fog computing nodes and, ultimately, towards cloud computing services. This paradigm aims to reduce latency and traffic issues by allowing processed data at the network’s edge to be transmitted to the cloud storage system via the network’s fog nodes.
- (v)
- Mobile Edge Computing: According to the European Telecommunications Standards Institute (ETSI), mobile edge computing (MEC) is a new platform that provides information technology (IT) and cloud computing capabilities within the radio access network (RAN) near mobile subscribers [18]. This paradigm was first realized in 2013 by IBM and Nokia Siemens. The authors in [51] have provided a detailed discussion of the evolution of this paradigm. Because of the benefits provided by MEC, the European fifth generation (5G) infrastructure public-private partnerships (PPP) have identified it as one of the next-generation 5G networks that will massively revolutionize mobile network intelligence. Reduced latency, improved energy efficiency for mobile devices, power saving mechanisms, support for context-awareness, and improved privacy and security for mobile applications are some of the primary benefits of MEC. These advantages stem from the critical role of this computing paradigm, which shifts data-intensive tasks to the edge and concurrently executes data processing near end-users rather than in a centralized cloud. As a result, there are fewer bottlenecks in the core, and heavy computational tasks are offloaded to the edge via network operators [51].
Essential Features of Edge Computing
- (i)
- Computing and Networking: Edge computing allows for advanced IT and network infrastructures to be shifted to the network’s edge, thus allowing computing and storage to take place close to where data are generated.
- (ii)
- Storage: In the edge computing framework, computing and storage devices such as cloudlets, fog nodes, or micro-data centers are deployed at the base station, which is located near the end-devices, to avoid obstructions and network failures. This has the potential to significantly contribute to the success of SG deployment because it promises to reduce data transmission delays while also improving QoS and quality of experience (QoE) for end users.
- (iii)
- Data Management: It is noted that the centralized data management model used in cloud computing fails to keep up with the rate at which data in SGs are generated. Thus, several studies have recently been conducted to investigate the adoption of a decentralized data management framework. For example, the authors in [67] have used edge computing to present a secure and efficient data management system for mobile healthcare systems.
Key Enabling Technologies for Edge Computing
- (i)
- Containerization: It has been noted that the widespread deployment of edge computing has been constrained by limitations associated with the use of virtual machines (VMs) as well as the bandwidth utilization of wide area networks (WANs) [68]. As a result, the emergence of containerization as a viable solution among virtualization technologies has garnered considerable attention from researchers and developers alike. Containerization is one of the most widely used virtual technologies for addressing some of the issues that VMs encounter when deployed in cloud computing paradigms. Containers, like VMs, partition the resources of physical machines into numerous user-space instances. However, these containerized instances are isolated and have a much smaller footprint than VMs. Consequently, large internet-based companies such as Google, Spotify, eBay, and Twitter, among others, have been experimenting with containerization technologies in order to scale their services efficiently.In terms of container technologies, Docker has emerged as the most popular and widely adopted solution for enabling edge computing. Many developers typically leverage Docker or Kubernetes, the two most widely used container technologies, to overcome some of the challenges inherent in latency-sensitive IoT applications. These technologies have been developed as a viable approach for developing an operating system tailored to these applications [69].
- (ii)
- Orchestration: Orchestration is defined in [69] as a technology for managing interactions between virtualized components such as containers and for composing, managing, and terminating services. To meet the requirements of orchestration models, the authors in [70] expanded the definition of orchestration to include the management of services workload placement and processing via dynamic and intelligent resource configuration in order to meet services level agreements. Orchestration technologies are divided into two categories: service orchestration and infrastructure orchestration. Orchestration is a broad concept in the context of edge computing, consisting of numerous management efforts at various levels. Orchestration is critical in multi-tier edge computing to ensure efficient and reliable operation of all components [71]. Additionally, in edge computing, a typical orchestrator is used to manage resource allocation.Although several works in the literature have used this technology to address a variety of problems, orchestration still faces issues with QoS estimation and matchmaking [72]. Consequently, the authors in [73] introduced an intelligent-based architecture for IoT-based applications that combines orchestration (used between the cloud and the edge) and AI techniques (which provides for the intelligence capability of an architecture). In a separate article, authors in [74] proposed an online orchestration framework for cross-edge service function chaining to improve cost-efficiency.
- (iii)
- Fifth-Generation (5G) Mobile Network: Cellular communication technologies have advanced tremendously over the last decades. Specifically, over the last two decades, cellular networks have evolved significantly from third-generation (3G) to fifth-generation (5G) technologies, necessitated by the proliferation of IoT devices [45,75]. Initially, the goal of preceding technologies such as 3G and 4G was to develop high-speed wireless networks capable of supporting the transition from voice-centric to multimedia-centric traffic. However, by advancing upon its predecessors, 5G promises to outperform them by delivering remarkable benefits to mobile end users, such as enhanced Mobile Broadband (eMBB), ultra-reliable low-latency communications (URLLC), and massive machine type communications (mMTC). To fully realize the benefits of a variety of applications such as AR, VR, and smart environments, 5G has been consolidated to facilitate and enhance the communication infrastructure’s overall performance. In 2020, 5G drew considerable attention from researchers as a promising wireless cellular network standard capable of meeting the stringent requirements of next-generation systems.This technology has been integrated into a variety of smart environments, including SGs [76], smart healthcare [77], and smart cities [78], each of which addresses a unique set of challenges. While 5G brings with it a slew of promising benefits, legacy computing paradigms may deny end users the opportunity to explore them. To this end, edge computing appears to be a viable solution for enabling the evolution of 5G by essentially pushing cloud functions to end users [79]. Specifically, the authors in [79] presented a taxonomy for edge computing in 5G, and emphasized critical aspects of its coordination, such as computational platforms, key attributes, 5G functions, and performance metrics. As a summary, a comprehensive investigation into MEC in 5G and IoT contexts can be accessed in [45].
Benefits of Edge Computing
- (i)
- Reduced Latency: The concept of edge computing has proven to be very beneficial for latency-sensitive applications because it aims to reduce data transmission times while also making the network structure easier to implement [80]. Edge computing has been identified as a suitable platform in this regard to ensure that the requirements emerging with SG applications such as wide area situational awareness (WASA), outage management, and substation automation are met appropriately as discussed in details in Section 3.2.3.
- (ii)
- Mobility enhancement: An edge computing architecture typically consists of geographically distributed fog and edge devices distributed across the network for computational and storage purposes. Edge computing, as a result of this benefit, can provide mobility support to all mobile end-devices used in SGs.
- (iii)
- Ease of data processing: Because of its ability to be deployed in close proximity to data sources, edge computing has the advantage of analyzing and extracting some useful insights from “big data”. Furthermore, since the number of smart meters deployed in SGs is expected to grow at an exponential rate in the future, edge computing can help manage and analyze data generated by smart meters in a more effective and efficient manner.
- (iv)
- Location Awareness: Unlike cloud computing, the edge computing paradigm can perform some computation functions on data based on its geographic location. Furthermore, this can be accomplished without the use of cloud services. Edge computing significantly performs better than traditional cloud computing in terms of location awareness, which will contribute to the success of WASA in SGs.
3.1.2. Artificial Intelligence
Deep Learning
AI for and on Edge Computing
3.1.3. Summary of the Discussion on Edge Intelligence
3.2. Smart Grid: A General Overview
3.2.1. Key Enabling Technologies of Smart Grid
Advanced Metering Infrastructure
Distributed Generation
Microgrid
Electric Vehicles
Internet of Things
Artificial Intelligence for Smart Grids
Edge Computing
Distributed Ledger Technology
3.2.2. Application Areas in Smart Grids
Substation Automation
Home Energy Management System
Wide-Area Situational Awareness
Overhead Transmission Line Monitoring
Demand Response
Outage Management
Plug-In Hybrid Electric Vehicles (PHEVs) Charging
Asset Management
3.2.3. Summary of the Discussion on Smart Grids
4. Architecture for Deploying Edge Intelligence in Smart Grids
4.1. General Edge Computing Architecture
4.2. Edge Intelligence-Based Architectures for SGs
4.3. Summary and Comparison
5. Computation Offloading for Edge Intelligence in Smart Grids
5.1. What Is Computation Offloading
5.2. Why Do We Need Computation Offloading
5.3. Single-User Case
5.4. Multi-User Case
5.5. Summary
6. Cyber Security Challenges and Solutions in Edge Intelligence-Based Smart Grids
6.1. Security Challenges
6.1.1. Distributed Denial-of-Service (DDoS)
6.1.2. Man-in-the-Middle
6.1.3. Physical Damage
6.1.4. Service or VM Manipulation
6.1.5. False Data Injection
6.2. Key Approaches to Solving Cyber Security Issues
6.2.1. ML and DL Algorithms for Cybersecurity
Support Vector Machine
K-Nearest Neighbor
Decision Tree
Deep Belief Network
Recurrent Neural Networks
Convolutional Neural Networks
6.2.2. Blockchain for Cybersecurity
6.3. Summary and Discussion
7. Research Challenges and Future Directions
7.1. Resource Management
7.1.1. Communication and Big Data Processing at the Edge
7.1.2. Load Balancing
7.2. Advanced AI Technologies
7.3. Intelligent Computation Offloading
7.4. Secured and Robust Situational Awareness Framework for Smart Grid
- SG’s control system must work consistently and be responsive to any real-time dangers detected in such an environment. However, cloud-based SG architectures struggle to meet the requirements for swiftly responding to real-time threats without degrading end-user QoS.
- Due to sensitivity of data acquired from SGs and IoT devices such as smart meters, and sensors, SGs must have an uncompromising level of security, as they can be vulnerable to cyber assaults.
- Due to the variability of power terminals and the diversity of communication protocols, SGs have faced a number of interconversion and interoperability issues. Additionally, there are issues with establishing and deploying diverse networks, administering and sustaining networks. This complicates the efficient and effective utilization of a large number of various terminals in SGs.
7.5. Privacy Concerns
7.6. Facilitation of Two-Way Communication
7.7. Access Control Mechanisms
7.8. Trust
7.9. Practical Implications of Research Directions
- A decrease in latency: The use of edge computing can make it possible to drastically cut down on the amount of time spent transmitting data within different SG elements. This will contribute to the real-time monitoring of frequency and voltage characteristics within the grid, hence eliminating power factor penalties.
- Privacy of transmitted data: While there is a significant risk of data leakage and other security issues associated with SGs, it has become abundantly evident that edge intelligence may help limit these kinds of problems to a significant degree. This is something that can be accomplished by performing computations, storing data, and processing them locally, as well as having the capacity to identify abnormalities using machine learning algorithms.
- Capabilities to engage in transactive energy: The edge intelligence present in SGs has the potential to facilitate the easier integration of microgrids, which in turn makes it possible for prosumers and energy providers to engage in economic transactions. This will further guarantee that there is a fair balance of demand and supply within the network, which will ultimately result in the grid becoming more stable and reliable.
- Increased dependability as a result of regular power status reports: Edge intelligence will make real-time transmission of network parameters possible, which will improve both the analysis of and the response to grid outages.
- Decentralized voltage control: Due to the incorporation of microgrids in SGs, there is a larger potential for voltage instability throughout the grid. Edge intelligence provides a decentralized framework for monitoring these oscillations and promptly implementing mitigation techniques to reduce their consequences.
- Asset management and planning: Because of the ever-increasing growth in the production, acquisition, and incorporation of renewable energy into the grid, there is a growing demand for asset management and planning that accounts for expansion within the grid. Edge intelligence provides a platform for the real-time documenting of such assets, as well as the analysis of their influence on the growth of the grid and the potential for future projections about the expansion and deployment of new assets.
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| Acronym | Meaning |
| 3G | Third Generation |
| 4G | Fourth Generation |
| 5G | Fifth Generation |
| ACS-CLPSO | Ant Colony System-Comprehensive Learning Particle Swarm Optimizer |
| ADMM | Alternating Direction of Method Multipliers |
| AI | Artificial Intelligence |
| AIoT | Artificial Intelligence of Things |
| AMI | Advanced Metering Infrastructure |
| ANN | Artificial Neural Network |
| AR | Augmented Reality |
| BiJOR | Bilevel Optimization Approach |
| BP | Back-Propagation |
| BRI | Better Response with Inertia |
| CBDS | Cooperative Bait Detection Scheme |
| CNN | Convolutional Neural Network |
| CO | Carbon diOxide |
| CPU | Central Processing Unit |
| DC | Direct Current |
| DDoS | Distributed Denial of Service |
| DG | Distributed Generation |
| DG | Distributed Generaion |
| DL | Distributed Learning |
| DLT | Distributed Ledger Technology |
| DoS | Denial of Service |
| DR | Demand Response |
| DSM | Demand Side Management |
| EC | Edge Computing |
| EI | Edge Intelligence |
| eMBB | Enhanced Mobile Broadband |
| EnPEO-DBN | Ensemble Population External Optimization-Based Deep Belief Network |
| ETSI | European Telecommunications Standards Institute |
| EVs | Electric Vehicles |
| FL | Federated Learning |
| G2V | Grid to Vehicle |
| HAN | Home Area Networks |
| HEMS | Home Energy Management Systems |
| IBM | International Business Machines |
| ICT | Information and Communication Technology |
| IoT | Internet of Things |
| IoVs | Internet of Vehicles |
| IT | Information Technology |
| K-NN | K-Nearest Neighbor |
| LAN | Local Area Networks |
| MAS | Multi-Agent System |
| MDMS | Meter Data Management System |
| MEC | Mobile Edge Computing |
| MECO | Mobile Edge Computation Offloading |
| MITM | Man-in-the-Middle |
| ML | Machine Learning |
| MM | Mobility Management |
| mMTC | Massive Machine Type Communications |
| NANs | Neighborhood Area Network |
| NILM | Non-Intrusive Load Monitoring |
| OD | Offloading Decision |
| OOCS | Optimal Offloading with Caching-Enhancement Scheme |
| OOCS | Optimal Offloading with Caching-Enhancement Scheme |
| P2P | Peer-to-Peer |
| PEO | Population External Optimization |
| PHEV | Plug-in Hybrid Electric Vehicles |
| PPP | Public Private Partnerships |
| PSO | Particle Swarm Optimization |
| PSO | Particle Swarm Optimization |
| QoE | Quality of Experience |
| QoS | Quality of Service |
| RA | Resource Allocation |
| RES | Renewable Energy Source |
| RFID | Radio Frequency Identification |
| RNN | Recurrent Neural Network |
| RTUs | Remote Terminal Units |
| SAS | Substation Automation Systems |
| SBSs | Small-Cell Base Stations |
| SCADA | Supervisory Control and Data Acquisition |
| SDP | Software Defined Perimeter |
| SGD | Stochastic Gradient Descent |
| SGs | Smart Grids |
| SVM | Support Vector Machine |
| UAVs | Unmanned Aerial Vehicles |
| uRLLC | Ultra-Reliable Low-Latency Communications |
| V2G | Vehicle to Grid |
| VMs | Virtual Machines |
| VR | Virtual Reality |
| WANs | Wide Area Networks |
| WASA | Wide Area Situational Awareness |
| WSN | Wireless Sensor Network |
References
- Mishra, J.; Sheetlani, J.; Reddy, K.H.K.; Roy, D.S. A novel edge-supported cost-efficient resource management approach for smart grid system. In Progress in Computing, Analytics and Networking; Springer: Berlin/Heidelberg, Germany, 2018; pp. 369–380. [Google Scholar]
- Yao, J.; Li, Z.; Li, Y.; Bai, J.; Wang, J.; Lin, P. Cost-efficient tasks scheduling for smart grid communication network with edge computing system. In Proceedings of the 2019 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 272–277. [Google Scholar]
- Molokomme, D.N.; Chabalala, C.S.; Bokoro, P.N. A review of cognitive radio smart grid communication infrastructure systems. Energies 2020, 13, 3245. [Google Scholar] [CrossRef]
- Kabalci, E.; Kabalci, Y. Smart Grids and Their Communication Systems; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar]
- Slama, S.B. Prosumer in smart grids based on intelligent edge computing: A review on Artificial Intelligence Scheduling Techniques. Ain Shams Eng. J. 2021, 13, 101514. [Google Scholar]
- Mehmood, M.Y.; Oad, A.; Abrar, M.; Munir, H.M.; Hasan, S.F.; Muqeet, H.; Golilarz, N.A. Edge computing for IoT-enabled smart grid. Secur. Commun. Netw. 2021, 2021, 5524025. [Google Scholar] [CrossRef]
- U.S. Department of Energy. Available online: https://www.energy.gov/oe/office-electricity (accessed on 24 April 2022).
- Strategic National Smart Grid Vision for the South African Electricity Supply Industry. Available online: https://www.ee.co.za/wp-content/uploads/2017/12/Smart-Grid-Vision-Document-2017.pdf (accessed on 22 January 2022).
- Onumanyi, A.J.; Isaac, S.J.; Kruger, C.P.; Abu-Mahfouz, A.M. Transactive energy: State-of-the-art in control strategies, architectures, and simulators. IEEE Access 2021, 9, 131552–131573. [Google Scholar] [CrossRef]
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergut, S.; Buccella, C.; Cecati, C.; Hancke, G.P. Smart grid technologies: Communication technologies and standards. IEEE Trans. Ind. Inform. 2011, 7, 529–539. [Google Scholar] [CrossRef] [Green Version]
- Bera, S.; Misra, S.; Rodrigues, J.J. Cloud computing applications for smart grid: A survey. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 1477–1494. [Google Scholar] [CrossRef]
- Li, Q.; Deng, Y.; Sun, W.; Li, W. Communication and Computation Resource Allocation and Offloading for Edge Intelligence Enabled Fault Detection System in Smart Grid. In Proceedings of the 2020 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Tempe, AZ, USA, 11–13 November 2020; pp. 1–7. [Google Scholar]
- Zhao, S.; Li, F.; Li, H.; Lu, R.; Ren, S.; Bao, H.; Lin, J.H.; Han, S. Smart and practical privacy-preserving data aggregation for fog-based smart grids. IEEE Trans. Inf. Forensics Secur. 2020, 16, 521–536. [Google Scholar] [CrossRef]
- Jiang, D.; Zhang, Y.; Song, H.; Wang, W. Intelligent optimization-based energy-efficient networking in cloud services for multimedia big data. In Proceedings of the 2018 IEEE 37th International Performance Computing and Communications Conference (IPCCC), Orlando, FL, USA, 17–19 November 2018; pp. 1–6. [Google Scholar]
- Goyal, S.; Bhushan, S.; Kumar, Y.; Rana, A.u.H.S.; Bhutta, M.R.; Ijaz, M.F.; Son, Y. An optimized framework for energy-resource allocation in a cloud environment based on the whale optimization algorithm. Sensors 2021, 21, 1583. [Google Scholar] [CrossRef]
- Aslanpour, M.S.; Gill, S.S.; Toosi, A.N. Performance evaluation metrics for cloud, fog and edge computing: A review, taxonomy, benchmarks and standards for future research. Internet Things 2020, 12, 100273. [Google Scholar] [CrossRef]
- Mach, P.; Becvar, Z. Mobile edge computing: A survey on architecture and computation offloading. IEEE Commun. Surv. Tutor. 2017, 19, 1628–1656. [Google Scholar] [CrossRef] [Green Version]
- Mao, Y.; You, C.; Zhang, J.; Huang, K.; Letaief, K.B. A survey on mobile edge computing: The communication perspective. IEEE Commun. Surv. Tutor. 2017, 19, 2322–2358. [Google Scholar] [CrossRef] [Green Version]
- Yang, R.; Yu, F.R.; Si, P.; Yang, Z.; Zhang, Y. Integrated blockchain and edge computing systems: A survey, some research issues and challenges. IEEE Commun. Surv. Tutor. 2019, 21, 1508–1532. [Google Scholar] [CrossRef]
- Zhang, X.; Biagioni, D.; Cai, M.; Graf, P.; Rahman, S. An edge-cloud integrated solution for buildings demand response using reinforcement learning. IEEE Trans. Smart Grid 2020, 12, 420–431. [Google Scholar] [CrossRef]
- Chang, Z.; Liu, S.; Xiong, X.; Cai, Z.; Tu, G. A survey of recent advances in edge-computing-powered artificial intelligence of things. IEEE Internet Things J. 2021, 8, 13849–13875. [Google Scholar] [CrossRef]
- Deng, S.; Zhao, H.; Fang, W.; Yin, J.; Dustdar, S.; Zomaya, A.Y. Edge intelligence: The confluence of edge computing and artificial intelligence. IEEE Internet Things J. 2020, 7, 7457–7469. [Google Scholar] [CrossRef] [Green Version]
- Meloni, A.; Pegoraro, P.A.; Atzori, L.; Benigni, A.; Sulis, S. Cloud-based IoT solution for state estimation in smart grids: Exploiting virtualization and edge-intelligence technologies. Comput. Netw. 2018, 130, 156–165. [Google Scholar] [CrossRef]
- Hudson, N.; Hossain, M.J.; Hosseinzadeh, M.; Khamfroush, H.; Rahnamay-Naeini, M.; Ghani, N. A framework for edge intelligent smart distribution grids via federated learning. In Proceedings of the 2021 International Conference on Computer Communications and Networks (ICCCN), Athens, Greece, 19–22 July 2021; pp. 1–9. [Google Scholar]
- Ghosh, A.M.; Grolinger, K. Edge-cloud computing for Internet of Things data analytics: Embedding intelligence in the edge with deep learning. IEEE Trans. Ind. Inform. 2020, 17, 2191–2200. [Google Scholar]
- Lodhi, A.H.; Akgün, B.; Özkasap, Ö. State-of-the-art techniques in deep edge intelligence. arXiv 2020, arXiv:2008.00824. [Google Scholar]
- Lei, W.; Wen, H.; Wu, J.; Hou, W. MADDPG-based security situational awareness for smart grid with intelligent edge. Appl. Sci. 2021, 11, 3101. [Google Scholar] [CrossRef]
- Guo, S.; Dai, Y.; Guo, S.; Qiu, X.; Qi, F. Blockchain meets edge computing: Stackelberg game and double auction based task offloading for mobile blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5549–5561. [Google Scholar] [CrossRef]
- Islam, S.; Badsha, S.; Sengupta, S.; La, H.; Khalil, I.; Atiquzzaman, M. Blockchain-enabled intelligent vehicular edge computing. IEEE Netw. 2021, 35, 125–131. [Google Scholar] [CrossRef]
- Zhuang, P.; Zamir, T.; Liang, H. Blockchain for cybersecurity in smart grid: A comprehensive survey. IEEE Trans. Ind. Inform. 2020, 17, 3–19. [Google Scholar] [CrossRef]
- Rigas, E.S.; Ramchurn, S.D.; Bassiliades, N. Managing electric vehicles in the smart grid using artificial intelligence: A survey. IEEE Trans. Intell. Transp. Syst. 2014, 16, 1619–1635. [Google Scholar] [CrossRef]
- Gilbert, G.M.; Naiman, S.; Kimaro, H.; Bagile, B. A critical review of edge and fog computing for smart grid applications. In Proceedings of the International Conference on Social Implications of Computers in Developing Countries, Dar es Salaam, Tanzania, 1–3 May 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 763–775. [Google Scholar]
- Ferrag, M.A.; Babaghayou, M.; Yazici, M.A. Cyber security for fog-based smart grid SCADA systems: Solutions and challenges. J. Inf. Secur. Appl. 2020, 52, 102500. [Google Scholar] [CrossRef]
- Rosero, D.; Díaz, N.; Trujillo, C. Cloud and machine learning experiments applied to the energy management in a microgrid cluster. Appl. Energy 2021, 304, 117770. [Google Scholar] [CrossRef]
- Feng, C.; Wang, Y.; Chen, Q.; Ding, Y.; Strbac, G.; Kang, C. Smart grid encounters edge computing: Opportunities and applications. Adv. Appl. Energy 2021, 1, 100006. [Google Scholar] [CrossRef]
- Li, T.; Yang, J.; Cui, D. Artificial-intelligence-based algorithms in multi-access edge computing for the performance optimization control of a benchmark microgrid. Phys. Commun. 2021, 44, 101240. [Google Scholar] [CrossRef]
- Wu, Y.; Wu, Y.; Guerrero, J.M.; Vasquez, J.C. Digitalization and decentralization driving transactive energy Internet: Key technologies and infrastructures. Int. J. Electr. Power Energy Syst. 2021, 126, 106593. [Google Scholar] [CrossRef]
- Massaoudi, M.; Abu-Rub, H.; Refaat, S.S.; Chihi, I.; Oueslati, F.S. Deep learning in smart grid technology: A review of recent advancements and future prospects. IEEE Access 2021, 9, 54558–54578. [Google Scholar] [CrossRef]
- Wu, Y.; Wu, Y.; Guerrero, J.M.; Vasquez, J.C. Decentralized transactive energy community in edge grid with positive buildings and interactive electric vehicles. Int. J. Electr. Power Energy Syst. 2022, 135, 107510. [Google Scholar] [CrossRef]
- Yu, S.; Chen, X.; Zhou, Z.; Gong, X.; Wu, D. When deep reinforcement learning meets federated learning: Intelligent multitimescale resource management for multiaccess edge computing in 5G ultradense network. IEEE Internet Things J. 2020, 8, 2238–2251. [Google Scholar] [CrossRef]
- Zhou, Z.; Chen, X.; Li, E.; Zeng, L.; Luo, K.; Zhang, J. Edge intelligence: Paving the last mile of artificial intelligence with edge computing. Proc. IEEE 2019, 107, 1738–1762. [Google Scholar] [CrossRef] [Green Version]
- Muniswamaiah, M.; Agerwala, T.; Tappert, C.C. A Survey on Cloudlets, Mobile Edge, and Fog Computing. In Proceedings of the 2021 8th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2021 7th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), Washington, DC, USA, 26–28 June 2021; pp. 139–142. [Google Scholar]
- Xu, D.; Li, T.; Li, Y.; Su, X.; Tarkoma, S.; Jiang, T.; Crowcroft, J.; Hui, P. Edge Intelligence: Empowering Intelligence to the Edge of Network. Proc. IEEE 2021, 109, 1778–1837. [Google Scholar] [CrossRef]
- Amin, S.U.; Hossain, M.S. Edge intelligence and Internet of Things in healthcare: A survey. IEEE Access 2020, 9, 45–59. [Google Scholar] [CrossRef]
- Liu, Y.; Peng, M.; Shou, G.; Chen, Y.; Chen, S. Toward edge intelligence: Multiaccess edge computing for 5G and internet of things. IEEE Internet Things J. 2020, 7, 6722–6747. [Google Scholar] [CrossRef]
- Khan, W.Z.; Ahmed, E.; Hakak, S.; Yaqoob, I.; Ahmed, A. Edge computing: A survey. Future Gener. Comput. Syst. 2019, 97, 219–235. [Google Scholar] [CrossRef]
- Van Le, D.; Tham, C.K. A deep reinforcement learning based offloading scheme in ad-hoc mobile clouds. In Proceedings of the IEEE INFOCOM 2018-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15–19 April 2018; pp. 760–765. [Google Scholar]
- Yang, H.; Luo, H.; Ye, F.; Lu, S.; Zhang, L. Security in mobile ad hoc networks: Challenges and solutions. IEEE Wirel. Commun. 2004, 11, 38–47. [Google Scholar] [CrossRef]
- Khalaf, O.I.; Ajesh, F.; Hamad, A.A.; Nguyen, G.N.; Le, D.N. Efficient dual-cooperative bait detection scheme for collaborative attackers on mobile ad-hoc networks. IEEE Access 2020, 8, 227962–227969. [Google Scholar] [CrossRef]
- Satyanarayanan, M.; Bahl, P.; Caceres, R.; Davies, N. The case for vm-based cloudlets in mobile computing. IEEE Pervasive Comput. 2009, 8, 14–23. [Google Scholar] [CrossRef]
- Taleb, T.; Samdanis, K.; Mada, B.; Flinck, H.; Dutta, S.; Sabella, D. On multi-access edge computing: A survey of the emerging 5G network edge cloud architecture and orchestration. IEEE Commun. Surv. Tutor. 2017, 19, 1657–1681. [Google Scholar] [CrossRef] [Green Version]
- Yahuza, M.; Idris, M.Y.I.B.; Wahab, A.W.B.A.; Ho, A.T.; Khan, S.; Musa, S.N.B.; Taha, A.Z.B. Systematic review on security and privacy requirements in edge computing: State of the art and future research opportunities. IEEE Access 2020, 8, 76541–76567. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, X.; Zhang, Y.; Wang, L.; Yang, J.; Wang, W. A survey on mobile edge networks: Convergence of computing, caching and communications. IEEE Access 2017, 5, 6757–6779. [Google Scholar] [CrossRef]
- Pang, Z.; Sun, L.; Wang, Z.; Tian, E.; Yang, S. A survey of cloudlet based mobile computing. In Proceedings of the 2015 International Conference on Cloud Computing and Big Data (CCBD), Shanghai, China, 4–6 November 2015; pp. 268–275. [Google Scholar]
- Teimoori, Z.; Yassine, A.; Hossain, M.S. A Secure Cloudlet-based Charging Station Recommendation for Electric Vehicles Empowered by Federated Learning. IEEE Trans. Ind. Inform. 2022, 18, 6464–6473. [Google Scholar] [CrossRef]
- Puthal, D.; Mohanty, S.P.; Bhavake, S.A.; Morgan, G.; Ranjan, R. Fog computing security challenges and future directions [energy and security]. IEEE Consum. Electron. Mag. 2019, 8, 92–96. [Google Scholar] [CrossRef]
- Zhang, J.; Tao, D. Empowering things with intelligence: A survey of the progress, challenges, and opportunities in artificial intelligence of things. IEEE Internet Things J. 2020, 8, 7789–7817. [Google Scholar] [CrossRef]
- openfog. OpenFog Reference Architecture for Fog Computing. Available online: https://www.iiconsortium.org/pdf/OpenFog_Reference_Architecture_2_09_17.pdf (accessed on 19 February 2022).
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In Proceedings of the Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing; Helsinki, Finland, 17 August 2012, pp. 13–16.
- Guevara, J.C.; Torres, R.d.S.; da Fonseca, N.L. On the classification of fog computing applications: A machine learning perspective. J. Netw. Comput. Appl. 2020, 159, 102596. [Google Scholar] [CrossRef]
- Khan, S.; Parkinson, S.; Qin, Y. Fog computing security: A review of current applications and security solutions. J. Cloud Comput. 2017, 6, 1–22. [Google Scholar] [CrossRef]
- Zhang, P.; Zhou, M.; Fortino, G. Security and trust issues in fog computing: A survey. Future Gener. Comput. Syst. 2018, 88, 16–27. [Google Scholar] [CrossRef]
- Barik, R.K.; Gudey, S.K.; Reddy, G.G.; Pant, M.; Dubey, H.; Mankodiya, K.; Kumar, V. FogGrid: Leveraging fog computing for enhanced smart grid network. In Proceedings of the 2017 14th IEEE India Council International Conference (INDICON), Roorkee, India, 15–17 December 2017; pp. 1–6. [Google Scholar]
- Hussain, M.; Beg, M. Fog computing for internet of things (IoT)-aided smart grid architectures. Big Data Cogn. Comput. 2019, 3, 8. [Google Scholar] [CrossRef] [Green Version]
- Preden, J.S.; Tammemäe, K.; Jantsch, A.; Leier, M.; Riid, A.; Calis, E. The benefits of self-awareness and attention in fog and mist computing. Computer 2015, 48, 37–45. [Google Scholar] [CrossRef]
- Galambos, P. Cloud, fog, and mist computing: Advanced robot applications. IEEE Syst. Man Cybern. Mag. 2020, 6, 41–45. [Google Scholar] [CrossRef]
- Li, X.; Huang, X.; Li, C.; Yu, R.; Shu, L. EdgeCare: Leveraging edge computing for collaborative data management in mobile healthcare systems. IEEE Access 2019, 7, 22011–22025. [Google Scholar] [CrossRef]
- Babirye, S.; Serugunda, J.; Okello, D.; Mwanje, S. Resource-Aware Workload Orchestration for Edge Computing. In Proceedings of the 2020 28th Telecommunications Forum (TELFOR), Belgrade, Serbia, 24–25 November 2020; pp. 1–4. [Google Scholar]
- Okwuide, J.; Haavisto, J.; Harjula, E.; Ahmad, I.; Ylianttila, M. SDN Enhanced Resource Orchestration for Industrial IoT in Containerized Edge Applications. IEEE Access 2020, 8, 2169–3536. [Google Scholar]
- Guim, F.; Metsch, T.; Moustafa, H.; Verrall, T.; Carrera, D.; Cadendelli, N.; Chen, J.; Doria, D.; Ghadie, C. Autonomous Lifecyle Management for Resource-efficient Workload Orchestration for Green Edge Computing. IEEE Trans. Green Commun. Netw. 2021, 6, 571–582. [Google Scholar] [CrossRef]
- Sonmez, C.; Ozgovde, A.; Ersoy, C. Fuzzy workload orchestration for edge computing. IEEE Trans. Netw. Serv. Manag. 2019, 16, 769–782. [Google Scholar] [CrossRef]
- Ndiaye, M.; Abu-Mahfouz, A.M.; Hancke, G.P.; Silva, B. Exploring control-message quenching in SDN-based management of 6LowPANs. In Proceedings of the 2019 IEEE 17th International Conference on Industrial Informatics (INDIN), Helsinki-Espoo, Finland, 22–25 July 2019; Volume 1, pp. 890–983. [Google Scholar]
- Wu, Y. Cloud-edge orchestration for the Internet of Things: Architecture and AI-powered data processing. IEEE Internet Things J. 2020, 8, 12792–12805. [Google Scholar] [CrossRef]
- Zhou, Z.; Wu, Q.; Chen, X. Online orchestration of cross-edge service function chaining for cost-efficient edge computing. IEEE J. Sel. Areas Commun. 2019, 37, 1866–1880. [Google Scholar] [CrossRef]
- Chen, S.; Wen, H.; Wu, J.; Lei, W.; Hou, W.; Liu, W.; Xu, A.; Jiang, Y. Internet of things based smart grids supported by intelligent edge computing. IEEE Access 2019, 7, 74089–74102. [Google Scholar] [CrossRef]
- Kumari, A.; Tanwar, S.; Tyagi, S.; Kumar, N.; Obaidat, M.S.; Rodrigues, J.J. Fog computing for smart grid systems in the 5G environment: Challenges and solutions. IEEE Wirel. Commun. 2019, 26, 47–53. [Google Scholar] [CrossRef]
- Ning, Z.; Dong, P.; Wang, X.; Hu, X.; Guo, L.; Hu, B.; Guo, Y.; Qiu, T.; Kwok, R.Y. Mobile edge computing enabled 5G health monitoring for Internet of medical things: A decentralized game theoretic approach. IEEE J. Sel. Areas Commun. 2020, 39, 463–478. [Google Scholar] [CrossRef]
- Gohar, A.; Nencioni, G. The role of 5G technologies in a smart city: The case for intelligent transportation system. Sustainability 2021, 13, 5188. [Google Scholar] [CrossRef]
- Hassan, N.; Yau, K.L.A.; Wu, C. Edge computing in 5G: A review. IEEE Access 2019, 7, 127276–127289. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge computing: Vision and challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Krichmar, J.L.; Severa, W.; Khan, M.S.; Olds, J.L. Making BREAD: Biomimetic strategies for artificial intelligence now and in the future. Front. Neurosci. 2019, 13, 666. [Google Scholar] [CrossRef] [Green Version]
- Olowononi, F.O.; Rawat, D.B.; Liu, C. Resilient machine learning for networked cyber physical systems: A survey for machine learning security to securing machine learning for cps. IEEE Commun. Surv. Tutor. 2020, 23, 524–552. [Google Scholar] [CrossRef]
- Ji, H.; Alfarraj, O.; Tolba, A. Artificial intelligence-empowered edge of vehicles: Architecture, enabling technologies, and applications. IEEE Access 2020, 8, 61020–61034. [Google Scholar] [CrossRef]
- Sodhro, A.H.; Pirbhulal, S.; De Albuquerque, V.H.C. Artificial intelligence-driven mechanism for edge computing-based industrial applications. IEEE Trans. Ind. Inform. 2019, 15, 4235–4243. [Google Scholar] [CrossRef]
- Shirazi, S.N.; Gouglidis, A.; Farshad, A.; Hutchison, D. The extended cloud: Review and analysis of mobile edge computing and fog from a security and resilience perspective. IEEE J. Sel. Areas Commun. 2017, 35, 2586–2595. [Google Scholar] [CrossRef] [Green Version]
- He, Y.; Wang, Y.; Qiu, C.; Lin, Q.; Li, J.; Ming, Z. Blockchain-based edge computing resource allocation in IoT: A deep reinforcement learning approach. IEEE Internet Things J. 2020, 8, 2226–2237. [Google Scholar] [CrossRef]
- Gunaratne, N.G.T.; Abdollahian, M.; Huda, S.; Ali, M.; Frontino, G. An edge tier task offloading to identify sources of variance shifts in smart grid using a hybrid of wrapper and filter approaches. IEEE Trans. Green Commun. Netw. 2021, 6, 329–340. [Google Scholar] [CrossRef]
- Zhu, Z.; Tian, Y.; Li, F.; Yang, H.; Ma, Z.; Rong, G. Research on edge intelligence-based security analysis method for power operation system. In Proceedings of the 2020 7th IEEE International Conference on Cyber Security and Cloud Computing (CSCloud)/2020 6th IEEE International Conference on Edge Computing and Scalable Cloud (EdgeCom), New York, NY, USA, 1–3 August 2020; pp. 258–263. [Google Scholar]
- Huh, J.H.; Seo, Y.S. Understanding edge computing: Engineering evolution with artificial intelligence. IEEE Access 2019, 7, 164229–164245. [Google Scholar] [CrossRef]
- Chung, H.M.; Maharjan, S.; Zhang, Y.; Eliassen, F.; Yuan, T. Edge Intelligence Empowered UAV s for Automated Wind Farm Monitoring in Smart Grids. In Proceedings of the GLOBECOM 2020–2020 IEEE Global Communications Conference, Taipei, Taiwan, 7–11 December 2020; pp. 1–6. [Google Scholar]
- Huang, Z.; Dong, F.; Shen, D.; Zhang, J.; Wang, H.; Cai, G.; He, Q. Enabling Low Latency Edge Intelligence based on Multi-exit DNNs in the Wild. In Proceedings of the 2021 IEEE 41st International Conference on Distributed Computing Systems (ICDCS), Washington DC, USA, 7–10 July 2021; pp. 729–739. [Google Scholar]
- Van Huynh, D.; Khosravirad, S.R.; Masaracchia, A.; Dobre, O.A.; Duong, T.Q. Edge Intelligence-based Ultra-Reliable and Low-Latency Communications for Digital Twin-enabled Metaverse. IEEE Wirel. Commun. Lett. 2022, 11, 1733–1737. [Google Scholar] [CrossRef]
- Hu, R.Q. Mobility-aware edge caching and computing in vehicle networks: A deep reinforcement learning. IEEE Trans. Veh. Technol. 2018, 67, 10190–10203. [Google Scholar]
- Zhang, H.; Wang, R.; Liu, J. Mobility Management for Ultra-Dense Edge Computing: A Reinforcement Learning Approach. In Proceedings of the 2019 IEEE 90th Vehicular Technology Conference (VTC2019-Fall), Honolulu, HI, USA, 22–25 September 2019; pp. 1–5. [Google Scholar]
- Dai, Y.; Zhang, K.; Maharjan, S.; Zhang, Y. Edge intelligence for energy-efficient computation offloading and resource allocation in 5G beyond. IEEE Trans. Veh. Technol. 2020, 69, 12175–12186. [Google Scholar] [CrossRef]
- Baumeister, T. Literature Review on Smart Grid Cyber Security; Collaborative Software Development Laboratory at the University of Hawaii: Honolulu, HI, USA, 2010; Volume 650. [Google Scholar]
- Kuzlu, M.; Pipattanasompom, M.; Rahman, S. A comprehensive review of smart grid related standards and protocols. In Proceedings of the 2017 5th International Istanbul Smart Grid and Cities Congress and Fair (ICSG), Istanbul, Turkey, 19–21 April 2017; pp. 12–16. [Google Scholar] [CrossRef]
- Liu, Y.; Yang, C.; Jiang, L.; Xie, S.; Zhang, Y. Intelligent edge computing for IoT-based energy management in smart cities. IEEE Netw. 2019, 33, 111–117. [Google Scholar] [CrossRef]
- Fang, X.; Misra, S.; Xue, G.; Yang, D. Smart grid: The new and improved power grid: A survey. IEEE Commun. Surv. Tutor. 2011, 14, 944–980. [Google Scholar] [CrossRef]
- Electricity, Gas and Water Supply Industry. 2016. Available online: https://http://www.statssa.gov.za/publications/Report-41-01-02/Report-41-01-022016.pdf (accessed on 5 February 2022).
- Ibrahim, I.D.; Hamam, Y.; Alayli, Y.; Jamiru, T.; Sadiku, E.R.; Kupolati, W.K.; Ndambuki, J.M.; Eze, A.A. A review on Africa energy supply through renewable energy production: Nigeria, Cameroon, Ghana and South Africa as a case study. Energy Strategy Rev. 2021, 38, 100740. [Google Scholar] [CrossRef]
- Kulkarni, S.; Gu, Q.; Myers, E.; Polepeddi, L.; Lipták, S.; Beyah, R.; Divan, D. Enabling a decentralized smart grid using autonomous edge control devices. IEEE Internet Things J. 2019, 6, 7406–7419. [Google Scholar] [CrossRef]
- Hussain, S.S.; Tak, A.; Ustun, T.S.; Ali, I. Communication modeling of solar home system and smart meter in smart grids. IEEE Access 2018, 6, 16985–16996. [Google Scholar] [CrossRef]
- Siddiqui, I.F.; Lee, S.U.J.; Abbas, A.; Bashir, A.K. Optimizing lifespan and energy consumption by smart meters in green-cloud-based smart grids. IEEE Access 2017, 5, 20934–20945. [Google Scholar] [CrossRef]
- Albayati, A.; Abdullah, N.F.; Abu-Samah, A.; Mutlag, A.H.; Nordin, R. A serverless advanced metering infrastructure based on fog-edge computing for a smart grid: A comparison study for energy sector in Iraq. Energies 2020, 13, 5460. [Google Scholar] [CrossRef]
- Yoldaş, Y.; Önen, A.; Muyeen, S.; Vasilakos, A.V.; Alan, I. Enhancing smart grid with microgrids: Challenges and opportunities. Renew. Sustain. Energy Rev. 2017, 72, 205–214. [Google Scholar] [CrossRef]
- Liu, C.H.; Gu, J.C. Modeling and integrating PV stations into IEC 61850 XMPP intelligent edge computing gateway. Energies 2019, 12, 1442. [Google Scholar] [CrossRef] [Green Version]
- Farhangi, H. The path of the smart grid. IEEE Power Energy Mag. 2009, 8, 18–28. [Google Scholar] [CrossRef]
- Senarathna, T.; Hemapala, K.U. Review of adaptive protection methods for microgrids. AIMS Energy 2019, 7, 557–578. [Google Scholar] [CrossRef]
- Usama, M.; Mokhlis, H.; Moghavvemi, M.; Mansor, N.N.; Alotaibi, M.A.; Muhammad, M.A.; Bajwa, A.A. A comprehensive review on protection strategies to mitigate the impact of renewable energy sources on interconnected distribution networks. IEEE Access 2021, 9, 35740–35765. [Google Scholar] [CrossRef]
- Mahat, P.; Chen, Z.; Bak-Jensen, B. Review on islanding operation of distribution system with distributed generation. In Proceedings of the 2011 IEEE Power and Energy Society General Meeting, Detroit, MI, USA, 24–28 July 2011; pp. 1–8. [Google Scholar]
- Khamis, A.; Shareef, H.; Bizkevelci, E.; Khatib, T. A review of islanding detection techniques for renewable distributed generation systems. Renew. Sustain. Energy Rev. 2013, 28, 483–493. [Google Scholar] [CrossRef]
- Norshahrani, M.; Mokhlis, H.; Abu Bakar, A.H.; Jamian, J.J.; Sukumar, S. Progress on protection strategies to mitigate the impact of renewable distributed generation on distribution systems. Energies 2017, 10, 1864. [Google Scholar] [CrossRef] [Green Version]
- AsghariGovar, S.; Pourghasem, P.; Seyedi, H. High impedance fault protection scheme for smart grids based on WPT and ELM considering evolving and cross-country faults. Int. J. Electr. Power Energy Syst. 2019, 107, 412–421. [Google Scholar] [CrossRef]
- Menezes, T.S.; Fernandes, R.A.; Coury, D.V. Intelligent islanding detection with grid topology adaptation and minimum non-detection zone. Electr. Power Syst. Res. 2020, 187, 106470. [Google Scholar] [CrossRef]
- Bakkar, M.; Bogarra, S.; Córcoles, F.; Aboelhassan, A.; Wang, S.; Iglesias, J. Artificial Intelligence-Based Protection for Smart Grids. Energies 2022, 15, 4933. [Google Scholar] [CrossRef]
- Khamis, A.; Xu, Y.; Dong, Z.Y.; Zhang, R. Faster detection of microgrid islanding events using an adaptive ensemble classifier. IEEE Trans. Smart Grid 2016, 9, 1889–1899. [Google Scholar] [CrossRef]
- Mwasilu, F.; Justo, J.J.; Kim, E.K.; Do, T.D.; Jung, J.W. Electric vehicles and smart grid interaction: A review on vehicle to grid and renewable energy sources integration. Renew. Sustain. Energy Rev. 2014, 34, 501–516. [Google Scholar] [CrossRef]
- Jiang, A.; Yuan, H.; Li, D.; Tian, J. Key technologies of ubiquitous power Internet of Things-aided smart grid. J. Renew. Sustain. Energy 2019, 11, 062702. [Google Scholar] [CrossRef] [Green Version]
- Reka, S.S.; Dragicevic, T. Future effectual role of energy delivery: A comprehensive review of Internet of Things and smart grid. Renew. Sustain. Energy Rev. 2018, 91, 90–108. [Google Scholar] [CrossRef]
- Hui, H.; Ding, Y.; Shi, Q.; Li, F.; Song, Y.; Yan, J. 5G network-based Internet of Things for demand response in smart grid: A survey on application potential. Appl. Energy 2020, 257, 113972. [Google Scholar] [CrossRef]
- Sakhnini, J.; Karimipour, H.; Dehghantanha, A.; Parizi, R.M.; Srivastava, G. Security aspects of Internet of Things aided smart grids: A bibliometric survey. Internet Things 2021, 14, 100111. [Google Scholar] [CrossRef]
- Pan, J.; Jain, R.; Paul, S.; Vu, T.; Saifullah, A.; Sha, M. An internet of things framework for smart energy in buildings: Designs, prototype, and experiments. IEEE Internet Things J. 2015, 2, 527–537. [Google Scholar] [CrossRef] [Green Version]
- Akhtaruzzaman, M.; Hasan, M.K.; Kabir, S.R.; Abdullah, S.N.H.S.; Sadeq, M.J.; Hossain, E. HSIC bottleneck based distributed deep learning model for load forecasting in smart grid with a comprehensive survey. IEEE Access 2020, 8, 222977–223008. [Google Scholar] [CrossRef]
- Chadoulos, S.; Koutsopoulos, I.; Polyzos, G.C. Mobile apps meet the smart energy grid: A survey on consumer engagement and machine learning applications. IEEE Access 2020, 8, 219632–219655. [Google Scholar] [CrossRef]
- Su, Z.; Wang, Y.; Luan, T.H.; Zhang, N.; Li, F.; Chen, T.; Cao, H. Secure and Efficient Federated Learning for Smart Grid With Edge-Cloud Collaboration. IEEE Trans. Ind. Inform. 2021, 18, 1333–1344. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Xu, L.; Zhang, Y. Permissioned blockchain and edge computing empowered privacy-preserving smart grid networks. IEEE Internet Things J. 2019, 6, 7992–8004. [Google Scholar] [CrossRef]
- Huang, Y.; Lu, Y.; Wang, F.; Fan, X.; Liu, J.; Leung, V.C. An edge computing framework for real-time monitoring in smart grid. In Proceedings of the 2018 IEEE International Conference on Industrial Internet (ICII), Seattle, WA, USA, 21–23 October 2018; pp. 99–108. [Google Scholar]
- Lu, W.; Ren, Z.; Xu, J.; Chen, S. Edge blockchain assisted lightweight privacy-preserving data aggregation for smart grid. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1246–1259. [Google Scholar] [CrossRef]
- Zhou, H.; Zhang, Z.; Li, D.; Su, Z. Joint Optimization of Computing Offloading and Service Caching in Edge Computing-based Smart Grid. IEEE Trans. Cloud Comput. 2022, 2022, 1–11. [Google Scholar] [CrossRef]
- Aranda, J.A.S.; dos Santos Costa, R.; de Vargas, V.W.; da Silva Pereira, P.R.; Barbosa, J.L.V.; Vianna, M.P. Context-aware Edge Computing and Internet of Things in Smart Grids: A systematic mapping study. Comput. Electr. Eng. 2022, 99, 107826. [Google Scholar] [CrossRef]
- Wang, Z.; Jiang, D.; Wang, F.; Lv, Z.; Nowak, R. A polymorphic heterogeneous security architecture for edge-enabled smart grids. Sustain. Cities Soc. 2021, 67, 102661. [Google Scholar] [CrossRef]
- Fan, J.; du Toit, W.; Backscheider, P. Distribution substation automation in smart grid. Prot. Control. J. 2009, 9, 65–68. [Google Scholar]
- Gungor, V.C.; Sahin, D.; Kocak, T.; Ergut, S.; Buccella, C.; Cecati, C.; Hancke, G.P. A survey on smart grid potential applications and communication requirements. IEEE Trans. Ind. Inform. 2012, 9, 28–42. [Google Scholar] [CrossRef] [Green Version]
- Peng, N.; Liu, X.; Liang, R.; Tang, Z.; Ren, X.; Hu, Y.; Li, G. Edge Computing Based Fault Sensing of the Distribution Cables Based on Time-domain Analysis of Grounding Line Current Signals. IEEE Trans. Power Deliv. 2022, 2022, 1–13. [Google Scholar] [CrossRef]
- Du, Y.; Zhang, Z.; Li, Y.; Li, H.; He, G.; Zhang, Z.; Zhao, Y. A new type of substation real-time detection system based on edge computing and RAFT consensus algorithm. In Proceedings of the 2021 6th Asia Conference on Power and Electrical Engineering (ACPEE), Chongqing, China, 8–11 April 2021; pp. 451–455. [Google Scholar]
- Huo, W.; Liu, F.; Wang, L.; Jin, Y.; Wang, L. Research on distributed power distribution fault detection based on edge computing. IEEE Access 2019, 8, 24643–24652. [Google Scholar] [CrossRef]
- Cen, B.; Hu, C.; Cai, Z.; Wu, Z.; Zhang, Y.; Liu, J.; Su, Z. A configuration method of computing resources for microservice-based edge computing apparatus in smart distribution transformer area. Int. J. Electr. Powe Energy Syst. 2022, 138, 107935. [Google Scholar] [CrossRef]
- Zhang, S.; Liu, Y.; Cai, Y.; Dong, S.; Xu, C.; Fang, R. A Multilevel Edge Computing Architecture and Edge Generation Method of Distribution Networks. In Proceedings of the 2020 IEEE Power & Energy Society General Meeting (PESGM), Virtual Event, 3–6 August 2020; pp. 1–5. [Google Scholar]
- Shakeri, M.; Shayestegan, M.; Abunima, H.; Reza, S.S.; Akhtaruzzaman, M.; Alamoud, A.; Sopian, K.; Amin, N. An intelligent system architecture in home energy management systems (HEMS) for efficient demand response in smart grid. Energy Build. 2017, 138, 154–164. [Google Scholar] [CrossRef]
- Bouhafs, F.; Mackay, M.; Merabti, M. Links to the future: Communication requirements and challenges in the smart grid. IEEE Power Energy Mag. 2011, 10, 24–32. [Google Scholar] [CrossRef]
- Saez-de Ibarra, A.; Martinez-Laserna, E.; Koch-Ciobotaru, C.; Rodriguez, P.; Stroe, D.I.; Swierczynski, M. Second life battery energy storage system for residential demand response service. In Proceedings of the 2015 IEEE International Conference on Industrial Technology (ICIT), Seville, Spain, 17–19 March 2015; pp. 2941–2948. [Google Scholar]
- Elkind, E. Reuse and Repower: How to Save Money and Clean the Grid with Second-Life Electric Vehicle Batteries; UC Berkeley, Berkeley Law; University of California: Berkeley, CA, USA, 2014; pp. 1–31. [Google Scholar]
- Casals, L.C.; Barbero, M.; Corchero, C. Reused second life batteries for aggregated demand response services. J. Clean. Prod. 2019, 212, 99–108. [Google Scholar] [CrossRef]
- Alcaraz, C.; Lopez, J. WASAM: A dynamic wide-area situational awareness model for critical domains in Smart Grids. Future Gener. Comput. Syst. 2014, 30, 146–154. [Google Scholar] [CrossRef]
- Law, Y.W.; Palaniswami, M.; Kounga, G.; Lo, A. WAKE: Key management scheme for wide-area measurement systems in smart grid. IEEE Commun. Mag. 2013, 51, 34–41. [Google Scholar] [CrossRef]
- Basu, C.; Agrawal, A.; Hazra, J.; Kumar, A.; Seetharam, D.P.; Béland, J.; Guillon, S.; Kamwa, I.; Lafond, C. Understanding events for wide-area situational awareness. In Proceedings of the ISGT 2014, Washington, DC, USA, 19–22 February 2014; pp. 1–5. [Google Scholar]
- Bahrami, S.; Sheikhi, A. From demand response in smart grid toward integrated demand response in smart energy hub. IEEE Trans. Smart Grid 2015, 7, 650–658. [Google Scholar] [CrossRef]
- Rastegar, M.; Fotuhi-Firuzabad, M. Outage management in residential demand response programs. IEEE Trans. Smart Grid 2014, 6, 1453–1462. [Google Scholar] [CrossRef]
- He, Y.; Jenkins, N.; Wu, J. Smart metering for outage management of electric power distribution networks. Energy Procedia 2016, 103, 159–164. [Google Scholar] [CrossRef]
- Jiang, Y.; Liu, C.C.; Diedesch, M.; Lee, E.; Srivastava, A.K. Outage management of distribution systems incorporating information from smart meters. IEEE Trans. Power Syst. 2015, 31, 4144–4154. [Google Scholar] [CrossRef]
- Raju, L.; Morais, A.A.; Rathnakumar, R.; Ponnivalavan, S.; Thavam, L. Micro-grid grid outage management using multi-agent systems. In Proceedings of the 2017 Second International Conference on Recent Trends and Challenges in Computational Models (ICRTCCM), Tindivanam, India, 3–4 February 2017; pp. 363–368. [Google Scholar]
- Kong, P.Y.; Karagiannidis, G.K. Charging schemes for plug-in hybrid electric vehicles in smart grid: A survey. IEEE Access 2016, 4, 6846–6875. [Google Scholar] [CrossRef]
- Debnath, U.K.; Ahmad, I.; Habibi, D. Gridable vehicles and second life batteries for generation side asset management in the Smart Grid. Int. J. Electr. Power Energy Syst. 2016, 82, 114–123. [Google Scholar] [CrossRef]
- Gomez-Quiles, C.; Asencio-Cortes, G.; Gastalver-Rubio, A.; Martinez-Alvarez, F.; Troncoso, A.; Manresa, J.; Riquelme, J.C.; Riquelme-Santos, J.M. A novel ensemble method for electric vehicle power consumption forecasting: Application to the Spanish system. IEEE Access 2019, 7, 120840–120856. [Google Scholar] [CrossRef]
- Lopes, J.A.P.; Soares, F.J.; Almeida, P.M.R. Integration of electric vehicles in the electric power system. Proc. IEEE 2010, 99, 168–183. [Google Scholar] [CrossRef] [Green Version]
- Martínez-Lao, J.; Montoya, F.G.; Montoya, M.G.; Manzano-Agugliaro, F. Electric vehicles in Spain: An overview of charging systems. Renew. Sustain. Energy Rev. 2017, 77, 970–983. [Google Scholar] [CrossRef]
- Chen, Y.; Oudalov, A.; Wang, J. Integration of electric vehicle charging system into distribution network. In Proceedings of the 8th International Conference on Power Electronics-ECCE Asia, Jeju, Korea, 30 May–3 June 2011; pp. 593–598. [Google Scholar]
- Eltoumi, F.M.; Becherif, M.; Djerdir, A.; Ramadan, H.S. The key issues of electric vehicle charging via hybrid power sources: Techno-economic viability, analysis, and recommendations. Renew. Sustain. Energy Rev. 2021, 138, 110534. [Google Scholar] [CrossRef]
- Ashfaq, M.; Butt, O.; Selvaraj, J.; Rahim, N. Assessment of electric vehicle charging infrastructure and its impact on the electric grid: A review. Int. J. Green Energy 2021, 18, 657–686. [Google Scholar] [CrossRef]
- Lee, Z.J.; Chang, D.; Jin, C.; Lee, G.S.; Lee, R.; Lee, T.; Low, S.H. Large-scale adaptive electric vehicle charging. In Proceedings of the 2018 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Aalborg, Denmark, 29–31 October 2018; pp. 1–7. [Google Scholar]
- Hutchinson, S.; Baran, M.; Lukic, S. Power supply for an electric vehicle charging system for a large parking deck. In Proceedings of the 2009 IEEE Industry Applications Society Annual Meeting, Houston, TX, USA, 4–8 October 2009; pp. 1–4. [Google Scholar]
- Jung, C.M.; Ray, P.; Salkuti, S.R. Asset management and maintenance: A smart grid perspective. Int. J. Electr. Comput. Eng. (2088-8708) 2019, 9, 3391–3398. [Google Scholar] [CrossRef]
- Ahmed, S.; Lee, Y.D.; Hyun, S.H.; Koo, I. A cognitive radio-based energy-efficient system for power transmission line monitoring in smart grids. J. Sens. 2017, 2017, 3862375. [Google Scholar] [CrossRef] [Green Version]
- Hanai, M.; Kojima, H.; Hayakawa, N.; Shinoda, K.; Okubo, H. Integration of asset management and smart grid with intelligent grid management system. IEEE Trans. Dielectr. Electr. Insul. 2013, 20, 2195–2202. [Google Scholar] [CrossRef]
- Teoh, Y.K.; Gill, S.S.; Parlikad, A.K. IoT and fog computing based predictive maintenance model for effective asset management in industry 4.0 using machine learning. IEEE Internet Things J. 2021, 2021, 1–8. [Google Scholar] [CrossRef]
- Ma, H.; Saha, T.K.; Ekanayake, C.; Martin, D. Smart transformer for smart grid—intelligent framework and techniques for power transformer asset management. IEEE Trans. Smart Grid 2015, 6, 1026–1034. [Google Scholar] [CrossRef] [Green Version]
- Cheng, M.; Zeng, Y.; Niu, R.; Chen, Y. Study on the model of advanced asset management in smart grid. In Proceedings of the 2011 4th International Conference on Electric Utility Deregulation and Restructuring and Power Technologies (DRPT), Weihai, China, 6–9 July 2011; pp. 781–785. [Google Scholar]
- Trajano, A.F.; de Sousa, A.A.M.; Rodrigues, E.B.; de Souza, J.N.; de Castro Callado, A.; Coutinho, E.F. Leveraging mobile edge computing on smart grids using LTE cellular networks. In Proceedings of the 2019 IEEE Symposium on Computers and Communications (ISCC), Barcelona, Spain, 29 June–3 July 2019; pp. 1–7. [Google Scholar]
- Zhang, X.; Wang, Y.; Lu, S.; Liu, L.; Shi, W. OpenEI: An open framework for edge intelligence. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–10 July 2019; pp. 1840–1851. [Google Scholar]
- Moghaddam, M.; Cadavid, M.N.; Kenley, C.R.; Deshmukh, A.V. Reference architectures for smart manufacturing: A critical review. J. Manuf. Syst. 2018, 49, 215–225. [Google Scholar] [CrossRef]
- Peng, N.; Liang, R.; Wang, G.; Sun, P.; Chen, C.; Hou, T. Edge Computing-Based Fault Location in Distribution Networks by Using Asynchronous Transient Amplitudes at Limited Nodes. IEEE Trans. Smart Grid 2020, 12, 574–588. [Google Scholar] [CrossRef]
- Sufyan, F.; Banerjee, A. Computation offloading for distributed mobile edge computing network: A multiobjective approach. IEEE Access 2020, 8, 149915–149930. [Google Scholar] [CrossRef]
- Xi, L.; Wang, Y.; Wang, Y.; Wang, Z.; Wang, X.; Chen, Y. Deep Reinforcement Learning-Based Service-Oriented Resource Allocation in Smart Grids. IEEE Access 2021, 9, 77637–77648. [Google Scholar] [CrossRef]
- Hou, W.; Jiang, Y.; Lei, W.; Xu, A.; Wen, H.; Chen, S. A P2P network based edge computing smart grid model for efficient resources coordination. Peer-Peer Netw. Appl. 2020, 13, 1026–1037. [Google Scholar] [CrossRef]
- Patil, P.; Hakiri, A.; Gokhale, A. Cyber foraging and offloading framework for internet of things. In Proceedings of the 2016 IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), Atlanta, GA, USA, 10–14 June 2016; Volume 1, pp. 359–368. [Google Scholar]
- Li, B.; Pei, Y.; Wu, H.; Shen, B. Heuristics to allocate high-performance cloudlets for computation offloading in mobile ad hoc clouds. J. Supercomput. 2015, 71, 3009–3036. [Google Scholar] [CrossRef]
- Wolski, R.; Gurun, S.; Krintz, C.; Nurmi, D. Using bandwidth data to make computation offloading decisions. In Proceedings of the 2008 IEEE International Symposium on Parallel and Distributed Processing, Miami, FL, USA, 14–18 April 2008; pp. 1–8. [Google Scholar]
- Akherfi, K.; Gerndt, M.; Harroud, H. Mobile cloud computing for computation offloading: Issues and challenges. Appl. Comput. Inform. 2018, 14, 1–16. [Google Scholar] [CrossRef]
- Dinh, T.Q.; La, Q.D.; Quek, T.Q.; Shin, H. Learning for computation offloading in mobile edge computing. IEEE Trans. Commun. 2018, 66, 6353–6367. [Google Scholar] [CrossRef]
- Jiang, C.; Cheng, X.; Gao, H.; Zhou, X.; Wan, J. Toward computation offloading in edge computing: A survey. IEEE Access 2019, 7, 131543–131558. [Google Scholar] [CrossRef]
- Lin, L.; Liao, X.; Jin, H.; Li, P. Computation offloading toward edge computing. Proc. IEEE 2019, 107, 1584–1607. [Google Scholar] [CrossRef]
- Noble, B.D.; Satyanarayanan, M.; Narayanan, D.; Tilton, J.E.; Flinn, J.; Walker, K.R. Agile application-aware adaptation for mobility. ACM SIGOPS Oper. Syst. Rev. 1997, 31, 276–287. [Google Scholar] [CrossRef]
- Guo, H.; Liu, J.; Zhang, J.; Sun, W.; Kato, N. Mobile-edge computation offloading for ultradense IoT networks. IEEE Internet Things J. 2018, 5, 4977–4988. [Google Scholar] [CrossRef]
- Yu, S.; Langar, R.; Fu, X.; Wang, L.; Han, Z. Computation offloading with data caching enhancement for mobile edge computing. IEEE Trans. Veh. Technol. 2018, 67, 11098–11112. [Google Scholar] [CrossRef]
- Dong, L.; Satpute, M.N.; Shan, J.; Liu, B.; Yu, Y.; Yan, T. Computation offloading for mobile-edge computing with multi-user. In Proceedings of the 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS), Dallas, TX, USA, 7–10 July 2019; pp. 841–850. [Google Scholar]
- Khayyat, M.; Elgendy, I.A.; Muthanna, A.; Alshahrani, A.S.; Alharbi, S.; Koucheryavy, A. Advanced deep learning-based computational offloading for multilevel vehicular edge-cloud computing networks. IEEE Access 2020, 8, 137052–137062. [Google Scholar] [CrossRef]
- Li, Y.; Wang, X.; Gan, X.; Jin, H.; Fu, L.; Wang, X. Learning-aided computation offloading for trusted collaborative mobile edge computing. IEEE Trans. Mob. Comput. 2019, 19, 2833–2849. [Google Scholar] [CrossRef]
- Verbelen, T.; Stevens, T.; De Turck, F.; Dhoedt, B. Graph partitioning algorithms for optimizing software deployment in mobile cloud computing. Future Gener. Comput. Syst. 2013, 29, 451–459. [Google Scholar] [CrossRef] [Green Version]
- Zhao, T.; Zhou, S.; Guo, X.; Niu, Z. Tasks scheduling and resource allocation in heterogeneous cloud for delay-bounded mobile edge computing. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–7. [Google Scholar]
- Sardellitti, S.; Scutari, G.; Barbarossa, S. Joint optimization of radio and computational resources for multicell mobile-edge computing. IEEE Trans. Signal Inf. Process. Netw. 2015, 1, 89–103. [Google Scholar] [CrossRef] [Green Version]
- Chen, X.; Shi, Q.; Yang, L.; Xu, J. ThriftyEdge: Resource-efficient edge computing for intelligent IoT applications. IEEE Netw. 2018, 32, 61–65. [Google Scholar] [CrossRef]
- Abebe, E.; Ryan, C. Adaptive application offloading using distributed abstract class graphs in mobile environments. J. Syst. Softw. 2012, 85, 2755–2769. [Google Scholar] [CrossRef]
- Kosta, S.; Aucinas, A.; Hui, P.; Mortier, R.; Zhang, X. Thinkair: Dynamic resource allocation and parallel execution in the cloud for mobile code offloading. In Proceedings of the 2012 Proceedings IEEE Infocom, Orlando, FL, USA, 25–30 March 2012; pp. 945–953. [Google Scholar]
- Chen, X. Decentralized computation offloading game for mobile cloud computing. IEEE Trans. Parallel Distrib. Syst. 2014, 26, 974–983. [Google Scholar] [CrossRef] [Green Version]
- Chen, L.; Zhou, S.; Xu, J. Computation peer offloading for energy-constrained mobile edge computing in small-cell networks. IEEE/ACM Trans. Netw. 2018, 26, 1619–1632. [Google Scholar] [CrossRef] [Green Version]
- Li, S.; Tao, Y.; Qin, X.; Liu, L.; Zhang, Z.; Zhang, P. Energy-aware mobile edge computation offloading for IoT over heterogenous networks. IEEE Access 2019, 7, 13092–13105. [Google Scholar] [CrossRef]
- Elgendy, I.A.; Zhang, W.Z.; Zeng, Y.; He, H.; Tian, Y.C.; Yang, Y. Efficient and secure multi-user multi-task computation offloading for mobile-edge computing in mobile IoT networks. IEEE Trans. Netw. Serv. Manag. 2020, 17, 2410–2422. [Google Scholar] [CrossRef]
- Huang, P.Q.; Wang, Y.; Wang, K.; Liu, Z.Z. A bilevel optimization approach for joint offloading decision and resource allocation in cooperative mobile edge computing. IEEE Trans. Cybern. 2019, 50, 4228–4241. [Google Scholar] [CrossRef] [Green Version]
- Chen, X.; Jiao, L.; Li, W.; Fu, X. Efficient multi-user computation offloading for mobile-edge cloud computing. IEEE/ACM Trans. Netw. 2015, 24, 2795–2808. [Google Scholar] [CrossRef] [Green Version]
- Humayed, A.; Lin, J.; Li, F.; Luo, B. Cyber-physical systems security: A survey. IEEE Internet Things J. 2017, 4, 1802–1831. [Google Scholar] [CrossRef]
- Singh, J.; Bello, Y.; Hussein, A.R.; Erbad, A.; Mohamed, A. Hierarchical security paradigm for iot multiaccess edge computing. IEEE Internet Things J. 2020, 8, 5794–5805. [Google Scholar] [CrossRef]
- Gligor, V.D. A note on denial-of-service in operating systems. IEEE Trans. Softw. Eng. 1984, SE-10, 320–324. [Google Scholar] [CrossRef]
- Yuan, X.; Li, C.; Li, X. DeepDefense: Identifying DDoS attack via deep learning. In Proceedings of the 2017 IEEE International Conference on Smart Computing (SMARTCOMP), Hong Kong, China, 29–31 May 2017; pp. 1–8. [Google Scholar]
- Nooribakhsh, M.; Mollamotalebi, M. A review on statistical approaches for anomaly detection in DDoS attacks. Inf. Secur. J. Glob. Perspect. 2020, 29, 118–133. [Google Scholar] [CrossRef]
- Bhat, S.A.; Sofi, I.B.; Chi, C.Y. edge computing and its convergence with blockchain in 5G and beyond: Security, challenges, and opportunities. IEEE Access 2020, 8, 205340–205373. [Google Scholar] [CrossRef]
- Li, X.; Chen, T.; Cheng, Q.; Ma, S.; Ma, J. Smart applications in edge computing: Overview on authentication and data security. IEEE Internet Things J. 2020, 8, 4063–4080. [Google Scholar] [CrossRef]
- Li, H.; Wu, J.; Xu, H.; Li, G.; Guizani, M. Explainable Intelligence-Driven Defense Mechanism against Advanced Persistent Threats: A Joint Edge Game and AI Approach. IEEE Trans. Dependable Secur. Comput. 2021, 19, 757–775. [Google Scholar] [CrossRef]
- Nayak, G.N.; Samaddar, S.G. Different flavours of man-in-the-middle attack, consequences and feasible solutions. In Proceedings of the 2010 3rd International Conference on Computer Science and Information Technology, Chengdu, China, 9–11 July 2010; Volume 5, pp. 491–495. [Google Scholar]
- Rahim, R. Man-in-the-middle-attack prevention using interlock protocol method. ARPN J. Eng. Appl. Sci 2017, 12, 6483–6487. [Google Scholar]
- Mohapatra, H.; Rath, S.; Panda, S.; Kumar, R. Handling of man-in-the-middle attack in wsn through intrusion detection system. Int. J. 2020, 8, 1503–1510. [Google Scholar] [CrossRef]
- Ranaweera, P.; Jurcut, A.D.; Liyanage, M. Survey on multi-access edge computing security and privacy. IEEE Commun. Surv. Tutor. 2021, 23, 1078–1124. [Google Scholar] [CrossRef]
- Chen, D.; Wawrzynski, P.; Lv, Z. Cyber security in smart cities: A review of deep learning-based applications and case studies. Sustain. Cities Soc. 2021, 66, 102655. [Google Scholar] [CrossRef]
- Xiao, Y.; Jia, Y.; Liu, C.; Cheng, X.; Yu, J.; Lv, W. Edge computing security: State of the art and challenges. Proc. IEEE 2019, 107, 1608–1631. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Alhakami, H.; Baz, A.; Al-Turjman, F. Securing demand response management: A certificate-based access control in smart grid edge computing infrastructure. IEEE Access 2020, 8, 101235–101243. [Google Scholar] [CrossRef]
- Nyamtiga, B.W.; Sicato, J.C.S.; Rathore, S.; Sung, Y.; Park, J.H. Blockchain-based secure storage management with edge computing for IoT. Electronics 2019, 8, 828. [Google Scholar] [CrossRef] [Green Version]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Chen, S.; Liu, D.; Li, J. Performance comparison and current challenges of using machine learning techniques in cybersecurity. Energies 2020, 13, 2509. [Google Scholar] [CrossRef]
- Javed, A.R.; Usman, M.; Rehman, S.U.; Khan, M.U.; Haghighi, M.S. Anomaly detection in automated vehicles using multistage attention-based convolutional neural network. IEEE Trans. Intell. Transp. Syst. 2020, 22, 4291–4300. [Google Scholar] [CrossRef]
- Marir, N.; Wang, H.; Feng, G.; Li, B.; Jia, M. Distributed abnormal behavior detection approach based on deep belief network and ensemble SVM using spark. IEEE Access 2018, 6, 59657–59671. [Google Scholar] [CrossRef]
- Xin, Y.; Kong, L.; Liu, Z.; Chen, Y.; Li, Y.; Zhu, H.; Gao, M.; Hou, H.; Wang, C. Machine learning and deep learning methods for cybersecurity. IEEE Access 2018, 6, 35365–35381. [Google Scholar] [CrossRef]
- Sheatsley, R.; Durbin, M.; Lintereur, A.; Mcdaniel, P. Improving Radioactive Material Localization by Leveraging Cyber-Security Model Optimizations. IEEE Sens. J. 2021, 21, 9994–10006. [Google Scholar] [CrossRef]
- Larriva-Novo, X.; Vega-Barbas, M.; Villagrá, V.A.; Rivera, D.; Álvarez-Campana, M.; Berrocal, J. Efficient distributed preprocessing model for machine learning-based anomaly detection over large-scale cybersecurity datasets. Appl. Sci. 2020, 10, 3430. [Google Scholar] [CrossRef]
- Podder, P.; Bharati, S.; Mondal, M.; Paul, P.K.; Kose, U. Artificial neural network for cybersecurity: A comprehensive review. arXiv 2021, arXiv:2107.01185. [Google Scholar]
- Mathai, K.J. Performance comparison of intrusion detection system between deep belief network (DBN) algorithm and state preserving extreme learning machine (SPELM) algorithm. In Proceedings of the 2019 IEEE International Conference on Electrical, Computer and Communication Technologies (ICECCT), Coimbatore, India, 20–22 February 2019; pp. 1–7. [Google Scholar]
- Huda, S.; Yearwood, J.; Hassan, M.M.; Almogren, A. Securing the operations in SCADA-IoT platform based industrial control system using ensemble of deep belief networks. Appl. Soft Comput. 2018, 71, 66–77. [Google Scholar] [CrossRef]
- Nguyen, G.N.; Le Viet, N.H.; Elhoseny, M.; Shankar, K.; Gupta, B.; Abd El-Latif, A.A. Secure blockchain enabled Cyber–physical systems in healthcare using deep belief network with ResNet model. J. Parallel Distrib. Comput. 2021, 153, 150–160. [Google Scholar] [CrossRef]
- Habibi, M.R.; Baghaee, H.R.; Dragičević, T.; Blaabjerg, F. Detection of false data injection cyber-attacks in DC microgrids based on recurrent neural networks. IEEE J. Emerg. Sel. Top. Power Electron. 2020, 9, 5294–5310. [Google Scholar] [CrossRef]
- Lin, T.N.; Giles, C.L.; Horne, B.G.; Kung, S.Y. A delay damage model selection algorithm for NARX neural networks. IEEE Trans. Signal Process. 1997, 45, 2719–2730. [Google Scholar]
- Ullah, I.; Mahmoud, Q.H. Design and development of a deep learning-based model for anomaly detection in IoT networks. IEEE Access 2021, 9, 103906–103926. [Google Scholar] [CrossRef]
- Kravchik, M.; Shabtai, A. Detecting cyber attacks in industrial control systems using convolutional neural networks. In Proceedings of the 2018 Workshop on Cyber-Physical Systems Security and PrivaCy, Toronto, ON, Canada, 15–19 October 2018; pp. 72–83. [Google Scholar]
- Susilo, B.; Sari, R.F. Intrusion detection in IoT networks using deep learning algorithm. Information 2020, 11, 279. [Google Scholar] [CrossRef]
- McLaughlin, N.; Martinez del Rincon, J.; Kang, B.; Yerima, S.; Miller, P.; Sezer, S.; Safaei, Y.; Trickel, E.; Zhao, Z.; Doupé, A.; et al. Deep android malware detection. In Proceedings of the Proceedings of the Seventh ACM on Conference on Data and Application Security and Privacy, Scottsdale, AZ, USA, 22–24 March 2017; pp. 301–308. [Google Scholar]
- Li, Y.; Xu, Y.; Liu, Z.; Hou, H.; Zheng, Y.; Xin, Y.; Zhao, Y.; Cui, L. Robust detection for network intrusion of industrial IoT based on multi-CNN fusion. Measurement 2020, 154, 107450. [Google Scholar] [CrossRef]
- Gimenez-Aguilar, M.; de Fuentes, J.M.; Gonzalez-Manzano, L.; Arroyo, D. Achieving cybersecurity in blockchain-based systems: A survey. Future Gener. Comput. Syst. 2021, 124, 91–118. [Google Scholar] [CrossRef]
- Razaque, A.; Al Ajlan, A.; Melaoune, N.; Alotaibi, M.; Alotaibi, B.; Dias, I.; Oad, A.; Hariri, S.; Zhao, C. Avoidance of cybersecurity threats with the deployment of a web-based blockchain-enabled cybersecurity awareness system. Appl. Sci. 2021, 11, 7880. [Google Scholar] [CrossRef]
- Zhang, L.; Zou, Y.; Wang, W.; Jin, Z.; Su, Y.; Chen, H. Resource allocation and trust computing for blockchain-enabled edge computing system. Comput. Secur. 2021, 105, 102249. [Google Scholar] [CrossRef]
- Wang, J.; Wu, L.; Choo, K.K.R.; He, D. Blockchain-based anonymous authentication with key management for smart grid edge computing infrastructure. IEEE Trans. Ind. Inform. 2019, 16, 1984–1992. [Google Scholar] [CrossRef]
- Zhao, Y.; Wang, W.; Li, Y.; Meixner, C.C.; Tornatore, M.; Zhang, J. Edge computing and networking: A survey on infrastructures and applications. IEEE Access 2019, 7, 101213–101230. [Google Scholar] [CrossRef]
- Xue, M.; Yuan, C.; Wu, H.; Zhang, Y.; Liu, W. Machine learning security: Threats, countermeasures, and evaluations. IEEE Access 2020, 8, 74720–74742. [Google Scholar] [CrossRef]
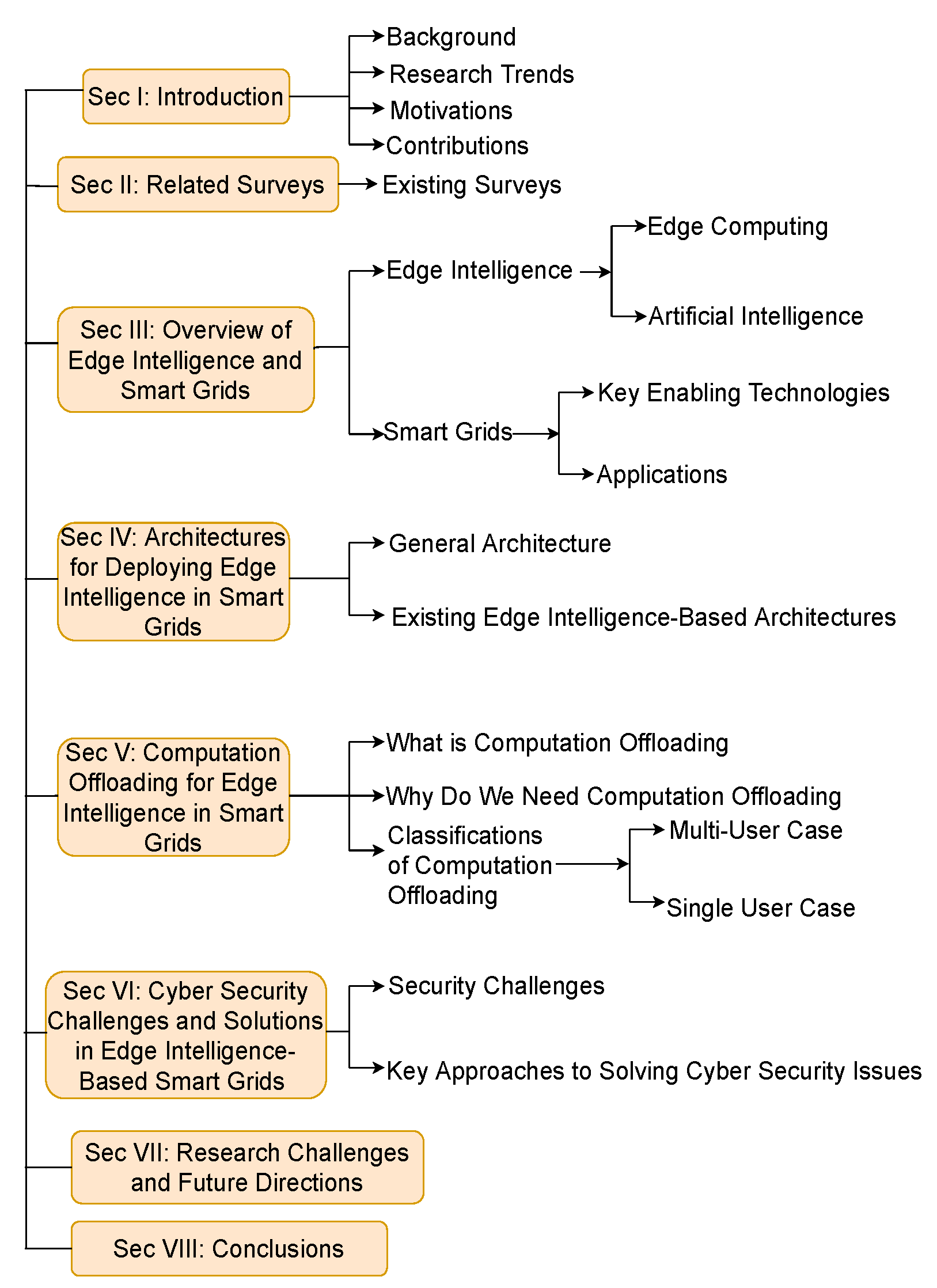





| Survey Articles | Year | Highlights |
|---|---|---|
| Rigas et al. [31] | 2014 | • Survey on AI techniques to render EVs in SGs • Identify the commonalities and key differences in the approaches • Develop classification of key technologies • Develop benchmarks for state-of-the-art |
| Meloni et al. [23] | 2018 | • Analyze case studies based on distribution networks monitoring • State-of-the-art solutions • Demonstrate the performance of Cloud-IoT-based architectural solution for SE in SG |
| Gilbert et al. [32] | 2019 | • Systematic review on the research trend of actual implementations of edge and fog computing for SG applications • Investigate the challenges hindering adoption of fog and edge computing in SG |
| Ferrag et al. [33] | 2020 | • Comprehensive survey of existing cyber security solutions for fog-based SG SCADA systems • Overview of architecture and the concept of fog-based SG SCADA • Summarize informal and formal security analysis techniques • Provides taxonomy of attacks mitigated by privacy-preserving and authentication solutions |
| Rosero et al. [34] | 2021 | • Identify elements in existing works to define cloud-based architecture • Revise and run microgrid real-time simulation platforms • Presents scalable and autonomous cloud-based architecture for forecasting, consumption, etc using ML techniques |
| Feng et al. [35] | 2021 | • Comprehensive review of interdisciplinary research on EC applications in SG • In-depth analysis of EC is conducted from SG perspective • Systematically explores application scenarios of EC in SG • Assisted synergistic effect of the integration of EC and SG |
| Slama [5] | 2021 | • Investigate EC solutions for the SG • Comprehensive review on emerging issues of EC in SG • Extensively covers techniques to improve reader awareness on prosumer SG system |
| Mehmood et al. [6] | 2021 | • Comprehensive review of SG systems based on IoT and EC • Development in the rising technologies • Framework for EC-IoT based SG is examined • Requirements to implement EC-IoT SG system are outlined |
| Li et al. [36] | 2021 | • Introduce AI-based algorithms for multi-access EC for benchmark microgrid performance optimization • Present online dual-network-based action-dependent heuristic dynamic programming method • Apply optimal control strategy to a benchmark microgrid system |
| Hudson et al. [24] | 2021 | • Provide an overview for how EC and EI can supplement AMI applications • FL-based architecture to empower distributed data processing • Demonstrate the efficacy of the architecture using NILM |
| Wu et al. [37] | 2021 | • Comprehensive discussion on the key infrastructures • Systematic overview on how IoT drives the digitization of transactive EI • Discussion on how to implement digitization and decentralization of transactive EI such as AMI • Highlights challenges and future trends from cyber space point of view |
| Massaoudi et al. [38] | 2021 | • Thorough review on the state-of-the-art advances of DL in SG systems • Bibliometric analysis • Taxonomy of the trending DL algorithms • DL enabling technologies (FL, EI and distributed computing) in SG |
| Metrics | Cloud | Fog | Edge |
|---|---|---|---|
| Deployment | Centralized | Decentralized | Decentralized |
| Distance from end users | Huge | Small | Extremely small |
| Computational Power | Pervasive | Limited | Limited |
| Efficiency | Low | High | Extremely High |
| Latency | High | Low | Ultra-low |
| Processing Location | Core | Fog server | Edge server |
| Storage Capacity | Pervasive | Limited | Limited |
| Privacy and Security | Low | Low | High |
| Mobility support | No | Yes | Yes |
| Processing Capability | Pervasive | Limited | Limited |
| Ref | Smart Grid Issue | Technique Used | Approach | Performance Metrics |
|---|---|---|---|---|
| [127] | Privacy protection and energy security | PBEM-SGN | Mathematical model | Gas and time cost |
| [132] | Spoofing, MIMT, DoS | Dynamic scheduling | Architecture and Simulation | Cumulative risk |
| [129] | Cyber attacks | PEO and EnPEO-DBN | Simulation | True positive rate and error rate |
| [27] | Security | Deep reinforcement learning | Evaluation | Processing time and rewards |
| Ref | Architecture Design | End User Devices | Type of Edge Server Devices | AI Algorithms Deployed at the Edge | Objectives | Pros | Cons |
|---|---|---|---|---|---|---|---|
| [6] | Three Layers: • Device • Edge • Cloud | • Smart phones • Video camera • Voltage sensors • Proximity sensors • Current sensors | Computers | _ | Manage high volume of data from IoT devices in SGs | Compatibility between layers was considered Provision was made for security and management services | Provides a generic framework with no specific SG application use case Provides no software layers No interconnections between edge nodes |
| [24] | Three Layers: • Smart users • Edge • Central Cloud | • Smart meters | MDMS | Federated learning | Reduce overall communication cost, preserve user privacy and enhance situational awareness in AMI | Tailored for AMI Provides for interconnection of edge nodes | Provides no software layers Does not indicate security and management services |
| [75] | Five Layers: • Device • Network • Data • Application • Cloud | • Solar and wind farm • Airport, mall and town | Microgrid central controller | _ | Enhancing the rapid response for user’s requirement, intelligent scheduling, maintenance and rapid market responses | Provides details about hardware and software layers Provides for security and management services Adapted for power distribution surveillance systems | No provisioning for ML deployment at the edge |
| [172] | Three Layers: • Device • Edge • Cloud | • Sensor • Machine tool • Robot | Edge cloud Edge controller Edge gateway | _ | Fault location in distribution grids | Provides details about the interconnection of devices at the edge layer It adapts the generic architecture for fault location application | No details of software layers No provisioning of security and management services |
| [174] | Three Layers: • Service • Edge • Cloud | • Power devices | Edge nodes | Deep reinforcement learning | Optimize communication, computing, and caching resources | It differentiates the service layer as a system consisting of users and power devices | No software layers No provision for security and management services |
| [27] | Three Layers: • Power terminal • Edge • Cloud | • Smart sensors • Microgrid facilities • Intelligent charging piles | Edge agents | Deep reinforcement learning | Enhance security situational awareness for SGs | Provides details about architecture’s adaptation to security situational awareness in SG | Provides no details of software layers |
| [175] | Three Layers: • Smart grid • Edge • Cloud | • Smart meters • Distributed generators • Distributed energy storage systems • Smart electrical appliances | Edge nodes | P2P model, Alternating direction of method multipliers | Enhance energy resource management and penetration of renewable energy sources | Provides adaptation to SG applications | No provisioning of security and management services |
| [20] | Two Layers: • Edge • Cloud | • RTUs | RL agent | Reinforcement learning | Enable large-scale deployment in a cost-efficient manner | Provides details about the operations at edge and cloud | Does not differentiate between device and edge |
| Reference | Architecture | Major Contributions on Computation Offloading |
|---|---|---|
| [180] | No | Offloading mechanism, interference, and energy consumption |
| [181] | No | Energy consumption, QoS guarantee, and QoE enhancement |
| [17] | Yes | Offloading decision, resource allocation, and mobility management |
| [184] | No | Optimal Offloading scheme, overall computation overhead, and computational efficiency |
| [182] | Yes | Task partitioning, allocation, and execution |
| [185] | No | Offloading decisions, caching enhancement, and reduce execution delay |
| Ref | Application Area | Technique | OD | RA | MM | Performance Metrics | Mathematical Tools | Accuracy |
|---|---|---|---|---|---|---|---|---|
| [187] | Vehicular | • Reinforcement learning • Distributed deep learning • Deep neural networks | Yes | Yes | No | • Reward ratio | Binary optimization | – |
| [199] | Multiuser interference environment | • BiJOR • ACS-CLPSO | Yes | Yes | No | • Average energy consumption • Average AN | Bilevel optimization | – |
| [180] | Wireless networks | • Q-Learning • BRI | Yes | No | No | • Performance ratio’s bound • Average energy consumption • Multiple user offloading | Non-coorporative exact potential game | 87.87% |
| [184] | Ultradense IoT networks | • Game-theoretic greedy | Yes | No | No | • Computation overhead • Running time • Energy consumption • Minimum processing time | MECO | 79%, 83%, and 52% |
| [186] | MEC system | • Spectral clustering • Label propagation theory • Graph cut | No | Yes | No | • Running time • Local energy consumption • Transmission energy consumption | Constrained double-objective optimization | – |
| [185] | Mobile collaborative | • Cooperative call graph • Coalition formation game | Yes | No | No | • Average delay • Average caching hit probability • Average offloading probability | OOCS | 42.83% and 33.28% |
| [173] | IoT | • Stochastic gradient descent • Queuing theory | No | Yes | No | • Execution time • Energy consumption • Payment cost | Nonlinear multiobjective optimization | – |
| [200] | Multi-channel wireless interference environment | • Heuristic • Nash Equilibrium | Yes | No | No | • No.of decision slots • Computation overhead • No.of beneficial cloud computing users | NP-hard | – |
| Ref | Application Area | Cybersecurity Issue | Method | Contribution |
|---|---|---|---|---|
| [236] | IoT | Trust | Blockchain |
|
| [202] | LTE Networks |
| SDP |
|
| [127] | Smart Grid |
| Blockchain |
|
| [230] | Industrial control systems |
| CNN |
|
| [237] | Smart Grid | Security | Blockchain |
|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Molokomme, D.N.; Onumanyi, A.J.; Abu-Mahfouz, A.M. Edge Intelligence in Smart Grids: A Survey on Architectures, Offloading Models, Cyber Security Measures, and Challenges. J. Sens. Actuator Netw. 2022, 11, 47. https://doi.org/10.3390/jsan11030047
Molokomme DN, Onumanyi AJ, Abu-Mahfouz AM. Edge Intelligence in Smart Grids: A Survey on Architectures, Offloading Models, Cyber Security Measures, and Challenges. Journal of Sensor and Actuator Networks. 2022; 11(3):47. https://doi.org/10.3390/jsan11030047
Chicago/Turabian StyleMolokomme, Daisy Nkele, Adeiza James Onumanyi, and Adnan M. Abu-Mahfouz. 2022. "Edge Intelligence in Smart Grids: A Survey on Architectures, Offloading Models, Cyber Security Measures, and Challenges" Journal of Sensor and Actuator Networks 11, no. 3: 47. https://doi.org/10.3390/jsan11030047
APA StyleMolokomme, D. N., Onumanyi, A. J., & Abu-Mahfouz, A. M. (2022). Edge Intelligence in Smart Grids: A Survey on Architectures, Offloading Models, Cyber Security Measures, and Challenges. Journal of Sensor and Actuator Networks, 11(3), 47. https://doi.org/10.3390/jsan11030047








