A Systematic Review of Radio Frequency Threats in IoMT
Abstract
:1. Introduction
1.1. Radiofrequency Attacks
1.2. Recommended Solutions
- A description of the current state of research on internet of things (IoT) side-channel attacks.
- The aim of this study was to understand the research gap about sniffing and replaying IoMT attacks in the healthcare ecosystem.
- The research papers were reviewed top-down to facilitate our future research, including those on cybersecurity systems, cybersecurity frameworks, cyber-attacks on layers and protocols, radio frequency machine learning, and deep learning in a cybersecurity field experimentation.
- The conclusions we have reached, and our plans for future work are presented.
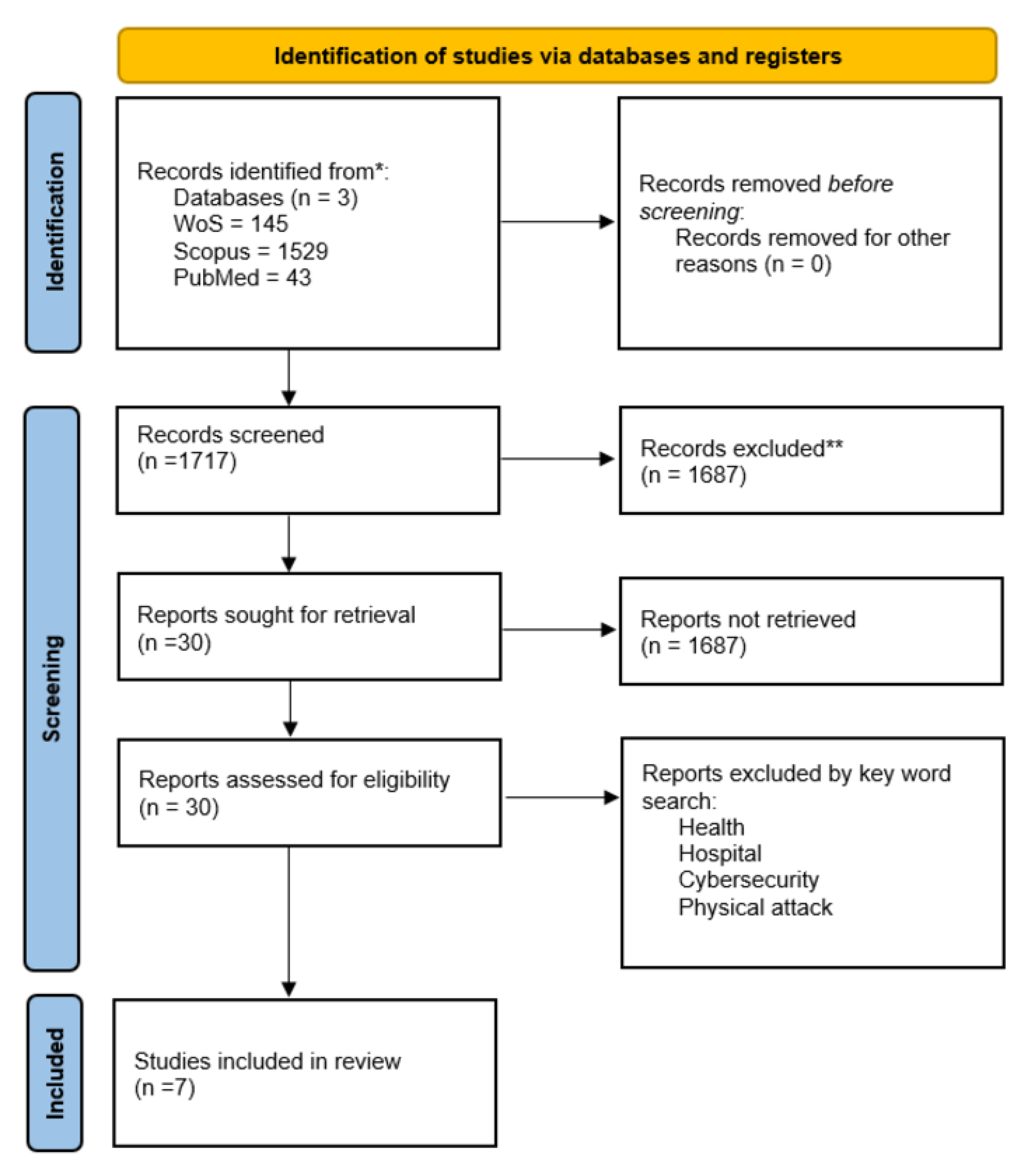
2. Methodology
2.1. Research Questions
- RQ1: How well has IoT been integrated into healthcare?
- RQ2: What is the current state of healthcare-RF cybersecurity research?
2.2. The Source of Data
- Web of Science (WoS);
- Scopus;
- PubMed.
2.3. Search Strategy and Selection Criteria
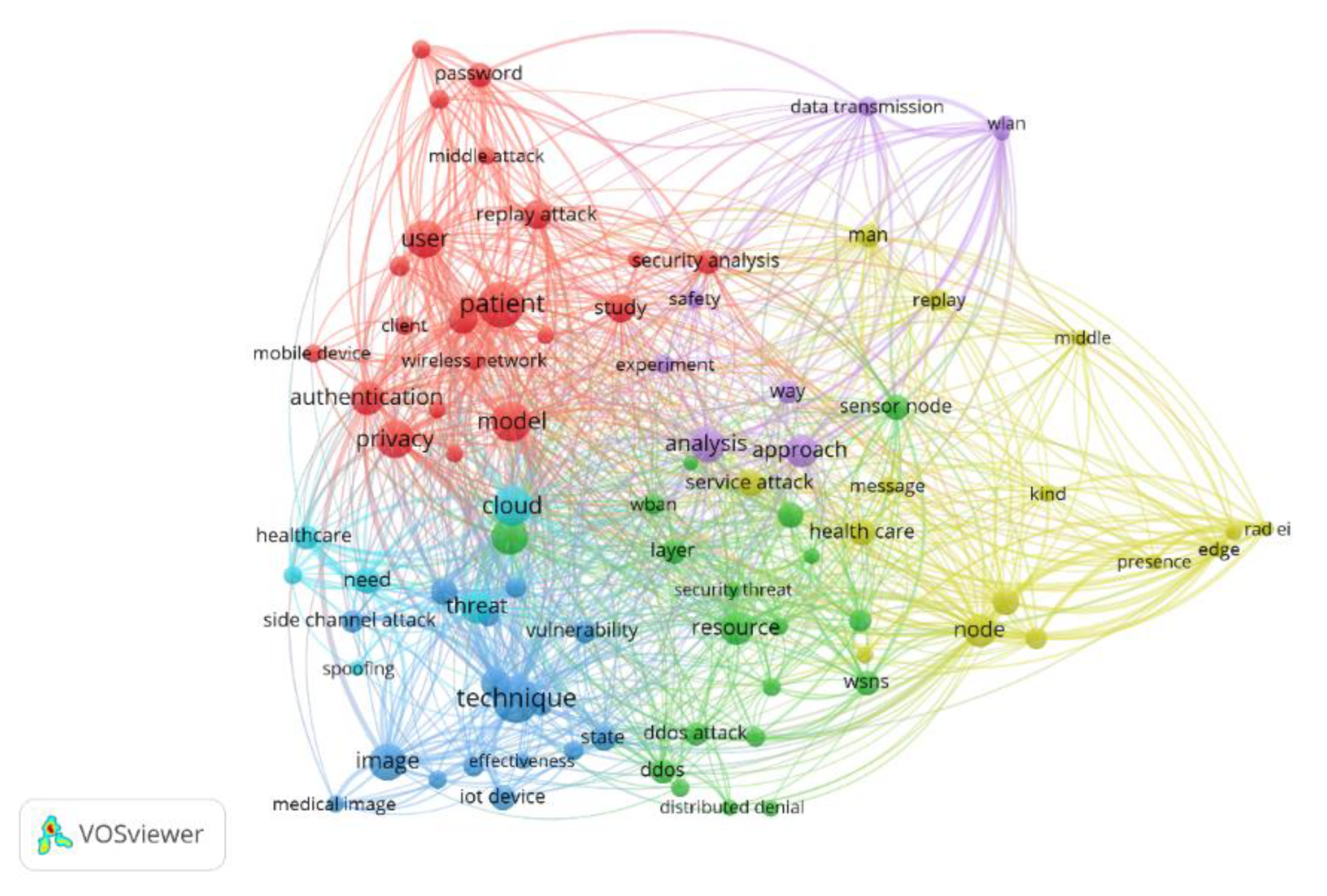
2.4. Data Collection and Visualization
2.5. Search Strategy and Selection Criteria
2.6. Data Generalization
3. Results and Discussion
- RQ1: How well has IoT been integrated into health care?
- 2.
- RQ2: What is the current state of healthcare-RF cybersecurity research?
3.1. Cyber Impacts and Layered Attacks
3.1.1. Cyber-Attacks Taxonomy
3.1.2. Cyber Security Framework
3.1.3. Cyber-Attacks Classification
3.2. Cyber-Physical Attacks on Protocols
Cyber-Physical Attacks on Low-Power Protocols
3.3. Sniffing Attack
3.4. Cybersecurity Experimentation with AI-Enabled CS
3.5. Radiofrequency Machine Learning and Data Set Creation
4. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
| The Objective |
| A Systematic Review of Radio Frequency Threats in IoMT. |
| Research Questions |
| RQ1: How well has IoT been integrated into healthcare? RQ2: What is the current state of healthcare-RF cybersecurity research? |
| Literature Reviewers |
| Primary reviewer: Mr. Irrai Anbu Jayaraj, Energy and Resources Institute, College of Engineering, IT and Environment, Charles Darwin University, NT, Australia. Second reviewer: Dr. Bharanidharan Shanmugam, Energy and Resources Institute, College of Engineering, IT and Environment, Charles Darwin University, NT, Australia. Third reviewer: Dr. Sami Azam, College of Engineering, IT and Environment, Charles Darwin University, NT, Australia. |
| Methodology of search |
| Search Terms:ALL (“JAMMING ATTACK”) AND ALL (“HEALTH”) AND PUBYEAR > 2002 ALL (“REPLAY ATTACK”) AND ALL (“HEALTH”) AND PUBYEAR > 2002 ALL (“SNIFFING ATTACK”) AND ALL (“HEALTH”) AND PUBYEAR > 2002 ALL (“TAMPERING ATTACK”) AND ALL (“HEALTH”) ALL (“SIDE CHANNEL ATTACK”) AND ALL VAND PUBYEAR > 2002 ALL (“DENIAL ATTACK”) AND ALL (“HEALTH”) AND PUBYEAR > 2002 ALL (“SPOOFING”) AND ALL (“HEALTH”) AND PUBYEAR > 2002 |
| The following databases are included: |
| Web of Science (WoS), Scopus, and PubMed |
| Process of evaluation (POE) |
| POE1: Range: Evaluations are based on the date range (2003–2022) and originality of the studies. POE2: Relevance: During the screening process, titles and abstracts are checked for relevance to IoMT in attacks on physical layers. POE3: Inclusion: Studies are evaluated against inclusion criteria. The inclusion of any study that does not meet all the criteria is discarded. POE4: Specificity: Checking whether the studies relate closely enough to the defined research field of IoMT in healthcare cybersecurity. POE5: Data: Data related to the research questions and contributions are analyzed for selected studies. |
| Criteria for the study |
| Inclusion Criteria (I)I1: The original research study was conducted by the corresponding author. I2: A publication about IoT and cybersecurity at the physical layer. I3: Research findings should be adequately explained in publications. I4: Years of publication between 2003 and 2022. Exclusion Criteria (E) E1: Reviews of the literature, secondary research, and other publications that are not related to the topic. E2: Publications that contain only ideas, such as magazines, interviews, and discussion papers. E3: Non-English publications. |
| Report |
| A spreadsheet is used to record and analyze findings. |
References
- Guri, M. MAGNETO: Covert channel between air-gapped systems and nearby smartphones via CPU-generated magnetic fields. Future Gener. Comput. Syst. 2021, 115, 115–125. [Google Scholar] [CrossRef]
- Guri, M.; Zadov, B.; Elovici, Y. ODINI: Escaping Sensitive Data From Faraday-Caged, Air-Gapped Computers via Magnetic Fields. IEEE Trans. Inf. Forensics Secur. 2020, 15, 1190–1203. [Google Scholar] [CrossRef]
- Mirsky, Y.; Guri, M.; Elovici, Y. HVACKer: Bridging the Air-Gap by Attacking the Air Conditioning System. arXiv 2017, arXiv:1703.10454. [Google Scholar]
- Guri, M.; Bykhovsky, D. aIR-Jumper: Covert air-gap exfiltration/infiltration via security cameras & infrared (IR). Comput. Secur. 2019, 82, 15–29. [Google Scholar]
- Kang, S.-G.; Song, M.-S.; Kim, J.-W.; Lee, J.W.; Kim, J. Near-Field Communication in Biomedical Applications. Sensors 2021, 21, 703. [Google Scholar] [CrossRef]
- Gomez, C.; Oller, J.; Paradells, J. Overview and Evaluation of Bluetooth Low Energy: An Emerging Low-Power Wireless Technology. Sensors 2012, 12, 11734–11753. [Google Scholar] [CrossRef]
- Pahlavan, K.; Krishnamurthy, P. Evolution and Impact of Wi-Fi Technology and Applications: A Historical Perspective. Int. J. Wirel. Inf. Netw. 2021, 28, 3–19. [Google Scholar] [CrossRef]
- Koutras, D.; Stergiopoulos, G.; Dasaklis, T.; Kotzanikolaou, P.; Glynos, D.; Douligeris, C. Security in IoMT Communications: A Survey. Sensors 2020, 20, 4828. [Google Scholar] [CrossRef]
- Aygun, I.; Kaya, B.; Kaya, M. Aspect Based Twitter Sentiment Analysis on Vaccination and Vaccine Types in COVID-19 Pandemic With Deep Learning. IEEE J. Biomed. Heal. Inform. 2022, 26, 2360–2369. [Google Scholar] [CrossRef]
- Pati, D.; Lorusso, L.N. How to Write a Systematic Review of the Literature. HERD 2018, 11, 15–30. [Google Scholar] [CrossRef]
- Kuckertz, A.; Block, J. Reviewing systematic literature reviews: Ten key questions and criteria for reviewers. Manag. Rev. Q. 2021, 71, 519–524. [Google Scholar] [CrossRef]
- Detecting Cybersecurity Attacks in Internet of Things Using Artificial Intelligence Methods: A Systematic Literature Review. Available online: https://www.mdpi.com/2079-9292/11/2/198/htm (accessed on 23 February 2022).
- Kelly, J.T.; Campbell, K.L.; Gong, E.; Scuffham, P. The Internet of Things: Impact and Implications for Health Care Delivery. J. Med. Internet Res. 2020, 22, e20135. [Google Scholar] [CrossRef] [PubMed]
- Edwards, T. Reviews: British Standards Institution: Glossary of documentation terms. BSI, I976. 8Ipp. BS 5408: I976. £8.20. ISBN o 580 09407 3. J. Librariansh. 1977, 9, 235–239. [Google Scholar] [CrossRef]
- Blažič, B.J. Changing the landscape of cybersecurity education in the EU: Will the new approach produce the required cybersecurity skills? Educ. Inf. Technol. 2021, 27, 3011–3036. [Google Scholar] [CrossRef]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. Syst. Rev. 2021, 10, 89. [Google Scholar] [CrossRef]
- Perianes-Rodriguez, A.; Waltman, L.; van Eck, N.J. Constructing bibliometric networks: A comparison between full and fractional counting. J. Inf. 2016, 10, 1178–1195. [Google Scholar] [CrossRef]
- van Eck, N.J.; Waltman, L. Software survey: VOSviewer, a computer program for bibliometric mapping. Scientometrics 2010, 84, 523. [Google Scholar] [CrossRef]
- Ferreira, R.; Gaspar, J.; Sebastião, P.; Souto, N. Effective GPS Jamming Techniques for UAVs Using Low-Cost SDR Platforms. Wirel. Pers. Commun. 2020, 115, 2705–2727. [Google Scholar] [CrossRef]
- Greene, K.; Rodgers, D.; Dykhuizen, H.; McNeil, K.; Niyaz, Q.; Shamaileh, K.A. Timestamp-based Defense Mechanism against Replay Attack in Remote Keyless Entry Systems. In Proceedings of the 2020 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 4–6 January 2020; pp. 1–4. [Google Scholar]
- Huang, S.; Lin, C.; Zhou, K.; Yao, Y.; Lu, H.; Zhu, F. Identifying physical-layer attacks for IoT security: An automatic modulation classification approach using multi-module fusion neural network. Phys. Commun. 2020, 43, 101180. [Google Scholar] [CrossRef]
- Shafiee, E.; Mosavi, M.R.; Moazedi, M. Detection of Spoofing Attack using Machine Learning based on Multi-Layer Neural Network in Single-Frequency GPS Receivers. J. Navig. 2017, 71, 169–188. [Google Scholar] [CrossRef]
- Bender, D.; Sartipi, K. HL7 FHIR: An Agile and RESTful approach to healthcare information exchange. In Proceedings of the 26th IEEE International Symposium on Computer-Based Medical Systems, Porto, Portugal, 20–22 June 2013; pp. 326–331. [Google Scholar]
- Hong, N.; Wang, K.; Yao, L.; Jiang, G. Visual FHIR: An Interactive Browser to Navigate HL7 FHIR Specification. In Proceedings of the 2017 IEEE International Conference on Healthcare Informatics (ICHI), Park City, UT, USA, 23–26 August 2017; pp. 26–30. [Google Scholar]
- Nahra, K.J. HIPAA Security Enforcement Is Here. IEEE Secur. Priv. 2008, 6, 70–72. [Google Scholar] [CrossRef]
- Agrafiotis, I.; Nurse, J.; Goldsmith, M.; Creese, S.; Upton, D. A taxonomy of cyber-harms: Defining the impacts of cyber-attacks and understanding how they propagate. J. Cybersecur. 2018, 4, tyy006. Available online: https://academic.oup.com/cybersecurity/article/4/1/tyy006/5133288 (accessed on 24 August 2020). [CrossRef] [Green Version]
- Cremer, F.; Sheehan, B.; Fortmann, M.; Kia, A.N.; Mullins, M.; Murphy, F.; Materne, S. Cyber risk and cybersecurity: A systematic review of data availability. Geneva Pap. Risk Insur.-Issues Pract. 2022, 47, 698–736. [Google Scholar] [CrossRef]
- Moreira, G.B.; Calegario, V.M.; Duarte, J.C.; dos Santos, A.F.P. Extending the VERIS Framework to an Incident Handling Ontology. In Proceedings of the 2018 IEEE/WIC/ACM International Conference on Web Intelligence (WI), Santiago, Chile, 3–6 December 2018; pp. 440–445. [Google Scholar]
- Dedeke, A.; Masterson, K. Contrasting cybersecurity implementation frameworks (CIF) from three countries. Inf. Comput. Secur. 2019, 27, 373–392. [Google Scholar] [CrossRef]
- Lejins, Y.; Leitch, J. A Holistic Approach to eHealth Security in Australia: Developing a National eHealth Sercurity and Access Framework (NESAF). Australian eHealth Informatics and Security Conference. 2012. Available online: https://ro.ecu.edu.au/aeis/8 (accessed on 24 February 2022).
- Mouaatamid, O.E.; Lahmer, M.; Belkasmi, M. Internet of Things Security: Layered classification of attacks and possible Countermeasures. Electron. J. Inf. Technol. 2016, 66–80. Available online: http://www.webmail.revue-eti.net/index.php/eti/article/view/98 (accessed on 28 September 2020).
- Hamza, T.; Kaddoum, G.; Meddeb, A.; Matar, G. A Survey on Intelligent MAC Layer Jamming Attacks and Countermeasures in WSNs. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–5. [Google Scholar]
- Patil, M.M.; Hanni, A.; Tejeshwar, C.H.; Patil, P. A qualitative analysis of the performance of MongoDB vs. MySQL database based on insertion and retriewal operations using a web/android application to explore load balancing—Sharding in MongoDB and its advantages. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 10–11 February 2017; pp. 325–330. [Google Scholar]
- Agarwal, M.; Biswas, S.; Nandi, S. An Efficient Scheme to Detect Evil Twin Rogue Access Point Attack in 802.11 Wi-Fi Networks. Int. J. Wireless Inf. Netw. 2018, 25, 130–145. [Google Scholar] [CrossRef]
- Lichtman, M.; Jover, R.P.; Labib, M.; Rao, R.; Marojevic, V.; Reed, J.H. LTE/LTE-A jamming, spoofing, and sniffing: Threat assessment and mitigation. IEEE Commun. Mag. 2016, 54, 54–61. [Google Scholar] [CrossRef]
- Giustiniano, D.; Schalch, M.; Liechti, M.; Lenders, V. Interference Suppression in Bandwidth Hopping Spread Spectrum Communications. In Proceedings of the 11th ACM Conference on Security & Privacy in Wireless and Mobile Networks (WiSec ’18), Stockholm, Sweden, 18–20 June 2018; Association for Computing Machinery: New York, NY, USA, 2018; pp. 134–143. [Google Scholar] [CrossRef]
- Wullems, C.; Tham, K.; Smith, J.; Looi, M. A trivial denial of service attack on IEEE 802.11 direct sequence spread spectrum wireless LANs. In Proceedings of the 2004 Symposium on Wireless Telecommunications, Pomona, CA, USA, 14–15 May 2004; pp. 129–136. [Google Scholar]
- Mekki, K.; Bajic, E.; Chaxel, F.; Meyer, F. A comparative study of LPWAN technologies for large-scale IoT deployment. ICT Express 2019, 5, 1–7. [Google Scholar] [CrossRef]
- Kumbhar, A. Overview of ISM Bands and Software-Defined Radio Experimentation. Wirel. Pers. Commun. 2017, 97, 3743–3756. [Google Scholar] [CrossRef]
- Nahapetian, A. Side-channel attacks on mobile and wearable systems. In Proceedings of the 2016 13th IEEE Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; pp. 243–247. [Google Scholar]
- Khattak, H.A.; Shah, M.A.; Khan, S.; Ali, I.; Imran, M. Perception layer security in Internet of Things. Future Gener. Comput. Syst. 2019, 100, 144–164. [Google Scholar] [CrossRef]
- Sauer, F.; Niedermaier, M.; Kießling, S.; Merli, D. LICSTER—A Low-cost ICS Security Testbed for Education and Research. arXiv 2019, arXiv:191000303. [Google Scholar]
- Abdulkareem, K.H.; Mohammed, M.A.; Gunasekaran, S.S.; Al-Mhiqani, M.N.; Mutlag, A.A.; Mostafa, S.A.; Ali, N.S.; Ibrahim, D.A. A Review of Fog Computing and Machine Learning: Concepts, Applications, Challenges, and Open Issues. IEEE Access 2019, 7, 153123–153140. [Google Scholar] [CrossRef]
- Xin, Y.; Kong, L.; Liu, Z.; Chen, Y.; Li, Y.; Zhu, H.; Gao, M.; Hou, H.; Wang, C. Machine Learning and Deep Learning Methods for Cybersecurity. IEEE Access 2018, 6, 35365–35381. [Google Scholar] [CrossRef]
- Sjarif, N.N.A.; Chuprat, S.; Mahrin, M.N.; Ahmad, N.A.; Ariffin, A.; Senan, F.M.; Zamani, N.A.; Saupi, A. Endpoint Detection and Response: Why Use Machine Learning? In Proceedings of the 2019 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 16–18 October 2019; pp. 283–288. [Google Scholar]
- Dujmić, M.; Delija, D.; Sirovatka, G.; Žagar, M. Using FireEye Endpoint Security for educational purposes. In Proceedings of the 2020 43rd International Convention on Information, Communication and Electronic Technology (MIPRO), Opatija, Croatia, 28 September–2 October 2020; pp. 1206–1211. [Google Scholar]
- Tselios, C.; Tsolis, G.; Athanatos, M. A Comprehensive Technical Survey of Contemporary Cybersecurity Products and Solutions. In Computer Security; Springer-Verlag: Berlin/Heidelberg, Germany, 2020; pp. 3–18. [Google Scholar]
- Copeland, M.; Jacobs, M. Reduce Cyber Security Vulnerabilities: IaaS and Data. In Cyber Security on Azure: An IT Professional’s Guide to Microsoft Azure Security; Copeland, M., Jacobs, M., Eds.; Apress: Berkeley, CA, USA, 2021; pp. 83–108. [Google Scholar]
- Wong, L.J.; Clark, I.V.W.H.; Flowers, B.; Buehrer, R.M.; Michaels, A.J.; Headley, W.C. The RFML Ecosystem: A Look at the Unique Challenges of Applying Deep Learning to Radio Frequency Applications. arXiv 2020, arXiv:201000432. [Google Scholar]
- Khan, H.A.; Sehatbakhsh, N.; Nguyen, L.N.; Callan, R.L.; Yeredor, A.; Prvulovic, M.; Zajic, A. IDEA: Intrusion Detection through Electromagnetic-Signal Analysis for Critical Embedded and Cyber-Physical Systems. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1150–1163. [Google Scholar] [CrossRef]



| Type of Attack | IoT Layer | Attack Area Description |
|---|---|---|
| Primary emulation | Perception | The primary transmitter/antenna emits information or spilling of information. |
| Spectrum sensing | Perception | Fake identification and observation of spectrum sensing process. |
| Control channel attack | Network | Untrusted system or process collecting confidential information of trusted system/process. |
| Cross-layer attack | All layers | Parallel attack on all the layers of IoT. |
| SDR device attack | All layers | SDR device antenna/battery and other core part disruption. |
| Jamming attack | All layers | Decreasing signal to interference noise ratio by blocking the information transfer between transmitter and receiver in the communication channel. |
| Replay attack | All layers | Interception of signal between transmitter and receiver to accomplish fake transmission. |
| Sniffing attack | All layers | Closely monitoring the sensitive or unauthorized information between transmitter and receiver in the communication channel. |
| Tampering attack | All layers | Closely monitoring the sensitive or unauthorized information between transmitter and receiver in the communication channel and modification of process/parameters to compromise the system. |
| Denial attack | All layers | Closely monitoring the sensitive or unauthorized information between transmitter and receiver in the communication channel, modification of process/parameters, and disrupting the availability. |
| Attack Search | Web of Science | Scopus | PubMed | Total |
|---|---|---|---|---|
| Jamming Attack | 17 | 330 | 0 | 347 |
| Replay Attack | 50 | 372 | 23 | 445 |
| Side-Channel Attack | 30 | 447 | 0 | 477 |
| Sniffing Attack | 0 | 18 | 1 | 19 |
| Spoofing Attack | 23 | 316 | 5 | 344 |
| Tampering Attack | 25 | 46 | 14 | 85 |
| Total | 145 | 1529 | 43 | 1717 |
| Type of Attack | Section | Data | Method | Conclusion/Result |
|---|---|---|---|---|
| This framework provides details related to incident insights. It classifies incidents based on external, internal, and partner-based threats. It also provides insights into hacking evidence, including IoT forensics), malware behavior, social engineering attacks, privilege misuse, and known and unintentional errors. | 3.1 | 2 | 3 | The key metrics on incidents are classified based on victims (size of the organization), actors, actions, assets, attributes, timelines, impacts, and repeated events. |
| The research explains various attacks on that three-layer IoT architecture, starting with physical attacks, jamming attacks, relay attacks, Sybil, selective forwarding, side-channel, replay, evil twin, sniffing, and spoofing. | 3.1 | 1 | 3 | The paper shows goal-based classification and the evolving spectrum-level vulnerabilities causing significant disruption to the OSI. |
| Their investigation claims that mobilityand QoS will be high for specific communication protocols. | 3.2 | 1 | 3 | The reverse engineering of the spectrum to retrieve those payloads and understand the protocols becomes a base process of attack strategies. The hardness scale depends on the main contributing factors: encryption, frequency band, modulation, spread spectrum, and protocols. |
| How asset mobility contributes to the continuous evaluation and monitoring of high-value assets and elevates risk mitigation strategies and guidelines. | 3.2 | 2 | 3 | The paper evaluates the reasoning behind new cybersecurity threats from radio channel-based adversaries such as cluster drones, mobile networks, satellites, marine, aeronautical, in-depth space communication, and IoT. |
| Categorization of attack levels—operating system level, user interface level—and how the sensitive information flows across the process are captured for further analysis. | 3.3 | 2 | 3 | The inheritance of password authentication shows the infancy of research rigor and does not contribute to sniffing attacks. |
| This paper contributes to knowledge more than the practical implementation of design, artifacts, proof of concepts, experimentation, evaluation, and future direction. | 3.3 | 1 | 4 | The main idea will enhance the motivation to identify the research focus with potential questions. IoMT is operating under MICS or ISM frequency. |
| The architectural design and completion of the Version 1 CASE-V testbed. They developed a web-based UI framework using the MEAN. | 3.4 | 2 | 4 | To reduce the dependability of an external penetration tester, a low-cost testbed can be performed to improve the effectiveness and usability of CSM. |
| The research claims that open-source hardware and software can develop a testbed within 500 euros for ethical Industrial Control System hacking, education, competency development, and research. | 3.4 | 1 | 4 | According to the analysis, insider threats and associated toolsimpact levels 0 and 1 compared to a remote intruder. The author’s findings proved that a low-cost testbed is possible in the corporate ecosystem. |
| Overview of publicly available data sets for intelligent cybersecurity intrusion detection system. Also, it proposed how ML and DL techniques can be used to analyze the raw network traffic data having real-time traffics from APT, malware, and botnets. | 3.5 | 2 | 4 | The research investigated the pros and cons between Machine Learning (ML) and Deep Learning (DL) algorithm support vector machines (SVM), deep belief network (DBN), recursive neural network (RNN), convolutional neural network (CNN), Fast-RNN and difference between ML and DL in terms of data and hardware dependencies, Feature processing, problem solving and execution time. |
| They investigated the publicly available database—IEEE, Science Direct, ACM, and Springer Link, between 1990 and 2019 to address the questions.1.ML algorithm used for endpoint detection and response (EDR)2. Alternative available for the EDR. | 3.5 | 2 | 4 | The research claims to analyze the Publication Trends in EDR and the techniques used for EDR. |
| Literature review data = 1; Public dataset = 2. | Literature study = 3; Experimental Study = 4. |
| Attacks | Web of Science | Scopus | PubMed |
|---|---|---|---|
| Jamming Attack | 17 | 330 | 0 |
| Replay Attack | 50 | 372 | 23 |
| Side-Channel Attack | 30 | 447 | 0 |
| Sniffing Attack | 0 | 18 | 1 |
| Spoofing Attack | 23 | 316 | 5 |
| Tampering Attack | 25 | 46 | 14 |
| Total | 145 | 1529 | 43 |
| Attacks | Web of Science | Scopus | PubMed |
|---|---|---|---|
| Jamming Attack | 16 | 330 | 0 |
| Replay Attack | 49 | 371 | 22 |
| Side-Channel Attack | 29 | 446 | 0 |
| Sniffing Attack | 0 | 18 | 1 |
| Spoofing Attack | 23 | 316 | 5 |
| Tampering Attack | 24 | 46 | 14 |
| Total | 141 | 1527 | 42 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jayaraj, I.A.; Shanmugam, B.; Azam, S.; Samy, G.N. A Systematic Review of Radio Frequency Threats in IoMT. J. Sens. Actuator Netw. 2022, 11, 62. https://doi.org/10.3390/jsan11040062
Jayaraj IA, Shanmugam B, Azam S, Samy GN. A Systematic Review of Radio Frequency Threats in IoMT. Journal of Sensor and Actuator Networks. 2022; 11(4):62. https://doi.org/10.3390/jsan11040062
Chicago/Turabian StyleJayaraj, Irrai Anbu, Bharanidharan Shanmugam, Sami Azam, and Ganthan Narayana Samy. 2022. "A Systematic Review of Radio Frequency Threats in IoMT" Journal of Sensor and Actuator Networks 11, no. 4: 62. https://doi.org/10.3390/jsan11040062
APA StyleJayaraj, I. A., Shanmugam, B., Azam, S., & Samy, G. N. (2022). A Systematic Review of Radio Frequency Threats in IoMT. Journal of Sensor and Actuator Networks, 11(4), 62. https://doi.org/10.3390/jsan11040062







