A Survey of Access Control Models in Wireless Sensor Networks
Abstract
:1. Introduction
2. Background
2.1. Security Vulnerabilities and Security Requirements
| Security Properties | Security Threats | Possible Solutions |
|---|---|---|
| Confidentiality | Message Disclosure | Encryption, Access Control |
| Integrity | Message Modification | Digital Signature, Secure Hash Function |
| Availability | DoS (denial of service), Wormhole, Sinkhole, Hello Flood | Intrusion Detection, Pairwise Authentication |
| Access Control, Authorization | Unauthorized and Unauthenticated Access | Access Control, Key Distribution, Encryption |
| Authentication | Message Modification, Sybil, Replay and Spoofing Attack | Random Key Distribution, Digital Signature |
| Freshness | Replay and Spoofing attack | Time-stamp, One Way Secure Hash Function |
| Secure Localization | Node Capture and Note Replication Attack | Temper-proof and Temper-evident |
| Forward and Backward Secrecy | Message Disclosure | Key Distribution |
2.2. Traditional Access Control Models
- Authorization TableA three-dimensional table, corresponding to subjects, actions and objects, respectively. Each entry in the table corresponds to an authorization.
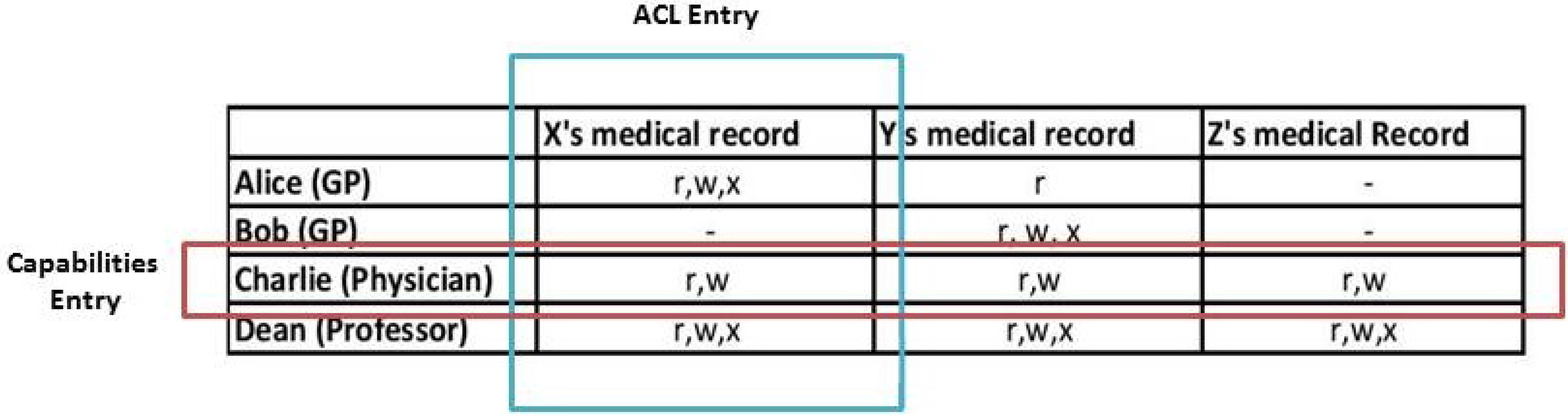
- Access Control List (ACL)Each ACL contains the list of subjects and their access permissions to a given object. When a subject tries to access an object, the ACL for that object is used to verify the request from the subject. If the subject access pair is in the ACL list, access will be granted. Otherwise, access will be denied. In the ACL approach, the lists of subject and action pair are stored for each object. An ACL is represented by a column in the matrix table as seen in Figure 1. In this figure, r, w and x stands for read, write and executable.
- CapabilitiesCapabilities are different from ACLs. Pairs of action and object are stored for each subject in the access control matrix. In a capability approach, the subject can get access to the object, when he presents the correct capability to the system. A subject’s capabilities are represented by a row in the access control matrix.
3. Access Control Models in WSNs
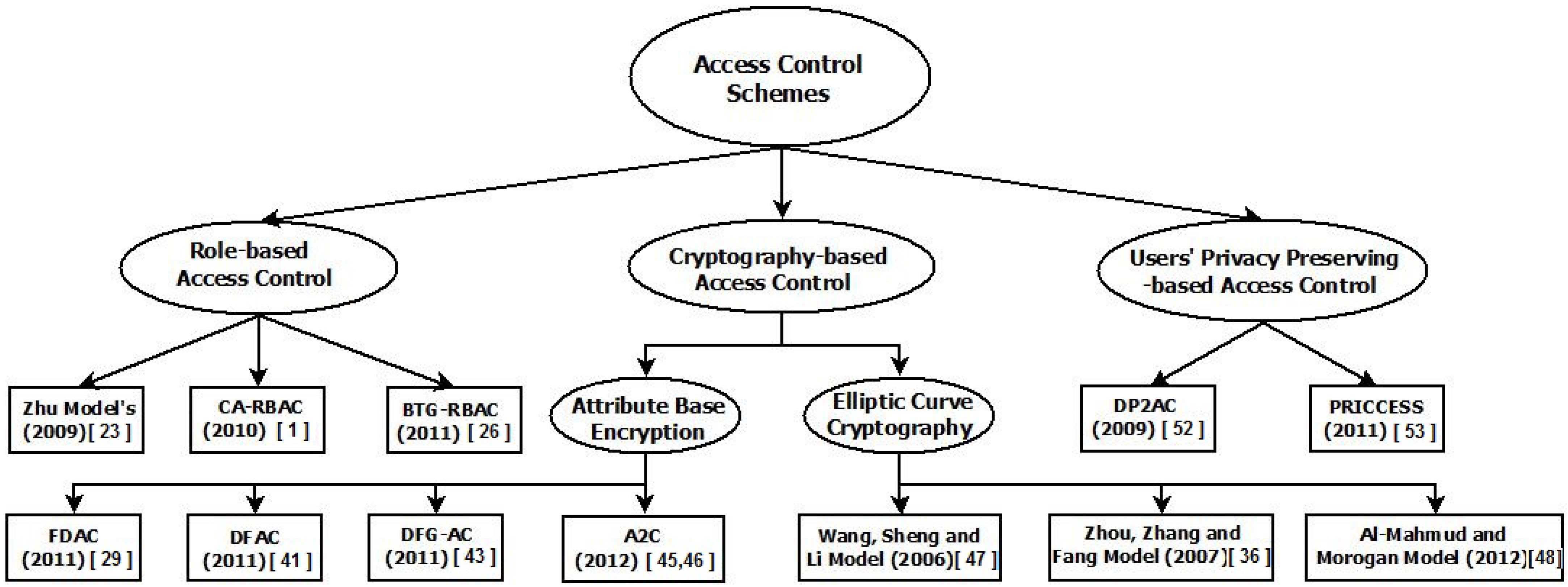
3.1. Role-Based Access Control (RBAC)
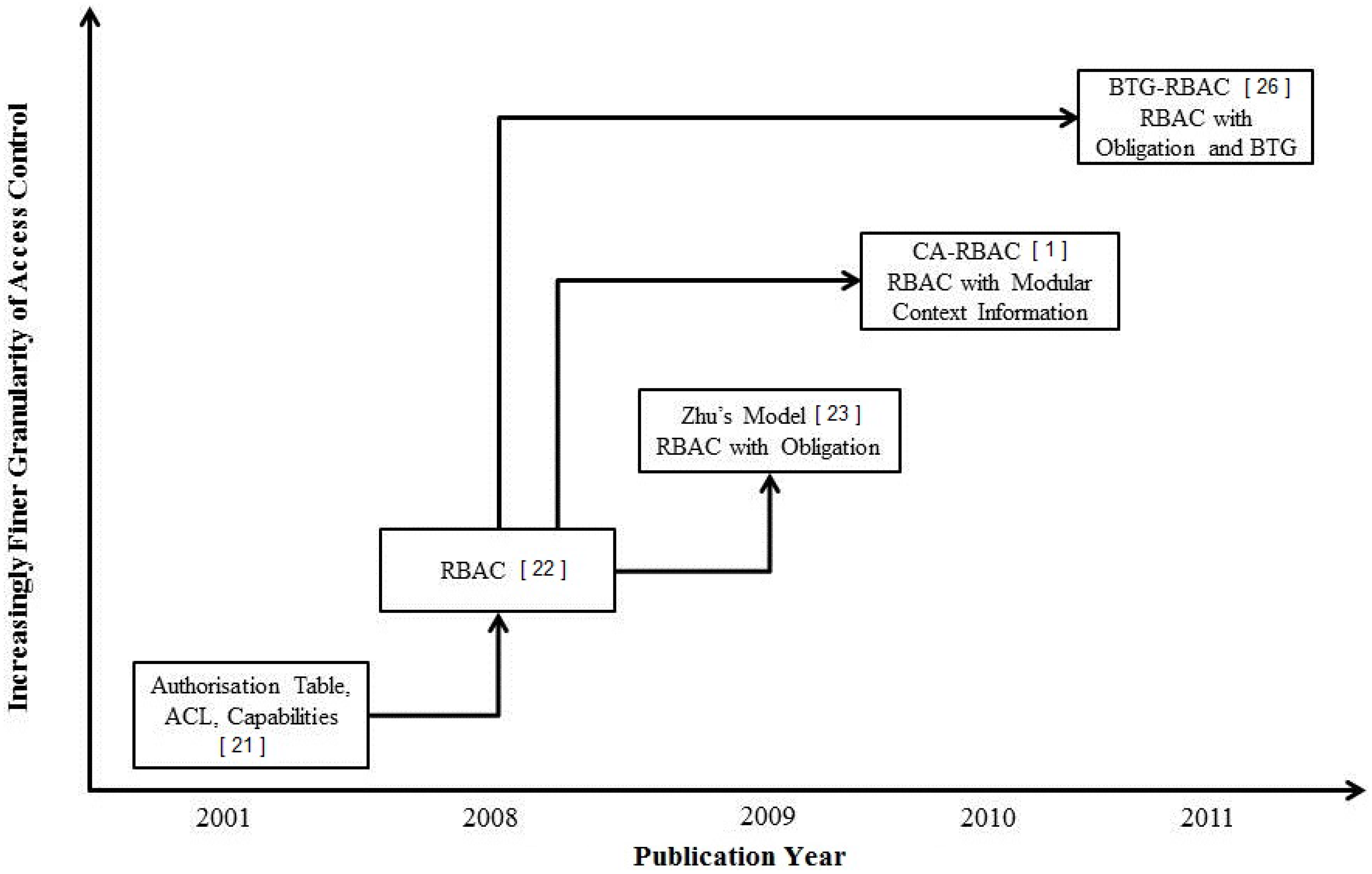
- Zhu’s Model [2009]Zhu et al. [23] proposed a light-weight policy-based access control model, which used authorization and obligation policies to perform actions and make access decisions at the sensor nodes in a WMSN. The main idea of the proposed approach is to support sensor-level access control policy. A light-weight policy system, which is known as Fingers [24], enables policy enforcement and interpretation on the distributed sensors to provide fine-grained access control. Each sensor manages its own policies to implement both the policy decision point (PDP) and policy enforcement point (PEP). A PDP interprets policies and makes a policy decision, while a PEP enforces the policy by permitting and denying a subject from performing the requested actions. A controller (perhaps a PDA) uses a Diffie–Hellman (DH) key agreement to share keys with the sensor nodes. The sensor nodes can communicate between each other in a WMSN by using secret keys from the controller. An authentication process is used to prevent malicious nodes and users from joining the network. Only the sensor nodes that have keys from the same controller can communicate with each other. If a user has access to the network controller, he can request it to perform some actions at the sensor nodes. As an application, this approach can be used in WMSN to prevent unauthorized access to actuators, such as insulin or other drug pumps, that may harm the patients.
- Context-Aware Role-Based Access Control (CA-RBAC) [2010]Garci-Morchon and Wehrle [1] proposed the context-aware role-based access control (CA-RBAC) model based on a modular context structure for WMSNs. The aim of the model is to provide context awareness and adapt its security properties to ensure the users’ safety in WMSNs. Wehrle et al. [25] pointed out that the RBAC model is not good enough to use in a WSN, because in traditional RBAC models, the roles and policies have to be predefined in advance. In the proposed model, the decision-making process is divided into three modular context situations: critical, emergency and normal condition. Based on these situations, the access privileges to sensed data will be different. The access control decision will be made based on context information, such as time, location, etc., and the access control policies of three different modules. In a WMSN, the sensor nodes are attached to the human body to sense and check medical information for a healthcare service. In the normal case, an authorized doctor needs to verify his access control role in order to access the medical data of a patient, but a nurse may not have the same level of privilege. When the system declares a critical or emergency case based on the modular context information, the doctor or nurse can perform any action and can access data, even though they may not be able to access that data in a normal condition. One of the disadvantages of this model is that there is no prevention or detection mechanism, as well as no verification process to check a user’s data access, when the critical situation occurs.
- Break-the-Glass Role-Based Access Control (BTG-RBAC) [2011]Ferreria et al. [26] proposed the break-the-glass role-based access control (BTG-RBAC) model based on the RBAC model. The main idea of this model is to gather necessary information from the end users with their collaboration for a usable access control policy that can perform the BTG action in emergency situations. The break-the-glass (BTG) rule allows the users’ to have emergency and urgent access to the system when a normal authentication does not perform or work properly. They introduced BTG rules in order to override access policy whilst providing non-repudiation mechanisms for its usage. In a real environment, unanticipated situations may occur because it is impossible to predict all of the access permissions in advance for all situations. The BTG extension is used for emergency and important cases whenever a user wants to access data urgently and immediately. When the user tries to perform BTG actions, the system will ask him if he really wants to perform that action on a specific object. If the user answers affirmatively, the system will activate the BTG operation and trigger the associated obligations, like alarms, log file, etc. The BTG-RBAC model made the system much more flexible than normal RBAC, but one of the disadvantages is that human processes are needed in order to enforce the BTG rules.
3.2. Cryptography-Based Access Control (CBAC)
3.2.1. Attribute-Based Encryption (ABE)-Based Fine-Grained Access Control

- Fine-Grained Distributed Data Access Control (FDAC) (2011)Yu et al. [29] proposed the fine-grained distributed data access control (FDAC) model based on ABE. The main idea of their approach is to provide a distributed data access control, which is able to support fine-grained access control over sensor data and is resilient against attacks, such as user collusion (unauthorized users may collude to compromise the encrypted data) and node compromise (the sensor node could be compromised by a malicious user, due to lack of compromise-resistant hardware.). A network controller, which stores access structures, acts like a central distribution centre and distributes keys to users in FDAC. Only users with the right access structure and the right key can access data at the sensor nodes. The access structures will be different for each user depending on the access privileges of users.For example, in a battlefield application, the sensor nodes may be responsible for collecting different types of data, such as vibration, smoke, etc., in different locations (village, forest). Therefore, the attributes, such as {location = village, data type = (vibration, smoke), owner = (explosion experts, officers)}, are used to specify the data access privileges of users. Based on the above example, the access structure of a user is designated as “(location is village) AND (type is vibration)”, which allows the user to obtain the vibration data within the village area. More sophisticated access structures can be defined based on the application requirements. If the network controller is compromised by a malicious user, there will be no security provisioning in the system anymore. User revocation (user revocation may be one of the following: the service subscription is expired, the user changes group intentionally or the user or group key is compromised) can be done by updating the master secret key that is embedded in the user secret key via broadcasting. In this approach, CP-ABE-based selective broadcast is used for user revocation, but there are no details on how to use it.
- Distributed Fine-Grained Access Control (DFAC) (2011)Ruj et al. [41] proposed a fully distributed fine-grained access control (DFAC) scheme using multi-authority ABE [42] to prevent a single point of failure. Instead of using one authority, like FDAC, several distribution centres (DCs) are used to store and distribute different access structures, sets of attributes and cryptographic keys to users and sensor nodes. All DCs are disjoint from each other. Each DC has its own access subtree (a subtree contains attributes at the leaf nodes of that subtree.) for each sensor node. Users, who want to access data at the sensor node, need to activate their ID with each DC to obtain access structures, access subtrees and keys. All of the subtrees from each DC are ANDed together to build a complete access structure for a single user, but the user has to store all of the access structures in order to access different types of data from the sensor network. This model facilitates modification and secret key distribution when the access rights of a user are changed, but the communication overhead of the user’s revocation process is higher than with FDAC.
- Distributed Fine-Grained Data Access Control for Distributed Sensor Networks (DFG-AC) (2011)Hur [43] proposed an access control model called distributed fine-grained data access control (DFG-AC). It uses both a network controller and a data aggregator for central key management and central storage. The collected data from sensor nodes are transferred to the data aggregator by using a distributed sensor data collection protocol, such as the Two-Tier Data Dissemination protocol (TTDD) [44]. The main idea of using the data aggregator as central storage is to perform more data encryption. Additionally, the users can get all of the information by accessing the data aggregator. The data aggregator is more powerful than the sensor nodes, and it can use complex encryption methods. The advantage of the proposed model is that it considers the stateless receiver problem. (Practically, users may miss a key update message. Therefore, they cannot keep their key states up-to-date. This problem is known as the stateless receiver problem.) To solve this problem, key revocation is done with a stateless group key distribution mechanism using a binary tree. One of the disadvantages is that the transmitting data from sensor nodes to the data aggregator consumes lots of battery power and energy. In addition, there might be a single point of failure because of the centralised data storage. This model provides user revocation by using the KP-ABE scheme with the attributes for distributed WSNs.
- Adaptive Access Control (A2C) (2012)Htoo et al. [45,46] proposed an adaptive access control (A2C) model with privilege overriding and behaviour monitoring to provide fine-grained access control for medical data in WSNs. A2C incorporates the concept of possibility-with-override and a user behaviour trust model into WSNs for hard-to-define and unanticipated situations. This model has a similar structure to BTG-RBAC, but the main difference is that no human effort is needed to override rules and policies, because of the introduction of the overriding access privileges, the users’ behaviour trust model and the prevention and detection mechanism. In this model, the users may be able to override a denial of access, when unexpected events occur. In addition, the users’ behaviour trust model is used to check user’s action, location, time, etc. The advantage of this model is that all of the user behaviour information is kept by the prevention and detection mechanism as an audit record to detect and prevent abnormal and unauthorised access, whenever the users try to access data from WSNs. ABE-based encryption and TTDD are used for data storage and data transmission. The main contribution of the proposed model is to adapt to unexpected situations by using privilege overriding and also to adjust its decision based on users’ behaviour trust values.
3.2.2. Elliptic Curve Cryptography-Based Access Control (EC-CBAC)
- Wang, Sheng and Li Model (2006)Wang et al. [47] proposed an access control model based on ECC. The main objective of the proposed model is to use an ECC scheme for granting user access rights to the collected data. Different users may have different levels of data access due to restriction of access implicated by the data confidentiality and privacy. ECC is used in key distribution and sharing information between the users and a key distribution centre (KDC). In this approach, KDC is responsible for generating all security primitives, such as random numbers, access lists and hash functions, and maintains a user list with associated user identifications. The users have to request access permission from KDC. Access lists, which comprise user identity, group identity and user privilege mask, define the user’s access privileges. User access privilege mask is a number of binary bits, and each bit represents a specific information or service. Therefore, users who possess the same mask and access privileges are put in the same group.
- Zhou, Zhang and Fang Model (2007)Zhou et al. [36] proposed an access control protocol based on ECC for node authentication and key establishment. The main idea of their approach is to accomplish node authentication and key establishment for new nodes, whenever they join the sensor network. The proposed access control model uses node identity and node bootstrapping time for the node authentication procedure. They introduced the node bootstrapping time into authentication procedures to differentiate malicious nodes from legitimate new nodes. In this model, the authors are mostly looking at the node deployment to prevent malicious nodes from joining the network. A certification authority (CA) is used to generate a certificate, which includes ID information and bootstrapping time, to authenticate the identity of a new node. Furthermore, the node certificate is signed with CA’s private key. Therefore, the adversaries cannot alter ID and bootstrapping time. When the new node is deployed in WSNs, it shows its certificate to the neighbour nodes in order to verify its identity with CA’s public key. This access control protocol enforces control sensor node deployment and prevents malicious nodes from joining sensor networks.
- Al-Mahmud and Morogan Model (2012)Al-Mahmud and Morogan [48] proposed an identity-based authentication and access control model in WSNs. The main idea of the proposed model is to use an identity-based signature (IBS) [49] for providing both user authentication and data access control in WSNs. This protocol is based on the IBS scheme, where an ECC-based digital signature algorithm (DSA) [50] is used to sign and verify a message. A base station (BS) is responsible for generating the private keys of both users and sensor nodes in the network. For the key distribution, a one pass key establishment protocol [51] is used to share session keys between sensor nodes and users. Users are required to register with BS. Based on the access request from the users, BS generates private key and access structure for each user. The sensor nodes are preloaded with hash value of user identities and the private key, which will be used for the authentication process. After the authentication process, the sensor node will check whether the user is authorized to access the data.
3.3. Users’ Privacy-Preserving Access Control (UPPAC)
- Distributed Privacy-Preserving Access Control (DP2AC) (2009)Zhang et al. [52] proposed distributed privacy-preserving access control (DP2AC). The owner of the sensor network generates the token by using a blind signature [54]. Users need to buy tokens from the network owner before entering the sensor network. The tokens can be verified by any sensor node in the network, but no one can tell the identity of the token holder, including the network owner. There is no relationship between user identities and tokens, so privacy preservation for users is achieved. Once the token is validated by a sensor node, it provides the user with a certain amount of requested data, which is equivalent to the denomination of the token. The main objective of the proposed DP2AC model is that the network owner can prevent unauthorised access to sensed data, while users can protect their data access privacy.However, a recent study [55] pointed out that DP2AC is not fine-grained access control, because each anonymous user has the same access privileges. Furthermore, the network user cannot sign a query command, because of the blind signature. As a result, the adversary can easily intercept the tokens and impersonate authorized users to access data at the sensor nodes. A disadvantage of using tokens in a WSN is that the sensor nodes need more storage for the token detection mechanism. All of the used tokens have to be recorded and stored in the sensor nodes to prevent the tokens being reused by malicious and unauthorized users.
- Distributed Privacy-Preserving Access Control (PRICCESS) (2011)He et al. [53] proposed the PRICCESS protocol for WSNs. The main contribution to the research community of this protocol is that it provides user privacy-preserving distributed access control in a single-owner multi-user sensor network. A ring signature [56] is used to protect the anonymity of users by using a group ID and group signature. Each group of users has different access privileges, IDs and keys for signature. Users have to activate their information with a network controller to receive the group ID and keys for data access. Users with the same access privileges are likely to be put in the same group by the network controller. The PRICCESS model used an ACL matrix to store the access list of the group for data access control in the network controller. Any user from the group can use a group key when he signs the message for data access request. Therefore, the network controller verifies that the message has been signed by one of the group members without knowing who the actual signer is. One of the disadvantage of using ring signature is that the overhead of signature becomes large when there is a large number of user groups in the network.
4. Comparison of Access Control Models in WSNs
4.1. Network Model
| Access Control Model | Network Architecture and Component | Key Management | Encryption and Decryption | Policy Specification and Decision-Making Process | User Revocation | User Privacy Preservation |
|---|---|---|---|---|---|---|
| Zhu’s Model [23] | Authentication Manager (AM) | DH | - | Role, Purpose, Operation | - | - |
| CA-RBAC [1] | System Administrator (SA) | - | - | Role, Context Information | - | - |
| BTG-RBAC [26] | System Administrator (SA) | - | - | Role, Purpose, Operation, Obligation | - | - |
| FDAC [29] | Network Controller (NC) | DB-DH | ABE | Attributes-Based Key | CP-ABE | - |
| DFAC [41] | Distribution Centre (DC) | B-DH | ABE | Attributes-Based Key | ABE | - |
| DFG-AC [43] | System Controller (SC) and Data Aggregator | B-DH | ABE | Attributes-Based Key | Attribute Level User Revocation | - |
| A2C [45] | System Administrator (SA) | - | ABE | Attributes-Based Key, Context Information, Behaviour Trust Value | - | - |
| Wang, Sheng and Li Model [47] | Key Distribution Centre (KDC) | EC-DH | ECC | Key | - | - |
| Zhou, Zhang and Fang Model [36] | Certificate Authority (CA) | DH | ECC | Key | - | - |
| Al-Mahmud and Morogan Model [48] | Base Station (BS) | One-Pass Key Establishment Protocol | ECC-Based IBE | Key (Built on ID) | - | - |
| DP2AC [52] | Network Owner | RSA-DH | RSA | Role, Token | - | Blind Signature |
| PRICCESS [53] | Certificate Authority (CA) | DH | ECC | Role, Group Key | - | Ring Signature |


4.2. Key Management
4.3. Data Encryption
4.4. Policy Specification and Decision-Making Process
4.5. User Revocation
4.6. Users’ Privacy Preservation
5. Evaluation of Access Control Model in WSNs
5.1. Evaluation Based on Features
- Support Data PrivacyThe need for data privacy is growing among all of the real-world applications in WSNs. Data privacy becomes more and more important in WSNs, when data are to be released to only authorized and legitimate users. The more data being disclosed, the more the owner of that data loses his own privacy.
- Support User PrivacyThe need for user privacy is important in some applications. Sometimes, a user, who tries to access data from the network, does not want to share his detailed information with other users in the network. This means that the users’ privacy preservation is needed to protect the privacy of user information in the network.
- FlexibilityNo matter how perfect an access control system is, if it does not support accommodation to changes, such as insertion and deletion of the application systems, the access control model is not feasible to use in real-world applications. In WSNs, the user characteristics and the access context are changing continuously. Therefore, the access control decisions must be synchronised with continuously changing security conditions. It is desirable for the access control model to handle the dynamism of users and environments. Therefore, the access control model needs to be flexible enough to support changes and synchronise with the access control decisions.
- Support for Emergency Data AccessAn ideal access control model needs to support data access, not only in normal situations, but also in an emergency situation. Many applications will benefit from such a provision.
- Context SensitivityAn access control model is context sensitive when context information plays a role in making the appropriate access decision. This means that the contextual information is used in defining policies for making an access control decision dynamically.
- GranularityThere are two different types of granularity in access control, which are fine-grained and coarse-grained. Fine-grained means that the access control models should allow different roles for specific data accesses and provide a fine-grained reference to the subjects and objects. Coarse-grained means that groups of users and collections of objects often share the same access control requirements. The access control system should then offer support for authorization specific to the groups of users, objects and possibly actions.
| Access Control Models | Support Data Privacy | Support User Privacy | Flexibility | Support For Emergency Access | Context Sensitivity | Granularity |
|---|---|---|---|---|---|---|
| Zhu’s Model [23] | Yes | No | No | No | No | Coarse-Grained |
| CA-RBAC [1] | Yes | No | Yes | Yes | Yes | Fine-Grained |
| BTG-RBAC [26] | Yes | No | Yes | Yes | No | Coarse-Grained |
| FDAC [29] | Yes | No | Yes | No | Yes | Fine-Grained |
| DFAC [41] | Yes | No | Yes | No | Yes | Fine-Grained |
| DFG-AC [43] | Yes | No | No | No | Yes | Fine-Grained |
| A2C [45] | Yes | No | Yes | Yes | Yes | Fine-Grained |
| Wang, Sheng and Li Model [47] | Yes | No | No | No | No | Coarse-Grained |
| Zhou, Zhang and Fang Model [36] | Yes | No | No | No | No | Coarse-Grained |
| Al-Mahmud and Morogan Model [48] | Yes | No | No | No | No | Coarse-Grained |
| DP2AC [52] | Yes | Yes | No | No | No | Coarse-Grained |
| PRICCESS [53] | Yes | Yes | No | No | No | Coarse-Grained |
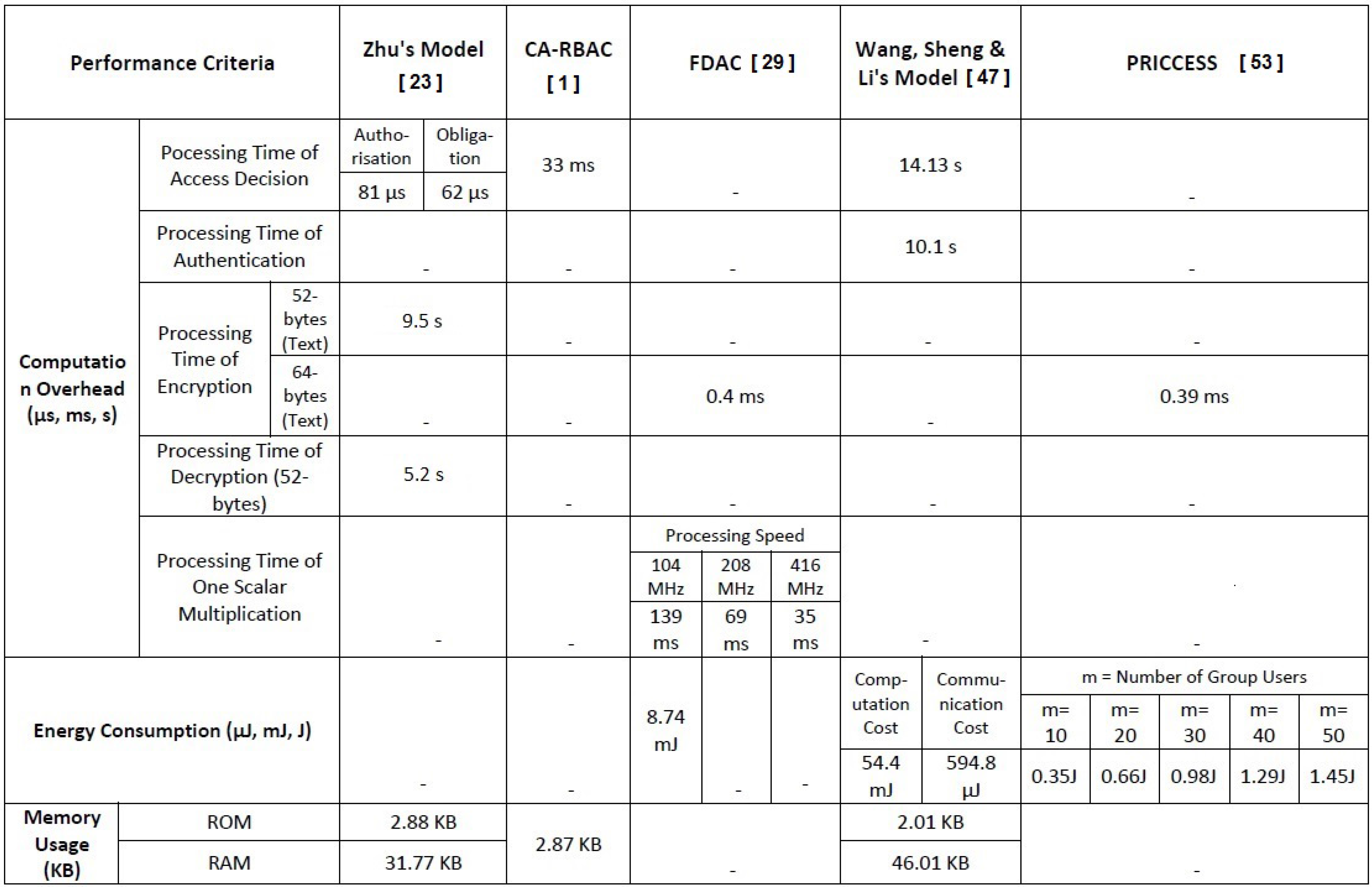
5.2. Evaluation Based on Performance

6. Potential Research Issues
- Various access control models have been proposed; however, no systematic comparisons have been conducted on these models. Further evaluation and comparison is desirable to learn the security services, performance, reliability and efficiency of these access control models.
- Most of the proposed access control models for WSNs are focused on node authentication and query authentication, but users’ data access control has received little attention. The control of the user to the sensed data at the sensor nodes merits more investigation.
- Current access control models need to be made much more flexible to make access decisions on the unexpected events, because it is hard to predefine all of the possibilities in a WSN. A new access control model is needed to address higher reliability, scalability, availability and accountability to prevent unauthorized user access and allow authorized users data access in unexpected and unpredictable cases.
- The performance of WSN access control models should be studied and measured carefully in the future. It would be useful to produce an appropriate benchmark for the WSN research community.
- It is also likely that more powerful sensor nodes will need to be designed in order to support the increasing requirements for computation and communication in the sensor nodes. This means that a powerful encryption and decryption method should be able to apply in the future.
7. Conclusion
Acknowledgement
Author Contributions
Conflict of Interest
References
- Garcia-Morchon, O.; Wehrle, K. Modular context-aware access control for medical sensor networks. In Proceedings of the 15th ACM symposium on Access control models and technologies (SACMAT ’10), Pittsburgh, PA, USA, 9–11 June 2010; pp. 129–138.
- Ngo, D.N. Deployment of 802.15.4 Sensor Networks for C4ISR Operations. PhD Thesis, Navy Postgraduate School, Monterey, CA, USA, 2006. [Google Scholar]
- Faye, Y.; Niang, I.; Noël, T. A survey of access control schemes in wireless sensor networks. World Acad. Sci. Eng. Technol. 2011, 5, 814–823. [Google Scholar]
- Vella, M.N. Survey of Wireless Sensor Network Security; Report; Texas A and M University-Corpus Christi, Computer Science Program, Texas A and M University Press: College Station, TX, USA, 2008. [Google Scholar]
- Sen, J. A survey on wireless sensor network security. Int. J. Commun. Netw. Inf. Secur. 2009, 1, 55–78. [Google Scholar]
- Ng, H.S.; Sim, M.L.; Tan, C.M. Security issues of wireless sensor networks in healthcare applications. BT Technol. J. 2006, 24, 138–144. [Google Scholar] [CrossRef]
- Wang, W.; Bhargava, B. Visualization of wormholes in sensor networks. In Proceedings of the 3rd ACM Workshop on Wireless Security (WiSe ’04), Philadelphia, PA, USA, 26 September 2004; pp. 51–60.
- Newsome, J.; Shi, E.; Song, D.; Perrig, A. The sybil attack in sensor networks: Analysis & defenses. In Proceedings of the 3rd International Symposium on Information Processing in Sensor Networks, Berkeley, CA, USA, 26–27 April 2004; pp. 259–268.
- Li, Z.; Gong, G. A Survey on Security in Wireless Sensor Networks; Technical Report; University of Waterloo: London, UK, 2008. [Google Scholar]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: attacks and countermeasures. In Proceedings of the 1st IEEE International Workshop on Sensor Network Protocols and Applications, Anchorage, AK, USA, 11 May 2003; pp. 113–127.
- Wood, A.D.; Stankovic, J.A. Denial of service in sensor networks. Computer 2002, 35, 54–62. [Google Scholar] [CrossRef]
- Perrig, A.; Stankovic, J.; Wanger, D. Security in wireless sensor networks. Commun. ACM 2004, 47, 53–57. [Google Scholar] [CrossRef]
- Gligor, V.D. Handling new adversaries in wireless ad-hoc networks (transcript of discussion). In Security Protocols XVI; Springer: Berlin/Heidelberg, Germany, 2011; Volume 6615, pp. 120–125. [Google Scholar]
- Wang, Y.; Attebury, G.; Ramamurthy, B. A survey of security issues in wireless sensor networks. IEEE Commun. Surv. Tutor. 2006, 8, 20–23. [Google Scholar] [CrossRef]
- Alemdar, H.; Ersoy, C. Wireless sensor networks for healthcare: A survey. Comput. Netw. 2010, 54, 2688–2710. [Google Scholar] [CrossRef]
- Pathan, A.S.K.; Lee, H.-W.; Hong, C.S. Security in wireless sensor networks: Issues and challenges. In Proceedings of the 8th International Conference on Advanced Communication Technology, Pyeongchang, Korea, 20–22 February 2006; Volume 2.
- Raymond, D.R.; Midkiff, S.F. Denial-of-service in wireless sensor networks: Attacks and defenses. IEEE Pervasive Comput. 2008, 7, 74–81. [Google Scholar] [CrossRef]
- Ferraiolo, D.F.; Kuhn, D.R. Role-based access controls. In Proceedings of the 15th National Computer Security Conference, Baltimore, MD, USA, 13–16 October 1992.
- Sandhu, R.; Munawer, Q. How to do discretionary access control using roles. In Proceedings of the 3rd ACM Workshop on Role-Based Access Control, Fairfax, VA, USA, 22–23 October 1998.
- Lampson, B. Protection. In Proceedings of the 5th Princeton Conference on Information Sciences and Systems, Princeton, NJ, USA, January 1971.
- Samarati, P.; Vimercati, S. Access control: Policies, models, and mechanisms. In Foundation of Security Analysis and Design; Springer: Berlin Heidelberg, Germany, 2001; Volume 2171, pp. 137–196. [Google Scholar]
- Zhao, G.; Chadwick, D.W. On the modeling of bell-lapadula security policies using RBAC. In Proceedings of the 2008 IEEE 17th Workshop on Enabling Technologies: Infrastructure for Collaborative Enterprises (WETICE ’08), Washington, DC, USA, 23–25 June 2008; pp. 257–262.
- Zhu, Y.; Keoh, S.L.; Sloman, M.; Lupu, E.C. A lightweight policy system for body sensor network. IEEE Trans. Netw. Serv. Manag. 2009, 6, 137–148. [Google Scholar] [CrossRef]
- Zhu, Y.; Keoh, S.L.; Sloman, M.; Lupu, E.; Zhang, Y.; Dulay, N.; Pryce, N. Finger: An efficient policy system for body sensor networks. In Proceedings of 5th IEEE International Conference on Mobile Ad Hoc and Sensor Systems, Atlanta, GA, USA, 29 September–2 October 2008; pp. 428–433.
- Morchon, O.G.; Wehrle, K. Efficient and context-aware access control for pervasive medical sensor networks. In Proceedings of 2010 8th IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops), Mannheim, Germany, 29 March–2 April 2010.
- Ferreria, A.; Correia, R.; Monterio, H.; Brito, M.; Antunes, L. Usable access control policy and model for healthcare. In Proceedings of 2011 24th International Symposium on Computer-Based Medical Systems (CBMS), Bristol, UK, 27–30 June 2011; pp. 1–6.
- Ghani, N.A.; Selamat, H.; Sidek, Z.M. Analysis of existing privacy-aware access control for e-commerce application. Glob. J. Comput. Sci. Technol. 2012, 12, 1–5. [Google Scholar]
- Al-Hamdani, W.A. Cryptography based access control in healthcare web systems. In Proceedings of 2010 Information Security Curriculum Development Conference (InfoSecCD ’10), Kennesaw, GA, USA, 1–3 October 2010; pp. 66–79.
- Yu, S.; Ren, K.; Lou, K. Fdac: Toward fine-grained distributed data access control in wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2011, 22, 673–686. [Google Scholar] [CrossRef]
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1983, 26, 96–99. [Google Scholar] [CrossRef]
- Malan, D.J.; Welsh, M.; Smith, M.D. A public-key infrastructure for key distribution in tinyos based on elliptic curve cryptography. In Proceedings of the First Annual IEEE Communications Society Conference on Sensor and Ad Hoc Communications and Networks, Santa Clara, CA, USA, 4–7 October 2004.
- Boneh, D.; Gentry, C.; Waters, B. Collusion resistant broadcast encryption with short ciphertexts and private keys. In Proceedings of the 25th annual international conference on Advances in Cryptology (CRYPTO’05), Berlin/Heidelberg, Germany, 20–24 August 2005; pp. 258–275.
- Gaubatz, G.; Kaps, J.-P.; Sunar, B. Public key cryptography in sensor networks—Revisited. In Security in Ad-hoc and Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2004; pp. 2–18. [Google Scholar]
- Gura, N.; Patel, A.; Wander, A.; Eberle, H.; Shantz, S.C. Comparing elliptic curve cryptography and RSA on 8-bit CPUs. In Cryptographic Hardware and Embedded Systems—CHES 2004; Springer: Berlin/Heidelberg, Germany, 2004; pp. 119–132. [Google Scholar]
- Wander, A.S.; Gura, N.; Eberle, H.; Gupta, V.; Shantz, S.C. Energy analysis of public-key cryptography for wireless sensor networks. In Proceedings of the 3rd IEEE International Conference on Pervasive Computing and Communications (PERCOM ’05), Kauai Island, HI, USA, 8–12 March 2005; pp. 324–328.
- Zhou, Y.; Zhang, Y.; Fang, Y. Access control in wireless sensor networks. Ad Hoc Netw. 2007, 5, 3–13. [Google Scholar] [CrossRef]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 89–98.
- Gentry, C. Handbook of information Security; John Wiley and Sons: Bakersfield, CA, USA, 2006. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy, Washington, DC, USA, 20–23 May 2007; pp. 321–334.
- Li, J.; Zhao, G.; Chen, X.; Xie, D.; Rong, C.; Li, W.; Tang, L.; Tang, Y. Fine-grained data access control systems with user accountability in cloud computing. In Proceedings of IEEE 2nd International Conference on Cloud Computing Technology and Science, Indianapolis, IN, USA, 30 November 2010.
- Ruj, S.; Nayak, A.; Stojmenovic, I. Distributed fine-grained access control in wireless sensor networks. In Proceedings of 2011 IEEE International Parallel and Distributed Processing Symposium (IPDPS), Anchorage, AK, USA, 16–20 May 2011; pp. 352–362.
- Chase, M.; Chow, S.S.M. Improving privacy and security in multi-authority attribute-based encryption. In Proceedings of the 16th ACM Conference on Computer and Communications Security, Chicago, IL, USA, 9–13 November 2009.
- Hur, J. Fine-grained data access control for distributed sensor networks. Wirel. Netw. 2011, 17, 1235–1249. [Google Scholar] [CrossRef]
- Ye, F.; Luo, H.; Cheng, J.; Lu, S.; Zhang, L. A two-tier data dissemination model for large-scale wireless sensor networks. In Proceedings of the 8th Annual International Conference on Mobile Computing and Networking (MobiCom’02), Atlanta, Georgia, USA, 23–28 September 2002; pp. 148–159.
- Maw, H.; Xiao, H.; Christianson, B. An adaptive access control model for medical data in wireless sensor networks. In Proceedings of 2013 IEEE 15th International Conference on e-Health Networking, Applications and Services (Healthcom) (IEEE Healthcom 2013), Lisbon, Portugal, 9–12 October 2013.
- Maw, H.A.; Xiao, H.; Christianson, B. An adaptive access control model with privileges overriding and behaviour monitoring in wireless sensor networks. In Proceedings of the 8th ACM International Symposium on QoS and Security for Wireless and Mobile Networks 2012 (ACM Q2SWinet 2012), Paphos, Cyprus, 24–25 October 2012.
- Wang, H.; Sheng, B.; Li, Q. Elliptic curve cryptography based access control in sensor networks. Int. J. Secur. Netw. 2006, 1, 127–137. [Google Scholar] [CrossRef]
- Al-mahmud, A.; Morogan, M.C. Identity-based authentication and access control in wireless sensor networks. Int. J. Comput. Appl. 2012, 41, 18–24. [Google Scholar] [CrossRef]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Advances in Cryptology; Springer: Berlin/Heidelberg, Germany, 1985; Volume 196, pp. 47–53. [Google Scholar]
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
- Wang, Y.; Wong, D.S.; Huang, L. A one-pass key establishment protocol for anonymous wireless roaming with PFS. In Proceedings of 2011 IEEE International Conference on Communications (ICC), Kyoto, Japan, 5–9 June 2011; pp. 1–5.
- Zhang, R.; Zhang, Y.; Ren, K. DP2AC: Distributed privacy-preserving access control in sensor networks. In Proceedings of the 28th IEEE International Conference on Computer Communications, Joint Conference of the IEEE Computer and Communications Societies (INFOCOM 2009), Rio de Janeiro, Brazil, 19–25 April 2009; pp. 1251–1259.
- He, D.; Bu, J.; Zhu, S.; Chan, S.; Chen, C. Distributed access control with privacy support in wireless sensor networks. IEEE Trans. Wirel. Commun. 2011, 10, 3472–3481. [Google Scholar] [CrossRef]
- Radu, C.; Govaerts, R.; Vandewalle, J. A restrictive blind signature scheme with applications to electronic cash. In Proceedings of the IFIP TC6/TC11 International Conference on Communications and Multimedia Security II, Essen, Germany, 23–24 September 1996; pp. 196–207.
- Li, M.; Lou, W.; Ren, K. Data security and privacy in wireless body area networks. Wirel. Commun. 2010, 17, 51–58. [Google Scholar] [CrossRef]
- Bender, A.; Katz, J.; Morselli, R. Ring signatures: Stronger definitions, and constructions without random oracles. J. Cryptol. 2008, 22, 114–138. [Google Scholar] [CrossRef]
- Perrig, A.; Szewczyk, R.; Wen, V.; Culler, D.; Tygar, J.D. Spins: Security protocols for sensor networks. Wirel. Netw. 2001, 8, 189–199. [Google Scholar] [CrossRef]
- Boneh, D.; Waters, B. Constrained Pseudorandom Functions and Their Applications; Cryptology ePrint Archive; Report 2013/352; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Mohammad, A.; Khdour, T.; Kanaan, G.; Kanaan, R.; Ahmad, S.B. Analysis of existing access control models from web services applications’ perspective. J. Comput. 2011, 3, 10–16. [Google Scholar]
- Sahafizadeh, E.; Parsa, S. Survey on access control models. In Proceedings of 2nd International Conference on Future Computer and Communication, Wuhan, China, 21–24 May 2010.
- Twidle, K.; Dulay, N.; Lupu, E.; Sloman, M. Ponder2: A Policy System for Autonomous Pervasive Environments. Available online: http://pubs.doc.ic.ac.uk/ponder2-policy-pervasive/ponder2-policy-pervasive.pdf (accessed on 9 May 2012).
- Liu, A.; Ning, P. TinyECC: A configurable library for elliptic curve cryptography in wireless sensor networks. In Proceedings of 2008 International Conference on Information Processing in Sensor Networks, St. Louis, MO, USA, 22–24 April 2008; pp. 245–256.
- Skipjack and KEA Algorithm Specifications. Available online: http://csrc.nist.gov/encryption/skipjack-kea.htm (accessed on 13 May 2013).
© 2014 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Maw, H.A.; Xiao, H.; Christianson, B.; Malcolm, J.A. A Survey of Access Control Models in Wireless Sensor Networks. J. Sens. Actuator Netw. 2014, 3, 150-180. https://doi.org/10.3390/jsan3020150
Maw HA, Xiao H, Christianson B, Malcolm JA. A Survey of Access Control Models in Wireless Sensor Networks. Journal of Sensor and Actuator Networks. 2014; 3(2):150-180. https://doi.org/10.3390/jsan3020150
Chicago/Turabian StyleMaw, Htoo Aung, Hannan Xiao, Bruce Christianson, and James A. Malcolm. 2014. "A Survey of Access Control Models in Wireless Sensor Networks" Journal of Sensor and Actuator Networks 3, no. 2: 150-180. https://doi.org/10.3390/jsan3020150
APA StyleMaw, H. A., Xiao, H., Christianson, B., & Malcolm, J. A. (2014). A Survey of Access Control Models in Wireless Sensor Networks. Journal of Sensor and Actuator Networks, 3(2), 150-180. https://doi.org/10.3390/jsan3020150




