Security Vulnerabilities in Bluetooth Technology as Used in IoT
Abstract
:1. Introduction
- Present an overview of Bluetooth technology with a focus on its security, vulnerabilities, threats, and risk mitigation solutions.
- Provide real-life examples of recent Bluetooth exploits.
- Discuss several recommended measures to secure Bluetooth communication.
2. Related Work
3. Overview of Bluetooth Technology
3.1. Bluetooth Frequency and Connectivity Ranges
3.2. Bluetooth Piconet
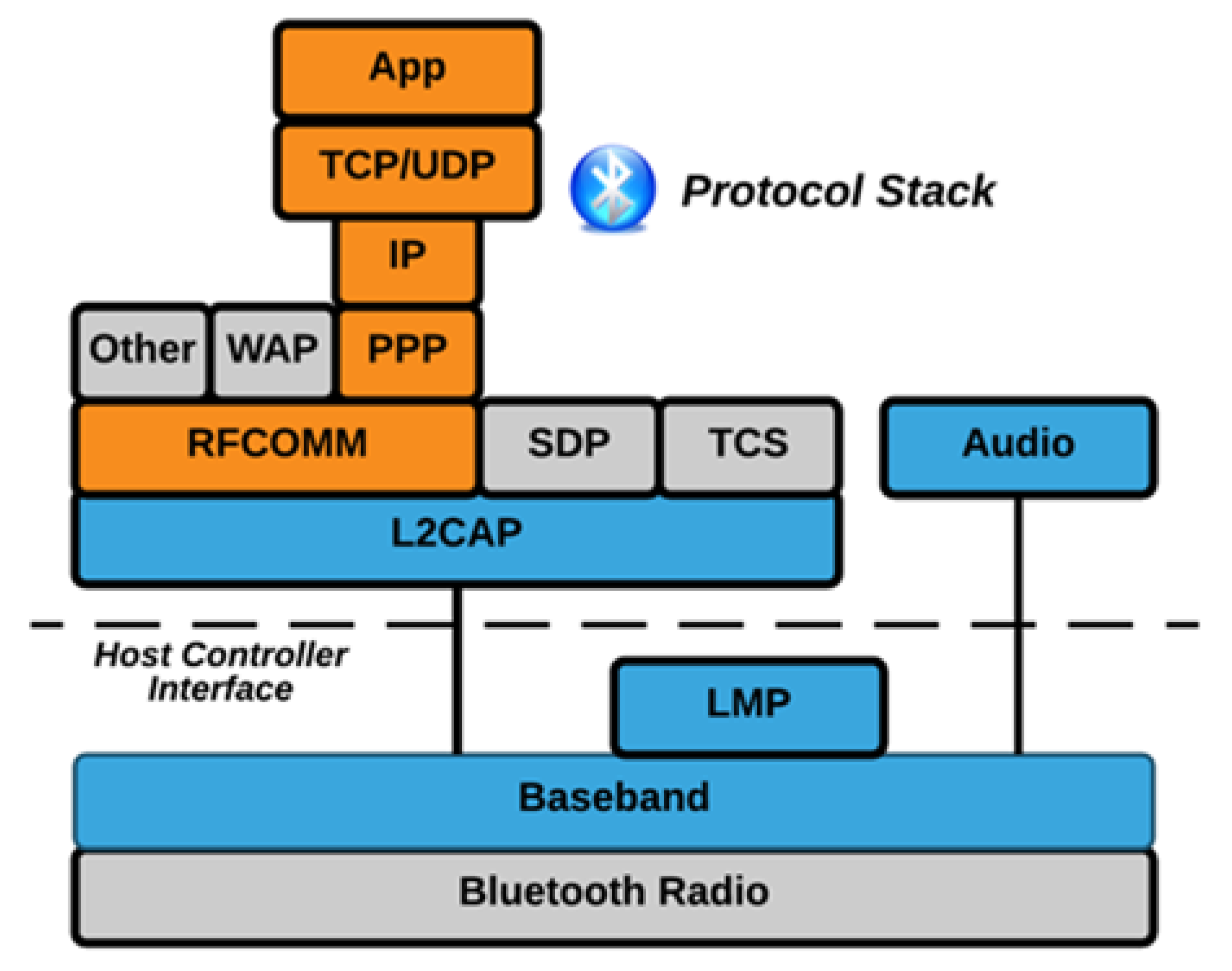
3.3. Bluetooth Protocol Stack
4. Bluetooth Security
- (1)
- Trusted—A trusted device has established a fixed relationship with another device and has unrestricted access to all services.
- (2)
- Untrusted—An untrusted device only has access to a restricted set of services. Although the device has passed authentication successfully, it does not have a fixed relationship with another device.
- (1)
- Adaptive Frequency Hopping: Frequency hopping in Bluetooth uses a 2.4 GHz ISM band with 79 channels to enable hops at 1600 hops per second. During the hopping, existing frequencies are excluded. The ability to frequency hop reduces both jamming and interference.
- (2)
- E0 Cipher Suite: The cipher generally has a key length of 128 bits and uses stream ciphering.
- (3)
- Undiscoverability: This prevents devices from responding to scanning attempts. A device’s 48-bit BD_ADDR address is also concealed.
- (4)
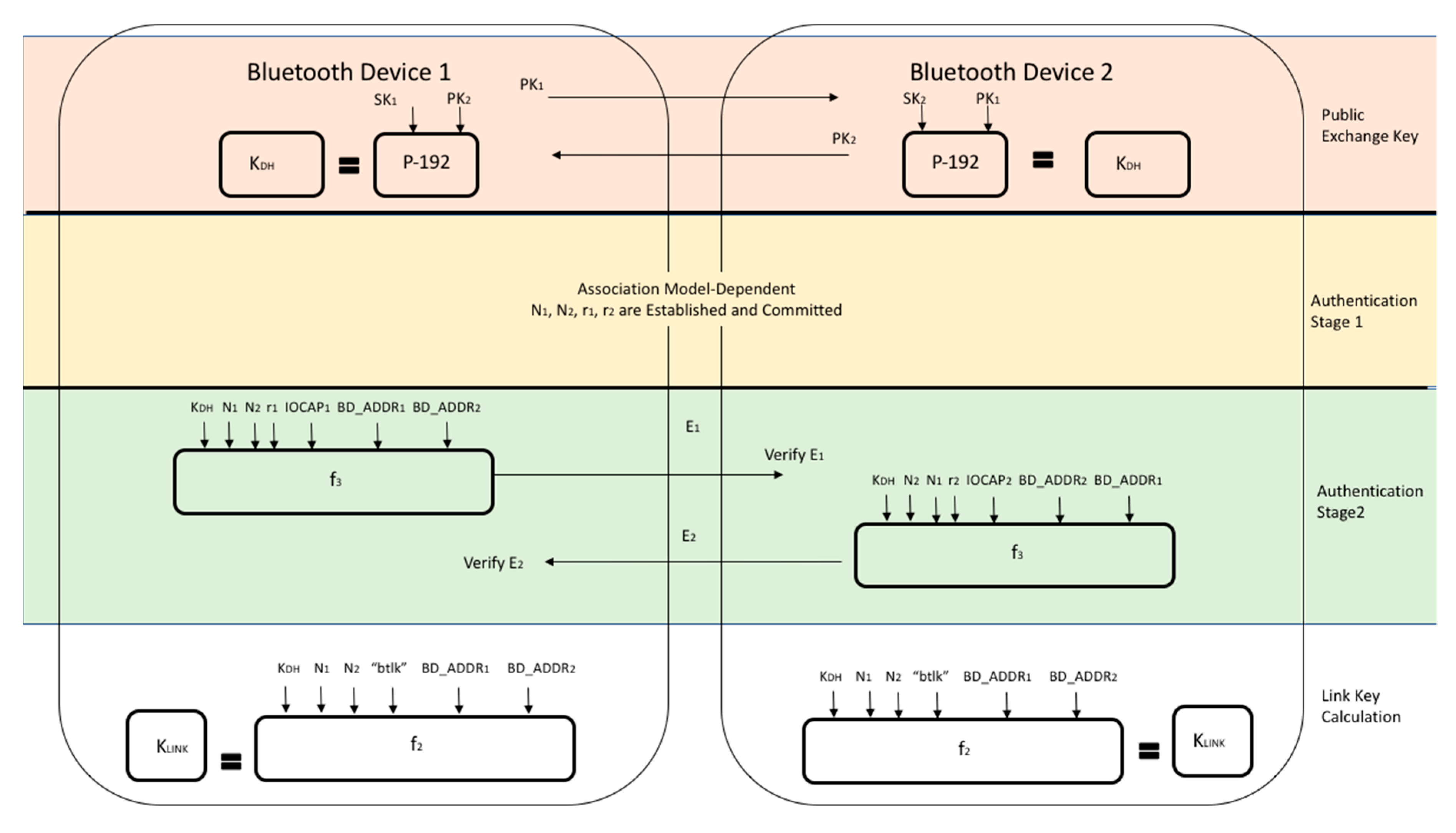
- Pairing: Pairing enables devices to communicate. A device’s BD_ADDR must be known for a pairing request to be made. The BD_ADDR, which is discussed in the previous two sections, is identified from knowledge of previous pairing or by scanning.
5. Bluetooth Vulnerabilities and Threats
5.1. Vulnerabilities in Bluetooth Versions
- (1)
- (2)
- Versions before Bluetooth 2.1 + EDR: Codes that consist of short PINs are permitted [2]. These PINs are easy for attackers to guess due to their short length [2]. These versions are lacking in PIN management, which is a desirable security capability at an enterprise level [2]. In addition, the keystreams in these early versions become vulnerable after being connected for 23.3 h [2]. This is the time period at which the keystream repeats [2]. This increases an adversary’s ability to decrypt messages [2].
- (3)
- Versions 2.1 and 3.0: If Security Mode 4 devices are connecting to devices that do not support Security Mode 4, earlier security modes are used in the connection [2]. For example, it is possible that Security Mode 1, which offers no security, will be used [2]. This rollback in security modes makes versions 2.1 and 3.0 more vulnerable to attacks [2]. In addition, SSP static keys are used in versions 2.1 and 3.0, which increases the device’s vulnerability to Man-in-the-Middle attacks [2].
- (4)
- Versions before Bluetooth 4.0: There is an unlimited number of authentication challenge requests, which enables adversaries to obtain information on many challenge responses [2]. This allows them to gain insight on secret link keys [2]. In addition, the stream cipher E0 function, which is used in early versions, is considered weak [2].
- (5)
- All versions of Bluetooth: Adversaries can view and potentially modify link keys if they are stored improperly [2]. In addition, encryption key lengths may be small, which can make them vulnerable to attackers [2]. It is possible that encryption keys can be as small as 1 byte [2]. Regarding authentication, there is no user authentication [2]. The Bluetooth standard only includes device authentication [2]. It is important to note that a device can remain in discoverable/connectable mode for an indefinite period of time [2,3].
5.2. Bluetooth Taxonomy of Attacks
5.3. Common Bluetooth Attacks
- (1)
- Cabir Worm: A malicious software that targets Bluetooth technology. Mobile phones that use the Symbian series 60 interface platform are vulnerable to the attacks [8]. For the attacks to be successful, the user must accept the worm [8]. This causes the malware to install on the device [8]. The worms are usually disguised in applications, which results in users unknowingly accepting them [8]. Once installed, the software is the able to use the compromised device to search for and send itself to other available devices [38]. The Mabir worm is a form of the Cabir worm [8]. This worm replicates by using Multimedia Messaging Service messages and Bluetooth [8].
- (2)
- Skulls Worm: The Skulls Worm, a malicious SIS (Symbian Installation System) trojan file, targets Symbian mobile phones with the Series 60 platform [8]. The worm poses as a Macromedia Flash player [8]. The user must open and install the SIS file for the worm to become active [8]. It then searches for additional devices to infect and the process repeats itself [8,38].
- (3)
- Lasco Worm: The Lasco worm, is a combination of a Bluetooth worm and SIS file [8]. It targets and infects Symbian mobile phones that support the Series 60 platform [8]. The user must open and install the velasco.sis file [8]. This prompts the activation of the worm [8]. It can then begin searching for additional devices to infect and the process repeats itself [8,38].
6. Bluetooth Risk Mitigation and Countermeasures
6.1. Mitigation Techniques
- Enhancement of Bluetooth user awareness: it is necessary to educate Bluetooth users to ensure they have knowledge of the proper Bluetooth security practices [2]. These security practices include:
- (1)
- Default settings should be updated to achieve optimal standards [2].
- (2)
- Ensuring devices are in and remain in a secure range. This is done by setting devices to the lowest power level [2].
- (3)
- Using long and random PIN codes, which make the codes less susceptible to brute-force attacks [2].
- (4)
- Changing the default PIN for devices and frequently updating this PIN (i.e., once every other month).
- (5)
- Setting devices to undiscoverable mode by default, except as needed for pairing [2]. Most active discovery tools require that devices be in discoverable mode to be identified. Devices set to undiscoverable mode will not be visible to other Bluetooth devices. Devices previously configured, better known as trusted devices, will be able to connect and communicate while in this hidden mode.
- (6)
- Turning off a device’s Bluetooth when not needed or in use, especially while in certain public areas such as shopping malls, coffee shops, public transportation, clubs, bars, etc [2]. This can prevent users from receiving advertisements from other Bluejackers.
- (7)
- Refraining from entering passkeys or PINs when unexpectedly prompted to do so.
- (8)
- Frequently updating software and drivers to have the most recent product improvements and security fixes.
- (9)
- It is recommended that users refrain from using non-supported or not secure Bluetooth-enabled devices or modules. This includes Bluetooth versions 1.0 and 1.2.
- (10)
- Pairing devices as needed [2]. Users need to maintain that any pairing should take place in a secure non-public setting [2]. This will help prevent attackers from intercepting pairing messages [2]. As previously mentioned, a crucial part of Bluetooth security is pairing, so users should have knowledge regarding eavesdropping [2].
- (11)
- Users should use SSP instead of legacy PIN authentication for the pairing exchange process when it is possible. This will help mitigate PIN cracking attacks.
- (12)
- (13)
- (14)
- All devices that are paired should be removed immediately after use.
- (15)
- Devices should be monitored and kept at close range.
- Use link encryption for all data transmissions to prevent any eavesdropping, including passive eavesdropping [2]. Use of the HID boot mode mechanism, a connectionless human interface device, should be avoided, as it sends traffic in plaintext.
- Lower the risk of broadcast interceptions by encrypting the broadcasts [2].
6.2. Applications for Protecting Bluetooth Devices
- (1)
- (2)
- Bluetooth file transfer: This application only enables authorized devices to be connected [40].
7. Commercial Product Examples
7.1. Bluetooth Automotive Hacks
7.2. Bluetooth Medical Hacks
7.3. Bluetooth Smartwatch/Smart Bracelet Hacks
7.4. Bluetooth Smartphone Hacks
7.5. Bluetooth Smarthome Hacks
7.6. Bluetooth Hacks on Children’s Toys
7.7. Issues with Vulnerabilities in Commercial Products
8. Recommendations to Secure Bluetooth Communications
9. Conclusions
Funding
Conflicts of Interest
References
- Bisikian, C. An overview of the Bluetooth wireless technology. IEEE Commun. Mag. 2001, 39, 86–94. [Google Scholar] [CrossRef] [Green Version]
- Cope, P.; Campbell, J.; Hayajneh, T. An Investigation of Bluetooth Security Vulnerabilities. In Proceedings of the 7th IEEE Annual Computing and Communication Workshop and Conference (IEEE CCWC 2017), Las Vegas, NV, USA, 9–11 January 2017. [Google Scholar]
- National Institute of Standards and Technology. Guide to Bluetooth Security: Recommendations of the National Institute of Standards and Technology; Special Publication 800-121 Revision 1; National Institute of Standards and Technology: Maryland, MD, USA, 2008.
- NIST Special Publication 800-121 Revision 2: Guide to Bluetooth Security. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-121r2.pdf (accessed on 6 June 2018).
- Gerez, S. Implementation of Digital Signal Processing: Some Background on GFSK Modulation. Available online: http://wwwhome.ewi.utwente.nl/~gerezsh/sendfile/sendfile.php/gfsk-intro.pdf?sendfile=gfsk-intro.pdf (accessed on 14 July 2018).
- Bluetooth 5 FAQ: Everything You Need to Know. Available online: https://www.macworld.com/article/3262664/hardware/bluetooth-5-faq-everything-you-need-to-know.html (accessed on 6 June 2018).
- Harris, A., III; Khanna, V.; Tuncay, G.; Want, R.; Kravets, R. Bluetooth low energy in dense IoT environments. IEEE Commun. Mag. 2016, 54, 30–36. [Google Scholar] [CrossRef]
- Nateq Be-Nazir Ibn, M.; Tarique, M. Bluetooth security threats and solutions: A survey. Int. J. Distrib. Parallel Syst. 2012, 3, 127. [Google Scholar]
- Panse, T.; Panse, P. A Survey on Security Threats and Vulnerability attacks on Bluetooth Communication. Int. J. Comput. Sci. Inf. Technol. 2013, 4, 741–746. [Google Scholar]
- Hassan, S.S.; Bibon, S.D.; Hossain, M.S.; Atiquzzzaman, M. Security Threats in Bluetooth Technology. Comput. Secur. 2017, 74, 308–322. [Google Scholar] [CrossRef]
- Darroudi, S.M.; Gomez, C. Bluetooth low energy mesh networks: A survey. Sensors 2017, 17, 1467. [Google Scholar] [CrossRef] [PubMed]
- Zou, Y.; Wang, X.; Hanzo, L. A survey on wireless security: Technical challenges, recent advances and future trends. arXiv, 2015; arXiv:1505.07919. [Google Scholar]
- Hayajneh, T.; Almashaqbeh, G.; Ullah, S.; Vasilakos, A.V. A survey of wireless technologies coexistence in WBAN: Analysis and open research issues. Wirel. Netw. 2014, 20, 2165–2199. [Google Scholar] [CrossRef]
- Sairam, K.; Gunasekaran, N.; Reddy, S.R. Bluetooth in wireless communication. IEEE Commun. Mag. 2002, 40, 90–96. [Google Scholar] [CrossRef]
- Jordan, R.; Abdallah, C.T. Wireless communications and networking: An overview. IEEE Antennas Propag. Mag. 2002, 44, 185–193. [Google Scholar] [CrossRef]
- Ferro, E.; Potorti, F. Bluetooth and Wi-Fi wireless protocols: A survey and a comparison. IEEE Wirel. Commun. 2005, 12, 12–26. [Google Scholar] [CrossRef]
- Bluetooth Versions Walkthrough and Bluetooth 4.0 Low Energy Development Resources. Available online: https://www.cnx-software.com/2013/06/05/bluetooth-versions-walkthrough-and-bluetooth-4-0-low-e (accessed on 6 June 2018).
- Shrivastava, M. Analysis of security risks in Bluetooth. Int. J. Comput. Acad. Res. 2012, 1, 88–95. [Google Scholar]
- National Institute of Standards and Technology. Guide to Bluetooth Security; NIST 800-121-Rev 1; NIST: Gaithersburg, MD, USA, 2016.
- Mitchell, A. The Car Whisperer: Eavesdrop Onand Take Part in Nearby Bluetooth Conversations. 2005. Available online: https://www.theinternetpatrol.com/the-car-whisperer-eavesdrop-on-and-take-part-in-nearby-bluetooth-conversations/ (accessed on 1 May 2016).
- Dunning, J.P. Bluetooth Threat Taxonomy. Available online: https://vtechworks.lib.vt.edu/bitstream/handle/10919/76883/etd-10242010-163002_Dunning_JP_T_2010.pdf?sequence =1&isAllowed=y) (accessed on 13 April 2018).
- Bluetooth Security. Available online: https://cs.stanford.edu/people/eroberts/courses/soco/projects/2003-04/wireless-computing/sec_bluetooth.shtml (accessed on 6 June 2018).
- Sen, J. Security and Privacy Challenges in Cognitive Wireless Sensor Networks. In Cognitive Radio Technology Applications for Wireless and Mobile Ad hoc Networks; Meghanathan, N., Reddy, Y.B., Eds.; IGI-Global: Hershey, PA, USA, 2013. [Google Scholar]
- Shaked, Y.; Wool, A. Cracking Bluetooth PIN. Available online: http://www.eng.tau.ac.il/~yash/shaked-wool-mobisys05/ (accessed on 6 June 2018).
- Saravanan, K.; Vijayanand, L.; Negesh, R.K. A Novel Bluetooth Man-In-The-Middle Attack Based on SSP using OOB Association model. arXiv, 2012; arXiv:1203.4649. [Google Scholar]
- Moreno, A.; Okamoto, E. BlueSnarf Revisted: OBEX FTP Service Directory Traversal. Available online: https://link.springer.com/content/pdf/10.1007%2F978-3-642-23041-7_16.pdf (accessed on 6 June 2018).
- Ahmed, M.; Musleh, A.; Marouf, A.; Mahmoud, A.; Abu-Amara, M. Bluetooth Security. Available online: https://www.slideshare.net/ram_ari/bluetooth-security (accessed on 7 June 2018).
- Becker, A. Bluetooth Security & Hacks; Seminar ITS Ruhr-Universitat Bochum SS2007; Ruhr University of Bochum: Bochum, Germany, 2007; Available online: https://gsyc.urjc.es/~anto/ubicuos2/bluetooth_security_and_hacks.pdf (accessed on 11 April 2018).
- Carettoni, L.; Merloni, C.; Zanero, S. Studying bluetooth malware propagation: The BlueBag project. IEEE Secur. Priv. 2007, 5, 17–25. [Google Scholar] [CrossRef]
- Trifinite: BlueBump. Available online: https://trifinite.org/trifinite_stuff_bluebump.html (accessed on 6 June 2018).
- BlueDump. Available online: https://trifinite.org/trifinite_stuff_bluedump.html (accessed on 6 June 2018).
- Trifinite: BluePrinting. Available online: https://trifinite.org/trifinite_stuff_blueprinting.html (accessed on 6 June 2018).
- Red Hat CVE-2017-1000251. Available online: https://access.redhat.com/security/cve/cve-2017-1000251 (accessed on 6 June 2018).
- The Attack Vector “BlueBorne” Exposes Almost Every Connected Device. Available online: https://www.armis.com/blueborne/ (accessed on 6 June 2018).
- Tsira, V.; Nandi, G. Bluetooth technology: Security issues and its prevention. Int. J. Comput. Appl. Technol. 2014, 5, 1833–1837. [Google Scholar]
- Nawir, M.; Amir, A.; Yaakob, N.; Lynn, O. Internet of Things (IoT): Taxonomy of Security Attacks. In Proceedings of the 2016 3rd International Conference on Electronic Design (ICED), Phuket, Thailand, 11–12 August 2016. [Google Scholar]
- Haataja, K. Security Threats and Countermeasures in Bluetooth-Enabled Systems. Kuopio University Publications H. Business and Information Technology 13. 2009. Page 75. Available online: http://epublications.uef.fi/pub/urn_isbn_978-951-27-0111-7/urn_isbn_978-951-27-0111-7.pdf (accessed on 14 July 2018).
- Chatterjee, A.; Arora, A.; Pandey, A.; Thakkar, H. Analysis and elicitation of Bluetooth versions and Bluetooth attacks. Int. J. Mod. Comput. Sci. 2017, 5, 3–17. [Google Scholar]
- Trifinite: BluePrinting. Available online: https://trifinite.org/trifinite_stuff_bluesmack.html (accessed on 7 June 2018).
- Using MultiBlue to Control Any Mobile Device. Available online: https://null-byte.wonderhowto.com/how-to/hack-bluetooth-part-2-using-multiblue-control-any-mobile-device-0164377/ (accessed on 6 June 2018).
- Trifinite Group. Available online: https://trifinite.org/trifinite_stuff_helomoto.html (accessed on 1 April 2018).
- Pandey, T.; Khara, P. Bluetooth Hacking and its Prevention. L & T Technology Services. Available online: http://www.larsentoubro.com/media/27618/bluetooth-hacking-and-its-prevention-2014.pdf (accessed on 1 April 2016).
- Naone, E. Taking Control of Cars from Afar. 14 March 2011. Available online: https://www.technologyreview.com/s/ 423292/taking-control-of-cars-from-afar/ (accessed on 11 April 2016).
- Markoff, J. Researchers Show How a Car’s Electronics Can Be Taken over Remotely. Available online: https://www.nytimes.com/2011/03/10/business/10hack.html (accessed on 7 June 2018).
- Trifinite: BluePrinting. Available online: https://trifinite.org/trifinite_stuff_carwhisperer.html (accessed on 7 June 2018).
- IGI Global: Disseminator of Knowledge. Available online: https://www.igi-global.com/dictionary/synchronous-connection-oriented-sco-link/28975 (accessed on 14 July 2018).
- Car Whisperer’ Puts Hackers in the Drivers Seat. Available online: https://www.pcworld.com/article/122077/article.html (accessed on 7 June 2018).
- Wright, J. I Can Hear You Now. Available online: http://www.willhackforsushi.com/presentations/icanhearyounow-sansns2007.pdf (accessed on 7 June 2018).
- Orthogonal. Available online: http://orthogonal.io/articles/developing-bluetooth-enabled-medical-devices/ (accessed on 11 April 2018).
- Bluetooth. Available online: https://www.bluetooth.com /markets/connected-device (accessed on 13 April 2018).
- Zetter, K. It’s Insanely Easy to Hack Hospital Equipment. 25 April 2014. Available online: https://www.wired.com/2014/ 04/hospital-equipment-vulnerable/ (accessed on 10 April 2016).
- Kijewski, M. The Medical Devices Most Vulnerable to Hackers. Available online: https://www.medtechintelligence.com/feature_article/medical-devices-vulnerable-hackers/ (accessed on 10 April 2018).
- Paganini, P. Smartwatch Hacked, How to Access Data Exchanged with Smartphone. 11 December 2014. Available online: http://securityaffairs.co/wordpress/31007/intelligence/smartwatch-hacked.html (accessed on 5 April 2016).
- Melamed, T. An Active Man-in-the-Middle Attack on Bluetooth Smart Devices. Int. J. Saf. Secur. Eng. 2018, 8, 200–211. [Google Scholar] [CrossRef]
- Mobile Fact Sheet. Available online: http://www.pewinternet.org/fact-sheet/mobile/ (accessed on 13 April 2018).
- Loo, A. Security threats of smart phones and Bluetooth. Commun. ACM 2009, 52, 150–152. [Google Scholar] [CrossRef]
- Olick, D. Why 2017 Will Finally be the Year of the Smart Home: Consumers Figure it Out. Available online: https://www.cnbc.com/2017/01/04/why-2017-will-finally-be-the-year-of-the-smart-home-consumers-figure-it-out.html (accessed on 13 April 2018).
- Estes, A.C. This Nest Security Flaw is Remarkably Dumb. Available online: https://gizmodo.com/this-nest-security-flaw-is-remarkably-dumb-1793524264 (accessed on 13 April 2018).
- Google-Nest-Cam-Bug-Disclosures. Available online: https://github.com/jasondoyle/Google-Nest-Cam-Bug-Disclosures/blob/master/README.md (accessed on 7 June 2018).
- Kite-Powell, J. This Company Staged a Hack with Multiple Devices to Show Your Home’s Vulnerability. Available online: https://www.forbes.com/sites/jenniferhicks/2017/09/19/this-company-staged-a-hack-with-multiple-devices-to-show-your-homes-vulnerablity/#654ac4565322 (accessed on 13 April 2018).
- Techopedia. Available online: https://www.techopedia.com/definition/24748/cyberattack (accessed on 13 April 2018).
- Khandelwal, A. Bluetooth Hack Affects 20 Million Amazon Echo and Google Home Devices. Available online: https://thehackernews.com/2017/11/amazon-alexa-hacking-bluetooth.html (accessed on 13 April 2018).
- Wagenseil, P. 75 Percent of Bluetooth Smart Locks Can Be Hacked. Available online: https://www.tomsguide.com/us/bluetooth-lock-hacks-defcon2016,news-23129.html (accessed on 13 April 2018).
- Dibrov, Y. IoT Devices Compromising Your Business Today. Available online: https://www.smartindustry.com/blog/smart-industry-connect/six-iot-devices-compromising-your-business-today/ (accessed on 13 April 2018).
- Samuels, M. With Teddy Bear Bluetooth Hack, 11-Year-Old Proves IoT Security is No Child’s Play. Available online: https://securityintelligence.com/news/with-teddy-bear-bluetooth-hack-11-year-old-proves-iot-security-is-no-childs-play/ (accessed on 13 April 2018).
- Smithers, R. Strangers Can Talk to Your Child through Connected Toys, Investigation Finds. Available online: https://www.theguardian.com/technology/2017/nov/14/retailers-urged-to-withdraw-toys-that-allow-hackers-to-talk-to-children (accessed on 13 April 2018).
- Rakic-Skokovic, M. Guidelines for Overcoming some IoT Security Issues. In Proceedings of the XVII International Scientific Conference on Industrial Systems (IS’17), Novi Sad, Serbia, 4–6 October 2017. [Google Scholar]








© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lonzetta, A.M.; Cope, P.; Campbell, J.; Mohd, B.J.; Hayajneh, T. Security Vulnerabilities in Bluetooth Technology as Used in IoT. J. Sens. Actuator Netw. 2018, 7, 28. https://doi.org/10.3390/jsan7030028
Lonzetta AM, Cope P, Campbell J, Mohd BJ, Hayajneh T. Security Vulnerabilities in Bluetooth Technology as Used in IoT. Journal of Sensor and Actuator Networks. 2018; 7(3):28. https://doi.org/10.3390/jsan7030028
Chicago/Turabian StyleLonzetta, Angela M., Peter Cope, Joseph Campbell, Bassam J. Mohd, and Thaier Hayajneh. 2018. "Security Vulnerabilities in Bluetooth Technology as Used in IoT" Journal of Sensor and Actuator Networks 7, no. 3: 28. https://doi.org/10.3390/jsan7030028
APA StyleLonzetta, A. M., Cope, P., Campbell, J., Mohd, B. J., & Hayajneh, T. (2018). Security Vulnerabilities in Bluetooth Technology as Used in IoT. Journal of Sensor and Actuator Networks, 7(3), 28. https://doi.org/10.3390/jsan7030028





