Secure Downlink Transmission with NOMA-Based Mixed FSO/RF Communications in Space–Air–Ground Integrated Networks
Abstract
1. Introduction
1.1. Background
1.2. Related Works
1.3. Motivations and Contributions
- We propose a novel secure transmission scheme for the SAGIN downlinks, which is a NOMA-based mixed FSO-RF communication system. Additionally, we analyze the secure transmission performance of this system.
- An analytical expression for the secrecy outage probability (SOP) in the presence of an eavesdropper was derived. Furthermore, extensive experiments were conducted to validate the advantages of the proposed NOMA-based mixed FSO-RF communication system and the accuracy of the derived SOP analytical expression.
- We investigated the impact of both amplify-and-forward (AF) and decode-and-forward (DF) relay protocols on the secure transmission performance within SAGIN. Experimental results demonstrate that the DF relay protocol achieves superior secrecy performance compared to the AF scheme.
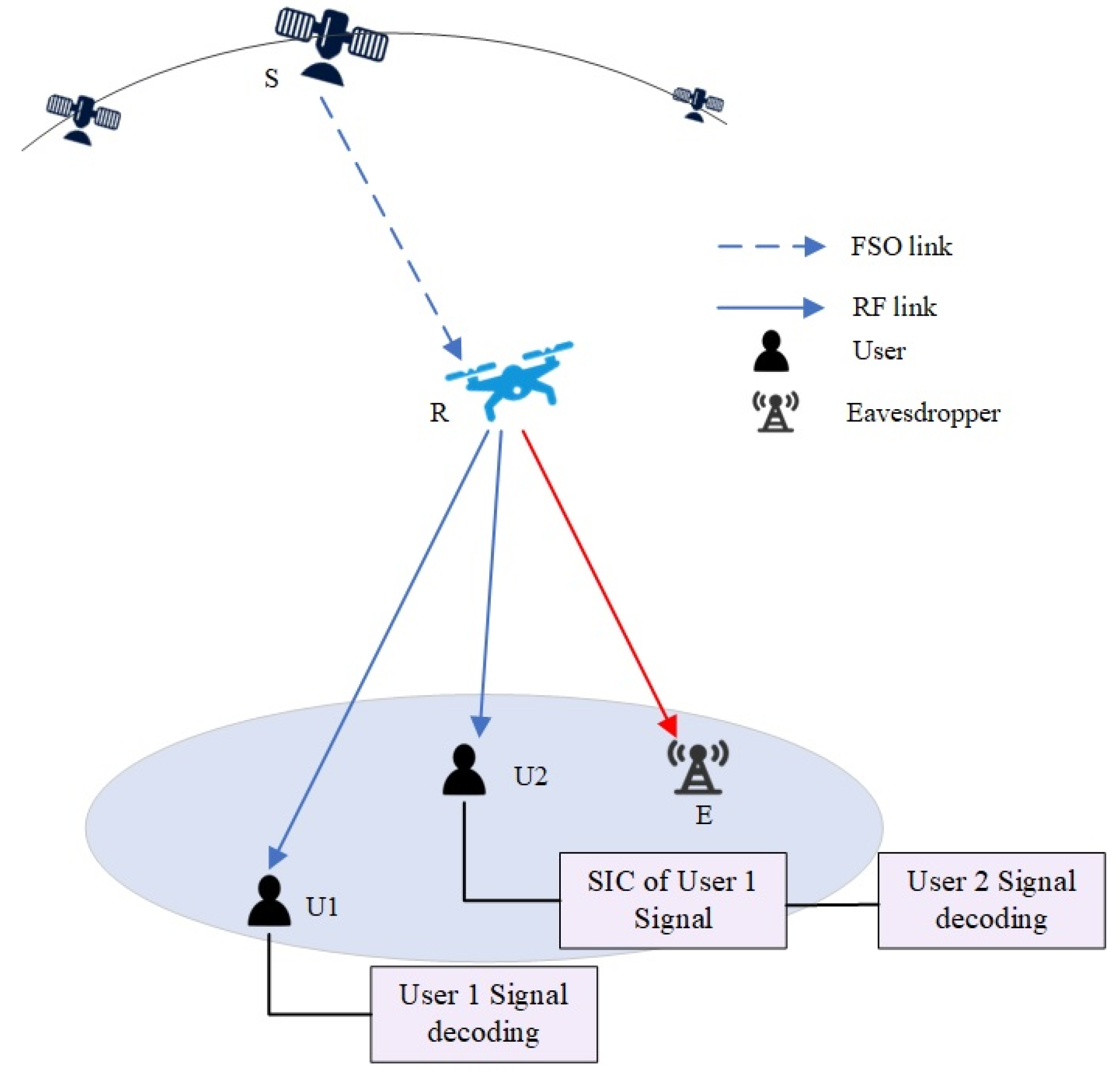
2. System and Channel Models
2.1. S-R FSO Link
2.2. R-U RF Link
- 1.
- AF Relaying
- 2.
- DF Relaying
3. Security Performance Analysis
3.1. Secrecy Capacity
- 3.
- AF Relaying
- 4.
- DF Relaying
3.2. Security Outage Probability
- 5.
- AF Relaying
- 6.
- DF Relaying
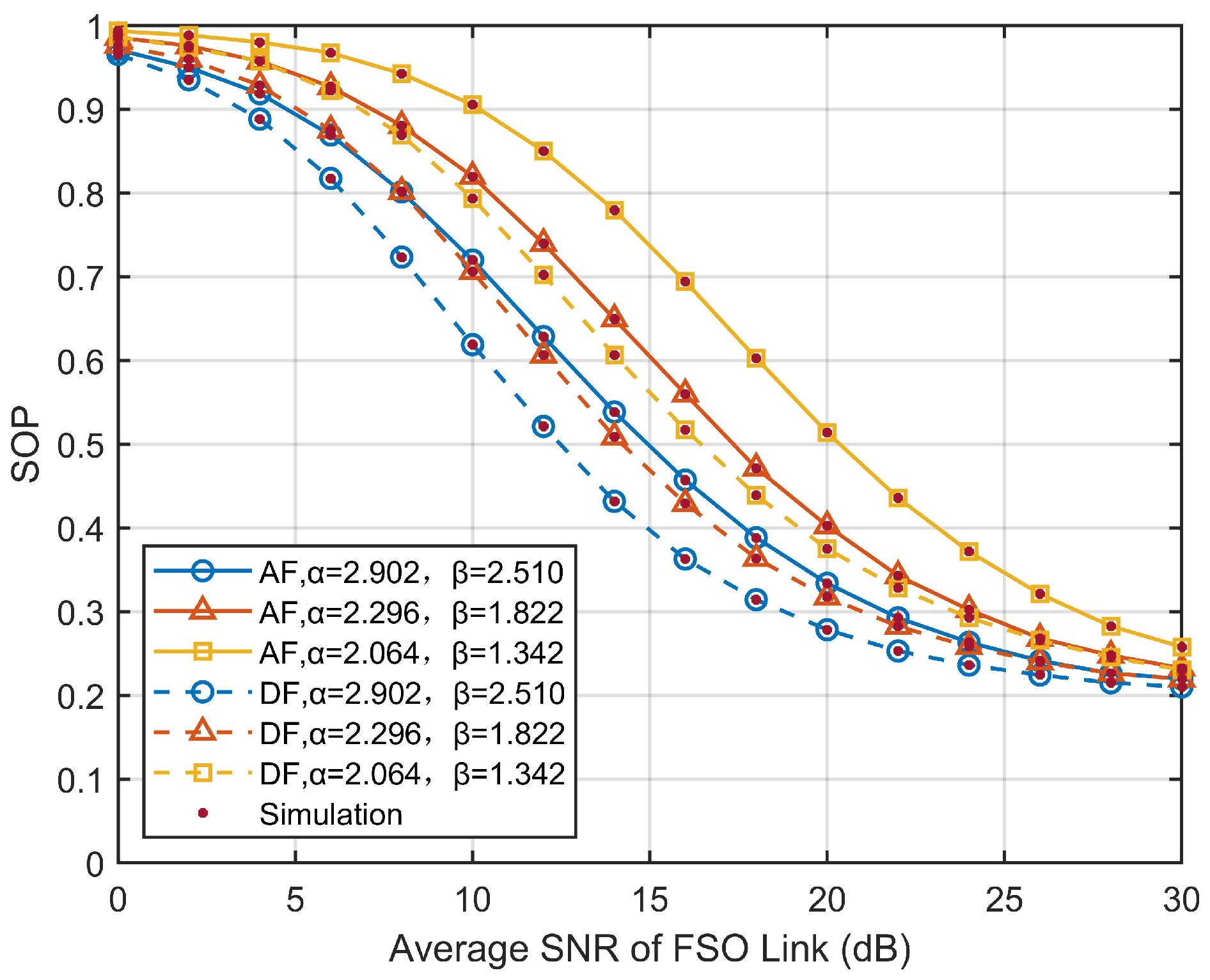
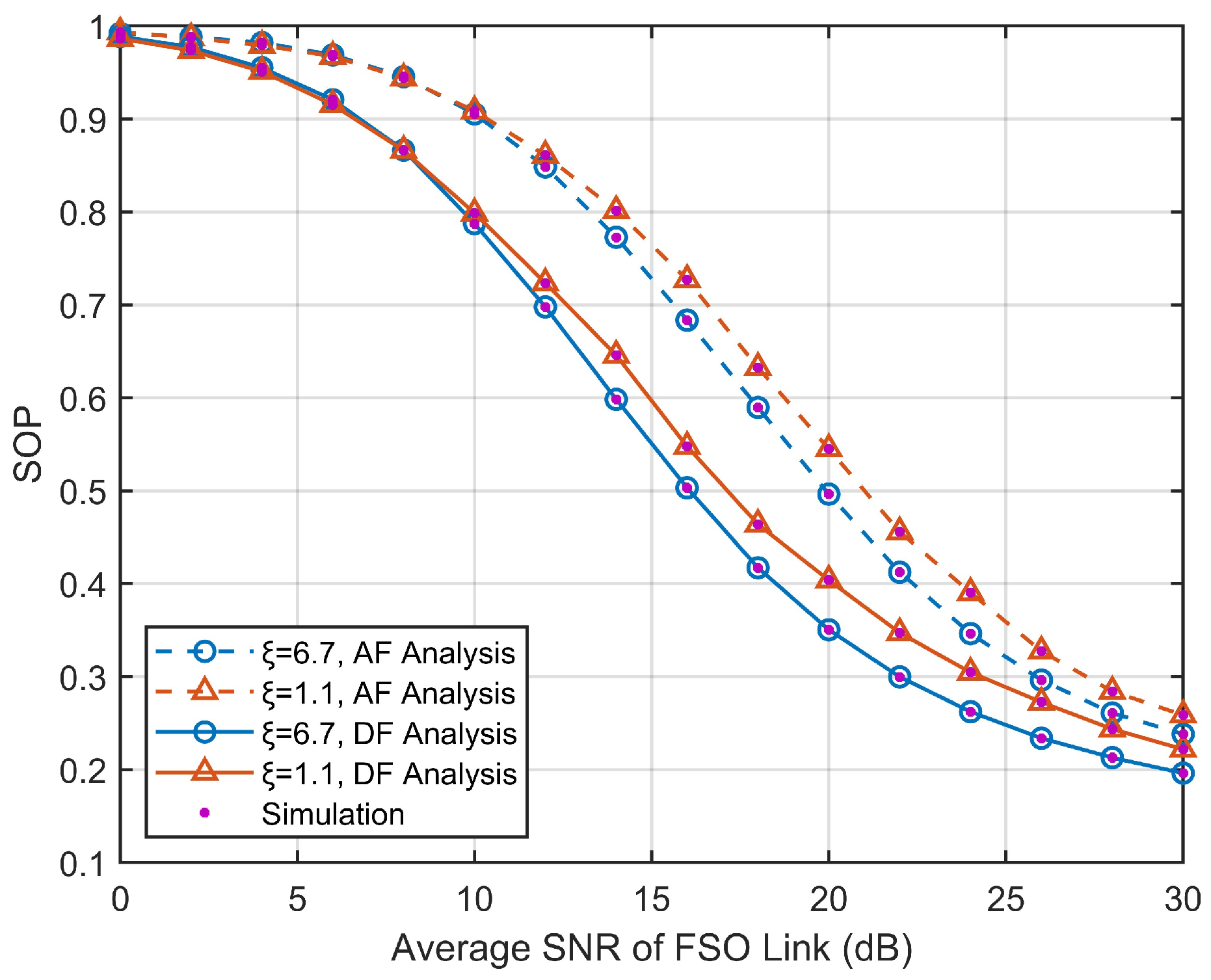
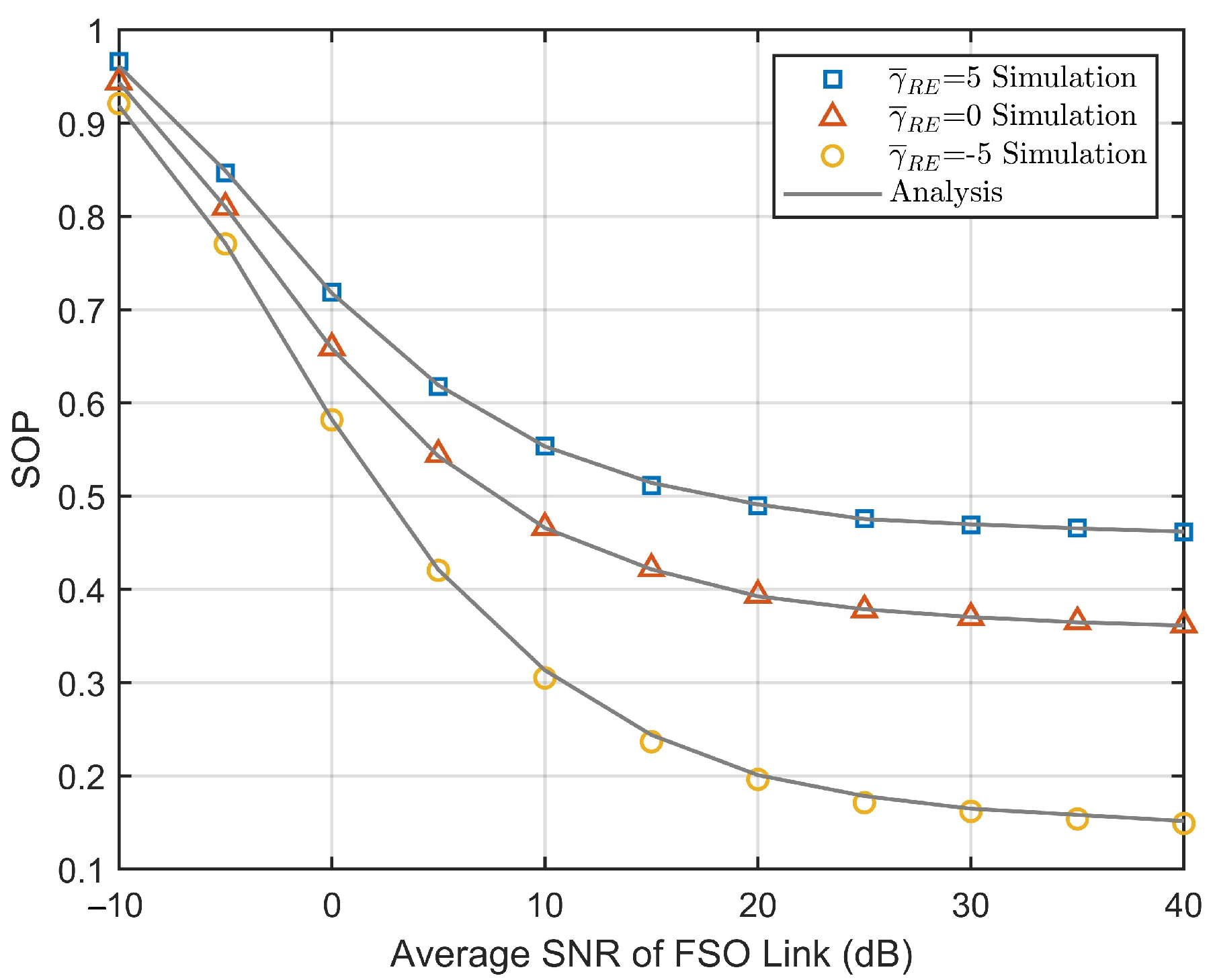
4. Numerical Results and Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Cheng, N.; He, J.C.; Yin, Z.S.; Zhou, C.H.; Wu, H.Q.; Lyu, F.; Zhou, H.B.; Shen, X.M. 6G service-oriented space-air-ground integrated network: A survey. Chin. J. Aeronaut. 2022, 35, 1–18. [Google Scholar] [CrossRef]
- Liu, J.; Shi, Y.; Fadlullah, Z.M.; Kato, N. Space-air-ground integrated network: A survey. IEEE Commun. Surv. Tutor. 2018, 20, 2714–2741. [Google Scholar] [CrossRef]
- Jia, Z.Y.; Sheng, M.; Li, J.D.; Zhou, D.; Han, Z. VNF-Based Service Provision in Software Defined LEO Satellite Networks. IEEE Trans. Wirel. Commun. 2021, 20, 6139–6153. [Google Scholar] [CrossRef]
- Hamza, A.S.; Deogun, J.S.; Alexander, D.R. Classification Framework for Free Space Optical Communication Links and Systems. IEEE Commun. Surv. Tutor. 2019, 21, 1346–1382. [Google Scholar] [CrossRef]
- Khalighi, M.A.; Uysal, M. Survey on Free Space Optical Communication: A Communication Theory Perspective. IEEE Commun. Surv. Tutor. 2014, 16, 2231–2258. [Google Scholar] [CrossRef]
- Zachár, G.; Vakulya, G.; Simon, G. Design of a VLC-based beaconing infrastructure for indoor localization applications. In Proceedings of the 2017 IEEE International Instrumentation and Measurement Technology Conference (I2MTC 2017), Turin, Italy, 22–25 May 2017. [Google Scholar]
- Hayal, M.R.; Elsayed, E.E.; Kakati, D.; Singh, M.; Elfikky, A.; Boghdady, A.I.; Grover, A.; Mehta, S.; Mohsan, S.A.H.; Nurhidayat, I. Modeling and Investigation on the Performance Enhancement of Hovering UAV-Based FSO Relay Optical Wireless Communication Systems under Pointing Errors and Atmospheric Turbulence Effects. Opt. Quantum Electron. 2023, 55, 1–23. [Google Scholar] [CrossRef]
- Yahia, O.B.; Erdogan, E.; Kurt, G.K.; Altunbas, I.; Yanikomeroglu, H. HAPS Selection for Hybrid RF/FSO Satellite Networks. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 2855–2867. [Google Scholar] [CrossRef]
- Zhang, Y.L.; Gao, X.Z.; Yuan, H.; Yang, K.; Kang, J.W.; Wang, P. Joint UAV trajectory and power allocation with hybrid FSO/RF for secure space–air–ground communications. IEEE Internet Things J. 2024, 11, 31407–31421. [Google Scholar] [CrossRef]
- Jamali, M.V.; Mahdavifar, H. Uplink Non-Orthogonal Multiple Access Over Mixed RF-FSO Systems. IEEE Trans. Wirel. Commun. 2020, 19, 3558–3574. [Google Scholar] [CrossRef]
- Islam, S.M.R.; Avazov, N.; Dobre, O.A.; Kwak, K.-S. Power-Domain Non-Orthogonal Multiple Access (NOMA) in 5G Systems: Potentials and Challenges. IEEE Commun. Surv. Tutor. 2017, 19, 721–742. [Google Scholar] [CrossRef]
- Bing, L.; Gu, Y.; Hu, L.; Aulin, T.; Yin, Y.; Wang, J. QoS Provision for Industrial IoT Networking: Multiantenna NOMA Based on Partial CSIT. IEEE Trans. Ind. Informatics. 2024, 20, 8239–8250. [Google Scholar] [CrossRef]
- Bankey, V.; Upadhyay, P.K. Physical Layer Security of Multiuser Multirelay Hybrid Satellite-Terrestrial Relay Networks. IEEE Trans. Veh. Technol. 2019, 68, 2488–2501. [Google Scholar] [CrossRef]
- Mukherjee, A.; Fakoorian, S.A.A.; Huang, J.; Swindlehurst, A.L. Principles of Physical Layer Security in Multiuser Wireless Networks: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 1550–1573. [Google Scholar] [CrossRef]
- Halima, N.B.; Boujemaa, H. Optimal Power Allocation and Harvesting Duration for Mixed RF/FSO Using Non-Orthogonal Multiple Access. Opt. Quantum Electron. 2020, 52, 442. [Google Scholar] [CrossRef]
- Li, R.; Chen, T.; Dang, A. Performance Analysis of a Multiuser Dual-Hop Amplify-and-Forward Relay System with FSO/RF Links. J. Opt. Commun. Netw. 2019, 11, 362–370. [Google Scholar] [CrossRef]
- Zhang, J.L.; Pan, X.J.; Pan, G.F.; Xie, Y.Y. Secrecy Analysis for Multi-Relaying RF-FSO Systems with A Multi-Aperture Destination. IEEE Photonics J. 2020, 12, 1–11. [Google Scholar] [CrossRef]
- Pattanayak, D.R.; Dwivedi, V.K.; Karwal, V.; Ansari, I.S.; Lei, H.; Alouini, M.-S. On the Physical Layer Security of a Decode and Forward Based Mixed FSO/RF Co-Operative System. IEEE Wirel. Commun. Lett. 2020, 9, 1031–1035. [Google Scholar] [CrossRef]
- Lei, H.J.; Luo, H.L.; Park, K.-H.; Ansari, I.S.; Lei, W.J.; Pan, G.F.; Alouini, M.-S. On Secure Mixed RF-FSO Systems with TAS and Imperfect CSI. IEEE Trans. Commun. 2020, 68, 4461–4475. [Google Scholar] [CrossRef]
- Liu, X.; Zhang, J.L.; Luo, W.W.; Song, J.Z.; Xie, Y.Y.; Pan, G.F. Secrecy Outage Analysis for RIS-Assisted Hybrid FSO-RF Systems with NOMA. Digit. Signal Process. 2024, 151, 104561. [Google Scholar] [CrossRef]
- Saber, M.J.; Mazloum, J.; Sazdar, A.M.; Keshavarz, A.; Piran, M.J. On Secure Mixed RF-FSO Decode-and-Forward Relaying Systems with Energy Harvesting. IEEE Syst. J. 2020, 14, 4402–4405. [Google Scholar] [CrossRef]
- Wang, X.H.; He, J.Y.; Xu, G.J.; Chen, J.J.; Gao, Y.H. Secrecy Performance of a Non-Orthogonal Multiple Access-Based Space-Air-Ground Integrated Network System with Stochastic Geometry Distribution of Terrestrial Terminals and Fog Absorption in Optical Link. Aerospace 2024, 11, 306. [Google Scholar] [CrossRef]
- Han, L.Q.; Wang, Y.W. Secrecy outage probability performance of mixed FSO-RF systems with nonzero-boresight pointing errors under three eavesdropping scenarios. Opt. Quantum Electron. 2025, 57, 375. [Google Scholar] [CrossRef]
- Singh, R.; Rawat, M.; Jaiswal, A. On the Physical Layer Security of Mixed FSO-RF SWIPT System with Non-Ideal Power Amplifier. IEEE Photonics J. 2021, 13, 1–17. [Google Scholar] [CrossRef]
- Odeyemi, K.O.; Owolawi, P.A. A Mixed FSO/RF Integrated Satellite-High Altitude Platform Relaying Networks for Multiple Terrestrial Users with Presence of Eavesdropper: A Secrecy Performance. Photonics 2022, 9, 32. [Google Scholar] [CrossRef]
- Osman, A.A.F.; Moualeu, J.M.; Takawira, F.; Yadav, K.; Upadhyay, P.K. On Secure Hybrid RF-FSO MIMO-NOMA Systems with Colluding and Non-Colluding Eavesdroppers. IEEE Wirel. Commun. Lett. 2024, 13, 2472–2476. [Google Scholar] [CrossRef]
- Pattanayak, D.R.; Dwivedi, V.K.; Karwal, V. On the Physical Layer Security of Hybrid RF-FSO System in Presence of Multiple Eavesdroppers and Receiver Diversity. Opt. Commun. 2020, 477, 126334. [Google Scholar] [CrossRef]
- Jurado-Navas, A.; Garrido-Balsells, J.M.; Paris, J.F.; Castillo-Vázquez, M.; Puerta-Notario, A. Impact of Pointing Errors on the Performance of Generalized Atmospheric Optical Channels. Opt. Express 2012, 20, 12550–12562. [Google Scholar] [CrossRef] [PubMed]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Academic: San Diego, CA, USA, 2007. [Google Scholar]
- Wolfram, I. Mathematica Edition, Version 8.0; Wolfram Res. Inc.: Champaign, IL, USA, 2010.
- Ansari, I.S.; Yilmaz, F.; Alouini, M.-S. Performance Analysis of FSO Links Over Unified Gamma-Gamma-Turbulence Channels. In Proceedings of the IEEE Vehicular Technology Conference, Glasgow, UK, 11–14 May 2015; pp. 1–5. [Google Scholar]
- Anees, S.; Bhatnagar, M. Performance of an Amplify-and-Forward Dual-Hop Asymmetric RF–FSO Communication System. J. Opt. Commun. Networking 2015, 7, 124–135. [Google Scholar] [CrossRef]
- Liu, Y.W.; Qin, Z.J.; Elkashlan, M.; Gao, Y.; Hanzo, L. Enhancing the Physical Layer Security of Non-orthogonal Multiple Access in Large-Scale Networks. IEEE Trans. Wirel. Commun. 2017, 16, 1656–1672. [Google Scholar] [CrossRef]
- Davis, P.J.; Rabinowitz, P. Methods of Numerical Integration; Academic Press: New York, NY, USA, 1984. [Google Scholar]
- Fan, L.S.; Lei, X.F.; Yang, N.; Duong, T.Q.; Karagiannidis, G.K. Secure Multiple Amplify-and-Forward Relaying with Cochannel Interference. IEEE Internet Things J. 2016, 3, 704–714. [Google Scholar] [CrossRef]
- Nguyen, B.V.; Kim, K. Secrecy Outage Probability of Optimal Relay Selection for Secure AnF Cooperative Networks. IEEE Commun. Lett. 2015, 19, 2001–2004. [Google Scholar] [CrossRef]
- Mohammad, T.; Nasim, M.; Chahé, N. Performance Analysis of an Asymmetric Two-Hop Amplify-and-Forward Relaying RF–FSO System in a Cognitive Radio with Partial Relay Selection. Opt. Commun. 2022, 505, 127478. [Google Scholar]
- Zedini, E.; Kammoun, A.; Alouini, M.-S. Performance of Multibeam Very High Throughput Satellite Systems Based on FSO Feeder Links with HPA Nonlinearity. IEEE Trans. Wirel. Commun. 2020, 19, 5908–5923. [Google Scholar] [CrossRef]
- Swaminathan, R.; Sharma, S.; Vishwakarma, N.; Madhukumar, A.S. HAPS-Based Relaying for Integrated Space-Air-Ground Networks with Hybrid FSO/RF Communication: A Performance Analysis. IEEE Trans. Aerosp. Electron. Syst. 2021, 57, 1581–1599. [Google Scholar]

| Ref. | FSO | RF | NOMA | Relay | Metrics |
|---|---|---|---|---|---|
| [17] | Gamma-Gamma | Nakagami-m | ✗ | DF | SOP, SPSC |
| [18] | ) | Nakagami-m | ✗ | DF | SOP, EST |
| [19] | ) | Nakagami-m | ✗ | DF | SOP, EST |
| [20] | Gamma-Gamma | Nakagami-m | ✓ | DF | SOP |
| [21] | ) | Nakagami-m | ✗ | DF | SOP, ASC |
| [22] | ) | Shadowed-Rician | ✓ | DF | SOP |
| [23] | Fisher-Snedecor | Nakagami-m | ✗ | DF | SOP |
| [24] | ) | Shadowed-Rician | ✗ | AF | SOP, EST, SPSC |
| [25] | Gamma-Gamma | Shadowed-Rician | ✗ | AF | SOP, COP |
| [26] | Gamma-Gamma | Nakagami-m | ✓ | AF | SOP, ASC |
| [27] | ) | Rayleigh | ✗ | DF | ASC, SOP, EST |
| Parameter | Symbol | Value |
|---|---|---|
| Altitude of satellite | 600 km | |
| Altitude of UAV | 20 km | |
| Altitude of ground user | 5 m | |
| Wavelength | 1550 nm | |
| Conversion coefficients | 0.85 | |
| Pointing error coefficient | 1.1, 6.7 | |
| Diameter of aperture at receiver | 1 m |
| Atmospheric Turbulence | Parameter Values |
|---|---|
| Weak turbulence | |
| Moderate turbulence | |
| Strong turbulence |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Y.; Li, Y.; Li, X.; Zhang, K.; Zhao, S. Secure Downlink Transmission with NOMA-Based Mixed FSO/RF Communications in Space–Air–Ground Integrated Networks. Photonics 2025, 12, 1012. https://doi.org/10.3390/photonics12101012
Li Y, Li Y, Li X, Zhang K, Zhao S. Secure Downlink Transmission with NOMA-Based Mixed FSO/RF Communications in Space–Air–Ground Integrated Networks. Photonics. 2025; 12(10):1012. https://doi.org/10.3390/photonics12101012
Chicago/Turabian StyleLi, Yu, Yongjun Li, Xin Li, Kai Zhang, and Shanghong Zhao. 2025. "Secure Downlink Transmission with NOMA-Based Mixed FSO/RF Communications in Space–Air–Ground Integrated Networks" Photonics 12, no. 10: 1012. https://doi.org/10.3390/photonics12101012
APA StyleLi, Y., Li, Y., Li, X., Zhang, K., & Zhao, S. (2025). Secure Downlink Transmission with NOMA-Based Mixed FSO/RF Communications in Space–Air–Ground Integrated Networks. Photonics, 12(10), 1012. https://doi.org/10.3390/photonics12101012





